|
|

This chapter describes the features and components in the Cisco Subscriber Edge Services Manager (Cisco SESM) Release 3.1(1) and Cisco Subscriber Policy Engine (Cisco SPE) Version 1.0. The chapter includes the following topics:
This section introduces the SESM product. It includes the following topics:
The Cisco Subscriber Edge Services Manager (SESM) works in conjunction with other network components to provide extremely robust, highly scalable connection management to Internet services.
Internet service providers (ISPs) and network access providers (NAPs) deploy SESM to provide their subscribers with a web interface for accessing multiple Internet services. The ISPs and NAPs can customize and brand the content of the web pages and thereby control the user experience for different categories of subscribers.
SESM Release 3.1(1) is a solution composed of a number of applications built on a core set of software components. ISPs and NAPs can use these core components to further develop and customize SESM web applications, if required. The Cisco Subscriber Edge Services Manager Web Developer Guide describes how to develop SESM applications.
An SESM solution is deployed with the Cisco Service Selection Gateway (SSG), a Cisco IOS feature on the Cisco 6400 Universal Access Concentrator (UAC). Together, SESM and SSG provide subscriber authentication, service selection, and service connection capabilities to subscribers of Internet services.
Subscribers interact with an SESM web application using a standard Internet browser. They do not need to download any software or plug-ins to use the SESM web pages. After a subscriber successfully authenticates, the SESM web application presents a list of services that the subscriber is currently authorized to use. The subscriber can gain access to one or more of those services by selecting them from a web page. Alternatively, an automatic connection feature might provide automatic connection to services.
SESM Release 3.1(1) web applications deployed in Directory Enabled Service Selection/Subscription (DESS) mode incorporate the use of the Cisco Subscriber Policy Engine (SPE) Version 1.0. The SPE allows subscribers to perform account maintenance and self-care activities, such as subscribing to new services, creating subaccounts (for other members of the family, for example), and changing basic account information, such as address, phone number, and e-mail.
For subscribers of Internet services, an SESM web application offers flexibility and convenience, including the ability to access multiple services simultaneously.
For Internet service providers, an SESM web application provides a way to control the subscriber experience and promote customer loyalty. Service providers can change the look and feel of their SESM web application, brand the application, and control the content of the pages displayed to their subscribers.
 |
Note The SESM product was previously called the Cisco Service Selection Dashboard (Cisco SSD). |
The Cisco Subscriber Policy Engine (SPE) Version 1.0 is a policy server specifically customized to provide granular subscriber service policy. SPE combines role-based access control (RBAC) functionality with an open policy server. Service providers can create differentiated subscriber groups. Service and content providers can use the SPE to provide value added and differentiated services to the subscriber population.
SPE is installed when SESM Release 3.1(1) is deployed in DESS mode to provide the following enhanced features and capabilities:
In the SESM product and its documentation, the SPE components and features are called the DESS components and features.
Figure 1-1 shows the relationship between the SESM and SPE products.

The SESM installation package includes a sample SESM web application, called the New World Service Provider (NWSP), that you can configure and subsequently execute as an example of SESM capabilities. You can create the desired look-and-feel and branded aspects of a customized SESM application by altering the sample application or writing your own application using the NWSP as an example.
The SESM installation package includes a captive portal sample application. This application demonstrates how several powerful features in SESM Release 3.1(1) work together to redirect unauthenticated users to an SESM sign-on page immediately after they open a web browser. See the "Key Features" section for more information about this and other SESM features.
The SESM Release 3.1(1) solution can be deployed in these modes:
The SESM core model implements these modes in a plug-in style. Web developers use the same SESM application programming interface (API) to develop applications intended for either the RADIUS or the DESS modes. Applications intended for DESS mode deployment can include additional features provided by SPE. The Cisco Subscriber Edge Services Manager Web Developer Guide describes how to create applications for both RADIUS and DESS mode deployments.
