|
|

This chapter describes how to initially configure the Cisco DSLAMs, and includes these sections:
The Cisco DSLAM default configuration is suitable for operation with most networks. By using network management applications and the text-based command-line interface (CLI), you can configure and customize all aspects of DSLAM operation to suit your needs.
The Cisco DSLAM ships with the ATM address autoconfigured, allowing the DSLAM to accomplish the following tasks:
The ILMI and PNNI protocols allow the DSLAM to be entirely self-configured when you use these protocols with an IP address autoconfiguration mechanism such as BOOTP.
You must assign an IP address to allow up to eight simultaneous Telnet sessions to connect to the DSLAM or to use the Simple Network Management Protocol (SNMP) system for the DSLAM. The Ethernet IP address is assigned either manually or by a BOOTP server. See the "Configuring IP Interface Parameters" section.
You can use either of two methods for configuring a DSLAM (see Figure 3-1):
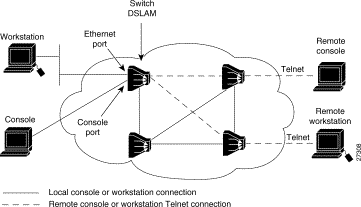
The DSLAM contains an NI-2 card and up to 32 line (modem) cards depending on the DSLAM. The slot configurations on the different DSLAMs are as follows:
Table 3-1 lists the NI-2 cards that can be installed in each of the DSLAM chassis, as well as the associated product numbers.
DS3+T1/E1 IMA1 NI-2-DS3-T1E1= Yes No Yes2 Yes3 DS3/2DS3 NI-2-DS3-DS3= No Yes Yes OC-3c/OC-3c SMF6 NI-2-155SM-155SM= Yes Yes Yes Yes7 OC-3c/OC-3c MMF8 NI-2-155MM-155MM= Yes Yes Yes Yes7 OC-3c/2DS3 SMF NI-2-155SM-DS3= No No Yes No OC-3c/2DS3 MMF NI-2-155MM-DS3= No No Yes No
Table 3-1: NI-2 Card and Chassis Compatibility
NI-2 Card
Product Number
Cisco 6015
Cisco 6100/6130
Cisco 6160
Cisco 6260
Line cards are assigned ports 1 to 4 or 1 to 8 in consecutive slots. Table 3-2 lists NI-2 port assignments. See the Hardware Installation Guide for your specific DSLAM system for more detailed information about possible subtending topologies.
| Port Type | OC3xOC3 | OC3x2DS3 | DS3x2DS3 | DS3xE1/T1 | Function |
|---|---|---|---|---|---|
Switch, Ethernet | eth 0/0 | eth 0/0 | eth 0/0 | eth 0/0 | The ATM switch or Ethernet CPU port (internal). |
Trunk | atm 0/1 | atm 0/1 | atm 0/1 | atm 0/11 | The trunk port connects to the network, either directly or through a subtended port in another DSLAM. |
Subtend 1 | atm 0/2 | atm 0/2 | atm 0/2 | — | A subtended port connects a second DSLAM to the network through a primary DSLAM. See the Hardware Installation Guide for your specific DSLAM. |
Subtend 2 | — | atm 0/3 | atm 0/3 | — | The DS3 configuration has a second subtended port. |
— | — | — | atm 0/2 through atm 0/9 | The DS3+T1/E1 IMA NI-2 card allows you to configure any WAN interface (the DS3, any T1 link, any E1 link, or any IMA group) as the trunk. | |
— | — | — | atm0/ima0 through atm0/ima3 | The eight links on the DS3+T1/E1 IMA NI-2 can be independent ATM links or can be configured into one or more IMA groups. |
| 1E1 does not have an atm 0/1 trunk. |
Obtain this information before you configure your DSLAM:
When you first power on your console and DSLAM, a screen similar to the following example appears:
Restricted Rights Legend
Use, duplication, or disclosure by the Government is
subject to restrictions as set forth in subparagraph
(c) of the Commercial Computer Software - Restricted
Rights clause at FAR sec. 52.227-19 and subparagraph
(c) (1) (ii) of the Rights in Technical Data and Computer
Software clause at DFARS sec. 252.227-7013.
Cisco Systems, Inc.
170 West Tasman Drive
San Jose, California 95134-1706
The script then displays the banner information, including the software version, followed by the installed hardware configuration.
cisco 6015 (NI2) processor with 60416K/5120K bytes of memory.
RC64475 CPU at 100Mhz, Implementation XX, Rev X.X
Bridging software.
1 Ethernet/IEEE 802.3 interface(s)
14 ATM network interface(s)
522232 bytes of non-volatile configuration memory.
4096K bytes of Boot Flash (Sector size 128K).
16384K bytes of Flash internal SIMM (Sector size 256K).
BOOTP automatically assigns an Ethernet IP address by adding the MAC and IP addresses of the Ethernet port to the BOOTP server configuration file. When the DSLAM boots, it automatically retrieves the IP address from the BOOTP server.
The DSLAM performs a BOOTP request only if the current IP address is set to 0.0.0.0. (This is the default for a new DSLAM or a DSLAM that has had its configuration file cleared using the erase startup-config command.)
To allow the DSLAM to retrieve its IP address from a BOOTP server you must first determine the MAC address of the DSLAM and then add that MAC address to the BOOTP configuration file on the BOOTP server.
Complete the following tasks to create a BOOTP server configuration file:
Step 1 Install the BOOTP server code on the workstation, if it is not already installed.
Step 2 Determine the MAC address from the label on the chassis.
Step 3 Add an entry in the BOOTP configuration file (usually /usr/etc/bootptab) for each DSLAM. Press Enter after each entry to create a blank line between each entry. See the sample BOOTP configuration file that follows this step list.
Step 4 Restart the DSLAM to automatically request the IP address from the BOOTP server.
This example of a BOOTP configuration file shows the newly added DSLAM entry:
# /etc/bootptab: database for bootp server (/etc/bootpd)
#
# Blank lines and lines beginning with '#' are ignored.
#
# Legend:
#
# first field -- hostname
# (may be full domain name)
#
# hd -- home directory
# bf -- bootfile
# cs -- cookie servers
# ds -- domain name servers
# gw -- gateways
# ha -- hardware address
# ht -- hardware type
# im -- impress servers
# ip -- host IP address
# lg -- log servers
# lp -- LPR servers
# ns -- IEN-116 name servers
# rl -- resource location protocol servers
# sm -- subnet mask
# tc -- template host (points to similar host entry)
# to -- time offset (seconds)
# ts -- time servers
<display truncated>
#########################################################################
# Start of individual host entries
#########################################################################
Switch: tc=netcisco0: ha=0000.0ca7.ce00: ip=192.31.7.97:
dross: tc=netcisco0: ha=00000c000139: ip=192.31.7.26:
<information deleted>
In a subtended network configuration, the head node acts as the host node connecting all the nodes to the network. The head node at the top of the subtend tree—that is, the node that is connected to the trunk—must have the subtend ID 0. (Subtend ID 0 is the default.)
You identify the node to the network with the subtend-id command. You must assign a unique subtend ID to each node in a subtend tree so that all subtended nodes have fair access to the trunk port of the head node.
To set the subtend node identifier, use the following command:
| Command | Task |
|---|---|
| Identify node# as the subtend hostnode. |
In this example, the DSL subtend node identifier is set to node 12:
DSLAM# configure terminal
DSLAM(config)# subtend-id 12
The DSLAM is autoconfigured with an ATM address that uses a hierarchical addressing model similar to the OSI Network Service Access Point (NSAP) addresses. PNNI uses this hierarchy to construct ATM peer groups. ILMI uses the first 13 bytes of this address as the switch prefix that it registers with end systems.
 |
Note If you manually change an ATM address, you must maintain the uniqueness of the address across the network. |
This section describes the ATM addressing scheme and tells you how to accomplish the following tasks:
This section describes the default addressing scheme and the features and implications of using this scheme.
During the initial startup, the DSLAM generates an ATM address using the defaults shown in Figure 3-2.
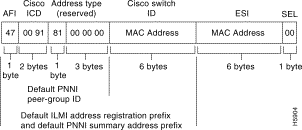
The default addressing scheme includes:
If you use the default address format, the following features and implications apply:
You can configure a new ATM address that replaces the previous ATM address when running IISP software only, or that replaces the previous ATM address and generates a new PNNI node ID and peer group ID as follows:
You can configure multiple addresses for a single switch and use this configuration during ATM address migration. ILMI registers end systems with multiple prefixes during this period until you remove an old address. PNNI automatically summarizes all the switch prefixes in its reachable address advertisement.
For operation with ATM addresses other than the autoconfigured ATM address, use the atm address command to manually assign a 20-byte ATM address to the switch. The atm address command address_template variable can be a full 20-byte address or a 13-byte prefix followed by ellipses (...). Entering the ellipses automatically adds one of the 6-byte switch MAC addresses in the ESI portion and 0 in the selector portion of the address.
 |
Caution ATM addressing can lead to conflicts if you do not configure it correctly. For example, when configuring a new ATM address, you must remove the old one from the configuration. |
When the switch initially powers on without previous configuration data, the ATM interfaces configure automatically on the physical ports. The DSLAM uses ILMI and the physical card type to automatically derive the following information:
You can accept the default ATM interface configuration or overwrite the default interface configuration using the CLI commands (see the ATM Switch Router Software Configuration Guide, Chapter 5, Configuring ATM Network Interfaces ).
