|
|

This chapter tells you how to complete quick configuration of the system using the VPN 3002 Hardware Client Manager.
Quick configuration supplies the minimal parameters needed to make the VPN 3002 operational.
The VPN 3002 Hardware Client Manager is an HTML-based configuration, administration, and monitoring system built into the VPN 3002. To use it, you need only connect to the VPN 3002 using a PC and browser on the same private network as the VPN 3002.
As you proceed, refer to the data you recorded in Table 2-2.
The figures that follow show only the main frame of the Manager window. To use features in the other frames, see the "Understanding the VPN 3002 Hardware Client Manager Window" section.
Access and log into the VPN 3002 Hardware Client Manager using these steps:
Step 1 Start the browser. See the "Browser Requirements" section. We recommend using Microsoft Internet Explorer for best results. Maximize the browser window for easiest reading.
Step 2 With the browser, connect to the IP address of the VPN 3002 on your private interface. Enter the IP address (for example, 192.168.10.1) in the Address or Location field. The browser displays the login screen.
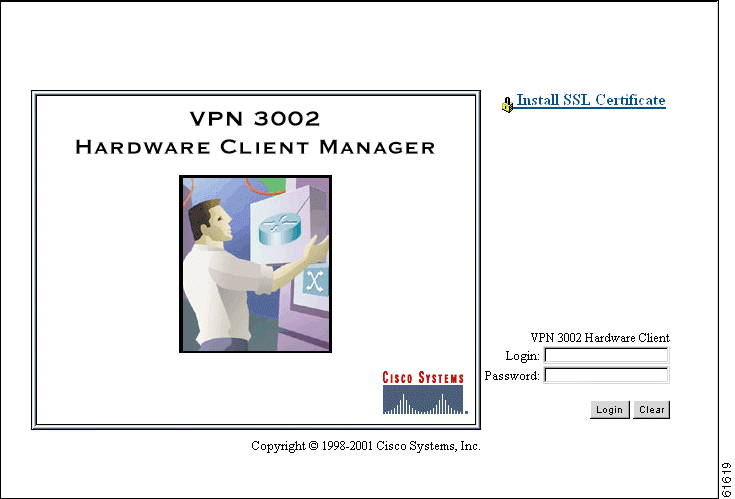
Step 3 Log in. Entries are case-sensitive, so type them exactly as shown. With Microsoft Internet Explorer, you can click the Tab key to move from field to field; with other browsers, you may have to change fields with the mouse. If you make a mistake, click the Clear button and start over.
*****.)
The Manager displays the VPN 3002 Hardware Client Manager Main screen.
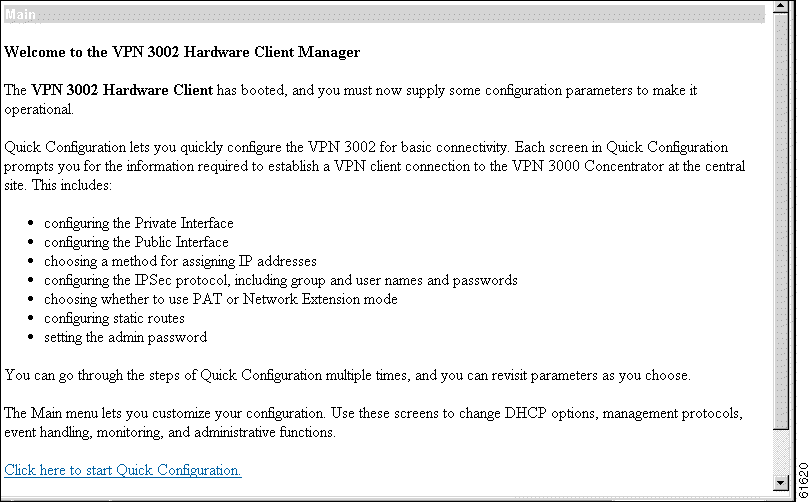
To start quick configuration, click the underlined link that says Click here to start Quick Configuration. The Manager displays the Time and Date screen, which is the first of the quick configuration screens.
Text entries are case-sensitive; that is, admin and ADMIN are different passwords.
After you make an entry in a field, do not press the keyboard Enter key. Just move the cursor from field to field. With Microsoft Internet Explorer, you can press the Tab key to move from field to field; other browsers may work differently.
On any screen where it appears, click the Back button to return to the previous screen.
Configuration entries take effect as soon as you click the Apply or Continue button, and they constitute the active or running configuration.
The banner across the top of the screen indicates the parameter currently displayed, both by showing in the top line the complete path to that parameter, for example, Configuration | Quick | Time and Date, and also by highlighting an abbreviated name of the parameter in the line below, such as Time. For configured parameters, the Manager adds a checkmark to the side of its abbreviated name.
You can go through the steps of quick configuration as many times as you want, and you do not have to proceed sequentially. You can also revisit individual parameters. To reach a screen, click either
If you make a mistake and see an Error screen with the message, "An error has occurred while attempting to perform the operation," and you return to the screen where you were working, carefully check all your previous entries on that screen. The Manager attempts to retain valid entries, but invalid entries are lost. See "Troubleshooting and System Errors" for more details.
Do not use the browser navigation toolbar buttons Back, Forward, or Refresh / Reload with the VPN 3002 Hardware Client Manager unless instructed to do so. To protect access security, clicking Refresh / Reload automatically logs out the Manager session. Clicking Back or Forward may display stale Manager screens with incorrect data or settings. We recommend that you hide the browser navigation toolbar to prevent mistakes while using the VPN Hardware Client Manager.
The Manager displays the Configuration | Quick | Time and Date screen.
