|
|

June 11, 2001
 |
Note The most current Cisco documentation for released products is available at Cisco.com at http://www.cisco.com. The online documents may contain updates and modifications made after the hardcopy documents were printed. |
These release notes for Cache software, Release 3.1.1 contain new and updated information, particularly in reference to features added since Release 3.0.1. They also contain installation instructions and information about known caveats.
 |
Note If you plan to upgrade from Cache software Release 2.x, verify that the features you require are in Release 3.1.1 before performing the upgrade procedure. See "Release 3.1.1 Feature Set" section 2. |
Cisco Cache software, Release 3.1.1, can operate on Cisco Content Engine 507, 560, 590, and 7320 models.
 |
Note The Content Engine 560 can operate a maximum of five 18-GB SCSI disk drives running Release 3.1.1. |
To determine the version of the software currently running on the Cisco Content Engine, log on to the Content Engine and enter the show version EXEC command.
See the "Installation Notes" section for procedures on how to upgrade to Release 3.1.1 software.
 |
Note If you plan to upgrade from Cache software Release 2.x, verify that the features you require are in Release 3.1.1 before performing the upgrade procedure. See "Release 3.1.1 Feature Set" section 2. |
This section contains:
The following table lists the principal features of Cache software, Release 3.1.1, and the associated command-line interface (CLI) commands.
 |
Note You must purchase a license key in order to activate the RealProxy features in the Cache software. |
| Cisco Cache Software, Release 3.1.1 Feature | Related CLI Commands |
|---|---|
| Streaming media splitting and caching |
|
RealProxy 8.0 support | disk |
Content preloading | pre-load |
| Proxy-style caching (nontransparent operation) | |
Hypertext Transfer Protocol (HTTP) proxy caching | http proxy incoming |
File Transfer Protocol (FTP) proxy caching | ftp proxy incoming |
Secure Shell (SSL) tunneling | https proxy incoming |
| Transparent caching | |
Transparent caching with the | http l4-switch enable |
Transparency through WCCP | wccp |
Accelerated WCCP Layer 2 support | wccp custom-web-cache |
Authentication bypass | bypass auth-traffic |
Overload bypass | bypass load |
Static bypass | bypass static |
Multiport transparent redirection | proxy-protocols |
WCCP flow protection | wccp slow-start |
| Logging | |
Squid-style transaction logging | transaction-logs |
Sanitized transaction logs | transaction-logs sanitize |
Pushing of log files | transaction-logs export |
| Cache hierarchy features | |
Outgoing Proxy | http proxy outgoing |
Internet Cache Protocol (ICP) | icp |
| Management features | |
Administration from GUI | gui-server |
Administration from CLI | trusted-host |
Boot from Flash memory | copy |
SNMP agent (MIB II and CE-MIB support) | snmp-server community |
SNMP traps | snmp-server enable traps |
Syslog | logging |
NTP time syncing | ntp |
| Cache parameter settings |
|
Cache freshness | http min-ttl |
Caching of content with cookies | http cache-cookies |
Object size capping | http object |
Selective abort of object downloading on client-abort (also called "quick_abort") | http cache-on-abort |
| Rules template | rule |
| TCP stack parameters |
|
User-configurable TCP parameters | tcp |
TCP-over-satellite extensions | tcp client-satellite |
| Miscellaneous features | |
Embed client information in HTTP headers | http append |
Microsoft NT LAN Manager (NTLM) authentication transparency | http authenticate-strip-ntlm |
The following features have been included in prior releases of the Cisco Cache Software, but are not included in the current Release 3.1.1:
The following features were added in Cache software, Release 3.1.1:
 |
Note You must purchase a license key in order to activate the RealProxy features in the Cache software. |
Cisco Cache software, Release 3.1.1, optionally includes the RealProxy from RealNetworks, Inc. to support both stream splitting (distributing "live" feeds) and streaming media caching (on-demand content) in both Real-Time Streaming Protocol (RTSP)-based streaming and other Real PNM (RealNetworks metafile) formats.
When performing stream splitting, the RealProxy accepts a "live" stream from a RealServer and re-serves the stream to multiple requesting RealPlayer clients, thus eliminating multiple connections to the RealServer. The RealServer is preconfigured to act as a RealMedia transmitter and the RealProxy is preconfigured to act as a RealMedia receiver.
Streaming media caching provides content on demand. If one user has viewed a cached streaming media file, it can be served to subsequent users without the requirement to connect with the origin server. Live broadcasts are not files and are not cached.
Use the rtsp proxy global configuration command to configure the Content Engine to accept redirected RTSP traffic or to configure the Content Engine as a media proxy to receive RTSP proxy-style requests from RealPlayer clients. The wccp media-cache global configuration command registers the Content Engine with Web Cache Communication Protocol (WCCP) version 2-enabled routers that can transparently redirect RTSP traffic to the Content Engine. Streaming media objects are cached in the media file system (mediafs) disk partitions. The RealProxy software is copied to the software file system (swfs) partition as part of the installation procedure. Use the disk EXEC command to create swfs and mediafs partitions. Use the mediafs EXEC command to maintain the mediafs partitions. For further information on disk partitions (swfs, mediafs, sysfs, and cfs), and the installation process, see the "Installation Notes" section.
RealProxy software is configured with the RealSystem administrator GUI, accessed from the RealProxy page of the Content Engine management GUI.
Table 1 describes the features and benefits of RealProxy software.
| RealProxy Feature | Description | Benefits |
|---|---|---|
Proxy for RealPlayer 8.0 | RealProxy makes requests for content on behalf of client RealPlayer users. |
|
Splitting support for live broadcasts | RealProxy "splits" a single inbound live broadcast feed to multiple client RealPlayers. |
|
Caching of RealSystem G2 and PNM content | RealProxy caches all proxied streaming media traffic from RealNetworks servers. RealProxy caches content locally after authentication with origin RealNetworks server. | Significantly reduces inbound bandwidth usage by eliminating redundant file transmissions across the network. |
Authentication/accounting | RealProxy authenticates every content request with the origin RealNetworks server before delivering the cached content to the client. |
|
Aggregate bandwidth thresholds | Thresholds cap inbound and outbound bandwidth to RealProxy. | Provides control over aggregate bandwidth usage within the network and prevents stress on mission-critical applications. |
Proxy routing | Ability to tier proxies and manage bandwidth at lower nodes in the network. "Parent" proxies can be chosen based on logical sets of rules on the downstream proxy. | Allows network administrators to proxy route requests, providing an additional level of control. |
Cisco Cache software, Release 3.1.1, can read a file of URLs and download the specified content into the Content Engine. This preloading can be scheduled with the pre-load schedule global configuration command, or triggered immediately with the pre-load force EXEC command.
The Rules Template feature allows for requests to be matched using an arbitrary number of parameters with an arbitrary number of policies applied against the matches. Requests can be matched against regular expressions symbolizing domain names, source IP addresses and network masks, destination IP addresses and network masks, destination port numbers, MIME-types, or regular expressions symbolizing a URL.
Policies that can be applied include blocking the request, using a specific object freshness calculation factor, not caching an object, bypassing an upstream proxy for the request, redirecting the request to a different URL, revalidating the object with the origin server, rewriting the URL, selectively caching the object, using a specific upstream proxy, or using a specific server for the request.
The options freshness-factor, redirect, rewrite, and use-server were not included in Cache software, Release 2.3.0, which is the release prior to Release 3.1.1 that includes the Rules Template feature.
Support for streaming protocols (such as RTSP and Real-Time Protocol [RTP]) is not implemented in Release 3.1.1, although RealProxy can use source-IP-based block and allow configurations to restrict client access.
Proxy protocols such as HTTP, FTP, and HTTPS are supported, but not on a per protocol basis.
The multiport feature can be summarized as follows:
The proxy incoming option of the http, https, ftp, and rtsp global configuration commands now support up to eight ports per protocol.
The multiport feature requires WCCP Version 2. The wccp port-list and the wccp service-number global configuration commands were added to the CLI to enable transparent redirection of HTTP, HTTPS, FTP, and RTSP traffic.
 |
Note DNS must be configured in order to support incoming HTTPS proxy requests |
There are two basic styles in which requests may be received: transparent and proxy-style. In addition, transparent requests have two distinct subcases depending on the addressing style within the message. There are no restrictions that prevent any of these styles of requests from coming in or being serviced on any of the ports as described.
A proxy style request arrives with the same IP address as the Content Engine; it has been specifically routed to that device by the client. A proxy-style URL (including the protocol and full path of the URL) is included in the request. In this mode, the Content Engine services any protocols it understands and for which it has been configured. The currently understood protocols are HTTP, HTTPS, and FTP.
A request redirected to the Content Engine from a router is called transparent. Transparent and proxy-mode requests may be distinguished by comparison of the destination IP address of the request and the IP address of the Content Engine. A nonmatching IP indicates that the request has been redirected and is therefore transparent. The style of the URL within the request may be proxy-style or server-style (that is, the URL does not include the protocol and host name). In general, transparent requests have a server-style URL, but proxy-style ones may also be received: for example, when the Content Engine is intercepting a request destined for a proxy. If a server-style URL is received, only HTTP is supported. However, if a proxy-style URL is received, all of the protocols understood by the Content Engine are supported.
WCCP (Web Cache Communication Protocol) is used to communicate the Content Engine configuration for transparent mode to the associated router(s). WCCP defines up to eight services, in which each service may have an associated list of ports, list of routers, and hash method. The hash method determines how URLs are redirected by the router to Content Engines in a cache farm.
