|
|

CiscoSecure EasyACS Version 1.0 is network security software that helps you authenticate users by allowing dial-in access to a Cisco network access server. CiscoSecure EasyACS is included with every Cisco network access server and is supported by Cisco as part of the Smartnet account.
CiscoSecure EasyACS Version 1.0 supports both Cisco network access servers (such as the Cisco 2509, 2511, 3620, 3640, and AS5200) and the PIX firewall. It is a basic access control server (ACS) for Windows NT Server Version 4.0. CiscoSecure EasyACS uses the Terminal Access Controller Access Control System (TACACS)+ protocol to provide Authentication, Authorization, and Accounting (AAA) to ensure a secure environment. This enables you to control access to your network from a central location. Each facet of AAA significantly contributes to the overall security of your network:
(For more information, see the sections "Authentication," "Authorization," and "Accounting" later in this chapter.)
CiscoSecure EasyACS can authenticate against either the Windows NT User Database or the CiscoSecure EasyACS User Database for authentication purposes. (For more information, see the section,"Selecting a Database" later in this chapter.)
This section describes the CiscoSecure EasyACS features:
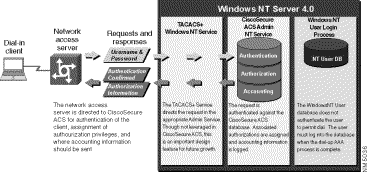
The network access server is configured to direct all dial-in user access requests to CiscoSecure EasyACS for authentication and authorization of privileges. Using the TACACS+ protocol, the network access server sends authentication requests to the CiscoSecure EasyACS server, which verifies the username and password either against the Windows NT User Database or the CiscoSecure EasyACS User Database. The CiscoSecure EasyACS server then returns a success or failure response to the network access server, which permits or denies user access.
When the user has been authenticated, a set of session attributes can be sent to the network access server to provide additional security. These attributes can include the IP address pool to pull from and the type of connection (for example, IP, IPX, or Telnet).
You can select the Windows NT User Database or the CiscoSecure EasyACS Database to authenticate usernames and passwords according to your network requirements. This section contrasts the advantages and limitations of each option.
CiscoSecure EasyACS can be configured to authenticate usernames and passwords against those usernames and passwords already configured in the Windows NT User Database. This means that in organizations where a substantial Windows NT User Database already exists, CiscoSecure EasyACS can leverage the work already invested in building that database without any added intervention by the system administrator. This eliminates the need to build two separate databases.
The pairing of CiscoSecure EasyACS and the Windows NT databases results in convenient administration of network security. The network access server presents the username to CiscoSecure EasyACS. CiscoSecure EasyACS looks in its own database to locate a match. If a match is not found, and the CiscoSecure EasyACS has been configured to "Check NT User Database for usernames not found in EasyACS," then the username and password are compared to the usernames and passwords residing in the Windows NT User Database. If a match is confirmed, the username (not password) is stored in the CiscoSecure EasyACS User Database for future authentication requests. This enables all future authentications by this user to occur much faster because CiscoSecure EasyACS goes directly to the Windows NT User Database for authentication. When this new user is added to the EasyACS Database, the user setup is automatically configured to use the Windows NT User Database for password authentication, and to assign the user to the group specified as NT Users.
The authorization privileges assigned to the NT Users group are then assigned to the user just authenticated. The system administrator can then choose to reassign this user to another group should privilege levels be required that differ from those in the default NT Users group. See Figure 1-1.

An added benefit of using the Windows NT User Database is a direct authentication to the database (bypassing the network access server). As such, you can require users to enter their username and password once, for the convenience of a simple, single login.
However, authenticating against the Windows NT User Database does not allow the storage of third-party passwords for added levels of security (for example, CHAP). Therefore, if security is a more important consideration than the benefits of leveraging the Windows NT User Database, you should use the CiscoSecure EasyACS Database.
The operation of CiscoSecure EasyACS provides a simple but effective security solution for dial-in users. The network access server presents the username to CiscoSecure EasyACS. CiscoSecure EasyACS looks in its own database to locate a match. If a match is not found, and CiscoSecure EasyACS has not been configured to "Check NT User Database for usernames not found in EasyACS," the user is not authenticated. However, if a match is found then the user is authenticated and assumes the authorization privileges of the "Group" to which the user is assigned. (See Figure 1-2.)
CiscoSecure EasyACS uses a built-in database that is a hash-indexed flat file. This type of file is not searched from the top of a text file as typically associated with the term flat file, but instead is indexed like a database. The hash-indexed flat file builds an index and tree structure so searches can occur exponentially rather than in a linear fashion, which enables the CiscoSecure EasyACS Database to rapidly authenticate users. Using the CiscoSecure EasyACS Database requires you to manually enter the usernames. However, after the names exist in the CiscoSecure EasyACS Database, administration is easier than using the Windows NT User Database.