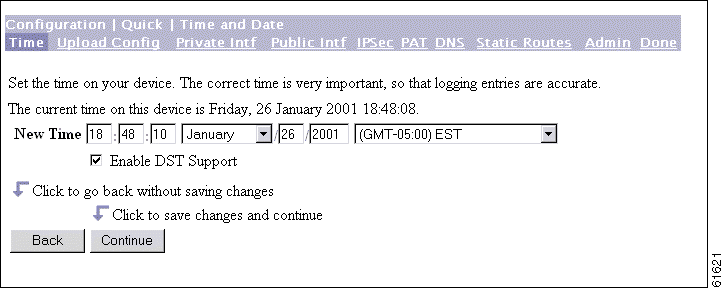
This screen lets you set the time and date on this device.
Step 1 The screen shows the current time and date on the device. The values in the New Time fields are the time on the browser PC, but any entries you make apply to the VPN 3002.
Step 2 Click Continue to save your changes and proceed with quick configuration.
The Manager displays the Configuration | Quick | Upload Config screen.
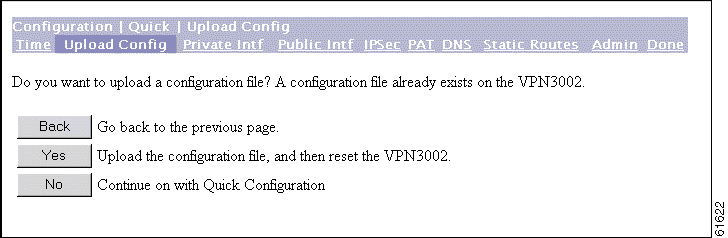
This feature enables you to use HTTP or HTTPS to transfer (upload) configuration files from your PC, or from a system accessible to your PC, to the VPN 3002 flash memory.
Step 1 If you do not want to upload a configuration file, click No, and continue to the next section.
Step 2 To upload an already existing configuration file, click Yes.
The Manager displays the Configuration | Quick | Upload Config | Browse screen.
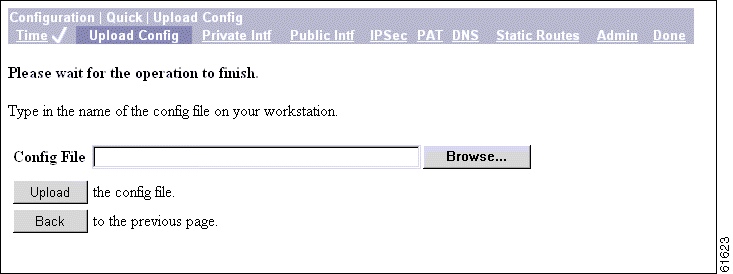
.
Step 1 In the Config File field, either enter the path to or use the Browse button to find the path to and name of the configuration file you want to upload.
Step 2 Click Upload to use this file as your configuration file, or click Back to return to the Configuration | Quick | Upload Config screen.
The VPN 3002 Configuration | Quick | Private Interface screen displays.
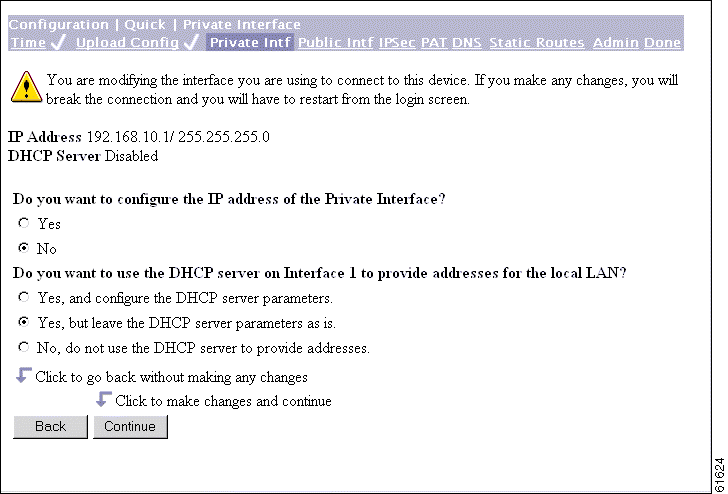
This screen lets you configure the VPN 3002 private interface, which is the interface to your private network (internal LAN).
The screen displays the current configuration settings.
 |
Note For the VPN 3002 to operate in Network Extension mode, you must change the private interface IP address from the default of 192.168.10.1. |
 |
Caution If you modify any parameters of the interface that you are currently using to connect to the VPN 3002, you will break the connection, and you will have to restart the Manager and quick configuration from the login screen. |
Step 1 To reconfigure the IP address for the private interface, select Yes. The Manager displays the Configuration | Quick | Private Interface | Address screen. See Figure 3-7 and perform the steps in that section.
Step 2 To use the VPN 3002 DHCP server to provide addresses for the local LAN, select one of the Yes options. If you select Yes, and configure the DHCP server parameters, the Manager displays the Configuration | Quick | Private Interface | DHCP Server screen. See Figure 3-8 and perform the steps in that section.
Step 3 When you have made your selections, click Continue to apply your changes and proceed. Click Back if you do not want to save your changes; you return to the Configuration | Quick | Private Interface screen.
The Configuration | Quick | Private Interface | Address screen lets you enter a new IP address and subnet mask for the private interface.
