|
|

This chapter describes how a Cisco Secure VPN Client (VPN Client) interoperates with a Cisco gateway using a pre-shared key or wildcard pre-shared key for Internet Key Exchange (IKE) authentication. With a pre-shared key, you can allow for one or more clients to use individual shared secret keys to authenticate encrypted tunnels to a gateway.With a wildcard pre-shared key, you can allow for one or more clients to use a shared secret key to authenticate encrypted tunnels to a gateway.
 |
Note Throughout this chapter, there are numerous configuration examples that include unusable IP addresses, passwords, and public key examples. Be sure to use your own IP addresses, passwords, and public keys when configuring your VPN Clients and gateway. |
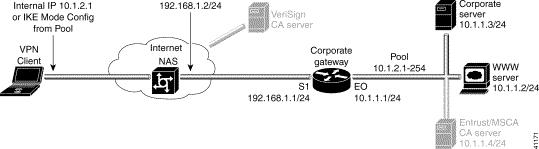
To configure a new gateway for a security policy on a VPN Client, perform the following tasks:
To open the Security Policy Editor
Click Start>Programs>Cisco Secure VPN Client>Security Policy Editor.
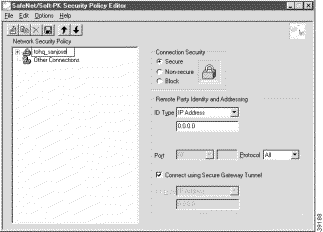
The SafeNet/Soft-PK Security Policy Editor window appears, as shown in Figure 5-2. Table 5-1 describes the field descriptions for the SafeNet/Soft-PK Security Policy Editor.
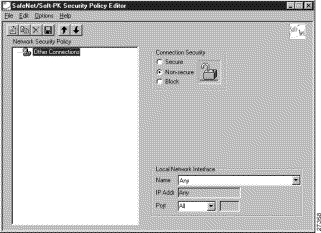
| Field | Description |
|---|---|
Security Policy Editor | This window establishes connections and their associated proposals, and lists connections in a hierarchical order that defines an IP data communications security policy. |
Other Connections | This object is a policy, or a default connection, and the first step in establishing security policies for individual connections. |
Connection Security | Under Connection Security, you can define IP access for this connection using Secure, Non-secure, and Block options. |
|
|
|
|
|
|
To configure other connections
In the left pane, Other Connections appears.
The Other Connections pane appears in the right pane. Use the Other Connections as the default for your security policy.
Step 2 In the right pane, under Connection Security, click the Non-Secure option. Leave all other fields as-is.
Figure 5-2 shows how this is displayed on the Other Connections pane. Table 5-2 describes the field descriptions for the Other Connections pane.
 |
Note If you do not specify the Non-Secure option for the Other Connections pane, you will not be able to modify the Internet Interface or Local Network Interface to add the pre-shared key. |
To create a new connection
Step 2 On the File menu, click New Connection.
In the left pane, the default New Connection placeholder appears for the New Connection pane.
Step 3 Select New Connection, and in its place, define a unique name for the connection to your gateway.
For example, if your router name is hq_sanjose, you might rename the connection tohq_sanjose, as shown in Figure 5-3. Table 5-2 describes the field descriptions for the New Connection pane.
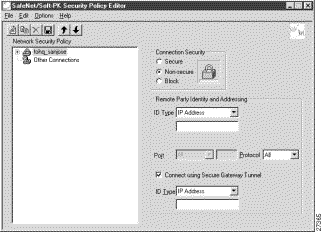
To define the new connection
The New Connection pane appears.
Step 2 In the right pane, click the Secure option.
Step 3 Either define the connection using a pre-shared key or wildcard pre-shared key.