The deployment option affects the following aspects of product installation and configuration:
See the "SESM in RADIUS Mode" section for more information about the components and data flow in a RADIUS mode deployment.
A DESS deployment requires the Cisco Directory Enabled Service Selection/Subscription (DESS) component. You can install the DESS component from the SESM installation package if your SESM purchase license allows it. The DESS component is the Cisco Subscriber Policy Engine (SPE) Version 1.0, packaged for inclusion in the SESM product package.
See the "SESM in DESS Mode" section for more information about the components and data flow in a DESS mode deployment.
J2EE Server
SESM web applications are J2EE applications, requiring a J2EE-compliant server.
See the "Host Key Feature on SSG" section before deploying a J2EE server other than the Jetty server.
JMX Server
SESM web applications require the services of a Java Management Extensions (JMX) server.
The installed NWSP sample application, the configuration files, and the startup scripts are set up to use the Sun example JMX server from Sun Microsystems. The SESM installation program installs the JMX server along with the Jetty server. If desired, web developers at your site can deploy a JMX-compliant server other than the Sun example server.
This section describes the network software that is required in an SESM deployment but is not provided by the SESM installation package.
The Cisco Service Selection Gateway (SSG) is a software feature module embedded in Cisco IOS software running on the Cisco 6400 Universal Access Concentrator (UAC). Each node route processor on the Cisco 6400 UAC can host an SSG. The SSG configured with the Web Selection option works in conjunction with SESM.
SSG performs authentication and service connection tasks on behalf of an SESM application.
SESM Release 3.1(1) requires the SSG feature set embedded in Cisco IOS Release 12.1(5)DC1 or later. For information about this release of SSG, see the following documents.
The "Related Documentation" section provides URLs to the online location of these documents.
Regardless of the SESM deployment mode (RADIUS or DESS), SSG and an SESM web application communicate using the RADIUS protocol.
The host key feature provides the following advantages to SESM applications:
 |
Note The host key feature is planned for general availability in Cisco IOS Release 12.2(2)B. |
When host key is enabled on the SSG, the SSG preserves the port number of the incoming HTTP request. This remote port number becomes the key that uniquely identifies each subscriber. The key is included in the request that is forwarded to the SESM web application.
The following scenarios require a RADIUS server:
SESM works with any RADIUS server that accepts vendor-specific attributes (VSAs). The VSAs define the subscriber and service profile information required in the SESM deployment. The Cisco Access Registrar is a carrier class RADIUS platform that is fully tested with SESM. See the "Configuring Cisco Access Registrar for SESM Deployments" section for more information about using Cisco Access Registrar in SESM deployments.
Also see the following references for more information about configuring a RADIUS server in an SESM deployment:
An LDAP directory allows interactive updates, a feature that is not supported by a RADIUS server. The DESS mode uses this update capability to offer SESM features that the RADIUS mode cannot provide, such as:
Table 1-1 describes the key features in SESM Release 3.1(1). For information about how to enable and configure these features, see Table 4-9.
| Feature | Description |
|---|---|
Multiple Internet service selection | An SESM web application provides a web portal from which subscribers can:
An SESM web application works in conjunction with SSG to authenticate the subscriber, to obtain the list of services that the subscriber is authorized to use, and to obtain session status information. The SESM application sends service connection requests to SSG, which makes the actual connection. |
JSPs provide a standard way to integrate Java code with HTML to present interactive, dynamically updated, personalized, and branded web pages to your subscribers. | |
Walled gardens, open gardens, retail pages, and service advertisements | The following features are implemented through the use of customized JSPs:
|
Captive portal | This feature works with the TCP redirect feature on the SSG to redirect HTTP requests for unauthenticated subscribers.
