|
|

This chapter provides an overview of the Cisco Broadband Operating System (CBOS) and its features, including features introduced in Release 2.4. CBOS is the common operating system for all Cisco Customer Premise Equipment (CPE), including the Cisco 627, Cisco 633, Cisco 673, Cisco 675, the Cisco 675e, the Cisco 677, the Cisco 677i, and the Cisco 678.
 |
Note These products are referred to as the Cisco 67x product line. When you see 67x in this documentation, substitute the hardware product you are using. |
The CBOS is modeled after the Cisco Internetworking Operating System (Cisco IOS) and features a similar command syntax and format.
This chapter includes the following sections:
For more information on using the CBOS, refer to "Using the Web Interface."
The list below defines the terminology used in this chapter.
The features listed in this section are new with Release 2.4 of CBOS.
When used with series 67x CPE, CBOS Release 2.4 supports a new provisioning mode, auto-provisioning, which adds the capability to automatically provision Cisco DSL Customer Premise Equipment (CPE). In addition to auto-provisioning, CBOS Release 2.4 offers continued support for CLI mode.
Auto-provisioning provides the following benefits:
In auto-provisioning mode, the following processes occur:
1. The DSL modem is initialized.
2. The physical line is trained; the connection to the DSLAM is established.
3. At this point an image maintenance check is done.
 |
Note If a new image is downloaded, this process can take several minutes. |
4. The modem queries the configuration database and retrieves provisioning data through SNMP.
5. The configuration data is then applied to the modem.
While in auto-provisioning mode, CLI commands for DSL modems are used primarily for viewing the configuration information. All CBOS 2.3 CLI commands are available in CBOS Release 2.4. They can be used to manage the area that auto-provisioning has not addressed or to override the parameters that are set by auto-provisioning.
Auto-provisioning is disabled by default. To enable auto-provisioning, follow these steps:
Step 1 Power on the CPE.
Step 2 Enter enable mode. At the CPE's prompt, enter:
enable
Step 3 From the command line, enter:
set mmi enabled
Step 4 Save the configuration. Enter:
write
Step 5 Reboot the CPE.
CBOS Release 2.4 is enhanced to support NetMeeting Version 3.0.1, voice and video interaction application, incoming and outgoing. This enhancement adds NAT/PAT support for H323 Version 2.
Use the following new command syntax:
set nat entry add inside-ip-address 1720 tcp
For example:
set nat entry add 10.0.0.2 1720 tcp
 |
Note You must specify an inside-ip address and port of 1720 for incoming packets. TCP port 1720 is used for call setup, and this entry is required for NAT to process the payload. |
If you are using a WAN interface other than wan0-0, you must add a static route so the CPE knows which WAN interface to use when communicating with the NetMeeting server. Without this statement, the default route, wan0-0, is used.
For example, add the following statement if your NetMeeting server is on wan0-4.
set route add ip 10.20.20.0 mask 255.255.255.0 gw wan0-4
Note that this statement will send all traffic out of the wan0-4 interface.
You can also use a host mask; that is, 255.255.255.255
CBOS Release 2.4 adds NAT/PAT support for specifying port ranges, including wildcards. This eliminates the need to manually enter a number for each port, allowing for bulk data entry.
Use the following new command syntax:
set nat entry add inside-ip-address port-range1 outside-ip-address
port-range2|* protocol
The following examples map inside ranges to outside ranges:
set nat entry add 10.0.0.2 2000-2099 192.168.1.1 2000-2099 udp
set nat entry add 10.0.0.2 2000-2099 * 2000-2099 udp
set nat entry add 10.0.0.2 2000-2099 192.168.1.1 3000-3099 udp
The port numbers specified for the range are not restricted. Inside and outside ranges can be the same or different. The port number used in a packet whose unmapped port number lies in a range will have the same offset from the beginning of the range after it is mapped. The third example above shows an outbound packet having inside port 2010 mapped to outside port 3010.