The WCCP services are numbered from 90 to 100 (11 total), of which 8 services may be active at a time. The services from 98 through 100 have specific labels and may not be modified. The remaining services are configurable by the user. WCCP allows for a priority to be included with each service, but these priorities are fixed for services configured from the Content Engine. Service 90 has the lowest priority, whereas service 100 has the highest.
At most eight WCCP services may be active at once. For each service, at most eight ports may be active.
Some ports are already in use for various features or system services (DNS, FTP server, and so forth). These ports should not be configured for proxying or transparent services.
The http proxy outgoing option can configure up to eight backup proxy servers. One proxy server functions as the primary proxy server, and all requests are redirected to it. If the primary proxy server fails to respond to the HTTP CONNECT, the server is noted as failed, and the requests are redirected to the next outgoing proxy server until one of the proxies services the request. This is currently available only for HTTP, not for HTTPS and FTP. Cache software, Release 3.1.1, also permits the specification of up to eight ports to receive incoming HTTP incoming proxy requests.
Accelerated WCCP is a generic term for a deployment in which WCCP on a router or switch can take advantage of switching hardware that either partially implements the traffic intercept or redirect function of WCCP in hardware (ASICs) or fully implements traffic intercept or redirect function in hardware at layer 2.
The Content Engine must have a direct physical connection with the router or switch. Related commands are wccp custom-web-cache, wccp media-cache, wccp reverse-proxy, wccp service-number, and wccp web-cache. The following are examples of CLI output that displays the Layer 2-redirect option:
cache(config)# wccp web-cache router-list-num 1 ?
l2-redirect WCCPv2 forwarding encapsulation method
password Authentication password (key)
weight Weight Percentage
<cr>
cache(config)# wccp web-cache router-list-num 1 l2-redirect ?
password Authentication password (key)
weight Weight Percentage
<cr>
The Content Engine using Cache software, Release 3.1.1, serves HTTP Range requests from the cache if the requested range exists in the Content Engine cache. Specifically, the Content Engine handles range request with the following logic:
lookup the object in the cache;
if object in the cache
{
check whether the requested ranges are in the cache;
if the requested ranges are in cache then serve the request from cache;
else pipe through the request;
}
else pipe through the request;
 |
Note The If-Range header is not fully supported. If a request has an If-Range header, it is piped through to the server even if the requested object is in the cache. |
The http cache-on-abort feature must be disabled for this feature to operate. Some client applications close the server connection immediately after receiving the response header for the normal GET request (for example, to a .pdf file ). If the http cache-on-abort is configured to not cache aborted objects, later range requests to that object will not hit in the cache at all.
Cisco Cache software, Release 3.1.1 is available to download from Cisco.com.
Cache software, Release 3.1.1, introduces optional software that requires the creation of two new types of disk partitions. The new disk partitions in Release 3.1.1 are the swfs (software file system), and mediafs (media file system) partitions. The swfs partition is factory installed for Content Engines shipped with Release 3.1.1, but must be created when upgrading from Release 2.x or 3.0.x. The mediafs partitions can be created as necessary.
This section contains the following:
 |
Note Refer to the Cisco Cache Software Configuration Guide, Release 3.1.1 for information on configuring optional software and standard Cache software features, and for instructions on booting the Content Engine in the event that a software upgrade fails. |
Use the procedure in this section to install more recent images of the Release 3.1.1 Cache software on a Content Engine already running a version of Release 3.1.1.
The requirements for this upgrade are:
 |
Note A full Release file comprises the 3.1.1 operating system, Management GUI, and all optional software. |
This section explains how to install a Release 3.1.x system image on a Content Engine running Release 3.1.1, with the assumption that all disk partitions remained unchanged.
Step 1 Log in to the Content Engine through Telnet or the console port.
 |
Note A console port connection is required if you are changing the basic startup configuration. The Telnet session is disconnected when the Content Engine reboots. |
Step 2 Save the current system configuration to Flash memory.
ContentEngine# copy running-config startup-config
Step 3 Verify that the present working directory is local1 or local2.
ContentEngine# cd /local1
ContentEngine# pwd
/local1
Step 4 Download the Release 3.1.x image from an FTP server to the Content Engine /loca1 or /local2 directory.
In the following example, the image file, ce590-311_FCS.bin, is downloaded from the /images directory of FTP server 172.16.8.9.
ContentEngine# copy ftp disk 172.16.8.9 /images ce590-cache-31x.bin
Enter username for remote ftp server: my_ftpserver_username
Enter password for remote ftp server: my_ftpserver_password
Step 5 Install the Release 3.1.x software with the install EXEC command.
The install command copies a new system image to Flash memory, and installs the optional software on the swfs partition. In the following example, the full release image file is in the sysfs directory /local1.
ContentEngine# install /local1/ce7320-cache-31x.bin
Step 6 Reboot the Content Engine.
ContentEngine# reload
Proceed with reload?[confirm] yes
For information on installing optional software, refer to Chapter 3 of the Cisco Cache Software Configuration Guide, Release 3.1.1.
The upgrade of a Release 3.0.x image to a Release 3.1.1 image is a three-part process as follows:
1. Copy a Release 3.1.x Flash memory-only image to Flash memory.
2. Boot with the Flash memory-only image, reformat the disk drives, and then copy the full Release 3.1.x image to a local disk.
3. Install the full Release 3.1.1 image.
Select the image file appropriate to the model of the Content Engine. The Flash memory-only file contains the Release 3.1.1 operating system only. The Release 3.1.1 full-release file contains Release 3.1.1 operating system and optional software.
Step 1 Log in to the Content Engine through Telnet or the console port.
 |
Note A console port connection is required if you are changing the basic startup configuration. The telnet session is disconnected when the Content Engine reboots. |
Step 2 Save the current system configuration to Flash memory.
ContentEngine# copy running-config startup-config
Step 3 If you wish to retain any sysfs files (such as the transaction logs) from Release 3.0.x disks, create a sysfs disk on disk01, and copy any log files from disk00 to disk01. All contents of disk00 will be erased as part of the upgrade procedure.
Step 4 Download the Release 3.1.1 Flash memory-only image file to a Windows NT, LINUX, or UNIX host that is running an FTP server.
Step 5 Perform the following substeps to copy the Release 3.1.1 Flash memory-only image file from an FTP server to the Content Engine Flash memory. In this example, the FTP server has the IP address 192.168.88.89 with the Flash memory-only system image file (ce7320-31x.flash) located in the /images directory:
a. At the EXEC command line of your Content Engine, enter the following:
ContentEngine# copy ftp flash 192.168.88.89 /images ce7320-31x.flash
b. Enter your FTP username and password when prompted:
Enter username for remote ftp server: my_ftpserver_username
Enter password for remote ftp server: my_ftpserver_password
Initiating FTP download. . .
Downloaded 10685440 byte image file
A new system image has been downloaded.
You should write it to flash at this time.
Write to flash [yes]: _
c. To write the new system image to Flash memory, press Enter to accept the default (yes) or enter yes.
Ok, writing new image to flash. . . . . . . . . . . . . . . . . . . . . . . . . . . .
. . . . . . . . . . . .
d. Reboot the Content Engine with the reload EXEC command.
ContentEngine# reload
Proceed with reload?[confirm] yes
After the reboot, the following message appears for each existing disk partition, indicating the conversion of the Release 3.0.x disk signature to the 3.1.1 format:
Converting disk signature format from 3.0 to 3.1:mydisk00
Cisco Content Engine Console
Step 6 Log in as admin.
Username: admin
Step 7 Configure the device with the basic startup parameters.
This step occurs only when the device does not have a saved configuration file (such as a new device). The following lines show an example of an interactive session from a Content Engine 590.
You may use Ctrl-D to abort Configuration Dialog at any prompt.
Would you like to enter the initial configuration?[yes]:yes
host name:mycontentengine
Admin password:mypassword
Please enter an interface from the following list:
0:FastEthernet 0/0
1:FastEthernet 0/1
enter choice:0
cache IP address: 10.1.1.1
IP network mask:255.255.0.0
Gateway IP address: 10.1.1.2
Use this configuration? [yes]:yes
Step 8 Erase all partitions on disk00 with the disk erase-all-partitions EXEC command.
ContentEngine# disk erase-all-partitions disk00
Step 9 Create the swfs disk partition with the disk recover EXEC command.
ContentEngine# disk recover
The swfs partition is created on disk00.
Step 10 Partition, format, and mount a sysfs partition.
A sysfs partition on a disk other than disk00 may already exist from Release 3.0.x. The sysfs partition is the repository for various log files (syslog, error log, and transaction logs). The full-release image file is downloaded to this partition. In the following example, a sysfs partition named disk00/01 is allocated 25 percent of the total disk and mounted at /local1. For further information on sysfs, refer to the "Maintaining the Hard Disk Storage" section in Chapter 2 of the Cisco Cache Software Configuration Guide, Release 3.1.
ContentEngine# disk partition disk00/01 25% sysfs
ContentEngine# sysfs format disk00/01
ContentEngine# sysfs mount disk00/01 local1
Step 11 Partition, format,and mount the mediafs disk partitions.
The mediafs partitions are used by the RealProxy to cache streaming objects. The mount point for this partition (like the cfs partition) is not visible to the user. The following example demonstrates how a mediafs partition of 10 GB is formatted and mounted as one of the partitions on disk03. For further information on mediafs, refer to the "Maintaining the Hard Disk Storage" section in Chapter 2 of the Cisco Cache Software Configuration Guide, Release 3.1.1.
ContentEngine# disk partition disk03/01 10g mediafs
ContentEngine# mediafs format disk03/01
ContentEngine# mediafs mount disk03/01
Step 12 Verify that the present working directory is local1 or local2.
ContentEngine# cd /local1
ContentEngine# pwd
/local1
Step 13 Download the full-release image file to the sysfs directory with the copy ftp disk EXEC command.
