|
|

 |
Note The information in this chapter applies to both UNIX workstations (Maps and SNA View) and Windows NT systems (SNA View). |
This chapter provides information on preparing to install CiscoWorks Blue Maps and SNA View on UNIX workstations and SNA View on Windows NT systems.
This chapter includes the following main sections:
This section describes the hardware and software requirements to run CiscoWorks Blue SNA View on a Windows NT system.
 |
Note Hardware and software version information is subject to change, based on enhancements to the product. For the most current version information, refer to the Release Notes for CiscoWorks Blue SNA View available on Cisco Connection Online. For more information, see the Release Notes for CiscoWorks Blue Maps and SNA View Software Release 3.0. |
For information about installing CiscoWorks Blue SNA View on Windows NT, see "Installing CiscoWorks Blue SNA View on Windows NT."
CiscoWorks Blue SNA View runs on Windows NT systems with Service Pack 5.
To install CiscoWorks Blue SNA View, you must have local administrator authority on the machine you are installing the software.
Table 2-1 lists commands that you can enter to verify hardware and software requirements:
Verify
| On Windows NT
|
|---|---|
| |
| |
| |
| |
| |
| |
This section lists the workstation requirements and Cisco IOS software requirements.
CiscoWorks Blue Maps and SNA View run on the following systems:
 |
Note The network management systems listed here (NetView for AIX, HP OpenView, and SunNet Manager) are optional and are used for event notification, automatic discovery, and trap collection. |
All platforms require the following hardware and software:
To install CiscoWorks Blue SNA View, you must have root authority on the machine you are installing the software.
Table 2-2 lists commands that you can enter to verify hardware and software requirements on all platforms.
| Verify | On AIX | On HP-UX | On Solaris |
|---|---|---|---|
Hard disk space | df -k | bdf | df -k |
Operating system version | oslevel | uname -a | uname -a |
NMS version | lslpp -L nv6000.base.obj | /usr/sbin/swlist | grep "Network Node Manager" | pkginfo | grep SNM /opt/OV/bin/ovversion |
RAM size | lscfg | grep mem1 lsattr -E -l mem0 -F "description value"2 | /usr/sam/lbin/getmem | dmesg | grep mem
|
Swap space size | lsps -s | swapinfo | swap -s |
X Window System version | Ask your system administrator. |
| |
| 1On an IBM RISC System 6000 workstation. 2On a Power-PC workstation. |
Your workstation must meet the following software requirements to run CiscoWorks Blue SNA View:
 |
Note The LU 6.2 communications program is not available on Windows NT systems. |
The Solaris patches listed by version in this section are required for you to install Maps and SNA View. You can install these separately or as a jumbo patch from Sun Microsystems, Inc. To obtain the patches, contact your Sun Microsystems representative or download them from the Sun web site.
The following minimum patch levels are required on Solaris Version 2.5.1:
The following minimum patch level is required on Solaris Version 2.6:
 |
Note Hewlett Packard often obsoletes old patches and incorporates their functions in new patches with different numbers. In the following sections, we list both the original patch we require and the latest patch, that we are aware of, that contains the required functions. |
The following minimum patch levels are required on HP-UX Version 11.00:
The following patches are required on AIX Version 4.2:
The following patches are required on AIX Version 4.3:
During installation, you might be asked to provide information needed by the installation program, such as the locations of key programs or the identifications of ports to be used. You should collect the following information in advance to make the installation process easier.
UNIX Workstations Only
UNIX Workstations and Windows NT
For routers to be managed by CiscoWorks Blue Maps applications, all routers must be running a Cisco IOS release indicated below:
This section describes how to configure a router for use with CiscoWorks Blue Maps and SNA View. For detailed information about configuring the Cisco IOS software with the snmp-server command, see the Cisco IOS Configuration Fundamentals Command Reference.
Configure the Cisco IOS software in every managed router using the following command:
snmp-server community string ROWhere:
string is the community string (a password for access to SNMP) in this router.
RO specifies read-only access to SNMP in this router.
For the trap daemon (cwbtrapd) to perform optimally for RSRB, all RSRB-enabled routers must specify their addresses in the traps that they generate. Therefore, you must configure the Cisco IOS software in every RSRB-enabled router using the following command:
snmp-server trap-source interfaceWhere:
interface specifies the router interface (such as tokenring1) whose IP address is used as the local address for RSRB peering and is stamped on the traps that this router generates.
 |
Note The information in this section applies to Ciscoworks Blue only if you are running a UNIX workstation with an NMS during an installation. |
To use router-generated traps, all DLSw- and RSRB-enabled routers must specify the CiscoWorks Blue Maps network management host as the destination of DLSw and RSRB traps. Therefore, you must configure the Cisco IOS software in every DLSw- and RSRB-enabled router.
 |
Note The information in this section applies to Ciscoworks Blue only if you are running a UNIX workstation with an NMS during an installation. |
To configure a DLSw router, use the following command:
snmp-server host address string dlsw
Where:
address is the IP address of the network management host, such as 123.45.67.89.
string is the community string for access to SNMP in the network management host.
dlsw limits the traps sent to DLSw-related traps.
To enable the DLSw traps, use the following command:
snmp-server enable traps dlsw [circuit | tconn]Where:
circuit limits the traps to DLSw circuit-related traps.
tconn limits the traps to DLSw peer-related traps.
To configure an RSRB router for traps, use the following command:
snmp-server host address string rsrbWhere:
address is the IP address of the management host, such as 123.45.67.89.
string is the read community string for access to SNMP in the management host.
rsrb sends only RSRB-related traps to address.
 |
Note The information in this section applies to UNIX workstations only. |
If you install the CiscoWorks Blue applications on an HP-UX system, you might need to change the following kernel parameters. Use the HP-UX sam command to change the kernel parameters if they are lower than the following settings:
See your HP-UX publications for instructions on changing these values.
