|
|

System commands allow host application program control of many configuration parameters and resources. These commands fall into five types: configuration control, system status, system diagnostics, system maintenance, and resource control.
System commands consist of a string of bytes immediately following the Network Header—refer to "Message Structure Overview." Although the format of the commands vary, they all begin with a Function Identifier. Table 4-1 shows the command type and Function ID for each system command.
.
| Function ID | Command Name | Command Type |
|---|---|---|
$49 | ISDN Port Control | Resource Control |
$65 | Subrate Path Control | Resource Control |
$66 | Voice Path Control | System Diagnostics |
$67 | DTMF Collection Control (Standard) | Resource Control |
$67 | DTMF Collection Control (Enhanced) | Resource Control |
$68 | MF Collection Control | Resource Control |
$69 | Outgoing Port Control | Resource Control |
$6A | Incoming Port Control | Resource Control |
$6C | Voice Port Control (Standard) | Resource Control |
$6C | Voice Port Control (Enhanced) | Resource Control |
$6D | Conference Control | Resource Control |
$6E | Speech Collection Control | Resource Control |
$70 | Port Hook State Control | Resource Control |
$72 | Port Supervision Control | System Diagnostics |
$80 | Request Resource Allocation | System Status |
$81 | Request Hardware Allocation | System Status |
$82 | Card Status | System Status |
$83 | Port Status | System Status |
$90 | Change Port Status | System Maintenance |
$91 | Voice Prompt Maintenance | System Maintenance |
$C0 00 | Configure VCA/Set System Clock | Configuration Control |
$C0 01 | Change Active Controllers | Configuration Control |
$C0 02 | T1 Synchronization Control | Configuration Control |
$C0 03 | Set/Reset Host Alarms | Configuration Control |
$C0 04 | Host Load Control | Configuration Control |
$C0 05 | Host Assume/Relinquish Port Control | Configuration Control |
The sections that follow describe each command. The sections are arranged in hexadecimal numerical order according to the command's Function ID.
The description for each command contains the following information:
Each byte in a command is a hexadecimal (base 16) number. Most commands require you to convert this hexadecimal number into binary (base 2) or decimal (base 10) numbers to interpret the byte. A decimal-hexadecimal-binary conversion table is provided in "Decimal/Hexadecimal/Binary Conversion." Users should set all undefined bits and bytes to zero within the present commands to allow for future enhancements.
Byte offset values under the Format heading are counted from the initial byte of the Network Header (byte offset 0 to 3). Interpret these values according to the list below.
| Byte Offset | Meaning |
|---|---|
a | Description applies to that single byte. |
a and b | Description applies to the two consecutive bytes. |
a to c | Description applies to all bytes a through c, inclusive. |
a/b | Description applies to the second nibble of byte a and all of byte b. |
a/n | Description applies to a variable number of consecutive bytes between a and n. |
n + 1 | Description applies to a byte that follows a variable number of bytes (a to n). |
 |
Note Unless otherwise stated, the MF processing described in this chapter applies to both MF and MFCR2 processing. |
Resource Control
Use the ISDN Port Control ($49) command for all call control functions for an ISDN call, including the following:
Use the $49 command to control ISDN B-channels and non-ISDN network interface ports.
This command also supports the control of disconnect at call tear down and the receipt of an ISDN Port Change of State ($EA) report. Refer to "System Reports," for information on system reports.
Total command length cannot exceed 250 bytes.
Specify the controlling port by either B-channel port address or D-channel port address and Call ID.
Choose the associated (outgoing) port in one of two ways: specify the port address, or specify the resource group for the system to reference.
The selected Call ID and B-channel is returned to the host if Return All is set in the Network Header. The returned command is truncated to report only through byte offset 14.
In interworking scenarios, either the controlling or associated port can be a non-ISDN port.
The call is controlled by the D-channel address and Call ID (if a B-channel has been selected, this address would be used instead). D-channel address and Call ID are reported to the host via the ISDN Inpulse Rule Complete ($ED) and ISDN Port Change of State ($EA) reports.
If you specify IEs, code them as they would appear in a D-channel message. IEs specified in the command are included in the next D-channel message transmission.
You can specify the following number of bytes of information for call record digit fields:
For this information, use standard system digit strings, IA5 (ASCII) digits, an IE header, or a complete IE. The information is contained in an Outpulse Control segment; use one segment per field. The Outpulse Control Code byte specifies the format of information contained in the segment. This format corresponds to the FLD, I FLD, and D FLD designations used in the ISDN Message Templates. In addition, you can specify individual IEs to be transmitted without storing the data into a digit field.
Connection of an ISDN incoming port to another ISDN incoming port or ISDN outgoing port to another ISDN outgoing port is supported, provided both ports are in the ACTIVE (answered) state.
The Main Command segment is composed of byte offsets 4 through 19 and must be included in its entirety. Disconnect Control and Rule Control bytes are included in the Main Command segment. Components of the Main Command segment are defined in the next section.
Figure 4-1 shows the byte formatting for this command.

Function ID (byte offset 4)—Byte immediately following the Network Header; uniquely identifies the command to the system.
Controlling Port Address (byte offsets 5 and 6)—Hexadecimal representation of the controlling port circuit address for which the command is sent. If the Controlling Address Identifier (byte offset 9) is $01, these bytes represent the specific B-channel assigned to the call or a non-ISDN port.
 |
Note If the host is to perform B-channel selection, the port address of the target channel should be specified along with the Controlling Call ID (byte offsets 7 and 8). |
Controlling Call ID (byte offsets 7 and 8)—Specifies the ISDN Call ID for the controlling port. If the host is to perform B-channel selection, specify the port address of the target channel along with the Controlling Call ID; set the Controlling Address Identifier (byte offset 9) to $01.
 |
Note You should set the Controlling Call ID value to zero ($00) and let the system assign the appropriate value when the command is processed. |
Controlling Address Identifier (byte offset 9)—Specifies whether the controlling port is identified by Call ID or by B-channel/non-ISDN port. If the host is to perform B-channel selection, specify the port address of the target channel along with the Call ID and set this byte to $01. Specify the byte according to the following list:
Associated Port Address (byte offsets 10 and 11)—Hexadecimal representation of the associated (outgoing) port circuit address for which the command is sent, or the resource group number from which to select the outgoing port. You must set the Associated Address Identifier (byte offset 14) to $01. Byte offsets 10 and 11 represent the specific B-channel to be used, a non-ISDN port, or the resource group number (byte offset 11) from which to select the port; select resource group by setting the P bit in the Connection Control bytes (byte offsets 15 and 16). For a new call, the D-channel designates the interface that carries the call. The actual channel selection depends upon the coding of the Channel ID IE. This IE can be host-specified or system-generated via the ISDN Transmit Message Template.
Associated Call ID (byte offsets 12 and 13)—Specifies the ISDN Call ID for the associated (outgoing) port. When the command is returned to the host, these bytes indicate the Call ID assigned to the call. These bytes must be set to $00 00.
Associated Address Identifier (byte offset 14)—Specifies that the associated (outgoing) port is identified by B-channel/non-ISDN port/resource group. Specify the byte according to the following list:
Connection Control (byte offsets 15 and 16)—Specifies the switching, attaching, hunting, and voice path control options when this command is used to connect a call. Byte offset 16 is reserved for future enhancements and must be set to $00. Construct byte offset 15 according to the following descriptions, then convert to hexadecimal for use in the command.
SAPVV000
The Disconnect Control bytes are always included in the command. You can only define byte offset 17 at this time. Byte offset 17 specifies the disposition of ports when the call is torn down, and the reporting that occurs for DISCONNECT messages, RELEASE messages, and on hook conditions. Byte offset 18 is reserved for future enhancements and should be set to $00.
Bit settings in byte offset 17 are overridden if any of the following commands are processed for either port in the $49 command:
The definition of this byte varies slightly for each case as described in the following text.
If you want to attach an outgoing port (S and A = 1 in byte offset 15 and 16), define the Disconnect Control byte as follows.
Disconnect Control (byte offsets 17 and 18)—Determines what actions to take on a port when the opposite end releases. This byte is ignored when used to attach to a virtual port. Specify values for the Disconnect Control byte, set byte offset 18 to 00. Construct the byte in binary according to the following descriptions, then convert to hexadecimal for use in the command.
0DRTICU0
If you want to detach an outgoing port (S = 1 and A = 0 in byte offset 15), define the Disconnect Control byte as follows.
Disconnect Control (byte offset 17)—Determines what actions to take on the outgoing port when it is detached via this command. The outgoing port may be connected to a virtual port. If you specify values for the Disconnect Control byte, you must set byte offset 18 to 00. Construct the byte in binary according to the following descriptions, then convert to hexadecimal for use in the command.
0DRTICU0
The Rule Control byte is always included in the command, and specifies rule processing. The null outpulse rule (outgoing port seized then transition immediately into wait for final answer - CP_WTFSUP MState) is not supported for ISDN ports. Therefore, if you set this byte to $00, it has no affect on the outcome of the $49 command.
Rule Control (byte offset 19)—Specifies whether an outpulse or inpulse rule is used in this command and the rule number, if any. Construct the byte in binary according to the descriptions that follow, then convert to hexadecimal for use in the command.
X0IRRRRR
The Outpulse Segment Count byte is always included and specifies how many Outpulse Control Segments are in the command. If you set this byte to $00, the IE Control byte follows in offset 21; otherwise, the IE Control byte follows the final Outpulse Control Segment.
Outpulse Segment Count (byte offset 20)—Specifies how many Outpulse Control Segments are included in the command. Convert from decimal to hexadecimal for use in the command. Valid values are from $00 to $05.
An Outpulse Control segment is up to 86 bytes long and is optional. Each segment consists of an Outpulse Control byte, an Outpulse String Length byte, and one or more Outpulse String bytes.
You can use up to five Outpulse Control Segments in a single command. Specify the number of segments with the Outpulse Segment Count byte in byte (offset 20). You must specify a valid outpulse rule for any new originating call attempt which uses an ISDN B-channel. The null outpulse rule is not valid for ISDN B-channels.
Figure 4-2 defines the format and components of the Outpulse Control segment.
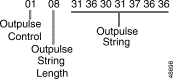
Outpulse Control—Specifies the call record field in which to save the information that follows and the format in which the information is specified. This information can be in the standard system format (binary coded decimal), IA5 (ASCII digits), an intermediate ISDN IE (header only), or a complete ISDN IE. Information can be specified when executing either an inpulse or outpulse rule. The inpulse rule may contain a DO ORULE token. If information will pass to an outpulse rule, construct the byte in binary according to the following descriptions, then convert to hexadecimal for use in the command.
FFF000XX
Outpulse String Length—Specifies the number of bytes in the string. Valid values for the number of bytes is defined as follows:
Outpulse String—Specifies the information to be outpulsed or forwarded. Information must be in the format specified by the Outpulse Control xx bits.
The IE Segment Count byte is used in all $49 commands to specify how many IEs are included in the command. If the Outpulse Segment count (byte offset 20) is set to $00, the IE Segment Count byte appears in offset 21. Otherwise, the IE Segment Count byte follows the final Outpulse Control Segment.
IE Segment Count (byte offset 21 or following final Outpulse Segment)—Specifies how many IEs are included in the command. Convert from decimal to hexadecimal for use in the command.
The IE Segment bytes contain IEs to be transmitted on the D-channel. The number of IEs contained in this segment appears in the IE Segment Count byte. The IEs to be transmitted on the D-channel must be coded exactly as they will appear in the D-channel message. Formats for IEs are contained in Belcore SR-3338.
System processing ensures proper IE ordering. It is assumed that the IEs received in the host command begin with Codeset 0. If you use a different Codeset, you must use the Codeset Shift in the IE count, and an IE segment with the Codeset Shift IE.
A $49 command returned by the system with a network status byte not equal to $01 indicates command was not processed. The following network status bytes may be returned: $03, $05, $0D, $0E, $0F, $11, $12, $15, $16, $17, $18, $1C, $1E, $1F, $20, $23, $24, $25, $26, $29, $2B, $35, $37, $38, $39, and $3C. Refer to "Network Status Byte Definitions," for more information.
If Return All was specified in the Network Header, byte offsets 4 through 14 are returned to the host with the Associated address information included.
Resource Control
Use the Subrate Path Control ($65) command to manage connections (paths) between subrate channels and to establish and maintain subrate connections. You can also use this command to remove a bearer channel connection from the Subrate Switching Card (SSC).
You can establish one-way (listen-only) or two-way connections between subrate channels with this command. To establish multiple connections with a single command, use either of the following modes:
A two-way path that is overwritten by a new path at only one endpoint causes the old destination to be set to idle. Figure 4-3 shows how the same source is switched to transmit to a new destination.

The $65 command allows you to connect or disconnect channels. When you disconnect a channel, you are setting it to listen to idle. When the SSC is brought into service, all paths are set to 8 kbps idle.
Use this command to specify the subrate channels to be switched in terms of how you identify them—by subrate channel width, subrate channel offset, and bearer channel. For example, you may want to switch a subrate channel that is 3 bits wide beginning at offset three on bearer channel 20 of a T1 card. The following rules apply:
Attachment to the Subrate Switching Card
When the system receives a $65 command for subrate path establishment, it checks the destination bearer channels to see if they are already attached to the SSC. If they are not attached and are idle and if there are time slots available on the SSC to which the bearer channels can be attached, then processing for the $65 command automatically attaches the destination bearer channels to the SSC, and the path connection is made.
The following rules apply:
After Attachment
No subrate switching occurs until the system has determined that all specified destination bearer channels are attached to the Subrate Switching Card. Initial connection of a bearer channel to the SSC for subrate path establishment automatically sets the unaddressed, or unused, portion(s) of the bearer channel to listen to idle.
Figure 4-4 shows the byte formatting for this command.

Function ID (byte offset 4)—Byte immediately following the Network Header; uniquely identifies the command to the VCO/4K system.
Control/Options (byte offset 5)—Sets up the conditions to be used for this command. Construct bytes in binary according to the descriptions that follow, then convert to hexadecimal for use in the command. All undefined bits must be set to zero.
D0MB0TPP
Parameter (byte offsets 6 and 7)—Parameter value, defined as follows:
Table 4-2 summarizes the interpretation of the M and B bits in the control options byte and their combined effects on the interpretation of the parameter byte (offsets 6 and 7).
| M | B | Comments |
|---|---|---|
0 | 0 | Parameter value is unused. One path is established between the source and the single destination channels (Source, Destination) or (S, D). |
0 | 1 | One-way or two-way contiguous channel bulk switch. P is the number of contiguous channels to switch in bulk. Source channels are switched one-to-one to destination channels. 'P' channels are switched as paths (S1, D1), (S2, D2),..., (SP, DP). |
1 | 0 | One-way noncontiguous channel broadcast. P is the number of destination channel identifiers included on command. The path control modifier must specify one-way. All destination channels are set to listen to the specified source channel (one-to-many source channel to destination channels). 'P' channels are switched as paths (S, D1), (S, D2),..., (S, DP). |
1 | 1 | One-way contiguous channel broadcast. P is the number of contiguous destination channels to switch to listen to a single source (one-to-many source channel to destination channels). Path control modifier must specify one-way. All destination channels are set to listen to the specified source channel. 'P' channels are switched as paths (S, D1), (S, D2),..., (S, DP). |
Subrate Channel Width/Rate (byte offset 8)—Width or rate, in bits per second, of the subrate channel being established. Valid entries appear in Table 4-3.
| Value | Path Rate |
|---|---|
1 | 8 kbps |
2 | 16 kbps |
3 | 24 kbps |
4 | 32 kbps |
5 | 40 kbps |
6 | 48 kbps |
7 | 56 kbps |
8 | 64 kbps |
Source Path Endpoint (byte offsets 9 to 11)—Port address of the speaker bearer channel (byte offsets 9 and 10) and offset into that channel (in bits) for the start of the subrate channel (byte offset 11). Bit offset entries are 0 to 7 inclusive.
Destination Path Endpoint (byte offsets 12 to 14)—Port address of the listener bearer channel (byte offsets 12 and 13) and offset into that channel (in bits) for the start of the subrate channel (byte offset 14).
If M = 1 and B = 0 in byte offset 5, this three-byte destination endpoint identifier will appear as many times as the number specified in the parameter bytes (byte offsets 6 and 7).
In all other combinations of M and B, only a single destination endpoint identifier is given on the command.
Table 4-4 shows the status codes which may be returned by the $65 command.
| Return Code | Description |
|---|---|
$01 | Successful execution. |
$03 | Syntax error. |
$06 | Port specified in command is not idle. |
$0F | Call or conference is not controlled by this host. |
$12 | Port is not line or trunk. |
$23 | Invalid port address (outside of hardware range). |
$24 | Port address is for a port or card that is not active. |
$29 | Could not be processed due to an internal memory allocation error. |
$5F | Subrate channel width must be greater than zero and less than or equal to eight. |
$60 | Subrate channel crosses bearer channel boundary. |
$56 | Bearer channel is not attached to the SSC (received only when command specifies to detach bearer channel). |
$57 | Bearer channel cannot be attached to an SSC due to timeslot exhaustion. |
$58 | Connection request rejected, no SSC in service. |
$59 | Connection request rejected, card redundancy switchover in process. |
$5A | Connection request rejected, SSC source and destination bearer subchannel overlap. |
$5B | Path removal failed, no such path exists. |
$5D | Path removal failed; path is one-way when the host specified two-way, or two-way when the host specified one-way. |
 |
Note Bearer channels which are assigned by the $65 command cannot be used by any other host command. If this is necessary, detach the bearer channels with the $65 command before you use other host commands for the affected port. |
Figure 4-5 provides a context for the examples that follow by illustrating the four types of switching available with the SSC in terms of the M, B, and PP bits in the control/options byte.

Assume no bearer channels are connected to the SSC—this is the first subrate switching function you are executing in a command. The following command instructs the system to establish a two-way three-bit wide (24 kbps) subrate channel between bearer channels at port addresses $0048 and $0128. The offset of the subrate channel is zero (0) on bearer $0048; offset five (5) on bearer $0128.
04 05 0607 08 091011 121314
65 02 0000 03 004800 012805
Function ID = 65 (Subrate Path Control)
Control/Options = 00000010 (= hexadecimal 02)
Parameter = 00 00 (unused)
Subrate Channel Width = 03 (3 bits wide, a 24-kbps channel)
Source Path Endpoint = 00 48 00
Destination Path Endpoint = 01 28 05
Because this is the first subrate connection made with the respective bearer channels, the unaddressed portions of those bearers are set to listen to the idle pattern automatically by the system.
One subrate connection now exists—the two-way path as commanded. The unaddressed portions of the bearer channels are set to listen to the idle pattern. This path is shown below in triplet form (bearer channel, subrate channel width, offset).
(0048, 03, 00) two-way with (0128, 03, 05), the new two-way path.
The following command will switch 16 one-bit wide subrate channels (8 kbps) in bulk as two-way connections. The source bearer channels are on adjacent bearer port addresses $0048 and $0049. The destination bearer channels are on adjacent bearer port addresses $0128 and $0129.
04 05 0607 08 091011 121314
65 12 0010 01 004800 012800
Function ID = 65 (Subrate Path Control)
Control/Options = 00010010 (= hexadecimal 02)
Parameter = 0010 (= hexadecimal 10, decimal 16)
Subrate Channel Width = 01 (one bit wide, an eight Kbps channel)
Source Path Endpoint = 00 48 00
Destination Path Endpoint = 01 28 00
A total of 16 two-way subrate connections now exist. These paths are shown below in triplet form (bearer channel, subrate channel width, offset).
