|
|

This chapter contains configuration procedures.
This chapter contains the following:
The BPX switch can be accessed through a local control port (over an RS-232 or Ethernet TCP/IP link.) An administration screen from a control terminal or from the Cisco WAN Manager Network Management Station (NMS) can issue BPX switch commands. Remote control terminal access is possible using a Virtual Terminal (vt) command if the node has been configured with a name and at least one trunk to the network has been established.
For Frame Relay connections in both tiered and non-tiered networks Cisco WAN Manager provides end-to-end configuration management using the Connection Manager. When an IPX or IGX is configured as an Interface Shelf, it can not be reached by the vt command, and Frame Relay end-to-end connections are configured from the Cisco WAN Manager via the Connection Manager over an in-band LAN connection. (Telnet can be used to access an interface shelf (e.g., IPX or IGX shelf or MGX 8220 shelf) if a Cisco WAN Manager workstation is not available to provide in-band management.)
You can monitor, manage and troubleshoot the BPX switch using the Cisco WAN Manager Network Management Station. Commands are issued to a BPX switch through the Node Administration window. Frame Relay connections are added via the Cisco WAN Manager Connection Manager. You can display and monitor the network's topology, monitor alarms, events, and statistics. Refer to the Cisco WAN Manager Operations publication for more information.
For detailed configuration information, refer to the Cisco WAN Switch Command Reference publication.
Refer to the applicable reference publications, Cisco IPX Reference, Cisco BPX 8600 Series Reference, Cisco IGX 8400 Series Reference, and Cisco MGX 8220 Reference, for node installation and operation.
As a minimum, the nodes need to be configured with name (cnfname), date (cnfdate), time (cnftime), timezone (cnftmzn), and trunks upped (uptrk) and added (addtrk or addshelf), as applicable. Connections can also be added now or later, after configuring the nodes for operation with the Cisco WAN Manager NMS manager.
The basic tasks to configure a BPX switch are as follows:
The following two examples are of the screens displayed when "dspnode" is entered at a BPX switch and at one of its IPX shelves, respectively. The "dspnode" screen displayed at the "hubone' BPX switch shows that it is connected to the "shlf3ipx" node via BNI trunk 3.3. The "dspnode" screen displayed at the "shlf3ipx" node show that it is connected to the BPX switch via AIT trunk 8.
Example of dspnode at node "hubone" BPX15 showing feeder shelves.
hubone TN edgar BPX 15 9.2 Nov. 20 1998 08:09 PST
BPX Interface Shelf Information
Trunk Name Type Alarm
1.2 shlf1 MGX 8220 OK
1.3 shlf2 MGX 8220 OK
3.1 shlf1IPX IPX/AF OK
3.2 shlf2IPX IPX/AF OK
3.3 shlf3IPX IPX/AF OK
4.1 shlf4IPX IPX/AF OK
4.3 shlf5IPX IPX/AF OK
Last Command: dspnode
Example of dspnode at node Shlf3IPX showing connection to "hubone"
shlf3IPX TN edgar IPX 8 9.2 Nov. 20 1998 09:24 PDT
BPX Switching Shelf Information
Trunk Name Type Alarm
8 hubone BPX MAJ
Last Command: dspnode
Next Command:
In setting up network management for a network, both the Cisco WAN Manager workstation and network nodes need to be configured. Cisco WAN Manager communicates over a standard physical LAN network to a gateway node or nodes, but a separate in-band IP relay network is setup for all nodes via a gateway node for SNMP and TFTP in-band communication over the node trunks.
On IPX, BPX, IGX switches, the following commands are used to configure the nodes for operation with Cisco WAN Manager: cnflan, cnfnwip, cnfstatmast, cnfsnmp. The MGX 8220 is configured with cnfifip and cnfstatsmgr. The cnflan command is only necessary for nodes or shelves in which the LAN port is actually connected to a physical Ethernet LAN as shown in Figure 12-1.