This section describes how to modify an ATM interface from the default configuration listed in "Configuring In-Band Management." You can accept the ATM interface configuration or overwrite the default interface configuration using the CLI commands, which are described in ATM Switch Router Software Configuration Guide, Chapter 6, Configuring Virtual Connections .
This example shows how to modify an OC-3 interface from the default settings to:
To change the configuration of an ATM interface, follow these steps:
| Command | Task | |
|---|---|---|
Step 1 | DSLAM# configure terminal
| Enter global configuration mode. |
Step 2 | DSLAM(config)# interface atm slot/port
| Select the physical interface to be configured and enter interface configuration mode. |
Step 3 | DSLAM(config-if)# no scrambling
cell-payload
| Disable cell-payload scrambling. |
Step 4 | DSLAM(config-if)# no scrambling
sts-stream
| Disable STS-stream scrambling. |
Step 5 | DSLAM(config-if)# sonet {stm-1 |
sts-3c}
| Configure SONET mode as SDH/STM-1. |
Step 6 | DSLAM(config-if)# end
| Return to privileged EXEC mode. |
Step 7 | DSLAM#
| — |
This example shows how to disable cell-payload scrambling and STS-stream scrambling and changes the SONET mode of operation to Synchronous Digital Hierarchy/Synchronous Transfer Module 1 (SDH/STM-1) of OC-3 physical interface 0/0:
DSLAM(config)# interface atm 0/1
DSLAM(config-if)# no scrambling cell-payload
DSLAM(config-if)# no scrambling sts-stream
DSLAM(config-if)# sonet stm-1
DSLAM(config-if)# exit
DSLAM(config)#
To display the physical interface configuration, use these privileged EXEC commands:
| Command | Task |
|---|---|
DSLAM# show interfaces atm slot/port | Show the physical layer configuration. |
DSLAM# show running-config | Show the physical layer configuration. |
In this example, the OC-3 physical interface configuration is displayed after you modify the defaults:
DSLAM# show interfaces atm 0/1
ATM0/1 is up, line protocol is up
Hardware is suni_dual
MTU 4470 bytes, sub MTU 4470, BW 155520 Kbit, DLY 100 usec,
reliability 250/255, txload 1/255, rxload 1/255
Encapsulation ATM, loopback not set
Last input 00:00:00, output 00:00:00, output hang never
Last clearing of "show interface" counters 3w1d
Queueing strategy: fifo
Output queue 0/40, 0 drops; input queue 0/75, 0 drops
5 minute input rate 0 bits/sec, 0 packets/sec
5 minute output rate 0 bits/sec, 0 packets/sec
435 packets input, 23055 bytes, 0 no buffer
Received 0 broadcasts, 0 runts, 0 giants, 0 throttles
4220 input errors, 4355 CRC, 0 frame, 0 overrun, 0 ignored, 0 abort
374 packets output, 19822 bytes, 0 underruns
0 output errors, 0 collisions, 0 interface resets
0 output buffer failures, 0 output buffers swapped out
In this example, the OC-3 physical layer configuration is displayed after you modify the defaults:
DSLAM# show running-config
Building configuration...
Current configuration : 3080 bytes
!
version 12.2
no service pad
service timestamps debug uptime
service timestamps log uptime
no service password-encryption
!
hostname ra6260_3
!
boot system tftp://64.101.176.211/test_image
slot 1 ATUC-4FLEXIDMT
slot 2 STUC-4-2B1Q-DIR-1
slot 3 ATUC-4FLEXICAP
slot 4 ATUC-4FLEXIDMT
slot 5 ATUC-1-DMT8
slot 6 ATUC-1-4DMT
slot 10 NI-2-155SM-155SM
slot 18 ATUC-1-4DMT
no logging console
enable password test
!
!
dsl-profile default
!
network-clock-select 1 ATM0/1
redundancy
ip subnet-zero
no ip domain-lookup
!
!
no atm oam intercept end-to-end
atm address 47.0091.8100.0000.0004.6dce.7401.0004.6dce.7401.00
atm router pnni
no aesa embedded-number left-justified
node 1 level 56 lowest
redistribute atm-static
!
!
!
!
interface ATM0/0
no ip address
atm maxvp-number 0
atm maxvc-number 4096
!
interface Ethernet0/0
ip address 10.91.209.71 255.255.255.0
!
interface ATM0/1
no ip address
sonet stm-1
no scrambling sts-stream
no scrambling cell-payload
no atm ilmi-keepalive
!
interface ATM0/2
no ip address
no atm ilmi-keepalive
!
interface ATM1/1
no ip address
no atm ilmi-keepalive
!
interface ATM1/2
no ip address
no atm ilmi-keepalive!
!
ip classless
ip route 0.0.0.0 0.0.0.0 10.91.209.1
no ip http server
ip pim bidir-enable
!
!
!
line con 0
exec-timeout 0 0
line aux 0
line vty 0 4
exec-timeout 0 0
password test
login
!
end
This section describes how to configure IP addresses on the DSLAM processor interfaces. You configure each IP address for one of the following types of connections:
 |
Note These IP connections are used only for network management. |
To configure the DSLAM to communicate using the Ethernet interface, provide the IP address and subnet mask bits for the interface as described in this section.
This section provides a summary of IP addressing concepts for those who are familiar with IP addressing.
Internet addresses are 32-bit values assigned to hosts that use the IP protocols. These addresses are in dotted decimal format (four decimal numbers separated by periods), such as 192.17.5.100. Each number is an 8-bit value between 0 and 255.
IP addresses are divided into three classes. These classes differ in the number of bits allocated to the network and host portions of the address:
The default IP address is none.
Enter your Internet address in dotted decimal format for each interface you plan to configure.
Subnetting is an extension of the Internet addressing scheme that allows multiple physical networks to exist within a single Class A, B, or C network. The subnet mask determines whether subnetting is in effect on a network. The usual practice is to use a few of the far-left bits in the host portion of the network address to assign a subnet field.
Internet addressing conventions allow a total of 24 host bits for Class A addresses, 16 host bits for Class B addresses, and 8 host bits for Class C addresses. When you are further subdividing your network (that is, subnetting your network), the number of host addressing bits is divided between subnetting bits and actual host address bits. You must specify a minimum of two host address bits, or the subnetwork is not populated by hosts.
 |
Note Because all zeros in the host field specifies the entire network, subnetting with subnet address 0 is illegal and is strongly discouraged. |
Table 3-3 provides a summary of subnetting parameters.
| First Class | First Byte | Network Bits | Host Bits | |
|---|---|---|---|---|
| Max Subnet Bits | Min Address Bits | |||
A | 1 to 126 | 8 | 22 | 2 |
B | 128 to 191 | 16 | 14 | 2 |
You define subnet mask bits as a decimal number between:
 |
Note Do not specify 1 as the number of bits for the subnet field. That specification is reserved by Internet conventions. |
To configure the IP address, perform the following steps, beginning in global configuration mode:
| Command | Task | |
|---|---|---|
Step 1 | DSLAM(config) interface ethernet slot/port | Select the interface to be configured. |
Step 2 | DSLAM(config) ip address A.B.C.D sub_net_A.B.C.D | Configure the IP and subnetwork address. |
This example shows how to configure the Ethernet CPU interface 0/0 with IP address 172.20.40.93 and subnetwork mask 255.255.255.0, and displays the interface information:
DSLAM# configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
DSLAM(config)# interface ethernet 0/0
DSLAM(config-if)# ip address 172.20.40.93 255.255.255.0
DSLAM(config-if)# end
DSLAM# show interface ethernet 0/0
Ethernet0/0 is up, line protocol is up
Hardware is AmdP2, address is 0001.64ff.a97f (bia 0001.64ff.a97f)
Internet address is 172.21.186.145/24
MTU 1500 bytes, BW 10000 Kbit, DLY 1000 usec,
reliability 255/255, txload 1/255, rxload 1/255
Encapsulation ARPA, loopback not set
Keepalive set (10 sec)
ARP type: ARPA, ARP Timeout 04:00:00
Last input 00:00:00, output 00:00:00, output hang never
Last clearing of "show interface" counters never
Input queue: 0/75/0/0 (size/max/drops/flushes); Total output drops: 0
Queueing strategy: fifo
Output queue :0/40 (size/max)
5 minute input rate 4000 bits/sec, 5 packets/sec
5 minute output rate 2000 bits/sec, 3 packets/sec
906236 packets input, 202482126 bytes, 0 no buffer
Received 889038 broadcasts, 0 runts, 0 giants, 0 throttles
0 input errors, 0 CRC, 0 frame, 0 overrun, 0 ignored
0 input packets with dribble condition detected
163965 packets output, 21172110 bytes, 0 underruns
0 output errors, 9 collisions, 1 interface resets
0 babbles, 0 late collision, 33 deferred
0 lost carrier, 0 no carrier
0 output buffer failures, 0 output buffers swapped out
After you configure the IP addresses for the Ethernet interface, test for connectivity between the DSLAM and a host. The host can reside anywhere in your network. To test for Ethernet connectivity, use this command in EXEC mode:
| Command | Task |
|---|---|
DSLAM# ping ip ip_address | Test the configuration using the ping command. The ping command sends an echo request to the host specified in the command line. |
For example, to test Ethernet connectivity from the DSLAM to a workstation with an IP address of 172.20.40.201, enter the command ping ip 172.20.40.201. If the DSLAM receives a response, this message appears:
DSLAM# ping ip 172.20.40.201
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.20.40.201, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/202/1000 ms
This section describes how to configure network clocking for the DSLAM. Each port has a transmit clock and derives its receive clock from the receive data. You can configure transmit clocking for each port in one of these ways:
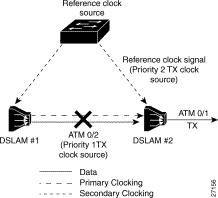
The DSLAM receives derived clocking, along with data, from a specified interface. For example, in Figure 3-3, the DSLAM extracts transmit clocking from the data received at ATM 0/1 and distributes it as the transmit clock to the rest of the DSLAM. ATM 0/2 then uses network-derived transmit clocking received from ATM 0/1.
