|
|

Threshold Manager is a WhatsUp Gold-launched application that allows you to set thresholds on Cisco RMON-enabled devices and retrieve event information. A working knowledge of RMON is required for using this application.
This chapter contains the following sections:
You can use Threshold Manager to configure and monitor Cisco devices by setting thresholds using Cisco-provided, predefined default policies in Cisco RMON-enabled network devices.
Policies are grouped in profiles for Cisco devices. You can use the predefined policies that are installed with Threshold Manager or create your own customized policies.
When a threshold policy is exceeded (an event has occurred), the agent in the device performs these functions:
1. Generates an alarm
2. Logs the event, and/or forwards a trap message to one or more network management stations
Next, Threshold Manger performs these functions:
1. Displays the logged events
2. Correlates the logged events to the threshold policies
You can then examine these events for potential problems. This process reduces management overhead and improves troubleshooting capabilities.
Threshold Manager provides these features:
Table 5-1 defines the common terms associated with Threshold Manager:
| Terms | Description |
|---|---|
Threshold | Defines the range in which you expect your network to perform. If thresholds exceed or go below the expected boundaries, you examine these areas for potential problems. |
Policy | Predefined configuration data that specifies the condition for triggering a threshold event. Threshold Manager uses policies to set thresholds in a Cisco router or a switch. |
Policy File | A collection of one or more policies that defines threshold values for specific MIB variables. Each threshold policy is associated with a single SNMP MIB variable type. If a policy specifies an interface type, Threshold Manager applies the policy to the matching device interface. If the policy does not specify an interface type, the application applies the value to all device interfaces. Multiple policy files can be enforced in a device or against a specific interface on a device. Two types of policy files are available:
|
Profile | A group of threshold policy files that cover a specific management area. Threshold Manager supports these four profile types:
|
Alarm | A list of parameters to be watched, and pointers to events that are triggered when defined values cross a given threshold. These parameters and pointers are defined by the RMON alarm group. For instance, you define an alarm by picking a variable, such as the number of Ethernet collisions, plus a time interval, such as 1 second, and a threshold, such as 60 collisions. Given this scenario, an alarm is generated when the number of Ethernet collisions exceeds 60 in 1 second. |
Event | Events and alarms are related elements in that an event defines the action triggered as a result of an alarm. For example, when the number of collisions on an Ethernet segment exceeds 60 per second, the corresponding event can cause a trap message to be sent to one or more management stations. Events are defined by the RMON event group. An event is generated by the RMON agent when a threshold policy has exceeded. An event can be signaled as a trap, a new entry in the RMON MIB log table, both, or neither. Threshold Manager displays all events captured from the log table and correlates the events to the configured threshold policies. |
Agent | A process in the device that handles SNMP requests. |
To start Threshold Manager from WhatsUp Gold:
Step 1 Click the task bar Start menu.
Step 2 Select Programs > CiscoWorks Windows 5.0 > WhatsUp Gold.
The WhatsUp Gold main window appears.
Step 3 Open a topology map.
A topology map with icons of all the devices in your network appears.
Step 4 Right click on the Cisco device icon.
A popup menu appears and displays several options.
Step 5 Select Threshold Manager.
The Community Strings dialog box appears.
Step 6 Enter the read community strings in the Read Community field.
Step 7 Enter the write community strings in the Write Community field.
Step 8 Click OK.
The Threshold Manager main window appears.
When you start Threshold Manager, the Threshold Manager main window appears (Figure 5-1).
Threshold Manager main window components are as follows:
Figure 5-1 shows the Threshold Manager main window.
The title bar displays the Threshold Manager application name and the active device name (Figure 5-1).
The menu bar provides access to all Threshold Manager dialog boxes (Figure 5-1).
Table 5-2 describes Threshold Manager menu options.
| Menu | Commands | What it Does |
|---|---|---|
File | New Threshold Manager | Displays a new Threshold Manager dialog box. Use this feature if you choose to run multiple instances of Threshold Manager simultaneously. |
| Print... | Displays a Print dialog box. Enter the appropriate settings and click OK to send the threshold events list display to the printer. |
| Print Setup... | Displays a Print setup dialog box. Use this dialog box to change the printer settings. |
| Exit | Exits the Threshold Manager application. |
Delete | Delete All Events | Deletes all events from the event log in the device. |
| Delete Selected Events | Deletes selected events from the event log in the device. |
View | Retrieve Events | Forces a retrieve event action from the device. |
Config | Thresholds | Displays the Config Thresholds dialog box. This dialog box provides you with tools to perform these tasks:
|
| Filter Profiles | Displays the Filter Profiles dialog box. |
Help | Using Threshold Manager | Opens the online help table of contents. |
| About | Displays Threshold Manager release version and copyright information. |
The Events List window displays threshold events stored as RMON log records in the managed device (Figure 5-1).