CBOS Release 2.4 adds NAT support for secured versions of the Remote Shell (rsh), Remote Copy (rcp) and Remote Login (rlogin) protocols.
CBOS Release 2.4 adds support for native NetBIOS (the Datagram Service and Session Service).
CBOS Release 2.4 supports up to eight virtual circuits (VCs) in the routed mode of operation. All CBOS VC-related functionality supports up to eight VCs. Use the following command to configure interfaces 0 through 7:
set interface wan0 maxvcs 8
CBOS Release 2.4 adds the command show parameters. This command displays all CPE modem parameters. This display assists in troubleshooting and includes:
The show parameters command is available in both auto-provisioning and CLI modes.
The CBOS show command continues to support the command keywords running|nvram for displaying configuration parameters. The following are the differences between the sub-commands:
 |
Note Neither the show param nor the show run command displays parameters configured through auto-provisioning. To display these parameters, use the individual show commands, such as show filter. |
The number of entries in the CBOS Release 2.4 error log is extended to display up to 40 entries. Use the show errors CLI command to display the last 40 log entries in the system. To allow more than 40 entries, you can use the syslog command.
CBOS Release 2.4 allows additional DHCP lease information to be logged in the error log. The default mode for lease logging is off. Use the following CLI command to enable or disable this feature:
set dhcp server lease logging [enable|disable]
CBOS Release 2.4 can dynamically detect the PPP Link Control Protocol (LCP) echo request (keepalive) time interval.
CBOS Release 2.4 monitors the incoming LCP Echo Request packets to deduce the time interval being used. Upon detection, the CPE changes its own LCP Echo-Request time interval from a default value of 10 seconds to the detected value. The CPE then uses this value for sending LCP Echo-Requests.
CBOS Release 2.4 defines factory default settings for DHCP and NAT/PAT. Upon initialization, the system boots up with NAT/PAT and DHCP support disabled as default configurations. To override the default settings, use the CLI commands:
set nat enabled
set dhcp enabled
For more information on NAT see the "Network Address Translation" section. For more information on DHCP see the"Understanding the DHCP Learn Mode and Standard DHCP Mode" section.
CBOS Release 2.4 provides additional diagnostics to validate the contents of flash memory at boot time as well as on-demand. At boot-up the system computes and verifies the CRC checksum value for the image, monitor, and configuration sections of flash memory. Upon error detection, the system displays and logs error messages.
show chksum is a combined command to display the CRC checksum for the image, monitor, user configuration, and custom configuration. This command does not use options to display the checksum for individual sections. Use the following CLI command to initiate CRC checksum computations:
show chksum {image|monitor|configuration|all}In the Cisco CPE 627 and 633 systems, the system returns pass/fail indication via blinking LEDs. In all other models, pass/fail is indicated on the display. See the Cisco 600 Series Installation and Operation Guide for more information on these indicators.
The following example shows the result of the checksum command:
cbos>show chksum
image: pass
monitor: pass
user config: pass
custom config: MIX header/trailer not found
cbos>
This section lists important features of CBOS.
CBOS includes Port Address Translation (PAT) features as discussed in the following sections.
CBOS features PAT support for Microsoft WINS-based applications:
CBOS features PAT support for UDP network-directed as well as subnetwork-directed broadcasts.
CBOS features PAT support for non-encrypted remote shell (rsh), remote copy (rcp), and remote login (rlogin) protocols.
You can apply NAT to the Ethernet, logical WAN interfaces and the VIPs (virtual interfaces). Eth0 and vip0 through vip2 can be configured as inside or outside interfaces, and wan0-0 through wan 0-7 can be configured as outside interfaces for NAT.
When NAT is enabled, NAT translates only inside to outside and outside to inside traffic. Traffic that remains within its own respective boundary (inside to inside or outside to outside) is not translated.
