|
|

This chapter describes how ATM connection services are established by adding ATM connections between ATM service interface ports in the network using ATM standard UNI 3.1 and Traffic Management 4.0. It describes BXM and ASI card operation and summarizes ATM connection parameter configuration
The chapter contains the following:
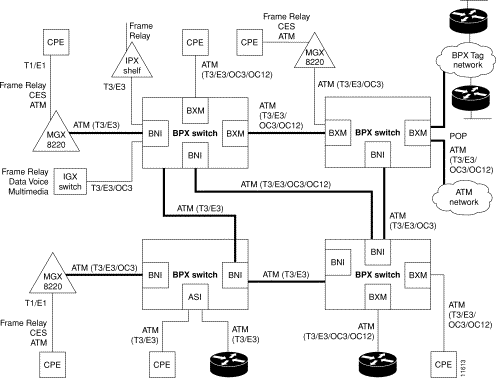
ATM connection services are established by adding ATM connections between ATM service interface ports in the network. ATM connections can originate and terminate on the ASI (ATM Service Interface) cards, on BXM-T3/E3, BXM-155 (OC-3), and BXM-622 (OC-12) cards configured for port (service access) operation on the BPX switch, or on the MGX 8220 (using the AUSM card for the MGX 8220). Frame relay to ATM network interworking connections are supported between either BXM or ASI cards to the IPX, IGX, or MGX 8220. Frame relay to ATM service interworking connections are supported between either BXM or ASI cards to FRSM cards on the MGX 8220.
Figure 7-1 is a depiction of ATM connections over a BPX switch network. It shows ATM connections via BXM-T3/E3, BXM-155, BXM-622, ASI-1, and ASI-155 cards, as well as over MGX 8220 switches. It also shows frame relay to ATM interworking connections over the MGX 8220, IPX, and IGX shelves. For further information on the MGX 8220, refer to the MGX 8220 Reference document.
. 
When an Extended Services Processor (ESP) is co-located with a BPX switch, ATM and Frame Relay Switched Virtual Circuits (SVCs) are supported in addition to Permanent Virtual Circuits (PVCs). For further information on ATM SVCs, refer to the CiscoWAN Service Node Extended Services Processor Installation and Operation document.
The ATM Forum Traffic Management 4.0 Specification defines five basic traffic classes:
Table 7-1 summarizes the major attributes of each of the traffic management classes:
| Attribute | CBR | rt-VBR | nrt-VBR | UBR | ABR |
|---|---|---|---|---|---|
Traffic Parameters |
|
|
|
|
|
PCR & CDVT | x | x | x | x | x |
SCR & MBS |
| x | x |
|
|
MCR |
|
|
|
| x |
QoS Parameters |
|
|
|
|
|
Pk-to-Pk CDV | x | x |
|
|
|
Max CTD | x | x |
|
|
|
CLR | x | x | x |
| nw specific |
Other Attributes |
|
|
|
|
|
Congestion Control Feedback |
|
|
|
| x |
Traffic parameters are defined as:
QoS (Quality of Service) parameters are defined as:
Congestion Control Feedback:
Standard ABR uses RM (Resource Management) cells to carry feedback information back to the connection's source from the connection's destination.
ABR sources periodically interleave RM cells into the data they are transmitting. These RM cells are called forward RM cells because they travel in the same direction as the data. At the destination these cells are turned around and sent back to the source as Backward RM cells.
The RM cells contain fields to increase or decrease the rate (the CI and NI fields) or set it at a particular value (the explicit rate ER field). The intervening switches may adjust these fields according to network conditions. When the source receives an RM cell it must adjust its rate in response to the setting of these fields.
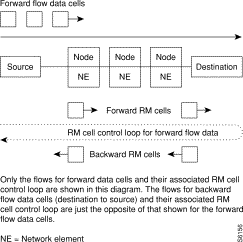
ABR sources and destinations are linked via bi-directional connections, and each connection termination point is both a source and a destination; a source for data that it is transmitting, and a destination for data that it is receiving. The forward direction is defined as from source to destination, and the backward direction is defined as from destination to source. Figure 7-2 shows the data cell flow in the forward direction from a source to its destination along with its associated control loop. The control loop consists of two RM cell flows, one in the forward direction (from source to destination) and the other in the backward direction (from destination to source).
The data cell flow in the backward direction from destination to source is not shown, nor are the associated RM cell flows. However, these flows are just the opposite of that shown in the diagram for forward data cell flows.
A source generates forward RM cells which are turned around by the destination and returned to the source as backward RM-cells. These backward RM-cells may carry feedback information from the network elements and/or the destination back to the source.
The parameter Nrm is defined as the maximum number of cells a source may send for each forward RM cell, i.e., one RM cell must be sent for every Nrm-1 data cells. Also, in the absence of Nrm-1 data cells, as an upper bound on the time between forward RM cells for an active source, an RM cell must be sent at least once every Trm msecs.