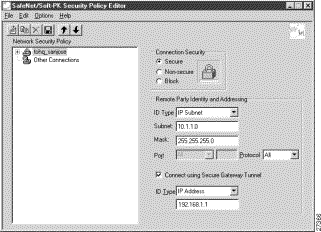
To define the connection for the VPN Client with a pre-shared key
In the right pane, under Remote Party IP Addressing, enter the following parameters:
Step 2 In the Subnet box, enter your corporate subnet. In this example, the IP address of the corporate subnet, 10.1.1.0 is entered.
Step 3 In the Mask box, enter the subnet mask of the IP address of your corporate subnet. In this example, the subnet mask of the corporate subnet, 255.255.255.0 is entered.
Step 4 The Port list and box are inactive as a default. In the Protocol list, click All.
Step 5 Select the Connect using Secure Gateway Tunnel check box.
Step 6 In the ID_Type list, click IP Address.
Step 7 In the ID_Type box, enter the IP address of the secure gateway. In this example, the secure gateway, 192.168.1.1 is entered.
Figure 5-4 shows how this is displayed on the New Connection pane for pre-shared key. Table 5-2 describes the field descriptions for the New Connection pane.
To define the connection for the VPN Client for a wildcard pre-shared key
In the right pane, under Remote Party IP Addressing, enter the following parameters:
Step 2 In the IP address value box, enter the wildcard IP address, 0.0.0.0.
Step 3 The Port list and box are inactive as a default. In the Protocol list, click All. Leave all other fields as-is.
Figure 5-5 shows how this is displayed on the New Connection pane for wildcard pre-shared key. Table 5-2 describes the field descriptions for the New Connection pane.
| Field | Description |
|---|---|
Network Security Policy | Under Network Security Policy, the proposals that will be used to negotiate the authentication and encryption methods are displayed. |
|
|
|
|
Connection Security | Under Connection Security, you can define IP access for this connection using Secure, Non-secure, and Block options. |
|
|
|
|
|
|
Remote Party Identity and Addressing | Under Remote Party Identity and Addressing, define the IPSec peer with which the VPN Client will establish a secure tunnel. |
ID Type | This list displays options for defining the IPSec peer identity including IP address, domain name, email address, IP subnet, IP address range, and distinguished name. Depending on the option you choose, different values will appear in the right pane. |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Port | This list shows the IPSec peer's protocol ports. A default of All secures all protocol ports. |
If selected, this check box specifies that the IPSec peer is protected by a secure IPSec-compliant gateway, such as a firewall. | |
ID_Type | This list shows the identification type of the gateway including IP address, domain name, and distinguished name. Depending on the option you choose, different values will appear in the right pane. |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
To specify the VPN Client's identity, perform the following tasks:
To choose an identity
The new connection expands with My Identity and Security Policy.
Step 2 Click My Identity.
The My Identity pane appears in the right pane.
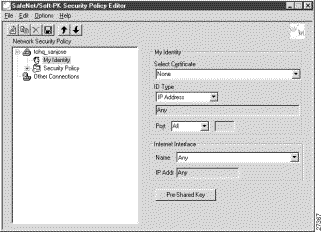
Step 3 In the right pane, under My Identity, enter the following:
a. In the ID_Type list, click IP Address.
b. In the Port list, click All.
Step 4 In the right pane, under Internet Interface (or Local Network Interface), enter the following:
a. In the Name list, click Any. The IP Addr list is inactive as a default.
Step 5 Click Pre-Shared Key.
The Pre-Shared Key window appears.
Figure 5-6 shows how this is displayed on the My Identity pane for pre-shared key. Table 5-3 describes the field descriptions for the My Identity pane.