In the following example, the full-release image file ce7320-cache-31x.bin is downloaded from the /images directory of the FTP server 176.16.8.9:
ContentEngine# copy ftp disk 176.16.8.9 /images ce7320-cache-31x.bin
Enter username for remote ftp server: my_ftpserver_username
Enter password for remote ftp server: my_ftpserver_password
Step 14 Install the full-release image software with the install EXEC command.
The install command copies a new system image to Flash memory, and installs the optional software on the swfs partition. In the following example, the full Release 3.1.1 image file is stored in the sysfs directory /local1.
ContentEngine# install /local1/ce7320-cache-31x.bin
Step 15 When the CLI prompt reappears, reboot the Content Engine with the reload EXEC command. Enter yes to confirm.
ContentEngine# reload
Proceed with reload?[confirm] yes
Step 16 Set the system clock if necessary with the clock set EXEC command.
ContentEngine# clock set 14:22:00 24 Jan 2001
WARNING: Setting the clock may cause a temporary service interruption.
Do you want to proceed?[no] yes
Mon Jan 24 14:22:00 EST 2001
ContentEngine#
For information on installing optional software, refer to Chapter 3 of the Cisco Cache Software Configuration Guide, Release 3.1.1.
 |
Note Verify that the features you require are in Release 3.1.1 before performing the upgrade procedure. See "Release 3.1.1 Feature Set" section on page 2. |
The upgrade of a Release 2.x.x image to a Release 3.x.x. image is a three part process as follows:
1. Install a special upgrade image.
2. Reboot with the upgrade image, rewrite the boot ROM and load a Flash memory only image into Flash Memory.
3. Reboot with the Flash memory only image, format disk drives, then install the full 3.1.x image.
Select the image file appropriate to the model of the Content Engine.
Before starting your 2.x to 3.1.x upgrade, ensure that the desired 3.1.x Flash memory-only image file resides on an FTP server that is accessible to the Content Engine to be upgraded.
Step 1 Log on to the Content Engine through the console port.
Console access is necessary for entering initial network configuration information.
Step 2 Install the transition image for your model of Content Engine according to normal Cache Software Release 2.x upgrade procedures.
 |
Note This procedure assumes that the Content Engine is configured to boot from Flash memory. See the Cache Software Release 2.x documentation for netboot and install procedures. |
Step 3 With the transition image installed, determine if the Content Engine IP parameters are properly configured with the show running-config EXEC command.
ContentEngine# show running-config
Building configuration...
Current configuration:
!
. . .
hostname ContentEngine
!
interface ethernet 0
ip address 172.16.193.250 255.255.255.224
ip broadcast-address 172.16.193.255
exit
!
!
interface ethernet 1
exit
!
ip default-gateway 172.16.193.225
ip name-server 172.16.2.133
ip domain-name cisco.com
ip route 0.0.0.0 0.0.0.0 172.16.193.225
. . .
If the IP parameters need to be modified, use the ip interface configuration command and the ip global configuration command. For instance, the basic IP parameters of IP address, default gateway, and netmask can be configured as follows:
ContentEngine# config
ContentEngine(config)# ip default-gateway ipaddress
ContentEngine(config)# interface ethernet 0
ContentEngine(config-if)# ip address ipaddress netmask
ContentEngine(config-if)# exit
ContentEngine(config)# exit
ContentEngine# write memory
Building configuration.... . [OK]
ContentEngine#
 |
Note The Content Engine must be rebooted for changed IP parameters to take effect. The write memory EXEC command saves the configuration to Flash memory. |
Step 4 Access the Content Engine TCL shell and enter upgrade to execute the TCL upgrade script.
ContentEngine# tcl
tcl% upgrade
Step 5 Enter the following information when prompted:
FTP Server IP Address: 172.16.63.150
Remote Filename :ce590-31x.flash
Remote username : my_ftp_username
Remote password : my_ftp_password
Are you sure you want to do this?
Type YES if you are:YES
upgrade:checking integrity of cookie...
cookie is valid.
upgrade:allocating memory for new image...
upgrade:saving old bootrom (boot by hitting 'D')...
. . . . . . . . BootROM length is 304397
Current Network parameters for this box are:
Ip address = 172.10.13.8
Ip mask = 255.255.255.0
Ip gateway = 172.10.55.2
Host name = CE_590
Those parameters may be saved so that the new version software will
automatically pick them up. If you choose not to save them now,
you'll need to input them manually later during upgrade process.
Want to save those network parameters now? Save?[yes]: yes
upgrade:Please specify password for admin so that upgraded software
will be safer after it comes up. Valid password would be alphanumerics
containing 3 to 8 characters.
Note:Your password WON'T BE SHOWN on the screen when you type it.
Enter password: ******
Re-enter password: ******
Password is accepted.
upgrade:save network parameters....
upgrade:initiating FTP download...
upgrade:12713984 bytes transferred
About to write to flash! Your old software will
no longer exist on flash. Are you sure you
want to do this? Type YES if you are: YES
Ok, initiating flash write
FlashUpgrade:invoked
FlashUpgrade[0]: erasing: . - programming:
FlashUpgrade[1]: erasing: . - programming:
FlashUpgrade[2]: erasing: . - programming:
....
Flash memory is now updated with the Release 3.1.1 Flash memory-only image.
Step 6 Perform a cold reboot using the following command:
tcl% reboot cold
The Content Engine reboots from Flash memory running the Release 3.1.1 Flash memory-only system image.
Step 7 Perform the following substeps to partition and format the disk drives in the Content Engine for the Release 3.1.1 software requirements.
Release 3.1 software cannot read or write Release 2.x disk partitions. The optional software available with Release 3.1 requires creating new disk partitions. See the "Maintaining the Hard Disk Storage" section in Chapter 2 of the Cisco Cache Software Configuration Guide, Release 3.1.1. for details on Release 3.1.1 disk partitions.
a. View all disk drives available to the Content Engine (and Storage Array if connected) by entering the show disks EXEC command:
ContentEngine# show disks
disk00 (scsi host 0, channel 0, id 0)
disk01 (scsi host 0, channel 0, id 1)
b. Remove all disk partitions with the disk erase-all-partitions EXEC command:
ContentEngine# disk erase-all-partitions disk00
ContentEngine# disk erase-all-partitions disk01
c. Create an swfs partition with the disk recover EXEC command. The swfs partition stores components of the Release 3.1.1 optional software.
ContentEngine# disk recover
d. Create and mount a sysfs partition. In this example we create a partition consuming 20% of the total disk space on disk00.
ContentEngine# disk partition disk00/01 20% sysfs
ContentEngine# sysfs format disk00/01
ContentEngine# sysfs mount disk00/01 local1
Step 8 Change the present working directory to /local1 with the cd EXEC command:
ContentEngine# cd /local1
ContentEngine# pwd
/local1
ContentEngine#
Step 9 Download the full 3.1.1 release image with the copy ftp disk EXEC command:
ContentEngine# copy ftp disk server-address server-directory ce590-cache-31x.bin
The following FTP authentication challenge displays, enter your FTP username and password:
Enter username for remote ftp server: my_ftp_user_name
Enter password for remote ftp server: my_ftp_password
The image file downloads to the currently mounted sysfs directory.
Step 10 Install the downloaded image file with the install EXEC command.
ContentEngine# install ce590-cache-31x.bin
Step 11 Save the running configuration with the write mem EXEC command:
ContentEngine# write mem
Step 12 Reboot the Content Engine with the reload EXEC command.
ContentEngine# reload
Proceed with reload?[confirm] yes
Once the reboot is complete, Release 3.1.1 and optional software are ready for configuration.
The downgrade of a Release 3.1.1 image to a Release 2.x.x image is a three part process as follows:
1. Netboot with a special transition image.
2. With the transition image, rewrite the boot ROM and load a Release 2.x.x Flash memory-only image into Flash memory.
3. Reboot with the Flash memory-only image, reformat the disk drives and install a standard Release 2.x.x .pax file.
Select the image file appropriate to the Content Engine.
 |
Note The 3.1.x to 2.x transition file may contain the word UPGRADE although it is used in a downgrade procedure. |
Before starting your Release 3.1.1 to 2.x.x downgrade, ensure that the transition image, the 2.3.0 target Flash memory-only image, and the full 2.x.x software release file reside on an FTP server that is accessible to the Content Engine being downgraded.
Step 1 Log on to the Content Engine through the console port.
Console access is necessary for entering initial network configuration information.
Before proceeding with the following steps, read and understand the entire procedure. Step 3 requires that you act promptly, or you will be required to start over.
Step 2 At the CLI prompt, reboot the Content Engine with the reload EXEC command.
ContentEngine# reload
Proceed with reload?[confirm] yes
The autoboot sequence begins and the BIOS boot messages displays.
Symbios, Inc. PCI boot ROM successfully installed!
.....
.....
Step 3 Perform the following substeps to interrupt the autoboot sequence:
a. Press the D key when you see the following message:
Cisco CE Booting From Flash.
b. Press the space bar when you see the following message:
Press any key to stop auto-boot...
Step 4 Perform the following substeps to enable the Content Engine to netboot the upgrade image.
a. Enter c in the [CE500 Series]: field.
[CE500 Series]:c
b. Enter the network parameters to enable a netboot from the 2.x upgrade image on the FTP server, as shown in the example:
boot device (flash,net) [ flash]:net
file name [ ] :/somedirectory/ce590-cache-2.x-UPGRADE.bin
cache IP address [ 10.1.16.104]:
IP network mask [ 255.255.254.0]:
server IP address [ ]:172.16.63.150
gateway IP address [ 10.1.16.1]: 10.1.16.2
protocol (rcp,ftp,tftp) [ ]: ftp
username [ ]: my_ftp_username
password [ ]: my_ftp_password
flags [ 0]:
Step 5 Enter @ in the [CE500 Series]: field to continue the boot sequence.