The BXM-T3/E3, BXM-155, and BXM-622 cards support ATM Traffic Management 4.0. The BXM cards are designed to support all the following service classes: Constant Bit Rate (CBR), Variable Bit Rate (VBR), Available Bit Rate (ABR with VS/VD, ABR without VS/VD, and ABR using Foresight), and Unspecified Bit Rate (UBR). ABR with VS/VD supports explicit rate marking and Congestion Indication (CI) control.
ForeSight may be used for congestion control across BPX/IGX/IPX switches for connections that have one or both end points terminating on ASI-T3/E3 or BXM cards. The ForeSight feature is a proprietary dynamic closed-loop, rate-based, congestion management feature that yields bandwidth savings compared to non-ForeSight equipped trunks when transmitting bursty data across cell-based networks. The BXM cards also support the VSVD congestion control mechanism as specified in the ATM Traffic Management 4.0 standards.
There are two connection addressing modes supported. The user may enter a unique VPI/VCI address in which case the BPX switch functions as a virtual circuit switch. Or the user may enter only a VPI address in which case all circuits are switched to the same destination port and the BPX switch functions as a virtual path switch in this case. The full ATM address range for VPI and VCI is supported.Virtual Path Connections are identified by an * in the VCI field. Virtual Circuit Connections specify both the VPI and VCI fields.
The VPI and VCI fields have significance only to the local BPX switch, and are translated by tables in the BPX switch to route the connection. Connections are automatically routed by the AutoRoute feature once the connection endpoints are specified.
ATM connections can be added using either the Cisco StrataView Plus Connection Manager or a node's command line interface (CLI). Typically, the Cisco StrataView Plus Connection Manager is the preferred method as it has an easy to use GUI interface. The CLI may be the method of choice in some special cases or during initial node setup for local nodes.
When adding ATM connections, first the access port and access service lines connecting to the customer CPE need to be configured. Also, the trunks across the network need to configured appropriately for the type of connection. Following that the addcon command may be used to add a connection, first specifying the service type and then the appropriate parameters for the connection.
For example, when configuring a BXM for CPE connections, the BXM is configured for port mode, a line is upped with the upln command and configured with the cnfln command. Then the associated port is configured with the cnfport command and upped with the upport command. Following this, the ATM connections are added via the addcon command with the syntax.
ATM connections for a BXM or ASI card are identified as follows:
The slot and port are related to the BPX switch hardware. Virtual path connections (VPCs) are identified by a "*" for the VCI field. Virtual circuit connections (VCCs) are identified by both a VPI and VCI field.
Connections added to the network are automatically routed once the end points are specified. This AutoRoute feature is standard with all BPX, IGX, and IPX switches. The network automatically detects trunk failures and routes connections around the failures.
The following parameters are entered for BXM addcon command. Depending upon the connection type, the user is prompted for the appropriate parameters as shown in the following:
addcon local_addr node remote_addr traffic_type....extended parameters
| Field | Value | Description |
|---|---|---|
local/remote_addr | slot.port.vpi.vci | desired VCC or VPI connection identifier |
node |
| slave end of connection |
traffic_type |
| Type of traffic, chosen from CBR, VBR, ABR, and UBR |
extended parameters |
| The traffic management and performance parameters associated with an ATM connection. |
The following figures and tables describe the parameters used to configure ATM connections:
The following figures list the connection parameters in the same sequence as they are entered when a connection is added:
The following figure shows the VSVD network segment and external segment options available when ABR Standard or ABR ForeSight is selected. ForeSight congestion control is useful when both ends of a connection do not terminate on BXM cards. At present, FCES (Flow Control External Segment) as shown in Figure 7-7 is not available for ABR with ForeSight.
The following figures list the connection parameters in the same sequence as they are entered when a connection is added:
| Connection Type | ATM Forum TM spec. 4.0 conformance definition | PCR Flow (1st leaky bucket) | CLP tagging (for PCR flow) | SCR Flow (2nd leaky bucket) | CLP tagging (for SCR flow) |
|---|---|---|---|---|---|
CBR | CBR.1 when policing set to 4 (PCR Policing only) | CLP(0+1) | no | off | n/a |
CBR | When policing set to 5 (off) | off | n/a | off | n/a |
UBR | UBR.1 when CLP setting = no | CLP(0+1) | no | off | n/a |
UBR | UBR.2 when CLP setting = yes | CLP(0+1) | no | CLP(0) | yes |
VBR, ABR, ATFR, ATFST | VBR.1 when policing set to 1 | CLP(0+1) | no | CLP(0+1) | no |
VBR, ABR, ATFR, ATFST | VBR.2 when policing set to 2 | CLP(0+1) | no | CLP(0) | no |
VBR, ABR, ATFR, ATFST | VBR.3 when policing set to 3 | CLP(0+1) | no | CLP(0) | yes |
VBR, ABR, ATFR, ATFST | when Policing set | CLP(0+1) | no | off | n/a |
VBR, ABR, ATFR, ATFST | when Policing set | off | n/a | off | n/a |
Note 1: - For UBR.2, SCR = 0
Note 2:
| PARAMETER WITH [DEFAULT SETTING] | BXM T3/E3, OC3 & OC12 RANGE | ASI T3/E3 RANGE | ASI-155 RANGE |
|---|---|---|---|
50- T3/E3 cells/sec 50 - OC3 50 - OC12 | T3: MCR - 96000 E3: MCR - 80000 Limited to MCR - 5333 cells/sec for ATFR connections. | OC3 (STM1): 0 - 353200
| |
%Util [100/100] for UBR [1/1] | 0 - 100% | 1 - 100% | 1 - 100% |
cells/sec 6 - T3/E3OC3/0C12 | T3: 0 - 96000 cells/sec E3: 0 - 80000 cells/sec | N/A | |
FBTC (AAL5 Frame Base Traffic Control): for VBR [disable] for ABR/UBR [enable] for Path connection [disable] | enable/disable | enable/disable | enable/disable |
|
for CBR [10000/10000], others [250000/250000] | 0 - 5,000,000 usec | T3/E3 1 - 250,000 usecs.
