|
|

August 11, 1997
These release notes identify the Cisco IOS Release 11.2 feature packs for Cisco 3600 series routers.
Product numbers for the supported feature packs are as follows:
* These feature packs contain encryption images.
These release notes contain the following sections:
RSL 5.01 supports the following Cisco 3600 series routers:
The heart of a Cisco IOS software feature pack is a CD-ROM that contains software images and RSL, a Windows 95 application, which loads the images onto the router. Each Cisco IOS Release 11.2 feature pack CD contains feature sets. For users without Windows 95, images can also be loaded with a Trivial File Transfer Protocol (TFTP) server application.
Each Cisco IOS Release 11.2 software feature pack box contains the following:
This section describes the Cisco feature packs, listing the software feature sets comprising each pack. You can use this information to identify your feature pack set in conjunction with the corresponding information provided in the table in the section "Cisco IOS Release 11.2 Feature Sets,". The table in that section identifies which features are supported for a feature set on a specific platform.
This section includes two tables: Table 1 identifies each feature pack as specified on the label of the CD containing the router software. It also lists the feature sets comprising the feature pack, giving the UNIX and DOS filenames of the images. The table provides a brief description of each feature set and the router platform on which the feature set runs. Table 1 also identifies the memory required to run each feature set on your specific platform; Table 2 describes the memory delivered by default and the memory upgrades available.
You can use Table 1 to identify the memory required for your configuration based on the image you run. You can then check this against Table 2 to determine how much memory is available on the router as the factory default and the upgrades that you can obtain to satisfy your requirements.
| Router Software Loader Description | Image Name (UNIX) | Image Name (DOS) | Flash Memory Required | Main Memory Required |
|---|---|---|---|---|
| Cisco 3600 IP Feature Pack Release 11.2 and 11.1 (model number CD36-C-11.2=) |
| |||
Cisco 3620 IP feature set 11.2(7)P | c3620-i-mz.112-7a.P | 80155207 | 4 MB | 16 MB |
Cisco 3640 IP feature set 11.2(7)P | c3640-i-mz.112-7a.P | 80156007 | 4 MB | 16 MB |
Cisco 3620 IP feature set 11.2(4)XA | c3620-i-mz.112-4.XA | 80155204 | 4 MB | 16 MB |
Cisco 3640 IP feature set 11.2(4)XA | c3640-i-mz.112-4.XA | 80156004 | 4 MB | 16 MB |
Cisco 3620 IP feature set 11.1(8)AA | c3620-i-mz.111-8.AA | 80131008 | 4 MB | 16 MB |
Cisco 3640 IP feature set 11.1(8)AA | c3640-i-mz.111-8.AA | 80131908 | 4 MB | 16 MB |
| Cisco 3600 IP Plus Feature Pack Release 11.2 and 11.1 (model number CD36-CP-11.2=) |
| |||
Cisco 3620 IP Plus feature set 11.2(7)P | c3620-is-mz.112-7a.P | 80155307 | 4 MB | 16 MB |
Cisco 3640 IP Plus feature set 11.2(7)P | c3640-is-mz.112-7a.P | 80156107 | 4 MB | 16 MB |