[CE500 Series]: @
boot device (flash,net) [ net]:
file name [/somedirectory/ce590-cache-2.x-transition.bin]:
cache IP address [ 10.1.16.104]:
IP network mask [ 255.255.254.0]:
server IP address [ 172.16.63.150]:
gateway IP address [ 10.1.16.2]:
protocol (rcp,ftp,tftp) [ ftp]:
username [ my_ftp_username]:
password [ my_ftp_password]:
flags [ 0]:
Loading from the network
Attaching network interface fei0... done.
Attaching network interface lo0... done.
Loading... Starting at 0x108000...
Step 6 Login to the Content Engine as admin.
Step 7 With the upgrade image installed, verify that the Content Engine IP parameters are properly configured with the show running-config EXEC command.
ContentEngine# show running-config
Building configuration...
Current configuration:
!
. . .
hostname ContentEngine
!
interface ethernet 0
ip address 10.1.16.104
ip broadcast-address 172.16.193.255
exit
!
!
interface ethernet 1
exit
!
ip default-gateway 10.1.16.2
ip name-server 172.16.2.133
ip domain-name cisco.com
ip route 0.0.0.0 0.0.0.0 172.16.193.225
. . .
If the IP parameters require modification, use the ip interface configuration command and the ip global configuration command. For instance, the basic IP parameters of IP address, default gateway, and netmask can be configured as follows:
ContentEngine# config
ContentEngine(config)# ip default-gateway ipaddress
ContentEngine(config)# interface ethernet 0
ContentEngine(config-if)# ip address ipaddress netmask
ContentEngine(config-if)# exit
ContentEngine(config)# exit
ContentEngine# write memory
Building configuration.... . [OK]
ContentEngine#
 |
Note The Content Engine must be rebooted for changed IP parameters to take effect. The write memory EXEC command saves the configuration to Flash memory. |
Step 8 Access the Content Engine TCL shell and enter upgrade to execute the TCL upgrade script.
ContentEngine# tcl
tcl% upgrade
Step 9 Enter the following information when prompted:
 |
Note If the Content Engine being downgraded was previously upgraded from Release 2.x.x to 3.1.1 with the procedures described in the Upgrading Cache Software, Release 2.x.x Systems to Release 3.1.1, the Release 2.x system network configuration is still preserved in Flash memory, and may be different than the 3.1.x configuration displayed by the upgrade script. If you type yes to confirm the network parameters, it is the former Release 2.x configuration that boots. |
FTP Server IP Address: 172.16.63.150
Remote Filename :ce590-cache-230.flash
Remote username : my_ftp_username
Remote password : my_ftp_password
Are you sure you want to do this?
Type YES if you are:YES
upgrade:checking integrity of cookie...
cookie is valid.
upgrade:allocating memory for new image...
upgrade:saving old bootrom (boot by hitting 'D')...
. . . . . . . . BootROM length is 304397
Current Network parameters for this box are:
Ip address = 172.10.13.8
Ip mask = 255.255.255.0
Ip gateway = 172.10.55.2
Host name = CE_590
Those parameters may be saved so that the new version software will
automatically pick them up. If you choose not to save them now,
you'll need to input them manually later during upgrade process.
Want to save those network parameters now? Save?[yes]: no
upgrade:initiating FTP download...
upgrade:12713984 bytes transferred
About to write to flash! Your old software will
no longer exist on flash. Are you sure you
want to do this? Type YES if you are: YES
Ok, initiating flash write
FlashUpgrade:invoked
FlashUpgrade[0]: erasing: . - programming:
FlashUpgrade[1]: erasing: . - programming:
FlashUpgrade[2]: erasing: . - programming:
....
Flash memory is now updated with the Release 2.x.x Flash memory-only image.
Step 10 Perform a cold reboot using the following command:
tcl% reboot cold
The Content Engine begins the autoboot sequence.
Step 11 Change the boot device parameter to boot the Content Engine from Flash Memory.
Perform the following substeps to interrupt the autoboot sequence:
a. Press the D key when you see the following message:
Cisco CE Booting From Flash.
b. Press the space bar after you see the following message:
Press any key to stop auto-boot...
c. Enter c in the [CE500 Series]: field.
[CE500 Series]:c
d. Enter flash as the boot device parameter. Change the other network parameters as necessary.
boot device (flash,net) [ net]:flash
file name[/somedirectory/ce590-cache-2.x-UPGRADE.bin ]:
cache IP address [ 10.1.16.104]:
IP network mask [ 255.255.254.0]:
server IP address [ 172.16.63.150]:
gateway IP address [ 10.1.16.2]:
protocol (rcp,ftp,tftp) [ ftp]:
username [ my_ftp_username]:
password [ my_ftp_password]:
flags [ 0]:
Step 12 Enter @ in the [CE500 Series]: field to continue the boot sequence.
[CE500 Series]: @
boot device (flash,net) [ flash]:
file name [/somedirectory/ce590-cache-2.x-upgrade.bin]:
cache IP address [ 10.1.16.104]:
IP network mask [ 255.255.254.0]:
server IP address [ 172.16.63.150]:
gateway IP address [ 10.1.16.1]:
protocol (rcp,ftp,tftp) [ ftp]:
username [ my_ftp_username]:
password [ my_ftp_password]:
flags [ 0]:
Starting at 0x108000...
The Content Engine is now running the Release 2.x.x Flash memory only image.
Step 13 Login as admin.
Step 14 Perform the following substeps to partition and format the disk drives of the Content Engine for Release 2.x.x software.
Release 2.x.x software cannot read or write Release 3.x disk partitions.
a. List all the disk drives available to the Content Engine with the show disk EXEC command:
contentengine# show disks
/c0t0d0 (scsi bus 0, unit 0, lun 0)
/c0t1d0 (scsi bus 0, unit 1, lun 0)
b. Partition and format all the disk drives with the disk manufacture EXEC command:
contentengine# disk manufacture c0t0d0
contentengine# disk manufacture c0t1d0
Step 15 Install and reload the 2.x .pax file of your choice according to standard Release 2.x upgrade procedures.
The Content Engine can be configured to accept transparently redirected RTSP requests, as well as traditional proxy-style RTSP requests from RealPlayer client software. The redirection of RTSP traffic to the media cache is enabled with the Content Engine command-line interface (CLI). The RealProxy software is configured with the RealAdministrator graphical user interface (GUI).
 |
Note You must purchase a license key in order to activate the RealProxy features in the Cache software. |
Complete the followings steps to enable transparent redirection of RTSP traffic to the RealProxy:
Step 1 On the WCCP Version 2 routers, configure the outbound interfaces to the Internet.
In the following example the outbound interface is the Ethernet 0 device.
router(config)# ip wccp 80
router(config)# interface Ethernet 0
router(interface)# ip wccp 80 redirect out
Step 2 Set the WCCP Version 2 parameters on the Content Engine.
In the following example, the WCCP Version 2 enabled routers have the IP addresses 172.16.25.25 and 172.16.25.24.
Console(config)# wccp version 2
Console(config)# wccp router-list 1 172.16.25.25 172.16.25.24
Console(config)# wccp media-cache router-list-num 1
Step 3 Set the IP address for the RealProxy.
Make sure the IP address of the RealProxy is visible to the RealPlayers that use it.
Console(config)# rtsp proxy media-real ip-address 172.16.16.16
Step 4 Enter your RealProxy license number.
Console(config)# rtsp proxy media-real license-key mylicense
Step 5 Enable the RealProxy.
Console(config)# rtsp proxy media-real enable
Step 6 Save the new configuration
Console# copy running-config startup-config
Step 7 Configure the RealProxy parameters with the RealSystem administrator GUI.
A RealProxy page has been added to the management GUI. To access the RealSystem administrator, click the Admin button on the RealProxy page. The Admin button is active when the RealProxy software is installed and enabled.
Step 8 Use the following commands to display RealProxy statistics:
Console# show statistics mediacache real requests
Console# show statistics mediacache real savings
 |
Note The mediacache real statistics relate only to objects transported over RTSP that were requested by a RealPlayer client. Objects transported over HTTP are counted in the HTTP statistics. Streaming objects requested by other clients or transported over other protocols, bypass the Content Engine. |
To configure the Content Engine to service RealPlayer to use RealProxy of the Cisco Content Engine, perform the following steps:
Step 1 Set the IP address for the RealProxy.
Make sure the IP address of the RealProxy is visible to the RealPlayers that use it.
Console(config)# rtsp proxy media-real ip-address 172.16.16.16
Step 2 Enter your RealProxy license number.
Console(config)# rtsp proxy media-real license-key mylicense
Step 3 Enable the RealProxy.
Console(config)# rtsp proxy media-real enable
Step 4 Configure the Content Engine to listen for RTSP traffic on a specified port.
The default RTSP port is 554.
Console# rtsp proxy incoming 554
Step 5 Configure RealPlayer clients to use RealProxy on the Content Engine.
a. Open RealPlayer.
b. Select View then Preferences from the menu bar.
c. Click the Proxy tab.
d. Click the Use RTSP proxy checkbox.
e. Enter the IP address of Cisco Content Engine in the Use RTSP proxy address field.
f. Specify the port number that you entered with the Cache Software rtsp proxy global configuration CLI command.
g. Select OK.
The RealPlayer configuration is shown in Figure 1.