|
An SESM web application can detect a subscriber's preferred locale, device and browser type, and connection location and respond with web pages appropriate to the subscriber's preferred language, device capabilities, and connection type. | |
This feature offers a streamlined login procedure in a PPP network. A subscriber who logs on using a PPP client can access the SESM without having to re-enter the username and password. | |
This feature on the SSG ensures that each currently logged-on subscriber is uniquely identified, regardless of the IP address being used. This SSG feature allows SESM applications to support the following types of subscribers:
This feature also enhances scaling and configuration of large SESM deployments. | |
Highly scalable | An SESM web server application is highly scalable in the following ways:
|
| The following features are provided by SPE and are available only when SESM is deployed in DESS mode. | |
Subscriber account self care | This feature allows subscribers to change their own account details, such as address information and passwords. This subscriber updating capability relieves the service provider from time-consuming maintenance tasks. The NWSP sample application illustrates this feature. |
Subscriber service subscription | This feature allows subscribers to subscribe to new services and have immediate access to those services. This feature relieves the service provider from time-consuming service enrollment tasks. It also benefits the subscriber because there is no delay in receiving access to a new service. Subscribers can also unsubscribe from a service. The NWSP sample application illustrates this feature. |
Subscriber subaccount creation and management | This feature allows a subscriber with a main account to create subaccounts, with different services and access information in each subaccount. For example, a family might have subaccounts for each family member, with a different set of authorized services within each subaccount. The main account can create and delete subaccounts and subscribe to services for the subaccounts. The NWSP sample application illustrates this feature. |
Cisco Distributed Administration Tool (CDAT) | CDAT is a web-based application for administrators to use in creating and maintaining the information on users, services, and access policy that is stored in an LDAP directory. The CDAT application is described in the Cisco Distributed Administration Tool Guide. |
Role based access control (RBAC) | RBAC is an access model that allows administrators to manage groups of subscribers, rather than individuals. Using the RBAC model, administrators define roles, which have specific privileges, and groups, which have assigned roles. Individual subscribers are then assigned to a group and inherit the roles of that group. The Cisco DESS and AUTH APIs implement the RBAC model. See the Cisco Distributed Administration Tool Guide for more information about RBAC. |
Accounting and Billing Features
Figure 1-2 shows an SESM deployment in an ISP or NAP communication network.
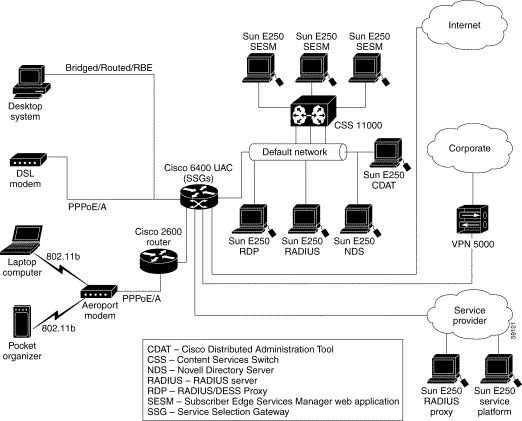
Regardless of the type of modem or connection layer protocol a subscriber uses, all TCP packets are routed by the SSG when the SSG is enabled. The SSG is a feature in the Cisco IOS running on the node route processors (NRPs) on the Cisco 6400 UAC. Each NRP has an SSG separately enabled. Therefore, a typical production deployment includes multiple SSGs.
Physically, the TCP traffic passes through the SSG on its way to SESM. Logically the HTTP traffic goes directly to an SESM web application running on a default network. The default network is an IP address or subnet that TCP packets can access without authentication. The SESM web applications and their associated J2EE web servers run in this default network. The default network is configured on the SSG.
Production deployments might include multiple instances of J2EE web servers and associated SESM web applications on the default network. For production deployments, we recommend using enterprise-class server systems with hot-swappable components and load-balancing across the multiple servers. The Domain Name System (DNS) resolves host names for any of the SESM web applications to the IP address of the load balancer. The Cisco Content Services Switch 11000 (CSS 11000) is preferred for load balancing.
