|
|

The VPN 3002 works in either of two modes: Client mode or Network Extension mode.
Policy management on the VPN 3002 includes deciding whether your want the VPN 3002 to use Client Mode or Network Extension mode.This section lets you enable or disable PAT.
Client mode, also called PAT (Port Address Translation) mode, isolates all devices on the VPN 3002 private network from those on the corporate network. In PAT mode:
Thus all traffic from the private network appears on the network behind the IKE peer with a single source IP address, which is the IP address of the VPN 3002 Private interface. This IP address is the one the central-site Concentrator assigns to the VPN 3002. The IP addresses of the computers on the VPN 3002 private network are hidden. You cannot ping or access a device on the VPN 3002 private network.
You assign the VPN 3002 to a Group on the central-site VPN 3002 Concentrator. If you enable split tunneling for that group, IPSec and PAT operate on all traffic that travels through the VPN 3002 to networks within the network list behind the central-site Concentrator, just as described above.
Traffic from the VPN 3002 to any destination other than those within the Concentrator's network list, travels in the clear without applying IPSec. NAT translates the network addresses of the devices connected to the VPN 3002 Private interface to the assigned IP address of the Public interface and also keeps track of these mappings so that it can forward replies to the correct device.
Thus the network and addresses on the private side of the VPN 3002 are hidden, and cannot be accessed directly.
For the VPN 3002 to use PAT, these are the requirements for the central-site Concentrator.
1. The Concentrator at the central site must be running Software version 3.x or later.
2. Address assignment must be enabled, by whatever method you choose to assign addresses (e.g., DHCP, address pools, per user, or client-specified). If the Concentrator uses address pools for address assignment, make sure to configure the address pools your network requires. See Chapter 6, Address Management, in the VPN 3000 Concentrator Series User Guide.
3. Configure a Group to which you assign this VPN 3002. This includes assigning a Group Name and Password. See Chapter 14, User Management, in the VPN 3000 Concentrator Series User Guide.
4. Configure one or more Users for the group, including User Names and Passwords.
Network Extension mode allows the VPN 3002 to present a full, routable network to the tunneled network. IPSec encapsulates all traffic from the VPN 3002 private network to networks behind the central-site Concentrator. PAT does not apply. Therefore, devices behind the Concentrator have direct access to devices on the VPN 3002 private network via the tunnel, and only over the tunnel, and vice versa. Either side can initiate data exchange.
In this mode, the Concentrator does not assign an IP address for tunneled traffic (as it does in Client/PAT mode). The tunnel is terminated with the VPN 3002 private IP address (i.e., the assigned IP address). To use Network Extension Mode, you must configure an IP address other than the default of 192.168.10.1 and disable PAT.
You assign the VPN 3002 to a Group on the central-site Concentrator. If you enable split tunneling for that group, IPSec operates on all traffic that travels through the VPN 3002 to networks within the network list behind the central-site Concentrator, just as described above. PAT does not apply.
Traffic from the VPN 3002 to any other destination than those within the Concentrator's network list travels in the clear without applying IPSec. NAT translates the network addresses of the devices on the VPN 3002 private network to the address of the VPN 3002 Public interface. Thus the network and addresses on the private side of the VPN 3002 are accessible via the tunnel, but are protected from the Internet, i.e., they cannot be accessed directly.
For the VPN 3002 to use Network Extension mode, these are the requirements for the central-site Concentrator.
1. The Concentrator at the central site must be running Software version 3.x or later.
2. Configure a Group to which you assign this VPN 3002. This includes assigning a Group Name and Password. See Chapter 14, User Management, in the VPN 3000 Concentrator Series User Guide.
3. Configure one or more Users for the group, including User Names and Passwords.
4. Configure either a default gateway or a static route to the VPN 3002 private network. See Chapter 8, IP Routing in the VPN 3000 Concentrator Series User Guide.
5. If you want the VPN 3002 to be able to reach devices on other networks that connect to this Concentrator, review your Network Lists. See Chapter 15, Policy Management in the VPN 3000 Concentrator Series User Guide.
The Configuration | Policy Management screen introduces this section of the Manager.
To enable or disable PAT, click Traffic Management.
The Manager displays the Configuration | Policy Management | Traffic Management screen.
To configure PAT (Port Address Translation) click PAT.
The Configuration | Policy Management | Traffic Management | PAT screen displays.
PAT mode provides many-to-one translation; that is, it translates many private network addresses to the single address configured on the public network interface.
To enable PAT, click Enable.
This screen lets you enable or disable PAT, which applies PAT to all configured traffic flowing from the private interface to the public interface.
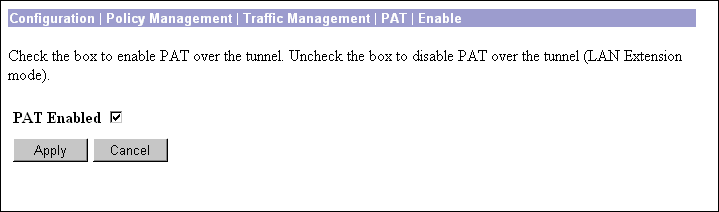
Check the box to enable Client Mode (PAT), or clear it to enable Network Extension Mode.
 |
Note Remember that to use Network Extension Mode, you must configure an IP address other than the default for the Private interface. If you don't change the IP address of the Private interface, you can't disable PAT. |
To enable or disable PAT, and include your setting in the active configuration, click Apply. The Manager returns to the Configuration | Policy Management | Traffic Management | PAT screen.
To save the active configuration and make it the boot configuration, click the Save Needed icon at the top of the Manager window.
To discard your entry and leave the active configuration unchanged, click Cancel. The Manager returns to the Configuration | Policy Management | Traffic Management | PAT screen.
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
Posted: Tue Nov 19 15:19:28 PST 2002
Copyright 1989-2000©Cisco Systems Inc.