| Field | Description |
|---|---|
Network Security Policy | Under Network Security Policy, the proposals that will be used to negotiate the authentication and encryption methods are displayed. |
|
|
My Identity | Under My Identity, specify options for determining the identity of the VPN Client. These options include Select Certificate, ID Type, and Port. |
If you are using digital certification, this list displays all the available digital certificates from which to choose. If you are not using digital certification, None is the default option. | |
This list indicates the IP address option for the VPN Client on the corporate subnet. | |
|
|
Port | This list shows the VPN Client's protocol ports. A default of All secures all protocol ports. |
Local Network Interface: | Under Local Network Interface or Internet Interface, specify the hardware interface on the PC or laptop through which the connection will be established. These options include Name and IP Addr options. |
Name | This list indicates the names of the hardware interfaces on the PC or laptop. A default of Any enables all hardware interfaces. |
IP Addr | This list indicates the IP addresses of the hardware interfaces on the PC or laptop. A default of Any enables all hardware interface IP addresses. |
|
|
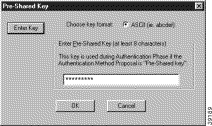
To enter the pre-shared key
The minimum keystring is 8 characters, and the maximum keystring is 128 characters. In this example, cisco1234 is entered.
To start the key exchange, both the VPN Client and the gateway must use the same public key.
Step 2 Click OK.
Figure 5-7 shows how this is displayed in the Pre-Shared Key dialog box.
 |
Note In the Cisco Secure VPN Client Version 1.0, the pre-shared keystring is visible from the Pre-Shared Key dialog box. In Cisco Secure VPN Client Version 1.1, the pre-shared keystring is hidden. |
To configure authentication on the VPN Client for a pre-shared key or wildcard-preshared key, perform the following steps:
To specify authentication security policy
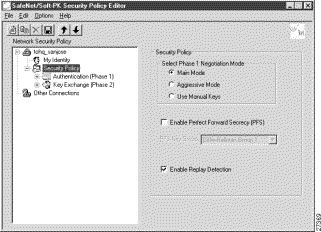
The Security Policy pane appears in the right pane.
Step 2 In the right pane, under Security Policy, click Main Mode.
Step 3 Select the Enable Replay Detection check box.
Figure 5-8 shows how this is displayed on the Security Policy pane. Table 5-4 describes the field descriptions for the Security Policy pane.
| Field | Description |
|---|---|
Network Security Policy | Under Network Security Policy, the proposals that will be used to negotiate the authentication and encryption methods are displayed. |
|
|
Security Policy | Under Security Policy, define the Select Phase 1 Negotiation Mode, Enable Perfect Forward Secrecy, or Replay Detection options. |
Select Phase 1 Negotiation Mode | Under Select Phase 1 Negotiation Mode, select the mode for authenticating ISAKMP SAs using Main Mode, Aggressive Mode, or Use Manual Key options. |
| |
| |
| |
When selected, this check box triggers an authentication method, which protects against repeat compromises of a shared secret key. | |
When selected, this check box sets a counter that determines whether or not a packet is unique to prevent data from being falsified. |
To specify authentication for phase 1 IKE
A new proposal appears called Proposal 1.
The Proposal 1 pane appears in the right pane.
In the right pane, under Authentication Method and Algorithms, in the Authentication Method list, Pre-Shared key appears. Because you have already specified a pre-shared key, you cannot make a selection here.
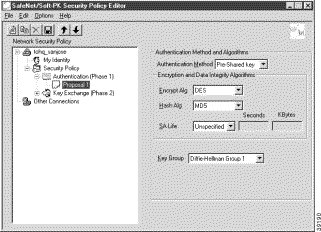
Step 2 In the right pane, under Authentication Method and Algorithms, select the following:
a. In the Encrypt Alg list, click DES.
b. In the Hash Alg list, click MD5.
c. In the SA Life list, click Unspecified.
d. In the Key Group list, click Diffie-Hellman Group 1.