| OC3/STM1: 0 - 10000 usecs. |
enable/disable | enable/disable | Select disable, as only ABR w/o VSVD is supported. | |
FCES (Flow Control External Segment) [disable] | enable/disable | enable/disable | N/A |
Default Extended Parameters[enable] | enable/disable | enable/disable | N/A |
enable/disable | enable/disable | enable/disable | |
cells/sec 50 - T3/E3OC3/OC12 | T3: MCR - 96000:T3 E3: MCR - 80000: E3
Limited to MCR - 5333 cells/sec for ATFR connections. | OC3/STM1: 0 - 353200 | |
1 - 5,000,000cells | T3/E3: 10 - 24000 cells
| OC3 (STM1): 10 - 1000 cells | |
|
For CBR: [4] | 1 - VBR.1 2 - VBR.2 3 - VBR.3 4 - PCR policing only 5 - off | 1 - VBR.1 2 - VBR.2 3 - VBR.3 4 - PCR policing only 5 - off | 1 - VBR.1 2 - VBR.2 3 - VBR.3 4 - PCR policing only 5 - off
|
|
max[MCR, PCR/10] | MCR - PCR cells/sec | MCR - PCR cells/sec | N/A |
62 - 8000 msec | 1000 - 255000 msecs. | N/A | |
ABRSTD: 1 - 100 msec ABRFST: 3 - 255 msec | 20 - 250 msecs. | N/A | |
|
For ATFR/ATFST [1366/1366] | 0 - 61440 cells | Applies to T3/E3 only | ATFR: 1 - 1366 cells |
1 - 100% | 1 - 100% | N/A | |
1 - 100% | 1 - 100% | N/A | |
|
For ATFR/ATFST [100/100] | 1 - 100% | 1 - 100% | 0 - 100% |
|
For ForeSight: max[PCR/128, 10]
For ABR STD[128] |
If ForeSight, then in absolute (0 - PCR)
If ABR then 2n (1 - 32768) |
If ForeSight, then in absolute (0 - PCR)
If ABR, then 2n (1 - 32768) | N/A |
|
For ForeSight [93]
For ABR STD [16] |
If ForeSight, then % (0% - 100%)
If ABR then 2n (1 - 32768) |
If ForeSight, then % (0% - 100%)
If ABR, then 2n (1 - 32768) | N/A |
2 - 256 cells | N/A | N/A | |
0 - 16700 msec | N/A | N/A | |
0 - 1,048,320 cells (different max range from TM spec. but limited by firmware for CRM(4095 only) where CRM=TBE/Nrm | N/A | N/A | |
0 - 24000 cells | T3/E3 ABR: 0 - 24000 cells ATFR: 1 - 107 cells | 0 - 999 cells | |
Trunk cell routing restrict (Y/N) [Y] | Y/N | Y/N | Y/N |
| Parameter | Description |
|---|---|
PCR | Peak cell rate: The cell rate which the source may never exceed |
%Util | % Utilization; bandwidth allocation for: VBR, CBR, UBR it's PCR*%Util, for ABR it's MCR*%Util |
MCR | Minimum Cell Rate: A minimum cell rate committed for delivery by network |
CDVT | Cell Delay Variation Tolerance: Controls time scale over which the PCR is policed |
FBTC (AAL5 Frame Basic Traffic Control) | To enable the possibility of discarding the whole frame, not just one non-compliant cell. This is used to set the Early Packet Discard bit at every node along a connection. |
VSVD | Virtual Source Virtual Destination: (see Meaning of VSVD and Flow Control External Segments, Figure 7-7) |
FCES (Flow Control External Segments) | (see Meaning of VSVD and Flow Control External Segments, Figure 7-7) |
SCR | Sustainable Cell Rate: Long term limit on the rate a connection can sustain |
MBS | Maximum Burst Size: Maximum number of cells which may burst at the PCR but still be compliant. Used to determine the Burst Tolerance (BT) which controls the time scale over which the SCR is policed |
Policing | (see definitions of Traffic Policing, Table 7-2) |
VC QDepth | VC Queue Depth |
CLP Hi | Cell Loss Priority Hi threshold (% of VC QMax) |
CLP Lo/EPD | Cell Loss Priority Low threshold (% of VC QMax)/Early Packet Discard. If AAL5 FBTC = yes, then for the BXM card this is the EPD threshold setting. For ASI cards, regardless of the FBTC setting, this is the CLP Lo setting. |
EFCI | Explicit Forward Congestion Indication threshold (% of VC QMax) |
ICR | Initial Cell Rate: The rate at which a source should send initially and after an idle period |
ADTF (ATM Forum TM 4.0 term) | The Allowed-Cell-Rate Decrease Factor: Time permitted between sending RM-cells before the rate is decreased to ICR |
Trm (ATM Forum TM 4.0 term) | An upper bound on the time between forward RM-cells for an active source, i.e., RM cell must be sent at least every Trm msec |
RIF (ATM Forum TM 4.0 term) | Rate Increase Factor: Controls the amount by which the cell transmission rate may increase upon receipt of an RM cell |
RDF (ATM Forum TM 4.0 term) | Rate Decrease Factor: Controls the amount by which the cell transmission rate may decrease upon receipt of an RM cell |