Table 5-3 shows the fields and associated policy for each threshold entry in the Events List window.
| Field | Policy |
|---|---|
Capture of Event Priority Icon | |
Log Time | Time and date the event was logged. The RMON agent in the managed device generates this value. |
Profile | Profile to which the threshold belongs. A profile is a group of policies. There are four profiles: system, interface, rmon_EtherStats, and customize. |
Description | Threshold policy description. |
Alarm Variable | Name of the MIB variable. |
Priority | Priority of the event. Values are 1 (highest) to 3 (lowest). The predefined threshold policies have default priority value, but you can change the value according to the importance of the information to you. If Threshold Manager cannot correlate the event with a policy file, it assigns the event a priority of 3. |
Log Description | Description of the event as defined in the corresponding RMON event entry. |
EventIndex | Index of the RMON corresponding event entry. |
LogIndex | Index of the RMON log entry. |
Owner | A text string that identifies the network management station or person to contact about the associated policy file. |
The status bar displays the event count and the last refresh date and time (Figure 5-1).
When you start Threshold Manager, the Threshold Manager main window appears and displays threshold events stored as RMON log records in the managed device (Table 5-3).
Threshold Manager correlates the event information with an existing policy by comparing the object identifier (OID) of the event with the value of the alarm variable in the policy configuration file. If a match occurs, Threshold Manager complements the event display fields of the logged entry with information from the policy file. If no match occurs, Threshold Manager displays a value of undefined.
Each event occupies a single line in the Threshold Manager events list and is displayed until one of the following situations occurs:
The following sections provide information about managing events:
Threshold Manager retrieves all events at startup and again when the refresh timer reaches a specified interval and displays the retrieved events in the Events List Window. For more information about the refresh timer, see "Retrieving Events."
From the Single Event View dialog box you can display complete information about a specific event. Use the Single Event View dialog box to determine what threshold settings in the RMON agent generated the event.
The Single Event View dialog box is divided into two panes:
Figure 5-2 shows the Single Event View dialog box.
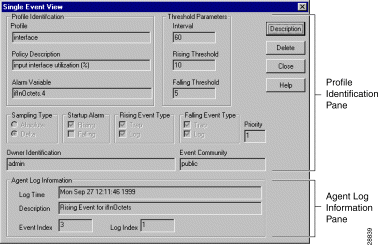
The Profile Identification pane contains parameters related to the threshold settings that generated the event (Figure 5-2). You can use this information to determine what conditions triggered the event.
If the threshold settings were created by a Threshold Manager policy file, the values from that policy file are displayed. If no policy file is associated with the threshold settings, the fields remain blank.
Table 5-4 shows the Profile Identification parameters and their description.
| Parameters | Description |
|---|---|
Name of the profile to which the policy file belongs. | |
Description of the policy. | |
Name of the MIB variable. | |
Threshold Parameters: Interval
| Interval, in seconds, over which the data is sampled and compared with rising and falling thresholds. |
Threshold Parameters: Rising Threshold
| Threshold for the sampled statistic. When the current sampled value is greater than or equal to this threshold, a single event is generated. A single event is also generated if the first sample after this entry becomes active, is greater than or equal to this threshold, and the associated Startup Alarm is equal to rising. After a rising event is generated, another such event is not generated until the sampled value falls below this threshold and reaches Falling Threshold. See "Creating New Policy Files." |
Threshold Parameters: Falling Threshold
| Threshold for the sampled statistic. When the current sampled value is less than or equal to this threshold, and the value at the last sampling interval was greater than this threshold, a single event is generated. A single event is also generated if the first sample after this entry becomes active, is less than or equal to this threshold, and the associated Startup Alarm is equal to falling. After a falling event is generated, another such event is not generated until the sampled value rises above this threshold and reaches Rising Threshold. See "Creating New Policy Files." |
|
| Method of sampling the selected variable and calculating the value to be compared with the thresholds. If the value is Absolute, the value of the selected variable is compared directly with the thresholds at the end of the sampling interval. If the value is Delta, the value of the selected variable at the last sample is subtracted from the current value, and the difference compared with the thresholds. |
|
| Alarm that can be sent when this entry first becomes active. If the first sample after this entry becomes active, is greater than or equal to Rising Threshold, and Startup Alarm is equal to rising, then a single rising alarm is generated. If the first sample after this entry becomes active or is less than or equal to Falling Threshold, and Startup Alarm is equal to falling, a single falling alarm is generated. |
|
| Agent notification for the rising event. In the case of log, an entry is made in the log table for each event. In the case of snmp-trap, an SNMP trap is sent to one or more management stations. |
|
| Agent notification for the falling event. In the case of log, an entry is made in the log table for each event. In the case of snmp-trap, an SNMP trap is sent to one or more management stations. |
Priority of the event. |
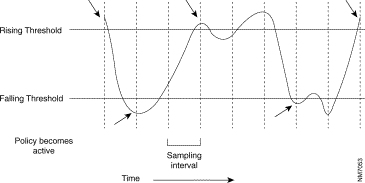
Figure 5-3 shows when rising and falling events occur with the Startup Alarm set to Rising and Falling.
