
 |  |
Chapter 6. Firewall Architectures
Contents:
Single-Box ArchitecturesScreened Host Architectures
Screened Subnet Architectures
Architectures with Multiple Screened Subnets
Variations on Firewall Architectures
Terminal Servers and Modem Pools
Internal Firewalls
6.1. Single-Box Architectures
The simplest firewall architectures have a single object that acts as the firewall. In general, the security advantage of single-box architectures is that they provide a single place that you can concentrate on and be sure that you have correctly configured, while the disadvantage is that your security is entirely dependent on a single place. There is no defense in depth, but on the other hand, you know exactly what your weakest link is and how weak it is, which is much harder with multiple layers.In practice, the advantages of single-box architectures are not in their security but in other practical concerns. Compared to a multiple-layer system that's integrated with your network, a single-box architecture is cheaper, easier to understand and explain to management, and easier to get from an external vendor. This makes it the solution of choice for small sites. It also makes it a tempting solution for people who are looking for magic security solutions that can be put in once and forgotten about. While there are very good single-box firewalls, there are no magic firewalls, and single-box solutions require the same difficult decisions, careful configuration, and ongoing maintenance that all other firewalls do.
6.1.1. Screening Router
It is possible to use a packet filtering system by itself as a firewall, as shown in Figure 6-1, using just a screening router to protect an entire network. This is a low-cost system, since you almost always need a router to connect to the Internet anyway, and you can simply configure packet filtering in that router. On the other hand, it's not very flexible; you can permit or deny protocols by port number, but it's hard to allow some operations while denying others in the same protocol, or to be sure that what's coming in on a given port is actually the protocol you wanted to allow. In addition, it gives you no depth of defense. If the router is compromised, you have no further security.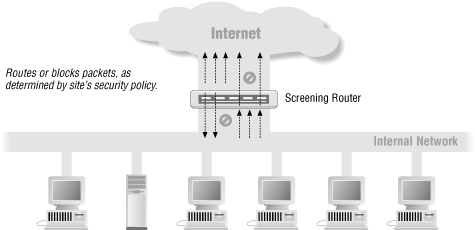
Figure 6-1. Using a screening router to do packet filtering
6.1.1.1. Appropriate uses
A screening router is an appropriate firewall for a situation where:
- The network being protected already has a high level of host security.
- The number of protocols being used is limited, and the protocols themselves are straightforward.
- You require maximum performance and redundancy.
6.1.2. Dual-Homed Host
A dual-homed host architecture is built around the dual-homed host computer, a computer that has at least two network interfaces. Such a host could act as a router between the networks these interfaces are attached to; it is capable of routing IP packets from one network to another. However, to use a dual-homed host as a firewall, you disable this routing function. Thus, IP packets from one network (e.g., the Internet) are not directly routed to the other network (e.g., the internal, protected network). Systems inside the firewall can communicate with the dual-homed host, and systems outside the firewall (on the Internet) can communicate with the dual-homed host, but these systems can't communicate directly with each other. IP traffic between them is completely blocked.Some variations on the dual-homed host architecture use IP to the Internet and some other network protocol (for instance, NetBEUI) on the internal network. This helps to enforce the separation between the two networks, making it less likely that host misconfigurations will let traffic slip from one interface to another, and also reducing the chance that if this does happen there will be vulnerable clients. However, it does not make a significant difference to the overall security of the firewall.
The network architecture for a dual-homed host firewall is pretty simple: the dual-homed host sits between, and is connected to, the Internet and the internal network. Figure 6-2 shows this architecture.
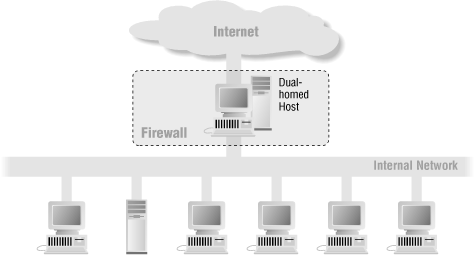
Figure 6-2. Dual-homed host architecture
Dual-homed hosts can provide a very high level of control. If you aren't allowing packets to go between external and internal networks at all, you can be sure that any packet on the internal network that has an external source is evidence of some kind of security problem.On the other hand, dual-homed hosts aren't high-performance devices. A dual-homed host has more work to do for each connection than a packet filter does, and correspondingly needs more resources. A dual-homed host won't support as much traffic as an equivalent packet filtering system.
Since a dual-homed host is a single point of failure, it's important to make certain that its host security is absolutely impeccable. An attacker who can compromise the dual-homed host has full access to your site (no matter what protocols you are running). An attacker who crashes the dual-homed host has cut you off from the Internet. This makes dual-homed hosts inappropriate if being able to reach the Internet is critical to your business.
You are particularly vulnerable to problems with the host's IP implementation, which can crash the machine or pass traffic through it. These problems exist with packet filtering routers as well, but they are less frequent and usually easier to fix. Architectures that involve multiple devices are usually more resilient because multiple different IP implementations are involved.
A dual-homed host can provide services only by proxying them, or by having users log into the dual-homed host directly. You want to avoid having users log into the dual-homed host directly. As we discuss in Chapter 10, "Bastion Hosts", user accounts present significant security problems by themselves. They present special problems on dual-homed hosts, where users may unexpectedly enable services you consider insecure. Furthermore, most users find it inconvenient to use a dual-homed host by logging into it.
Proxying is much less problematic but may not be available for all services you're interested in. Chapter 9, "Proxy Systems", discusses some workarounds for this situation, but they do not apply in every case. Using a dual-homed host as your only network connection actually slightly eases some problems with proxying; if the host pretends to be a router, it can intercept packets bound for the outside world and transparently proxy them without anybody else's cooperation.
Proxying is much better at supporting outbound services (internal users using resources on the Internet) than inbound services (users on the Internet using resources on the internal network). In a dual-homed host configuration, you will normally have to provide services to the Internet by running them on the dual-homed host. This is not usually advisable because providing services to the Internet is risky, and the dual-homed host is a security-critical machine that you don't want to put risky services on. It might be acceptable to put a minimally functional web server on the dual-homed host (for instance, one that was only capable of providing HTML files and had no active content features, additional protocols, or forms processing), but it would clearly be extremely dangerous to provide a normal web server there.
The screened subnet architecture we describe in a later section offers some extra options for providing new, untrusted, or inbound services (e.g., you can add a worthless machine to the screened subnet that provides only an untrusted service).
6.1.2.1. Appropriate uses
A dual-homed host is an appropriate firewall for a situation where:
- Traffic to the Internet is small.
- Traffic to the Internet is not business-critical.
No services are being provided to Internet-based users.
The network being protected does not contain extremely valuable data.
6.1.3. Multiple-Purpose Boxes
any single-box firewalls actually provide some combination of proxying and packet filtering. This gives you many of the advantages of both; you can allow some protocols at high speed while still having detailed control. It also gives you many of the disadvantages of both; you are vulnerable to problems where protocols that you thought were forced through the proxies are simply passed on by the packet filters. In addition, you have all the normal risks of having only a single entity between you and the great outside world.6.1.3.1. Appropriate uses
A single machine that does both proxying and packet filtering is appropriate for a situation where:
- The network to be protected is small.
- No services are being provided to the Internet.


