|
|

This chapter describes how to use the Cisco Network Order Manager to configure one or more Cisco DSLAM devices which may be connected in a subtended configuration.
CNOM supports management of PVC and SPVC connections starting at the ATM interface of a DSL port and terminating at a trunk port. Connections are supported for any combination of chassis and network interface cards with the following exceptions:
A subtended DSLAM network architecture is illustrated in Figure 3-1.
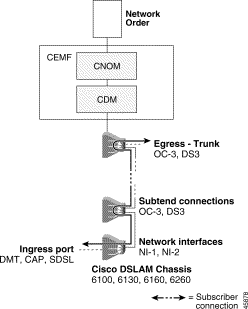
 |
Note The dotted lines in Figure 3-1 indicate that more DSLAMs can be added to the network. |
Before you can use CNOM to configure Cisco DSLAM devices, you must install the following software:
Refer to the installation guides for each product for installation procedures. The CNOM installation procedure is described in "Installing Cisco Network Order Manager."
After you install CDM and CNOM, use the following procedure to get the two components to interoperate:
1. Discover and commission DSLAMs and their subrack components.
2. Discover Subtends using the CDM Subtend Manager (refer to the CDM documentation).
 |
Note To make connections on a DSLAM, you must Discover Subtends using the CDM Subtend Manager. This applies to a single chassis as well as subtended chassis. |
3. Set up line IDs for the ingress ports using the CNOM set_line_ids script (this is an optional step as the containment path can be used instead).
4. Set up profiles of the same name for all interface types and ATM QoS using the CNOM create_ni2_profile script.
5. Set up the subscriber connections using the CNOM connect_cdm script.
The connection policy for DSLAM-only architecture allows CNOM to maintain an identifier for the subscriber DSL port. You must resolve the identifier to a CEMF object identifier and configure a mapping attribute on each subscriber ATM interface to allow CNOM to resolve from an external name to a CEMF name and object ID.
The policy connectSubscriber_cdm sets up end-to-end PVC or SPVC connections across a subtended network of DSLAMs.
 |
Caution When you run policies, be sure that the policy is one designated for the specified application. For example, the policy listed above is specifically designed for use in a CDM environment. |
To run the policy successfully, meet the following conditions:
The policy expects the following attributes in the work order:
workOrder:DDMWorkOrder.connectionIdentifierworkOrder:DDMWorkOrder.ingressIdentifierworkOrder:DDMWorkOrder.serviceCharacteristicsworkOrder:DDMWorkOrder.autoAllocateworkOrder:DDMWorkOrder.setupSoftPVCworkOrder:DDMWorkOrder.ingressVCIworkOrder:DDMWorkOrder.egressVCI |
Note For descriptions of these attributes, refer to the "Cisco Network Order Manager Policies" section. |
To manage a profile, create a profile which corresponds to each connection metric that is required. The profiles corresponding to the same connection metric must use the same name.
For instance, an operator may provide a service (called Gold) which is characterized by:
and another service (called Silver) with:
To define each type of service, the operator might:
1. Create profiles named Gold and Silver for ATM QoS.
2. Create Gold and Silver profiles for each type of DSL port (for example, DMT and CAP ports on a chassis with NI-2 line cards).
3. Apply the appropriate set of profiles to the CAP or DMT port to configure the port for service:
In the CNOM work order, the value of workOrder:DDMWorkOrder.serviceCharacteristics specifies the appropriate set of profiles to apply; therefore, the value must match the name of the required profile. For example, if serviceCharacteristics is set to Gold, the system applies the appropriate DSL-specific Gold profile and the ATM QoS Gold profile.
 |
Note The name of a DSL-specific profile (CAP, DMT, SDSL) must match the name of the corresponding ATM QoS profile; otherwise, the DSL profile is not applied to the connection when the work order is invoked. |
Use the following profiles in the connection policy for creating connections in a DSLAM-only architecture:
 |
Note An ATM QoS profile is mandatory. The DSL-specific profile is optional; if you do not specify one, the default profile for that port type will be used. |
NI-2 profiles consist of DSL parameter profiles and ATM QoS. You can set up the profiles in the CDM GUI, or by using the policies supported by the CDM NOA module.
 |
Note CNOM configures the ADSL and the DMT profiles separately with the GUI, for DMT profile, but configures the ADSL and the DMT profiles together when using the DMT profile policy. |
To manage connections in a DSLAM-only network architecture, use the following sections as a guide.