The Agent Log Information pane (Figure 5-2) contains configuration information obtained by Threshold Manager from the RMON agent log. These values display whether a Threshold Manager policy file can be associated with the event.
This Agent Log Information provides:
Table 5-5 describes the action buttons in the Single Events View dialog box.
| Button | Action |
|---|---|
Description | Provides details of the event. |
Delete | Deletes the event from the event log. |
Close | Closes the window. |
Help | Opens context-sensitive help for the dialog box. |
Threshold Manager retrieves events from the RMON agent log in these situations:
You can also force a retrieve event action in the Threshold Manager events list from the RMON agent log.
When the application is operational, Threshold Manager automatically retrieves events from the RMON log at regular intervals. This interval is defined by the refresh timer parameter associated with that instance of Threshold Manager. This parameter is defined when you initiate a Threshold Manager session. The default is 360 seconds. If the refresh timer is set to 0, the Threshold Manager will not automatically retrieve events from the RMON agent.
You can sort events and change the order in which you view events in the Threshold Manager events list. You can reorder these fields:
You can delete events from the RMON log in the managed device in these cases:
You can also delete selected events or all events in the log. When you delete a selected event, all events with the same EventIndex value are removed from the RMON log.
You can manage existing threshold settings and policies or create new policies. This capability allows you to tailor alarms and events to your specific network needs.
These sections provide information about managing thresholds:
From the the Configure Thresholds dialog box, you can modify and create policies and work with threshold settings. When Threshold Manager is installed, 18 policy files appear in this dialog box. You can select one or all to use as thresholds.
The Configure Thresholds dialog box (Figure 5-4) defaults to the Config Threshold tab. The Config Threshold tab is divided into two panes:
Figure 5-4 shows the Configure Thresholds dialog box.
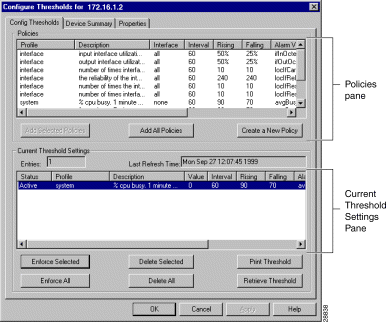
The Policies pane (Figure 5-4) displays all the existing policy files that can be applied to the managed device. The displayed policies can be default policies provided by Cisco, modified policies, or any user-defined policies. Threshold Manager provides detailed information about each policy to help you determine which thresholds to set in the RMON agent.
The content of this pane is specific to the instance of Threshold Manager and is visible only at your local machine.
From the Policies pane, you can:
For more information on the policies, see "Obtaining Managed Device Information."
From the Current Threshold Settings pane (Figure 5-4), you can display the threshold settings for the RMON agent in a managed device. The threshold settings that display an active status are those enforced in the RMON agent. These threshold settings are viewable from any Threshold Manager launched against that device. The Current Threshold Settings pane also provides information on the number of current threshold settings, the status of those settings, and the last time the current threshold settings pane was updated.
From the Current Threshold Settings pane, you can:
If Threshold Manager created the threshold settings, the fields displayed in the Current Threshold Settings pane will contain data provided by the policy file. If Threshold Manager did not create the policy or Threshold Manager cannot associate a policy with an event, only the information provided by the RMON agent will be displayed.