Because the port providing the network clock source could fail, Cisco IOS software provides the ability to configure additional interfaces as clock sources with priorities 1 to 4.
If the network clock source interface stops responding, the software switches to the next highest-configured priority network clock source. For example, Figure 3-4 shows:
 |
Note By default, the network clock is nonrevertive. Nonrevertive means that once a network clock source fails and the DSLAM switches to the clock source with the next highest priority, manual intervention is required to force the DSLAM to switch back to a higher-priority clock source. The algorithm to switch to the highest priority best clock only runs if you configure the network-clock-select command as revertive. |
These sections describe network clocking:
To configure the network clocking priorities and sources, use the following commands in global configuration mode:
This example sets up the DSLAM building-integrated time source (BITS) interface as the highest-priority clock source, then configures the BITS interface for T1 at 0.6 dB (0 to 133 feet, or 0 to 40.5 meters).
DSLAM# configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
DSLAM(config)# network-clock-select 1 BITS
DSLAM(config)# network-clock-select BITS T1 0.6db
This example configures ATM 0/1, the trunk, as the second-highest priority timing source.
DSLAM# configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
DSLAM(config)# network-clock-select 2 atm 0/1
This example configures the DSLAM system clock as the third-highest priority timing source.
DSLAM# configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
DSLAM(config)# network-clock-select 3 system
This example shows how to configure the network clock to revert back to the highest priority clock source after a failure:
DSLAM(config)# network-clock-select revertive
DSLAM(config)#
To configure the location from which an interface receives its transmit clocking, perform the following steps, beginning in global configuration mode:
| Command | Task | |
|---|---|---|
Step 1 | DSLAM(config)# interface atm slot/port
| Select the interface to be configured. |
Step 2 | DSLAM(config-if)# clock source {loop-timed | network-derived}
| Configure the interface network clocksource. |
 |
Note When an interface has its clock source set to Network-Derived, the interface uses the highest-priority valid clock source available (assuming that the network clock source is configured to be revertive). |
This example configures ATM 0/1 to receive its transmit clocking from a network-derived source:
DSLAM(config)# interface atm 0/1
DSLAM(config-if)# clock source network-derived
DSLAM(config-if)#
This example displays the network clocking configuration shown in Figure 3-4:
DSLAM# show network-clocks
PLL failed: 58886; PLL Passed: 1082982
FAIL: 0; NCO: F984; REF: F982; ERR: 2; ERR_D: 0; MAG: -1;
clock configuration is NON-Revertive
Priority 1 clock source: BITS clock
Priority 2 clock source: No clock
Priority 3 clock source: No clock
Priority 4 clock source: No clock
Priority 5 clock source: System clock
Current clock source:System clock, priority:5
Nettime Config Register Contents:
NDIV:FF SRC:2, SLOCK:0, TLOCK:0, NFAIL:0, E1:0, NSEL:0
Trunk LED Register CLK_SEL:3
BITS Register Contents:
CR1: CB, CR2: 0, CR3: 0, ICR: 0, TSR: C1, PSR: 31, ESR: 77, CR4: 0
BITS Source configured as: T1 Short Haul, 0-133ft/0.6db pulse, 100 ohm cable, 1n
This example displays the clock source configuration of ATM 0/2:
DSLAM# show running-config interface atm 0/2
Building configuration...
Current configuration : 62 bytes
!
interface ATM0/2
no keepalive
atm manual-well-known-vc
atm access-group tod1 in
atm pvc 0 35 rx-cttr 3 tx-cttr 3 interface ATM0/2 0 any-vci encap qsaal
atm route-optimization soft-vc interval 360 time-of-day 18:0 5:0
clock-source network-derived
!
Any module in a DSLAM chassis capable of receiving and distributing a network timing signal can propagate that signal to any similarly capable module in the chassis. These modules are capable of receiving and distributing a primary reference source (PRS) for the clock:
 |
Note A trunk port can propagate a clocking signal in either direction. |
If you issue the network-clock-select command with the appropriate parameters, you can define a particular port in a DSLAM chassis (subject to the above limitations) to serve as the source of a PRS for the entire chassis or for other devices in the networking environment. This command is described in the "Configuring Network Clock Priorities and Sources" section.
You can also use the network-clock-select command to designate a particular port in a DSLAM chassis to serve as a master clock source for distributing a single clocking signal throughout the chassis or to other network devices. You can distribute this reference signal in any location the network needs to globally synchronize the flow of constant bit rate (CBR) data.
For network routing, the default software image for the DSLAM contains the PNNI routing protocol. The PNNI protocol provides the route dissemination mechanism for complete plug-and-play capability. This section describes modifications you can make to the default PNNI or Interim-Interswitch Signaling Protocol (IISP) routing configurations.
Use the atm route command to configure a static route. Static route configuration allows ATM call setup requests to be forwarded on a specific interface if the addresses match a configured address prefix.
 |
Note An interface must be UNI or IISP if it is configured with a static route. Static routes configured as PNNI interfaces default as down. |
This example shows how to use the atm route command to configure the 13-byte peer group prefix as 47.0091.8100.567.0000.0ca7.ce01 at ATM 0/1:
DSLAM(config)# atm route 47.0091.8100.567.0000.0ca7.ce01 atm 0/1
DSLAM(config)#
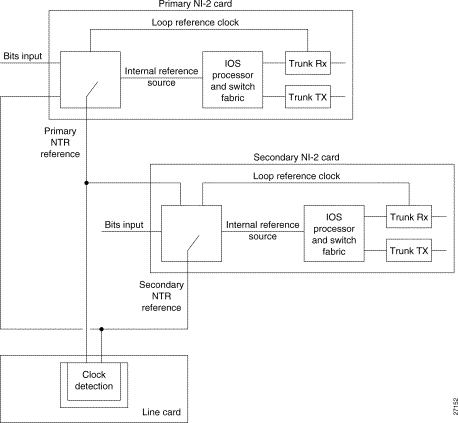
This section describes how to configure redundancy for the NI-2 card and APS link and includes the following information:
The NI-2 Card redundancy feature provides redundancy on the Cisco 6130, Cisco 6160, and Cisco 6260 DSLAM systems. This redundancy feature has two main components.
On a system with two NI-2 cards of the same interface types (trunk and subtend), the NI-2 cold redundancy feature allows a standby NI-2 card to assume system operations if the active NI-2 card completely fails. The NI-2 card in slot 10 is called the primary card and the card in slot 11 is called the secondary card. Either card can be active or standby.
The standby NI-2 begins the boot process but does not process its configuration. While the standby unit is monitoring the state of the active unit, the active unit synchronizes configuration changes with the standby unit if it is configured to do so. This allows the standby unit to become active with the most recent configuration possible following a switchover. Configuration information could be lost during the switchover if configuration synchronization is disabled.
The switchover from one NI-2 to the other NI-2 does not cause a reset of the line cards. The active unit communicates line card information to the standby unit to decrease switchover time. When the switchover is complete, the object database on the newly active unit may not match the objects in the system, but this situation will correct itself during normal operation as the active unit discovers the new cards or discovers that cards have been removed.
SONET APS provides recovery from a cut fiber or the failure of an optical transmitter or receiver for OC-3 interfaces on an NI-2 card. APS redundancy is available on OC-3c/2DS3 NI-2 card trunk interfaces and OC-3c/OC-3c NI-2 card trunk and subtend interfaces. The active interface switches over when a SONET failure condition (loss of signal or loss of frame) is detected.
When both primary and secondary fiber connections are cabled, the active NI-2 card transmits and receives identical data signals over both fiber connections and can switch the receive path between the two upon a fiber or OC-3c port failure.
APS fiber redundancy is nonrevertive. The NI-2 will switch back to the primary fiber only if manually forced through a CLI command or if a failure condition occurs on the secondary fiber. If both fibers are failed, the system will switch to the first good fiber that is available.
Cold redundancy is redundancy in which the standby unit does not completely mirror the state of the active unit. With cold redundancy, the standby unit loses transient state information and must process its configuration during the switchover, which may lead to a period of data loss.
Cisco recommends testing the redundancy feature in the local test environment before placing the unit in production.