Nrm (ATM Forum TM 4.0 term), BXM only. | Nrm Maximum number of cells a source may send for each forward RM cell, i.e. an RM cell must be sent for every Nrm-1 data cells |
FRTT (ATM Forum TM 4.0 term), BXM only. | Fixed Round Trip Time: the sum of the fixed and propagation delays from the source to a destination and back |
TBE (ATM Forum TM 4.0 term), BXM only. | Transient Buffer Exposure: The negotiated number of cells that the network would like to limit the source to sending during start-up periods, before the first RM-cell returns. |
IBS | Initial Burst Size
|
Trunk cell routing restriction (Y/N) [Y] | The default (Y) restricts ATM connection routes to include only ATM trunks. Selecting (N) allows the network to route these connections over non-ATM trunks (e.g., Fastpacket trunks). |
The CBR (constant bit rate) category is a fixed bandwidth class. CBR traffic is more time dependent, less tolerant of delay, and generally more deterministic in bandwidth requirements. CBR is used by connections that require a specific amount of bandwidth to be available continuously throughout the duration of a connection. Voice, circuit emulation, and high-resolution video are typical examples of traffic utilizing this type of connection. A CBR connection is allowed to transmit cells at the peak rate, below the peak rate, or not at all. CBR is characterized by peak cell rate (PCR).
The parameters for a CBR connection are shown in Figure 7-3 in the sequence in which they occur during the execution of the addcon command. The CBR policing definitions are summarized in Table 7-5.
| Connection Type | ATM Forum TM spec. 4.0 conformance definition | PCR Flow (1st leaky bucket) | CLP tagging (for PCR flow) | SCR Flow (2nd leaky bucket) | CLP tagging (for SCR flow) |
|---|---|---|---|---|---|
CBR | CBR.1 when policing set to 4 (PCR Policing only) | CLP(0+1) | no | off | n/a |
CBR | When policing set to 5 (off) | off | n/a | off | n/a |
VBR (variable bit rate) connections may be classified as rt-VBR or nrt-VBR connections.
The rt-VBR (real-time variable bit rate) category is used for connections that transmit at a rate varying with time and that can be described as bursty, often requiring large amounts of bandwidth when active. The rt-VBR class is intended for applications that require tightly constrained delay and delay variation. An example of rt-VBR is video conferencing which requires real-time data transfer with bandwidth requirements that can vary in proportion to the dynamics of the video image at any given time. The rt-VBR category is characterized in terms of PCR, SCR (sustained cell rate), and MBS (maximum burst size).
The nrt-VBR (non-real time variable bit rate) category is used for connections that are bursty but are not constrained by delay and delay variation boundaries. For those cells in compliance with the traffic contract, a low cell loss is expected. Non-time critical data file transfers are an example of an nrt-VBR connection. A nrt-VBR connection is characterized by PCR, SCR, and MBS.
Configuring VBR connections. The characteristics of rt-VBR or nrt-VBR are supported by appropriately configuring the parameters of the VBR connection.
The parameters for a VBR connection are shown in Figure 7-4 in the sequence in which they occur during the execution of the addcon command. The VBR policing definitions are summarized in Table 7-6.
| Connection Type | ATM Forum TM spec. 4.0 conformance definition | PCR Flow (1st leaky bucket) | CLP tagging (for PCR flow) | SCR Flow (2nd leaky bucket) | CLP tagging (for SCR flow) |
|---|---|---|---|---|---|
VBR, ABR, ATFR, ATFST | VBR.1 when policing set to 1 | CLP(0+1) | no | CLP(0+1) | no |
VBR, ABR, ATFR, ATFST | VBR.2 when policing set to 2 | CLP(0+1) | no | CLP(0) | no |
VBR, ABR, ATFR, ATFST | VBR.3 when policing set to 3 | CLP(0+1) | no | CLP(0) | yes |
VBR, ABR, ATFR, ATFST | when Policing set | CLP(0+1) | no | off | n/a |
VBR, ABR, ATFR, ATFST | when Policing set | off | n/a | off | n/a |
An ATFR (ATM to Frame Relay) connection is a frame relay to ATM connection and is configured as a VBR connection, with a number of the ATM and frame relay connection parameters being mapped between each side of the connection.