(0048, 1, 0) two-way with (0128, 1, 0)
(0048, 1, 1) two-way with (0128, 1, 1)
(0048, 1, 2) two-way with (0128, 1, 2)
(0048, 1, 3) two-way with (0128, 1, 3)
(0048, 1, 4) two-way with (0128, 1, 4)
(0048, 1, 5) two-way with (0128, 1, 5)
(0048, 1, 6) two-way with (0128, 1, 6)
(0048, 1, 7) two-way with (0128, 1, 7)
(0049, 1, 0) two-way with (0129, 1, 0)
(0049, 1, 1) two-way with (0129, 1, 1)
(0049, 1, 2) two-way with (0129, 1, 2)
(0049, 1, 3) two-way with (0129, 1, 3)
(0049, 1, 4) two-way with (0129, 1, 4)
(0049, 1, 5) two-way with (0129, 1, 5)
(0049, 1, 6) two-way with (0129, 1, 6)
(0049, 1, 7) two-way with (0129, 1, 7)
System Diagnostics
Use the Voice Path Control ($66) command for immediate setup of voice paths between receivers (A) and senders (B). A receiver is any system resource capable of receiving a signal, and can be an incoming circuit, outgoing circuit, MF receiver, DTMF receiver, DCC port, or CPA port. A sender is any system resource capable of sending a signal, and can be an incoming circuit, outgoing circuit, system tones, voice announcement port (DVC or IPRC), or conference (DCC) port. The voice path remains established until it is torn down by the release of one of the circuits involved, a call processing action, an inpulse or outpulse rule, another $66 command, or a resource control command. You can tear down a two-way path in only one direction, converting it to a one-way path.
The $66 command can also be used to set a conference party to listen to quiet or to another tone. A second $66 command is used to send the party back to the conference.
Minimum command length for the $66 command is 10 bytes. If a command is too short, it is rejected and a syntax error with a status byte of 03 is returned to the host.
This command establishes a voice path between the specified resources without doing any checking of call state. The command does not affect call state or linkages.
Virtual port addresses ($80 00 to $80 FF) cannot be used with this command.
Outpulse channels and voice ports (DVC and IPRC) cannot be used as receivers (A).
MF receiver, DTMF receiver, and CPA ports cannot be used as senders (B).
When the command is used to convert a two-way path into a one-way path, a $66 command is issued with the port to be removed from the two-way path specified as the A address and no B address specified in the command.
When the command is used to set a conference party to listen to a tone, a one-way path is specified with the conference party as the A address, and the tone as B. To return the party to the conference, a second command is sent to break the path; the conference party is specified as the A address and 0 (zero) is specified as the B address.
Figure 4-6 shows the byte formatting for this command.

Function ID (byte offset 4)—Byte immediately following the Network Header; uniquely identifies the command to the system.
Path Control Modifier (byte offset 5)—Determines the type of voice path constructed. Specify this byte according to the following list:
A Address (byte offset 6 and 7)—Port address of the receiver.
B Address (byte offset 8 and 9)—Port address of the sender. The port addresses reserved for tones are listed in "Tone Values."
No response from the system upon successful completion is provided unless Return All has been set in the Network Header. A command that is returned by the system with a network status byte not equal to $01 indicates that the command was not processed. The following network status bytes may be returned: $18, $23, $3C, and $61. Refer to "Message Structure Overview," or "Network Status Byte Definitions," for more information.
Assume there is an incoming circuit at address $20. The following command connects the incoming circuit (receiver - A) to dial tone (sender - B).
04 05 0607 0809
66 01 0020 04C2
Function ID = 66 (Voice Path Control)
Path Control Modifier = 01 (one-way path)
A Address = $0020
B Address = $04C2 (dial tone)
Assume there is an outgoing circuit at address $21, and the voice path established in Example 4-3 is still connected. The following command converts the path from one-way to two-way:
04 05 0607 0809
66 02 0020 0021
Function ID = 66 (Voice Path Control)
Path Control Modifier = 02 (two-way connection)
A Address = $0020
B Address = $0021
Assume the two-way path established in Example 4-4 is still connected (two-way path between $20 and $21). The following command converts the path into a one-way path so that $20 listens to $21, but $21 no longer listens to $20.
04 05 0607 0809
66 00 0021 0000
Function ID = 66 (Voice Path Control)
Path Control Modifier = 00 (break path)
A Address = $0021
B Address = $0000 (no B address specified)
Assume the two-way path established in Example 4-4 is still connected (two-way path between $20 and $21). The following command breaks this path so that both ports listen to quiet.
04 05 0607 0809
66 00 0021 0020
Function ID = 66 (Voice Path Control)
Path Control Modifier = 00 (break path)
A Address = $0021
B Address = $0020
Assume the circuit at address $25 is participating in a conference. The following command removes this port from the conference and sets it to listen to quiet.
04 05 0607 0809
66 01 0025 04C0
Function ID = 66 (Voice Path Control)
Path Control Modifier = 01 (one-way path)
A Address = $0025
B Address = $04C0 (quiet)
Assume the circuit at address $25 is still listening to quiet as shown in Example 4-7. The following command returns this port to the conference in which is was participating.
04 05 0607 0809
66 00 0025 0000
Function ID = 66 (Voice Path Control)
Path Control Modifier = 00 (break path)
A Address = $0025
B Address = $0000 (no B address required)
Resource Control
The DTMF Collection Control ($67) (Standard) command instructs the system to collect DTMF digits sent over any line or trunk circuit without an inpulse rule. It also collects dial pulse (DP) digits on a SLIC or DID circuit. DTMF digits include 1 to 9 inclusive, 0 ($A), and the special characters S ($B) and # ($C). DP digits include 1 to 9 and 0 ($A) only. Digits are sent to the host in the form of a DTMF Digit ($D1) report. The command also attaches or detaches DTMF receivers to or from a trunk. Digits to be used for reenter and end of string can be defined (DTMF only), and the use of beep tones for prompts is allowed. First digit and interdigit timing is set at 6 seconds; field timing, set in Collection Timeout byte, begins when first digit is received. Collection in progress can be terminated by this command; the digits collected until the termination order are returned to the host as a successful DTMF Digit ($D1) report.
An enhanced structure for this command provides control over first digit processing, timers, and internal storage of received digits. Refer to the "DTMF Collection Control ($67) (Enhanced) Command" section for a description of the $67 (Enhanced) command structure.
The minimum command length for the $67 (Standard) command is 10 bytes. If a command is too short, it is rejected and a syntax error with a status byte of 03 is returned to the host.
If this command is used to attach or detach a DTMF receiver, the DTMF Collection Control byte is set to $00, and the bytes following it are not included in the command.
The Controlling Port cannot be participating in a conference. If it is, the command is returned with a network status byte value of $1C.
All DTMF receiver ports must be members of a single resource group for the system to allocate them. It is not necessary to specify the group number in the command; the system determines the resource group from the database configuration.
A DTMF receiver can be attached to any incoming or outgoing T1 or E+M circuit for DTMF digit collection.
SLIC and DID circuits have an on-board DTMF receiver per port; DP digit detection is handled by the firmware resident on the card. UTC circuits have an on-board DTMF receiver per port. When sending a command for these port types, the receiver address should be $000. DTMF digit collections performed for a controlling port residing on a SLIC, DID, or UTC card always use the on-board receiver; a DTMF receiver cannot be allocated to the call.
DP digits can only be collected on a SLIC or DID circuit. Clear and reenter characters and their associated tones are not allowed for DP digit collection. DP digits are reported in a DTMF Digit ($D1) report; no differentiation is made between DP and DTMF digits in this report. The digit string must be all DTMF or all DP. The # and S characters are not supported in DP collection.
Timers specified in seconds can vary as much as ± one half second. This variation affects the $67 standard command and is most pronounced in values set to 1 or 2 seconds.
This command can be used for both DP and DTMF digit collection. In the descriptions that follow, the words DTMF only are used to indicate that the item described is not valid for DP collections and should be set to zero.
Figure 4-7 shows the byte formatting for this command.

Function ID (byte offset 4)—Byte immediately following the Network Header; uniquely identifies the command to the system.
Controlling Port Address (byte offsets 5 and 6)—Hexadecimal representation of the circuit address to which the DTMF receiver is attached.
Receiver Port Control Code (byte offset 7)—Sets up the conditions used for this command. Construct byte in binary according to the descriptions below, then convert to hexadecimal for use in the command. The CCC bits are part of the Receiver Port Address and are included in the conversion from hexadecimal to binary just to provide the proper spacing to interpret the Receiver Port Control Code bits.
SAPR0CCC
DTMF Receiver Port Address (byte offset 7 and 8)—Includes second digit of previous byte (Receiver Port Control Code). If P = 0, this three-digit number is the hexadecimal representation of the receiver port. If P = 1 or the controlling port resides on a SLIC, DID, or UTC, set to $000.
Digit Collection Control (byte offset 9)—Determines if DTMF receiver is to be enabled and the maximum number of digits that can be collected using this command. Construct the byte in binary according to the descriptions below, then convert to hexadecimal for use in the command.
M0FFFFFF
Reenter Digits (byte offset 10)—Determines if the caller is allowed to enter one or two DTMF digits as a reenter code that deletes the digits already entered and begins a new digit string. If only one digit is used, it appears in the first nibble of this byte; the second nibble must be $F. If two digits are used, they appear in the order in which they must be entered by the user. If End of String digits are specified, they must be different from the Reenter digits. In addition to digits 1 to 9, the digit 0 (hexadecimal A) and the characters S (hexadecimal B) and # (hexadecimal C) can be used. If reenter is not allowed, both nibbles must be $F. DTMF only.
End of String Digits (byte offset 11)—Determines if the caller is allowed to enter one or two DTMF digits as an end of string code that signals the end of the digits to be entered. If only one digit is used, it appears in the first nibble of this byte; the second nibble must be $F. If two digits are used, they appear in the order in which they must be entered by the user. If the end of string signal is not allowed, both nibbles must be $F (digits are collected until the total number of digits specified is received, the first digit timer expires, the interdigit timer expires, or the field timer expires). If Reenter digits are specified, they must be different from the End of String digits. In addition to digits 1 to 9, the digit 0 (hexadecimal A) and the characters S (hexadecimal B) and # (hexadecimal C) can be used. DTMF only.
Collection Timeout (byte offset 12)—Specifies the number of seconds, in hex, allowed for the user to enter the number of digits specified in the Digit Collection Control byte minus 1. This timer starts when the first digit is received; first digit timing is always 6 seconds. Valid values for the collection timer are 1 through 60 seconds decimal ($01 to $3C), inclusive, and 0 (timer is not set). Convert from decimal to hexadecimal for the correct value.
User Prompts (byte offset 13)—Determines if a beep tone is used to signal that: the user has entered the reenter code (if allowed); the user has entered the end of string code (if allowed); the DTMF receiver is enabled. Construct byte in binary according to the descriptions on the following page, then convert to hexadecimal for use in the command.
IJK00000
DTMF Digit ($D1) report.
A command returned by the system with a network status byte not equal to $01 indicates that the command was not processed. The following network status bytes may be returned: $03, $0A, $0E, $0F, $11, $12, $13, $16, $17, $18, $1C, $1F, $22, $24, $26, $2C, $33, $34, and $3C. Refer to "Message Structure Overview," or "Network Status Byte Definitions," for more information.
For DRC/8, if Return All in the Network Header is used, the port address of the DTMF receiver requested by resource group number is returned in the port address bytes. For DRC24/48, the port address is not returned. Bytes 7 and 8 are set to 0 (zero). For SLIC, DID, and UTC ports, this address is the same as the controlling port address.
A command returned with a network status byte of $1F indicates that no DTMF receivers were available to satisfy this command. If this returned command is followed by a Resource Limitation ($D6) report, all members of the DTMF resource group were busy (allocated or out of service). If no $D6 is sent, a DTMF resource group does not exist (no members). Refer to the "Resource Limitation ($D6) Report" section for more information.
Assume there is a DTMF receiver at address $50, and an incoming T1 trunk at address $21. The following command attaches the DTMF receiver to the incoming trunk. Notice there are no digits collected, and the digit collection bytes have been omitted.
04 0506 07 0809 10 11
67 0021 05 0000 00 00
Function ID = 67 (DTMF Digit Collection Control)
Controlling Port Address = 0021
Receiver Port Control Code = 11000000
DTMF Receiver Port Address = $050
Digit Collection Control = 00000000
The remainder of the digit collection bytes are unnecessary and omitted.
Assume there is an outgoing E+M trunk at address $21 and a DTMF receiver at address $51. The following command attaches the DTMF receiver to the port and enables it. When the receiver is enabled, the user hears a beep tone (beep tone when receiver enabled), and has 32 seconds to enter seven digits. The reenter code SS allows the user to erase any digits that have been entered and start over.
04 0506 07 0809 10 11 12 13 14 15 16 17 18
67 0021 05 1000 01 11 BB FF 32 00 10 00 00
Function ID = 67 (DTMF Digit Collection Control)
Controlling Port Address = $0021
Receiver Port Control Code = 11010000
DTMF Receiver Port Address = $051
Digit Collection Control = 10000111
Reenter Digits = $BB (SS on telephone)
End of String Digits = none ($FF)
Collection Timeout = 32 seconds
User Prompts = 00100000
Assume there is an incoming UTC circuit at address $108. The following command collects up to 10 digits in 30 seconds. When the on-board receiver is enabled, the user hears a beep tone (beep tone when receiver attached). The end of string code ## allows the user to indicate when all digits have been entered; when this code is received the user hears another beep tone (beep tone for end of string code).
04 0506 07 0809 10 11 12 13 14 15 16 17 18 19
67 0108 00 0000 10 00 10 10 FF CC 01 10 00 00
Function ID = 67 (DTMF Digit Collection Control)
Controlling Port Address = $0108
Receiver Port Control Code = $00 (not required—use on-board receiver)
DTMF Receiver Port Address = $0000
Digit Collection Control = 10001010
Reenter Digits = none ($FF)
End of String Digits = ## ($CC)
Collection Timeout = 30 seconds
User Prompts = 01100000
Resource Control
The DTMF Collection Control ($67) (Enhanced) command instructs the system to collect DTMF digits sent over any line or trunk circuit without an inpulse rule. It also collects dial pulse (DP) digits on a SLIC or DID circuit. DTMF digits include 1 to 9, 0 ($A), and the special characters * ($B) and # ($C). DP digits include 1 to 9 and 0 ($A) only. Digits are sent to the host in the form of a DTMF Digit ($D1) report.
This command also attaches or detaches DTMF receivers to or from a trunk. For DTMF applications, you can define Reenter and End Of String digits. Collection in progress can be terminated by this command; the digits collected until the termination order are returned to the host as a successful DTMF Digit ($D1) report. This command can also be used as a command segment in the Incoming Port Control ($6A) command.
Fourth column DTMF digits A, B, C, and D may be used with the $67 (Enhanced) command only when the system feature flag, "Enable 4th Column DTMF", is enabled. (Refer to the Cisco VCO/4K System Administrator's Guide for more information.) A control bit in the $67 (Enhanced) command indicates the requirement to use a receiver resource which supports fourth column DTMF digits. Command processing verifies whether the fourth column DTMF system feature is enabled when this control bit is set to 1; an error code of $4F is returned if the control bit is set, but the system feature is not enabled.
The fourth column DTMF system feature flag affects the mapping of DTMF digits used in the Reenter/End of String segment of the command. Refer to the "Reenter Digits" and "End of String Digits" explanations which follow.
Features of this command not accessible with the $67 (Standard) command structure include:
The minimum command length for the $67 (Enhanced) command is 10 bytes. If a command is too short, it is rejected and a syntax error with a status byte of 03 is returned to the host.
The $67 (Enhanced) command has the format:
Main Command segment [optional segments...]
The Main Command segment is 8 bytes long (offsets 4 through 11) and must be included in its entirety every time the enhanced structure is used. If the command is used to attach or detach a receiver without further actions, no optional segments are required.
Timers, specified in seconds, may vary ± one-half second. This variation affects the $67 (Enhanced) command and is most pronounced in values set to 1 or 2 seconds.
Four optional segments are available for use with the enhanced $67 command structure.
Each segment can be included only once in a single command. When more than one segment is used, they must appear in the following order—[Collection Timers] [Reenter/End of String] [First Digit] [Enabling Options].
If a segment is not to be included, it is omitted.
If the controlling port (port from which digits are collected) is an outgoing port, the detachment of the outgoing port upon receipt of the first digit cannot be specified in the command.
All DTMF receiver ports must be members of a single resource group for the system to allocate them. It is not necessary to specify the group number in the command; the system determines the resource group from the database configuration.
A DTMF receiver can be attached to any incoming or outgoing T1 or E+M circuit for DTMF digit collection.
SLIC and DID circuits have an on-board DTMF receiver per port; DP digit detection is handled by the firmware resident on the card. UTC circuits have an on-board DTMF receiver per port.
When sending a command for these port types, the receiver address should be $000. DTMF digit collections performed for a controlling port residing on a SLIC, DID, or UTC card always use the on-board receiver; a DTMF receiver cannot be allocated to the call.
Collected digits are reported to the host in a $D1 report and can be stored in any of the controlling port's five digit fields (ANI and Fields 1 through 4). Collected digits may also be appended to the string already contained in one of the digit fields; the field length restrictions of 20 digits for fields 1 through 4 and 12 digits for ANI still apply. Any appended digits in excess of the field limit are reported to the host, but not saved internally by the system.
DP digits can only be collected on a SLIC or DID circuit. Clear and Reenter characters and their associated tones are not allowed for DP digit collection. DP digits are reported in a DTMF Digit ($D1) report; no differentiation is made between DP and DTMF digits in this report. The digit string must be all DTMF or all DP. The # and * characters are not supported in DP collection.
This command can be used for both DP and DTMF digit collection. In the descriptions that follow, the words DTMF only are used to indicate that the item described is not valid for DP collections and should be set to zero.
Figure 4-8 shows the byte formatting for this command.
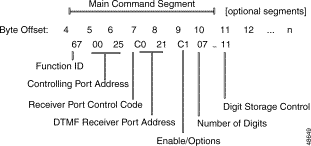
Function ID (byte offset 4)—Byte immediately following the Network Header; uniquely identifies the command to the system.
Controlling Port Address (byte offsets 5 and 6)—Hexadecimal representation of the circuit address to which the DTMF receiver is attached.
Receiver Port Control Code (byte offset 7)—Sets up the conditions used for this command. Construct the byte in binary according to the descriptions that follow, then convert to hexadecimal for use in the command. The CCC bits are part of the Receiver Port Address and are included in the conversion from hexadecimal to binary just to provide the proper spacing to interpret the Receiver Port Control Code bits.
SAPR0CCC
DTMF Receiver Port Address (byte offsets 7 and 8)—Includes second digit of previous byte (Receiver Port Control Code). If P = 0, this three-digit number is the hexadecimal representation of the receiver port. If P = 1 or the controlling port resides on a SLIC, DID, or UTC, set to $000.
Enable/Options (byte offset 9)—Determines if DTMF receiver is to be enabled using this command and which optional segments (if any) are included. Construct the byte in binary according to the descriptions below, then convert to hexadecimal for use in the command.
MND0TRFE
Number of Digits (byte offset 10)—Determines the number of digits to be collected using this command. When S and A = 0 in the Digit Storage Control byte, possible values are 1 to 40, inclusive. Otherwise, the value depends on the field number specified in the Digit Storage Control byte. Convert from decimal to hexadecimal for use in the command.
Digit Storage Control (byte offset 11)—Determines if collected digits are stored in or appended to one of the controlling port's digit collection fields (1 to 4, ANI). Up to 12 digits can be stored in the ANI field, and up to 20 digits in fields 1 through 4. Construct the byte in binary according to the descriptions below, then convert to hexadecimal for use in the command. If digits are not to be stored, this byte must be set to $00.