Before you can set a threshold in the RMON agent, you must add the settings to the Current Threshold Settings pane. You can add all policies as threshold settings or you can add specific policies. A policy can result in multiple threshold settings in the Current Threshold Settings pane. The number of times Threshold Manager adds the policy to the Current Threshold Settings pane depends on the target type and number of interfaces defined in the policy file.
A policy added to the Current Threshold Settings pane retains a pending status. This status does not change until you enforce the threshold settings to the RMON agent. Threshold settings with a pending status are viewable only from local machines.
From the Modify Threshold dialog box, you can:
You can temporarily alter threshold settings for an alarm object instance. This helps you monitor network performance for a specific period of time or fine-tune threshold settings before applying them permanently. Changes to existing threshold settings are not saved in the associated policy file. Therefore, if the device loses power or is shut down, the modifications are lost. To make permanent changes to the threshold settings, alter the associated policy file, and add the new threshold settings to the Current Threshold Settings pane.
You can also alter a threshold setting that has a pending or active status. A threshold setting with a failed status means the threshold setting was rejected by the RMON agent and cannot be altered.
You can remove active threshold settings enforced in the RMON agent and pending threshold settings from the Current Threshold Settings pane of the Configure Thresholds dialog box. Deleting a threshold setting removes all events associated with that threshold setting from the RMON log.
Threshold settings with a pending status are removed from the Current Threshold Setting pane when you:
From the Device Summary dialog box, you can display summary information about the device and the RMON MIB. The Device Summary dialog box displays information about the device currently managed by Threshold Manager. This can help you determine the class of the target device or obtain information about the device interfaces. From the Configure Thresholds dialog box, click the Device Summary tab to access the Device Summary dialog box.
You can also retrieve the latest Interface/Port List information.
Table 5-6 describes the fields in the Device Summary dialog box.
| Field | Description |
|---|---|
Device Class | Type of device. |
Last Refresh Time | Last time events were retrieved by the agent. |
Log Entries | Number of entries in the log, alarm, and event tables.1
|
System Name | Information about the system. One or more fields might be blank, depending on the device configuration.
|
Interface/Port List
| List of interfaces and ports available to the device. The icon in the left column is either an I (interface) or P (port). A red icon means the interface or port is down, and a green icon means the interface or port is up. The list of ports and interfaces for the device provides you with information about individual interfaces. This is helpful when you are designing and applying policies to specific interfaces. You can sort on the fields in this dialog box to present the information in a meaningful manner. |
There is a one-to-one relationship between a single instance of Threshold Manager and the managed device. Threshold Manager allows you to alter both the target device and the run-time parameters from within the application. This is particularly useful if you want to use a single instance of Threshold Manager to apply threshold settings in multiple devices or if you started the application with the wrong run-time parameters.
From the Properties dialog box, you can change device information and:
Threshold Manager is delivered with a set of predefined policy files that are used to set threshold values into RMON device agents. A Threshold Manager policy file contains at least one threshold policy (the default policy) for the alarm variable defined in the policy file.
A policy file can contain more than one threshold policy to define threshold values for specific interface types, but it contains policies for only one MIB variable. There is a separate policy for each MIB variable.
When an interface-specific policy is defined, Threshold Manager applies the threshold policy to the matching interface type. If no interface-specific threshold policy is defined, Threshold Manager applies the default threshold value to all device interfaces.
These sections provide information about policy files:
A policy file is an ASCII file; it is defined by keywords used by Threshold Manager to scan the file. Each policy file defines an alarm variable to be monitored by a device RMON agent and one or more threshold policies to be sent to the device agent for monitoring purposes.
Threshold Manager imposes strict rules whenever a policy file is created either manually or through the Create Threshold Policy dialog box. It is strongly recommended that you customize policy files by using the Threshold Manager GUI.
A policy file is composed of many keyword-value pairs. Use these guidelines to create policy files:
Target_Type = etherStats
Rising_Threshold = 200
Falling_Threshold = 20
Sample_Interval = 60:0:300
Interface_Threshold = ethernetCsmacd:375000000:187500000:100000000
Interface_Threshold = ethernetCsmacd:37500000:18750000:10000000
The syntax of this special keyword-value pair is as follows:
Interface_Threshold=interface_type:rising_thresh_value:falling_thres
h_value:interface_speed
where interface_speed is optional.