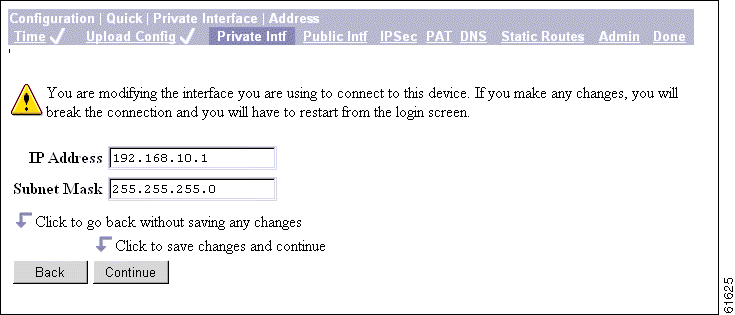
Step 1 In the IP Address field, enter the IP address for this interface, using dotted decimal notation (for example, 192.168.12.34). Be sure no other device is using this address on the network.
Step 2 In the Subnet Mask field, enter the subnet mask for this interface, using dotted decimal notation (for example, 255.255.255.0). The Manager automatically supplies a standard subnet mask appropriate for the IP address you just entered. For example, an IP address of 192.168.12.34 is a Class C address, and the standard subnet mask is 255.255.255.0. You can accept this entry or change it.
Step 3 Click Continue to save your changes. You must now restart the Manager and quick configuration from the login screen.
Click Back if you don't want to save your changes. You return to the Configuration | Quick | Private Interface screen.
The Configuration | Quick | Private Interface | DHCP Server screen lets you enable and configure the VPN 3002 to serve as a Dynamic Host Configuration Protocol (DHCP) server for the private network.
The DHCP server for the Private interface lets IP hosts in its network automatically obtain IP addresses from a limited pool of addresses for a fixed length of time, or lease period. Before the lease period expires, the VPN 3002 displays a message offering to renew it. If the lease is not renewed, the connection terminates when the lease expires, and the IP address becomes available for reuse. Using DHCP simplifies configuration since you do not need to know what IP addresses are considered valid on a particular network.
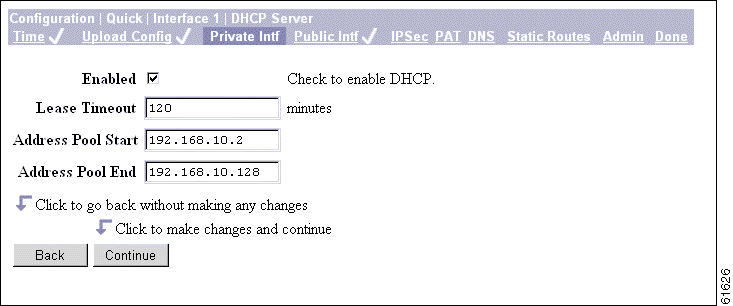
Step 1 Check the Enabled box to enable DHCP services for this interface.
Step 2 In the Lease Timeout field, enter the amount of time, in minutes, that DHCP clients own the IP address the DHCP server assigns. The minimum is 5, maximum is 500,000 and default is 120 minutes.
The Lease Timeout period you configure applies only when the tunnel to the VPN Concentrator is established. When the tunnel is not established, the Lease Timeout period is 5 minutes.
Step 3 In the Address Pool Start/End fields enter the range of IP addresses that this DHCP server can assign, using dotted decimal notation (for example, 10.10.99.51 - 10.10.99.178). Be sure no other device is using these addresses on the network. The default address pool is 127 IP addresses, and the start of the range is next IP address after that of the private interface. You can configure another range of IP addresses for the pool, but in no case can the pool have more than 127 addresses.
Step 4 Click Continue to save your changes.The Manager displays the Configuration | Quick |
Private Interface | DHCP server address pool screen.
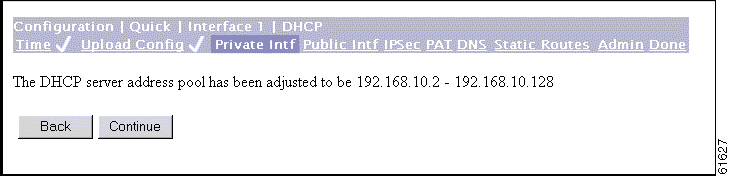
This screen confirms the DHCP server address pool range you entered.
Step 5 Click Continue to apply your choice and proceed. Click Back to return to the Configuration | Quick | Private Interface | DHCP Server screen.
Step 6 You might need to restart the Manager and quick configuration from the login screen.
The Manager displays the Configuration | Quick | Public Interface screen.
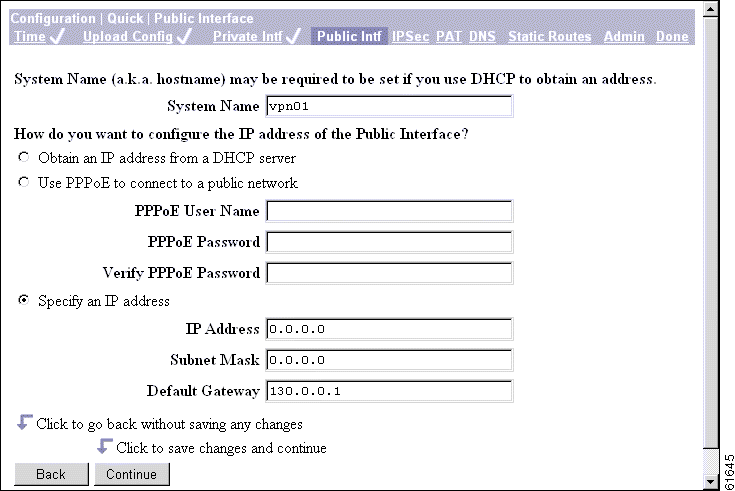
The public interface can obtain an IP address in one of three ways: using DHCP, PPPoE, or by static addressing. You configure one of these methods; depending on the method you choose, complete
Step 2, or Steps 3 and 4, or Steps 5-8.