In addition, using the CiscoSecure EasyACS Database for authentication supports both PAP and CHAP.
After CiscoSecure EasyACS has been installed, you configure and manage it through the specially designed web-based GUI. You can display the web-based interface using either Microsoft Internet Explorer 3.0 or Netscape Navigator 3.0. (Because CiscoSecure EasyACS requires support of frame technology, earlier versions of these browsers are not supported.) The web-based interface allows you to easily modify the authentication and authorization parameters of any user or group in CiscoSecure EasyACS. Because CiscoSecure EasyACS can be viewed from a browser, you can manage it from anywhere on the LAN or WAN.
The web-based interface not only makes viewing and editing user and group information possible, it also allows you to restart the service, add remote administrators, change network access server information, and view reports from anywhere on the network. These reports track connection activity, show which users are currently logged in, and list the failed authentication and authorization attempts.
The web-based interface makes all of this information easily accessible to the user. In addition, the interface constantly displays a help screen of specific information and, if more extensive information is needed, clicking More Detailed Help will take you to the relevant point in the documentation. Online documentation is always available through this interface, making remote administration easy.
To get to the CiscoSecure EasyACS web-based interface, enter one of the following addresses on the address line of your browser:
From the browser on the server, EasyACS is installed at the following URLs:
http://localhost:2002
http://<NT Server IP address>:2002
http://<NT Server Host name>:2002
From a browser on a workstation:
http://<NT Server IP address>:2002
http://<NT Server Host name>:2002
CiscoSecure EasyACS has a built-in web server for support using an HTML interface. This eliminates the necessity of installing another web server on the Windows NT server running CiscoSecure EasyACS. Because the CiscoSecure web server uses port 2002, you can use another web server on the same machine to provide other web services.
CiscoSecure EasyACS software uses AAA to help you to monitor and control the following:
Authentication allows network managers to deny intruders from their networks. Simple authentication methods use a database of usernames and passwords.
CiscoSecure EasyACS software uses the TACACS+ protocol to accept usernames and password information sent from a network access server by different protocols such as PAP, CHAP, and standard Telnet.
Although both PAP and CHAP are authentication protocols used to encrypt passwords, each provides a different level of security.
PAP uses clear-text passwords and is the least sophisticated authentication protocol. Authenticating users against the Windows NT User Database only allows password encryption using PAP.
CHAP uses a challenge-response mechanism with one-way encryption on the response. It allows CiscoSecure EasyACS to negotiate downward from the most secure to the least secure encryption mechanism, and it protects passwords transmitted in the process. If you are using the CiscoSecure EasyACS Database for authentication, you can use either PAP or CHAP.
To enable PAP, enter this command in the network access server for each dial-in interface:
ppp authenticate pap
To enable CHAP, enter this command in the network access server for each dial-in interface:
ppp authenticate chap
You can configure an account to do any one of the following:
Never expiring simply means that CiscoSecure EasyACS will not disable access under any condition.
Expiration on a certain date makes it possible to set a specific duration of time that the user can have access.
Expiration after a specific number of failed attempts to authenticate can also be defined. By entering values in the Expiration portion of the User Setup window, you can prevent intruders from getting several chances to attempt to break into your network. If the number of failed attempts is reached (this is displayed in Reports & Activity, under Daily Failed Attempt Reports), you can reset the Failed attempt count to zero by clicking the reset button.
The two expiration conditions can be used together or individually.
Disabling the user means that CiscoSecure EasyACS doesn't permit access under any condition. To see a list of accounts that have been disabled, see the Reports & Activity Section.
Authorization allows network managers to limit the network services available to each user. The authorization function restricts the exposure of the internal network to outside callers and simplifies the view of the network. Authorization also allows mobile users to connect to the closest local connection with the same access privileges they would have if they were directly connected to their local networks. Finally, authorization is used to specify which commands a new system administrator or user can issue on specific network devices.
CiscoSecure EasyACS authorization for IP networks and the assignment of an IP address to a dial-in user can be configured in the following way:
Accounting allows system administrators to bill departments or customers for connection time or resources used on the network (for example, duration of calls). Furthermore, accounting allows you to track suspicious connection attempts into the network. In addition, the accounting functionality enables you to track router configurations.
Because CiscoSecure EasyACS software uses Transmission Control Protocol (TCP), its accounting information database receives reliable accounting information and provides a secure and complete accounting log. CiscoSecure EasyACS provides a daily output file in a format that can be easily imported into most popular databases and spreadsheets.
The accounting portion of AAA contains the following information:
The billing information includes connect time, user ID, connection location, amount of data transferred, start time, and stop time.
|
|