|
|

This chapter describes how to configure IP addresses on multiple remote Cisco Secure VPN Clients (VPN Clients) using Internet Key Exchange Mode Configration (IKE Mode Configuration). With IKE Mode Configuration, you can set up Virtual Private Networks (VPNs) with dynamic IP addressing from a Cisco router (gateway) to multiple VPN Clients for scalable IP Security Protocol (IPSec) policy. You can use IKE mode configuration to replace static or dynamic IP address on VPN Clients. This chapter contains the following sections:
 |
Note Throughout this chapter, there are numerous configuration examples that include unusable IP addresses, passwords, and public key examples. Be sure to use your own IP addresses, passwords, and public keys when configuring your VPN Clients and gateway. |
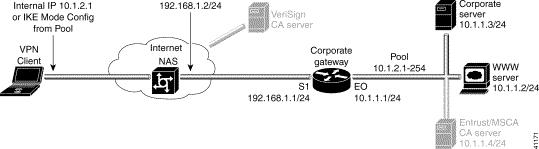
To configure IKE Mode Configuration on the VPN Client, you must specify an internal network address on the VPN Client. To do this, you must follow "Specifying an Internal Network Address on the VPN Client" in "Configuring Manual Configuration."
IKE Mode configuration is enabled by default on the VPN Client.
To configure the gateway, perform the following tasks:
To configure the gateway, perform the following tasks, as described in Table 4-1:
| Command | Purpose |
|---|---|
router> enable
| To enter privileged EXEC mode, enter the enable user EXEC command. |
router# configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
| To enter global configuration mode, enter the configure privileged EXEC command. To configure the terminal attached at console port, enter the terminal keyword. |
router(config)# ip domain-name example.com
| To define a default domain name that the Cisco IOS software uses to complete unqualified host names, use the ip domain-name global configuration command. An unqualified host name is a host name without a dotted-decimal domain name. In this example, example.com is defined as the default domain name. |
router(config)# hostname hq_sanjose
| To specify or modify the host name for the network server, enter the hostname global configuration command. The host name is used in prompts and default configuration filenames. In this example, hq_sanjose is defined as the host name. The hq_sanjose host name replaces the default router host name. |
To define IPSec transform set on the gateway, perform the following tasks, as described in Table 4-2:
| Command | Purpose | ||
|---|---|---|---|
| To define a combination of security associations to occur during IPSec negotiations and enter crypto transform configuration mode, enter the crypto ipsec transform-set global configuration command. In this example, the transform set named vpn-transform is defined with two security algorithms: esp-des and ah-md5-hmac.
| ||
| To specify IPSec encapsulation between the gateway and the VPN Client, enter the mode crypto transform configuration command. The mode command is only applicable to traffic whose source and destination addresses are the IPSec peer addresses; it is ignored for all other traffic. (All other traffic is in tunnel mode only.) In this example, tunnel mode is configured for vpn-transform for an IPSec encrypted tunnel. | ||
| To exit crypto map configuration mode, enter the exit crypto transform configuration command. |
To define a dynamic crypto map, perform the following tasks, as described in Table 4-3:
| Command | Purpose | ||
|---|---|---|---|
hq_sanjose(config)# crypto dynamic-map vpn-dynamic 1
| To define a dynamic crypto map entry and enter the crypto map configuration mode, enter the crypto dynamic-map command. In this example, the dynamic map name is vpn-dynamic, and the sequence number (or priority) is 1. | ||
hq_sanjose(config-crypto-map)# set transform-set vpn-transform
| To specify which transform sets are allowed for the crypto map entry, enter the set transform-set crypto map configuration command. In this example, the transform set previously defined in Defining an IPSec Transform Set, vpn-transform is applied to the vpn-dynamic dynamic crypto map.
| ||
hq_sanjose(config-crypto-map)# match address 101
| To specify an extended access list for a crypto map entry, enter the match address crypto map configuration command. This access list determines which traffic should be protected by IPSec and which traffic should not be protected by IPSec. If this is configured, the data flow identity proposed by the IPSec peer must fall within a permit statement for this crypto access list. If this is not configured, the router will accept any data flow identity proposed by the IPSec peer. However, if this is configured but the specified access list does not exist or is empty, the router will drop all packets. | ||
hq_sanjose(config-crypto-map)# exit
| To exit crypto map configuration mode, enter the exit crypto map configuration command. |
To define the VPN Clients' IP address pool, perform the following tasks, as described in Table 4-4:
| Command | Purpose | ||
|---|---|---|---|
hq_sanjose(config)# ip local pool vpn-pool 10.1.2.1-10.1.2.254
| To define a local IP address pool for VPN Clients, enter the ip local pool command. You can use existing local address pools to define a set of addresses. The IP address pool must be within the IP range of the corporate subnet. In this example, the pool name is vpn-pool. This IP address pool has a range from 10.1.2.1---10.1.2.254. The local address pool for VPN Clients is defined. | ||
hq_sanjose(config)# crypto isakmp client configuration address-pool local vpn-pool
| To configure the local IP address pool for VPN Clients to reference IKE on your router, use the crypto isakmp client configuration address-pool local global configuration command. In this example, the pool name is vpn-pool. The IP address pool for VPN Clients is set to reference IKE on your router. | ||
hq_sanjose(config)# crypto map vpnclient client configuration address initiate
| To configure IKE Mode Configuration on the static crypto map, use the crypto map client configuration address global configuration command. In this example, the crypto map is vpnclient. To indicate that IKE Mode Configuration is to be gateway-initiated, use the initiate keyword.
A crypto map is defined for gateway-initiated IKE Mode Configuration. | ||
hq_sanjose(config)# exit
| To exit global configuration mode, enter the exit global configuration command. |
To define a static crypto map, perform the following tasks, as described in Table 4-5:
| Command | Purpose | ||
|---|---|---|---|
hq_sanjose(config)# crypto map vpnclient 1 ipsec-isakmp vpn-dynamic
| To define a static crypto map and add a dynamic crypto map set to a static crypto map set, enter the crypto map global configuration command. In this example, the vpn-dynamic dynamic map (child) is applied to the vpnclient static crypto (parent) map. | ||
hq_sanjose(config)# access-list 101 permit ip 192.168.1.1 255.255.255.0 host 10.1.2.1
| (Optional) To permit all IP traffic between the host and the gateway when using static IP addressing on the VPN Client, use the extended version of the access-list global configuration command.
In this example, all IP traffic is permitted between the two IPSec peers. | ||
hq_sanjose(config)# interface ethernet0/0
| To configure an interface, enter the interface global configuration command. This command invokes the interface (config-if) configuration mode. | ||
hq_sanjose(config-if)# ip address 10.1.1.1 255.255.255.0
| To indicate an IP address to the interface, enter the ip address interface configuration command. In this example, 10.1.1.1 is specified as the IP address of the Ethernet 0/0 interface. | ||
hq_sanjose(config-if)# crypto map vpnclient
| To apply a previously defined crypto map set to an interface, enter the crypto map interface configuration command. In this example, crypto map vpnclient is applied to outbound packets from Ethernet interface 0/0. |
For more information on IKE Mode Configuration, refer to the "IKE Mode Configuration (Dynamic IP Addressing)" section in "Case Study for Layer 3 Authentication and Encryption."
For more information on configuring Cisco IOS software commands, refer to the "Cisco IOS Software Documentation Set" section in the "Preface."
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
Posted: Thu Jul 27 18:11:13 PDT 2000
Copyright 1989-2000©Cisco Systems Inc.