000SAFFF
The Collection Timers segment is an optional $67 segment that is three bytes in length and specified only when T = 1 in the Enable/Options byte (offset 9). If this condition is true, this segment must appear in byte offsets 12 through 14. Figure 4-9 defines the format and components of the Collection Timers segment.
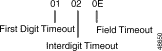
First Digit Timeout—Specifies the number of seconds, in hex, allowed for the user to enter the first digit of the string. This timer starts when the DTMF receiver port is enabled. Allowed values are 1 to 30 seconds (decimal) or $01 to $1E (hexadecimal), and 0 (timer is not set). Convert from decimal to hexadecimal for the correct value.
Interdigit Timeout—Specifies the number of seconds, in hexadecimal, allowed for the user to pause between entering digits. This timer starts when the first digit is received. Allowed values are 1 to 10 seconds (decimal) or $01 to $0A (hexadecimal), and 0 (timer is not set). Convert from decimal to hexadecimal for the correct value.
Field Timeout—Specifies the number of seconds, in hex, allowed for the user to enter the number of digits specified. This timer starts when the first digit is received. Allowed values are 1 to 60 seconds (decimal) or $01 to $3C (hexadecimal) inclusive, and 0 (timer is not set). Convert from decimal to hexadecimal for the correct value.
The Reenter/End of String segment is an optional $67 segment that is five bytes in length and specified only when R = 1 in the Enable/Options byte (byte offset 9). If a Collection Timers segment is included in the command, this segment immediately follows it; if not, this segment begins at byte offset 12. Figure 4-10 defines the format and components of the Reenter/End of String segment.
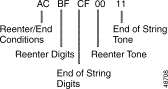
Reenter/End Conditions—Determines conditions for use of Reenter and End of String codes. Construct byte in binary according to the descriptions below, then convert to hexadecimal for use in the command. DTMF only.
RSTUVW00
Reenter Digits—Determines the one or two DTMF digits recognized as the reenter code. If only one digit is used, it appears in the first nibble of this byte; the second nibble must be $F. If two digits are used, they must appear in the order in which they are to be entered by the user. If End of String digits are specified, they must be different from the Reenter digits. Either R or S must be set to 1 in the previous byte. If R and S are both 0 and the D bit in the Enable/Options byte (byte offset 9) is not set, set this byte to $FF. If R and S are both 0 and the D bit in the Enable/Options byte (byte offset 9) is set, set this byte to $00. In addition to digits 1 to 9, the digit 0 (hexadecimal A) and the characters * (hexadecimal B) and # (hexadecimal C) can be used.
If the D bit in the Enable/Options byte (byte offset 9) is set, the DTMF digits in this segment are remapped to utilize fourth-column DTMF digits. DTMF digits 0 to 9 (hexadecimal 0 to 9), A to D (hexadecimal A to D), and the characters * (hexadecimal E) and # (hexadecimal F) can be used.
End of String Digits—Determines the one or two DTMF digits to be recognized as the End of String code. If only one digit is used, it appears in the first nibble of this byte; the second nibble must be $F. If two digits are used, they must appear in the order in which they are to be entered by the user. If Reenter digits are specified, they must be different from the End of String digits. Either T or U must be set to 1 in the previous byte. If T and U are both 0 and the D bit in the Enable/Options byte (byte offset 9) is not set, set this byte to $FF. If T and U are both 0 and the D bit in the Enable/Options byte (byte offset 9) is set, set this byte to $00. In addition to digits 1 to 9, the digit 0 (hexadecimal A) and the characters * (hexadecimal B) and # (hexadecimal C) can be used.
If the D bit in the Enable/Options byte (byte offset 9) is set, the DTMF digits in this segment are re-mapped to utilize fourth-column DTMF digits. DTMF digits 0 to 9 (hexadecimal 0 to 9), A to D (hexadecimal A to D), and the characters * (hexadecimal E), and # (hexadecimal F) can be used.
Reenter Tone—Determines the tone presented upon detection of the reenter code. Refer to "Tone Values," for tones and their values and use the hexadecimal value in the command. Either R or S must be set to 1 in the previous byte. If R and S are both 0, set this byte to $00.
End of String Tone—Determines the tone presented upon detection of the End of String code. Refer to "Tone Values," for tones and their values and use the hexadecimal value in the command. Either T or U must be set to 1 in the previous bit. If T and U are both 0, set this byte to $00.
The First Digit segment is an optional $67 (Enhanced) segment that is two bytes in length and specified only when F = 1 in the Enable/Options byte (offset 9). This segment must follow any Collection Timers or Reenter/End of String segments included in the command. Figure 4-11 defines the format and components of the First Digit segment.
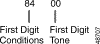
First Digit Conditions—Determines conditions for use of first digit processing. Construct byte in binary according to the descriptions below, then convert to hexadecimal for use in the command. DTMF only.
F000TWAR
First Digit Tone—Determines the tone presented upon detection of the first digit. Refer to "Tone Values," for tones and their values and use the hexadecimal value in the command. T must be set to 1 in the previous byte. If T is 0, set this byte to $00.
The Enabling Options segment is an optional $67 (Enhanced) segment that is up to 16 bytes in length and specified only when E = 1 in the Enable/Options byte (offset 9). This segment must follow any Collection Timers, Reenter/End of String, or First Digit segments included in the command. Figure 4-12 defines the format and components of the Enabling Options segment.
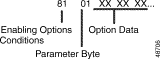
Enabling Options Conditions—Determines conditions for enabling of the DTMF receiver. Construct byte in binary according to the descriptions below, then convert to hexadecimal for use in the command. DTMF only.
D0ATWPSV
Parameter Byte—Contents of this byte are determined by the setting of the Enabling Options byte as follows:
Option Data—Determined by the setting of the Enabling Options byte as follows:
DTMF Digit ($D1) report.
If a report upon receipt of first digit was specified (First Digit segment was included in command with proper bit settings), the first $D1 report received contains only one digit and the report indicates it is a first digit report. The full digit string, including the first digit, is reported in a second $D1 when digit collection ends. Refer to the "DTMF Digit ($D1) (Standard) Report" section for more information.
A command returned by the system with a network status byte not equal to $01 indicates that the command was not processed. The following network status bytes may be returned: $03, $09, $0A, $0E, $0F, $11, $12, $13, $16, $17, $18, $1C, $1F, $22, $24, $26, $27, $2C, $2E, $2F, $30, $33, $34, $3C, $43, $44, $45, $46, $47 and $48. Refer to "Message Structure Overview," or "Network Status Byte Definitions," for more information.
A network status byte value of $4F is returned if fourth-column DTMF digits are used (D bit set in byte offset 9) and the system feature, "Enable 4th Column DTMF", is not enabled.
A network status byte value of $50 (feature semantics error) is returned if fourth-column DTMF digits are used in the Reenter Digits and End of String Digits segments, and the D bit is not set in byte offset 9.
For DRC/8, if Return All is used, the port address of the DTMF receiver requested by resource group number is returned in the port address bytes. For DRC24/48, the port address is not returned. For SLIC, DID, and UTC ports, this address is the same as the controlling port address.
A command returned with a network status byte of $1F indicates that no DTMF receivers were available to satisfy this command. If this returned command is followed by a Resource Limitation ($D6) report, all members of the DTMF resource group were busy (allocated or out of service). If no $D6 is sent, a DTMF resource group does not exist (no members). Refer to the "Resource Limitation ($D6) Report" section for more information on the $D6 report.
Assume there is a DTMF receiver at address $50, and an incoming T1 trunk at address $21. The following command attaches the DTMF receiver to the incoming trunk, sets up collection of 7 digits and places any collected digits into Field 1. The command also starts a 10-second first digit timer, a 6-second interdigit timer, and a 30-second field timer. Finally, the command sets ## as the End of String digits and ** as the Reenter String digits, and presents a beep if the End of String digit terminator is entered.
04 0506 07 0809 10 11 12 13 14 15 16 17 18 19
67 0021 C0 50CC 07 11 0A 06 1E 54 BB CC 00 00
Function ID = 67 (DTMF Collection Control)
Controlling Port Address = $0021
Receiver Port Control Code = 11000000
DTMF Receiver Port Address = $050
Digit Collection Control = 11001100
Number of Digits To Collect = 07
Digit Storage Control = 00010001
The Collection Timers Segment is as follows:
First Digit Timeout = $0A (10)
Interdigit Timeout = $06 (6)
Field Timeout = $1E (30)
The Reenter/End of String Segment is as follows:
Reenter/End Conditions = 01010100
Reenter Digits = $BB (** on telephone)
End of String Digits = $CC (##)
Reenter Tone = 0 (no tone - off due to V bit)
End of String Tone = 0 (beep on End of String code)
Assume there is a DTMF receiver at address $50, and an incoming T1 trunk at address $21. The following command attaches the DTMF receiver to the incoming trunk, sets up collection of 4 digits and appends any collected digits into Field 1. The command does not start a first digit timer, but it does set a 6-second interdigit timer and a 10-second field timer. Finally, the command aborts voice prompts when the first digit is entered, enables the receiver immediately, and plays two voice prompts ("Please dial the number you wish to reach" and "For assistance, dial...") when the receiver is enabled.
04 0506 07 0809 10 11 12 13 14 15 16 17 18 19 20
67 0021 C0 50CB 04 09 00 06 0A 02 00 81 02 11 38
Function ID = 67 (DTMF Collection Control)
Controlling Port Address = $0021
DTMF Receiver Port Address = $050
Digit Collection Control = 11001011
Number of Digits To Collect = 04
Digit Storage Control = 00001001
The Collection Timers Segment is as follows:
First Digit Timeout = 0 (no first digit timing)
Interdigit Timeout = $06 (6)
Field Timeout = $0A (10)
The First Digit Segment is as follows:
First Digit Conditions = 00000010
First Digit Tone = 0 (T = 0)
The Enabling Options Segment is as follows:
Enabling Options Conditions = 10000001
Parameter Byte = 02 (number of voice prompts in command)
Prompt Bytes = $11 $38
Assume there is a DTMF receiver at address $50, and an incoming T1 trunk at address $21. The following command attaches the DTMF receiver to the incoming trunk, sets up collection of 10 digits and stores any collected digits into Field 3. The command starts a 15-second first digit timer, a 6-second interdigit timer and a 10-second field timer. It sets # as the End of String digit and * as the Reenter String digit, and presents a beep tone if # is entered and a dial tone if * is entered. Finally, the command reports the first digit to the host when detected and sends a wink to the outgoing port when the first digit is detected.
04 0506 07 0809 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25
67 0021 F0 00CF 0A 13 0F 06 0A AC AC BF CF 03 00 84 00 82 02 20
Function ID = 67 (DTMF Collection Control)
Controlling Port Address = $0021
Receiver Port Control Code = 11110000
DTMF Receiver Port Address = $050
Digit Collection Control = 11001111
Number of Digits To Collect = $0A (10)
Digit Storage Control = 00010011
Collection Timers Segment
Reenter/End of String Segment
Reenter/End Conditions = 10101100
Reenter Digits = $BF (* on telephone)
End of String Digits = $CF (# on telephone)
Reenter Tone = 3 (Dial tone)
End of String Tone = 0 (beep on End of String code)
The First Digit Segment is as follows:
First Digit Conditions = $84 (10000100)
First Digit Tone = 0 (T = 0)
The Enabling Options Segment is as follows:
Enabling Options Conditions = 10000010
Parameter Byte = 02 (wait for supervision before starting first digit timer)
Prompt Bytes = $20 (wait 32 seconds for answer supervision)
 |
Note Unless otherwise stated, the MF processing described in this section applies to both MF and MFCR2 processing. |
Resource Control
The MF Collection Control ($68) command enables a host to collect the MF digits collection; sent over a trunk circuit. The collected digits are sent to the host in the form of an MF Digit ($D0) report. This command also attaches or detaches MF receivers or MFCR2 transceivers to or from a trunk. Up to 20 MF digits can be collected and stored in a 30-second period (via a single $68 command using one MF receiver port).
This command allows users the option of keeping a call in an active state when garbled digits are received or no KP or ST digits are detected. The default is to consider the error a call failure and tear down the call. Use this command as a command segment in the Incoming Port Control ($6A) command.
The minimum length for the $68 command is 11 bytes. If a command is too short, it is rejected and a syntax error with a status byte of 03 is returned to the host.
All MF receiver ports must be members of a single resource group for the system to allocate them. Also, all MFCR2 transceiver ports must be members of a single resource group. It is not necessary to specify the group number in the command; the system determines the resource group from the database configuration.
The Controlling Port cannot be participating in a conference. If it is, the command is returned with a $1C network status byte.
For MF processing, digits received have KP, ST, STP, ST2P, and ST3P stripped from the MF Digit ($D0) report.
An MF receiver or MFCR2 transceiver can be attached to any incoming or outgoing trunk/line circuit.
The host has the option of tearing down the call upon collection error or keeping the call active. The following conditions are collection errors (call failures):
A garbled MF digit is declared if one of the following conditions exists:
Upon error, the host can specify to either force the controlling port to idle (tear down the call), or place the port in CP_SETUP state to await further host action (such as connection to a live operator). If an error condition occurs, the $D0 report indicates the reason for the call failure and whether the controlling port has been left in CP_SETUP state or forced to idle.
Figure 4-13 shows byte formatting for this command.
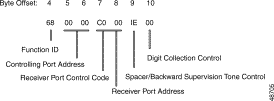
Function ID (byte offset 4)—Byte immediately following the Network Header; uniquely identifies the command to the system.
Controlling Port Address (byte offset 5 and 6)—Hexadecimal representation of the circuit address to which the MF receiver is attached.
Receiver Port Control Code (offset byte 7)—Bits 7 to 3 (SPARE bits) set up the conditions used for this command. Construct byte in binary according to the descriptions that follow, then convert to hexadecimal for use in the command. Bits 2 to 0 (CCC bits) are part of the Receiver Port Address and are included in the conversion from hexadecimal to binary just to provide the proper spacing to interpret the Receiver Port Control Code bits.
SAPRECCC
Receiver Port Address (byte offsets 7 and 8)—Includes bits 0, 1, and 2 of byte 7. If P = 0, this three-digit number is the hexadecimal representation of the receiver port. If P = 1, set to $000.
Spacer Byte/Backward Supervision Tone (byte offset 9)—In MF processing, this byte is not used and is reserved for future enhancements; set to $00.
In MFCR2 processing, this byte determines the backward supervision tone and end-of-collection backward supervision tone to be used in controlling the collection process.
IIIIEEEE
Digit Collection Control (byte offset 10)—Determines if MF collection is enabled or not; specify the byte according to the list below.
EMNNNNNN
 |
Note Bits 0 to 5 are used for MFCR2 processing only. |
MF Digit ($D0) report.
The report contains either valid digit report or error indicator. Possible errors include: KP not received within 15 seconds (timeout); ST not received within 30 seconds (timeout); digit off time > 6 seconds (timeout); and digit on time > 6 seconds (garbled digit). Refer to the "MF Digit ($D0) Report" section for more information.
A command returned by the system with a network status byte not equal to $01 indicates command was not processed. The following network status bytes may be returned: $03, $0A, $0E, $0F, $11, $12, $14, $16, $17, $18, $1C, $1F, $22, $24, $26, and $3C. Refer to "Message Structure Overview," or "Network Status Byte Definitions," for more information.
A command returned with a network status byte of $1F indicates no MF receivers were available to satisfy this command. If this returned command is followed by a Resource Limitation ($D6) report, all members of the MF resource group were busy (allocated or out of service). If no $D6 report is sent, an MF resource group does not exist (no members). Refer to the "Resource Limitation ($D6) Report" section for more information.
If Return All is used, the port address of the MF receiver requested by resource group number is returned in the port address bytes.
Assume there is a trunk at address $19. The following command attaches an MF receiver from the MF resource group to the trunk, without enabling the receiver.
04 0506 07 0809 10
68 0019 E0 0000 00
Function ID = 68 (MF Collection Control)
Controlling Port Address = $0019
Receiver Port Control Code = 11100000
MF Receiver Port Address = $000 (use MF receiver group)
Spacer Byte = 00
Digit Collection Control = 00 (do not enable receiver)
Assume there is a trunk at address $18 and an MF receiver at address $60. The following command attaches the MF receiver to the trunk, enables the receiver, and collects a string of MF digits. After digit collection, the receiver is detached. If an error occurs, the controlling port is placed into CP_SETUP state until further host action.
04 0506 07 0809 10
68 0018 D8 6000 80
Function ID = 68 (MF Collection Control)
Controlling Port Address = $0018
Receiver Port Control Code = 11011000
MF Receiver Port Address = $060
Spacer Byte = 00
Digit Collection Control = 80 (enable receiver)
Assume there is a trunk at address $208. The following command hunts an MF receiver, attaches it to the trunk, enables the receiver, and collects a string of MF digits. After digit collection, the receiver is detached. If an error occurs, the controlling port is reordered through PST processing.
04 0506 07 0809 10
68 0208 E0 0000 80
Function ID = 68 (MF Collection Control)
Controlling Port Address = $0208
Receiver Port Control Code = 11011000
MF Receiver Port Address = $000 (use MF receiver group)
Spacer Byte = 00
Digit Collection Control = 80 (enable receiver)
Resource Control
Use the Outgoing Port Control ($69) command to link or remove outgoing circuits to or from a call's resource chain. This command also begins outpulse or inpulse rule processing for outgoing ports. Digit strings contained in call record fields can be overwritten and new digits supplied using this command. Control of disconnect at call teardown and receipt of on hook reports is also included. This command can be used as a command segment in the Incoming Port Control ($6A) command.
Use fourth-column DTMF digits with the $69 command only when the system feature flag, "Enable 4th Column DTMF" is enabled. No explicit indicator is used in the $69 command. The fourth-column DTMF system feature flag affects the mapping of DTMF digits used in the digit string portion of the command. Refer to the Digit String explanation below.
The minimum length for the $69 command is 11 bytes. If a command is too short, it is rejected and a syntax error with a status byte of 03 is returned to the host.
The $69 command has the following format:
Main Command segment [optional Disconnect Control byte] Outpulse Control segment
Both the Main Command segment and the Outpulse Control segment must be included every time the command is used. At least one Outpulse Control segment is required in the command. Up to five Outpulse Control segments can be included in a single command.
Use of the optional Disconnect Control byte is determined by a bit setting in the Main Command segment. When used, it must appear in byte offset 10. One or more Outpulse Control segments must then follow it. When the command is constructed without the optional Disconnect Control, default settings are used so that when one end hangs up the other end is forced idle with Permanent Signal Timing and both on hooks are reported to the host.
Up to 20 digits can be specified for each field, up to 12 for ANI. These digits are contained in an Outpulse Control segment; one segment is used per field. This command can affect all aspects of call processing: voice paths, states, resource linkages, and supervision.
This command can use virtual ports as the controlling port. The Controlling and Outgoing Ports cannot participate in a conference. If either does, the command is returned with a $1C network status byte.
For outgoing SLIC ports and other ports that require only a seizure, the Rule Control byte can be set to $80. This calls the null outpulse rule that performs a seizure only.
DID ports are supported by this command as an incoming (controlling) port only.
To execute an inpulse or outpulse rule on an already off hook outgoing port or to idle an outgoing port with no incoming port attached, the controlling port address can be set to $00 00. This allows rule execution on an outgoing port in CP_SETUP state that has been detached from a call or conference. If the controlling port address is set to $00 00 and no inpulse or outpulse rule is specified, the command will idle an outgoing port left in setup state with no incoming port attached, making the port available for allocation.