Table 3-4 lists the NI-2 cards and compatible chassis that support cold redundancy.
| NI-2 Card | Cisco 6130 | Cisco 6160 | Cisco 6260 |
|---|---|---|---|
DS3/2DS3 | Yes | Yes | Yes1 |
Yes | Yes | Yes4 | |
OC-3c/OC-3c MMF3, 5 | Yes | Yes | Yes |
No | Yes | No | |
OC-3c/2DS3 MMF5, 6 | No | Yes | No |
DS3+T1/E1 IMA7 | No | Yes8 | No |
Ensure that the following product revisions are installed on your system:
To properly configure and activate redundancy, ensure that you are running Cisco IOS Release 12.1(7)DA or a later version of IOS on one of the Supported Platforms. You must install a second NI-2 card (must be the same type as the primary NI-2 card).
Perform the task in the "Configure the NI-2 Cards for File Synchronization" section to configure NI-2 cards and SONET ports.
NI-2 cold redundancy supports autosynchronization of the primary and secondary NI-2 card file systems, but you must manually synchronize the flash files and bootflash files before you can enable autosynchronization.
To manually synchronize the flash and bootflash on the NI-2 cards, complete the following steps:
| Command | Purpose | |
|---|---|---|
Step 1 | DSLAM> enable
| Enter privileged EXEC mode. |
Step 2 | DSLAM# secondary sync flash
| Manually synchronize the flash files. |
Step 3 | DSLAM# secondary sync bootflash
| Manually synchronize the bootflash files. |
After you manually synchronize the flash and bootflash, configure the NI-2 cards for automatic synchronization. To enable autosynchronization of the primary and secondary NI-2 cards, complete the following steps:
| Command | Purpose | |
|---|---|---|
Step 1 | DSLAM# configure terminal
| Enter global configuration mode. |
Step 2 | DSLAM(config)# auto-sync
| Enter autosync submode. |
Step 3 | DSLAM(config-auto-sync)# flash
| Autosynchronize the flash files.1 |
Step 4 | DSLAM(config-auto-sync)# bootflash
| Autosynchronize the bootflash files.1 |
Step 5 | DSLAM(config-auto-sync)# config
| Autosynchronize the startup configuration file (default). |
Step 6 | DSLAM(config-auto-sync)# running-config
| Autosynchronize the running configuration file (default). |
Step 7 | DSLAM(config-auto-sync)# exit
| Exit from autosync submode. |
| 1You will not be able to perform this operation until you manually synchronize the file systems. |
Use the show running-config command to verify that you entered the commands correctly. Use the dir flash, dir secondary-flash, dir bootflash, and dir secondary-bootflash commands to verify that the files synchronized properly.
 |
Note Because the config and running-config synchronizations are enabled by default, they do not show up in the running configuration. |
Cisco provides Cisco.com as a starting point for all technical assistance. Customers and partners can obtain documentation, troubleshooting tips, and sample configurations from online tools.
For Cisco.com registered users, additional troubleshooting tools are available from the TAC website. To obtain troubleshooting help, go to the Cisco Troubleshooting Assistant web site on Cisco Connection Online (CCO) at http://www.cisco.com/public/support/tac/troubleshoot.shtml. Also see the "Monitoring Redundancy States" section.
Use the show redundancy states command to display the current redundancy states of the NI-2 cards.
Use the show aps command to display the APS status of each SONET port on both NI-2 cards.
This section provides output from the show running-config command.
DSLAM# show running-config
Building configuration...
Current configuration : 1917 bytes
!
version 12.1
no service pad
service timestamps debug uptime
service timestamps log uptime
no service password-encryption
!
hostname DSLAM
!
slot 7 ATUC-4FLEXIDMT
slot 10 NI-2-155MM-155MM
slot 11 NI-2-155MM-155MM
slot 34 ITUC-1-8IDSL
enable password test
!
!dsl-profile default
network-clock-select 1 ATM0/1
redundancy
auto-sync
flash
bootflash
ip subnet-zero
ip host-routing
no ip finger
no ip domain-lookup
ip host spur 123.45.678.91
ip domain-name cisco.com
ip name-server 123.45.678.92
ip name-server 123.45.6.789
!
no atm oam intercept end-to-end
atm address 47.0091.8100.0000.0030.b690.ac01.0030.b690.ac01.00
atm address 47.0091.8100.0000.00b0.c2ff.6001.00b0.c2ff.6001.00
atm router pnni
no aesa embedded-number left-justified
node 1 level 56 lowest
redistribute atm-static
!
icm size 4194304
!
interface ATM0/0
no ip address
atm cac service-category abr deny
atm maxvp-number 0
atm maxvc-number 4096
atm maxvci-bits 12
!interface ATM7/3
no ip address
no atm ilmi-keepalive
...
You can set several system parameters as part of the initial system configuration, but these parameters are not required. To set the system parameters, perform the following steps, beginning in privileged EXEC mode:
| Command | Task | |
|---|---|---|
Step 1 | DSLAM> clock set hh:mm:ss day month year
| Set the internal clock. |
Step 2 | DSLAM> configure terminal
| Enter global configuration mode from theterminal. |
Step 3 | DSLAM(config)# hostname name
| Set the system name. |
This example shows how to configure the time, date, and month using the clock set command:
DSLAM# clock set 15:01:00 17 October 2000
This example shows how to configure the host name using the hostname command:
DSLAM# configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
DSLAM(config)# hostname Publications
Publications#
This example shows how to confirm the clock setting using the show clock command:
Publications# show clock
*15:03:12.015 UTC Fri Oct 17 2000
Publications#
This section describes the Simple Network Management Protocol (SNMP), SNMP MIBs, and how to configure SNMP on Cisco DSLAMs in the following sections:
SNMP is an application-layer protocol that provides a message format for communication between SNMP managers and agents. SNMP provides a standardized framework and a common language used for the monitoring and management of devices in a network.
The SNMP framework has three parts:
The SNMP manager is the system used to control and monitor the activities of network hosts using SNMP. For Cisco DSLAMS, this system is called the Cisco Digital Subscriber Line (DSL) Manager (CDM) and its associated framework, the Cisco Element Manager Framework (Cisco EMF). A plug-in software module, referred to as an element manager, adds custom graphical user interface (GUI) windows and modeling behavior to the standard Cisco EMF system. Element manager software allows you to manage specific types of network equipment, such as Cisco DSLAMs. Cisco EMF software is the framework that supports the functions of the CDM element manager..
The SNMP agent is the software component within the managed device that maintains the data for the device and reports these data, as needed, to managing systems. The agent and MIB reside on the routing device (DSLAM, access server, or switch). To enable the SNMP agent on a Cisco routing device, you must define the relationship between the manager and the agent.
The Management Information Base (MIB) is a virtual information storage area for network management information, which consists of collections of managed objects. Within the MIB there are collections of related objects, defined in MIB modules. MIB modules are written in the SNMP MIB module language, as defined in STD 58, RFC 2578, RFC 2579, and RFC 2580 (see the ""MIBs and RFCs" section" for an explanation of RFC and STD documents). Note that individual MIB modules are also referred to as MIBs; for example, the Interfaces Group MIB (IF-MIB) is a MIB module within the MIB on your system.
The SNMP agent contains MIB variables whose values the SNMP manager can request or change through Get or Set operations. A manager can get a value from an agent or store a value into that agent. The agent gathers data from the MIB, the repository for information about device parameters and network data. The agent can also respond to manager requests to Get or Set data.
Figure 3-5 illustrates the communications relationship between the SNMP manager and agent. A manager can send the agent requests to get and set MIB values. The agent can respond to these requests. Independent of this interaction, the agent can send unsolicited notifications (traps or informs) to the manager to notify the manager of network conditions.

 |
Note This chapter discusses how to enable the SNMP agent on your Cisco device, and how to control the sending of SNMP notifications from the agent. For information on using SNMP management systems, see the appropriate documentation for your NMS application. |
A key feature of SNMP is the ability to generate notifications from an SNMP agent. These notifications do not require that requests be sent from the SNMP manager. Unsolicited (asynchronous) notifications can be generated as traps or inform requests. Traps are messages alerting the SNMP manager to a condition on the network. Inform requests (informs) are traps that include a request for confirmation of receipt from the SNMP manager. Notifications can indicate improper user authentication, restarts, the closing of a connection, loss of connection to a neighbor DSLAM, or other significant events.
Traps are less reliable than informs because the receiver does not send any acknowledgment when it receives a trap. The sender cannot determine if the trap was received. An SNMP manager that receives an inform request acknowledges the message with an SNMP response protocol data unit (PDU). If the manager does not receive an inform request, it does not send a response. If the sender never receives a response, the inform request can be sent again. Thus, informs are more likely to reach their intended destination.
However, traps are often preferred because informs consume more resources in the DSLAM and in the network. Unlike a trap, which is discarded as soon as it is sent, an inform request must be held in memory until a response is received or the request times out. Also, traps are sent only once, while an inform may be retried several times. The retries increase traffic and contribute to a higher overhead on the network. Thus, traps and inform requests provide a trade-off between reliability and resources. If it is important that the SNMP manager receives every notification, use inform requests. However, if you are concerned about traffic on your network or memory in the DSLAM and you need not receive every notification, use traps.
Figure 3-6 through Figure 3-9 illustrate the differences between traps and inform requests.
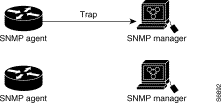
In Figure 3-6, the agent DSLAM successfully sends a trap to the SNMP manager. Although the manager receives the trap, it does not send any acknowledgment to the agent. The agent has no way of knowing that the trap reached its destination.