Step 1 Assign a System Name, also known as a hostname. This is optional unless you use DHCP to obtain an IP address and your ISP requires a hostname.
Step 2 To have the DHCP server assign the public interface IP address, subnet mask, and default gateway, accept the default value, Obtain an IP address from a DHCP server.
Step 3 To have Point-to-Point Protocol over Ethernet (PPPoE) establish the connection between the VPN 3002 and the central-site VPN Concentrator, select Use PPPoE to connect to a public network.
Step 4 For a PPPoE connection, enter the PPPoE username and password. Verify the password by reentering it. The maximum number of characters for either username or password is 64.
Step 5 To assign a static IP address, subnet mask, and default gateway, select Specify an IP address.
Step 6 To specify an IP address, in the IP Address field, enter the IP address for this interface, using dotted decimal notation (for example, 192.168.12.34). Be sure no other device is using this address on the network.
Step 7 If you specify an IP address, in the Subnet Mask field, enter the subnet mask for this interface, using dotted decimal notation (for example, 255.255.255.0). The Manager automatically supplies a standard subnet mask appropriate for the IP address you just entered. For example, an IP address of 192.168.12.34 is a Class C address, and the standard subnet mask is 255.255.255.0. You can accept this entry or change it.
Step 8 If you specify an IP address, in the Default Gateway field, enter the IP address or hostname of the system to which the VPN 3002 should forward packets that do not have a static route. The default gateway must be accessible from the VPN 3002 public network. If you are using DHCP to acquire the public IP address, DHCP usually supplies the default gateway, and you should leave this field blank.
To specify no default gateway—which means the VPN 3002 drops unrouted packets—leave this field at 0.0.0.0.
Step 9 Click Continue to apply your choices to the interface and proceed. Click Back to return to the Configuration | Quick | Private Interface screen.
See the sections that follow for more information about DHCP, PPPoE, and static addressing.
Dynamic Host Configuration Protocol (DHCP) is a communications protocol that lets IP hosts in its network automatically obtain IP addresses from a limited pool of addresses for a fixed length of time, or lease period. Using DHCP simplifies configuration since you can manage the assignment of IP addresses from a central point. You do not need to manually enter an IP address for the public interface, and you do not need to know what IP addresses are considered valid on a particular network.
The DHCP server for the Public interface resides on the central-site VPN Concentrator.
PPP over Ethernet (PPPoE) is a proposal that specifies how a network client interacts with a service provider's equipment, such as a broadband modem—xDSL, cable, or wireless—to achieve access to high-speed data networks. It relies on the Ethernet and PPP standards. It includes an authentication strategy that requires a username and password to create a PPPoE session on the VPN 3002.
If a PPPoE session fails due to a PPP authentication failure, the VPN 3002 does not attempt a new session until 30 seconds have passed.
This option enables you to set a static IP address, subnet mask, and default gateway for the public interface.
After you click Continue to apply your changes to the Public Interface parameters, the Manager displays the Configuration | Quick | IPSec screen.
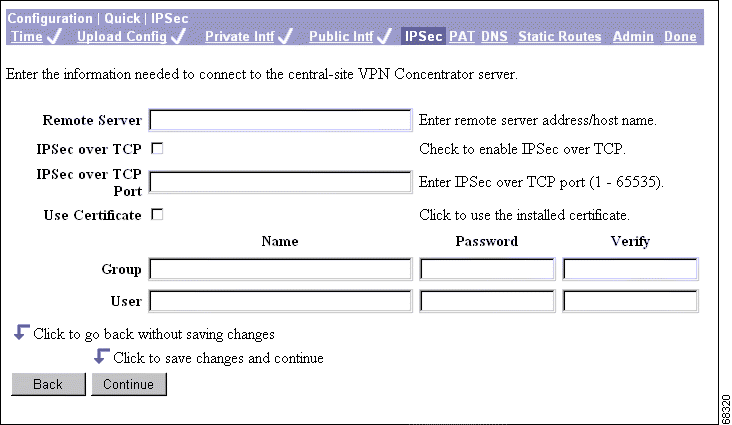
This screen lets you configure the IPSec parameters. IPSec is the protocol that enables the VPN 3002 to connect to the VPN Concentrator over a secure VPN tunnel.
Step 1 In the Remote Server field, enter the IP address or hostname of the VPN Concentrator to which this VPN 3002 hardware client connects. Note that to enter a hostname, a DNS server must be configured.
Step 2 Check the IPSec over TCP box if you want to connect using IPSec over TCP. This feature must also be enabled on the VPN Concentrator to which this VPN 3002 connects.
Step 3 Enter the IPSec over TCP port number. You can enter only one port. The port that you configure on this VPN 3002 must also be configured on the VPN Concentrator to which this VPN 3002 connects.
 |
Note If you enter a well-known port, for example port 80 (HTTP) or port 443 (HTTPS), the system displays a warning to notify you that the protocol associated with that port will no longer work on the public interface, with the consequence that you can no longer use a browser to manage the VPN 3002 through the public interface. To solve this problem, reconfigure the HTTP/HTTPS management to different ports. |
Step 4 Check the Use Certificate box to use digital certificates for authentication. If you are using digital certificates, there is no need to enter a group name and group password.
Step 5 Select a Certificate Transmission option. If you want the VPN 3002 to send the peer the identity certificate and all issuing certificates (including the root certificate and any subordinate CA certificates), click Entire certificate chain. If you want to send the peer only the identity certificate, click Identity certificate only.
Step 6 If you are not using digital certificates, in the Group Name field, enter a unique name for this group (maximum is 32 characters, case-sensitive). This is the same group name that you configure for this VPN 3002 on the central-site VPN Concentrator.