Threshold Manager uses interface-specific policies to set specific interface thresholds. If the interface speed is specified in the policy, the policy is applied to interfaces that match both the interface type and speed. If interface speed is not present, the policy is applied to the interface that matches the specified interface type, regardless of speed. The default policy is used to set thresholds for interfaces without an interface-specific policy defined.
Policies are loaded into Threshold Manager during startup and when a new instance of Threshold Manager is launched to monitor another device. After the policies are loaded, any new policy file created manually is ignored by Threshold Manager. However, a new policy file that is created and saved in the Create Threshold Policy dialog box is immediately visible inside Threshold Manager.
Policy files are grouped into three types: global, device class, and host. All policy files are saved under the config directory of the Threshold Manager. Policy files under the config directory are global policy files and are used for all devices. Policy files under the device class subdirectory apply to devices that belong to the same device class family. Policy files that are saved in the host subdirectory are used to set thresholds against only the specific host.
When reading policies for a given device, Threshold Manager searches that host subdirectory to locate any host-specific policy files defined for that device. It then scans the device class subdirectory for policy files defined for that device class. Last, it picks up any policy files not defined elsewhere.
Threshold Manager policy files require specific naming conventions to simplify file parsing for existing policies and when a new policy file is created. The two Threshold Manager policy file naming conventions are:
Threshold Manager provides 18 pre-defined policy files. In addition, there could be policies that are device-specific that are under the device subdirectories. These device- specific policies override the default policies.
Table 5-7 contains a brief description of the policy files.
| Policy File | Description | Default Threshold |
|---|---|---|
Average CPU busy in the last 5 minutes. See the description in the next entry. | 90% | |
Average CPU busy in the last minute. Both policies 1 and 2 are used so that the user gets at least 2 events (traps and/or logs) in case the CPU load keeps increasing. | 70% | |
Ethernet segment utilization (RMON Ethernet statistic group). | 50% | |
Free memory. | Falling threshold (absolute): 500 KB | |
Interface input utilization. | 50% | |
Interface output utilization. | 50% | |
Carrier transitions. | 10/minute | |
Reliability of the interface. | Falling threshold: 240 | |
Number of resets. | 10/minute | |
Number of restarts. | 10/minute | |
Buffer allocating failures. | 5/30 seconds | |
Buffer creation failures. | 5/30 seconds | |
Ethernet segment utilization (RMON Ethernet statistic group). | 500/second | |
Ethernet segment alignment error (RMON Ethernet statistic group). | 50/minute | |
Ethernet segment collision errors (RMON Ethernet statistic group). | 50/minute | |
Ethernet segment size errors (RMON Ethernet statistic group). | 50/minute | |
Ethernet segment size errors (RMON Ethernet statistic group). | 50/minute | |
Ethernet fragmentation errors (RMON Ethernet Statistic group). | 50/minute |
You can modify an existing threshold policy file so that you can change threshold settings for an Alarm variable without redefining the complete policy. You can also create a policy file once and then tailor it for specific interface types.
From the Modify Threshold Policy dialog box, you can:
When you complete your modifications, you can save the changes in the host-specific, device class, or global directories. Saving a policy file automatically updates the existing policy file in the Policies pane. Clicking Continue applies the altered policy directly to the Current Threshold Settings pane without saving the changes.
You can create customized threshold policies to design threshold settings specific to the conditions and performance of your network. You can also define which alarm variables to monitor, the type of threshold variable, and the specific interfaces to which the thresholds apply.
By creating new threshold policies you can:
Cisco maintains a list of all SNMP MIBs supported by Cisco IOS Release 10.2 and later. This list is located at:
The SNMP MIBs are organized by device class for both routers and switches.
Table 5-8 describes the Create Threshold Policy dialog box fields.
| Fields | Description |
|---|---|
Profile | Name of the profile to which the new policy file will belong. The value of this field is customized and cannot be altered. |
Policy | String of any alphanumeric characters used to describe the policy file. You must enter a value in this field. |
Alarm Variable | String of any alphanumeric characters representing the name of the SNMP MIB object. If the policy file is saved, the value of this field is used as the policy file name. |
Alarm OID | Uniquely identifies the threshold variable. You must enter a value in this field. You may or may not have to qualify the instance ID, depending on the value of the next field. |
Target Type | Defines how Threshold Manager manipulates the alarm object ID. If this value is one of the five Threshold Manager target types, you do not have qualify the instance identifier for the OID. These target types are known variables to Threshold Manager, and the application provides the mechanism to access the instance identifier of the object in the SNMP MIB. If you define this value as customized, you must provide the instance identifier for the alarm object. |
Table 5-9 describes the Create Threshold Policy dialog box fields.