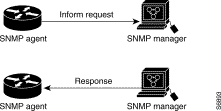
In Figure 3-7, the agent DSLAM successfully sends an inform request to the manager. When the manager receives the inform request, it sends a response to the agent. Thus, the agent knows that the inform request reached its destination. Notice that, in this example, twice as much traffic is generated as in Figure 3-6; however, the agent knows that the manager received the notification.
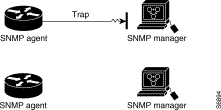
In Figure 3-8, the agent sends a trap to the manager, but the trap does not reach the manager. Because the agent has no way of knowing that the trap did not reach its destination, the trap is not sent again. The manager never receives the trap.
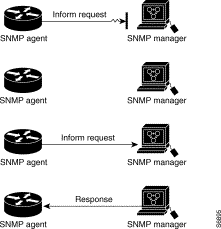
In Figure 3-9, the agent sends an inform request to the manager, but the inform request does not reach the manager. Because the manager did not receive the inform request, it does not send a response. After a period of time, the agent will resend the inform request. The second time, the manager receives the inform request and replies with a response. In this example, there is more traffic than in Figure 3-8; however, the notification reaches the SNMP manager.
MIB modules typically are defined in RFC documents submitted to the Internet Engineering Task Force (IETF), an international standards body. RFCs are written by individuals or groups for consideration by the Internet Society and the Internet community as a whole, usually with the intention of establishing a recommended Internet standard. Before being given RFC status, recommendations are published as Internet Draft (I-D) documents. RFCs that have become recommended standards are also labeled as standards (STD) documents. You can learn about the standards process and the activities of the IETF at the Internet Society website at http://www.isoc.org . You can read the full text of all RFCs, I-Ds, and STDs referenced in Cisco documentation at the IETF website at http://www.ietf.org .
The Cisco implementation of SNMP uses the definitions of MIB II variables described in RFC 1213 and definitions of SNMP traps described in RFC 1215.
Cisco provides its own private MIB extensions with every system. Cisco enterprise MIBs comply with the guidelines described in the relevant RFCs unless otherwise noted in the documentation. You can find the MIB module definition files and list of which MIBs are supported on each Cisco platform on the Cisco MIB website on Cisco.com.
For a list of MIB-related functionality, see the "MIB Features in Cisco IOS Release 12.2DA" section".
Cisco IOS software supports the following versions of SNMP:
Both SNMPv1 and SNMPv2c use a community-based form of security. The community of managers able to access the agent MIB is defined by an IP address Access Control List and password.
SNMPv2c support includes a bulk retrieval mechanism and more detailed error message reporting to management stations. The bulk retrieval mechanism supports the retrieval of tables and large quantities of information, minimizing the number of round-trips required. The SNMPv2C improved error handling support includes expanded error codes that distinguish different kinds of error conditions; these conditions are reported through a single error code in SNMPv1. Error return codes now report the error type. Three kinds of exceptions are also reported: no such object exceptions, no such instance exceptions, and end of MIB view exceptions.
SNMPv3 provides for both security models and security levels. A security model is an authentication strategy that is set up for a user and the group in which the user resides. A security level is the permitted level of security within a security model. A combination of a security model and a security level will determine which security mechanism is employed when handling an SNMP packet.
Three security models are available: SNMPv1, SNMPv2c, and SNMPv3. Table 3-5 identifies what the combinations of security models and levels mean.
 |
Note SNMPv2p (SNMPv2 Classic) is not supported in any Cisco IOS releases after 11.2. SNMPv2c replaces the Party-based Administrative and Security Framework of SNMPv2p with a Community-based Administrative Framework. SNMPv2c retained the bulk retrieval and error handling capabilities of SNMPv2p. |
You must configure the SNMP agent to use the version of SNMP supported by the management station. An agent can communicate with multiple managers; for this reason, you can configure the Cisco IOS software to support communications with one management station using the SNMPv1 protocol, one using the SNMPv2c protocol, and another using SMNPv3.
The SNMPv3 feature supports RFCs 1901 to 1908, 2104, 2206, 2213, 2214, and 2271 to 2275. For additional information on SNMPv3, refer to RFC 2570, Introduction to Version 3 of the Internet-standard Network Management Framework (note that this is not a standards document).
There is no specific command that you use to enable SNMP. The first snmp-server command that you enter enables the supported versions of SNMP.
To configure SNMP support, perform the tasks described in the following sections.
You can assign views to community strings to limit which MIB objects an SNMP manager can access. You can use a predefined view, or create your own view. If you are using a predefined view or no view at all, skip this task.
To create or modify an SNMP view record, use the following command in global configuration mode:
| Command | Purpose |
|---|---|
DSLAM(config)# snmp-server view
view-name oid-tree {included | excluded}
| Creates or modifies a view record. |
To remove a view record, use the no snmp-server view command.
You can enter this command multiple times for the same view record. Later lines take precedence when an object identifier is included in two or more lines.
Use an SNMP community string to define the relationship between the SNMP manager and the agent. The community string acts like a password to regulate access to the agent on the DSLAM. Optionally, you can specify one or more of the following characteristics associated with the string:
To configure a community string, use the following command in global configuration mode:
| Command | Purpose |
|---|---|
DSLAM(config)# snmp-server community
string [view view-name] [ro|rw] [number]
| Defines the community access string. |
You can configure one or more community strings. To remove a specific community string, use the no snmp-server community command.
For an example of configuring a community string, see the "SNMP Configuration Examples" section."
To specify an identification name (ID) for a local SNMP engine, use the following command in global configuration mode:
| Command | Purpose |
|---|---|
DSLAM(config)# snmp-server engineID local engineid-string
| Specifies the name of the local SNMP engine (or copy of SNMP). |
To specify an ID for a remote SNMP engine, use the following command in global configuration mode:
| Command | Purpose |
|---|---|
DSLAM(config)# snmp-server engineID remote ip-address
[udp-port port-number] engineid-string
| Specifies the name of the remote SNMP engine (or copy of SNMP). |
To specify a new SNMP group, or a table that maps SNMP users to SNMP views, use the following command in global configuration mode:
To configure the recipient of an SNMP trap operation, use the following command in global configuration mode:
| Command | Purpose |
|---|---|
DSLAM(config)# snmp-server host host-id
[traps|informs][version {1 | 2c | 3
[auth|noauth|priv]} ] community-string
[udp-portport-number] [notification-type]
| Specifies whether you want the SNMP notifications sent as traps or informs, the version of SNMP to use, the security level of the notifications (for SNMPv3), and the recipient (host) of the notifications. |
To configure a new user to an SNMP group, use the following command in global configuration mode:
| Command | Purpose |
|---|---|
DSLAM(config)# snmp-server user username groupname [remote
ip-address [udp-port port]] {v1 | v2c | v3
[encrypted][auth{md5|sha}auth-password]}
[accessaccess-list]
| Configures a new user to an SNMP group. |
You can set the system contact, location, and serial number of the SNMP agent so that these descriptions can be accessed through the configuration file. To do so, use the following commands in global configuration mode, as needed:
You can define the maximum packet size permitted when the SNMP agent is receiving a request or generating a reply. To do so, use the following command in global configuration mode:
| Command | Purpose |
|---|---|
DSLAM(config)# snmp-server packetsize
byte-count
| Establishes the maximum packet size. |
You can limit the number of TFTP servers used for saving and loading configuration files via SNMP to the servers specified in an access list. To do so, use the following command in global configuration mode:
| Command | Purpose |
|---|---|
DSLAM(config)# snmp-server
tftp-server-list number
| Limits the number of TFTP servers used for configuration file copies via SNMP to the servers in an access list. |
To monitor and troubleshoot SNMP status and information, use the following commands in EXEC mode, as needed:
To monitor SNMP trap activity in real time for the purposes of troubleshooting, use the SNMP debug commands, including the debug snmp packet EXEC command. For documentation of SNMP debug commands, see the Cisco IOS Debug Command Reference.
To disable any version of the SNMP agent, use the following command in global configuration mode:
| Command | Purpose |
|---|---|
DSLAM(config)# no snmp-server
| Disables SNMP agent operation. |
To configure the DSLAM to send SNMP traps or informs, perform the tasks described in the following sections:
 |
Note Most Cisco IOS commands use the word "traps" in their command syntax. Unless there is an option within the command to specify either traps or informs, the keyword traps should be taken to mean either traps or informs, or both. Use the snmp-server host command to specify whether you want SNMP notifications to be sent as traps or informs. |
To configure the DSLAM to send traps or informs to a host, use the following commands in global configuration mode:
The snmp-server host command specifies which hosts will receive SNMP notifications, and whether you want the notifications sent as traps or inform requests. The snmp-server enable traps command globally enables the production mechanism for the specified notification types (such as traps, config traps, entity traps, and so on).
You can specify a value other than the default for the source interface, message (packet) queue length for each host, or retransmission interval.
To change notification operation values, use the following commands in global configuration mode, as needed:
For inform requests, you can configure inform-specific operation values in addition to the operation values mentioned. To change inform operation values, use the following command in global configuration mode:
You can globally enable or disable authenticationFailure, linkUp, linkDown, warmStart, and coldStart notifications (traps or informs) individually. (These traps constitute the "generic traps" defined in RFC 1157.) To enable any of these notification types, use the following command in global configuration mode:
For example, to globally enable only linkUp and linkDown SNMP traps or informs for all interfaces, use the snmp-server enable traps snmp linkup linkdown form of this command.