Step 7 If you are not using digital certificates, in the Group Password field, enter a unique password for this group (minimum is 4 characters, maximum is 32, case-sensitive). This is the same group password that you configure for this VPN 3002 on the central-site VPN Concentrator. The field displays only asterisks.
Step 8 In the Group Verify field, reenter the group password to verify it. The field displays only asterisks.
Step 9 If you are not using digital certificates, in the User Name field, enter a unique name for the user in this group (maximum is 32 characters, case-sensitive). This is the same username that you configure for this VPN 3002 on the central-site VPN Concentrator.
Step 10 In the User Password field, enter the password for this user (maximum is 32 characters). This is the same user password that you configure for the VPN 3002 on the central-site VPN Concentrator.
Step 11 In the User Verify field, reenter the user password to verify it. The field displays only asterisks.
 |
Note When you enable interactive hardware client authentication for a group, the VPN Concentrator pushes that policy to the VPN 3002s in the group. If you set a username and password on the VPN 3002 and later enable interactive hardware client authentication for the group to which the VPN 3002 belongs, the software deletes the username and password from the configuration file, and from the password field in the html interface. When you try to connect, the software prompts you for a username and password. |
Step 12 Click Continue to apply your changes and proceed. Click Back if you want to return to the Configuration | Quick | Public Interface screen.
The Manager displays the Configuration | Quick | PAT screen.
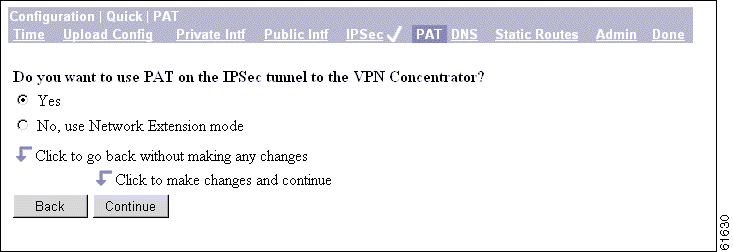
You use this screen to configure this VPN 3002 to use either PAT or Network Extension mode.
Step 1 Accept the default, Yes, if you want to use PAT. Otherwise, check No, use Network Extension mode. Note that you cannot disable PAT if you have not changed the IP address for the private interface.
Step 2 Click Continue to proceed with quick configuration, or click Back to return to the Configuration | Quick | IPSec screen.
See the sections below for more information about PAT and Network Extension mode.
Client mode, also called Port Address Translation (PAT) mode, isolates all devices on the VPN 3002 private network from those on the corporate network. In PAT mode:
All traffic from the private network appears on the network behind the central-site VPN Concentrator (the IKE peer) with a single source IP address. This IP address is the one the central-site VPN Concentrator assigns to the VPN 3002. The IP addresses of the computers on the VPN 3002 private network are hidden. You cannot ping or access a device on the VPN 3002 private network from outside of that private network, or directly from a device on the private network at the central site.
You assign the VPN 3002 to a client group on the central-site VPN Concentrator. If you enable split tunneling for that group, IPSec and PAT are applied to all traffic that travels through the VPN 3002 to networks within the network list for that group behind the central-site VPN Concentrator.
Traffic from the VPN 3002 to any destination other than those within the network list for that group on the central-site VPN Concentrator travels in the clear without applying IPSec. NAT translates the network addresses of the devices connected to the VPN 3002 private interface to the assigned IP address of the public interface and also keeps track of these mappings so that it can forward replies to the correct device.
The network and addresses on the private side of the VPN 3002 are hidden, and cannot be accessed directly.
For the VPN 3002 to use PAT, you must meet these requirements for the central-site VPN Concentrator.
1. The VPN Concentrator at the central site must be running Software version 3.x or later.
2. Address assignment must be enabled, by whatever method you choose to assign addresses (the options are DHCP, address pools, per user, or client-specified). If the central-site VPN Concentrator uses address pools for address assignment, make sure to configure the address pools your network requires. Refer to the chapter, "Address Management," in the VPN 3000 Series Concentrator Reference Volume 1: Configuration.
3. Configure a group to which you assign this VPN 3002. This includes assigning a group name and password. Refer to the chapter, "User Management," in the VPN 3000 Series Concentrator Reference Volume 1: Configuration.
4. Configure one or more users for the group, including usernames and passwords.
Network Extension mode allows the VPN 3002 to present a single, routable network to the remote private network over the VPN tunnel. IPSec encapsulates all traffic from the VPN 3002 private network to networks behind the central-siteVPN Concentrator. PAT does not apply. Therefore, devices behind the VPN Concentrator have direct access to devices on the VPN 3002 private network over the tunnel, and only over the tunnel, and vice versa. The VPN 3002 must initiate the tunnel, but after the tunnel is up, either side can initiate data exchange.
In this mode, the central-site VPN Concentrator does not assign an IP address for tunneled traffic (as it does in Client/PAT mode). The tunnel is terminated with the VPN 3002 private IP address (the assigned IP address). To use Network Extension mode, you must configure an IP address other than the default of 192.168.10.1 and disable PAT.
In Network Extension mode, the VPN 3002 automatically attempts to establish a tunnel to the VPN Concentrator. However, if you enable interactive unit authentication in either Client or Network Extension mode, the tunnel establishes when you perform the following steps.
Step 1 Click the Connection/Login Status button on the VPN 3002 Hardware Client login screen. The Connection/Login screen displays.
Step 2 Click Connect Now in the Connection/Login screen.
Step 3 Enter the username and password for the VPN 3002.
Alternatively, you can initiate a tunnel by clicking Connect Now on the in the Monitoring | System Status screen.