The parameters for an ATFR connection are shown in Figure 7-5 in the sequence in which they occur during the execution of the addcon command.
The term ABR is used to specify one of the following:
The ABR (available bit rate) category utilizes a congestion flow control mechanism to control congestion during busy periods and to take advantage of available bandwidth during less busy periods. The congestion flow control mechanism provides feedback to control the connections flow rate through the network in response to network bandwidth availability. The ABR service is not restricted by bounding delay or delay variation and is not intended to support real-time connections. ABR is characterized by: PCR and MCR.
Policing for ABR connections is the same as for VBR connections which are summarized in Table 7-6.
The ABR connections are configured as either ABR Standard (ABRSTD) connections or as ABR ForeSight (ABRFST) connections.
The parameters for an ABRSTD connection are shown in Figure 7-6 in the sequence in which they occur during the execution of the addcon command.
The ABRSTD connection supports all the features of ATM Standards Traffic Management 4.0 including VSVD congestion flow control.
VSVD and flow control with external segments are shown in Figure 7-7.
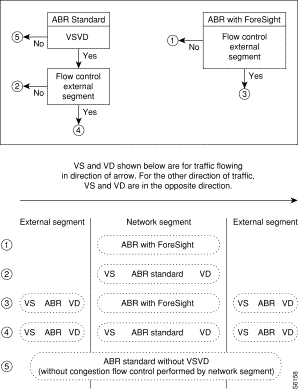
The ABRFST connection uses the propriety ForeSight congestion control and is useful when configuring connections on which both ends do not terminate on BXM cards.
The parameters for an ABRFST connection are shown in Figure 7-8 in the sequence in which they occur during the execution of the addcon command.
An ATFST connection is a frame relay to ATM connection that is configured as an ABR connection with ForeSight. ForeSight congestion control is automatically enabled when connection type ATFST is selected. A number of the ATM and frame relay connection parameters are mapped between each side of the connection.
The parameters for an ATFST connection are shown in Figure 7-9 in the sequence in which they occur during the execution of the addcon command.
The unspecified bit rate (UBR) connection service is similar to the ABR connection service for bursty data. However, UBR traffic is delivered only when there is spare bandwidth in the network. This is enforced by setting the CLP bit on UBR traffic when it enters a port.
Therefore, traffic is served out to the network only when no other traffic is waiting to be served first. The UBR traffic does not affect the trunk loading calculations performed by the switch software.
The parameters for a UBR connection are shown in Figure 7-10 in the sequence in which they occur during the execution of the addcon command.
The UBR policing definitions are summarized in Table 7-7.
| Connection Type | ATM Forum TM spec. 4.0 conformance definition | PCR Flow (1st leaky bucket) | CLP tagging (for PCR flow) | SCR Flow (2nd leaky bucket) | CLP tagging (for SCR flow) |
|---|---|---|---|---|---|
UBR | UBR.1 when CLP setting = no | CLP(0+1) | no | off | n/a |
UBR | UBR.2 when CLP setting = yes | CLP(0+1) | no | CLP(0) | yes |
Traffic Policing, also known as Usage Parameter Control (UPC), is implemented using either an ATM Forum single or dual-leaky bucket algorithm. The buckets represent a GCRA (Generic Cell Rate Algorithm) defined by two parameters:
If the cells are clumped too closely together, they are non-compliant and are tagged or discarded as applicable. If other cells arrive on time or after their expected arrival time, they are compliant, but three is no accrued credit.
A GCRA viewpoint is as follows:
CBR traffic is expected to be at a constant bit rate, have low jitter, and is configured for a constant rate equal to Peak Cell Rate (PCR). The connection is expected to be always at peak rate.
When a connection is added, a VPI.VCI address is assigned, and the UPC parameters are configured for the connection. For each cell in an ATM stream seeking admission to the network, the VPI.VCI addresses are verified and each cell is checked for compliance with the UPC parameters. The CBR cells are not enqueued, but are processed by the policing function and then sent to the network unless discarded.
For CBR, traffic policing is based on:
The CBR connection may be configured with policing selected as either 4 or 5. With policing set to 5, there is no policing. With policing set to 4, there is single leaky bucket PCR policing as shown in Figure 7-11. The single leaky bucket polices the PCR compliance of all cells seeking admission to the network, both those with CLP = 0 and those with CLP =1. Cells seeking admission to the network with CLP set equal to 1 may have either encountered congestion along the user's network or may have lower importance to the user and have been designated as eligible for discard in the case congestion is encountered. If the bucket depth CDVT (0+1) limit is exceeded, it discards all cells seeking admission. It does not tag cells. If leaky bucket 1 is not full, all cells (CLP =0 and CLP=1) are admitted to the network.