Note that linkUp and linkDown notifications are enabled by default on specific interfaces, but will not be sent unless they are enabled globally. To control (disable or re-enable) the sending of linkUp/linkDown notifications for specific interfaces, use the no snmp trap link-status command in interface configuration mode. You can also specify the linkUp and linkDown traps from within a DSL profile. See the "Enabling and Disabling LinkUp/Down Traps" section for more information about enabling and disabling them.
The SNMP manager feature allows a DSLAM to serve as an SNMP manager. As an SNMP manager, the DSLAM can send SNMP requests to agents and receive SNMP responses and notifications from agents. When the SNMP manager process is enabled, the DSLAM can query other SNMP agents and process incoming SNMP traps.
Most network security policies assume that DSLAMs will accept SNMP requests, send SNMP responses, and send SNMP notifications.
With the SNMP manager functionality enabled, the DSLAM may also send SNMP requests, receive SNMP responses, and receive SNMP notifications. Your security policy implementation may need to be updated prior to enabling this feature.
SNMP requests typically are sent to User Datagram Protocol (UDP) port 161. SNMP responses are typically sent from UDP port 161. SNMP notifications are typically sent to UDP port 162.
Sessions are created when the SNMP manager in the DSLAM sends SNMP requests, such as inform requests, to a host, or receives SNMP notifications from a host. One session is created for each destination host. If there is no further communication between the DSLAM and host within the session timeout period, the session will be deleted.
The DSLAM tracks statistics, such as the average round-trip time required to reach the host, for each session. Using the statistics for a session, the SNMP manager in the DSLAM can set reasonable timeout periods for future requests, such as informs, for that host. If the session is deleted, all statistics are lost. If another session with the same host is later created, the request timeout value for replies will return to the default value.
Sessions consume memory. A reasonable session timeout value should be large enough that regularly used sessions are not prematurely deleted, yet small enough such that irregularly used, or one-time sessions, are purged expeditiously.
To enable the SNMP manager process and set the session timeout value, use the following commands in global configuration mode:
| Command | Purpose | |
|---|---|---|
Step 1 | DSLAM(config)# snmp-server
manager
| Enables the SNMP manager. |
Step 2 | DSLAM(config)# snmp-server
manager session-timeout seconds
| (Optional) Changes the session timeout value. |
To monitor the SNMP manager process, use the following commands in EXEC mode, as needed:
The following example enables SNMPv1, SNMPv2c, and SNMPv3. The configuration permits any SNMP manager to access all objects with read-only permissions using the community string named public. This configuration does not cause the DSLAM to send any traps.
DSLAM(config)# snmp-server community public
The following example permits any SNMP to access all objects with read-only permission using the community string named public. The DSLAM also will send alarm traps to the hosts 172.16.1.111 and 172.16.1.33 using SNMPv1 and to the host 172.16.1.27 using SNMPv2c. The community string named public is sent with the traps.
DSLAM(config)# snmp-server community public
DSLAM(config)# snmp-server enable traps alarms
DSLAM(config)# snmp-server host 172.16.1.27 version 2c public
DSLAM(config)# snmp-server host 172.16.1.111 version 1 public
DSLAM(config)# snmp-server host 172.16.1.33 public
The following example allows read-only access for all objects to members of access list 4 that specify the comaccess community string. No other SNMP managers have access to any objects. SNMP Authentication Failure traps are sent by SNMPv2c to the host cisco.com using the community string named public.
DSLAM(config)# snmp-server community comaccess ro 4
DSLAM(config)# snmp-server enable traps snmp authentication
DSLAM(config)# snmp-server host cisco.com version 2c public
The following example sends Entity MIB inform notifications to the host cisco.com. The community string is restricted. The first line enables the DSLAM to send Entity MIB notifications in addition to any traps or informs previously enabled. The second line specifies that the notifications should be sent as inform requests, specifies the destination of these informs, and overwrites any previous snmp-server host commands for the host cisco.com.
DSLAM(config)# snmp-server enable traps entity
DSLAM(config)# snmp-server host informs cisco.com restricted entity
The following example enables the DSLAM to send all traps to the host myhost.cisco.com using the community string public:
DSLAM(config)# snmp-server enable traps
DSLAM(config)# snmp-server host myhost.cisco.com public
The following example will not send traps to any host. The syslog traps are enabled for all hosts, but only ATM soft traps are enabled to be sent to a host.
DSLAM(config)# snmp-server enable traps syslog
DSLAM(config)# snmp-server host bob public atm-soft
The following example enables the DSLAM to send all inform requests to the host myhost.cisco.com using the community string named public:
DSLAM(config)# snmp-server enable traps
DSLAM(config)# snmp-server host myhost.cisco.com informs version 2c public
In the following example, the SNMP manager is enabled and the session timeout is set to a larger value than the default:
DSLAM(config)# snmp-server manager
DSLAM(config)# snmp-server manager session-timeout 1000
This section describes the MIB features available in Cisco IOS Release 12.2DA. You can download the SNMP (version2) standard and Cisco enterprise specific MIBs from the following URL:
ftp://ftp.cisco.com/pub/mibs/v2/
The MIB module is for managing the collection and storage of accounting information for connections in a connection-oriented network such as ATM.
The MIB module describes managed objects for ADSL CAP line interfaces.
The MIB module describes managed objects for ADSL DMT line interfaces. This MIB contains a table to configure the DSL profile.
The MIB module defines objects for the management of a pair of ADSL modems at each end of the ADSL line. This MIB contains a table to configure the DSL profile.
The MIB module which provides an ADSL line coding textual convention to be used by ADSL lines.
This is the MIB Module for ATM and AAL5-related objects for managing ATM interfaces, ATM virtual links, ATM cross-connects, AAL5 entities, and AAL5 connections.
Updated version of the Soft PVC MIB released with the PNNI V1.0 Errata and PICS (af-pnni-81.00). This MIB reflects the characteristics unique to soft PVC.
The MIB module is for representing physical entities in the system.
The MIB module defines the IANAifType textual convention, and thus the enumerated values of the ifType object defined in MIB-II's ifTable.
The MIB module, derived from RFC-2233, describes generic objects for network interface sub-layers. This MIB is an updated version of MIB-II's ifTable, and incorporates the extensions defined in RFC-1229.
The MIB module manages Inverse Multiplexing for ATM (IMA) interfaces.
This MIB module provides textual conventions to be used by systems supporting 15-minute based performance history counts.
The MIB module manages ATM PNNI routing.
This MIB module defines the second version of the Management Information Base (MIB-II) for use with network management protocols in TCP/IP- based internets.
This MIB module defines objects for managing DS1 interfaces, including T1 and E1.
This MIB module defines objects for managing DS3 and E3 interfaces.
The MIB module describes SONET/SDH interfaces objects.
This MIB Module defines the SNMP Management Architecture. See RFC-2271 for a description of this MIB module.
This MIB module defines MIB objects that provide mechanisms to remotely configure the parameters used by an SNMP entity for the generation of SNMP messages. See RFC-2273 for a description of this MIB module.
This MIB module contains management information definitions for the SNMP User-based Security Model. See RFC-2274 for a description of this MIB module.
This MIB module is the SNMPv2 conformance MIB. See RFC-1904 for a description of this MIB module.
This MIB module defines all SNMPv2 entities. See RFC-1907, Management Information Base for Version 2 of the Simple Network Management Protocol, for a description of this MIB module.
See RFC-1902, Structure of Management Information for Version 2 of the Simple Network Management Protocol, for a description of this MIB module.
See RFC-1903, Textual Conventions for Version 2 of the Simple Network Management Protocol for a description of this MIB module.
The management information definitions for the View-based Access Control Model for SNMP. See RFC-2275 for a description of this MIB module.
This MIB module defines managed objects that extend the ADSL-DMT-LINE-MIB. This MIB contains a table to configure the DSL profile.
This MIB module defines managed objects that extend the ADSL-DMT-LINE-MIB. This MIB contains a table to configure the DSL profile.
This MIB module extends the capabilities of the ATM-MIB. Specifically, it defines the managed objects that support signal monitoring and SVC signaling management.
This MIB module defines the managed objects that support ATM access control.
This MIB module augments the atmVplTable and atmVclTable defined by the ATM-MIB. In addition, it provides address tables for SVPs and SVCs.
This MIB module defines the managed objects that support the configuration of ATM interfaces.
A set of managed objects for tracking the status of DS3/E3/DS1/E1 and SONET interfaces.
This MIB module defines the managed objects that support ATM resource management.
This MIB module defines the managed objects that facilitate the diagnosis of failures of ATM signaling requests.
This MIB module manages Frame Relay to ATM interworking connections, and Frame Relay to Frame Relay switched connections via an ATM switching fabric, on a Cisco ATM switch.
This MIB module describes a set of objects used for switch Resource Management (RM) for Frame Relay/Frame based User-to-Network (FUNI) to ATM interworking function (IWF) connections.
This MIB module augments the definition of the atmTrafficDescrParamTable defined by the ATM-MIB.
This MIB module defines the managed objects that support the creation (and deletion) of bulk files of SNMP data.