Cisco 3620 IP Plus feature set 11.2(4)XA | c3620-is-mz.112-4.XA | 80155304 | 4 MB | 16 MB |
Cisco 3640 IP Plus feature set 11.2(4)XA | c3640-is-mz.112-4.XA | 80156104 | 4 MB | 16 MB |
Cisco 3620 IP feature set 11.1(8)AA | c3620-i-mz.111-8.AA | 80131008 | 4 MB | 16 MB |
Cisco 3640 IP feature set 11.1(8)AA | c3640-i-mz.111-8.AA | 80131908 | 4 MB | 16 MB |
| Cisco 3600 IP Plus 40 Feature Pack Release 11.2 and 11.1 (model number CD36-CW-11.2=) |
| |||
Cisco 3620 IP Plus 40 feature set 11.2(7)P1 | c3620-is40-mz.112-7a.P | 80200507 | 4 MB | 16 MB |
Cisco 3640 IP Plus 40 feature set 11.2(7)P1 | c3640-is40-mz.112-7a.P | 80200607 | 4 MB | 16 MB |
Cisco 3620 IP Plus feature set 11.2(4)XA | c3620-is-mz.112-4.XA | 80155304 | 4 MB | 16 MB |
Cisco 3640 IP Plus feature set 11.2(4)XA | c3640-is-mz.112-4.XA | 80156104 | 4 MB | 16 MB |
Cisco 3620 IP feature set 11.1(8)AA | c3620-i-mz.111-8.AA | 80131008 | 4 MB | 16 MB |
Cisco 3640 IP feature set 11.1(8)AA | c3640-i-mz.111-8.AA | 80131908 | 4 MB | 16 MB |
| Cisco 3600 IP Plus 56 Feature Pack Release 11.2 and 11.1 (model number CD36-CY-11.2=) |
| |||
Cisco 3620 IP Plus 56 feature set 11.2(7)P2 | c3620-is56-mz.112-7a.P | 80200707 | 4 MB | 16 MB |
Cisco 3640 IP Plus 56 feature set 11.2(7)P2 | c3640-is56-mz.112-7a.P | 80200807 | 4 MB | 16 MB |
Cisco 3620 IP Plus feature set 11.2(4)XA | c3620-is-mz.112-4.XA | 80155304 | 4 MB | 16 MB |
Cisco 3640 IP Plus feature set 11.2(4)XA | c3640-is-mz.112-4.XA | 80156104 | 4 MB | 16 MB |
Cisco 3620 IP feature set 11.1(8)AA | c3620-i-mz.111-8.AA | 80131008 | 4 MB | 16 MB |
Cisco 3640 IP feature set 11.1(8)AA | c3640-i-mz.111-8.AA | 80131908 | 4 MB | 16 MB |
| Cisco 3600 IP/IPX/AT/DEC Feature Pack Release 11.2 and 11.1 (model number: CD36-B-11.2=) |
| |||
Cisco 3620 IP/IPX/AppleTalk/DECnet feature set 11.2(7)P | c3620-d-mz.112-7a.P | 80155007 | 4 MB | 16 MB |
Cisco 3640 IP/IPX/AppleTalk/DECnet feature set 11.2(7)P | c3640-d-mz.112-7a.P | 80155807 | 4 MB | 16 MB |
Cisco 3620 IP/IPX/AppleTalk/DECnet feature set 11.2(4)XA | c3620-d-mz.112-4.XA | 80155004 | 4 MB | 16 MB |
Cisco 3640 IP/IPX/AppleTalk/DECnet feature set 11.2(4)XA | c3640-d-mz.112-4.XA | 80155804 | 4 MB | 16 MB |
Cisco 3620 Desktop feature set 11.1(8)AA | c3620-d-mz.111-8.AA | 80130808 | 4 MB | 16 MB |
Cisco 3640 Desktop feature set 11.1(8)AA | c3640-d-mz.111-8.AA | 80131708 | 4 MB | 16 MB |
| Cisco 3600 IP/IPX/AT/DEC Plus Feature Pack Release 11.2 and 11.1 (model number CD36-BP-11.2=) | ||||
Cisco 3620 IP/IPX/AppleTalk/DECnet Plus feature set 11.2(7)P | c3620-ds-mz.112-7a.P | 80155107 | 4 MB | 24 MB |
Cisco 3640 IP/IPX/AppleTalk/DECnet Plus feature set 11.2(7)P | c3640-ds-mz.112-7a.P | 80155907 | 4 MB | 24 MB |
Cisco 3620 IP/IPX/AppleTalk/DECnet Plus feature set 11.2(4)XA | c3620-ds-mz.112-4.XA | 80155104 | 4 MB | 24 MB |
Cisco 3640 IP/IPX/AppleTalk/DECnet Plus feature set 11.2(4)XA | c3640-ds-mz.112-4.XA | 80155904 | 4 MB | 24 MB |
Cisco 3620 Desktop feature set 11.1(8)AA | c3620-d-mz.111-8.AA | 80130808 | 4 MB | 16 MB |
Cisco 3640 Desktop feature set 11.1(8)AA | c3640-d-mz.111-8.AA | 80131708 | 4 MB | 16 MB |