Figure 5-9 shows how this is displayed on the Authentication (Phase 1)—Proposal 1 pane for pre-shared key. Table 5-5 describes the field descriptions for the Authentication (Phase 1)—Proposal 1 pane for pre-shared key.
| Field | Description | ||
|---|---|---|---|
Network Security Policy | Under Network Security Policy, the proposals that will be used to negotiate the authentication and encryption methods are displayed. | ||
|
| ||
Authentication Method and Algorithms | Under Authentication Method and Algorithms, define the authentication method used and authentication and encryption algoritms. | ||
Authentication Method | This list defines the authentication method being used, either Pre-Shared Key or RSA Signatures. The default is the method of authentication selected under My Identity. | ||
|
| ||
|
| ||
Encryption and Data Integrity Algorithms | Under Encryption and Data Integrity Algorithms, define the algorithms to be used during Phase 1 negotiation including Encrypt Alg, Hash Alg, SA Life, and Key Group. | ||
Encrypt Alg | This list allows you to specify encryption with DES or Triple DES options. | ||
|
| ||
|
| ||
Hash Alg | This list allows you to specify authentication with MD5 and SHA-1 options. | ||
|
| ||
SA Life | (Optional) This list allows you to specify the period for which the IKE SA is valid using Unspecified, Seconds, Kbytes, or Both options.
| ||
|
| ||
|
| ||
|
| ||
|
| ||
Key Group | This list allows you to specify the Diffie-Hellman key exchange using Diffie-Hellman Group 1 or Diffie-Hellman Group 2 options.
| ||
|
| ||
|
|
To specify authentication for phase 2 IKE
In the left pane, under Key Exchange (Phase 2), a new proposal appears called Proposal 1.
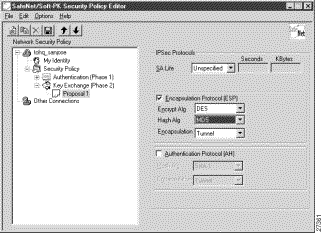
Step 2 In the right pane, under IPSec Protocols, select the following:
a. In the SA Life list, click Unspecified.
b. Select the Encapsulation Protocol (ESP) check box.
c. In the Encrypt Alg list, click DES.
d. In the Hash Alg list, click MD5.
e. In the Encapsulation list, click Tunnel.
Figure 5-10 shows how this is displayed on the Authentication (Phase 2)—Proposal 1 pane for pre-shared key. Table 5-6 describes the field descriptions for the Authentication (Phase 2)—Proposal 1 pane for pre-shared key.
| Field | Description | ||
|---|---|---|---|
Network Security Policy | Under Network Security Policy, the proposals that will be used to negotiate the authentication and encryption methods are displayed. | ||
|
| ||
IPSec Protocols | Under IPSec Protocols, define the algorithms to be used during Phase 2 key exchange, including SA Life, Encrypt Alg, Hash Alg, and Encapsulation options. | ||
SA Life | This list allows you to specify the period for which the IKE SA is valid using Unspecified, Seconds, Kbytes, or Both options.
| ||
|
| ||
|
| ||
|
| ||
|
| ||
Encapsulation Protocol | If selected, this check box indicates that encryption and authentication will be selected for this proposal. | ||
This list allows you to specify encryption with DES or Triple DES options. | |||
|
| ||
|
| ||
This list allows you to specify authentication with MD5 or SHA-1 options. | |||
|
| ||
|
| ||
Encapsulation | This list allows you to specify encapsulation method with Tunnel or Transport options. | ||
|
| ||
|
|
To save your policy
The Security Policy Editor dialog box appears. Before your policy is implemented, you must save your policy settings.
Step 2 Click OK.
Figure 5-11 shows how this is displayed in the Security Policy Editor dialog box.

To configure a pre-shared key or wildcard pre-shared key on the gateway, perform the following steps:
To configure the gateway, perform the following tasks, as described in Table 5-7:
| Command | Purpose |
|---|---|
router> enable
| To enter privileged EXEC mode, enter the enable user EXEC command. |
router# configure terminal
Enter configuration commands, one per line.