You always assign the VPN 3002 to a client group on the central-site VPN Concentrator. If you enable split tunneling for that group, IPSec operates on all traffic that travels through the VPN 3002 to networks within the network list for that group behind the central-site VPN Concentrator. PAT does not apply.
Traffic from the VPN 3002 to any other destination than those within the network list on the central-site VPN Concentrator travels in the clear without applying IPSec. NAT translates the network addresses of the devices on the VPN 3002 private network to the address of the VPN 3002 public interface. Thus the network and addresses on the private side of the VPN 3002 are accessible over the tunnel, but are protected from the Internet, that is, they cannot be accessed directly.
For the VPN 3002 to use Network Extension mode, you must meet these requirements for the central-site VPN Concentrator.
1. The VPN Concentrator at the central site must be running Software version 3.x or later.
2. Configure a group to which you assign this VPN 3002. This includes assigning a group name and password. Refer to the chapter, "User Management," in the VPN 3000 Series Concentrator Reference Volume 1: Configuration.
3. Configure one or more users for the group, including usernames and passwords.
4. Configure either a default gateway or a static route to the VPN 3002 private network. Refer to the chapter, "IP Routing," in the VPN 3000 Series Concentrator Reference Volume 1: Configuration.
5. If you want the VPN 3002 to be able to reach devices on other networks that connect to the VPN Concentrator, review your Network Lists. Refer to the chapter, "Policy Management," in the VPN 3000 Series Concentrator Reference Volume 1: Configuration.
The VPN 3002 always initiates the tunnel to the central-site VPN Concentrator. The central-site VPN Concentrator cannot initiate a tunnel to a VPN 3002. The VPN 3002 creates only one IPSec tunnel to the central-site VPN Concentrator, in either PAT or Network Extension mode. The tunnel can support multiple encrypted data streams between users behind the VPN 3002 and the central site. With split tunneling enabled, it can also support multiple unencrypted data streams to the internet.
In PAT mode, the tunnel establishes when data passes to the VPN Concentrator, or when you click Connect Now in the Monitoring | System Status screen.
In Network Extension mode, the VPN 3002 automatically attempts to establish a tunnel to the VPN Concentrator.
In either Client or Network Extension mode, when you enable interactive unit authentication, the tunnel establishes when you perform the following steps.
Step 1 In the VPN 3002 Hardware Client login screen, click the Connection/Login Status button. The Connection/Login screen displays.
Step 2 Click Connect Now.
Step 3 Enter the username and password for the VPN 3002.
Refer to the section, "Logging in With Interactive Unit and Individual User Authentication," in
Chapter 1 of the VPN 3002 Hardware Client Reference for detailed instructions.
Alternatively, you can click Connect Now on the in the Monitoring | System Status screen, after which the system prompts you to enter the username and password for the VPN 3002. Refer to the section, Monitoring | System Status in the "Monitoring" chapter of the VPN 3002 Hardware Client Reference for detailed instructions.
After the tunnel is established between the VPN 3002 and the central-site VPN Concentrator, the VPN Concentrator can initiate data exchange only in Network Extension mode with all traffic travelling through the tunnel. If you want the tunnel to remain up indefinitely, you should configure the VPN 3002 for Network Extension mode and not use split tunneling.
Table 3-1 summarizes instances in which the VPN 3002 and the central-site VPN Concentrator can initiate data exchange.
| Mode | Tunneling Policy | VPN 3002 Can Send Data First | Central-Site VPN Concentrator Can Send Data First (after VPN 3002 initiates the tunnel) |
|---|---|---|---|
PAT | Yes | No | |
PAT | Split tunneling enabled | Yes | No |
Network Extension | All traffic tunneled | Yes | Yes |
Network Extension | Split tunneling enabled | Yes | No |
The Manager displays the Configuration | Quick | DNS screen.
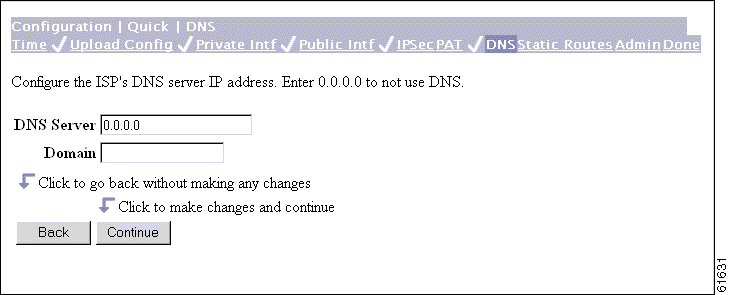
This screen lets you specify a Domain Name System (DNS) server for your local ISP, which lets you enter Internet hostnames (for example, mail01) rather than IP addresses for servers as you configure and manage the VPN 3002. While hostnames are easier to remember, using IP addresses avoids problems that might occur with the DNS server offline or congested. If you use a hostname to identify the central-site VPN Concentrator, you must configure a DNS server on the VPN 3002 (see Configuration | System | Servers | DNS).
Step 1 In the DNS Server field, enter the IP address of your local DNS server, using dotted decimal notation (for example, 10.10.0.11).
Step 2 In the Domain field, enter the local ISP domain name.
Step 3 Click Continue to proceed.
The Manager displays the Configuration | Quick | Static Routes screen. The Static Routes list shows manual IP routes that have been configured. The format is [destination network address/subnet mask -> outbound destination].