This MIB facilitates writing of configuration files in the following ways: to and from the net, copying running configurations to startup configurations and vice-versa, and copying a configuration (running or startup) to and from the local IOS file system.
This MIB module defines the managed objects that facilitate the management of configuration files.
This MIB module defines the managed objects that support the monitoring of alarms generated by physical entities contained by the system.
This MIB module monitors the asset information of items in the ENTITY-MIB, such as serial numbers, and software and hardware revision levels.
This MIB module defines the objects that support provisioning of "container'" class physical entities.
This MIB module defines the enterprise-specific object identifiers that Cisco products use to populate the entPhysicalTable of the ENTITY-MIB.
The MIB module is for invoking Internet File Transfer Protocol (FTP) operations for network management purposes.
This MIB module describes IDSL (ISDN Digital Line Subscriber) line interfaces. The structure of this module resembles that of the ADSL-LINE-MIB (RFC-2662).
The MIB module describes objects for invoking OAM loopback ping on ATM connections.
The MIB module defines objects for managing Cisco specific extensions to the PNNI MIB.
This MIB module defines the Cisco enterprise-specific object identifiers assigned to platforms. A platform assigns its corresponding object identifier to the sysObjectID object.
This MIB module describes all variations of the symmetric DSL line interfaces. The structure of this module resembles and maintains consistency with the ADSL-LINE-MIB, ADSL-DMT-LINE-MIB, CISCO-ADSL-DMT-LINE-MIB, and CISCO-ADSL-CAP-LINE-MIB.
This MIB module defines the Cisco enterprise-specific structure of management information.
This MIB module defines the managed objects that support syslog monitoring.
The systemGroup (see RFC-1907) provides a standard set of basic system information. This MIB module contains Cisco-defined extensions to the systemGroup
The MIB module tracks and stores the modifications in data of NMS specified MIB tables implemented in the SNMP agent.
The MIB module contains a collection of managed objects that are general in nature and apply to different types of DSL modems. The structure of this module resembles the ADSL-LINE-MIB, CISCO-SDSL-LINE-MIB, ADSL-DMT-LINE-MIB, and CISCO-ADSL-DMT-LINE-MIB.
After you complete autoconfiguration and any manual configurations, copy the configuration into NVRAM. If you power off your DSLAM prior to saving the configuration in NVRAM you lose all manual configuration changes.
An example of the copy running-config command is:
DSLAM# copy running-config startup-config
Building configuration...
[OK]
After you finish configuring the DSLAM, you can use the commands described in this section to confirm the hardware, software, and interface configuration:
Use the show hardware command to confirm the correct hardware installation. For example:
DSLAM# show hardware
Chassis Type: C6260
I/O Card: 6260-E1-IO
Slot 1 : ATUC-1-4DMT Slot 17: STUC-4-2B1Q-DIR-1
Slot 2 : ATUC-1-4DMT Slot 18: ATUC-1-DMT8
Slot 3 : ATUC-1-4DMT Slot 19: ATUC-1-4DMT
Slot 4 : ATUC-1-4DMT Slot 20: ATUC-1-DMT8
Slot 5 : ATUC-1-4DMT Slot 21: ATUC-1-4DMT
Slot 6 : ATUC-1-4DMT Slot 22: ATUC-1-4DMT
Slot 7 : ATUC-1-4DMT Slot 23: ATUC-1-4DMT
Slot 8 : ATUC-1-4DMT Slot 24: ATUC-1-4DMT
Slot 9 : ATUC-4FLEXIDMT Slot 25: ATUC-1-4DMT
Slot 10: NI-2-DS3-T1E1 Slot 26: ATUC-1-4DMT
Slot 11: EMPTY Slot 27: ATUC-4FLEXIDMT
Slot 12: ATUC-1-4DMT Slot 28: ATUC-1-4DMT
Slot 13: ATUC-4FLEXIDMT Slot 29: ATUC-1-DMT8
Slot 14: STUC-4-2B1Q-DIR-1 Slot 30: ATUC-1-4DMT
Slot 15: STUC-4-2B1Q-DIR-1 Slot 31: STUC-4-2B1Q-DIR-1
Slot 16: STUC-4-2B1Q-DIR-1 Slot 32: ATUC-1-4DMT-I
Fan Module 1: Present 2: Present
Power Supply Module 1: 6260-PEM-AC
Power Supply Module 2: 6260-PEM-AC
Use the show version command to confirm that the correct version and type of software are being used and that the configuration register has been installed. For example:
DSLAM# show version
Cisco Internetwork Operating System Software
IOS (tm) NI2 Software (NI2-DSL-M), Experimental Version 12.1(20010416:212622) []
Copyright (c) 1986-2001 by cisco Systems, Inc.
Compiled Mon 16-Apr-01 17:26 by chrel
Image text-base: 0x800082C0, data-base: 0x8132A000
ROM: System Bootstrap, Version 12.0(5)DA, EARLY DEPLOYMENT RELEASE SOFTWARE (fc)
BOOTFLASH: NI2 Software (NI2-DBOOT-M), Version 12.1(6)DA, EARLY DEPLOYMENT RELE)
6260_E1IMA uptime is 1 week, 6 days, 5 hours, 48 minutes
System returned to ROM by reload
System image file is "flash:ni2-dsl-mz.v121_7_da.20010416"
cisco 6260 (NI2) processor with 60416K/5120K bytes of memory.
RC64475 CPU at 100Mhz, Implementation 48, Rev 0.0
Bridging software.
1 Ethernet/IEEE 802.3 interface(s)
112 DMT DSL Port interface(s)
20 SDSL DSL Port interface(s)
13 ATM network interface(s)
522232 bytes of non-volatile configuration memory.
4096K bytes of Boot Flash (Sector size 128K).
16384K bytes of Flash internal SIMM (Sector size 256K).
Configuration register is 0x2102
Use the show interface ethernet command to confirm that the Ethernet interface is configured correctly. For example:
DSLAM# show interface ethernet 0/0
Ethernet0/0 is up, line protocol is up
Hardware is AmdP2, address is 0001.64ff.a97f (bia 0001.64ff.a97f)
Internet address is 172.21.186.145/24
MTU 1500 bytes, BW 10000 Kbit, DLY 1000 usec,
reliability 255/255, txload 1/255, rxload 1/255
Encapsulation ARPA, loopback not set
Keepalive set (10 sec)
ARP type: ARPA, ARP Timeout 04:00:00
Last input 00:00:00, output 00:00:00, output hang never
Last clearing of "show interface" counters never
Input queue: 0/75/0/0 (size/max/drops/flushes); Total output drops: 0
Queueing strategy: fifo
Output queue :0/40 (size/max)
5 minute input rate 2000 bits/sec, 3 packets/sec
5 minute output rate 1000 bits/sec, 2 packets/sec
910869 packets input, 202979554 bytes, 0 no buffer
Received 890807 broadcasts, 0 runts, 0 giants, 0 throttles
0 input errors, 0 CRC, 0 frame, 0 overrun, 0 ignored
0 input packets with dribble condition detected
166029 packets output, 21332341 bytes, 0 underruns
0 output errors, 9 collisions, 1 interface resets
0 babbles, 0 late collision, 33 deferred
0 lost carrier, 0 no carrier
0 output buffer failures, 0 output buffers swapped out
Use the show atm addresses command to confirm correct configuration of the ATM address for the DSLAM. For example:
DSLAM# show atm addresses
Switch Address(es):
47.0091.8100.0000.0001.64ff.a980.0001.64ff.a980.00 active
NOTE: Switch addresses with selector bytes 01 through 7F
are reserved for use by PNNI routing
PNNI Local Node Address(es):
47.0091.8100.0000.0001.64ff.a980.0001.64ff.a980.01 Node 1
Soft VC Address(es):
47.0091.8100.0000.0001.64ff.a980.4000.0c98.0020.00 ATM0/2
47.0091.8100.0000.0001.64ff.a980.4000.0c98.0030.00 ATM0/3
Soft VC Address(es) for Frame Relay Interfaces :
ILMI Switch Prefix(es):
47.0091.8100.0000.0001.64ff.a980
ILMI Configured Interface Prefix(es):
LECS Address(es):
After you configure the IP addresses for the Ethernet interface, test for connectivity between the DSLAM and a host. The host can reside in any location on your network. To test for Ethernet connectivity, use this command:
| Command | Task |
|---|---|
Test the configuration using the ping command. The ping command sends an echo request to the host specified in the command line. |
For example, to test Ethernet connectivity from the DSLAM to a workstation with an IP address of 172.20.40.201, enter the command ping ip 172.20.40.201. If the DSLAM receives a response, this message appears:
DSLAM# ping ip 172.20.40.201
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.20.40.201, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/202/1000 ms
Use the ping atm command to confirm that the ATM interfaces are configured correctly. For example:
DSLAM# ping atm interface atm 0/1 5 seg-loopback
Type escape sequence to abort.