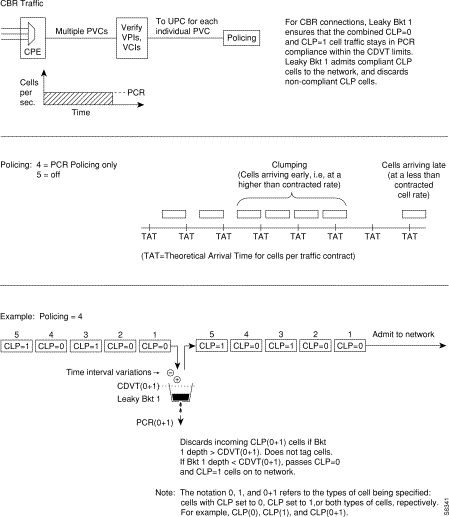
Figure 7-12 shows a CBR.1 connection policing example, with policing set to 4, where the CDVT depth of the single leaky bucket is not exceeded, and all cells, CLP(0) and CLP(1) are admitted to the network.
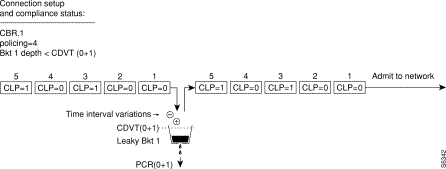
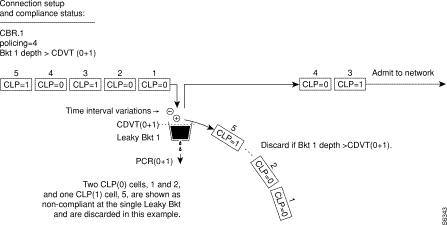
Figure 7-13 shows a CBR connection policing example, with policing =4, where the CDVT(0+1) of the single leaky bucket is exceeded and non-compliant cells are discarded. The leaky bucket only discards cells; it does not tag them
The contract for a variable bit rate connection is set up based on an agreed upon sustained cell rate (SCR) with allowance for occasional data bursts at a Peak Cell Rate (PCR) as specified by maximum burst size MBS.
When a connection is added, a VPI.VCI address is assigned, and UPC parameters are configured for the connection. For each cell in an ATM stream, the VPI.VCI addresses are verified and each cell is checked for compliance with the UPC parameters as shown in Figure 7-14.
The VBR cells are not enqueued, but are processed by the policing function and then sent to the network unless discarded.
For VBR, traffic policing, depending on selected policing option, is based on:
The policing options, selected by entering 1-5 in response to the policing choice prompt, are as follows for VBR connections:
VBR.1 VBR with policing set to 1. | CLP(0+1) cells compliant with leaky bucket 1 are passed to leaky bucket 2; non-compliant cells are discarded. CLP(0+1) cells compliant with leaky bucket 2 are admitted to the network; non-compliant cells are discarded. |
VBR.2 VBR with policing set to 2. | CLP(1) cells compliant with leaky bucket 1 are admitted to the network; non-compliant CLP(0+1) cells are dropped. CLP(0) cells compliant with leaky bucket 1 are applied to leaky bucket 2; non-compliant cells are dropped. CLP(0) cells compliant with leaky bucket 2 are admitted to the network; non-compliant cells are dropped. |
VBR.3 VBR with policing set to 3.
| CLP(1) cells compliant with leaky bucket 1 are admitted to the network; non-compliant CLP(0+1) cells are dropped. CLP(0) cells compliant with leaky bucket 1 are applied to leaky bucket 2; non-compliant cells are dropped. CLP(0) cells compliant with leaky bucket 2 are admitted to the network; non-compliant cells are tagged and admitted to the network. |
VBR with policing set to 4. | CLP(0+1) cells compliant with leaky bucket 1 are admitted to the network; non-compliant cells are dropped. Leaky bucket 2 is not active. |
VBR with policing set to 5. | Policing is off, so there is no policing of cells on ingress. |
Leaky bucket 1 polices for the PCR compliance of all cells seeking admission to the network, both those with CLP = 0 and those with CLP =1. For example, cells seeking admission to the network with CLP set equal to 1 may have either encountered congestion along the user's network or may have lower importance to the user and have been designated as eligible for discard in the case congestion is encountered. If the bucket depth in the first bucket exceeds CDVT (0+1), it discards all cells seeking admission. It does not tag cells.
With policing set to 1 (VBR.1), all cells (CLP=0 and CLP=1) that are compliant with leaky bucket 1, are sent to leaky bucket 2. With policing set to 2 (VBR.2) or to 3 (VBR.3), all CLP=1 cells compliant with leaky bucket 1 are admitted directly to the network, and all CLP=0 cells compliant with leaky bucket 1 are sent to leaky bucket 2.