The J2EE web servers receive the HTTP requests for the SESM web application. The SESM web application works with an SSG to establish a session for the user. SESM determines the IP address of the SSG that should handle the session as follows:
An SESM Release 3.1(1) web application is highly scalable. You can start and stop instances of SESM web applications without affecting subscribers. This is because an SESM application is completely stateless. It does not store any subscriber session information. Rather, the SESM application queries SSG for session state information.
This section describes how various access methods connect to an SESM web application.
Point-to-Point Protocol Example
This example describes the connection sequence for Point-to-Point Protocol (PPP) access to SESM. For example, consider a DSL subscriber using a PPP client configured on a laptop computer.
1. The subscriber launches the PPP client.
2. The TCP packet travels to the NRP on the Cisco 6400, which has SSG enabled.
3. The SSG on the NRP authenticates the PPP user.
4. The subscriber launches a web browser and sends an HTTP message.
5. The TCP packet containing the first HTTP request travels through the SSG, to the SSG's default network, to the J2EE web server and the SESM application.
6. If the SESM single sign-on feature for PPP subscribers is enabled, the user is already authenticated and SESM does not request an additional authentication. Rather, SESM queries the SSG for the subscriber's cached profile. A session is established, and SESM returns the subscriber's home page with a list of authorized services.
7. If the SESM single sign-on feature is disabled, or if PPP authentication failed in step 6, SESM returns the SESM logon page. When this request reaches an SESM web application, the application requests authentication services from the SSG. After the subscriber is authenticated, a session is established.
Routed Example
This example describes the connection sequence for a routed access to SESM, which includes the RFC1483 routed access method and the Routed Bridged Encapsulation (RBE) access method.
1. The subscriber launches a web browser and sends an HTTP message.
2. The TCP packet containing the first HTTP request travels through the SSG, to the SSG's default network, to the J2EE web server and the SESM application.
3. SESM returns the SESM logon page.
4. When SESM receives the subscriber's logon information, it requests authentication services from the SSG. After the subscriber is authenticated, a session is established.
This section describes SESM deployment in RADIUS mode. It includes the following topics:
Figure 1-3 shows a simplified view of SESM deployed in RADIUS mode and the communication mechanisms used between the various software components.
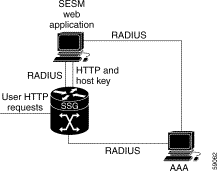
SSG and the SESM web application work together to process subscriber requests.
Table 1-2 describes the role of SESM applications and SSG in processing typical subscriber actions in a RADIUS deployment.
| Subscriber Action | Software Activity | Components Involved |
|---|---|---|
Subscriber logs on | Authenticate the subscriber in the system. | The SESM application initiates authentication by sending a message to SSG, using the RADIUS protocol. SSG forwards the RADIUS message to the RADIUS server. The RADIUS server authenticates the user and returns a message containing information from the subscriber's user profile. SSG creates an internal host object that represents the subscriber in the current session and forwards the message to SESM. |
Display web interface containing customized content appropriate for the logged on subscriber. | The RADIUS message contains the subscriber's user profile as stored in the RADIUS database. SESM can analyze the user profile and send appropriate content accordingly. | |
Display the list of services that the subscriber is currently authorized to access. | The RADIUS message contains the list of services from the subscriber's profile. Authorization is implied for all services in the list. The SESM application obtains a service profile directly from the RADIUS server for each service in the list. | |
Subscriber selects a service | Access the service. | SESM sends a connection request to SSG. SSG creates a connection object, connecting the host object to the service. When the service is connected, SSG creates a service object. SSG then switches traffic from that subscriber to the requested service. |
Subscriber selects a second service | Access a second service, without reauthentication. | The SESM application sends the request to the SSG. SSG creates a second connection object and service object. Both services are concurrently accessed. |
Subscriber deselects a service | Stop access to the service. | The SESM application sends the request to the SSG. SSG destroys the appropriate connection object. |
Table 1-3 summarizes the steps required to deploy SESM in RADIUS mode.