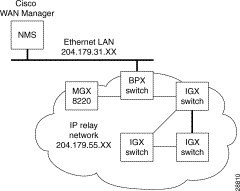
Refer to the Cisco WAN Manager Operations, Cisco WAN Switching Command Reference, and Cisco MGX 8220 Reference publications for additional information.
Step 2 Enter physical IP addresses and physical LAN node names (with a letter "p", for example, such as "nw1bpx1p", to differentiate from IP relay name) in /etc/hosts and also enter IP relay addresses with actual configured node names ("nw1bpx1", for example).
beacon% more /etc/hosts
#
# Sun Host Database
#
# If the NIS is running, this file is only consulted when booting
#
127.0.0.1 localhost
#
204.179.61.121 beacon loghost
# node physical ethernet LAN addresses
204.179.61.104 nw1bpx1p
204.179.61.71 nw1axi1p
# node ip relay addresses
204.179.55.101 nw1ipx1
204.179.55.102 nw1ipx2
204.179.55.103 nw1ipx3
204.179.55.123 nw1igx1
204.179.55.111 nw1bpx1
204.179.55.105 nw1axi1
If the workstation is connected to the corporate network for access to hosts on another network, add any IP addresses and associated names of the hosts that you may want to connect to your workstation, as the NIS is disabled.
Step 3 Enter the name or IP address of the gateway node in config.sv, using physical LAN name e.g., "nw1bpx1p". Note; normally a BPX switch is used for the gateway node because of its greater processing power.
0|Network1|nw1bpx1p|9600|0|7|6|0|30|1024|9.1|
or
0|Network1|204.179.61.104|9600|0|7|6|0|30|1024|9.1|
Step 4 Enter IP Relay subnet mask in /etc/rc2.d/S72inetsvc file as follows:
vi /etc/rc2.d/S72inetsvc
/usr/sbin/route add "224.0.0.0 ...................{this is already there
# route add for Cisco WAN Manager
route add net 204.179.55.0 204.179.61.104 1
Normally, the System Administrator will provide the IP addresses for the workstation and node. Refer to the Cisco WAN Manager Operations manual for instructions on configuring the Cisco WAN Manager workstation.
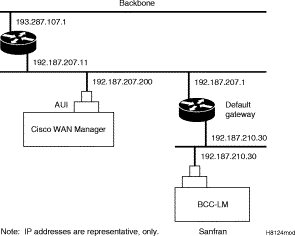
The addresses shown are just examples. Use the addresses obtained from your System Administrator. (This example is for a workstation named "hedgehog" at address 192.187.207.200. It also assumes that the BPX, IGX, or IPX switch LAN port for node sanfran has been assigned an IP address of 192.187.210.30 and a hostname of sanfran. Your own host name and addresses will be different.)
192.187.207.200 hedgehog
192.187.210.30 sanfran
Step 2 Configure the LAN port on the BPX/IPX switch using a dumb terminal or an RS-232 connection via the workstation (using the vt command, as applicable) to enter the appropriate cnflan parameters.
The cnflan command configures the node's communication parameters so that the node can communicate with a Cisco WAN Manager terminal over an Ethernet LAN using the TCP/IP protocol. The parameters contain address information about the Ethernet TCP/IP network that is used to connect the Cisco WAN Manager station to an IGX or BPX switch. The values used must conform to those of the network and should be supplied by the Ethernet network administrator.
The cnflan command has the following parameters:
A cnflan screen is shown in the following example for the LAN setup shown in Figure 12-2. An IP address of 192.187.210.30 has been entered as the active IP address for the node. The IP Subnet mask is entered as 255.255.255.0 for a Class C LAN network. The TCP service port is entered as 5120. Since the workstation and node are on different networks in this example, a gateway address of 192.187.207.1 (the address of the node serving as a gateway for Cisco WAN Manager, in this example), which must be obtained from your System Administrator, has been entered. If the workstation and node are both on the same network, no gateway address is needed. The "Maximum LAN Transmit Unit" and "Ethernet Address" parameters are not configurable by the cnflan command. The "Ethernet Address" is a hardware address that is different for every node controller card, e.g., BCC.