The $69 command operates in conjunction with the Auto Retry feature for outgoing ports. When hunting from an outgoing port resource group and a supervision error is detected for the outgoing port, call processing can rehunt the group and replace the outgoing port. This feature and the number of rehunts performed is configured using the system administration Resource Group Summary screen. Refer to the Cisco VCO/4K System Administrator's Guide for more information.
Figure 4-14 shows the byte formatting for this command.
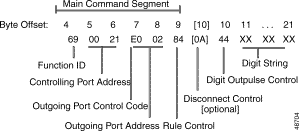
The Main Command segment is composed of byte offsets 4 through 9 and must be included in its entirety. Components of the Main Command segment are defined as follows:
Function ID (byte offset 4)—Byte immediately following the Network Header; uniquely identifies the command to the system.
Controlling Port Address (byte offset 5 and 6)—Hexadecimal representation of the incoming circuit address to which the outgoing port is or will be linked. When using this command to execute a rule on an outgoing port in CP_SETUP state (no incoming port attached), these bytes must be set to $00 00.
Outgoing Port Control Code (byte offset 7)—Sets up the conditions for this command. Construct byte in binary according to the following description, then convert to hexadecimal for use in the command. The CCC bits (see next page) are part of the Outgoing Port Address and are included in the conversion from hexadecimal to binary to provide the proper spacing to interpret the Outgoing Port Control Code bits.
SAPVVCCC
Outgoing Port Address (byte offset 7 and 8)—Includes second digit of previous byte (Outgoing Port Control Code). If P = 0, this three-digit number is the hexadecimal representation of the outgoing circuit. If P = 1, this three-digit number is the hexadecimal representation of the resource group to hunt for an available circuit; convert decimal to hexadecimal for the group number.
Rule Control (byte offset 9)—Determines if an outpulse or inpulse rule is used in this command and the rule number, if any. Also includes bit setting that determines if the command is compatible with V2.01 applications (if bit N = 1 the command is not compatible with V2.01). Construct the byte in binary according to the descriptions that follow, then convert to hexadecimal for use in the command.
XNIRRRRR
The Disconnect Control byte is used only when N = 1 in the Rule Control byte (offset 9). In addition to determining the disposition of ports when the call is torn down, this byte also specifies the reporting that occurs for on hook conditions. When N = 1 in byte offset 9, the Disconnect Control byte appears in byte offset 10.
This byte is processed by the system in the following two cases:
The Disconnect Control byte is ignored when the outgoing port is being attached to a virtual incoming port. Also, bit settings in this byte are overridden if any of the following commands are processed for either port in this $69 command:
The definition of this byte varies slightly for each case as described in the text that follows.
When attaching an outgoing port (S and A = 1 in byte offset 7), the Disconnect Control byte is defined as follows.
Disconnect Control (byte offset 10)—Included only if N = 1 in the Rule Control byte. This byte determines what actions to take on a port when the opposite end goes on hook. It is ignored when used to attach to a virtual port. Construct the byte in binary according to the descriptions below, then convert to hexadecimal for use in the command.
000TICU0
When detaching an outgoing port (S = 1 and A = 0 in byte offset 7), the Disconnect Control byte is defined as follows.
Disconnect Control (byte offset 10)—Included only if N = 1 in the Rule Control byte. Determines what actions to take on the outgoing port when it is detached via this command. The outgoing port may be connected to a virtual port. Construct the byte in binary according to the following descriptions, then convert to hexadecimal for use in the command.
000TICU0
Outpulse Control Segment
The Outpulse Control segment is up to 11 bytes long and it is used in all $69 commands. Always use a single-byte Outpulse Control segment of $00 to terminate this command. You can use up to five Outpulse Control segments in a single command. When a Disconnect Control byte is used, the first Outpulse Control segment begins at byte offset 11; otherwise the first segment begins at byte offset 10. The Outpulse Control segment is defined as follows.
Digit Outpulse Control—Specifies the call record field into which the digit string that follows is to be saved, and the number of digits in the string. The final byte of this command must always be a Digit Outpulse Control Byte = $00 to signal that there are no further digits to be outpulsed. If the digit string contained in a field is to be replaced by a new digit string, the field number and string are specified here. Only the field specified here is replaced; digit strings in any other field contained in the outpulse rule remain unchanged and are processed. Digit strings can be specified when executing either an inpulse or outpulse rule; the inpulse rule may contain a DO ORULE token. If a digit string is to be passed to an outpulse rule, construct the byte in binary according to the descriptions below, then convert to hexadecimal for use in the command.
FFFNNNNN
Digit String—The digit string contains half as many bytes as specified in the NNNNN bits. Each nibble in the hexadecimal byte represents a single digit; digits represented are from 1 to 9 inclusive, 0 ($A), plus the special characters * ($E) and # ($F). If there is an odd number of digits in the string, the second digit of the final byte should be 0. Up to 20 digits can be specified (up to 12 for ANI).
If the system feature "Enable 4th Column DTMF" is set, the DTMF digits in this string are remapped to utilize fourth-column DTMF digits. DTMF digits 0 to 9 (hexadecimal 0 to 9), A to D (hexadecimal A to D), and the characters * ($E), and # ($F) can be used.
 |
Note The special characters * and # are represented differently in DTMF Digit ($D1) reports and $69 command outpulse segments. In $D1 reports, * and # are indicated by the hexadecimal characters $B and $C, respectively. |
If the system feature "Enable 4th Column DTMF" is set, the DTMF Digit ($D1) report indicates * and # with the hexadecimal characters $E and $F, respectively.
No response from the system upon successful completion unless Return All has been set in the Network Header. A command returned by the system with a network status byte not equal to $01 indicates that the command was not processed. The following network status bytes may be returned: $03, $0D, $0E, $0F, $11, $12, $15, $16, $17, $18, $1C, $1F, $20, $22, $23, $24, $25, $26, $2B, $35, $37, $3A and $3C. Refer to "Message Structure Overview," or "Network Status Byte Definitions," for more information.
A network status byte value of $4F is returned if fourth-column DTMF digits are used and the system feature "Enable 4th Column DTMF" is not enabled.
A $DA report is generated when any supervision error is detected, or a supervision event occurs for which a REP or ANSREP condition token has been specified in the answer supervision template called by the outpulse rule, or a REP END is used in an outpulse rule.
If more than 20 digits are specified for a single digit string, the command is processed without error return, but only the first 20 digits of the string are stored and outpulsed.
A command returned with a network status byte of $1F indicates that no outgoing ports were available in the resource group and is followed by a Resource Limitation ($D6) report. A network status byte of $25 indicates that the command could not be processed because all outpulsing channels are busy, but is not followed by a $D6 report. Refer to the "Resource Limitation ($D6) Report" section for more information.
If Return All is used, the port address of any resource that was requested by resource group number is returned in place of the group number.
When the incoming port is on a T1, E+M, or UTC, answer supervision is passed back to the incoming when the call goes stable.
Assume there is a nonidle incoming circuit at address $0018. The following command attaches an idle outgoing circuit from resource group 2 to the incoming circuit, begins outpulse rule 4, and passes it three digits to be placed in call field 2, and seven digits to be placed in call field 4.
04 0506 07 0809 10 11 12 131415161718
69 0018 E0 0284 43 6A 30 875551234000
The Main Command Segment is as follows:
Function ID = 69 (Outgoing Port Control)
Controlling Port Address = $0018
Outgoing Port Control Code = 11100000
Outgoing Port Address = resource group 2 ($002)
Rule Control = 10000100
The Outpulse Control Segment 1 is as follows:
Digit Outpulse Control = 01000011
Digit String = 603 (final 0 is ignored)
The Outpulse Control Segment 2 is as follows:
Digit Outpulse Control = 10000111
Digit String = 5551234 (final 0 is ignored)
The Outpulse Control Segment 3 is as follows:
Digit Outpulse Control = 00 (no further digits in command)
The following command attaches the idle outgoing circuit at address $20 to the nonidle incoming circuit at address $18. No outpulsing is specified, and no digits are sent, so the digit string is omitted.
04 0506 07 0809 10
69 0018 C0 2000 00
Function ID = 69 (Outgoing Port Control)
Controlling Port Address = $0018
Outgoing Port Control Code = 11000000
Outgoing Port Address = $20
Rule Control = 00000000
The Outpulse Control Segment is as follows:
Digit Outpulse Control = 00 (no further digits in command)
Assume the circuit at $10F is an incoming port with a COS = AT and in a setup state (CP_SETUP). Also assume that the circuit at $45 is an outgoing port that was first in a stable call, then participating in a conference, and finally removed from the conference (currently in CP_SETUP). The following command places these two ports into a stable call.
04 0506 07 0809 10
69 010F D0 4500 00
Function ID = 69 (Outgoing Port Control)
Controlling Port Address = $010F
Outgoing Port Control Code = 11000000
Outgoing Port Address = $45
Rule Control = 00000000
The Outpulse Control Segment is as follows:
Digit Outpulse Control = 00 (no further digits in command)
Assume the circuit at $256 is an incoming T1 port that has gone off hook and is awaiting host action. Resource group 10 contains SLIC ports with COS = O. The command below hunts group 10 for an idle SLIC port, executes the null outpulse rule (seize only), then places both ports into a wait for answer state (CP_WANS for the incoming, CP_WTFSUP for the outgoing). When the SLIC port goes off hook, answer supervision is returned to the incoming T1 port. When the outgoing SLIC goes on hook, the incoming T1 is returned to CP_SETUP to await further action (Disconnect Control byte included in command at byte offset 10).
04 0506 07 0809 10 11
69 0256 E8 0AC0 08 00
Function ID = 69 (Outgoing Port Control)
Controlling Port Address = $0256
Outgoing Port Control Code = 11101000
Outgoing Port Address = resource group 10 ($A)
Rule Control = 11000000
Disconnect Control Byte = 00001000
The Outpulse Control Segment is as follows:
Digit Outpulse Control = 00 (no further digits in command)
Assume the outgoing circuit at $11F has been attached to the virtual call generation incoming port $8012, an outpulse rule was executed and the port has answered. The following command detaches the outgoing port from the virtual so that further action can be taken (prompts played, connection made to another call, etc.).
04 0506 07 0809 10 11
69 8012 81 1F40 02 00
Function ID = 69 (Outgoing Port Control)
Controlling Port Address = $8012
Outgoing Port Control Code = 10000001
Outgoing Port Address = resource group 10 ($A)
Rule Control = 01000000
Disconnect Control Byte = 00000010
The Outpulse Control Segment is as follows:
Digit Outpulse Control = 00 (no further digits in command)
Resource Control
Use the Incoming Port Control (Macro) ($6A) command to instruct the system to force call origination or disconnect, begin an inpulse or outpulse rule, or execute one of the following commands or segments:
Specify only one inpulse rule, outpulse rule, or command segment in a single command. Up to five Outpulse Control segments can be included in a single command when an outpulse or inpulse rule is specified for an incoming port. Command segments follow the general format for their command, but the Function ID, any trailing Spacer Bytes, and Controlling Port Address, are omitted. Spacer Bytes in the MF Collection Control ($68) command segment must be included whenever it is used.
Control of disconnect at call tear down and receipt of Permanent Signal Condition/on hook reports are also included in this command.
The minimum length for the $6A command is 12 bytes. If a command is too short, it is rejected and a syntax error with a status byte of 03 is returned to the host.
The $6A command has the format:
Main Command segment [optional segment(s)...]
Use only one command segment in a single command. Up to five Outpulse Control segments can be included.
This command can be used with virtual call generation ports. Specify the virtual port by either address, or as a hunt from resource group $FE.
When a physical port is used as the Incoming (Controlling) port, it must be off hook and in a nonidle state in order for this command to be processed, except in the case of forced origination. For forced origination, port must have a COS = A and be off hook and idle, or a virtual port.
If an inpulse or outpulse rule is specified in the command, no command segments can be attached.
Call origination can be forced by setting S = 1 and A = 1 in the Incoming Port Control Code byte. The port specified in the Controlling Port Address bytes must be either a physical port with COS = A and be off hook and idle, or a virtual port. An inpulse rule or command segment can also be specified.
Because the incoming port must be off hook, a $72 command segment can only be used to unseize an incoming port or for T1 or UTC hookflash. Refer to the "Port Supervision Control ($72) Command" section for more information.
DID ports are supported by this command as an incoming (controlling) port only.
This command can be used to transfer an incoming port by causing a disconnect while maintaining the port in setup state, and then including a $69 segment that attaches a new outgoing port.
Figure 4-15 shows the byte formatting for this command.
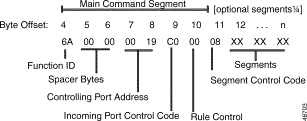
The Main Command segment is composed of byte offsets 4 to 11 and must be included in its entirety. Components of the Main Command segment are defined as follows.
Function ID (byte offset 4)—Byte immediately following the Network Header; uniquely identifies the command to the system.
Spacer bytes (byte offsets 5 and 6)—The lower byte and a half are reserved for referencing or "naming" a call; the remaining bytes are reserved for future enhancements.
Controlling Port Address (byte offsets 7 and 8)—If P = 0 (below), hexadecimal representation of the incoming circuit. If P = 1, this number is the hexadecimal representation of the resource group number to hunt for an available circuit.
Incoming Port Control Code (byte offset 9)—Sets up the conditions used for this macro command. Construct the byte in binary according to the descriptions below, then convert to hexadecimal for use in the command.
SAPTICU0
Rule Control (byte offset 10)—Determines if an inpulse or outpulse rule is used in this macro command, and the rule number, if any. Construct byte in binary according to the descriptions below, then convert to hexadecimal for use in the command.
I0URRRRR
Segment Control Code (byte offset 11)—Identifies the Resource Control command segment included in this macro; a segment is allowed only if Inpulse Rule Control byte = 0. Construct the byte in binary according to the descriptions below, then convert to hexadecimal for use in the command.
CDMAPSD0
Optional Segments consists of the command segment or Outpulse Control segment(s) to be included in this macro and begins with byte offset 12. The type of segment included is defined in the Segment Control Code (byte offset 11). The command segment format follows that of the command represented, with the exclusion of the Function ID, any trailing Spacer Bytes, and Controlling (incoming) Port Address. Spacer bytes in the MF Collection Control ($68) command segment must be included whenever it is used. Outpulse Control segment can be included only when I or U = 1 in the Rule Control byte (offset 10) and are defined in the "Outgoing Port Control ($69) Command" section. Only one command segment can be specified. Up to five Outpulse Control segments can be included in a single command.
If an inpulse rule or outpulse rule is included in this command, a $D0, $D1, $DA or $DD report may be returned.
No response from the system upon successful completion is provided unless Return All has been set in the Network Header. If the command is returned by the system with a Network Status byte not equal to $01, it indicates that the command was not processed. The following network status bytes may be returned—$03, $06, $0F, $10, $11, $12, $18, $1C, $1F, $21, $24, $26, $2B, $37, and $3C—in addition to any network status bytes specific to the command segments. Refer to "Message Structure Overview," or "Network Status Byte Definitions," for more information.
If Return All is used, the port address of any resource that was requested by resource group number is returned in place of the group number.
A Resource Limitation ($D6) report indicates the command could not be processed due to lack of available resources when the command or segment attempted to select from a resource group, or when an inpulse or outpulse rule is executed. Refer to the "Resource Limitation ($D6) Report" section for more information.
If command processing involves a port change of state, an Incoming Port Change of State ($DB) or Outgoing Port Change of State ($DA) report is returned by the system.
Forced disconnect causes the system to return Incoming Port Change of State ($DB), Outgoing Port Change of State ($DA), and Permanent Signal Condition ($D2) reports unless T = 1 (controls $DB reporting) and/or C = 1 (controls $DA reporting) in the Incoming Port Control Code.
Assume there is an incoming circuit at address $0018 that has gone off hook. The following command processes inpulse rule 5 on $0018.
04 0506 0708 09 10 11
6A 0000 0018 00 85 00
The Main Command Segment is as follows:
Function ID = 6A (Incoming Trunk Control)
Spacer Bytes = 00 00
Controlling Port Address = $0018
IP Control Code = 00000000
Rule Control = 10000101
Segment Control Code = 00000000
Assume there is an incoming circuit at address $0020 with a stable call in progress. The following command forces it to disconnect. Notice there are no segments attached to this command.
04 0506 0708 09 10 11
6A 0000 0020 80 00 00
The Main Command Segment is as follows:
Function ID = 6A (Incoming Port Control)
Spacer Bytes = 00 00
Controlling Port Address = $0020
IP Control Code = 10000000
Rule Control = 00000000
Segment Control Code = 00000000
No optional segments
Assume there is an incoming circuit at address $0019 with COS = AT that is off hook and idle, and an outgoing circuit at address $0025. The command below initiates a call on the incoming circuit, then attaches it to the outgoing circuit and processes outpulse rule 4. The format for attaching $0025 and executing outpulse rule 4 is taken from the Outgoing Port Control ($69) command.
04 0506 0708 09 10 1112131415
6A 0000 0019 C0 00 08C0258400
The Main Command Segment is as follows:
Function ID = 6A (Incoming Trunk Control)
Spacer Bytes = 00 00
Controlling Port Address = $0019
IP Control Code = 11000000
Rule Control = 00000000
Segment Control Code = 00001000
Outgoing Port Control Command Segment = C0 25 84 00
Function ID = omitted
Controlling Port Address = omitted
Outgoing Port Control Code = 11000000
Outgoing Port Address = $025
Outpulse Rule Control = 10000100
Digit Outpulse Control = 00000000
Assume there is an incoming circuit at address $0020 with a stable call in progress. The command below forces it to disconnect. The incoming circuit is left in setup mode while the outgoing circuit begins Permanent Signal Timing. The Attach Outgoing Port Control command attaches the incoming circuit to an outgoing circuit hunted from group 2.
04 0506 0708 09 10 111213141516
6A 0000 0020 88 00 08E002800000
The Main Command Segment is as follows:
Function ID = 6A (Incoming Port Control)
Spacer Bytes = 00 00
Controlling Port Address = $0020
IP Control Code = 10001000
Rule Control = 00000000
Segment Control Code = 00001000
Outgoing Port Control Command Segment = E0 02 80 00
Function ID = omitted
Controlling Port Address = omitted
Outgoing Port Control Code = 11100000
Outgoing Port Address = $002
Outpulse Rule Control = 10000000
Digit Outpulse Control = 00000000
End of Outgoing Port Control ($69) command segment.
Resource Control
Use the Change Incoming Port ($6B) command to switch all resources for an active call from one incoming port to another. The original port is forced to an idle state.
The minimum length for the $6B command is 9 bytes. If a command is too short, it is rejected and a syntax error with a status byte of 03 is returned to the host.
The old incoming port should have other resources linked to it and be participating in a call for this command to have any effect. The command adjusts all speech paths from the old incoming port to the new incoming port. This command can be used for transferring calls.
The controlling or new incoming port cannot be participating in a conference. If it is, the command is returned with a $1C network status byte.
If the old incoming port is involved in inpulse rule processing, the rule is aborted when this command is received.
The new incoming port must be in CP_SETUP state or, if COS = AT or A2, the port can also be in CP_IDLE if it is off hook. Hunting can be done only if all members of the group specified have COS = A and are off hook. An idle port in that group is selected.
Use this command to replace a virtual port with a physical incoming port. The call must be in either a wait for answer or stable condition to perform this action. The virtual port is idled when removed from the call.
Disconnect Control settings for both the incoming and outgoing ports are determined in the Outgoing Port Control ($69) command. These settings can be carried over from the $69 command or cleared using two bit settings in the $6B command's Port Selection Control segment (byte offset 7). The Disconnect Control settings cannot be set when the incoming port is a virtual call generation port. Refer to the Disconnect Control byte description in the $69 command for details on disconnect settings.
Figure 4-16 shows the byte formatting for this command.
Function ID (byte offset 4)—Byte immediately following the Network Header; uniquely identifies the command to the system.