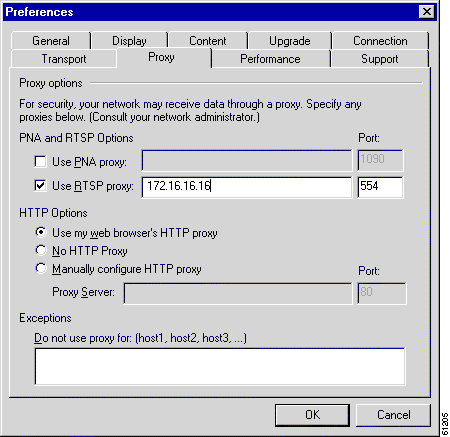
RealPlayer is now able to use the Cisco Content Engine's RealProxy to fetch streaming objects.
For more information on setting up the Real Player, please see the RealProxy 'readme'- 'Setting Up Real Server' and 'Setting Up RealPlayer' at the following URL:
http://service.real.com/help/library/guides/proxy/readme.htm#5
Step 6 Save the Content Engine configuration to Flash memory.
Console# copy running-config startup-config
Step 7 Use the following commands to display RealProxy statistics:
Console# show statistics mediacache real requests
Console# show statistics mediacache real savings
 |
Note The mediacache real statistics relate only to objects transported over RTSP that were requested by a RealPlayer client. Objects transported over HTTP are counted in the HTTP statistics. Streaming objects requested by other clients or transported over other protocols, bypass the Content Engine. |
Caveats describe unexpected behavior of Cisco Cache Software, Release 3.1.1. Severity 1 caveats are the most serious caveats, severity 2 caveats are less serious. Severity 3 caveats are moderate caveats, and only select severity 3 caveats are included in this section. The following caveats are still open (unresolved) at the printing of these release notes.
1. Disable logging to disk.
Console# config
Console(config)# no logging disk enable
Console(config)# exit
2. Go to the directory that contains the log file.
3. Remove the log file and create an empty new file.
Console# delfile syslog.txt
Console# mkfile syslog.txt
4. Enable logging to disk.
Console# config
Console(config)# logging disk enable
Console(config)# exit
 |
Note This applies only to default values. Any value that is configured as a non-default value will always take effect. |
Verifier didn't respond. Need to re-register verifier. when setting
cfg/gl/cache/wccp/service_data_base (Error number: 64)
Console(config)# no rtsp proxy media-real enable
Console(config)# rtsp proxy media-real enable
The Cisco Content Engine management information base (MIB) has changed since the 2.x version of the MIB.
You can access the Cisco Content Engine MIB here:
ftp://ftp.cisco.com/pub/mibs/v2/CISCO-CONTENT-ENGINE-MIB.my
Third party software used under license accompanies the Cisco Cache Software, Release 3.1.1. One or more of the following notices may apply in connection with the license and use of such third party software.
fxpcontrol
Copyright © 1995, David Greenman. All rights reserved.
Redistribution and use in source and binary forms, with or without modification, are permitted provided that the following conditions are met:
Redistributions of source code must retain the above copyright notice unmodified, this list of conditions, and the following disclaimer.
Redistributions in binary form must reproduce the above copyright notice, this list of conditions and the following disclaimer in the documentation and/or other materials provided with the distribution.
THIS SOFTWARE IS PROVIDED BY THE AUTHOR AND CONTRIBUTORS \Q\QAS IS'' AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE AUTHOR OR CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
ld.so
Copyright © 1994-1997, Eric Youngdale, Peter MacDonald, David Engel, Hongjiu Lu and Mitch D'Souza. All rights reserved.
Redistribution and use in source and binary forms, with or without modification, are permitted provided that the following conditions are met:
Redistributions of source code must retain the above copyright notice, this list of conditions and the following disclaimer.
The name of the above contributors may not be used to endorse or promote products derived from this software without specific prior written permission.
THIS SOFTWARE IS PROVIDED BY THE CONTRIBUTORS \Q\QAS IS'' AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
md5
Copyright © 1991, 1992, RSA Data Security, Inc. All rights reserved.
License to copy and use this software is granted provided that it is identified as the "RSA Data Security, Inc. MD5 Message-Digest Algorithm" in all material mentioning or referencing this software or this function. License is also granted to make and use derivative works provided that such works are identified as "derived from the RSA Data Security, Inc. MD5 Message-Digest Algorithm" in all material mentioning or referencing the derived work. RSA Data Security, Inc. makes no representations concerning either the merchantability of this software or the suitability of this software for any particular purpose. It is provided "as is" without express or implied warranty of any kind. These notices must be retained in any copies of any part of this documentation and/or software.
mktemp
Copyright © 1996, Todd C. Miller <Todd.Miller@courtesan.com> All rights reserved.
Redistribution and use in source and binary forms, with or without modification, are permitted provided that the following conditions are met:
Redistributions of source code must retain the above copyright notice, this list of conditions and the following disclaimer.
Redistributions in binary form must reproduce the above copyright notice, this list of conditions and the following disclaimer in the documentation and/or other materials provided with the distribution.
All advertising materials mentioning features or use of this software must display the following acknowledgement:
This product includes software developed by Todd C. Miller.
The name of the author may not be used to endorse or promote products derived from this software without specific prior written permission.
THIS SOFTWARE IS PROVIDED \Q\QAS IS'' AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE AUTHOR BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
ntp-4.0.99j
Copyright © David L. Mills 1992-2000, All rights reserved.
Permission to use, copy, modify, and distribute this software and its documentation for any purpose and without fee is hereby granted, provided that the above copyright notice appears in all copies and that both the copyright notice and this permission notice appear in supporting documentation, and that the name University of Delaware not be used in advertising or publicity pertaining to distribution of the software without specific, written prior permission. The University of Delaware makes no representations about the suitability this software for any purpose. It is provided "as is" without express or implied warranty.
strace
Copyright © 1991, 1992, Paul Kranenburg <pk@cs.few.eur.nl>
Copyright © 1993, Branko Lankester <branko@hacktic.nl>
Copyright © 1993, Ulrich Pegelow <pegelow@moorea.uni-muenster.de>
Copyright © 1995, 1996 Michael Elizabeth Chastain <mec@duracef.shout.net>
Copyright © 1993, 1994, 1995, 1996 Rick Sladkey <jrs@world.std.com> All rights reserved.
Redistribution and use in source and binary forms, with or without modification, are permitted provided that the following conditions are met:
Redistributions of source code must retain the above copyright notice, this list of conditions and the following disclaimer.
Redistributions in binary form must reproduce the above copyright notice, this list of conditions and the following disclaimer in the documentation and/or other materials provided with the distribution.
The name of the author may not be used to endorse or promote products derived from this software without specific prior written permission.
THIS SOFTWARE IS PROVIDED BY THE AUTHOR \Q\QAS IS'' AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE AUTHOR BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
The following third party software is subject to the Berkeley Software Distribution (BSD) license.
ftp-0.16
Copyright © 1989, The Regents of the University of California. All rights reserved.
inetd-0.16
Copyright © 1983, 1991, The Regents of the University of California. All rights reserved.
ping
Copyright © 1989 The Regents of the University of California. All rights reserved. This code is derived from software contributed to Berkeley by Mike Muuss.
telnet-0.16
Copyright © 1989, The Regents of the University of California. All rights reserved.
tftp
Copyright © 1983, 1993, The Regents of the University of California. All rights reserved.
syslogd
Copyright © 1983, 1988, 1993, 1994, The Regents of the University of California. All rights reserved.
util-linux
Copyright © 1989, The Regents of the University of California. All rights reserved.
Redistribution and use in source and binary forms, with or without modification, are permitted provided that the following conditions are met:
Redistributions of source code must retain the above copyright notice, this list of conditions and the following disclaimer.
Redistributions in binary form must reproduce the above copyright notice, this list of conditions and the following disclaimer in the documentation and/or other materials provided with the distribution.
Neither the name of the University of California, nor the names of its contributors may be used to endorse or promote products derived from this software without specific prior written permission.
THIS SOFTWARE IS PROVIDED BY THE REGENTS AND CONTRIBUTORS \Q\QAS IS'' AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE REGENTS OR CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
Cisco Cache Software, Release 3.1.1 incorporates software licensed under the GNU General Public License. To obtain source code for any of the modified GPL code in the Cisco Cache Software, Release 3.1.1, please send a request to ce-sw-req@cisco.com.
Version 2, June 1991
Copyright © 1989, 1991 Free Software Foundation, Inc.
59 Temple Place, Suite 330, Boston, MA 02111-1307 USA
Everyone is permitted to copy and distribute verbatim copies of this license document, but changing it is not allowed.
Preamble
The licenses for most software are designed to take away your freedom to share and change it. By contrast, the GNU General Public License is intended to guarantee your freedom to share and change free software--to make sure the software is free for all its users. This General Public License applies to most of the Free Software Foundation's software and to any other program whose authors commit to using it. (Some other Free Software Foundation software is covered by the GNU Library General Public License instead.) You can apply it to your programs, too.
When we speak of free software, we are referring to freedom, not price. Our General Public Licenses are designed to make sure that you have the freedom to distribute copies of free software (and charge for this service if you wish), that you receive source code or can get it if you want it, that you can change the software or use pieces of it in new free programs; and that you know you can do these things.
To protect your rights, we need to make restrictions that forbid anyone to deny you these rights or to ask you to surrender the rights. These restrictions translate to certain responsibilities for you if you distribute copies of the software, or if you modify it.
For example, if you distribute copies of such a program, whether gratis or for a fee, you must give the recipients all the rights that you have. You must make sure that they, too, receive or can get the source code. And you must show them these terms so they know their rights.
We protect your rights with two steps:(1) copyright the software, and (2) offer you this license which gives you legal permission to copy, distribute and/or modify the software.
