|
|

These release notes are for use with the Cisco Cache Engine User Guide, Version 2.0.0 publication and contain information that was not available for inclusion in that manual. These release notes discuss the following topics:
The port range values for the CLI commands have been increased from Version 2.01. The new port range values are 1 to 65,535 inclusive.
The following commands have port range values between 1 and 65,535:
For a complete description of the these commands, refer to the "Command Reference" appendix in the Cisco Cache Engine User Guide, Version 2.0.0 publication. This appendix is available at the following URL:
http://www.cisco.com/univercd/cc/td/doc/product/iaabu/webcache/ce20/ver20/wc202cli.htm
The http global configuration command has been updated to include the object url-validation option. This command has a dependency with the ip name-server CLI command.
When the ip name-server is not configured (for example, during transparent proxy), http object url-validation should be dynamically turned off.
When ip name-server is configured, http object url-validation should be turned on automatically if and only if it was configured to be on.
For a complete description of the updated http and show http commands, refer to the "Command Reference" appendix in the Cisco Cache Engine User Guide, Version 2.0.0 publication. This appendix is available at the following URL:
http://www.cisco.com/univercd/cc/td/doc/product/iaabu/webcache/ce20/ver20/wc202cli.htm
 | Caution URL Validation is on by default. Cisco Systems strongly recommends that you keep URL Validation enabled, because disabling URL validation might make the Cache Engine vulnerable to corruption from the HTTP objects in the cache. |
With this feature users can specify a list of IP addresses or domain names in the form mydomain.com, for which the Cache Engine will not use an upstream proxy and will contact the end server directly. This feature is supported in transparent and proxy mode.
The maximum number of no-proxy domains is 64. The Cache Engine will not use an upstream proxy for any domain that ends with a listed domain name. For example, if you specify cisco.com, the configured outgoing proxy server will be bypassed each time the cache engine tries to retrieve a web page from videos.cisco.com, or personals.cisco.com.
For IP addresses, enter the full IP address or use the asterisk "*" as a wild card for IP address fields. For example, when you enter 161.102.*.*, the Cache Engine will bypass the configured outbound proxy server and try to connect with web servers with IP addresses in the range 161.102.0.0 to 161.102.255.255.
On the Cache Engine Management Interface GUI, on the Caching menu, under the HTTP Proxy option, a Do not use Outgoing HTTP Proxy for the following local domains checkbox has been added. Click this box to bypass the outgoing proxy server for the domains entered in the adjacent list box. Each user-specified no-proxy IP address or domain name in the list box should be delimited by a carriage-return.
The exclude list option has been added to the http proxy outgoing global configuration command. Use this command to specify domains for which the Cache Engine will not use an upstream proxy.
http proxy outgoing {exclude {enable | list {domain-name | ip-address }} | host {hostname | ip-address}}Only one domain can be specified per command line. To specify multiple domains for proxy exclusion, execute the command for each domain. In the following example, cisco.com and the address 10.9.8.7 are proxy-excluded.
console(config)#http proxy outgoing exclude list cisco.com
console(config)#http proxy outgoing exclude list 10.9.8.7
For a complete description on the updated http command, refer to the section "Related Documentation" for CCO location for the updated Appendix A, "Command Reference" in the
Cisco Cache Engine User Guide, Version 2.0.0 publication.
Custom web caching allows a user-configurable port of interception to efficiently perform transparent caching at branch offices where enterprises run HTTP traffic on ports other than port 80. In Version 2.0.3, custom web caching provides support for transparent interception of HTTP traffic on any configurable port (1 to 65,535). In Version 2.0.1, the transparent mode web caching is hard-coded to HTTP standard port number 80.
Figure 1 shows a network topology using transparent web caching.
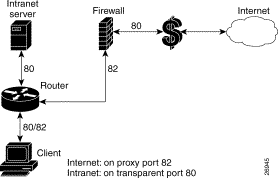
Figure 2 shows a network topology using the custom transparent cache server.
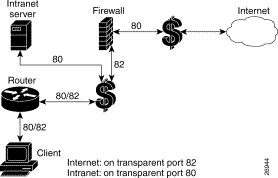 Network Topology Using Custom Transparent Cache Server
Network Topology Using Custom Transparent Cache Server
On the Cache Engine Management Interface GUI, the Custom Web Cache option has been added under the WCCP menu. Using this GUI option you can configure the Cache Engine to cache custom web traffic (custom configured outgoing port HTTP requests). This service requires you to use WCCP Version 2. Click HELP for information on configuring custom HTTP caching services.