For VBR connections, the purpose of leaky bucket 2 is to police the cells passed from leaky bucket 1 for conformance with maximum burst size MBS as specified by BT and for compliance with the SCR sustained cell rate. The types of cells passed to leaky bucket 2 depend on how policing is set:
Figure 7-15 shows a VBR connection policing example, with policing set to 4, leaky bucket 1 compliant, and all cells being admitted to the network
.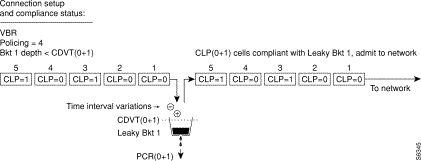
Figure 7-16 shows a VBR connection policing example, with the policing set to 4, and leaky bucket 1 non-compliant which indicates that the connection has exceeded the PCR for a long enough interval to exceed the CDVT (0+1) limit. Non-compliant cells with respect to leaky bucket 1 are discarded.
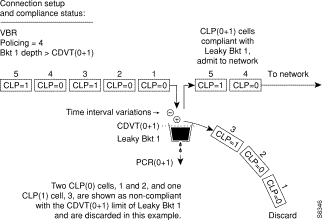
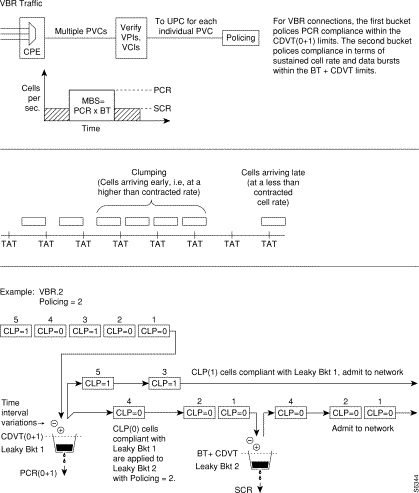
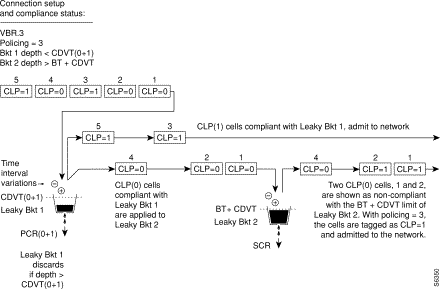
Figure 7-17 shows a VBR.2 connection policing example, with policing = 2, and both buckets compliant. Leaky bucket two is policing the CLP(0) cell stream for conformance with maximum burst size MBS (as specified by BT), and for compliance with the SCR sustained cell rate.
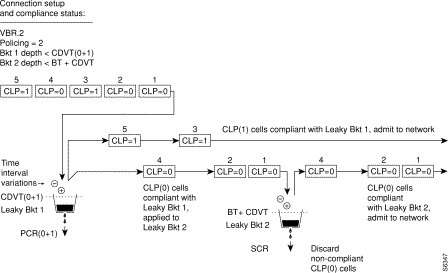
Figure 7-18 shows a VBR.2 connection policing example, with policing set to 2, and leaky bucket 2 non-compliant. Leaky bucket 2 is shown policing the CLP(0) cell stream for conformance with maximum burst size MBS (as specified by BT), and for compliance with SCR (sustained cell rate). In this example (policing set to 2), CLP tagging is not enabled, so the cells that have exceeded the BT + CDVT limit are discarded. In the example, either the sustained cell rate could have been exceeded for an excessive interval, or a data burst could have exceeded the maximum allowed burst size.
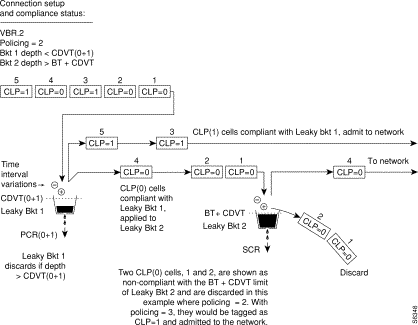
Figure 7-19 shows a VBR.1 connection policing example, with policing set to 1, and both buckets compliant. Leaky bucket 1 is policing the CLP (0+1) cell stream for conformance with the PCR limit. Leaky bucket 2 is policing the CLP (0+1) cell stream for conformance CDVT plus maximum burst size MBS (as specified by BT), and for compliance with SCR sustained cell rate.
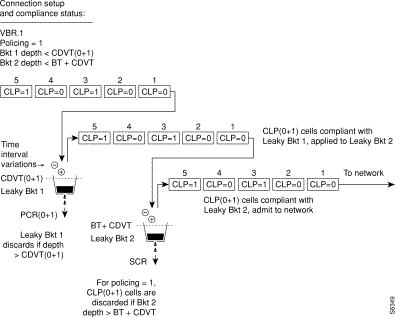
Figure 7-20 shows a VBR.3 connection policing example, with policing set to 3, and Leaky bucket 2 shown as non-compliant. Leaky bucket 2 is shown policing the CLP(0) cell stream for conformance with maximum burst size MBS (as specified by BT), and for compliance with SCR sustained cell rate. For the policing = 3 selection, CLP tagging is enabled, so the cells that have exceeded the BT + CDVT(0+1) limit are tagged as CLP=1 cells and admitted to the network. In this example, either the sustained cell rate could have been exceeded for an excessive interval, or a data burst could have exceeded the maximum burst size allowed.