Example: Configuring a Control Port (Gateway Router Example)
beta TN YourID.1 BPX 15 9.2 Dec. 3 1998 02:16 PST
Active IP Address: 192.187.210.30
IP Subnet Mask: 255.255.255.0
IP Service Port: 5120
Default Gateway IP Address: 192.187.207.1
Maximum LAN Transmit Unit: 1500
Ethernet Address: 00.C0.43.00.00.20
Type State
TCP UNAVAIL
UDP READY
Telnet READY
This Command: cnflan
Enter IP Address:
Step 3 Connect the Cisco WAN Manager workstation and the BPX switch to a LAN network. The LAN port on the BPX switch provides a DB-15 connector that can be connected to a Y-cable which in turn is connected to an AUI.
Step 4 To test that a LAN connection to the BPX switch LAN port is okay, for example, for a hostname of "sanfran" entered in the config.sv file, you could enter the following at the Cisco WAN Manager workstation:
ping sanfran
Step 5 An IP Relay address needs to be configured for each node. The following example shows an example of using the cnfnwip command to configure the IP Relay address for a node. Also, at the workstation, the /etc/hosts table and routing need to be set up for each node in the network. This is so that network management using SNMP and statistics collection using TFTP via inband ILMI may be carried out. Also, assuming an isolated network for the nodes, the workstation must be isolated from the NIS reference pages in order that the Cisco WAN Manager workstation consults the /etc/hosts table. Refer to the Cisco WAN Manager Operations manual for further information.
Example Display using cnfnwip to configure IP Relay address (required for each node):
beta TN YourID BPX 15 9.2 Dec. 3 1998 02:11 PST
Active Network IP Address: 192.187.57.10
Active Network IP Subnet Mask: 255.255.255.192
Last Command: cnfnwip
Next Command:
Step 6 Once the workstation and BPX switch interface have been set up, Cisco WAN Manager can be started. The following example shows the dsplan screen after Cisco WAN Manager has been started and the communication sockets are active.
Example of dsplan after Cisco WAN Manager has been started:
beta TN YourID.1 BPX 15 9.2 Dec. 3 1998 02:16 PST
Active IP Address: 192.187.210.30
IP Subnet Mask: 255.255.255.0
IP Service Port: 5120
Default Gateway IP Address: 192.187.207.1
Maximum LAN Transmit Unit: 1500
Ethernet Address: 00.C0.43.00.00.20
Control Socket - Ready
Open Socket Descriptor - 2
Last Command: dsplan
Next Command:
Figure 12-3 shows an example of a Cisco WAN Manager workstation LAN connection to a BPX switch on a network with no gateway router, nor connection to another LAN. This type of LAN connection could also be connected through a "Hub" which is essentially a signal splitter (passive or active).
At installation, initial access to the MGX 8220 is provided by the control port. The following is a brief overview of initial configuration. Refer to the Cisco MGX 8220 Reference manual for detailed information. Also refer to appropriate release notes for applicable firmware and software versions.
Step 2 Login.
login: "LoginID"
password:
card number: 3
xxxxAXIS.1.3.ASC.a >
Step 3 Name the shelf.
xxxxAXIS.1.3.ASC.a > cnfname nw1axi1
Step 4 Set the date.
nw1nw1axi1.1.3.ASC.a > cnfdate 05/02/96
Step 5 Set the time.
nw1saxi1.1.3.ASC.a > cnftime 15:31:00
Step 6 Enter Help for a list of commands.
nw1saxi1.1.3.ASC.a > Help
Step 7 Check versions of ASC, and Service Module (e.g., FRSM, AUSM) Firmware.
nw1axi1.1.3.ASC.a > version
***** AXIS ASC Card *****2
Firmware Version = 2.1.12b_______
Backup Boot version = model-B BT_2.0.0_______
ASCFRSM Xilinx file = asc025.h
ASCBNM Xilinx file = bnmt3andsrefix
VxWorks version 5.1.1-R3000.