Also, for each author's protection and ours, we want to make certain that everyone understands that there is no warranty for this free software. If the software is modified by someone else and passed on, we want its recipients to know that what they have is not the original, so that any problems introduced by others will not reflect on the original authors' reputations.
Finally, any free program is threatened constantly by software patents. We wish to avoid the danger that redistributors of a free program will individually obtain patent licenses, in effect making the program proprietary. To prevent this, we have made it clear that any patent must be licensed for everyone's free use or not licensed at all.
The precise terms and conditions for copying, distribution and modification follow.
GNU GENERAL PUBLIC LICENSE
TERMS AND CONDITIONS FOR COPYING, DISTRIBUTION AND MODIFICATION
This License applies to any program or other work which contains a notice placed by the copyright holder saying it may be distributed under the terms of this General Public License. The "Program", below, refers to any such program or work, and a "work based on the Program" means either the Program or any derivative work under copyright law: that is to say, a work containing the Program or a portion of it, either verbatim or with modifications and/or translated into another language. (Hereinafter, translation is included without limitation inthe term "modification".) Each licensee is addressed as "you".
Activities other than copying, distribution and modification are not covered by this License; they are outside its scope. The act of running the Program is not restricted, and the output from the Program is covered only if its contents constitute a work based on the Program (independent of having been made by running the Program). Whether that is true depends on what the Program does.
1. You may copy and distribute verbatim copies of the Program's source code as you receive it, in any medium, provided that you conspicuously and appropriately publish on each copy an appropriate copyright notice and disclaimer of warranty; keep intact all the notices that refer to this License and to the absence of any warranty; and give any other recipients of the Program a copy of this License along with the Program.
You may charge a fee for the physical act of transferring a copy, and you may at your option offer warranty protection in exchange for a fee.
2. You may modify your copy or copies of the Program or any portion of it, thus forming a work based on the Program, and copy and distribute such modifications or work under the terms of Section 1 above, provided that you also meet all of these conditions:
a) You must cause the modified files to carry prominent notices stating that you changed the files and the date of any change.
b) You must cause any work that you distribute or publish, that in whole or in part contains or is derived from the Program or any part thereof, to be licensed as a whole at no charge to all third parties under the terms of this License.
c) If the modified program normally reads commands interactively when run, you must cause it, when started running for such interactive use in the most ordinary way, to print or display an announcement including an appropriate copyright notice and a notice that there is no warranty (or else, saying that you provide a warranty) and that users may redistribute the program under these conditions, and telling the user how to view a copy of this License. (Exception:if the Program itself is interactive but does not normally print such an announcement, your work based on the Program is not required to print an announcement.)
These requirements apply to the modified work as a whole. If identifiable sections of that work are not derived from the Program, and can be reasonably considered independent and separate works in themselves, then this License, and its terms, do not apply to those sections when you distribute them as separate works. But when you distribute the same sections as part of a whole which is a work based on the Program, the distribution of the whole must be on the terms ofthis License, whose permissions for other licensees extend to the entire whole, and thus to each and every part regardless of who wrote it.
Thus, it is not the intent of this section to claim rights or contest your rights to work written entirely by you; rather, the intent is to exercise the right to control the distribution of derivative or collective works based on the Program.
In addition, mere aggregation of another work not based on the Program with the Program (or with a work based on the Program) on a volume of a storage or distribution medium does not bring the other work under the scope of this License.
3. You may copy and distribute the Program (or a work based on it, under Section 2) in object code or executable form under the terms of Sections 1 and 2 above provided that you also do one of the following:
a) Accompany it with the complete corresponding machine-readable source code, which must be distributed under the terms of Sections 1 and 2 above on a medium customarily used for software interchange; or,
b) Accompany it with a written offer, valid for at least three years, to give any third party, for a charge no more than your cost of physically performing source distribution, a complete machine-readable copy of the corresponding source code, to be distributed under the terms of Sections 1 and 2 above on a medium customarily used for software interchange; or,
c) Accompany it with the information you received as to the offer to distribute corresponding source code. (This alternative is allowed only for noncommercial distribution and only if you received the program in object code or executable form with such an offer, in accord with Subsection b above.)
The source code for a work means the preferred form of the work for making modifications to it. For an executable work, complete source code means all the source code for all modules it contains, plus any associated interface definition files, plus the scripts used to control compilation and installation of the executable. However, as a special exception, the source code distributed need not include anything that is normally distributed (in either source or binary form) with the major components (compiler, kernel, and so on) of the operating system on which the executable runs, unless that component itself accompanies the executable.
If distribution of executable or object code is made by offering access to copy from a designated place, then offering equivalent access to copy the source code from the same place counts as distribution of the source code, even though third parties are not compelled to copy the source along with the object code.
4. You may not copy, modify, sublicense, or distribute the Program except as expressly provided under this License. Any attempt otherwise to copy, modify, sublicense or distribute the Program is void, and will automatically terminate your rights under this License. However, parties who have received copies, or rights, from you under this License will not have their licenses terminated so long as such parties remain in full compliance.
5. You are not required to accept this License, since you have not signed it. However, nothing else grants you permission to modify or distribute the Program or its derivative works. These actions are prohibited by law if you do not accept this License. Therefore, by modifying or distributing the Program (or any work based on the Program), you indicate your acceptance of this License to do so, and all its terms and conditions for copying, distributing or modifying the Program or works based on it.
6. Each time you redistribute the Program (or any work based on the Program), the recipient automatically receives a license from the original licensor to copy, distribute or modify the Program subject to these terms and conditions. You may not impose any further restrictions on the recipients' exercise of the rights granted herein. You are not responsible for enforcing compliance by third parties to this License.
7. If, as a consequence of a court judgment or allegation of patent infringement or for any other reason (not limited to patent issues), conditions are imposed on you (whether by court order, agreement or otherwise) that contradict the conditions of this License, they do not excuse you from the conditions of this License. If you cannot distribute so as to satisfy simultaneously your obligations under this License and any other pertinent obligations, then as a consequence you may not distribute the Program at all. For example, if a patent license would not permit royalty-free redistribution of the Program by all those who receive copies directly or indirectly through you, then the only way you could satisfy both it and this License would be to refrain entirely from distribution of the Program.
If any portion of this section is held invalid or unenforceable under any particular circumstance, the balance of the section is intended to apply and the section as a whole is intended to apply in other circumstances.
It is not the purpose of this section to induce you to infringe any patents or other property right claims or to contest validity of any such claims; this section has the sole purpose of protecting the integrity of the free software distribution system, which is implemented by public license practices. Many people have made generous contributions to the wide range of software distributed through that system in reliance on consistent application of that system; it is up to the author/donor to decide if he or she is willing to distribute software through any other system and a licensee cannot impose that choice.
This section is intended to make thoroughly clear what is believed to be a consequence of the rest of this License.
8. If the distribution and/or use of the Program is restricted in certain countries either by patents or by copyrighted interfaces, the original copyright holder who places the Program under this License may add an explicit geographical distribution limitation excluding those countries, so that distribution is permitted only in or among countries not thus excluded. In such case, this License incorporates the limitation as if written in the body of this License.
9. The Free Software Foundation may publish revised and/or new versions of the General Public License from time to time. Such new versions will be similar in spirit to the present version, but may differ in detail to address new problems or concerns.
Each version is given a distinguishing version number. If the Program specifies a version number of this License which applies to it and "any later version", you have the option of following the terms and conditions either of that version or of any later version published by the Free Software Foundation. If the Program does not specify a version number of this License, you may choose any version ever published by the Free Software Foundation.
10. If you wish to incorporate parts of the Program into other free programs whose distribution conditions are different, write to the author to ask for permission. For software which is copyrighted by the Free Software Foundation, write to the Free Software Foundation; we sometimes make exceptions for this. Our decision will be guided by the two goals of preserving the free status of all derivatives of our free software and of promoting the sharing and reuse of software generally.
NO WARRANTY
11. BECAUSE THE PROGRAM IS LICENSED FREE OF CHARGE, THERE IS NO WARRANTY FOR THE PROGRAM, TO THE EXTENT PERMITTED BY APPLICABLE LAW. EXCEPT WHEN OTHERWISE STATED IN WRITING THE COPYRIGHT HOLDERS AND/OR OTHER PARTIES PROVIDE THE PROGRAM "AS IS" WITHOUT WARRANTY OF ANY KIND, EITHER EXPRESSED OR IMPLIED, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE. THE ENTIRE RISK AS TO THE QUALITY AND PERFORMANCE OF THE PROGRAM IS WITH YOU. SHOULD THE PROGRAM PROVE DEFECTIVE, YOU ASSUME THE COST OF ALL NECESSARY SERVICING, REPAIR OR CORRECTION.
12. IN NO EVENT UNLESS REQUIRED BY APPLICABLE LAW OR AGREED TO IN WRITING WILL ANY COPYRIGHT HOLDER, OR ANY OTHER PARTY WHO MAY MODIFY AND/OR REDISTRIBUTE THE PROGRAM AS PERMITTED ABOVE, BE LIABLE TO YOU FOR DAMAGES, INCLUDING ANY GENERAL, SPECIAL, INCIDENTAL OR CONSEQUENTIAL DAMAGES ARISING OUT OF THE USE OR INABILITY TO USE THE PROGRAM (INCLUDING BUT NOT LIMITED TO LOSS OF DATA OR DATA BEING RENDERED INACCURATE OR LOSSES SUSTAINED BY YOU OR THIRD PARTIES OR A FAILURE OF THE PROGRAM TO OPERATE WITH ANY OTHER PROGRAMS), EVEN IF SUCH HOLDER OR OTHER PARTY HAS BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES.