Old Incoming Port Address (byte offset 5 and 6)—Hexadecimal representation of the circuit address from which to switch active call processing.
Port Selection Control (byte offset 7)—Specifies the disconnect control settings for the incoming and outgoing ports, and determines whether to switch the call to a specific incoming port or select one from a resource group. The first bit setting specifies whether to carry the disconnect bit settings from the old incoming port to the new incoming port, or clear the settings. The second bit determines whether to maintain the settings on the outgoing port as currently defined, or clear the settings. The third bit determines whether a specific incoming port is used or an available port hunted from a resource group. Construct the byte in binary, then convert to hexadecimal for use in the command. Note the NNN bits are part of the New Incoming Port Address. They are included in the conversion from hexadecimal to binary just to provide the proper spacing to interpret the Port Selection Control bits.
CKP00NNN
New Incoming Port Address (byte offsets 7 and 8)—Includes second digit of previous byte (Port Selection Control Code). If P = 0, this three-digit number is the hexadecimal representation of the incoming port. If P = 1, this three-digit number is the hexadecimal representation of the resource group to hunt for an available port; convert decimal to hexadecimal for the group number.
No response from the system upon successful completion is provided unless Return All has been set in the Network Header. A command returned by the system with a network status byte not equal to $01 indicates that the command was not processed. The following network status bytes may be returned: $06, $0E, $0F, $10, $11, $12, $18, $1C, $1F, $21, $24, $26, $35, and $3C. Refer to "Message Structure Overview," or "Network Status Byte Definitions," for more information.
If Return All is used, the port address of the new incoming port requested by resource group number is returned in place of the group number.
A Resource Limitation ($D6) report indicates that the command could not be processed because of a lack of available resources in a specified resource group. Refer to the "Resource Limitation ($D6) Report" section for more information.
The old incoming port is released and Permanent Signal processing begins for that port (unless it is a virtual port). An Incoming Port Change of State ($DB) report for the old port address is returned when that physical port goes on hook. A Permanent Signal Condition ($D2) report may also be returned. If the old incoming port is a virtual port or its COS = A, it is returned to an idle condition; no $DB report is generated.
Assume there is an active call on the incoming port at address $18. Resource group 6 consists of ports with a COS = AT, and all ports in that group are off hook. The following command switches that call to an idle port in resource group 6, and forces the port at address $18 to go idle.
04 0506 07 08
6B 0018 20 06
Function ID = 6B (Change Incoming Port)
Controlling Port Address = $0018
Port Selection Control = 00100000
New Incoming Port Address = resource group 6 ($006)
Assume there is an active call between a virtual port and an outgoing port. The following command transfers the call to an incoming circuit at $211 that is already in setup state.
04 0506 07 08
6B 8025 02 11
Function ID = 6B (Change Incoming Port)
Controlling Port Address = 8025 (virtual port)
Port Selection Control = 00000010
New Incoming Port Address = 211
Assume there is an active call on the incoming port at address $20. The following command switches that call to an incoming circuit at $221 that is already in setup state. The disconnect settings for the incoming ports are carried over and the current outgoing disconnect settings are maintained.
04 0506 07 08
6B 0020 C2 21
Function ID = 6B (Change Incoming Port)
Controlling Port Address = 0020
Port Selection Control = 11000010
New Incoming Port Address = 221
Resource Control
Use the Voice Port Control ($6C) (Standard) command to instruct the system to play up to 14 voice prompts to a line or trunk port. A prompt consists of one or more words; all prompts are downloaded to the Digital Voice Card (DVC) or Integrated Prompt/Record Card (IPRC) at system boot. Prompts are identified by number (refer to "System Digitized Voice Card Prompts," for a listing of prompt numbers and scripts). When more than one prompt is specified in the command, they are played in the order in which they appear. You can use this command to link a voice card port to, or remove it from, a call's resource chain, and you can also use it as a command segment in the Incoming Port Control ($6A) command.
This command can specify whether a Voice Port Status ($DE) report is generated when all voice prompts have been presented.
The minimum length for the $6C (Standard) command is 10 bytes. If a command is too short, it is rejected and a syntax error with a status byte of 03 is returned to the host.
All DVC or IPRC ports must be members of a single resource group for the system to allocate them. You do not need to specify the group number in the command; the system determines the resource group from the database configuration.
The controlling port cannot be participating in a conference. If it is, the command is returned with a $1C network status byte.
This command can be used as a segment in an Incoming Port Control ($6A) command. While voice prompts are being played, other commands can be sent for this port—such as an Outgoing Port Control ($69) command—without interfering with the prompts. This command is aborted if a Voice Path Control ($66) command is received for the controlling port, outpulse rule processing resets the voice path of the controlling port, or another $6C (Standard) command is received for this port.
Once a Voice Port Control command has been used to begin playing prompts to an incoming port, an inpulse rule can be started using a $6A command. If rule processing encounters a TONE ENAB, TONE FDIG, TONE END, or TONE CLR token while prompts are being played, the $6C (Standard) command is aborted. A TONE NOW token is not executed until the prompts are completed.
A DVC or IPRC port can be attached to any incoming or outgoing trunk/line circuit. Prompts can be presented to either incoming or outgoing ports.
Multiple prompt libraries can be used; however, you must number the libraries consecutively. Refer to the Cisco VCO/4K Card Technical Descriptions for further information.
Figure 4-17 shows the byte formatting for this command.
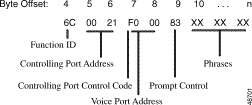
Function ID (byte offset 4)—Bytes immediately following the Network Header; uniquely identifies the command to the system.
Controlling Port Address (byte offsets 5 and 6)—Hexadecimal representation of the circuit address to which the prompts are to be played.
Controlling Port Control Code (byte offset 7)—Sets up the conditions used for this command. Construct the byte in binary according to the descriptions on the following page, then convert to hexadecimal for use in the command. The CCC bits are part of the Port Address and are included in the conversion from hexadecimal to binary just to provide the proper spacing to interpret the Controlling Port Control Code bits.
SAPR0CCC
Voice Port Address (byte offset 7 and 8)—Includes second digit of previous byte (Voice Port Control Code). If P = 0, this three-digit number is the hexadecimal representation of the voice port. If P = 1, these three digits should be 0; the system determines the correct group to hunt based on the system database.
Prompt Control (byte offset 9)—Determines the number of prompts to be played; you can specify up to 14 prompts in a single command. If no prompts are to be played, this byte must be $00. Construct byte in binary according to the descriptions below, then convert to hexadecimal for use in the command.
XR00FFFF
Phrases (byte offset 10 to n)—The phrase number(s) corresponding to the phrase(s) to be played. The number of phrase bytes required is equal to the number of phrases specified in the FFFF bits of the Prompt Control byte. Phrases are played in the order in which they appear in the command. Refer to "System Digitized Voice Card Prompts," for a listing of phrases by number. Convert the phrase number from decimal to hexadecimal for the correct byte value.
No response from the system upon successful completion is provided unless you specified Voice Port Status ($DE) report in the command or set Return All in the Network Header. If you specify a command to select from a resource group, the command returned contains the port address of the voice port selected by the system. A command returned by the system with a network status byte not equal to $01 indicates that the command was not processed. The following network status bytes may be returned: $03, $07, $09, $0D, $0E, $0F, $11, $12, $16, $17, $18, $1C, $1F, $22, $24, $26, $27, and $3C. Refer to "Message Structure Overview," or "Network Status Byte Definitions," for more information.
A command returned with a $1F network status byte indicates that no voice ports were available to satisfy this command. If this returned command is followed by a Resource Limitation ($D6) report, all members of the voice card resource group were busy (allocated or out of service). If no $D6 is sent, a voice card resource group does not exist (no members). Refer to the "Resource Limitation ($D6) Report" section for more information on the $D6 report.
Assume there is an active call on the incoming port at address $18. The following command starts a series of prompts to be played to that port. Upon completion of prompts, a $DE report is generated.
04 0506 07 0809 10 1112131415
6C 0018 D0 50C6 27 5B4B4C4D4F
Function ID = 6C (Voice Port Control)
Controlling Port Address = 0018
Controlling Port Control Code = 11010000
Voice Port Address 050
Prompt Control = 11000110
The following command aborts the prompts started by the command in Example 4-30 and releases the voice port (removes it from the call's resource chain).
04 0506 07 0809
6C 0018 80 5000
Function ID = 6C (Voice Port Control)
Controlling Port Address = 0018
Controlling Port Control Code = 10010000
Voice Port Address 050
Prompt Control = 00000000
Resource Control
The Voice Port Control ($6C) (Enhanced) command is specific to the IPRC. It is used to instruct the system to play up to 20 voice prompts, consisting of one or more words each, to a line or trunk port in the form of a single announcement. The $6C (Enhanced) command also allows the system application to play prompts from any one of 16 prompt libraries and to loop the playback of individual prompts or a list of prompts. The $6C (Enhanced) command is also used to record a prompt to any of the 16 prompt libraries.
This command gives you the ability to access any of the temporary prompts maintained by an individual IPRC port for play or record operations. Temporary prompts are maintained by the IPRC as long as the associated playback port is involved with a call. When the playback port is released from the call, the temporary prompt is erased. The temporary prompts are accessed for recording and subsequent playback through inpulse rule processing and $6C (Enhanced) command processing.
All prompts are downloaded to the IPRC at IPRC card initialization. Prompts are identified by number Refer to "Integrated Prompt and Record Card Prompt Library," for a listing of the standard prompt library and their numbers. When more than one prompt is specified in the command, they are played in the order in which they appear. You can use this command to link a voice card port to, or remove it from, a call's resource chain, and you can also use it as a command segment in the Incoming Port Control ($6A) command.
This command can specify whether a Voice Port Status ($DE) report is generated when all voice prompts have been presented.
The minimum length for the enhanced $6C (Enhanced) command is 10 bytes. If a command is too short, it is rejected and a syntax error with a status byte of 03 is returned to the host.
All IPRC ports must be members of a single resource group for the system to allocate them. You do not need to specify the group number in the command; the system determines the resource group from the database configuration.
The controlling port cannot be participating in a conference. If it is, the command is returned with a $1C network status.
This command can be used as a segment in a $6A command. While voice prompts are being played, other commands can be sent for this port (such as an Outgoing Port Control ($69) command) without interfering with the prompts. This command is aborted if a Voice Path Control ($66) command is received for the controlling port, outpulse rule processing resets the voice path of the controlling port, or another Voice Port Control command is received for this port. An IPRC port can be attached to any incoming or outgoing trunk/line circuit. Prompts can be presented to either incoming or outgoing ports.
Multiple prompt libraries can be used; however, you must number the libraries consecutively. Refer to the Cisco VCO/4K Card Technical Descriptions for further information.
Figure 4-18 shows the byte formatting for this command.
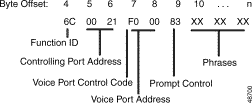
Function ID (byte offset 4)—Bytes immediately following the Network Header; uniquely identifies the command to the system.
Controlling Port Address (byte offsets 5 and 6)—Hexadecimal representation of the circuit address to which the prompts are to be played.
Voice Port Control Code (byte offset 7)—Sets up the conditions used for this command. The CCC bits are part of the Port Address and are included in the conversion from hexadecimal to binary just to provide the proper spacing to interpret the Controlling Port Control Code bits. Construct the byte in binary according to the following descriptions, then convert to hexadecimal for use in the command.
SAPR0CCC
Voice Port Address (byte offsets 7 and 8)—Includes second digit of previous byte (Voice Port Control Code). If P = 0, this three-digit number is the hexadecimal representation of the voice port. If P = 1, these three digits should be 0; the system determines the correct group to hunt based on the system database.
Prompt Control (byte offset 9)—Controls prompt playback and record. Construct the byte in binary according to the descriptions below, then convert to hexadecimal for use in the command.
XREP0000
Play Segment (byte offset 10...)—Determines the number of prompts to play, the library from which to access the prompt, and the prompt phrase IDs. Include when P equals zero (P = 0) in Prompt Control (byte offset 9).
Figure 4-19 shows the byte formatting for the Play Segment.
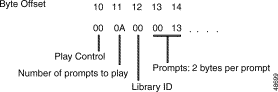
Record Segment (byte offset 10...)—Used to define the library to record a prompt to, the maximum record time value, and the prompt ID. Include when P equals zero (P = 0) in Prompt Control (byte offset 9).
Figure 4-20 shows the byte formatting for the Record Segment.
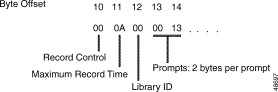
No response from the system upon successful completion is provided unless you specified Voice Port Status ($DE) report in the command or set Return All in the Network Header. If command specified to select from resource group, the command returned contains the Port Address of the voice port selected by the system. A command returned by the system with a network status byte not equal to $01 indicates that the command was not processed. The following network status bytes may be returned: $03, $09, $0E, $0F, $11, $12, $16, $17, $18, $1F, $22, $24, $26, $27, $3C, $43, $44, $45, $46. $47, and $48. Refer to "Message Structure Overview," or "Network Status Byte Definitions," for more information.
A command returned with a $1F network status byte indicates that no voice ports were available to satisfy this command or that no IPRC ports were available from the specified prompt library. If a returned command is followed by a Resource Limitation ($D6) report, all members of the voice card resource group were busy (allocated or out of service). If no $D6 is sent, a voice card resource group does not exist (no members). Refer to the "Resource Limitation ($D6) Report" section for more information on the $D6 report.
Take port 29 off hook.
Tx Host: ALL HOST-F0 40 80 00 DB 00 80 00 29 00 00 00
Record for 10 seconds and store the recording in temporary Prompt ID 80 01.
Rx Host: HOST1-DF DF 00 00 6C 00 29 E0 00 F0 001 0A 00 80 01
TX Host: HOST1-DF DF 80 01 6C 00 29 E2 AF F0 00 0A 00 80 01
Record the complete message.
TX: Host: ALL HOST-F0 40 80 00 DE 00 29 00 00 02 AF 00
Play the temporary prompt stored in Prompt ID 80 01 to port 29.
Rx Host: HOST1-DF DF 00 00 6C 00 29 20 00 E0 00 01 00 80 01
Tx Host: HOST1-DF DF 80 01 6C 00 29 20 00 E0 00 01 00 80 01
Tx Host: ALL HOSTS-F0 40 80 00 DE 00 29 00 00 02 AF 10
Tx Host: ALL HOSTS-F0 40 80 00 DB 00 40 00 29 00 00 00
Take port 29 off hook.
Tx Host: ALL HOSTS-F0 40 80 00 DB 00 80 00 29 00 00 00
Record for 5 seconds and store the recording in temporary Prompt ID 80 01.
Rx Host: HOST1-DF DF 00 00 6C 00 29 E0 00 F0 00 05 00 80 01
Tx Host: HOST1-DF DF 80 01 6C 00 29 E0 00 F0 00 05 00 80 01
Record the complete message.
Tx Host: AL HOST-F0 40 80 00 DE 00 29 00 00 02 B1 00
Seize out port 2A.
Rx Host: HOST1-DF DF 00 00 69 00 29 C0 2A 80 00
Tx Host: HOST1-DF DF 80 01 69 00 29 C0 2A 80 00
The 00 is replaced by whatever port sent the recording.
Answer port 2A.
Tx Host: ALL HOST-F0 40 80 00 DA 00 80 00 2A 00 29 32 06 80
Play the temporary prompt stored in Prompt ID 80 01 to Port 2A.
Rx Host: HOST1-DF DF 00 00 6C 00 2A 20 00 E0 00 01 00 80 01
Tx Host: HOST1-DF DF 80 01 6C 00 2A 20 00 E0 00 01 00 80 01
Tx Host: ALL HOSTS-F0 40 80 00 DE 00 2A 00 00 02 B2 10
Resource Control
The Conference Control ($6D) command controls the conferencing features. Up to eight conference ports can be used for a conference. An incoming or outgoing line/trunk port can be marked to listen only (one-way path) or listen and talk (two-way path). A single conference can accommodate up to eight two-way line/trunk ports, or up to seven two-way line/trunk ports and as many one-way line/trunk ports as are available in the system. The system can support up to 128 simultaneous conferences. The $6D command lets the host perform one of the following functions:
In addition, the following features support talk-only conference support for Communication Assistance for Law Enforcement Act (CALEA) applications:
The minimum length for the $6D command is 8 bytes. If a command is too short, it is rejected and a syntax error with a status byte of 03 is returned to the host.
All conference ports must be members of a single resource group for the system to allocate them. The system determines the resource group from the database configuration.
Reserved conference ports remain reserved until the conference is torn down. If a line/trunk port is deleted from a reserved conference, the conference port to which it was linked remains reserved.
The system can accommodate up to eight Digital Conference Cards and a total of 128 simultaneous conferences and/or monitors. When a conference is reserved or started, the system assigns it a conference number. If Return All has been set in the Network Header, the conference number is returned to the host in the second byte of the command (byte offset 5). The system requires the conference number to add ports to, delete ports from, adjust input/output gain levels for, or tear down a conference.
To add a port to a conference, one of the following conditions must be true:
If an idle port with COS = 2 is used, it assumes a COS of T. While in a conference, the port is assigned an internal COS of C. When a port is removed from a conference (delete or tear down) and the command specifies to leave that port active, it remains in the CP_SETUP MState until further host action. Refer to "Call Processing States," for information on major and supplementary call processing states.
When a line/trunk port involved in a conference goes on hook, it is automatically deleted from the conference.
Other resource control commands cannot be used on ports in a conference. To collect digits or play prompts, the port must first be removed from the conference, instructed to perform the action, and then added back to the conference. The $66 command can be used to make the port in a conference listen to Quiet; however, anything transmitted by that port can still be received by other conference parties.
If one port in a stable call is added to a conference (also if the outgoing port is in CP_WTFSUP or the incoming is in CP_WANS), the other port in the call is placed into CP_SETUP unless it is a virtual port or its COS = A. If a physical port is placed into CP_SETUP, the host must take some action on that port. Virtual ports and ports with COS = A are returned to CP_IDLE and are available for use.
Figure 4-21 shows the byte formatting for this command.
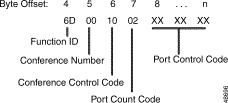
Function ID (byte offset 4)—Byte immediately following the Network Header; uniquely identifies the command to the system.
Conference Number (byte offset 5)—Specifies the number of the conference upon which the action should be taken. To start or reserve a conference, specify a conference identifier from 0 to 128; 0 is valid only if a conference is available for allocation. When the conference identifier = 0, the system returns the ID of the allocated conference. When adding to, deleting from, adjusting input/output levels for, or tearing down a conference, the conference number is required. Convert from decimal to hexadecimal for the conference number.
Conference Control Code (byte offset 6)—Determines the action to be taken for this command. Construct the byte in binary according to the descriptions below, then convert to hexadecimal for use in the command.
 |
Note Set only one of the following bits (R, S, T, A, D, or G) to 1; all other bits must be set to 0 (zero). |
RSTADG00
Port Count Code (byte offset 7)—Specifies the number of ports affected by this command. If R = 1 in Conference Control Code (byte offset 6), the Port Count Code specifies how many conference ports to reserve. In this case, Port Control Codes are not specified. For all other settings, the Port Count Code specifies how many Port Control Code bytes are contained in this command. Convert from decimal to hexadecimal for use in the command.