| Fields | Description |
|---|---|
Sampling Interval | Sets the minimum and maximum values, in seconds, for the boundaries of the sampling interval. |
Rising and Falling Thresholds | Rising and falling thresholds for the sampled data. You must enter a value in these fields. |
Interface Type | Determines the type of physical interface against which the threshold settings are applied. You can define multiple interface specific thresholds within a single policy file. This field is optional and can be used only if the variable is part of an interface table or the Ethernet statistical table. |
Interface Speed | Used to calculate the line usage. Like the Interface Type, this field applies only to interface-type variables and is optional. |
Interface List | Indicates the specific threshold values for each interface you selected. |
Sampling Type | Defines the method used to derive the value of the selected variable to be compared with the threshold. Allowable values are:
|
StartUp Alarm | Defines the amount of time (in seconds) over which the data is sampled and compared with a threshold. |
Rising Event Type and Falling Event Type | Agent notification for the rising event. In the case of log, an entry is made in the log table for each event. In the case of snmp-trap, an SNMP trap is sent to one or more management stations. Agent notification for the falling event. In the case of log, an entry is made in the log table for each event. In the case of snmp-trap, an SNMP trap is sent to one or more management stations. |
Event Priority | Priority of the event. |
Owner Identification | Indicates the severity of the event generated as a result of the policy file. This keyword is predefined in the default policy files. For customized policies, the event priority value is assigned by the creator of the policy. Allowable values are 1 (most critical) to 3 (least critical). |
Event Community | Specifies the SNMP community where the trap is sent. |
The policy configuration file is a text file that sets the parameters of the threshold for a specific MIB variable. The data in the configuration file is composed of keyword-value pairs in the form of <item name> = <item value>. Policy configuration files are secured using the standard file security procedures in the host operating system.
After you create a policy file, you can:
You can save a threshold policy file in the host-specific, device class, or global directory. The host-specific directory takes on the name of the managed device. This name can be the host name or IP address of the device, depending on how you identified the device when you launched Threshold Manager. Policy files previously saved under the host name of a device will not appear in the Policies pane if you specify the IP address of the managed device when you launch Threshold Manager.
You cannot save a policy file that has a customized target type.
If the policy file is of an interface variable type, you can apply the threshold settings to one or more interfaces.
You can also add a policy file directly as a threshold setting without saving it to disk. This feature lets you create and add temporary threshold settings. However, there is no permanent record of these policies. They are lost when the managed device is turned off or goes down or when you delete the threshold settings from Threshold Manager.
You can assign multiple threshold settings to one or more interfaces within a single policy file. You can also define common variables once while retaining the freedom to specify individual threshold on an interface-by-interface basis.
After you have defined each specific threshold setting, you can apply it to one or more physical interfaces.
The current Threshold Manager implementation does not allow you to delete existing threshold policies from within the application. You can delete policies using the delete function of the Windows operating systems.
The policies are located in the Threshold-Mgr/Config directory. Depending on how you saved the policy file, it can be found in one of the following subdirectories:
All default policies in this release of Threshold Manager are found in the global directory.
The defaults in this dialog box apply to the current device configuration. You must set the IP address of the device to be managed.
You can use Threshold Manager to filter out profiles. A profile is a set of policy files that belong to a specific management area. When you filter a profile, all the policy files in that profile are no longer available to this instance of Threshold Manager. Filtering profiles is useful when you want to limit the number or focus on the type of policies available to an RMON agent. You can also use it when you want to set interface-related thresholds. By disabling all other profiles, only the interface policies are shown in the windows that manage policies.
Profiles appearing in the Hide Profile pane are no longer available to this version of Threshold Manager, and policy files contained in these profiles will not be displayed in the Policies pane of the Configure Thresholds dialog box. However, any threshold settings active in the RMON agent that belong to the filtered profile are not affected.
You can access online help in Threshold Manager as follows:
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
Posted: Fri Nov 15 05:07:19 PST 2002
All contents are Copyright © 1992--2002 Cisco Systems, Inc. All rights reserved.
Important Notices and Privacy Statement.