These values are the minimum values needed for Maps and SNA View. If you have other resource-intensive applications on this workstation, you might need to increase these values. If you are unable to start the Process Manager, if you get "out of space" errors while trying to start other CiscoWorks Blue processes, or if you get Java exceptions with the message "out of memory," try increasing the swap space.
 |
Note The information in this section applies to UNIX workstations only. |
Before you install CiscoWorks Blue Maps or SNA View on UNIX workstations, you must have root user authority. The user named root can perform functions restricted from normal users. You can log in to your system as the root user, or you can become the root user by using the su command. You will then be asked to enter the root user's password.
 |
Caution If you are a relatively inexperienced UNIX user, limit your activities as the root user to the tasks described in this publication. As the root user, you can adversely affect your operating environment if you are unaware of the effects of the commands that you use. |
If you are not logged in, you can log in as the root user by responding to the login prompt with the username root.
login: root
Password: rootpassword
If you are already logged in, but not as the root user, use the su command to become the root user:
% suPassword: rootpassword
 |
Note The information in this section applies to UNIX workstations only. |
This section describes how you can specify selected DLSw routers as key devices to limit some of the SNMP traffic on your network.
A key device is a router that you designate as "key." This means that the router is in close proximity to the mainframe, or it supports an important set of network resources. You can use key routers to reduce the SNMP traffic needed to manage your network, to minimize the number of devices shown on a DLSw map, and for circuit polling, which is needed for SNA correlation. You can also specify a faster polling rate for key devices.
You can limit some of the SNMP traffic involved in discovering and polling routers by selecting only key routers that are in close proximity to the mainframe and that are responsible for handling traffic between the mainframe and other remote routers and devices in your network. If a router is marked as a key device, the poller daemon polls this router for all of the circuits in addition to the peer connections. If a router is not marked as a key device, the poller daemon polls the router for the peer connections.
A DLSw circuit is represented in both of the DLSw peers through which an SNA session passes. Because part of the circuit information is duplicated in each peer router, the DLSw Maps application can find the SNA path used, even if it polls only one of the routers (a key router, for example). Polling one peer reduces the polling interval and reduces network traffic.
If you designate a set of routers as key devices, you can later display a view of just the key devices. This view is called the key devices view of the network and is described in the CiscoWorks Blue Maps and SNA View User Guide.
The key devices view of the network displays just the DLSw-enabled peer routers that are designated as key devices. The key devices view represents all the peers of a key router with one icon, which is called an aggregated peer router icon. The connection between each key router and its aggregated peer router icon is shown as a single connection called an aggregated peer connection.
To see how using key devices removes the clutter from your maps, compare the key devices view with the global view shown in the CiscoWorks Blue Maps and SNA View User Guide.
The DLSw application lets you define two different polling intervals:
You can specify how the DLSw application polls routers for peer connection information and for circuit information. You can select from the following polling methods:
If you make no changes, the DLSw polling daemon uses all three polling methods: It polls key routers and non-key routers for peer connection information, and it polls key routers for circuit information. You can change these selections using the polling values in the cwbinit file.
You can also use the cwbinit file to configure multiple polling threads. By default, Key-----Peer polling uses five threads so that it can poll more key routers concurrently, while Non--Key--Peer polling uses only one thread by default. You can change these settings in the cwbinit file.
This section gives you guidance in choosing which routers to designate as key devices. Usually, you want to choose key routers for the following reasons:
The following two network examples show how to choose key routers.
Figure 2-1 shows a network in which the two DLSw-enabled data center routers handle all the peer connections between the mainframe and the remote branch routers. In this case, you should designate these two data center routers as key devices.
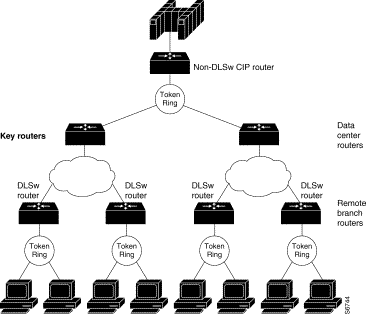
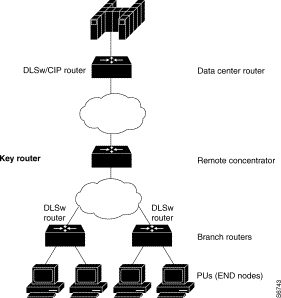
Figure 2-2 shows a network in which one DLSw-enabled concentrator router handles all the connections between the mainframe and the remote branch routers. In this case, you should designate the concentrator router as a key device.
Initially, no routers are marked as key devices when they are added to the database. You must take some action to mark a router as a key device. There are several ways that you can define a router as a key device.
For each router that you include in the seed file, you can use the key parameter to designate that router as a key device. If the key parameter is not used, the router is not a key device in the seed file. To see which routers are key devices, select Edit > Key Device(s) from the menu bar on the Motif application on UNIX workstations. In the list of routers, the key devices are highlighted.
Once you mark a router as a key device, removing the key parameter in the seed file will not change the device's status as a key device. To change the router's status as a key device, select Edit > Key Device(s) from the menu bar on the Motif application on UNIX workstations, deselect the router in the router list, and click Apply.
Step 2 Select those routers that you want to add to the list of key devices. Each router that you select is highlighted.
Step 3 Deselect those routers that you do not want to be key devices. The routers that you select here will not be highlighted.
Step 4 Click Apply to apply your changes in the database.
Step 5 Click Close to close the window.
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
Posted: Mon Sep 4 10:53:00 PDT 2000
Copyright 1989-2000©Cisco Systems Inc.