Port Control Code (byte offset 8 to n)—Three-byte set required when a conferencing action is required for a specific line/trunk port. One Port Control Code byte set is required for each line/trunk port affected when S, T, A, D, or G = 1 in the Conference Control Code (byte offset 6); the number of Port Control Code byte sets must be equal to PPPP specified in the Port Count Code (byte offset 7). When T = 1 in the Conference Control Code (byte offset 6), any line/trunk port that should be left active must be represented by a Port Control Code byte set.
 |
Note Do not specify Port Control Codes when reserving a conference (R=1). The system will automatically reserve the ports based on their availability. Setting R=1 and specifying Port Control Codes causes a syntax error. |
Construct the bytes in binary according to the following descriptions, then convert to hexadecimal for use in the command.
IIIIA0LL WSV00PPP PPPPPPPP
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| ||
 |
Note Do not set both the talk-only bit (A) and the listen-only bit (W) equal to 1 for the same port and time. Failure to follow this guideline results in a port added to a conference which can neither receive from nor transmit to other ports. |
No response from the system upon successful completion is provided unless Return All has been set in the Network Header. Return All should be used when R or S = 1 in the Conference Control Code to track the conference number assigned by the system. Any command returned by the system with a network status byte not equal to $01 indicates that the command was not processed. The following network status bytes may be returned: $03, $0B, $0C, $0F, $12, $1C, $1D, $1E, $1F, $21, $23, $24, $29, $3C, $54, and $55. Refer to "Message Structure Overview," or "Network Status Byte Definitions," for more information.
A command returned with a $1F network status byte indicates that no conference ports were available to satisfy this command. If this returned command is followed by a Resource Limitation ($D6) report, all members of the DCC resource group were busy (allocated or out of service). If no $D6 report is sent, a DCC resource group does not exist (no members). Refer to the "Resource Limitation ($D6) Report" section for more information on the $D6 report.
When a conference is torn down or a line/trunk port is deleted from a conference and the port(s) is idled, an Incoming Port Change of State ($DB) or Outgoing Port Change of State ($DA) report is received for each port sent to idle (except for those with COS = A). The type of report is based on whether the port was considered incoming or outgoing prior to being added to the conference structure. Permanent Signal Condition ($D2) reports may also be returned by the system under these conditions.
Assume that an incoming port at address $18 and an outgoing port at address $30 are connected in a stable call. A third port at address $45 is in CP_SETUP state. The following command creates a conference using these three ports.
04 05 06 07 080910111213141516
6D 00 40 03 400018B00030E00045
Function ID = 6D (Conference Control)
Conference Number = 00 (begin a new conference)
Conference Control Code = 01000000
Port Count Code = 03 (3 ports)
The Port Control Code sets are as follows:
First set = 40 00 18
Port Address = 018
Second set = B0 00 30
Port Address = 030
Third set = E0 00 45
Port Address = 045
Assume the conference above was assigned a conference number of 4 by the system. An incoming port at address $27 is in CP_SETUP state. The following command adds the port at address $27 to conference 4 as a listener (one-way).
04 05 06 07 080910
6D 04 10 01 008027
Function ID = 6D (Conference Control)
Conference Number = 04 (conference number 4)
Conference Control Code = 00010000
Port Count Code = 01 (1 ports)
Port Control Code sets
First set = 00 80 27
Port Address = 027
The command below removes the port at address $45 from conference 4. The port is to be idled and sent through Permanent Signal processing.
04 05 06 07 080910
6D 04 08 01 004045
Function ID = 6D (Conference Control)
Conference Number = 04 (conference number 4)
Conference Control Code = 00001000
Port Count Code = 01 (1 ports)
Port Control Code sets
First set = 00 40 45
Port Address = 045
The following command tears down conference 4, leaving the ports at addresses $18 and $30 in CP_SETUP state so that an Outgoing Port Control ($69) command can be used to reconnect them into a stable call. Port $27 is released and put through Permanent Signal processing. Note that it is not necessary to include a Port Control Code byte set for a port that is to be idled when a conference is torn down.
04 05 06 07 080910111213
6D 04 20 02 000018000030
Function ID = 6D (Conference Control)
Conference Number = 04 (conference number 4)
Conference Control Code = 00100000
Port Count Code = 02 (2 ports)
Port Control Code sets
First set = 00 00 18
Port Address = $018
Second set = 00 00 30
Port Address = $030
Resource Control
The Speech Collection Control ($6E) command instructs the system to collect the spoken digits 0 to 9 inclusive and the words oh (used for zero), yes, and no sent over any line or trunk circuit. Digits are sent to the host in the form of a Spoken Digit ($D4) report and can be stored in any of the controlling port's digit fields (1 to 4 and ANI). This command is also used to attach or detach SRC ports to or from a line or trunk. First digit, interdigit, and field timing can be specified in the command. Enabling of the SRC port can be done immediately or delayed until one of the following conditions is met:
Collection in progress can be terminated by this command; the digits collected prior to the termination order are returned to the host in a successful $D4 report. This command can be used as a command segment in the Incoming Port Control ($6A) command.
The minimum length for the $6E command is 13 bytes. If a command is too short, it is rejected and a syntax error with a status byte of 03 is returned to the host.
The $6E command has the format:
Main Command segment [optional segments...]
The Main Command segment is 8 bytes long (offsets 4 through 12) and must be included in its entirety every time the $6E command is used. If default collection timer values and receiver enabling is used, no optional segments are required.
Two optional segments are available for use with the $6E command:
Each segment can be included only once in a single command. When more than one segment is used, they must appear in the following order:
[Collection Timers] [Enabling Options]
If a segment is not to be included, it is omitted.
A command can specify to present up to 14 voice prompts prior to enabling the SRC port. Prompts are specified in the Enabling Options segment.
If any of the timers (default digit timers, Collection Timers segment timers, or Enabling Options timers) set in the command expire, the command is aborted. A $D4 report is issued indicating which timer expired. The report indicates the reason for the command abort.
Timers specified in seconds may vary by as much ± one half second. This variation affects the $6E command and is most pronounced in values set to 1 or 2 seconds.
Up to 15 digits can be collected using a single $6E command. Collected digits are reported to the host in a $D4 report and can be stored in any of the controlling port's five digit fields (ANI and Fields 1 through 4). Collected digits may also be appended to the string already contained in one of the digit fields. Field length restrictions of 20 digits for Fields 1 through 4 and 12 digits for ANI still apply. Any appended digits in excess of the field limit are reported to the host but are not saved internally by the system.
Yes/no responses cannot be stored in a digit field.
The controlling port cannot be participating in a conference. If it is, the command is returned with a $1C network status byte.
All SRC receiver ports must be members of a single resource group for the system to allocate them. You do not need to specify the group number in the command; the system determines the resource group from the database configuration.
An SRC port can be attached to any incoming or outgoing circuit for spoken digit collection.
If either spoken or DTMF digits are to be accepted, this command must be either preceded or followed by a DTMF Collection Control ($67) command.
Figure 4-22 shows the byte formatting for this command.
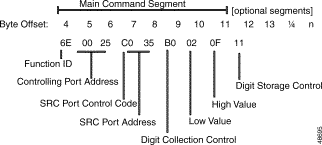
Main Command Segment
The Main Command segment is composed of byte offsets 4 to 12 and must be included in its entirety. This segment can be used without optional segments for attaching or detaching an SRC port, enabling an already attached SRC port, or collecting a digit string or a yes or no response. Collected digits can be stored in or appended to the controlling port's digit fields as specified in this segment. Components of the Main Command segment are defined as follows.
Function ID (byte offset 4)—Byte immediately following the Network Header; uniquely identifies the command to the system.
Controlling Port Address (byte offset 5 and 6)—Hexadecimal representation of the circuit address to which the SRC port is attached.
SRC Port Control Code (byte offset 7)—Sets up the conditions used for this command. Construct the byte in binary according to the descriptions below, then convert to hexadecimal for use in the command. The CCC bits are part of the SRC Port Address and are included in the conversion from hexadecimal to binary just to provide the proper spacing to interpret the SRC Port Control Code bits.
SAPR0CCC
SRC Port Address (byte offsets 7 and 8)—Includes second digit of previous byte (SRC Port Control Code). If P = 0, this three-digit number is the hexadecimal representation of the receiver port. If P = 1, set to $000.
Digit Collection Control (byte offset 9)—Determines if SRC is to be enabled, a Collection Timers segment is attached, an Enabling Option Segment is attached, and the vocabulary (digits or yes/no) to be used for this collection. Construct byte in binary according to the descriptions that follow, then convert to hexadecimal for use in the command.
M0TEVVVV
Low Value of Collection Range (byte offset 10)—Determines the minimum number of digits or words to be collected. Value must be less than or equal to the High Value of Collection Range specified in byte offset 11. Convert decimal to hexadecimal for this value.
High Value of Collection Range (byte offset 11)—Determines the maximum number of digits or words to be collected. Value must be less than or equal to 15 and greater than or equal to the Low Value of Collection Range specified in byte offset 11. Convert decimal to hexadecimal for this value.
Digit Storage Control (byte offset 12)—Determines if Collected digits are stored in or appended to one of the controlling port's digit collection fields (1 to 4, ANI). Construct byte in binary according to the descriptions below, then convert to hexadecimal for use in the command. If digits are not to be stored (yes/no values cannot be stored), this byte must be set to $00.
000SAFFF
Collection Timers Segment
The Collection Timers Segment is an optional $6E segment that is three bytes in length and specified only when the Digit Collection Control (byte offset 9) T bit is set to 1. If this condition is true, this segment must appear in byte offsets 13 through 15.
Figure 4-23 shows the byte formatting for the Collection Timers segment.

First Digit Timeout—Specifies the number of seconds, in hex, allowed for the user to speak the first digit of the string. This timer starts when the SRC port is enabled. Allowed values are 1 to 25 seconds decimal ($01 to $19), inclusive. Convert from decimal to hexadecimal for the correct value. To use default timer value (4 seconds), set byte to $00.
Interdigit Timeout—Specifies the number of seconds, in hex, allowed for the user to pause between speaking digits. This timer starts when the first digit is received. Allowed values are 1 to 25 seconds decimal ($01 to $19), inclusive. Convert from decimal to hexadecimal for the correct value. To use default timer value (2 seconds), set byte to $00.
Field Timeout—Specifies the number of seconds, in hex, allowed for the user to enter the number of digits specified in the High Value Collection Range (byte offset 11) minus 1. This timer starts when the recognizer is enabled. Allowed values are 1 to 60 seconds decimal ($01 to $3C), inclusive. Convert from decimal to hexadecimal for the correct value. To use default timer value (20 seconds), set byte to $00.
Enabling Options Segment
The Enabling Options segment is an optional $6E segment that is from 2 to 15 bytes in length. This segment is used to delay the speech recognition attempt until the specified enabling event has completed. When the Digit Collection Control (byte offset 9) T bit is set to 1 and the E bit is set to 1, this segment must start at byte offset 16. If T = 0 and E = 1, this segment starts at byte offset 13.
Figure 4-24 shows byte formatting of the Enabling Options segment.
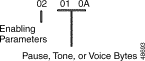
Enabling Parameters Byte—Determines which of the four enabling options are used for this command. Only one enabling option can be specified in a single $6E command. Depending upon the option specified, a variable number of additional bytes follow this byte. Construct the byte in binary according to the descriptions below, then convert to hexadecimal for use in the command.
00A0PTSV
Pause Byte—Single byte used only when P = 1 in Enabling Parameters byte. Determines the number of seconds to wait before enabling the SRC port. Duration is specified in 0.1-second increments. This timer starts when the command is processed. Allowed values are 0.1 second to 25.5 seconds decimal ($01 to $FF) in 0.1-second increments. Convert from decimal to hexadecimal for the correct value.
Tone Bytes—Two bytes used only when T = 1 in Enabling Parameters byte. Determines the tone to present and the number of seconds to present the tone before enabling the SRC port. Individual bytes are defined as follows.
Voice Bytes—Up to 15 bytes used only when V = 1 in Enabling Parameters byte. Determines the total number of prompts and specific prompts to present before enabling the SRC port. Individual bytes are defined as follows:
Play/Record Segment Bytes—Determines the setting of the Play/Record segment byte—if A = 1, then the option data is the $6C (Enhanced) command's Play/Record segment, starting with byte offset 7 of $6C (Enhanced) command.
Spoken Digit ($D4) report.
A command returned by the system with a network status byte not equal to $01 indicates that the command was not processed. The following network status bytes may be returned: $03, $09, $0A, $0E, $0F, $11, $12, $13, $16, $17, $18, $1C, $1F, $22, $24, $26, $27, $2C, $2D, $2E, $2F, $30, $31, $32, $33, $34, $3C, $43, $44, $45, $46, $47, and $48. Refer to "Message Structure Overview," or "Network Status Byte Definitions," for more information.
If Return All is used, the port address of the SRC port requested by resource group number is returned in the port address bytes.
A command returned with a $1F network status byte indicates that no SRC ports were available to satisfy this command. If this returned command is followed by a Resource Limitation ($D6) report, all members of the SRC resource group were busy (allocated or out of service). If no $D6 is sent, an SRC resource group does not exist (no members). Refer to the "Resource Limitation ($D6) Report" section for more information on the $D6 report.
The following host command performs a speech recognition only. The command sets up the recognizer port at $28 to collect 7 digits.
04 0506 07 0809 10 11 12
6E 0048 D0 2880 07 07 00
Function ID = 6E (Speech Collection Control)
Controlling Port Address = 48
SRC Port Control = 11010000
SRC Port Address/Group = 28
Digit Collection Control = 10000000
Low Value of Collection Range = 07
High Value of Collection Range = 07
Digit Storage Control = $00 (do not store collected digits in controlling port's call record)
The following command sets up an SRC port to collect a range of 4 to 11 digits following a voice announcement. The command selects an SRC from a resource group, uses the default first digit, interdigit and field collection timers, and stores the collected digit information in digit field 1 of the controlling port's call record.
04 0506 07 0809 10 11 12 13 14 15 16
6E 0048 E0 0090 04 0B 11 01 02 71 4C
Function ID = 6E (Speech Collection Control)
Controlling Port Address = 48 SRC Port Control = 11100000
SRC Port Address/Group = 00
Digit Collection Control = 10010000
Low Value of Collection Range = 04
High Value of Collection Range = 0B
Digit Storage Control = 00010001
Enabling Parameters = 00000001
Voice Bytes = 02 71 4C
The following command sets up an SRC port to recognize the response Yes or No. The command selects a SRC from a resource group, uses a first digit timer of 5 seconds, and plays a beep prior to enabling the receiver.
04 0506 07 0809 10 11 12 13 14 15 16 17 18
6E 0048 F0 00B1 01 01 00 05 00 00 04 00 00
Function ID = 6E (Speech Collection Control)
Controlling Port Address = 48
SRC Port Control = 11110000
SRC Port Address/Group = 00
Digit Collection Control = 10110001
Low Value of Collection Range = 01
High Value of Collection Range = 01
Digit Storage Control = 00 (not used for Yes and No)
First Digit Timer = 05 (5 seconds)
Interdigit Timer = 00 (use default value of 2 seconds)
Field Collection Timer = 00 (use default value of 20 seconds)
Enabling Parameters = 00000100
Tone Bytes = 00 00
Resource Control
The Port Hook State Control ($70) command provides the host with following functionality:
Normal system host commands must be used to connect the two ports into a call prior to processing an answer condition for the outgoing port, and for setting up a voice path between two ports.
The $70 command is recommended for use only with call scenarios in which all signaling or call control occurs outside the system.
 |
Note The $70 command does not support PRI (or PRI/N) ports. All signaling for these ports must be received over an ISDN D-channel. |
Hook state processing within the command for a specified line/trunk is controlled by the Hook State byte and COS byte. Table 4-5 summarizes the $70 command processing for each hook state and COS.
| Command Hook State/COS | System Port State/COS | Action |
|---|---|---|
Offhook/Default | Idle/T or 2 | The port goes to CP_SETUP, for COS of 2 is set to 2T, start and end records are allocated. |
Idle/O | The port goes to CP_MBUSY (far end busy out). | |
Nonidle/T or 2T | Ignored. | |
Nonidle/O or 2U | The port goes to CP_STABLE (answer condition). | |
Offhook/Incoming | Idle/T or 2 | The port goes to CP_SETUP. For COS 2, the COS is set to 2T. Start and end records are allocated. |
Idle/O | The command is rejected with $18 error. | |
Nonidle/T or 2T | The command is ignored. | |
Nonidle/O or 2U | The command is rejected with $18 error. | |
Offhook/Outgoing | Idle/2 or O | The port goes to CP_SETUP. For COS of 2, the COS is set to 2U. |
Idle/T | The command is rejected with $18 error. | |
Nonidle/T or 2T | The command is rejected with $18 error. | |
Nonidle/O or 2U | The command is ignored. | |
Onhook/Any | Idle/Any | The command is ignored. |
Nonidle/T or 2T | The call is torn down with immediate guard complete. | |
Nonidle/O or 2U | The call is torn down with immediate guard complete. |
The execution of an inpulse or outpulse rule within the $70 command is controlled by the Rule Control byte and the Rule Identifier byte. The Rule Control byte specifies whether the rule is an inpulse rule or an outpulse rule. The Rule Identifier specifies which rule to execute. Execution is valid for both incoming and outgoing ports. Table 4-6 summarizes the processing for inpulse and outpulse rules within the $70 command. Rules can only be executed when a port is offhook.
| Rule Control Byte | Rule Identifier | $70 Command Processing | ||
|---|---|---|---|---|
Inpulse | $00 (zero) | Default inpulse rule for the specified port is invoked (if one is assigned).
| ||
Nonzero | Specified inpulse rule is invoked. | |||
Outpulse | $00 (zero) | No rule is invoked. | ||
Nonzero | Specified outpulse rule is invoked. |
The usage guidelines for the $70 command are as follows:
Figure 4-25 shows the byte formatting for this command.
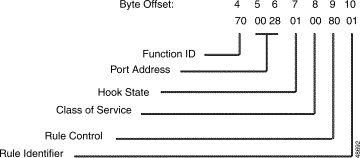
Function ID (byte offset 4)—Byte immediately following the Network Header. The Function ID uniquely identifies the command to the system.
Port Address (byte offset 5 and 6)—Hexadecimal representation of the circuit address. This number must fall within the range of 0 to 7FFF. This address must also correspond to a card and line or trunk port configured in the system. The exception is PRI ports; PRI is not supported by the $70 command.
Hook State (byte offset 7)—Used to define the Hook State for the port and whether to suppress the Outgoing Port Change of State ($DA) and Incoming Change of State ($DB) reports. The format for the byte is as follows:
S000000H
Class of Service (byte offset 8)—Used to define the COS (incoming or outgoing) when the port is defined in the database as having a COS of two-way. Valid values for this byte are 00 (default), 01 (incoming), or 02 (outgoing.) A COS of none (0) is only valid with a hook state of offhook and a COS defined in the database as two-way.
Rule Control (byte offset 9)—Specifies whether to invoke an inpulse rule or an outpulse rule. The format of the byte is as follows:
OI000000
Rule Identifier (byte offset 10)—Specifies which inpulse or outpulse rule to invoke. If this byte is nonzero, the rule corresponding to the Rule Identifier is invoked. When an inpulse rule is being invoked (the I bit in byte offset 9 is set to 1) and the Rule Identifier is zero, a default inpulse rule is invoked if one is defined for the port in the database. When an outpulse rule is being invoked (the O bit in byte offset 9 is set to 1) and the Rule Identifier is zero, no outpulse rule is invoked. If the Rule Identifier is not valid (a number other than 1 to 30), an error is returned.