The global configuration command wccp custom-web-cache and no wccp custom-web-cache has been added. Using this command you can configure the Cache Engine to cache custom web traffic (custom configured outgoing port HTTP requests). To use this command, you must be using WCCP Version 2.
wccp custom-web-cache router-list-num list-number port port-number [hash-destination-ip | hash-destination-port | hash-source-ip | password word | weight]In Version 2.0.1, error conditions are not handled transparently by the Cache Engine. When an error occurs, either during the processing of the request from the client or during the processing of the response from the server, the Cache Engine sends back an HTML page to the client which contains the error description. The end users see this Cache Engine generated page instead of the familiar browser pop-up error window or alert box compromising the claim of transparency.
With the transparent error reporting feature, the end users can continue to see browser-generated messages for errors that the Cache Engine encounters while processing the request or response.
In Version 2.0.3, transparent error reporting is implemented as follows:
The global configuration command error-handling and no error-handling has been added. Using this command you can customize how the Cache Engine should handle errors. To use the transparent option, you must be using WCCP Version 2.
error-handling {reset-connection | send-cache-error | transparent}In Version 2.0.1, WCCP currently redirects all packets for certain traffic to be intercepted (for example, HTTP) to the Cache Engines as they come online. The drawback is that existing TCP connections to the web server are broken. The same thing happens when WCCP goes down and then the TCP connections established by the Clients to the Cache Engine are broken. This problem is worse when there is a cluster of Cache Engines. As new Cache Engines are added and existing ones removed, the TCP connections end up being redirected to the wrong Cache Engine and the clients get a TCP RESET, which breaks the connection. In Version 2.0.2, the flow protection feature is designed to keep the TCP flow intact as well as not overwhelm the Cache Engines when they come up or are reassigned new traffic. This feature also has a slow start mechanism whereby the Cache Engines try to take load appropriate for their capacity.
The global configuration command wccp flow-redirect and no wccp flow-redirect has been added. Using this command you can enable flow redirection. To use this command, you must be using WCCP Version 2.
wccp flow-redirect enableRefer to the section "Related Documentation" for CCO location for the updated Appendix A, "Command Reference" in the Cisco Cache Engine User Guide, Version 2.0.0 publication.
The bypass feature has been enhanced as described in the following two subsections. There are two kinds of bypass (load based and authentication based).
In V2.0.1, the method of doing Load Bypass was to bypass all new connections for a short period of time (two to four seconds) and then start accepting the connections again. The new method in V2.0.3, is to bypass only a bucket at a time but for longer periods of time (ten minutes by default). If the load is still high, more buckets are bypassed until the load becomes such that the Cache Engine can handle it. Once the Cache Engine has bypassed enough buckets to be able to handle the load, it will start accepting bypassed buckets, one at a time and based on the bucket return configuration, until all buckets are serviced again.
The Cache Engine Management Interface GUI, WCCP menu, BYPASS Proxy option, has been moved to the Caching menu, under the Bypass option. You can now do the following:
Click HELP for information on configuring the bypass feature.
The Authentication Bypass feature is also located in this new GUI location. Some web sites, due to IP authentication, may not allow the Cache Engine to connect directly on behalf of the client. In order to avoid a disruption of service, the Cache can use Authentication Bypass to generate a dynamic access-list for these client/server pairs. Authentication Bypass triggers are also propagated upstream and downstream in the case of hierarchical caching. To enable Authentication Bypass on the Cache Engine, select the On radio button. To disable Authentication Bypass without losing your settings, select the Off radio button. The default value is Off.
The packets could be bypassed by Authentication Bypass even if load bypass is not enabled. Once a client/server pair goes into Authentication Bypass, it is bypassed for a configurable amount of time (ten minutes by default).
The Tunnel Bypass option is no longer available. This option was for debugging purposes to force all WCCP-redirected traffic to bypass the Cache Engine.
Implementation of enhancements to the TCP stack that improve network responsiveness, particularly in high-latency networks (for example, satellite). Satellite providers need these improvements to fully utilize their satellite links. They want to distribute content to many distributed caches.
The global configuration command tcp has been updated to include TCP client and server maximum segment size (client-mss and server-mss) and TCP satellite (client-satellite and server-satellite) options. Using this command you can configure TCP parameters. To disable TCP parameters, use the no form of this command.
tcp {client-mss size | client-receive-buffer kbytes | client-rw-timeout seconds | client-satellite | client-send-buffer kbytes | cwnd-base factor | init-ssthresh value | keepalive-probe-cnt count | keepalive-probe-interval seconds | keepalive-timeout seconds | listen-queue length server-receive-buffer kbytes | server-mss size | server-rw-timeout seconds | server-satellite | server-send-buffer kbytes}The show tcp command TCP configuration output has been updated to show the new TCP setting options:
Console# show tcp
==TCP Configuration==
TCP keepalive timeout 300 sec
TCP keepalive probe count 4
TCP keepalive probe interval 75 sec
TCP client max segment size 1460
TCP server max segment size 1460
TCP client satellite (RFC1323) disable
TCP server satellite (RFC1323) disable
TCP server R/W timeout 120 sec
TCP client R/W timeout 120 sec
TCP server send buffer 8 k
TCP server receive buffer 32 k
TCP client send buffer 32 k
TCP client receive buffer 8 k
TCP Listen Queue 200
TCP init ssthresh 65536
TCP cwnd base 2
For more information on these commands, refer to the section "Related Documentation" for CCO location for the updated Appendix A, "Command Reference" in the Cisco Cache Engine User Guide, Version 2.0.0 publication.