CBOS supports any TCP/UDP traffic that does not carry source and/or destination IP addresses or ports in the application data (i.e.: HTTP, TFTP, Telnet, archie, finger, NTP, NFS), plus the following:
Due to memory restrictions, the maximum number of NAT entries that can be configured is 100, and the maximum number of routes is 60. If this limit is exceeded an error message similar to the following is logged:
Unable to add ENTRY_NAME parameter to section SECTION_NAME (IP Routing) due to memory restriction.
When a dynamic NAT entry is created from a static NAT entry that has a wildcard port or port range, but the global IP doesn't match the address of the outgoing interface, the dynamic NAT entry will show the interface as wan0-*, and a warning is entered in the error log. The address in the following example is mapped to the global IP requested, and the packet is sent to the proper interface, but the global IP address is inappropriate for that interface.
mc5-1#sh nat
mc5-1#
NAT is currently enabled
Port Network Global
eth0 Inside
wan0-0 Outside 192.168.21.1
wan0-1 Outside 192.168.20.1
vip0 Outside
vip1 Outside
vip2 Outside
Local IP :Port Global IP : Port Timer Flags Proto Interface
10.0.0.2:200 192.168.20.1:200 0 0x10041 icmp eth0 wan0-1
10.0.0.2:256 192.168.20.1:256 60 0x24046 icmp eth0 wan0-*
wan0-* and flag 2xxxx indicate a missing route.
A line similar to the following will appear in the error log:
xx xxx:xx:xx:xx IP Warning IPNAT: route missing for 192.168.20.1.
This will happen only if you are using multiple wan0-x interfaces.
Use the following commands to globally configure interface timeout values. The network generates dynamic NAT table entries based on traffic.
| Command | Description |
|---|---|
set nat {enable | disable} | Global on and off command for all interfaces |
set nat disable | Disables NAT on all interfaces |
set nat entry add | Adds a static NAT entry |
set nat entry delete | Deletes a static NAT entry |
set nat outside-ip address | Adds a specific static NAT entry to the WAN0-0 table |
show nat | Displays all NAT entries, including static and wildcard Wildcard entries display as asterisks. |
Table 1-2 lists commands to set NAT protocols for specific interfaces.
| Command | Description |
|---|---|
set nat outside ip-address | Sets Outside Global IP Address for the WAN0-0 Interface as in CBOS Release 2.2 |
set interface wan0-x outside-ip 172.167.20.42 | Sets a specific outside IP address for WAN0-x interface |
set int vip0 inside | Sets virtual interface 0 as an inside network |
 |
Note The command set interface eth0 outside ip address is invalid. |
The show nat command includes the NAT Status and Network Side for all Interfaces.
The following is another example of this format:
sh nat Example
cbos#sh nat
NAT is currently enabled
Port Network Global
eth0 Inside
wan0-0 Outside 192.161.23.4
vip0 Outside
vip1 Outside
vip2 Outside
CBOS recognizes IP Precedence bits defining Type of Service (TOS) in the IP header and routes IP packets based on this value. With this feature, you can use IP Precedence to route packets to a specific interface.
IP Precedence bits map to individual interfaces according to the following rules:
IP Precedence bits route IP packets to individual interfaces according to the following rules:
Extensions to the CBOS CLI allow users with enable-level access to configure and map IP Precedence values to different interfaces. The syntax for this command is:
set route add ip ip_address gateway gw_address precedence nTable 1-3 shows examples of the set route command.
| Command | Description |
|---|---|
set route add ip 192.200.1.0 gw 192.100.10.1 precedence 5 | Routes packet from network 192.200.1.0 with a precedence of 5 to the gateway at 192.100.10.1 |
set route add ip 192.200.1.0 gw wan0-1 precedence 5 | Sets IP Precedence to 5 for gateway interface wan0-1 |
set route default wan0-1 precedence 5 | Sets a default route for precedence 5 packets to wan0-1 |
The set route command can accept either an IP address or an interface as valid entries according to the command syntax set route default {ip-address | interface} or set route add ip ip-address gw {ip-address | interface}. When using IP address as a gateway, the gateway address must exist in one of WAN interfaces. Use show route to display WAN addresses.
