|
|

The Simple Network Management Protocol (SNMP) based on the use of PDU/IP allows the exchange of variables (identifier and value) between a manager and an agent. The PDUs (Protocol Data Units) are coded in ASN.1 (Abstract Syntax Notation One). The specifications for this protocol are essentially contained in RFC 1155 and RFC 1157.
The user has access to the services offered by one or more managers located on PCs or workstations.. The user can trigger actions and look up information. The user interface of the managers is specific to each manager.
The manager is in charge of presenting the actions or consultations proposed to the user. It generates the SNMP requests to the agents and interprets their responses. The interface between the manager and the agent complies with the SNMP protocol over PDU/IP.
The agent is in charge of replying to requests from managers. It collects the information managed by the equipment and performs the actions requested by the managers.
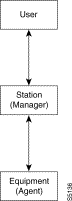 SNMP Protocol
SNMP Protocol
Each PDU (Protocol Data Unit) contains a character string, called a community string, used to check that the manager and the agent are authorized to dialog together. In general, most equipment units define two community strings, one for read access and one for read/write access. They can also define a list of IP addresses of managers authorized to dialog with them..
The variables implemented by an agent are described in the MIBs (Management Information Bases) according to the SMI (Structure for Management Information) description. The MIB is a standard implemented by most equipment units having an SNMP agent. The specifications for MIB are given in RFC 1213.
SMI classifies all variables in tree form and one need only give the list of node numbers to designate any variable unequivocally. Each equipment can defined, from the enterprise node, a sub-tree specific to it; one then speaks of a private MIB.
SNMP defines five types of PDU:
Get Request: Transmitted by the manager to the agent to obtain the values of designated variables.
Get Next Request: Transmitted by the manager to the agent to obtain the identifiers and the values of variables located "after" the designated variables (according to the numbering of tree nodes).
Set Request: Transmitted by the manager to the agent to modify the values of designated variables.
Get Response: Transmitted by the agent to the manager in response to a Get Request, a Get Next Request or a Set Request.
Trap: Transmitted by the agent, on its initiative, to inform the manager of a special event noted on the equipment; the generic-trap variable of this PDU takes on the following values:
In V12.2, the SNMP agent offers access to the groups defined in MIB (RFC 1213) as well as to part of the groups defined in the Cisco private MIB (see Appendix G of the Management Functions Manual).
The SNMP agent offers three community strings:
The SNMP agent replies, in principle, to any manager using a correct community string.
It is also possible to configure it (in C49 R0 P4) so that it responds only to managers whose IP addresses are listed in C49 R2.
An SNMP trap contains the IP address of the transmitting SNMP agent (not to be confused with the IP source address of the IP frame). In the case of an IP host, the agent uses the generally unique address of the host. In the case of an IP router, there are several addresses available to the agent.
The SNMP agent of the first module uses, as transmitting IP address, the IP address associated with the virtual port stipulated in C49 R1 P1 (the IP address is configured in C41 R2). The other two modules use the parameters C49 R1 P2 and C49 R1 P3 if they are present.
This list of managers receiving traps can be configured in C49 R2 and C49 R3. When this list, of up to three managers, is empty, no trap is generated.
Each manager is designated by its IP address (C49 R2). The SNMP agent sends the traps to each manager having a "Send trap" parameter equal to "yes " (C49 R3).
It is possible, for example, to sent traps to only one of the three managers and to reply to the requests from all three (see § 3.21.2.2. Manager control).
Standard traps (generic-trap = 0 to 5)
The traps Cold Start (generic-trap = 0), Link Down (generic-trap = 2), and Link Up (generic-trap = 3) are always transmitted provided at least one trap-recipient manager is stipulated in C49 R2 and C49 R3.
The traps Warm Start (generic-trap = 1) and Egp Neighbor Loss (generic-trap = 5) are not offered in V12.2.
The Authentication Failure trap (generic-trap = 4) is generated when the SNMP agent receives a request from an unauthorized manager or a request containing an incorrect community string.
12.2 FastPADmp Configuration Manual Addendum
Chapter 11 12.2 SNMP Agent 5 When incorrect requests are received periodically (for example, when a manager polls the agent every minute to follow traffic trends), the Authentication Failure traps, which are always generated, may flood the SNMP trap-recipient managers.