| Activity | Reference |
|---|---|
1. Install and configure a RADIUS AAA server. | "Configuring RADIUS" and documentation from the RADIUS server vendor |
2. Ensure that all Node Route Processors (NRPs) performing the SSG function are running Cisco IOS Release 12.1(5)DC1 or later. | Cisco 6400 NRP—Release Notes for Cisco IOS Release 12.1(5)DC 1 |
3. Configure SSG. Use Cisco IOS commands on the SSG host to:
|
Cisco 6400 Command Reference Guide1 |
4. Install and configure the SESM, which includes the NWSP sample application and a Jetty web server. | |
5. Create user and service profiles in the RADIUS database. | "Configuring RADIUS" and documentation from the RADIUS server vendor |
| 1See the "Related Documentation" section for links to the online versions of these documents. | |
This section describes SESM deployment in DESS mode. It includes the following sections:
Figure 1-4 shows a simplified view of SESM deployed in DESS mode and the communication mechanisms used between the various software components.
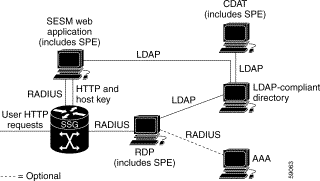
The optional AAA server might provide the following services:
For more information about SPE, including its logical relationship to SESM components, see the "Cisco Subscriber Policy Engine" section.
Table 1-4 describes the role of SESM applications and SSG in processing typical subscriber actions in a DESS deployment.
| Subscriber Action | Software Activity | Components Involved |
|---|---|---|
Subscriber logs on | Authenticate the user in the system. | The SESM application initiates authentication by sending a RADIUS message to SSG. SSG forwards the RADIUS message to the RDP. The RDP can authenticate using RADIUS or the LDAP directory, depending on how the RDP is configured:
The response is returned to the SESM application following the same path. SSG creates an internal host object that represents the subscriber in the current session. |
Display appropriate web pages to user. | After the subscriber is authenticated, the SESM application uses the DESS API to retrieve a user profile from the LDAP directory. The SESM application can analyze the profile and display appropriate web pages. | |
Display the list of services in the subscriber's profile. | The SESM application uses the DESS API to retrieve service profiles from the LDAP directory for each service in the list. | |
Subscriber selects a service | Access the service. | SSG sends an authorization request to RDP. Regardless of the RDP mode, RDP always uses the DESS API to send service authorization requests to the LDAP directory. If the service is authorized, SSG creates an internal connection object, connecting the host object to the service. When the service is connected, SSG creates a service object. SSG then switches traffic from that subscriber to the requested service. |
Subscriber selects a second service | Access a second service without reauthentication. | SSG sends another authorization request to RDP. Regardless of how it mode, RDP always uses the DESS API to send service authorization requests to the LDAP directory. If the service is authorized, SSG creates a second connection object and service object. Both services are concurrently accessed. |
Subscriber updates an e-mail address | Update the LDAP directory. | The SESM application sends the update to the directory using the DESS API. |
Subscriber creates a subaccount | Update the LDAP directory. | The SESM application sends the update to the directory using the DESS API. |
Subscriber deselects a service | Terminate access to the service. | The SESM application sends the request to the SSG. SSG destroys the appropriate connection object. |
Table 1-5 summarizes the installation and configuration activities for SESM in DESS mode.
| Activity | Reference |
|---|---|
1. (Optional) Install and configure a RADIUS server if:
| "Configuring RADIUS" and documentation from the RADIUS server vendor |
2. Ensure that all Node Route Processors (NRPs) performing the SSG function are running Cisco IOS Release 12.1(5)DC1 or later. | Cisco 6400 NRP - Release Notes for Cisco IOS Release 12.1(5)DC 1 |
3. Configure SSG. Use SSG commands on the SSG host to:
|
Cisco 6400 Command Reference Guide1 |
4. Install and configure an LDAP directory. Note If you are using NDS, you must enable the cleartext password option. | Documentation from the directory vendor |
5. Install and configure the SESM software components, which include: the NWSP sample application, Jetty web server, RDP, DESS, and CDAT. | |
6. Create roles, groups, and user and service profiles in the LDAP directory. | Cisco Distributed Administration Tool Guide |
| 1See the "Related Documentation" section for links to the online versions of SSG documents. | |
This section describes the components that you can install from the SESM installation package.