End with CNTL/Z.
| To enter global configuration mode, enter the configure privileged EXEC command. To configure the terminal attached at console port, enter the terminal keyword. |
router(config)# ip domain-name example.com
| To define a default domain name that the Cisco IOS software uses to complete unqualified host names, use the ip domain-name global configuration command. An unqualified host name is a host name without a dotted-decimal domain name. In this example, example.com is defined as the default domain name. |
router(config)# hostname hq_sanjose
| To specify or modify the host name for the network server, enter the hostname global configuration command. The host name is used in prompts and default configuration filenames. In this example, hq_sanjose is defined as the host name. The hq_sanjose host name replaces the default router host name. |
hq_sanjose(config)# ip name-server
192.168.1.1
| To specify the address of a name server to use for name and address resolution, enter the ip name-server global configuration command. In this example, the gateway is defined as the IP name server. The gateway's IP address is 192.168.1.1. |
To configure ISAKMP on the gateway, perform the following tasks, as described in Table 5-8:
| Command | Purpose |
|---|---|
hq_sanjose(config)# crypto isakmp policy 3
| To define an IKE policy, use the crypto isakmp policy global configuration command. This command invokes the ISAKMP policy configuration (config-isakmp) command mode. IKE policies define a set of parameters to be used during the IKE negotiation. In this example, the ISAKMP policy is assigned a priority of 3. |
hq_sanjose(config-isakmp)# encryption des
| (Optional) To specify the encryption algorithm, use the encryption (IKE policy) ISAKMP policy configuration command. The options for encryption are the des and 3des keywords. DES is configured by default for minimum security and fastest processing. |
hq_sanjose(config-isakmp)# hash sha
| (Optional) To specify the hash algorithm, use the hash (IKE policy) ISAKMP policy configuration command. IKE policies define a set of parameters to be used during IKE negotiation. The options for hashing are the sha and md5 keywords. SHA is configured by default for maximum authentication with slower processing than MD5. |
hq_sanjose(config-isakmp)# authentication
pre-share
| To specify the authentication method, use the authentication (IKE policy) ISAKMP policy configuration command. The options for authentication method are the rsa-sig, rsa-encr, and pre-share keywords. To specify pre-shared key as the authentication method, enter the pre-share keyword. |
hq_sanjose(config-isakmp)# group 1
| (Optional) To specify the Diffie-Hellman group identifier, use the group ISAKMP policy configuration command. The options for Diffie-Hellman group are the 1 and 2 keywords. Diffie-Hellman Group 1 is configured by default for minimum security with the fastest processing time. |
hq_sanjose(config-isakmp)# lifetime 86400
| (Optional) To specify the lifetime of an IKE SA before it expires, use the lifetime ISAKMP policy configuration command. The lifetime can be using an integer from 60 to 86,400 seconds. A day (86,400 seconds) is configured by default. |
hq_sanjose(config-isakmp)# exit
| To exit ISAKMP policy configuration (config-isakmp) command mode, enter the exit ISAKMP policy configuration command. |
hq_sanjose(config)# crypto isakmp key
cisco1234 address 10.1.2.1
or
hq_sanjose(config)# crypto isakmp key
cisco1234 address 0.0.0.0
| To configure a pre-shared authentication key, use the crypto isakmp key global configuration command. You must configure this key whenever you specify pre-shared key in an IKE policy. Use any combination of alphanumeric characters between 8 and 128 bytes. This pre-shared key must be identical at both peers. The VPN Client pre-shared key and IP address are specified as follows:
|
 |
Caution For security purposes, you must distribute the pre-shared key (pre-shared key or wildcard pre-shared key) to remote users through a secure out-of-band channel. For more details, see "Authentication and Encryption Features" in "Case Study for Layer 3 Authentication and Encryption." |
To configure IPSec on the gateway, perform the following tasks, as described in Table 5-9:
| Command | Purpose | ||
|---|---|---|---|
hq_sanjose(config)# crypto ipsec
transform-set vpn-transform esp-des
esp-md5-hmac
| To define a combination of security associations to occur during IPSec negotiations, enter the crypto ipsec transform-set global configuration command. This command invokes the crypto transform (cfg-crypto-trans) configuration mode. In this example, the transform set named vpn-transform is defined with two security algorithm keywords: esp-des and ah-md5-hmac. This is the recommended combination for minimum encryption and authentication.