END USER LICENSE AND SOFTWARE WARRANTY
Software License
PLEASE READ THIS SOFTWARE LICENSE CAREFULLY BEFORE DOWNLOADING, INSTALLING OR USING CISCO OR CISCO-SUPPLIED SOFTWARE.
BY DOWNLOADING OR INSTALLING THE SOFTWARE, OR USING THE EQUIPMENT THAT CONTAINS THIS SOFTWARE, YOU ARE CONSENTING TO BE BOUND BY THIS LICENSE. IF YOU DO NOT AGREE TO ALL OF THE TERMS OF THIS LICENSE, THEN (A) DO NOT DOWNLOAD, INSTALL OR USE THE SOFTWARE, AND (B) YOU MAY RETURN THE SOFTWARE FOR A FULL REFUND, OR, IF THE SOFTWARE IS SUPPLIED AS PART OF ANOTHER PRODUCT, YOU MAY RETURN THE ENTIRE PRODUCT FOR A FULL REFUND. YOUR RIGHT TO RETURN AND REFUND EXPIRES 30 DAYS AFTER PURCHASE FROM CISCO OR AN AUTHORIZED CISCO RESELLER, AND APPLIES ONLY IF YOU ARE THE ORIGINAL PURCHASER.
The following terms govern your use of the Software except to the extent a particular program (a) is the subject of a separate written agreement with Cisco or (b) includes a separate "click-on" license agreement as part of the installation and/or download process. To the extent of a conflict between the provisions of the foregoing documents, the order of precedence shall be (1) the written agreement, (2) the click-on agreement, and (3) this Software License.
License. Subject to the terms and conditions of and except as otherwise provided in this Agreement, Cisco Systems, Inc. or the Cisco Systems, Inc. subsidiary licensing the Software, if sale is not directly by Cisco Systems, Inc. ("Cisco"), and its suppliers grant to Customer ("Customer") a nonexclusive and nontransferable license to use the specific Cisco program modules, feature set(s) or feature(s) for which Customer has paid the required license fees (the "Software"), in object code form only. In addition, the foregoing license shall also be subject to the following limitations, as applicable:
Unless otherwise expressly provided in the documentation, Customer shall use the Software solely as embedded in, for execution on, or (where the applicable documentation permits installation on non-Cisco equipment) for communication with Cisco equipment owned or leased by Customer;
Customer's use of the Software shall be limited to use on a single hardware chassis, on a single central processing unit, as applicable, or use on such greater number of chassises or central processing units as Customer may have paid Cisco the required license fee; and
Customer's use of the Software shall also be limited, as applicable and set forth in Customer's purchase order or in Cisco's product catalog, user documentation, or web site, to a maximum number of (a) seats (i.e. users with access to the installed Software), (b) concurrent users, sessions, ports, and/or issued and outstanding IP addresses, and/or (c) central processing unit cycles or instructions per second. Customer's use of the Software shall also be limited by any other restrictions set forth in Customer's purchase order or in Cisco's product catalog, user documentation or web site for the Software.
NOTE: For evaluation or beta copies for which Cisco does not charge a license fee, the above requirement to pay a license fee does not apply.
General Limitations. Except as otherwise expressly provided under this Agreement, Customer shall have no right, and Customer specifically agrees not to:
(i) transfer, assign or sublicense its license rights to any other person, or use the Software on unauthorized or secondhand Cisco equipment, and any such attempted transfer, assignment or sublicense shall be void;
(ii) make error corrections to or otherwise modify or adapt the Software or create derivative works based upon the Software, or to permit third parties to do the same; or
(iii) decompile, decrypt, reverse engineer, disassemble or otherwise reduce the Software to human-readable form to gain access to trade secrets or confidential information in the Software.
To the extent required by law, at Customer's request, Cisco shall provide Customer with the interface information needed to achieve interoperability between the Software and another independently created program, on payment of Cisco's applicable fee. Customer shall observe strict obligations of confidentiality with respect to such information.
Upgrades and Additional Copies. For purposes of this Agreement, "Software" shall include (and the terms and conditions of this Agreement shall apply to) any upgrades, updates, bug fixes or modified versions (collectively, "Upgrades") or backup copies of the Software licensed or provided to Customer by Cisco or an authorized distributor for which Customer has paid the applicable license fees. NOTWITHSTANDING ANY OTHER PROVISION OF THIS AGREEMENT: (1) CUSTOMER HAS NO LICENSE OR RIGHT TO USE ANY SUCH ADDITIONAL COPIES OR UPGRADES UNLESS CUSTOMER, AT THE TIME OF ACQUIRING SUCH COPY OR UPGRADE, ALREADY HOLDS A VALID LICENSE TO THE ORIGINAL SOFTWARE AND HAS PAID THE APPLICABLE FEE FOR THE UPGRADE; (2) USE OF UPGRADES IS LIMITED TO CISCO EQUIPMENT FOR WHICH CUSTOMER IS THE ORIGINAL END USER PURCHASER OR LESSEE OR WHO OTHERWISE HOLDS A VALID LICENSE TO USE THE SOFTWARE WHICH IS BEING UPGRADED; AND (3) USE OF ADDITIONAL COPIES IS LIMITED TO BACKUP PURPOSES ONLY.
Proprietary Notices. Customer agrees to maintain and reproduce all copyright and other proprietary notices on all copies, in any form, of the Software in the same form and manner that such copyright and other proprietary notices are included on the Software. Except as expressly authorized in this Agreement, Customer shall not make any copies or duplicates or any Software without the prior written permission of Cisco. Customer may make such backup copies of the Software as may be necessary for Customer's lawful use, provided Customer affixes to such copies all copyright, confidentiality, and proprietary notices that appear on the original.
Protection of Information. Customer agrees that aspects of the Software and associated documentation, including the specific design and structure of individual programs, constitute trade secrets and/or copyrighted material of Cisco. Customer shall not disclose, provide, or otherwise make available such trade secrets or copyrighted material in any form to any third party without the prior written consent of Cisco. Customer shall implement reasonable security measures to protect such trade secrets and copyrighted material. Title to Software and documentation shall remain solely with Cisco.
Term and Termination. This License is effective until terminated. Customer may terminate this License at any time by destroying all copies of Software including any documentation. Customer's rights under this License will terminate immediately without notice from Cisco if Customer fails to comply with any provision of this License. Upon termination, Customer must destroy all copies of Software in its possession or control.
Customer Records. Customer grants to Cisco and its independent accountants the right to examine Customer's books, records and accounts during Customer's normal business hours to verify compliance with this Agreement. In the event such audit discloses non-compliance with this Agreement, Customer shall promptly pay to Cisco the appropriate licensee fees.
Export. Software, including technical data, may be subject to U.S. export control laws, including the U.S. Export Administration Act and its associated regulations, and may be subject to export or import regulations in other countries. Customer agrees to comply strictly with all such regulations and acknowledges that it has the responsibility to obtain licenses to export, re-export, or import Software.
Restricted Rights. Cisco's commercial software and commercial computer software documentation is provided to United States Government agencies in accordance with the terms of this Agreement, and per subparagraph "(c)" of the "Commercial Computer Software - Restricted Rights" clause at FAR 52.227-19 (June 1987). For DOD agencies, the restrictions set forth in the "Technical Data-Commercial Items" clause at DFARS 252.227-7015 (Nov 1995) shall also apply.
Limited Warranty
Cisco Systems, Inc. or the Cisco Systems, Inc. subsidiary licensing the Software, if sale is not directly by Cisco Systems, Inc. ("Cisco") warrants that commencing from the date of delivery to Customer (but in case of resale by a Cisco reseller, commencing not more than ninety (90) days after original shipment by Cisco), and continuing for a period of the longer of (a) ninety (90) days or (b) the period set forth in the Warranty Card accompanying the Product (if any): (a) the media on which the Software is furnished will be free of defects in materials and workmanship under normal use; and (b) the Software substantially conforms to its published specifications. The date of shipment of a Product by Cisco is set forth on the packaging material in which the Product is shipped. Except for the foregoing, the Software is provided AS IS. This limited warranty extends only to the Customer who is the original licensee. Customer's sole and exclusive remedy and the entire liability of Cisco and its suppliers under this limited warranty will be, at Cisco or its service center's option, repair, replacement, or refund of the Software if reported (or, upon request, returned) to the party supplying the Software to Customer, if different than Cisco. In no event does Cisco warrant that the Software is error free or that Customer will be able to operate the Software without problems or interruptions. In addition, due to the continual development of new techniques for intruding upon and attacking networks, Cisco does not warrant that the Software or any equipment, system or network on which the Software is used will be free of vulnerability to intrusion or attack.
Y2K. Cisco represents that Products which it has designated as "Year 2000 Compliant" (or Status Description "Green") as set forth in the "Compliance Table," (including accompanying Notes), located in Cisco's "Year 2000 Compliance" web pages beginning at http://www.cisco.com (the "Year 2000 Pages") are "Year 2000 Compliant," meaning that, as delivered to Customer:
A. The Products accurately process data and time calculations before and during the years 1999 and 2000;
B. All manipulation of time-related data yields the desired results for valid date values within the application domain;
C. Date elements in those Products use four digit storage and indicate century to eliminate the chance for errors;
D. If a date element exists without a century indication, the correct century continues to be unambiguous and produces accurate results; and Software accurately processes date and time data when used in conjunction with other Year 2000 compliant software products.