Using this feature you can customize the blocked message that is sent back to a user when a request from the client matches a blocked URL. You can create your own HTML page called block.html and place it in the /local/etc/ directory. If you want to embed graphics into the HTML page, place the corresponding graphics gif/jpeg file in the /local/lib/gui/pub directory.
Following is an example of the block.html file:
<HTML>
<HEAD>
<TITLE>
URL Blocked
</TITLE>
</HEAD>
<BODY>
The site you are trying to view is blocked. Please contact your system administrator if
you need to unblock this site <IMG_SRC = /local/lib/gui/pub/stop.gif width=492
height=94 border=0>
</BODY>
</HTML>
Once you have created your customized block.html page, you can turn on this feature from the CLI or GUI.
On the Cache Engine Management Interface GUI, CACHING menu, URL Filtering option, a Display customized URL blocking message (/local/etc/block.html) checkbox has been added. Check this box to turn on or off the customized URL block message.
The global configuration command url-filter has been updated to support this feature. Using this command you can enable URL blocking.
To turn on the customized URL blocking message, enter:
url-filter bad-sites-allow [custom-message]To turn off the customized URL blocking message, enter:
url-filter bad-sites-allowTo disable URL blocking, use the no form of this command.
Refer to the section "Related Documentation" for CCO location for the updated Appendix A, "Command Reference" in the Cisco Cache Engine User Guide, Version 2.0.0 publication.
Refer to the section "Related Documentation" for CCO location for the updated Chapter 2, "Installing the Cache Engine" in the Cisco Cache Engine User Guide, Version 2.0.0 publication. The following changes are described in the updated chapter:
Section "Enabling Cache Support on the Router" starting on page 2-10.
ip wccp enable
ip web-cache redirect
ip wccp {web-cache | services}
where services is the number of predefined services (0 to 99)
ip wccp {web-cache | services} redirect out
console#config
Enter configuration commands, one per line. End with CNTL/Z
console(config)#logging console alerts
console(config)#
console(config)#logging console
Translating "console" using configured ip name-server(s)...Failed
% Incomplete command.
console(config)#
Cisco Connection Online (CCO) is Cisco Systems' primary, real-time support channel. Maintenance customers and partners can self-register on CCO to obtain additional information and services.
Available 24 hours a day, 7 days a week, CCO provides a wealth of standard and value-added services to Cisco's customers and business partners. CCO services include product information, product documentation, software updates, release notes, technical tips, the Bug Navigator, configuration notes, brochures, descriptions of service offerings, and download access to public and authorized files.
CCO serves a wide variety of users through two interfaces that are updated and enhanced simultaneously: a character-based version and a multimedia version that resides on the World Wide Web (WWW). The character-based CCO supports Zmodem, Kermit, Xmodem, FTP, and Internet e-mail, and it is excellent for quick access to information over lower bandwidths. The WWW version of CCO provides richly formatted documents with photographs, figures, graphics, and video, as well as hyperlinks to related information.
You can access CCO in the following ways:
For a copy of CCO's Frequently Asked Questions (FAQ), contact cco-help@cisco.com. For additional information, contact cco-team@cisco.com.
Cisco documentation and additional literature are available in a CD-ROM package, which ships with your product. The Documentation CD-ROM, a member of the Cisco Connection Family, is updated monthly. Therefore, it might be more current than printed documentation. To order additional copies of the Documentation CD-ROM, contact your local sales representative or call customer service. The CD-ROM package is available as a single package or as an annual subscription. You can also access Cisco documentation on the World Wide Web at http://www.cisco.com, http://www-china.cisco.com, or http://www-europe.cisco.com.
If you are reading Cisco product documentation on the World Wide Web, you can submit comments electronically. Click Feedback in the toolbar and select Documentation. After you complete the form, click Submit to send it to Cisco. We appreciate your comments.

![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
Posted: Sat Sep 28 02:59:36 PDT 2002
All contents are Copyright © 1992--2002 Cisco Systems, Inc. All rights reserved.
Important Notices and Privacy Statement.