When you install the NWSP component, the installation program prompts you to choose a deployment mode. The installation program then installs and configures software appropriate for that mode. In SESM Release 3.1(1), the modes are Demo mode, RADIUS mode, and DESS mode.
An installation of the NWSP component installs the following items:
See the Cisco Subscriber Edge Services Manager Web Developer Guide for information about developing a customized SESM application. Use the configuration information in "Configuring Components after Installation," to deploy and configure the customized application.
The captive portal sample application demonstrates how several powerful features in this SESM release work together to redirect unauthorized users to an SESM sign-on page immediately after opening a web browser. With this feature, the service provider does not need to provide users with the URL to the SESM sign-on page.
This section defines the differences between a sample and a demo application.
SESM Sample Application
An SESM sample application is a fully functioning web application that was built using the SESM development library. It uses the services of the Jetty web server and the JMX management server. Before running the sample application, you need all other solution components installed and configured. For example, you need a fully configured SSG component running on a Cisco 6400 UAC. The RADIUS server (for RADIUS mode) or the LDAP-compliant directory (for the DESS mode) must be installed, configured, running, and populated with user and service information.
Demo Mode
 |
Note If you install the Demo mode, and then later want to perform some development on a customized SESM application, we recommend that you perform another installation. Otherwise, you will need to perform extensive edits to the MBean configuration files. |
Demo mode simulates the actions of an SESM deployment in both RADIUS and DESS modes. It uses a local copy of a Merit RADIUS file to obtain profile information. See "Demo Quick Start," for information about installing and using SESM in Demo mode.
When you install the jetty component from the SESM installation package, you install the following items:
The NWSP application, CDAT, and RDP are installed with configuration files and startup scripts that are ready to run using the Jetty web server and the Sun example JMX server. However, SESM is designed to allow the use of any J2EE web server and any JMX-compliant server. An SESM web application, such as the NWSP sample application, requires an HTTP listener (web server) and a JMX server.
 |
Note For SESM Release 3.1(1), the host key feature works only with a Jetty server. |
When you install the directory-enabled service selection (DESS) component from the SESM installation package, you install the following items:
See the Cisco Distributed Administration Tool Guide for information about the RBAC model, the DESS and AUTH extensions to an LDAP directory, and how to develop subscriber and service profile information in the RBAC model.
The RADIUS/DESS Proxy (RDP) server is a RADIUS server that can proxy profile requests or use the DESS APIs to query the directory for profiles. RDP acts as the mediator between SSG, which communicates using RADIUS protocol messages, and the LDAP directory schema extensions, which require the DESS API for communication. RDP is a required component in the deployment of SESM in DESS mode.
You can configure the RDP to run in two modes:
RDP is a Java2 application that uses the services of a JMX server for configuration.
The Cisco Distributed Administration Tool (CDAT) is an administrator's web-based interface for managing data in the DESS and AUTH extensions to the LDAP directory. CDAT provides the means for creating and maintaining users, services, user groups, service groups, roles, and policy rules for the RBAC model.
CDAT, a J2EE application, runs on a J2EE server and uses the services of a JMX server for configuration.
This guide describes how to install and configure CDAT. For information about using CDAT, creating profiles in the RBAC model, and the DESS and AUTH directory extensions, see the Cisco Distributed Administration Tool Guide.
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
Posted: Wed Jul 24 12:07:11 PDT 2002
All contents are Copyright © 1992--2002 Cisco Systems, Inc. All rights reserved.
Important Notices and Privacy Statement.