|
|

Tunneling is the heart of virtual private networking. The tunnels make it possible to use a public TCP/IP network, such as the Internet, to create secure connections between remote users and a private corporate network.
The secure connection is called a tunnel, and the VPN 3002 uses the IPSec tunneling protocol to:
The VPN 3002 functions as a bidirectional tunnel endpoint: it can receive plain packets from the private network, encapsulate them, create a tunnel, and send them to the other end of the tunnel where they are unencapsulated and sent to their final destination; or it can receive encapsulated packets from the public network, unencapsulate them, and send them to their final destination on the private network.
This section explains how to configure the IPSec tunneling protocol.
This section lets you configure the IPSec tunneling protocol.
1. Click IPSec.
The VPN 3002 complies with the IPSec protocol and is specifically designed to work with the VPN Concentrator. IPSec provides the most complete architecture for VPN tunnels, and it is perceived as the most secure protocol.
In IPSec terminology, a "peer" is a remote-access client or another secure gateway. During tunnel establishment under IPSec, the two peers negotiate Security Associations that govern authentication, encryption, encapsulation, key management, etc. These negotiations involve two phases: first, to establish the tunnel (the IKE SA); and second, to govern traffic within the tunnel (the IPSec SA).
The VPN 3002 initiates all tunnels with the VPN Concentrator; the Concentrator functions only as responder. The VPN 3002 as initiator propose SAs; the responder accepts, rejects, or makes counter-proposals—all according to configured SA parameters. To establish a connection, both entities must agree on the SAs.
The Cisco VPN 3002 supports these IPSec attributes, but they are configurable on the central-site Concentrator, not on the VPN 3002:
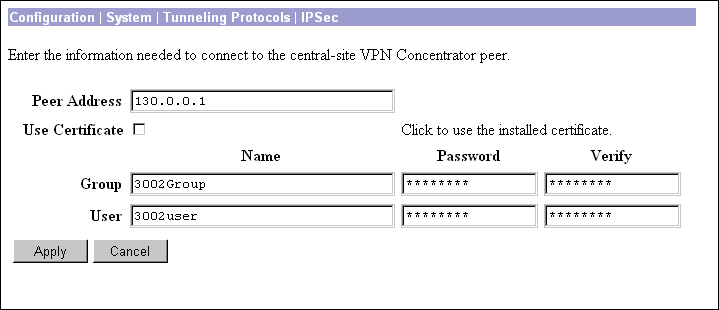
Enter the IP address or hostname of the remote IKE peer. This is the IP address or hostname of the public interface on the VPN Concentrator to which this VPN 3002 connects. Use dotted decimal notation; e.g., 192.168.34.56.
This parameter specifies whether to use preshared keys or a PKI (Public Key Infrastructure) digital identity certificate to authenticate the peer during Phase 1 IKE negotiations. See the discussion under Administration | Certificate Management, which is where you install digital certificates on the VPN 3002.
Check the box to use digital certificates.
The VPN 3002 connects to the VPN 3000 Series Concentrator using this Group name and password, which must be configured on the central-site Concentrator. Group and user names and passwords must be identical on the VPN 3002 and on the Concentrator to which it connects.
In the Group Name field, enter a unique name for the group to which this VPN 3002 belongs. This is the group name configured on the central-site Concentrator to which this VPN 3002 connects. Maximum is 32 characters, case-sensitive.
In the Group Password field, enter a unique password for this group. This is the group password configured on the Concentrator to which this VPN 3002 connects. Minimum is 4, maximum is 32 characters, case-sensitive. The field displays only asterisks.
In the Group Verify field, re-enter the group password to verify it. The field displays only asterisks.
You must also enter a username and password, and they must match the username and password configured on the central-site Concentrator to which this VPN 3002 connects.
In the User Name field, enter a unique name for the user in this group. Maximum is 32 characters, case-sensitive.This is the user name configured on the central-site Concentrator to which this VPN 3002 connects. Maximum is 32 characters, case-sensitive.
In the User Password field, enter the password for this user. This is the user password configured on the central-site Concentrator to which this VPN 3002 connects. Minimum is 4, maximum is 32 characters, case-sensitive.
In the User Verify field, re-enter the user password to verify it. The field displays only asterisks.
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
Posted: Tue Nov 19 15:16:15 PST 2002
Copyright 1989-2000©Cisco Systems Inc.