The set route default command includes a precedence field that defines the default routes for packets with Precedence bits set. The syntax for the set route default command is:
set route default {ip address | interface} precedence nThe show route command includes a column [P] showing the precedence level. The following is an example of this format:
#show route
[TARGET] [MASK] [GATEWAY] [M] [P] [TYPE] [IF] [AGE
0.0.0.0 0.0.0.0 0.0.0.0 1 SA WAN0-0 0
0.0.0.0 0.0.0.0 0.0.0.0 1 5 SAR WAN0-1 0
192.168.10.0 255.255.255.0 0.0.0.0 1 LA ETH0 0
192.168.1.0 255.255.255.0 0.0.0.0 1 A WAN0-0 0
192.168.2.0 255.255.255.0 0.0.0.0 1 AR WAN0-1 0
WAN Interfaces...
192.168.1.72 255.255.255.255 0.0.0.0 1 HA WAN0-0 0
192.168.2.72 255.255.255.255 0.0.0.0 1 HA WAN0-1 0
192.168.3.72 255.255.255.255 0.0.0.0 1 HA WAN0-2 0
CBOS TFTP Client and Server programs feature checksum validation for image and configuration file transfers. Image and configuration files will be written to NVRAM only after a successful checksum validation.
 |
Caution The running configuration will be deleted when a TFTP file transfer is done. |
CBOS factory default settings for the Cisco 675 and higher are:
set ppp wan0-0 ipcp 0.0.0.0 |
Note The show run command does not show these services as enabled. Default settings are not displayed in the running configuration. |
The GSI 3.2 firmware update provides for lower baud rates to the 17 Kbaud and 64 Kbaud. CBOS Release 2.3 and later supports these rates in the Cisco 675 and 675e. The Cisco 677s can support these rates after downloading the CBOS Release 2.3 or later image. Service providers now have a wider range of desirable rates from which to chose for these products. (See Table 1-4 and Table 1-5.)
| Bit Rate per Constellation Size (kb/s) | ||||||||
|---|---|---|---|---|---|---|---|---|
| Symbol Rate (Kbaud) | Signal | 256 uncoded | 256 | 128 | 64 | 32 | 16 | 8 |
136 | Payload with RS | 1024 | 896 | 768 | 640 | 512 | 384 | 256 |
340 | Payload with RS | 2560 | 2240 | 1920 | 1600 | 1280 | 960 | 640 |
680 | Payload with RS | 5120 | 4480 | F/A | 3200 | F/A | 1920 | F/A |
952 | Payload with RS | 7168 | 6272 | F/A | 4480 | F/A | 2688 | F/A |
| RS = Reed-Solomon error correction F/A = Future Availability | ||||||||
| Downstream Kbaud | Upstream Kbaud |
|---|---|
136 | 17 |
136 | 68 |
136 | 136 |
340 | 68 |
340 | 136 |
680 | 136 |
952 | 136 |
The show rates command includes entries with the following baud rate combinations:
cbos#show rates
Possible ATM/ADSL Line Rates
Downstream Upstream (Kbps)
---------------------------------------------
952 Kbaud Downstream ----- 136 Kbaud Upstream
7168 1088
6272 952
4480 680
2688 408
---------------------------------------------
680 Kbaud Downstream ----- 136 Kbaud Upstream
5120 1088
4480 952
3200 680
1920 408
---------------------------------------------
340 Kbaud Downstream ----- 136 Kbaud Upstream
2560 1088
2240 952
1920 816
1600 680
1280 544
960 408
640 272
91
340 Kbaud Downstream ----- 68 Kbaud Upstream
2560 544
2240 476
1920 408
1600 340
1280 272
960 204
640 136
45
---------------------------------------------
136 Kbaud Downstream ----- 136Kbaud Upstream
1024 1088
896 952
768 816
640 680
512 544
384 408
256 272
136 Kbaud Downstream ----- 68 Kbaud Upstream
1024 544
896 476
768 408
640 340
512 272
384 204
256 136
45
136 Kbaud Downstream ----- 17 Kbaud Upstream
1024 136
896 119
768 102
640 85
512 68
384 51
256 34
11
The CBOS CLI allows a user with exec-level access to set the upstream transmit power.