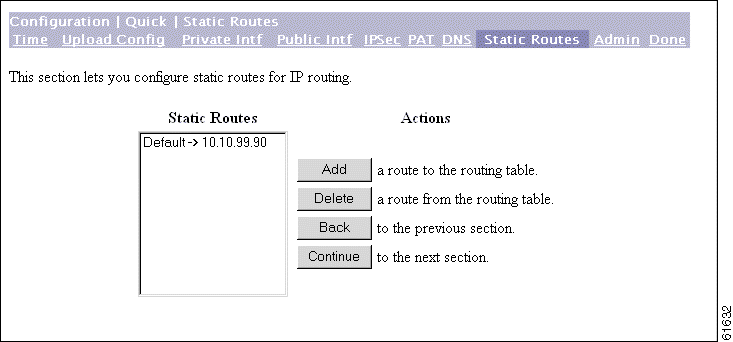
You use this screen to add or delete static routes for IP routing.
Step 1 Click Add to add a route to the routing table. The Manager displays the Configuration | Quick | Static Routes | Add screen.
Step 2 To delete a route, select it, and click Delete. The Manager deletes the route instantly, and there is no confirmation.
Step 3 Click Continue to proceed.
This screen lets you add a new static route to the IP routing table.
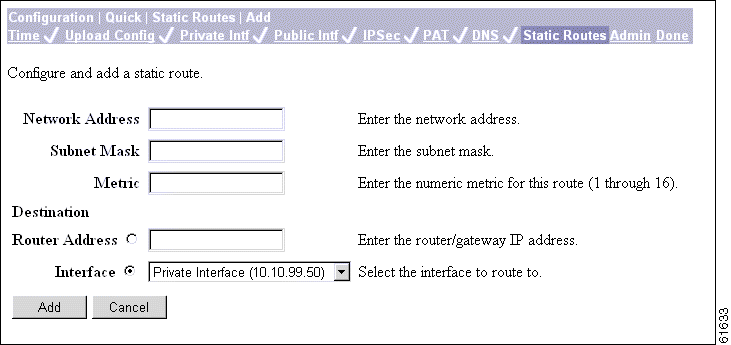
Step 1 In the Network Address field, enter the network IP address for this static route. Packets with this address will be sent to the Destination below. Use dotted decimal notation; for example, 192.168.12.0.
Step 2 In the Subnet Mask field, enter the subnet mask for the network IP address, using dotted decimal notation (such as 255.255.255.0). The subnet mask indicates which part of the IP address represents the network and which part represents hosts. The router subsystem looks at only the network part.
The Manager automatically supplies a standard subnet mask appropriate for the IP address you just entered. For example, the IP address 192.168.12.0 is a Class C address, and the standard subnet mask is 255.255.255.0. You can accept this entry or change it.
Step 3 In the Metric field, enter the cost for this route. Use a number from 1 to 16, where 1 is the lowest cost. The routing subsystem always tries to use the least costly route. For example, if a route uses a low speed line, you might assign a high metric so the system will use it only if all high-speed routes are unavailable.
Step 4 In the Destination Router Address or Interface fields, click a radio button to select the outbound destination for these packets. You can select only one destination: either a specific router or gateway, or a VPN 3002 interface.
For Router Address, enter the IP address of the specific router or gateway to which to route these packets; that is, the IP address of the next hop between the VPN 3002 and the packet's ultimate destination. Use dotted decimal notation; for example, 10.10.0.2.
For Interface, click the drop-down menu button and select a configured VPN 3002 interface as the outbound destination.
Step 5 To add a new static route to the list of configured routes, click Add. The new route displays at the bottom of the Static Routes list.
To discard your entry, click Cancel. The Manager returns to the Configuration | Quick | Static Routes screen, and the Static Routes list is unchanged.
The Manager displays the Configuration | Quick | Admin Password screen.
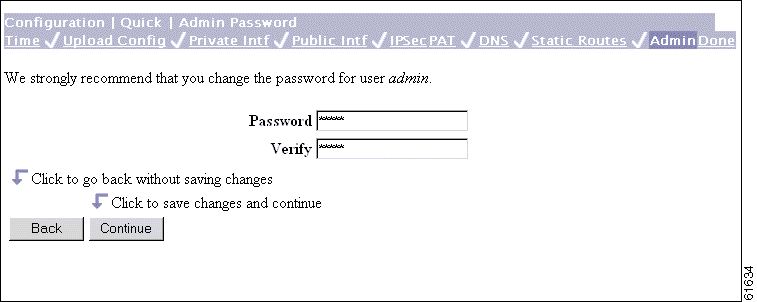
This screen lets you change the password for the admin administrator user. For ease of use during startup, the default admin password supplied with the VPN 3002 is also admin. Since the admin user has full access to all management and administration functions on the device, we strongly recommend you change this password to improve device security. You can further configure all administrator users on the regular Administration | Access Rights | Administrators Manager screen.
Step 1 In the Password field, enter a new password. For maximum security, the password should be at least 8 characters long, a mixture of upper- and lower-case alphabetic and numeric characters, and not easily guessed; for example, W8j9Haq3. (The field shows only asterisks.)
Step 2 In the Verify field, reenter the new password to verify it.
Step 3 Click Continue to proceed.
The Manager displays the Configuration | Quick | Done screen.

You have finished quick configuration, and your entries constitute the active or running configuration. This configuration has now been saved as the boot configuration. The VPN 3002 now has enough information, and it is operational. The VPN 3002 can now establish a secure VPN tunnel to the central-site VPN Concentrator.
Now that the VPN 3002 is operational, you can:
To use other VPN 3002 Hardware Client Manager functions, click the section you want in the left frame of the Manager window or on the Manager toolbar in the top frame of the Manager window.
For details on the frames, functions, and icons in the Manager window, see the next section, "Understanding the VPN 3002 Hardware Client Manager Window."
For details on the VPN 3002 hardware, all the functions available in the VPN 3002 Hardware Client Manager, or using the command-line interface, refer to the VPN 3002 Hardware Client Reference (online only).