The generation of this trap may be disabled in C49 R1 P0 to overcome the problem.
It is also possible to perform this operation by means of the snmpEnableAuthenTraps variable of the SNMP group of MIB II.
Private traps (generic-trap = 6)
The equipment generates a certain number of events grouped in 26 families. Appendix A of the Management Functions Manual contains the complete list of events generated.
It is possible, by configuration, to request the transmission of the trap associated with each event. The selection of each event for which the equipment is to trigger the transmission of the corresponding trap is done in Class 5 (this class is also used to configure the transmission of alarm messages).
If an event was selected in Class 5, the corresponding private trap is transmitted when the equipment generates this event.
Appendix G of the Management Functions Manual describes the association of events with the six types of private traps.
As the SNMP protocol relies on PDU/IP, the equipment must be configured at least as IP host so that a manager can reach the SNMP agent. If necessary, refer to Chapter 3.20 for the detailed configuration of the LAN connection function.
Table 11-1 lists the indispensable parameters:
| SNMP agent accessible on LAN side | SNMP agent accessible on WAN side |
|---|---|
LAN line: C1 R1, C12 | WAN line: C1 R1, C12, ... |
| WAN switching, services, ... |
A local virtual port in C35 R0 | A local virtual port in C35 R0 |
VIP association: line in C35 R1 | C35 R1 empty |
C36 empty | A connection to the manager in C36 R0, C36 R2, C36 R3, C36 R4 |
Port not indispensable C17 R0 P0=no, C38 to C40 empty. | Port not indispensable C17 R0 P0=no, C38 to C40 empty. |
Routing of IP frames not indispensable C41 R0 P0 = no | Routing of IP frames not indispensable C41 R0 P0 = no |
IP address and parameters associated with the virtual port in C41 R1, C41 R2, C41 R3, C41 R4 | IP address and parameters associated with the virtual port in C41 R1, C41 R2, C41 R3, C41 R4 |
LAN encapsulation in C41 R6 | C41 R6 not necessary |
C42 empty | IP address associated with the remote router in C42 R0, C42 R1, C42 R2 |
ARP protocol sufficient: C43 empty | ARP protocol sufficient: C43 empty |
Passive RIP use: C44 empty | Passive RIP use: C44 empty |
EGP not indispensable C47 R0 P0=no C47 R1, C47 R2, C47 R3, C47 R4, C47 R5 empty | EGP not indispensable C47 R0 P0=no C47 R1, C47 R2, C47 R3, C47 R4, C47 R5 empty |
SNMP Class 49 to be completed | SNMP Class 49 to be completed |
Equipment whose SNMP agent can be reached over WAN lines.
Not dealt with here.
P0 91 FRL standard profile
P46 43 Subscriber number 43 (virtual line)
P0 1,2,1,0 Empty status, VP number 2 of remote type
P0 90002043 Aimed point
P0 2,0,0 First module VP
P0 1,3,0 Multiplexed type, datagram mode, without grouping
P0 1,10,10 Valid status, Inactivity timer, Call retransmission
P0 0 No IP routing
P1 0 Normal mode
P2 0 No ICMP redirect
P3 0 No routing source
P0 1,2,0 Valid status, remote VP, No Proxy ARP
P0 194,1,1,1 IP address of Remote interface
P0 255,255,255,0 Remote interface network mask
P0 1500 Remote interface MTU
P0 194,1,1,2 Next router interface IP address (enabling the manager to be reached)
P0 90002043 Aimed point of next router (enabling the manager to be reached)
P0 1 Valid status
P0 2 No passive RIP
P0 0 No active EGP
P0 Public Community string for read access (used by the manager)
P1 Private Community string for read and write access (used by the manager)
P2 Public Community string for traps
P0 0 No Authentication Failure trap
P1 2 IP address of remote VP in the traps
P4 1 Filtering of managers listed in C49R2
P0 195,1,1,1 IP address of a manager
P0 1,1 alid status, sending of traps to this manager
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
Posted: Thu Jan 25 13:58:56 PST 2001
All contents are Copyright © 1992--2001 Cisco Systems, Inc. All rights reserved.
Important Notices and Privacy Statement.