The command format and content is verified within call processing when the $70 command is received. Any format or content error results in the command being returned to the host without processing. When an error occurs, the appropriate error code is inserted into the network status byte. Table 4-7 describes the valid $70 command error codes.
| Error Code | Meaning |
|---|---|
$0F | The port address you specified in offset bytes 5 and 6 is under the control of another host. |
$12 | The port address specified in offset bytes 5 and 6 is for a port other than a T1 port. The $70 command does not support any other circuit types. |
$18 | The specified port address has an incorrect COS for the requested operation. This error occurred due to one of the following conditions:
|
$23 | The port address you specified in offset bytes 5 and 6 is not within the range of 0 to 7FFF or the port is not defined in the system configuration. |
$24 | The port address you specified is for a port on a card that is inactive. Specified ports must be on active cards for the $70 command. |
$26 | The specified port is in an uncontrollable state (CP_MBUSY). |
$29 | A system internal processing error has occurred. Start and End call records could not be allocated for this call. |
$2B | The specified inpulse or outpulse rule byte value is not within the valid range of 1 to 30. Refer to the Cisco VCO/4K System Administrator's Guide for more information. |
$3E | The value of the Hook State Control byte (offset byte 7) is invalid. Valid values for offset byte 7 are 00 (onhook), 01 (offhook), or 80 and 81 (suppress reports). |
$3F | The value of the Class of Service byte (offset byte 8) is invalid. Valid values for offset byte 8 are 00 (default COS), 01 (incoming), or 02 (outgoing). |
$40 | The value of the Rule Control byte (offset byte 9) is invalid. Valid values for offset byte 9 are 40 (inpulse rule) or 80 (outpulse rule). |
$41 | The length of the command is invalid. The $70 command must be exactly 7 bytes long (not counting the Network Header). |
$42 | The port specified in offset bytes 5 and 6 is not in a valid state to execute an inpulse rule or an outpulse rule. |
System Diagnostics
Use the Port Supervision Control ($72) command for manual host control over outward handshake and supervision signals on both incoming and outgoing circuits. Available actions are seize and wink (hookflash if off hook); their effects on different system hardware types are summarized in Table 4-8. This command can be used as a command segment in an Incoming Port Control ($6A) command.
| Hardware Type | Seize Effect | Wink Effect |
|---|---|---|
SLIC-2 | Ring line | No effect |
DID-2 | Tip/ring reversal | Tip/ring reversal for 200 ms or unreversal for 500 ms1 |
UTC-2 (LS) | Close loop | On hook for 500 ms2 |
UTC-2 outgoing (GS) | Ground ring | On hook for 500 ms2 |
UTC-2 incoming (GS) | Ground tip/close loop | On hook for 500 ms2 |
T1 | Raise A/B signal | Raise/lower A/B signal for 250 ms2 |
E+M | Raise E/M lead | Raise E/M lead for 250 ms |
| 1DID wink when on hook provides a 200 ms wink signal; DID wink when off hook provides a T1 500 ms hook flash; signal. 2T1 wink when on hook provides a wink signal; T1 and UTC wink when off hook provides a T1 hook flash; signal. |
The minimum length for the $72 command is 9 bytes. If a command is too short, it is rejected and a syntax error with a status byte of 03 is returned to the host.
Wink applies only to idle ports, and has no effect on off hook ports except DID, UTC, and T1 ports. A wink specified for an off hook DID, UTC, or T1 port provides a hookflash signal. Command does not affect voice path, states, or resource linkages.
Figure 4-26 shows the byte formatting for this command.
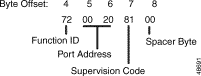
Function ID (byte offset 4)—Byte immediately following the Network Header; uniquely identifies the command to the system.
Controlling Port Address (byte offsets 5 and 6)—Hexadecimal representation of the address of the port acted upon.
Supervision Code (byte offset 7)—Determines whether an action is executed (seize, wink) or cancelled (seize only), and the type of action performed. Construct the byte in binary according to the descriptions below, then convert to hexadecimal for use in the command.
A0000MMM
Spacer Byte (byte offset 8)—Byte reserved for future enhancements; set to $00.
No response from the system upon successful completion unless Return All has been set in the Network Header. Command returned by the system with a Network Status byte not equal to $01 indicates command was not processed. The following network status bytes may be returned: $03, $23, $24, and $3C. Refer to "Message Structure Overview," or "Network Status Byte Definitions," for more information.
Assume there is an T1 circuit at address $23. The following command causes the T1 port to seize outwards by raising its AB signals.
04 0506 07 08
72 0023 81 00
Function ID = 72 (Port Supervision Control)
Controlling Port Address = 0023
Supervision Code = 10000001
Spacer Byte = 00
Assume the T1 port in Example 4-42 is still seized. The following command causes a hookflash on the port by lowering the A/B signal for 250 ms.
04 0506 07 08
72 0023 82 00
Function ID = 72 (Port Supervision Control)
Controlling Port Address = 0023
Supervision Code = 10000010
Spacer Byte = 00
Assume the T1 port in Example 4-42 is still seized. The following command causes the port to unseize by lowering its AB signals.
04 0506 07 08
72 0023 01 00
Function ID = 72 (Port Supervision Control)
Controlling Port Address = 0023
Supervision Code = 00000001
Spacer byte = 00
System Status
Use the Request Resource Allocation ($80) command to obtain a Resource Allocation ($80) report. This report is a bit map that specifies the online or offline status of every port within a given resource group and port address range. At least one request for each resource group in the system is necessary to determine the complete configuration.
The minimum length for the $80 command is 6 bytes. If a command is too short, it is rejected and a syntax error with a status byte of 03 is returned to the host.
The Resource Allocation ($80) report takes the form of a command returned from the host with a Network Status byte = $01 and the bit-mapped information for the requested address range and resource group. Although this command can be used at any time after system boot, its use is recommended during periods of low traffic volume because of the communications link and system processing overhead required.
Figure 4-27 shows the byte formatting for this command.
Function ID (byte offset 4)—Byte immediately following the Network Header; uniquely identifies the command to the system.
Address Range and Resource Group (byte offset 5)—Determines the range of port addresses and resource group for which the report is requested. Construct the byte in binary according to the descriptions below, then convert to hexadecimal for use in the command.
RRGGGGGG
Resource Allocation ($80) report. The system returns a copy of the command with allocation information attached as a report, and a $01 network status byte. A $0D network status byte indicates that the command was not processed. Refer to "Message Structure Overview," or "Network Status Byte Definitions," for more information.
The following command requests a report of all ports between $00 and $1FF that are in resource group 21.
04 05
80 15
Function ID = 80 (Request Resource Allocation)
Address Range and Resource Group = 00010101
The following command requests a report of all ports between $400 and $5FF that are in resource group 1.
04 05
80 81
Function ID = 80 (Request Resource Allocation)
Address Range and Resource Group = 10000001
System Status
Use the Request Hardware Allocation ($81) command to obtain a Hardware Allocation ($81) report. This report is a bit map that allows the host to match the logical port addresses used in system commands to their corresponding physical rack-level-slot hardware addresses. Reports are requested by port address ranges of 512 ports each; one request for each address range is necessary to determine the complete system configuration.
The minimum length for an $81 command is 6 bytes. If a command is too short, it is rejected and a syntax error with a $03 network status byte is returned to the host.
The $81 report takes the form of a command returned from the host with a $01 network status byte and the bit-mapped information for the requested address range. Although this command can be used at any time after system boot, its use is recommended during periods of low traffic volume because of the communications link and system processing overhead required.
This command returns the address range of Four Span Programmable T1 Interface (4xT1) and Four Span Programmable E1 Interface (4xE1) card spans correctly because ports are added to the database contiguously and in ascending order. Users of ICCs must use the Card Status ($82) command to determine the correct port address range for the spans. ICC spans are added in descending order, and not necessarily contiguously.
Figure 4-28 shows the byte formatting for this command.
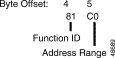
Function ID (byte offset 4)—Byte immediately following the Network Header; uniquely identifies the command to the system.
Address Range (byte offset 5)—Specifies the port address range for which the Hardware Allocation report is to be generated. Specify the byte as follows:
Hardware Allocation Report ($81). The system returns copy of command with allocation information attached as a report and a $01 network status byte. A $03 network status byte indicates that the command was not processed. Refer to "Message Structure Overview," or "Network Status Byte Definitions," for more information.
The following command requests a report of all ports between $00 and $1FF inclusive.
04 05
81 00
Function ID = 81 (Request Hardware Allocation)
Address Range = 00 (ports $00 - $1FF)
System Status
Use the Card Status ($82) command to obtain the Card Status ($82) report. You can specify a single card or a range of cards.
Specify the card by its rack-level-slot (R-L-S) position. Specify a range of cards by encoding the starting R-L-S and ending R-L-S in the command. One $82 report is generated for each card specified in the range. For single cards, the starting R-L-S and the ending R-L-S should be the same.
The $82 report takes the form of a command returned with a $01 network status byte. The report includes the status of the card and the type of the card.
Cisco recommends that you use the command during periods of low traffic volume because of the communications link and system processing overhead.
Figure 4-29 shows the byte formatting for this command.

Function ID (byte offset 4)—Byte immediately following the Network Header; uniquely identifies the command to the system.
R-L-S of the first card in range (byte offsets 5, 6, and 7)—The rack, level and slot number of the first card in the range for which the status is requested. These three bytes correspond to the rack, level and slot location of the card, represented in hex. Valid values for rack are 1 or 2; valid values for level are 0 through 3; valid values for slot are from 1 to 21 (0 to 15 in hexadecimal). Convert the decimal value of the slot into hexadecimal for encoding.
Span Specifier (byte offset 8)—Specifies the span number of the first card in the range. Value of zero specifies that the request is for all spans of a multispan card. For a single-span card, this value can be either 0 or 1.
R-L-S of the last card in range (byte offsets 9, 10, and 11)—This is an optional field. The rack, level and slot number of the last card in the range for which the status is requested. These three bytes correspond to the rack, level, and slot location of the card represented in hexadecimal. Valid values for rack are 1 or 2; valid values for level are 0 to 3; valid values for slot are 1 to 21 (0 to 15 in hexadecimal). Convert the decimal value of the slot into hexadecimal for encoding.
Span Specifier (byte offset 12)—This is an optional field. Specifies the span number of the last card in the range. Zero specifies that the request is for all spans of a multispan card. For a single-span card, this value can be either 0 or 1. If a report is required for a single card, the bytes 9 to 12 are not required in the command.
The R-L-S encoding in bytes 9 to 11 must designate a location at the higher end of the range than the R-L-S specified in byte 5. For example, if bytes 5 to 7, specify rack 1, level 2, and slot 1, bytes 9 to 11 can not specify rack 1, level 1 and slot 1; however, rack 2, level 0, and slot 1 would be valid.
If bytes 5, 6, 7, and 8 (first R-L-S and span), specify rack 1, level 2, slot 1 and span 0, and bytes 9, 10, 11, and 12 (last R-L-S and span) specify rack 2, level 0, slot 1 and span 2, an $82 report is generated for all spans of a card at 1,2,1 (if it is a multispan card), and for all spans of each of the cards in between, and for spans 1 and 2 of a card at 2,0,1.
If any of the slots falling within the range contains a multispan card, an $82 report will be generated for each of the spans in the slot.
One $82 report is generated for each of the cards specified in an $82 command. For any multispan card, a separate report is generated for each of the spans. If the command is processed without any errors, the $82 report indicates a $01 network status byte (NSB).
An NSB of INVALID_RLS_CODE ($4A) indicates that the R-L-S encoding is not valid.
An NSB of INVALID_COMMAND_LENGTH ($41) indicates invalid command length.
An NSB of INVALID_RLSRANGE ($52) indicates that the R-L-S range specified in the command is not valid. This could be because the ending R-L-S is sequentially lower than the starting R-L-S.
An NSB of INVALID_SPAN_CODE ($53), indicates that the span specified in the command is invalid. This will be the return code for cases where a single-span card status is requested with a span specifier greater than 1, or for a multispan card with a span specifier greater than 4.
The following command requests the status of the cards located at R-L-S 1,1,6 and R-L-S 1,1, 7.
04 050607 08 091011 12
82 010106 00 010107 02
Function ID = 82 (Card Status command)
Starting RLS = 1,1,6
Span specifier = 0
Ending RLS = 1,1,7
Span specifier = 2
Request for all spans of the card at R-L-S 1,1,6 and for spans 1 and 2 of the card at R-L-S 1,1,7
System Status
Use the Port Status ($83) command to obtain the Port Status ($83) report. The command queries the status of a range of ports specified by either a port address range or the rack, level and slot (R-L-S) encoding of a card, with the specified span or resource group.
In the case of a query for ports in a multispan card (through R-L-S specification), you must also specify the span (interface).
You can specify a range of ports in different ways, depending upon the application. You can get the status of all the ports on a card by specifying the R-L-S encoding for the card in the command.
You can also get the status of all ports within a port address range by specifying the port address range, which can span cards. If the starting port address and the ending port address are same, the report is generated for that particular port.
You can get the status of all ports within a resource group by specifying the resource group number.
The $83 report takes the form of a command returned with a $01 network status byte. The report contains a series of status report elements; each element contains the port address and its call processing state.
More than one $83 report may be generated for one $83 command if all the port status report elements could not be accommodated in one report. An indicator is present in a group of reports, that identifies which reports are generated for one $83 command.
Cisco recommends that the command be used during periods of low traffic volume because of the communications link and VCO/4K system processing overhead.
Figure 4-30 shows the byte formatting for this command.
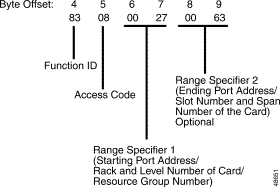
Function ID (byte offset 4)—Byte immediately following the network header; uniquely identifies the report from the VCO/4K system.
Access Code (byte offset 5)—A port address range can be specified in different ways. The access code specifies the way in which the port address range is chosen. Construct the byte in binary according to the descriptions below, then convert to hexadecimal for use in the command.
C000 AGR0
Range Specifier 1 (byte offset 6 and 7)—Set the field after converting the corresponding values into two bytes, right justified, in hexadecimal.
Range Specifier 2 (byte offset 8 and 9)—This is an optional field. If bit G is set in the Access Code, this field should not be included in the command.
The $83 report is generated by the system with a $01 network status byte (NSB), if the command is processed successfully.
If the port range for which the status report is requested is such that one $83 report can not accommodate all the port status report elements, the report is split into as many $83 reports as necessary.
An NSB of OK_MSG ($01) indicates the successful processing of the command.
An NSB of INVALID_ACCESS_CODE ($49) indicates and invalid Access Code.
An NSB of INVALID_COMMAND_LENGTH ($41) indicates an invalid command length.
An NSB of INVALID_RLS_CODE ($4A) indicates an invalid R-L-S encoding.
An NSB of BADGRP_MSG ($0D) indicates an out of range resource group number.
An NSB of WRGGRP_MSG ($39) indicates an undefined resource group number.
An NSB of BADMAT_MSG ($23) indicates that the port address range specified in the command is not valid. This could also be because the ending port address is less than the starting port address.
An NSB of INVALID_SPAN_CODE ($53), indicates that the span specified in the command is invalid. This will be the NSB for cases when the port status of a single span card is requested with a span specifier greater than 1, or for a multispan card with a span specifier greater than 4.
The following command requests status reports for ports $27 and $28. The command specifies the range through port addresses.
04 05 0607 0809
83 08 0027 0028
Function ID = 83 (Port Status command)
Access Code = 0000 1000 (C000 AGRS)
Staring Port Address = 0027
Ending Port Address = 0028
System Maintenance
The Change Port Status ($90) command enables host to activate and deactivate individual ports on an internal service circuit or network interface card. This command performs the same action as taking ports out-of-service using the system administration Card Maintenance screen. Changes performed by the command can be written to the database on the C:\ drive.
The minimum length for a $90 command is 8 bytes. If a command is too short, it is rejected and a syntax error with a $03 network status byte is returned to the host.
This command can be used for ports on all service circuit and network interface card types. When a port is activated, it is placed in idle state. A port can be deactivated immediately (regardless of whether the port is in stable state) or when the port is in idle state (if not idle, the command is aborted). You can specify single ports, clusters of 8 and 24 ports, and groups of nonconsecutive ports. All ports specified in a single command must reside on the same card.
You must specify the activation and deactivation of PRI/N card ports on a port basis only, not on a span basis, in order to avoid an FRM error message. For example, instead of specifying a span (DF DF 00 00 90 72 00 38), specify the ports you want to activate or deactivate (DF DF 00 00 90 72 00 38 FF FF FE) on the span.
Port Status ($D3) reports are issued for each port affected by the command. When the command is used to deactivate clusters and groups of ports only if they are idle, the command may be returned with a $01 Network Status byte (command processing successful) although not all ports specified in the command experienced status changes.
This command can also seize out (busy out) the affected line/trunk ports regardless of their class of service (COS). Busying out ports prevents connected equipment from attempting to use ports taken out of service on the system.
Figure 4-31 shows the byte formatting for this command.
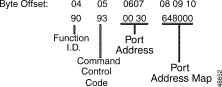
Function ID (byte offset 4)—Byte immediately following the Network Header; uniquely identifies the command to the system.
Command Control Code (byte offset 5)—Specifies the type of action to be performed. Actions include activating/deactivating ports, seizing out on port, and updating the database on hard disk. The status of a single port, a cluster of ports, or a group of ports, can be changed. Construct the byte in binary according to descriptions below, then convert to hexadecimal for use in the command.
AAMD00CC
 |
Note Setting bit M to either 0 or 1, for E1, 4xE1, T1, or 4xT1 ports, results in the same response—E1, 4xE1, T1, or 4xT1 ports always seize out when a $90 command is used to deactivate them. |
Port Address (byte offset 6 and 7)—Hexadecimal representation of the first port address affected by the change of state. Check CC bits in the Command Control Code to determine which port address this byte should represent. If CC = 00, this is the address of the single port affected. If CC = 01 or CC = 10, this is the first address of the cluster of eight or twenty-four ports. If CC = 11, this is the port address of the port represented by the first bit of the Port Address Map (starting in byte offset 8).
Port Address Map (byte offset 8 to 10)—Included only when CC = 11 in the Command Control Code. One to three bytes specifying the ports to be affected by the status change. Each bit represents one of up to 24 consecutive ports, beginning with the port at the port address specified in byte offset 6 & 7. A "1" in the port's bit position indicates its status is to be changed. For card types with 8 ports, use only byte offset 8 to indicate status changes; bytes 9 & 10 can be omitted. Construct the bytes according to the format shown Figure 4-32 and convert to hexadecimal.
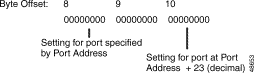
A Port Status ($D3) report is generated for each port affected. The Old Status/New Status byte (byte offset 5) in the $D3 report indicates whether the command was successfully executed and the new port status. The $D3 report Originator byte (byte offset 8) is $61 when the port change of state attempt was originated by the host with a $90 command. However, if a port is deactivated using a $90 command and the card it resides on is later taken out-of-service, any $D3 reports generated when the card returns to service will contain a $12 Originator byte value (port busied out via system administration) rather than a $61 byte value.
When the command is applied to the first port of the DTG card, the $D3 report generated will always indicate no status change (this port is not supported and remains deactivated at all times). Also, port status changes applied to DTG ports are only performed on the ports residing on the Active tone card. Although the ports on the Standby tone card are assigned the same logical addresses as the ports on the Active card, any $D3 report generated represents the status of the Active tone card port.
A command returned by the system with a network status byte not equal to $01 indicates that the command was not processed. The following network status bytes may be returned: $03, $0E, $23 and $3B.
Assume there is an incoming trunk port at port address $30. The status of the port is CP_IDLE. The command below deactivates the port, writes the change to the hard disk, and seizes out the far end.