Should a Product that is so identified as "Year 2000 Compliant" not be Year 2000 Compliant or should Cisco otherwise breach the foregoing representation, Cisco will, as Customer's sole and exclusive remedy, repair or replace the Product so that it becomes Year 2000 Compliant or, if Cisco is unable to repair or replace the Product to make it Year 2000 Compliant, Cisco will refund the purchase price of the Product paid to Cisco, provided that Customer returns the Product to Cisco as originally delivered by Cisco (except for normal wear and tear) and pursuant to Cisco's then-current RMA policy. The foregoing representation and remedy shall only apply to Products returned prior to January 31, 2001, or to Products returned before the Products are no longer supported pursuant to Cisco's standard support policies, whichever event first occurs. Each Product ordered will be subject to Cisco's then-current "Year 2000 Pages" as of the date of delivery.
Restrictions. This warranty does not apply if the Product (a) has been altered, except by Cisco, (b) has not been installed, operated, repaired, or maintained in accordance with instructions supplied by Cisco, (c) has been subjected to abnormal physical or electrical stress, misuse, negligence, or accident; or (d) is licensed, for beta, evaluation, testing or demonstration purposes for which Cisco does not receive a payment of purchase price or license fee.
DISCLAIMER OF WARRANTY. EXCEPT AS SPECIFIED IN THIS WARRANTY, ALL EXPRESS OR IMPLIED CONDITIONS, REPRESENTATIONS, AND WARRANTIES INCLUDING, WITHOUT LIMITATION, ANY IMPLIED WARRANTY OR CONDITION OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE, NONINFRINGEMENT, SATISFACTORY QUALITY OR ARISING FROM A COURSE OF DEALING, LAW, USAGE, OR TRADE PRACTICE, ARE HEREBY EXCLUDED TO THE EXTENT ALLOWED BY APPLICABLE LAW. TO THE EXTENT AN IMPLIED WARRANTY CANNOT BE EXCLUDED, SUCH WARRANTY IS LIMITED IN DURATION TO THE WARRANTY PERIOD. BECAUSE SOME STATES OR JURISDICTIONS DO NOT ALLOW LIMITATIONS ON HOW LONG AN IMPLIED WARRANTY LASTS, THE ABOVE LIMITATION MAY NOT APPLY TO YOU. THIS WARRANTY GIVES YOU SPECIFIC LEGAL RIGHTS, AND YOU MAY ALSO HAVE OTHER RIGHTS WHICH VARY FROM JURISDICTION TO JURISDICTION. This disclaimer and exclusion shall apply even if the express warranty set forth above fails of its essential purpose.
General Terms Applicable to the Limited Warranty Statement and Software License
Disclaimer of Liabilities. IN NO EVENT WILL CISCO OR ITS SUPPLIERS BE LIABLE FOR ANY LOST REVENUE, PROFIT, OR DATA, OR FOR SPECIAL, INDIRECT, CONSEQUENTIAL, INCIDENTAL, OR PUNITIVE DAMAGES HOWEVER CAUSED AND REGARDLESS OF THE THEORY OF LIABILITY ARISING OUT OF THE USE OF OR INABILITY TO USE SOFTWARE EVEN IF CISCO OR ITS SUPPLIERS HAVE BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES. In no event shall Cisco's or its suppliers' liability to Customer, whether in contract, tort (including negligence), or otherwise, exceed the price paid by Customer. The foregoing limitations shall apply even if the above-stated warranty fails of its essential purpose. BECAUSE SOME STATES OR JURISDICTIONS DO NOT ALLOW LIMITATION OR EXCLUSION OF CONSEQUENTIAL OR INCIDENTAL DAMAGES, THE ABOVE LIMITATION MAY NOT APPLY TO YOU.
The Warranty and the Software License shall be governed by and construed in accordance with the laws of the State of California, without reference to principles of conflict of laws, provided that for Customers located in a member state of the European Union, Norway or Switzerland, English law shall apply. The United Nations Convention on the International Sale of Goods shall not apply. If any portion hereof is found to be void or unenforceable, the remaining provisions of the Warranty and the Software License shall remain in full force and effect. Except as expressly provided herein, the Software License constitutes the entire agreement between the parties with respect to the license of the Software and supersedes any conflicting or additional terms contained in the purchase order
If Customer has entered into a contract directly with Cisco for supply of the Products subject to this warranty, the terms of that contract shall supersede any terms of this Warranty or the Warranty Card, or the Software License, which are inconsistent with that contract. Customer acknowledges that: the Internet URL address and the web pages referred to in this document may be updated by Cisco from time to time; the version in effect at the date of delivery of the Products to the Customer shall apply.
[INSERT THE FOLLOWING IN ALL THE LANGUAGES ON THE WARRANTY CARD:
ENGLISH: For warranty or license terms which may apply in particular countries and for translations of the above information, please visit the following URL:]
http://www.cisco.com/univercd/cc/td/doc/es_inpck/cetrans.htm
Cisco Cache Software Command Reference, Release 2.3.0
Cisco Cache Software Command Reference, Release 3.1.1
Cisco Cache Software Configuration Guide, Release 2.x.x
Cisco Cache Software Configuration Guide, Release 3.1.1
See also any associated Release Notes and any hardware documentation associated with the Content Engine you are using.
The following sections provide sources for obtaining documentation from Cisco Systems.
You can access the most current Cisco documentation on the World Wide Web at the following sites:
Cisco documentation and additional literature are available in a CD-ROM package, which ships with your product. The Documentation CD-ROM is updated monthly and may be more current than printed documentation. The CD-ROM package is available as a single unit or as an annual subscription.
Cisco documentation is available in the following ways:
If you are reading Cisco product documentation on the World Wide Web, you can submit technical comments electronically. Click Feedback in the toolbar and select Documentation. After you complete the form, click Submit to send it to Cisco.
You can e-mail your comments to bug-doc@cisco.com.
To submit your comments by mail, use the response card behind the front cover of your document, or write to the following address:
Attn Document Resource Connection
Cisco Systems, Inc.
170 West Tasman Drive
San Jose, CA 95134-9883
We appreciate your comments.
Cisco provides Cisco.com as a starting point for all technical assistance. Customers and partners can obtain documentation, troubleshooting tips, and sample configurations from online tools. For Cisco.com registered users, additional troubleshooting tools are available from the TAC website.
Cisco.com is the foundation of a suite of interactive, networked services that provides immediate, open access to Cisco information and resources at anytime, from anywhere in the world. This highly integrated Internet application is a powerful, easy-to-use tool for doing business with Cisco.
Cisco.com provides a broad range of features and services to help customers and partners streamline business processes and improve productivity. Through Cisco.com, you can find information about Cisco and our networking solutions, services, and programs. In addition, you can resolve technical issues with online technical support, download and test software packages, and order Cisco learning materials and merchandise. Valuable online skill assessment, training, and certification programs are also available.
Customers and partners can self-register on Cisco.com to obtain additional personalized information and services. Registered users can order products, check on the status of an order, access technical support, and view benefits specific to their relationships with Cisco.
To access Cisco.com, go to the following website:
The Cisco TAC website is available to all customers who need technical assistance with a Cisco product or technology that is under warranty or covered by a maintenance contract.
If you have a priority level 3 (P3) or priority level 4 (P4) problem, contact TAC by going to the TAC website:
P3 and P4 level problems are defined as follows:
In each of the above cases, use the Cisco TAC website to quickly find answers to your questions.
To register for Cisco.com, go to the following website:
http://www.cisco.com/register/
If you cannot resolve your technical issue by using the TAC online resources, Cisco.com registered users can open a case online by using the TAC Case Open tool at the following website:
http://www.cisco.com/tac/caseopen
If you have a priority level 1 (P1) or priority level 2 (P2) problem, contact TAC by telephone and immediately open a case. To obtain a directory of toll-free numbers for your country, go to the following website:
http://www.cisco.com/warp/public/687/Directory/DirTAC.shtm l
P1 and P2 level problems are defined as follows:
This document is to be used in conjunction with the documents listed in the "Related Documentation" section.
AccessPath, AtmDirector, Browse with Me, CCDE, CCIP, CCSI, CD-PAC, CiscoLink, the Cisco NetWorks logo, the Cisco Powered Network logo, Cisco Systems Networking Academy, the Cisco Systems Networking Academy logo, Fast Step, Follow Me Browsing, FormShare, FrameShare, GigaStack, IGX, Internet Quotient, IP/VC, iQ Breakthrough, iQ Expertise, iQ FastTrack, the iQ Logo, iQ Net Readiness Scorecard, MGX, the Networkers logo, Packet, RateMUX, ScriptBuilder, ScriptShare, SlideCast, SMARTnet, TransPath, Unity, Voice LAN, Wavelength Router, and WebViewer are trademarks of Cisco Systems, Inc.; Changing the Way We Work, Live, Play, and Learn, Discover All That's Possible, and Empowering the Internet Generation, are service marks of Cisco Systems, Inc.; and Aironet, ASIST, BPX, Catalyst, CCDA, CCDP, CCIE, CCNA, CCNP, Cisco, the Cisco Certified Internetwork Expert logo, Cisco IOS, the Cisco IOS logo, Cisco Systems, Cisco Systems Capital, the Cisco Systems logo, Enterprise/Solver, EtherChannel, EtherSwitch, FastHub, FastSwitch, IOS, IP/TV, LightStream, MICA, Network Registrar, PIX, Post-Routing, Pre-Routing, Registrar, StrataView Plus, Stratm, SwitchProbe, TeleRouter, and VCO are registered trademarks of Cisco Systems, Inc. and/or its affiliates in the U.S. and certain other countries.
All other trademarks mentioned in this document or Web site are the property of their respective owners. The use of the word partner does not imply a partnership relationship between Cisco and any other company. (0105R)
Copyright © 2001, Cisco Systems, Inc.
All rights reserved.
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
Posted: Sat Sep 28 03:34:43 PDT 2002
All contents are Copyright © 1992--2002 Cisco Systems, Inc. All rights reserved.
Important Notices and Privacy Statement.