Available Bit Rate (ABR) connections are policed the same as the VBR connections, but in addition use either the ABR Standard with VSVD congestion flow control method or the ForeSight option to take advantage of unused bandwidth when it is available.
The contract for a unspecified bit rate connection is similar to the ABR connection service for bursty data. However, UBR traffic is delivered only when there is spare bandwidth in the network.
When a connection is added, a VPI.VCI address is assigned, and UPC parameters are configured for the connection. For each cell in an ATM stream, the VPI.VCI addresses are verified and each cell is checked for compliance with the UPC parameters as shown in Figure 7-21.
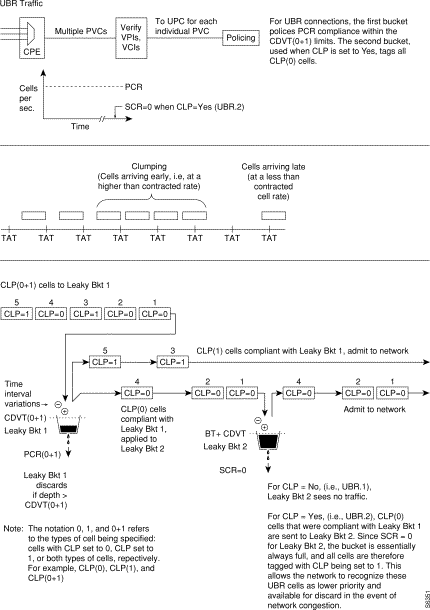
Leaky bucket 1 polices the UBR connection for PCR compliance. When CLP=No (UBR.1), all cells that are compliant with leaky bucket 1 are applied to the network. However, these cells are treated with low priority in the network with % utilization default of 1%.
When CLP=Yes (UBR.2), CLP(0) cells that are compliant with leaky bucket 1 are sent to leaky bucket 2. Since SCR=0 for leaky bucket 2, the bucket is essentially always full, and all the CLP(0) cells sent to leaky bucket 2 are therefore tagged with CLP being set to 1. This allows the network to recognize these UBR cells as lower priority cells and available for discard in the event of network congestion.
With the introduction of traffic shaping for CBR, VBR, and UBR, the user has the option to provide traffic shaping for these connections types on the BXM. Previously, only ABR utilized traffic shaping. Traffic shaping involves passing CBR, VBR, or UBR traffic streams through VC queues for scheduled rate shaping.
Traffic shaping is performed on a per port basis. When traffic shaping is enabled, all traffic exiting the port (out to the network) is subject to VC scheduling based on the parameters configured by the user for the connection.
Figure 7-22 shows an example of traffic shaping. In this example, port 1 is configured to perform traffic shaping. Note that all the ATM cells regardless of class of service pass through the VC queues before leaving the card when traffic shaping is enabled. In the example, port 2 is not configured for traffic shaping, and only the ABR traffic with FCES (flow control external segment) passes through the VC queues.
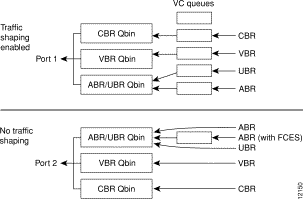
Traffic shaping is disabled by default. The cnfport command is used to enable and disable the function on a per port basis. No connections should be enabled on the port prior to changing the port traffic shaping parameter. If there are existing connections when the port is toggled, then these connections will not be updated unless the card is reset, connections are rerouted, a switchcc occurs, or the user modifies the connection parameters.
Traffic shaping rates are listed in Table 7-8.
| Service Type | MCR | PCR |
|---|---|---|
CBR | PCR | PCR |
VBR | SCR * %Util | PCR |
UBR | 0 | PCR |
ABR | MCR * %Util | PCR |
The following is a listing of the LMI and ILMI parameters for the ASI and BXM:
For ILMI information, refer to Table 7-9
| Parameter | Description |
|---|---|
VPI.VCI | VCCI for ILMI signaling channel equal 0.16 |
Polling Enabled | Keep-alive polling |
Trap Enabled | VCC change of state traps |
Polling Interval | Time between GetRequest polls |
Error Threshold | Number of failed entries before ILMI link failure is declared. |
Event Threshold | Number of successful polls before ILMI link failure is cancelled. |
Addr Reg Enab | SVC Address Registration procedures enabled. |
For the LMI information, refer to Table 7-10.
| Parameter | Description |
|---|---|
VPI.VCI | VCCI for LMI signaling channel equal 0.31 |
Polling Enable | Keep-alive polling |
T393 | Status Enquiry timeout value |
T394 | Update Status timeout value |
T396 | Status Enquiry polling timer |
N394 | Status Enquiry retry count |
N395 | Update Status retry count |
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
Posted: Mon Jan 15 19:35:40 PST 2001
All contents are Copyright © 1992--2001 Cisco Systems, Inc. All rights reserved.
Important Notices and Privacy Statement.