|
|

This chapter describes how to install the Secure Content Accelerator as a free-standing or rack-mounted unit. Suggestions for using the Secure Content Accelerator in conjunction with other networking hardware are described in Appendix B , Deployment Examples.
This chapter contains the following sections:
Before you select an installation site for the Secure Content Accelerator, read the electrical, environmental, and physical requirements as described in Appendix A.
To install the Secure Content Accelerator, you need the following tools and equipment:
The Secure Content Accelerator shipment contains the following items:
 |
Note A tamper-evident sticker is affixed to the Secure Content Accelerator. When using the device for FIPS-compliant operation, this sticker must remain in place and untouched. |
To unpack the Secure Content Accelerator:
1. Remove all enclosed packing materials. Save the packing materials in case you need to repack the Secure Content Accelerator later.
2. Remove all accessories from the shipping carton.
3. Check the accessories against the items listed in the section "Shipment Contents".
Prior to installing the Secure Content Accelerator, observe the following installation requirements:
Before you begin, you will need the mounting brackets and six screws shipped with the Secure Content Accelerator, a #2 Phillips screwdriver, rack-mounting screws and an appropriate screwdriver.
1. Position the Secure Content Accelerator with the front panel facing you.
2. Position a mounting bracket on one side of the chassis, aligning the holes in the bracket with the screw holes on the chassis.
3. Secure the bracket to the chassis with three screws and the Phillips screwdriver.
4. Repeat steps 2 and 3 to install a mounting bracket on the other side of the chassis.
5. Raise the Secure Content Accelerator to the installation height. Align the screw holes of the mounting brackets with the holes on the equipment rack.
6. Use the appropriate screwdriver and screws to secure each mounting bracket to each side of the rack.
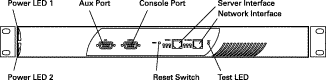
The front panel of the Secure Content Accelerator, shown in Figure 2-1, contains the following connectors, switches, and LEDs:
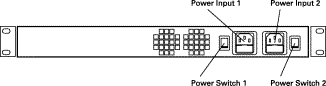
The rear panel of the Secure Content Accelerator, shown in Figure 2-2, contains the following connectors and switches:
| LED Name | Color | State | SCA | SCA2 |
|---|---|---|---|---|
LK | Green | Off | No link established | N/A |
On | Link established | N/A | ||
LNK | Green | Off | N/A | No link established |
On | N/A | Link established | ||
TX | Amber | Blinking | Transmit activity detected | N/A |
ACT | Amber | Blinking | N/A | Transmit activity detected |
RX | Green | Blinking | Receive activity detected | N/A |
100 | Green | Off | N/A | 10Mbps |
On | N/A | 100Mbps | ||
White | Off | Power supply is not working | ||
On | Power supply is working | |||
Test | Amber | Off | Self-diagnostics are successful | |
On | Self-diagnostics are running | |||
SCA and SCA2 models can be differentiated by the text on the product label.
The Secure Content Accelerator is powered by dual AC power supplies. Before you install the power cords, ensure that you have read Appendix A for electrical specifications.
1. Ensure that the Secure Content Accelerator power switches are in the 0 (off) position.
2. Attach the power cables to the Secure Content Accelerator by plugging the AC power cord connector into the power receptacle at the rear panel.
3. Plug the power cords into dedicated three-wire grounding receptacles.
4. Switch the power switches to the 1 (on) position.
 |
Note Connect the power supplies to different circuits to further ensure appliance availability. |
This section describes how to attach the Secure Content Accelerator to Ethernet. For network deployment instructions and suggestions, see Appendix B, Deployment Examples.
1. Connect the "Network" port to the Internet.
2. Connect the "Server" port to the servers (or to the "Network" port if using one-port mode).
3. Check the LK LEDs for connection viability. If one or both LK LEDs are not lit, see Appendix D, Troubleshooting, for suggestions.
A version of the configuration utility is stored on the SSL appliance. You may use a serial or Telnet connection, or a Web browser to use the device-stored version for configuration. To install the remote configuration manager, follow the appropriate instructions below.
 |
Note Certain functions are not available in all configuration methods. See Appendix C for more information. |
 |
Note When using the device in FIPS-compliant operation, only a serial management connection is allowed. |
You must be logged into the system as a root user before installing the software.
1. Insert the CD-ROM into the computer CD-ROM drive.
2. Enter the following commands:
mount -o map=off /mnt/cdrom
cd /mnt/cdrom/Linux/i386
./install_csca
To run the configuration manager, enter csacfg at a Linux shell prompt.
You must be logged into the system as a root user before installing the software.
1. Insert the CD-ROM into the computer CD-ROM drive.
2. Enter the following command:
pkgadd -d /cdrom/cdrom0/Solaris/Sparc
3. Respond to the following screen prompt, pressing Enter to install the software:
The following packages are available:
1. CSCAconfg Cisco Configuration Manager
Select package(s) you wish to process (or "all" to process all packages). (default: all) [?,??,q]
4. Type q to exit after installation.
To run the configuration manager, enter csacfg at a Unix shell prompt.
1. Insert the CD-ROM into the computer CD-ROM drive.
2. Double-click the My Computer icon to open it.
3. Double-click the CD icon.
4. Double-click the MSWin icon to open the directory.
5. Double-click the WinNT4 icon (Windows NT) or Win2K icon (Windows 2000) to open the directory.
6. Double-click the setup.exe application to run it. An Install Shield application opens. Follow the instructions on the screen to install the configuration manager and OpenSSL.
To start the configuration manager, use the Start menu and point to Programs>Cisco Systems> Cisco Secure Content Acc. Manager, or double-click the shortcut on the desktop.
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
Posted: Wed Aug 21 01:58:36 PDT 2002
All contents are Copyright © 1992--2002 Cisco Systems, Inc. All rights reserved.
Important Notices and Privacy Statement.