 |
Caution This command should be used only by advanced users. |
The syntax for the command is:
set interface wan0 txpower value_in_db
Valid values are:
CBOS allows you to learn the starting addresses for the DCHP pool. CBOS features the ability to use the IP address and mask learned during IPCP negotiation to define the range of IP addresses.
CBOS WAN Link LED blink patterns include an indicator of the connection state of the Cisco 675 as listed in Table 1-6.
| Blink Pattern/Rate | Description |
|---|---|
Steady on | A link is established to the WAN port. All parameters for physical and logical connections are correctly set. The equipment successfully transmits and receives data. |
Continuous rapid blinking, about 3 blinks per second | The equipment is trying to establish a connection. The pattern continues until a connection is established. |
Intermittent blinking For the Cisco 675: 6 rapid blinks followed by a 2-second pause before repeating For the Cisco 677x: 5 rapid blinks followed by a 2-second pause before repeating | The equipment is trying to establish a physical connection. At this time, the training session is not yet completed; there are no logical connections and negotiated line conditions with other equipment (such as DSLAMs) are not yet established. |
Off | Check all connections. Ensure the WAN0 interface is not disabled. |
CBOS supports the set filter command. See the "set filter" section in "Introduction to the Cisco Broadband Operating System."
This section describes the CBOS-supported features that are common to the Cisco Customer Premise Equipment (CPE) product line.
DHCP automatically configures the IP addresses of both the Cisco CPE 67x series products and PC clients within the SOHO network. NAT uses one or more public IP address to translate the SOHO network's private IP address space into real, Internet-valid network IP addresses (Figure 1-1).
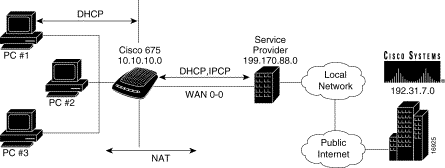
 |
Note The Cisco 67x CPE products and CBOS are Y2K compliant. |
The combination of DHCP and NAT in the Cisco PPP/ATM environment supports client configuration using DHCP and NAT by automatically configuring both the Cisco 67x and the associated SOHO network at power-on. A minimal configuration is required in the user PC (typically a single check-box to enable DHCP operation) but all PCs within the network have identical settings which simplifies initial provisioning and network support.
Two components make up the dynamic host configuration protocol on the Cisco 67x:
When the Cisco 67x DHCP server operates in:
The configuration information that the Cisco 67x DHCP server is able to assign to SOHO clients includes, but is not limited to, the following:
 |
Note The Cisco 67x does not automatically resolve DNS addresses. Therefore, you must enter the following configuration parameters as IP addresses. |
 |
Note Not all DHCP clients accept or understand every configuration parameter option passed to them. |
NAT in the Cisco 67x translates private IP addresses to public IP addresses. By dynamically creating a table of translation information each time data is exchanged with any network outside of the SOHO network, the CPE device allows multiple PCs to oversubscribe a single, public IP address. This powerful feature both conserves IP addresses and minimizes customer reconfiguration of a local SOHO network.
Use NAT if you cannot use a network's internal private addresses outside either for security reasons or because the addresses are invalid outside the network.