To make connections in a DSLAM-only network architecture, use the CNOM policy in Table 3-1.
| Policy | Description |
|---|---|
| Creates a PVC from a DSL port to the top trunk in a subtend tree |
 |
Caution When you run policies, be sure that the policy is one designated for the specified application. For example, the command listed in Table 3-1 is specifically designed for use in a CDM environment. |
For information about the work order interface, refer to "Cisco Network Order Manager Policies."
When the connectSubscriber_cdm policy is invoked, CNOM performs the following steps to create a connection from a DSL port to the top trunk of a subtended tree of DSLAMs.
1. CNOM identifies the DSLAM line port by querying for the line ID attribute on the interface, or by using the name supplied in the incoming work order.
2. CNOM configures the DSL port by applying profiles.
3. CNOM deploys the PVC objects on the appropriate ports in the DSLAMs in subtend path.
4. CNOM generates appropriate VPI and VCI values for the intermediate PVCs.
5. CNOM invokes the connect action on the PVC objects to configure the PVCs in the nodes.
If a connection is:
workOrder:DDMWorkOrder.connectionIdentifier value. Expanding this object shows the objects CDMDmmConnectObj and ATM.CDMDmmConnectObj, the PVCs set up in this connection are displayed. In the case of: CNOM performs the following steps to execute the connectSubscriber_cdm policy:
Initial State: ddmGateway:DDM.connectSubscriber_cdm_checkIngressInfo
1. Determine if the parameter sent is alias or containment path—NOP.
2. Find object:
a. Path—Find the port object name through which connections are made on the DSLAM: ResolveName.
b. Alias—Find the port to which the alias name maps: FindMappedObject.
3. Create an object for the connection: CreateConnectionObject.
4. Determine the egress port on the DSLAM: GetTrunk.
5. Set up transport parameters for the DSL Port: ConfigureDSLPort.
6. Connect the PVC, set VPI/VCI: ConnectPVC.
To remove a connection in a DSLAM-only network architecture, use the CNOM policy in Table 3-2.
| Policy | Description |
|---|---|
| Disconnects a PVC |
The disconnectSubscriber_cdm policy takes the connectionIdentifier supplied in the earlier connection in the attribute workOrder:DDMWorkOrder.connectionIdentifier, and removes the connection.
The restoreCDMConnection policy restores connections on a DSLAM subtended network which were made earlier using the CNOM policy connectSubscriber_cdm. The policy reconstructs the configuration on the CEMF database without changing the node. Since CDM supports synchronization from the node to the CEMF database, the policy is able to handle both cases where the CDM configuration may already have been synchronized and where the CDM configuration has not yet been synchronized.
The restoreCDMConnection policy performs the following functions:
CDMDMMConnectionObj object to hold CDM PVCs. The clearCDMConnection policy deletes a CDM PVC from the CEMF database for an PVC object that has already been deleted in the node. To delete a PVC from a DSLAM-only network architecture, use the CNOM policy in Table 3-3.
| Policy | Description |
|---|---|
| Deletes a PVC |
The clearCDMConnection policy takes the connectionIdentifier supplied in the earlier connection in the attribute workOrder:DDMWorkOrder.connectionIdentifier, and deletes the PVC.
 |
Note If a CDM PVC object does not exist in the CEMF database after a possible CDM synchronization with the node, the PVC object is not present in the connectionObjects view. In this case, the only procedure the policy performs is to delete the connection objects. |
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
Posted: Tue Sep 17 07:52:45 PDT 2002
All contents are Copyright © 1992--2002 Cisco Systems, Inc. All rights reserved.
Important Notices and Privacy Statement.