|
|

This appendix provides additional information on requesting digital certification from the Microsoft CA server and configuring ca-identity configuration commands on your gateway. Use this appendix with "Configuring Digital Certification."
This CA requires that both IPSec peers transact with a Registration Authority (RA), which then forwards the requests through to the CA. Both the remote IPSec peer and the local IPSec peer must be configured with the both the CA and RA public keys. The CA and RA public keys are signature and encryption key pairs, which must be generated and enrolled for authentication to occur.
For information on configuring Microsoft Certificate Services, see the following URLs:
 |
Note While Cisco Secure VPN Client supports Microsoft Certificate Services, these enrollment methods are subject to change over time. Please see the Microsoft web site at http://www.microsoft.com for the current enrollment method. |
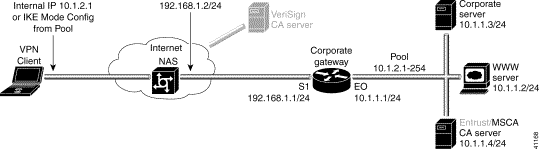
This step corresponds to "Declaring the CA" in "Configuring Digital Certification."
To enroll your certificate with a Microsoft CA, perform the following tasks, as described in Table B-1:
| Command | Purpose |
|---|---|
hq_sanjose(config)# crypto ca identity example.com
| To declare the CA your router should use, enter the crypto ca identity global configuration command. This command invokes the ca-identity (cfg-ca-id) configuration mode. In this example, example.com is defined as the domain name for which this certificate is requested. |
hq_sanjose(cfg-ca-id)# enrollment mode ra
| To indicate compatibility with the CA's Registration Authority (RA) system, enter the enrollment mode ra ca-identity configuration command. |
hq_sanjose(cfg-ca-id)# enrollment url http://microsoft-ca
| To specify the CA's location where your router should send certificate requests by indicating the CA's enrollment URL, enter the enrollment url ca-identity configuration command. In this example, http://microsoft-ca is specified as the CA server. |
hq_sanjose(cfg-ca-id)# query url http://microsoft-ca
| To specify Lightweight Directory Access Protocol (LDAP) support, enter the query url ca-identity configuration command. This command is required if your CA supports both RA and LDAP. LDAP is a query protocol used when the router retrieves certificates and CRLs. The default query protocol is Certificate Enrollment Protocol (CEP). In this example, http://microsoft-ca is specified as the LDAP server. |
hq_sanjose(cfg-ca-id)# crl optional
| To allow other peers' certificates to still be accepted by your router even if the appropriate Certificate Revocation List (CRL) is not accessible to your router, use the crl optional ca-identity configuration command. |
hq_sanjose(cfg-ca-id)# exit
| To exit ca-identity (cfg-ca-id) configuration mode, enter the exit ca-identity configuration command. |
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
Posted: Thu Jul 27 18:07:22 PDT 2000
Copyright 1989-2000©Cisco Systems Inc.