Kernel: WIND version 2.4.
Made on Thu May 2 16:42:36 PDT 1996.
Boot line:
sl(0,0)
cc
Step 8 Enter Ethernet LAN port IP address.
nw1axi1.1.3.ASC.a > cnfifip
cnfifip "-ip <ip addr> -if <Interface> -msk <NetMask> -bc <Brocast addr>
"
-ip <IP addr> where IP addr = nnn.nnn.nnn.nnn
-if <Interface> where Interface = 26,28,37, 26: Ethernet, 28: Slip 37: ATM
-msk <NetMask> where NetMask = nnn.nnn.nnn.nnn
-bc <BrocastAddr> where BrocastAddr = nnnnnnnn, n is hexdecimal, ethernet only
nw1axi1.1.3.ASC.a > cnfifip -ip 204.179.61.71 -if 26
Step 9 Enter IP Relay Address for SNMP Management and Stats Collection.
nw1axi1.1.3.ASC.a > cnfifip -ip 204.179.55.105 -if 37
Step 10 Configure stat master address (IP of Cisco WAN Manager workstation).
cnfstatsmgr "<ip address>"
nw1axi1.1.3.ASC.a > cnfstatsmgr 204.179.61.121 {this is IP address of Cisco
WAN Manager workstn}
Starting with switch software Release 9.2, BXM cards support virtual trunks. For additional information, refer to Chapter 15, Configuration, BXM Virtual Trunks.
This section details the steps for setting up a virtual trunk. Virtual trunking is an optional feature that must be enabled by Cisco prior to adding virtual trunks. Also, revision levels of ASI and BNI firmware must be current. The following procedure assumes that Cisco equipment is used in the ATM Cloud as well as in the Cisco WAN Switching subnetworks. In this case, a BNI output from the subnetwork is connected to an ASI UNI input at the ATM Cloud (see Figure 12-4). Proceed as follows:
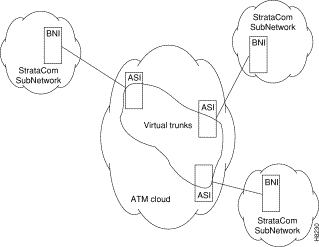 Virtual Trunks across a Cisco Wan Switching ATM Cloud
Virtual Trunks across a Cisco Wan Switching ATM Cloud
Step 2 Configure the cloud ASI ports. For each ASI port connected to a BNI virtual trunk port, do the following:
upln <slot.port>
upport <slot.port>
cnfport <slot.port> and set the shift parameter to "N" for no shift if the cloud contains BPX switches.
Step 3 Execute addcon. In the cloud network, add a virtual path ASI connection for each virtual trunk that is to route through the cloud. An example of this syntax is:
addcon joker 5.1.1.* swstorm 6.2.10.*
Where 5.1 and 6.2 are ASI ports hooked up and configured for virtual trunking. Daxcons are acceptable.
Note that the third number is the VPI which must correspond to the virtual trunk VPI configured with cnftrk in step 4.
When the cloud is a public ATM service and not a Cisco WAN Switching cloud, the VPI is provided by the carrier, as well as the guaranteed BW associated with the VPI.
The CBR/VBR/ABR parameters must also correspond to the Virtual Trunk Type of the virtual trunk. For T3, set PCR to the bandwidth of the virtual trunk, and CDVT to 24000 for the connection so that the ASI does not drop cells. These are values that Cisco recommends based on testing.
Step 4 Configure BNI virtual trunks. On the BNIs that connect to the cloud ASI ports, configure up to 32 virtual trunks, as follows:
uptrk <slot.port.vtrk>
cnftrk <slot.port.vtrk>
For cnftrk, make sure that the virtual trunk type and the VPI correspond to the ASI Virtual Path connections that have been set up.
addtrk <slot.port.vtrk>
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
Posted: Thu Jul 26 18:09:04 PDT 2001
All contents are Copyright © 1992--2001 Cisco Systems, Inc. All rights reserved.
Important Notices and Privacy Statement.