04 05 0607
90 70 0030
Function ID = 90 (Change Port Status)
Command Control Code = 01110000
Port Address = 00 30
The same action can be performed using the following command:
04 05 0607 080910
90 73 0030 800000
Function ID = 90 (Change Port Status)
Command Control Code = 01110011
Port Address = 00 30
Port Address Map = 10000000 00000000 00000000
The following command deactivates the ports at addresses $00 31, $00 32, $00 35 and $00 38. Ports are deactivated only if they are in idle state. Changes are written to the hard disk and the ports are not seized out at the far end. Note that all the ports are on one card.
04 05 0607 080910
90 93 0030 648000
Function ID = 90 (Change Port Status)
Command Control Code = 10010011
Port Address = 00 30
Port Address Map = 01100100 10000000 00000000
The command below activates the port at address $00 49 and writes the change to the hard disk. Because the port is activated, no outward seizure can be performed.
04 05 0607
90 10 0049
Function ID = 90 (Change Port Status)
Command Control Code = 00010000
Port Address = 00 49
Resource Control
Use the Voice Prompt Maintenance Control ($91) command to allow the host to maintain voice prompt information on the IPRCs in a system. The $91 command provides a mechanism for the host to upload voice prompt information from, and download prompt information to, one or more IPRCs.
This command returns a $01 network status byte upon acceptance of the command, which indicates that the command was successfully validated and that the prompt maintenance operation has begun. When the command processing completes, a subsequent message is sent to the host to indicate the completion status. The requested command is re-sent with a $4B network status byte, which indicates that the command processed successfully, or a $4C network status byte, which indicates that an error was encountered while processing the command.
The $91 command has the format:
Main Command Segment [optional segment(s)...]
Figure 4-33 shows the byte formatting for this command.
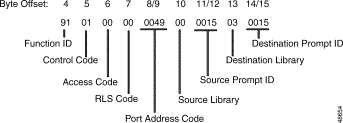
Main Command Segment
The Main Command segment is composed of byte offsets 4 to 15 and must be included in its entirety. Components of the Main Command segment are defined as follows.
Function ID (byte offset 4)—Byte immediately following the Network Header; uniquely identifies the command to the system.
Control Code (byte offset 5)—1 byte.
Access Code (byte offset 6)—1 byte.
RLS Code (byte offset 7)—1 byte.
Port Address Code (byte offsets 8 and 9)—2 bytes.
Source Library (byte offset 10)—1 byte.
Source Prompt ID (byte offsets 11 and 12)—2 bytes.
Destination Library (byte offset 13)—1 byte, upload only.
Destination Prompt ID (byte offsets 14 and 15)—2 bytes, upload only.
Configuration Control
Use the Configure VCA/Set System Clock ($C0 00) command to configure any specific Virtual Communication Addresses (VCAs) needed in addition to the global communications address, $DF. This command also allows you to set the system real-time clock. Specific VCAs are especially important when a single host controls multiple systems, and are maintained through system resets or power-down cycles.
In a redundant system, this command can be sent to both the active and standby controllers.
Figure 4-34 shows the byte formatting for this command.
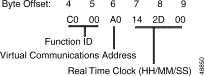
Function ID (byte offsets 4 and 5)—Bytes immediately following the Network Header; uniquely identifies the command to the system.
Virtual Communications Address (byte offset 6)—Hexadecimal representation of new address; system still responds to commands sent to the global address $DF. Specifying $FF in this byte leaves the VCA unchanged, and is used when just setting the clock. Specifying $FE sets the VCA to the global address $DF.
Real Time Clock (byte offset 7 D9)—24-hour clock setting; hours, minutes, and seconds are represented separately in hex. To leave the hours, minutes, or seconds unchanged, specify $FF in the byte. If there is no change to the clock, set all three bytes to $FF.
No response from the system upon successful completion is provided unless Return All has been set in the Network Header. A command returned by the system with a network status byte not equal to $01 indicates that the command was not processed.
Invalid clock values, such as 44:55:66, cause the system to return the command with a network status byte of $1A (bad date/time). If the command specifies to change both the VCA and the time, the VCA is changed even if the clock value is invalid. Refer to "Message Structure Overview," or "Network Status Byte Definitions," for more information.
The following command sets the Virtual Communications Address to $B0 and leaves the system time unchanged.
0405 06 070809
C000 B0 FFFFFF
Function ID = C0 00 (Configure VCA/Set System Clock)
Virtual Communications Address = B0
Real Time Clock = No change ($FF in all time bytes)
The following command sets the Virtual Communications Address to $A0 and sets the system time to 8:45:00pm.
0405 06 070809
C000 A0 142D00
Function ID = C0 00 (Configure VCA/Set System Clock)
Virtual Communications Address = $A0
Real Time Clock = Change time to 8:45:00pm ($14 = 20; $2D = 45; $00 = 00)
The following command sets the system time to 12:00:00 midnight without configuring a new Virtual Communications Address.
0405 06 070809
C000 FF 000000
Function ID = C0 00 (Configure VCA/Set System Clock)
Virtual Communications Address = $FF (do not configure new address)
Real Time Clock = Change time to 12:00:00 midnight [$00 = 00 (first hour of the day is hour 0); $00 = 00; $00 = 00]
Configuration Control
Use the Change Active Controllers ($C0 01) command in redundant systems to transfer system control from the active side to the standby side. This command can be sent to either the active or standby system controller. Optional reset of previously active side is also available.
The $C0 01 command can only function if both sides, active and standby, are operational.
The $C0 01 command is forwarded, via the update channel, to the active system for processing; however, the standby side system cannot unilaterally make itself active. This action requires the participation of the active side processor and the AAC.
A controller can request a change to standby from active, but only the AAC can complete standby to active transitions. When a request is sent to a standby processor, the $C0 01 command is sent to the active side processor. The active side processor then sends a message to the AAC, changing system control to standby status. The AAC does this by using its switchover circuitry and changes the formerly standby side status to active.
If a switchover is desired following an AAC reset of the active side, toggle the A/B side switch to the side that needs to be made active. If you reset a controller via the AAC front panel, the normal AAC failure detection and switchover circuitry is disabled. In this event, if you then reset the active side from the AAC front panel, the standby side will not change status to active.
Use the MVME147 reset button, or physically remove the combined controller, to make a switchover. These actions do not disable the AAC detection/switchover logic.
 |
Note If there is no active controller, the AAC reset of the active side causes loss of operation for several minutes. |
Figure 4-35 shows the byte formatting for this command.

Function ID (byte offsets 4 and 5)—Bytes immediately following the Network Header; uniquely identifies the command to the system.
Condition Code (byte offset 6)—Determines the conditions of the transfer; specify this byte as follows:
Active/Standby Mode ($DC) report from both sides is provided when transfer has occurred.
No response from the system upon successful completion is provided unless Return All has been set in the Network Header. A command returned with a $03 network status byte indicates a syntax error. A command returned with a $08 network status byte indicates that the system is not redundant and cannot perform a switchover. A command returned with a $36 network status byte indicates that the switchover request has been queued until completion of File Synchronization between the active and standby sides. A $5E network status byte is returned to indicate that a host-initiated switchover request was denied due to a Live Upgrade in progress.
The following command forces a transfer without a reset.
0405 06
C001 00
Function ID = C0 01 (Change Active Controllers)
Condition Code = 00 (no reset)
The following command specifies a transfer, resetting the previously active side.
0405 06
C001 04
Function ID = C0 01 (Change Active Controllers)
Condition Code = 04 (reset previously active side after transfer)
Configuration Control
Use the T1 Synchronization Control ($C0 02) command to alter Master Timing Link parameters. All changes made using this command become part of the system database. This command allows the following:
If the command is used to switch to incoming synchronization, the system verifies that the card on which the specified port(s) is located is an in-service T1 or PRI card, and that the primary and secondary addresses are not on the same T1 or PRI card. If these conditions are met or no switch to incoming is specified in the command, the database is updated on both the active and standby sides before switching to the new timing source occurs. If the new timing source has active alarms, the database is updated but the switch to the new source does not occur. For a flowchart of T1/PRI Synchronization, refer to the Cisco VCO/4K System Administrator's Guide.
Figure 4-36 shows the byte formatting for this command.

Function ID (byte offsets 4 and 5)—Bytes immediately following the Network Header; uniquely identifies the command to the VCO/4K system.
Synchronization Mode (byte offset 6)—Specifies the Master Timing Link parameters to be altered.
Primary Link Value (byte offsets 7 and 8)—T1 port address; specify only if Synchronization Mode = 03 or 04; new primary link value to be used for timing
Secondary Link Value (byte offsets 9 and 10 or 7 and 8 if no Primary Link Value)—T1 or PRI port address; specify only if Synchronization Mode = 03 or 05; new secondary link value to be used for timing
No response from the VCO/4K upon successful completion is provided unless Return All has been set in the Network Header. A command returned by the VCO/4K with a network status byte not equal to $01 indicates that the command was not processed. The following network status bytes may be returned: $03, $19, $23, $24, and $2A. Refer to "Message Structure Overview," or "Network Status Byte Definitions," for more information.
A command returned by the system with a $2A network status byte indicates that the primary and secondary values specified are on the same T1 or PRI card.
The following command changes the primary and secondary link values in the database. If the primary link is available, timing is switched to it. If the primary is not available, the system switches timing to the secondary value. If neither primary nor secondary links are available, timing switches to Internal. If both link values specified in the command are the same as those already in use on the VCO/4K system, no change occurs.
0405 06 07080910 11121314
C002 03 00000018 00000059
Function ID = C0 02 (T1 Synchronization Control)
Synchronization Mode = change Master Timing Link (new primary and secondary - $03)
Primary Link Value = 0018
Secondary Link Value = 0059
The following command will cause the VCO/4K system to switch to internal synchronization. If the VCO/4K system is already using internal synchronization, no change occurs.
0405 06
C002 01
Function ID = C0 02 (T1 Synchronization Control)
Synchronization Mode = switch to internal synchronization ($01)
No link values needed in command
This following command switches timing to a new secondary link value and updates the database. Timing is switched to this new secondary link regardless of whether a secondary or primary link was already being used.
0405 06 07080910 11121314
C002 05 00000000 00000017
Function ID = C0 02 (T1 Synchronization Control)
Synchronization Mode = change Master Timing Link (secondary - $05)
Primary Link Value = not necessary for this command; omitted
Secondary Link Value = 0017
Configuration Control
Use the Set/Reset Host Alarms ($C0 03) command to set or clear major, minor, and auxiliary alarms controlled by the host. These host alarms affect the alarm indicators located on the front of the Alarm Arbiter Card (AAC) as a central monitor point. Major and minor alarms are accompanied by an audible signal if the AAC is equipped with the audible alarm and closes the external alarm contacts on the AAC. This command does not reset the system internally controlled alarms. Any alarms set by this command are cleared when the system resets.
If an AAC is connected to a CO alarm system (external alarm), this command should be used with those implications in mind.
Figure 4-37 shows the byte formatting for this command.

Function ID (byte offsets 4 and 5)—Bytes immediately following the Network Header; uniquely identifies the command to the system.
Alarm Control Code (byte offset 6)—Determines whether an alarm is set or reset, and the type of alarm. The first digit of this byte specifies whether the alarm is set or reset; the second digit specifies the type of alarm.
Upon setting or clearing an alarm, the system generates an Alarm Condition ($F0) report indicating the alarm condition and severity. Command returned by the system with a Network Status byte equal to $03 indicates a syntax error. Refer to "Message Structure Overview," or "Network Status Byte Definitions," for more information.
Messages written to the system printer will reflect the alarm set/clear by the host. The alarms are also displayed on the System Alarm Display and output as part of the Periodic Alarm Reports. For more information on the system alarm report and display information, refer to Cisco VCO/4K System Administrator's Guide and Cisco VCO/4K System Messages.
The following command sets a host major alarm on the system.
0405 06
C003 80
Function ID = C0 03 (Set/Reset Host Alarms)
Alarm Control Code = 80
First digit = 8 (set an alarm)
Second digit = 0 (major alarm)
The following command clears a host minor alarm on the system.
0405 06
C003 01
Function ID = C0 03 (Set/Reset Host Alarms)
Alarm Control Code = 01
First digit = 0 (clear an alarm)
Second digit = 1 (minor alarm)
Configuration Control
Use the Host Call Load Control ($C0 04) command in conjunction with the Host Control of Call Load feature. (Refer to the System Host Configuration screen information in the Cisco VCO/4K System Administrator's Guide.) When the feature is enabled, this command allows the host to start or stop the sending of Inpulse Rule Complete ($DD) reports and Incoming Port Change of State ($DB) reports that indicate an off hook on an incoming port. Because calls cannot be completed through the system without host intervention, this effectively stops call processing.
The system verifies that the Enable Host Control of Call Load feature has been enabled before processing the command. If the feature is not enabled, the command is returned with a $1B network status byte (feature not enabled) in the Network Header.
If byte offset 6 is set at 01, no off hook reports ($DB with offhook state) and no Inpulse Rule Complete reports ($DD) are sent to a host link until it has issued a $C0 04 command indicating that it is ready to process calls. In addition, commands received from that host link are rejected until it is ready to process calls. On hook reports for both incoming and outgoing ports are still sent to the host as well as other reports.
If byte offset 6 is set at 02, new call reports will not be sent to a host link until that link has indicated that it is ready to process calls. However, commands will still be accepted from the host link for calls in progress.
The $C0 04 command can be used, for example, to allow the host to request configuration information after a system reboot, before handling calls. Also, with byte offset 6 set at 02 as described above, current calls can be completed, with no new calls taken - a type of "graceful" shutdown.
This command affects only the host port on which it is received. If there are multiple active links to the host, the command must be sent over each active link.
Figure 4-38 shows the byte formatting for this command.

Function ID (byte offsets 4 and 5)—Bytes immediately following the Network Header; uniquely identifies the command to the system.
Load Control Code (byte offset 6)—Specifies whether the system should process incoming calls by reporting them to the host.
No response from the system upon successful completion unless Return All has been set in the Network Header. A command returned by the system with a $1B network status byte indicates that the Host Load Control feature is not enabled and the command was not processed. A $03 network status byte indicates a syntax error in the command. Refer to "Message Structure Overview," or "Network Status Byte Definitions," for more information.
Table 4-9 summarizes $C0 04 command modes.
| Host Link State | Affect On Messaging |
|---|---|
ONLINE_READY | "Normal" messaging. All host commands and reports are allowed. Set by disabling the Call Load feature (and host link becomes active), or by a $C0 04 host command with a parameter value of 00. |
ONLINE_NOT_READY | Call processing is effectively suspended; host commands are rejected (original feature functionality). Set by a $C0 04 host command with a parameter value of 00. None of the following are allowed:
|
ONLINE_RESTRICTED | Processing of calls in progress; host commands accepted (enhanced feature functionality). Set by a $C0 04 command with a parameter value of 02. None of the following are allowed:
|
The following command instructs the system to start sending Incoming Port Change of State ($DB) and Inpulse Rule Complete (Macro) ($DD) reports to the host.
0405 06
C004 00
Function ID = C0 04 (Host Call Load Control)
Load Control Code = 00 (report call events to host; normal call processing)
The following command instructs the system to stop sending change of state and Inpulse Rule Complete (Macro) ($DD) reports to the host.
0405 06
C004 01
Function ID = C0 04 (Host Call Load Control)
Load Control Code = 01 (no reports to host; call processing suspended)
In the following command, current calls can be run to completion (i.e., host commands are accepted for calls in progress). No new calls will be reported to the host ("restricted" call processing).
0405 06
C004 02
Function ID = C0 04 (Host Call Load Control)
Load Control Code = 02 (no reports to host; commands will be accepted for calls already in progress)
Configuration Control
Use the Host Assume/Relinquish Port Control ($C0 05) command to extend the system controller functionality. This command allows a host to relinquish control of a call assigned to itself, or assume control of a call that has been assigned to a different host.
The $C0 05 command has been extended to perform the assume/relinquish port control and assume/relinquish conference control functions. A function code has been added to allow a host link to override a controlling host assignment. Two port control operating modes, and two conference control operating modes, are provided.
The 00 port control operating mode allows a host to assume control of a port, and the 01 port control operating mode allows a host to relinquish control of a port. In either case, the assignment override remains in effect as long as the affected port is involved in a call, or until a subsequent override command is received. The relinquish mode clears the controlling host assignment for the specified port so that another host can take control of that port.
The 02 conference control operating mode allows a port to relinquish control of a port, and the 03 conference control operating mode allows a port to assume control of a port. In either case, the assignment override remains in effect as long as the affected port is involved in a call, or until a subsequent override command is received. The relinquish mode clears the controlling port assignment for the specified port so that a host can take control of that port.
All command modes affect all line/trunk and virtual ports associated with the named port; all line/trunk and virtual ports in the call chain will have their controlling host indicators cleared or overridden. Resource ports are not affected.
Figure 4-39 shows the byte formatting for this command.
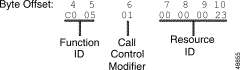
Function ID (byte offsets 4 and 5)—Bytes immediately following the Network Header; uniquely identifies the command to the system.
Call Control Modifier (byte offset 6)—Determines the type of action to be taken.
Port Address/Conference Number (byte offsets 7 and 8)—Port Address or Conference Number for which control is being seized or relinquished. A 0000 value is invalid.
Table 4-10 shows the network status bytes (NSBs) associated with the $C0 05 command.
| NSB | Description |
|---|---|
$03 | Syntax error. |
$0F | Call or conference is not controlled by this host. Indicates that the host port from which this command was received does not correspond to the port controlling the call. This return code is possible only when relinquishing a port (Port Control Modifier value 00). |
$11 | The port in command is idle but should not be. Indicates that the circuit identified by the port address specified in the command (usually a controlling port or incoming port) is in the CP_IDLE MState and the command cannot be processed. |
$23 | An invalid port address is specified in the command. Indicates that the port address byte values do not fall within the range $00 00 to $07 FF, or $80 00 to $80 FF (virtual ports). This NSB also indicates an invalid conference number for host control modifiers 02 and 03. |
A Call Control Modifier value of 00 (relinquish control) causes the switch to set the controlling host indicator to "no host" for the specified port and any other associated ports. An alternate host can subsequently take control of that port (and any/all associated ports by sending a command which affects that port.
A Port Control Modifier value of 01 (assume control) causes the switch to override any existing controlling host indicator for the specified port and any associated ports. The controlling host identifier for these ports is set to the host issuing the command. Assumption of control over a port is therefore equivalent to the aggregate behavior provided by a "relinquish control" command followed by normal host command processing which affects that port. Refer to "Message Structure Overview," or "Network Status Byte Definitions," for more information.
A Call Control Modifier value of 02 (relinquish conference control by conference number) causes the switch to set the controlling host indicator to no host for the specified conference number. The controlling host identifier for the conference call, as well as for all individual interface ports involved in that conference, are also set to no host. An alternate host can subsequently take control of that conference call (and all associated ports) by sending a command which affects that conference call.
A Call Control Modifier value of 03 (assume conference control by conference number) causes the switch to override any existing controlling host indicator for the specified conference number. The controlling host identifier for the conference call, as well as for all individual interface ports involved in that conference, are also set to the host issuing the command. This command mode assists in load sharing among controlling hosts.
The following command instructs the system relinquish host control of the specified port address.
0405 06 0708
C005 00 nnnn
Function ID = C0 05 (Host Assume/Relinquish Port Control)
Port Control Modifier = 00 (Relinquish control)
Port Address = nnnn (represents specified port address)
The following command instructs the system to assume host control of the specified port address.
0405 06 0708
C005 01 nnnn
Function ID = C0 05 (Host Assume/Relinquish Port Control)
Port Control Modifier = 01 (Assume control)
Port Address = nnnn (represents specified port address)
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
Posted: Sat Sep 28 14:30:58 PDT 2002
All contents are Copyright © 1992--2002 Cisco Systems, Inc. All rights reserved.
Important Notices and Privacy Statement.