The VPN 3002 Hardware Client Manager window on your browser consists of three frames—top, left, and main—and it provides helpful messages and tips as you move the mouse pointer over window items. The title bar and status bar also provide useful information.
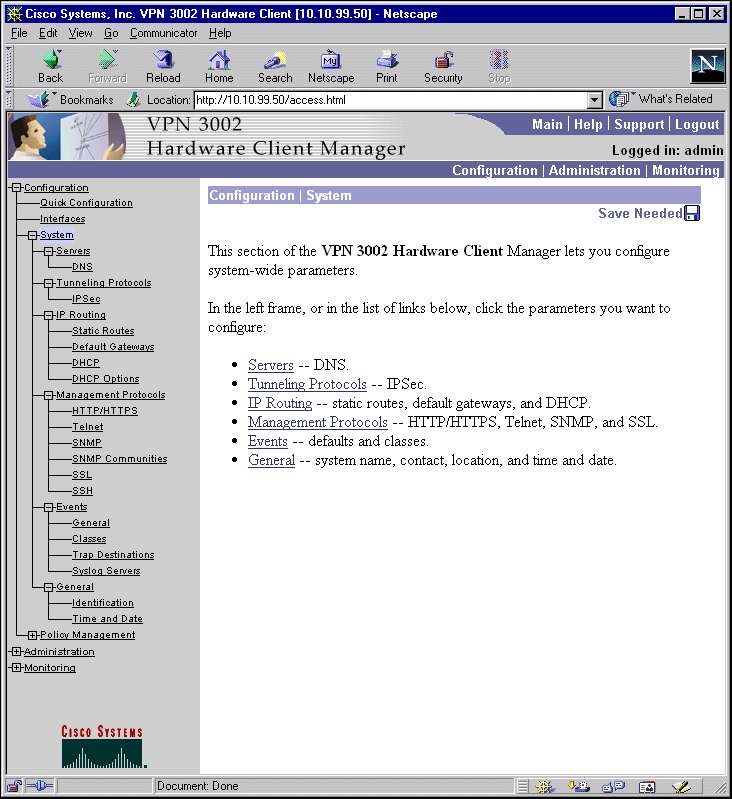
Title bar | The title bar at the top of the browser window includes the VPN 3002 device name or IP address in brackets, for example, [10.10.4.6]. |
Status bar | The status bar at the bottom of the browser window displays Manager activity and explanatory messages for some items. |
Mouse pointer and tips | As you move the mouse pointer over an active area, the pointer changes shape and icons change color. A description also appears in the status bar area. If you momentarily rest the pointer on an icon, a descriptive tip appears for that icon. |
Top frame | The Manager toolbar in the top frame provides quick access to Manager features. These include the following icons: |
| Click the Main tab to go to the main Manager screen, and to close all subordinate sections and titles in the left frame. |
Click the Help tab to open context-sensitive online help. Help opens in a separate browser window that yo can move or resize as you want. Close the help window when you are finished. | |
Click the Support tab to open a Manager screen with links to Cisco support and documentation resources. | |
Click the Logout tab to log out of the Manager and return to the login screen. | |
| The administrator username you used to log in to this Manager session. |
Click the Configuration tab to go to the main Configuration screen, to open the first level of subordinate Configuration pages in the left frame if they are not already open, and to close any open Administration or Monitoring pages in the left frame. | |
Click the Administration tab to go to the main Administration screen, to open the first level of subordinate Administration pages in the left frame if they are not already open, and to close any open Configuration or Monitoring pages in the left frame. | |
Click the Monitoring tab to go to the main Monitoring screen, to open the first level of subordinate Monitoring pages in the left frame if they are not already open, and to close any open Configuration or Administration pages in the left frame. | |
| Click the Save icon to save the active configuration and make it the boot configuration. In this state, the reminder indicates that the active configuration is the same as the boot configuration, but you can save it anyway. When you change the configuration, the reminder changes to Save Needed. |
| This reminder indicates that yo have changed the active configuration. Click the Save Needed icon to save the active configuration and make it the boot configuration. As you make configuration entries, they take effect immediately and are included in the active, or running, configuration. However, if you reboot the VPN 3002 without saving the active configuration, and configuration changes are lost. Clicking on this reminder saves the active configuration as the boot configuration and restores the Save reminder. |
| Click the Refresh icon to refresh (update) the screen contents on screens where it appears (mostly in the Monitoring section). The date and time above this reminder indicate when the screen was last updated. |
| Click the Reset icon to reset, or start anew, the screen contents on screens where it appears (mostly in the Monitoring section). |
| Click the Restore icon to restore the screen contents to their status prior to when you last clicked the Reset icon. |
Click the Cisco Systems logo to open a browser and go to the Cisco.com web site, www.cisco.com | |
Left frame | On Manager screens, the left frame provides a table of contents. The table of contents uses the familiar Windows Explorer metaphor of collapsed and expanded entries. |
| Click a title to open subordinate sections and titles, and to go to that Manager screen in the main frame. |
| Click the closed/collapsed icon to open subordinate sections and titles. Clicking on this icon does not change the screen in the main frame. |
| Click the open/expanded icon to close subordinate sections and titles. Clicking on this icon does not change the screen in the main frame. |
Main frame | The main frame displays the current VPN 3002 Hardware Client Manager screen. Many screens include a bullet list of links and descriptions of subordinate sections and titles. you can click a link to go to that Manager screen, and open subordinate sections and titles in the table of contents. |
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
Posted: Mon Nov 25 08:19:45 PST 2002
Copyright 1989-2000©Cisco Systems Inc.