Basic NAT allows a mapping between one private address and one public address. (This is not supported on the 67x CPE devices.) NAT with Port Address Translation (PAT or NAPT) is an extension to NAT in that PAT uses TCP/UDP ports in addition to network addresses (IP addresses) to map many private network addresses to a single outside address.
Public IP addresses can be obtained in one of the following ways:
1. Using IPCP
2. Setting a value on the CPE.
With RFC1483 routing, you must use the second method.
Network Address Translation is predominantly application-independent. Applications that include IP addresses within the packet payload will fail without special NAT-wise consideration.
Other benefits of the Cisco implementation of NAT on CPE products include:
When both NAT and DHCP are enabled, NAT obtains the public address used for translation in the same manner as described above. However, DHCP does not require any additional provisioning, because NAT translates all address information to the outside, public address.
The result for the SOHO user is as follows:
1. SOHO users turn on their un-configured machines with DHCP enabled. Within seconds, they can be surfing the Internet using a configuration transparently supplied by their service provider.
2. Clients are not affected by changes at the service provider.
This section describes actions necessary to set the NAT to the outside IP address when using auto-provisioning.
Using the command-line interface, follow these steps:
Step 1 From the system prompt, enter the CBOS command to set the NAT to the outside IP address:
This automatically puts the NAT on WAN0-0.
Step 2 If you are using multiple virtual circuits (VCs), add the following command:
You must enter a line for each wan0-x interface.
Using CDCM, follow these steps:
Step 1 For each outside NAT interface, create a Service Profile for each wan0-X interface. See the CDCM User Guide for instructions. The VCC will appear in the ATM VCC box as ATMVCC-X.
 |
Note These numbers start counting from 1, whereas CBOS starts counting from 0. |
Step 2 Click the NAT tab. SeeFigure 1-2.
If you want to use auto-provisioning with NAT or if you are using RFC1483 routing, you must modify the NAT tab in the Service Profile that will be used with the applicable VCC. Enter the NAT outside IP address for the interface in the Translation IP Address field; the other fields can be any numbers, because they are not used.
To use different outside IP addresses for other interfaces (for example, wan0-1, wan0-2, and so on), you must create a service profile for each address and apply it to the VCCs.
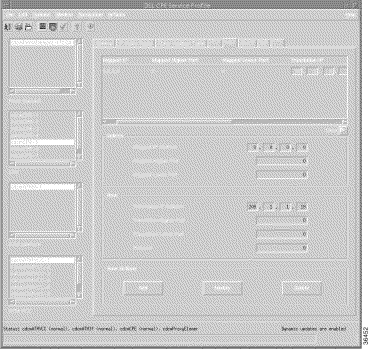
Step 3 In the Translation IP address field of the Row box, enter the global outside address (x.x.x.x). All other fields can be 0, but they must be filled in.
In addition to DHCP and NAT, CBOS also supports the following applications for management and control of the system:
 |
Note Devices behind a CPE cannot ping the terminating router in PPP routing mode with RIPv1 enabled unless there is a static route on the upstream router pointing to the Ethernet address of the CPE: |
When a PPP link is established between the CPE and the terminating router and an IP address is negotiated by the CPE from a local IP pool on the terminating router, RIPv1 information is not passed to and from the CPE about the network of the Virtual Interface because the Virtual Interface on the terminating router is a locally connected device.
For ping to work in this situation, you must add a static route on the terminating router for the network of the devices behind the CPE with the destination pointing to the Eth0 interface of the CPE.
/etc/syslog.conf configuration file (remember to use tabs, not spaces). Several systems, such as Linux and FreeBSD, have SYSLOG set up properly by default. |
Caution For security reasons, Cisco recommends that you disable the TFTP application, except when uploading or downloading a file. Typically, use TFTP to transfer new software from Cisco to your Cisco 67x. |
.cfg extension to make the configuration file easy to locate and to assure that it can be viewed and edited by a standard text editor. Archive an image of your configuration file before making changes to it so you can easily recover the old file if necessary. |
Note These applications are only accessible when the Cisco 67x is in routing mode except for TFTP, ping, and Telnet in managed bridging mode. |
If you are using a Windows 2000 server, under certain conditions if you try to transfer files from more than one PC at a time, file transfer on both PCs will stop.