| ||
hq_sanjose(cfg-crypto-trans)# mode tunnel
| (Optional) To specify encapsulation between the gateway and the VPN Client, enter the mode crypto transform configuration command. The mode command is only applicable to traffic whose source and destination addresses are the IPSec peer addresses; it is ignored for all other traffic. (All other traffic is in tunnel mode only.) The options for encapsulation are tunnel and transport keywords. Tunnel is configured by default for IPSec encapsulation. | ||
hq_sanjose(cfg-crypto-trans)# exit
| To exit crypto transform (cfg-crypto-trans) configuration mode, enter the exit crypto transform configuration command. |
To define a dynamic crypto map, perform the following tasks, as described in Table 5-10:
| Command | Purpose | ||
|---|---|---|---|
hq_sanjose(config)# crypto dynamic-map
vpn-dynamic 1
| To define a dynamic crypto map entry, use the crypto dynamic-map command. This command invokes the crypto map (config-crypto-map) configuration mode. The dynamic map entry will reference the static crypto map entry. In this example, the dynamic map name is vpn-dynamic, and the sequence number (or priority) is 1. | ||
hq_sanjose(config-crypto-map)# set
transform-set vpn-transform
| To specify which transform sets are allowed for the crypto map entry, enter the set transform-set crypto map configuration command. In this example, the transform set previously defined in Configuring IPSec, vpn-transform, is applied to the vpn-dynamic dynamic crypto map.
| ||
hq_sanjose(config-crypto-map)# set
security-association lifetime seconds 2700
| (Optional) If you want the security associations for this crypto map to be negotiated using shorter IPSec SA lifetimes than the globally specified lifetimes, specify a key lifetime for the crypto map entry. Specify the IPSec lifetimes using one of the following keywords: seconds or kilobytes. The crypto map's security associations are negotiated according to the global lifetimes. In this example, the SA lifetime is 2700 seconds. | ||
hq_sanjose(config-crypto-map)# exit
| To exit crypto map (config-crypto-map) configuration mode, enter the exit crypto map configuration command. |
To define a static crypto map, perform the following tasks, as described in Table 5-11:
| Command | Purpose | ||
hq_sanjose(config)# crypto map vpnclient 1
ipsec-isakmp vpn-dynamic
| To define a static crypto map and add a dynamic crypto map set to a static crypto map set, enter the crypto map global configuration command. In this example, the vpn-dynamic dynamic map (child) is applied to the vpnclient static crypto map (parent). | ||
hq_sanjose(config)# access-list 101 permit
ip 192.168.1.1 255.255.255.224 host
10.1.2.1
| (Optional) To permit all IP traffic between the host and the gateway when using static IP addressing on the VPN Client, use the extended version of the access-list global configuration command.
In this example, all IP traffic is permitted between the two IPSec peers. | ||
hq_sanjose(config)# interface ethernet0/0
| To configure an interface, enter the interface global configuration command. This command invokes the interface (config-if) configuration mode. | ||
hq_sanjose(config-if)# ip address 10.1.1.1
255.255.255.0
| To indicate an IP address to the interface, enter the ip address interface configuration command. In this example, 10.1.1.1 is specified as the IP address of the Ethernet 0/0 interface. | ||
hq_sanjose(config-if)# crypto map vpnclient
| To apply a previously defined crypto map set to an interface, enter the crypto map interface configuration command. In this example, crypto map vpnclient is applied to outbound packets from Ethernet interface 0/0. |
For more information on pre-shared key and wildcard pre-shared key, refer to the "Pre-Shared Keys" section or "Wildcard Pre-Shared Keys" section in "Case Study for Layer 3 Authentication and Encryption."
For more information on configuring Cisco IOS software commands, refer to the "Cisco IOS Software Documentation Set" section in the "Preface."
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
Posted: Sat Jul 13 18:01:42 PDT 2002
All contents are Copyright © 1992--2002 Cisco Systems, Inc. All rights reserved.
Important Notices and Privacy Statement.