Sending Seg-Loopback 5, 53-byte OAM Echoes to a neighbour,timeout is 5 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/4 ms
DSLAM#
Use the show atm interface command to confirm the ATM interfaces are configured correctly. For example:
DSLAM# show atm interface
Interface: ATM0/0 Port-type: cpu
IF Status: UP Admin Status: UP
Auto-config: disabled AutoCfgState: not applicable
IF-Side: not applicable IF-type: not applicable
Uni-type: not applicable Uni-version: not applicable
Max-VPI-bits: 4 Max-VCI-bits: 14
Max-VP: 0 Max-VC: 4096
ConfMaxSvpcVpi: 0 CurrMaxSvpcVpi: 0
ConfMaxSvccVpi: 0 CurrMaxSvccVpi: 0
ConfMinSvccVci: 35 CurrMinSvccVci: 35
Configured virtual links:
PVCLs SoftVCLs SVCLs TVCLs PVPLs SoftVPLs SVPLs Total-Cfgd Inst-Conns
26 0 0 0 0 0 0 26 26
Logical ports(VP-tunnels): 0
Input cells: 106840 Output cells: 0
5 minute input rate: 0 bits/sec, 0 cells/sec
5 minute output rate: 0 bits/sec, 0 cells/sec
Input AAL5 pkts: 0, Output AAL5 pkts: 0, AAL5 crc errors: 0
Interface: ATM0/2 Port-type: e1_ima_link
IF Status: UP Admin Status: UP
Auto-config: enabled AutoCfgState: waiting for response from peer
IF-Side: Network IF-type: UNI
Uni-type: Private Uni-version: V3.0
Max-VPI-bits: 8 Max-VCI-bits: 14
Max-VP: 255 Max-VC: 16383
ConfMaxSvpcVpi: 255 CurrMaxSvpcVpi: 255
ConfMaxSvccVpi: 255 CurrMaxSvccVpi: 255
ConfMinSvccVci: 35 CurrMinSvccVci: 35
Svc Upc Intent: pass Signalling: Enabled
ATM Address for Soft VC: 47.0091.8100.0000.0001.64ff.a980.4000.0c98.0020.00
Configured virtual links:
PVCLs SoftVCLs SVCLs TVCLs PVPLs SoftVPLs SVPLs Total-Cfgd Inst-Conns
2 0 0 0 1 0 0 3 2
Logical ports(VP-tunnels): 0
Input cells: 925 Output cells: 74
5 minute input rate: 0 bits/sec, 0 cells/sec
5 minute output rate: 0 bits/sec, 0 cells/sec
Input AAL5 pkts: 0, Output AAL5 pkts: 0, AAL5 crc errors: 0
[additional interfaces deleted]
Use the show atm status command to confirm the status of ATM interfaces. For example:
DSLAM# show atm status
NUMBER OF INSTALLED CONNECTIONS: (P2P=Point to Point, P2MP=Point to MultiPoint,)
Type PVCs SoftPVCs SVCs TVCs PVPs SoftPVPs SVPs Total
P2P 26 0 0 0 0 0 0 26
P2MP 0 0 0 0 0 0 0 0
MP2P 0 0 0 0 0 0 0 0
TOTAL INSTALLED CONNECTIONS = 26
PER-INTERFACE STATUS SUMMARY AT 07:15:04 UTC Wed Oct 18 2000:
Interface IF Admin Auto-Cfg ILMI Addr SSCOP Hello
Name Status Status Status Reg State State State
------------- -------- ------------ -------- ------------ --------- --------
ATM0/0 UP up n/a UpAndNormal Idle n/a
ATM0/2 UP up waiting Restarting Idle n/a
Use the show atm vc command to confirm the status of ATM virtual channels. For example:
DSLAM# show atm vc
Interface VPI VCI Type X-Interface X-VPI X-VCI Encap Status Name
ATM0/0 0 36 PVC ATM0/2 0 16 ILMI DOWN
ATM0/0 0 38 PVC ATM0/2 0 5 QSAAL DOWN
ATM0/0 0 500 PVC ATM0/1 0 500 SNAP UP
ATM0/1 0 500 PVC ATM0/0 0 500 SNAP UP
ATM0/2 0 5 PVC ATM0/0 0 38 QSAAL DOWN
ATM0/2 0 16 PVC ATM0/0 0 36 ILMI DOWN
Use the show running-config command to confirm that the configuration being used is configured correctly. For example:
DSLAM# show running-config
Building configuration...
Current configuration : 12407 bytes
!
version 12.1
no service pad
service timestamps debug uptime
service timestamps log uptime
no service password-encryption
!
hostname 6260_E1IMA
!
boot system flash:ni2-dsl-mz.v121_7_da.20010416
slot 1 ATUC-1-4DMT
slot 2 ATUC-1-4DMT
slot 3 ATUC-1-4DMT
slot 4 ATUC-1-4DMT
slot 5 ATUC-1-4DMT
slot 6 ATUC-1-4DMT
slot 7 ATUC-1-4DMT
slot 8 ATUC-1-4DMT
slot 9 ATUC-4FLEXIDMT
slot 10 NI-2-DS3-T1E1
slot 12 ATUC-1-4DMT
slot 13 ATUC-4FLEXIDMT
slot 14 STUC-4-2B1Q-DIR-1
slot 15 STUC-4-2B1Q-DIR-1
slot 16 STUC-4-2B1Q-DIR-1
slot 17 STUC-4-2B1Q-DIR-1
slot 18 ATUC-1-DMT8
slot 19 ATUC-1-4DMT
slot 20 ATUC-1-DMT8
slot 21 ATUC-1-4DMT
slot 22 ATUC-1-4DMT
slot 23 ATUC-1-4DMT
slot 24 ATUC-1-4DMT
slot 25 ATUC-1-4DMT
slot 26 ATUC-1-4DMT
slot 27 ATUC-4FLEXIDMT
slot 28 ATUC-1-4DMT
slot 29 ATUC-1-DMT8
slot 30 ATUC-1-4DMT
slot 31 STUC-4-2B1Q-DIR-1
slot 32 ATUC-1-4DMT-I
no logging console
enable password cisco
!
!
!
!
!
!
dsl-profile default
alarms
dmt check-bytes interleaved downstream 4 upstream 6
dmt codeword-size downstream 16 upstream 8
sdsl bitrate 528
!
atm oam max-limit 1600
no atm oam intercept end-to-end
atm address 47.0091.8100.0000.0001.64ff.a980.0001.64ff.a980.00
atm router pnni
no aesa embedded-number left-justified
node 1 level 56 lowest
redistribute atm-static
!
atm ni2-switch trunk ATM0/IMA0
!
icm size 4194304
!
!
interface ATM0/0
no ip address
atm maxvp-number 0
atm maxvc-number 4096
atm maxvpi-bits 4
!
interface Ethernet0/0
ip address 172.21.186.145 255.255.255.0
!
interface ATM0/2
no ip address
no atm ilmi-keepalive
atm oam 0 5 seg-loopback
atm oam 0 16 seg-loopback
clock source loop-timed
framing crc4
lbo short gain10
ima-group 0
!
ip default-gateway 172.21.186.129
ip classless
ip route 0.0.0.0 0.0.0.0 172.21.186.129
no ip http server
!
atm route 47.0091.8100.5670.0000.ca7c.e01... ATM0/0
snmp-server trap-source ATM0/0
snmp-server enable traps config
snmp-server enable traps alarms
!
!
line con 0
transport input none
line aux 0
line vty 0 4
password cisco
login
!
end
Use the show startup-config command to confirm that the configuration saved in NVRAM is configured correctly. For example:
DSLAM# show startup-config
Using 1657 out of 522232 bytes
!
! Last configuration change at 11:35:31 EDT Thu Jun 3 1999
! NVRAM config last updated at 11:40:08 EDT Thu Jun 3 1999
!
version XX.X
no service pad
service timestamps debug uptime
service timestamps log uptime
no service password-encryption
service internal
!
hostname ni2-3
!
enable password lab
!
!
dmt-profile default
network-clock-select 1 ATM0/1
network-clock-select 2 system
ip subnet-zero
ip host-routing
ip domain-name cisco.com
ip name-server 171.69.204.11
!
atm address 47.0091.8100.0000.007b.f444.7801.007b.f444.7801.00
atm router pnni
no aesa embedded-number left-justified
node 1 level 56 lowest
redistribute atm-static
!
clock timezone EST -5
clock summer-time EDT recurring
!
process-max-time 200
!
interface ATM0/0
ip address 70.0.0.2 255.0.0.0
no ip directed-broadcast
map-group test
atm cac service-category abr deny
atm maxvp-number 0
!
interface Ethernet0/0
ip address 172.27.32.157 255.255.255.0
no ip directed-broadcast
no ip proxy-arp
no keepalive
!
interface ATM0/1
no ip address
no ip directed-broadcast
no atm auto-configuration
no atm ilmi-keepalive
no atm address-registration
no atm ilmi-enable
atm cac service-category abr deny
atm manual-well-known-vc
atm nni
atm pvc 0 500 interface ATM0/0 0 500 encap aal5snap
atm oam 0 500 seg-loopback
!
interface ATM0/2
no ip address
no ip directed-broadcast
no atm ilmi-keepalive
atm cac service-category abr deny
!
ip default-gateway 172.27.144.4
ip classless
!
!
map-list test
ip 70.0.0.1 atm-vc 500
!
line con 0
exec-timeout 0 0
transport input none
line aux 0
line vty 0 4
exec-timeout 0 0
password lab
login
!
sntp server 171.69.204.139
end
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
Posted: Tue Dec 10 09:43:32 PST 2002
All contents are Copyright © 1992--2002 Cisco Systems, Inc. All rights reserved.
Important Notices and Privacy Statement.