This conditions under which this occurs are:
To prevent this situation, you can allow one PC at a time to do a file transfer using Microsoft networking or use another file transfer mechanism such as FTP.
This section gives the transmission rates for Cisco CPE devices.
Table 1-7 shows the SDSL 2B1Q transmission specification.
| Specification | Downstream and Upstream |
|---|---|
Maximum Transmit Power | 13.5 dBm |
Maximum Rate | 1168 kbps |
Spectrum | DC-2.92 MHz |
Bandwidth | 2.92 MHz |
Table 1-8 shows the CAP RADSL transmission specification.
| Specification | Downstream | Upstream |
|---|---|---|
Maximum Transmit Power | 22.7 dBm | 13.3 dBm |
Maximum Rate | 7168 kbps | 1088 kbps |
Spectrum | 240 - 1335 KHz | 35 - 191.4 KHz |
Bandwidth | 1.095 MHz | 156 KHz |
Table 1-9 shows the DMT Issue 2 RADSL transmission specification.
| Specification | Downstream | Upstream |
|---|---|---|
Maximum Transmit Power | 20.4 dBm/Hz | 12.5 dBm/Hz |
Maximum Rate | 8032 kbps | 864 kbps |
Spectrum | 138-1104 KHz | 26-138 KHz |
Bandwidth | 966 KHz | 112 KHz |
Table 1-10 shows the Cisco 677 transmission specification.
| Specification | Downstream | Upstream |
|---|---|---|
Maximum Transmit Power | -36.5 dBm | -38 dBm/Hz |
Maximum Rate | 8032 kbps | 800 kbps |
Spectrum | 138-1104 KHz | 26-138 KHz |
Bandwidth | 966 KHz | 112 KHz |
 |
Note The Cisco 677 does not support CAP mode. |
Table 1-11 shows the transmission specification for the Cisco 677i.
| Specification | Downstream | Upstream |
|---|---|---|
Maximum Rate | 8032 kbps | 800 kbps |
Spectrum | 280-1104 KHz | 172-256 KHz |
Bandwidth | 824 KHz | 84 KHz |
 |
Note The Cisco 677 does not support CAP mode. |
The CBOS includes two interfaces you can use to configure and operate the Cisco 67x:
DHCP pools and IP filters start counting from 0 in CBOS; however, counting starts at 1 in CDCM. When the CPE receives the values, it automatically decrements them by one, so pool 1 becomes pool 0, filter 1 becomes filter 0, and so on.
When you use auto-provisioning to configure DHCP pools for a CPE device, you must always configure the first pool on the CPE . This is because, even if the first pool is not configured, it will be enabled and populated with default values of IP 10.0.0.2, netmask 255.255.255.0, and size 252.
 |
Note When you configure eth0 in the Web Interface as 0.0.0.0 so it gets an
IP address from IPCP negotiation, the following message displays
when the CPE is downloading the configuration via MMI:Target conflicts with another interfaceThis message indicates that the interface being configured has the same IP & mask value as others, which is the case when we use IPCP to get an IP address. This message can be safely ignored. |
The following CBOS items cannot currently be configured using CDCM:
From the CBOS prompt, use the help command to display the online help system for a specified command. Refer to "CBOS Commands," for more information on the help command. To access the Help facility, enter the following command from the command line:
help {command-name}
or
? {command-name}
For example, to display information about the show version command, enter:
help show version
or
? show version
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
Posted: Sat Sep 28 01:09:52 PDT 2002
All contents are Copyright © 1992--2002 Cisco Systems, Inc. All rights reserved.
Important Notices and Privacy Statement.