| Cisco 3600 IP/IPX/AT/DEC Plus 40 Feature Pack Release 11.2 and 11.1 (model number CD36-BW-11.2=) | ||||
Cisco 3620 IP/IPX/AppleTalk/DECnet Plus 40 feature set 11.2(7)P1 | c3620-ds40-mz.112-7a.P | 80200907 | 4 MB | 24 MB |
Cisco 3640 IP/IPX/AppleTalk/DECnet Plus 40 feature set 11.2(7)P1 | c3640-ds40-mz.112-7a.P | 80201007 | 4 MB | 24 MB |
Cisco 3620 IP/IPX/AppleTalk/DECnet Plus feature set 11.2(4)XA | c3620-ds-mz.112-4.XA | 80155104 | 4 MB | 24 MB |
Cisco 3640 IP/IPX/AppleTalk/DECnet Plus feature set 11.2(4)XA | c3640-ds-mz.112-4.XA | 80155904 | 4 MB | 24 MB |
Cisco 3620 Desktop feature set 11.1(8)AA | c3620-d-mz.111-8.AA | 80130808 | 4 MB | 16 MB |
Cisco 3640 Desktop feature set 11.1(8)AA | c3640-d-mz.111-8.AA | 80131708 | 4 MB | 16 MB |
| Cisco 3600 IP/IPX/AT/DEC Plus 56 Feature Pack Release 11.2 and 11.1 (model number CD36-BY-11.2=) | ||||
Cisco 3620 IP/IPX/AppleTalk/DECnet Plus 56 feature set 11.2(7)P2 | c3620-ds56-mz.112-7a.P | 80201107 | 4 MB | 24 MB |
Cisco 3640 IP/IPX/AppleTalk/DECnet Plus 56 feature set 11.2(7)P2 | c3640-ds56-mz.112-7a.P | 80201207 | 4 MB | 24 MB |
Cisco 3620 IP/IPX/AppleTalk/DECnet Plus feature set 11.2(4)XA | c3620-ds-mz.112-4.XA | 80155104 | 4 MB | 24 MB |
Cisco 3640 IP/IPX/AppleTalk/DECnet Plus feature set 11.2(4)XA | c3640-ds-mz.112-4.XA | 80155904 | 4 MB | 24 MB |
Cisco 3620 Desktop feature set 11.1(8)AA | c3620-d-mz.111-8.AA | 80130808 | 4 MB | 16 MB |
Cisco 3640 Desktop feature set 11.1(8)AA | c3640-d-mz.111-8.AA | 80131708 | 4 MB | 16 MB |
| Cisco 3600 Enterprise Feature Pack Release 11.2 and 11.1 (model number CD36-A-11.2=) |
| |||
Cisco 3620 Enterprise feature set 11.2(7)P | c3620-j-mz.112-7a.P | 80155407 | 8 MB | 24 MB |
Cisco 3640 Enterprise feature set 11.2(7)P | c3640-j-mz.112-7a.P | 80156207 | 8 MB | 24 MB |
Cisco 3620 Enterprise feature set 11.2(4)XA | c3620-j-mz.112-4.XA | 80155404 | 8 MB | 24 MB |
Cisco 3640 Enterprise feature set 11.2(4)XA | c3640-j-mz.112-4.XA | 80156204 | 8 MB | 24 MB |
Cisco 3620 Enterprise feature set 11.1(8)AA | c3620-j-mz.111-8.AA | 80131408 | 4 MB | 24 MB |
Cisco 3640 Enterprise feature set 11.1(8)AA | c3640-j-mz.111-8.AA | 80132308 | 4 MB | 24 MB |
| Cisco 3600 Enterprise Plus Feature Pack Release 11.2 and 11.1 (model number CD36-AP-11.2=) |
| |||
Cisco 3620 Enterprise Plus feature set 11.2(7)P | c3620-js-mz.112-7a.P | 80155507 | 8 MB | 24 MB |
Cisco 3640 Enterprise Plus feature set 11.2(7)P | c3640-js-mz.112-7a.P | 80156307 | 8 MB | 24 MB |
Cisco 3620 Enterprise Plus feature set 11.2(4)XA | c3620-js-mz.112-4.XA | 80155504 | 8 MB | 24 MB |
Cisco 3640 Enterprise Plus feature set 11.2(4)XA | c3640-js-mz.112-4.XA | 80156304 | 8 MB | 24 MB |
Cisco 3620 Enterprise feature set 11.1(8)AA | c3620-j-mz.111-8.AA | 80131408 | 4 MB | 24 MB |
Cisco 3640 Enterprise feature set 11.1(8)AA | c3640-j-mz.111-8.AA | 80132308 | 4 MB | 24 MB |
| Cisco 3600 Enterprise Plus 40 Feature Pack Release 11.2 and 11.1 (model number CD36-AW-11.2=) |
| |||
Cisco 3620 Enterprise Plus 40 feature set 11.2(7)P1 | c3620-js40-mz.112-7a.P | 80201307 | 8 MB | 24 MB |
Cisco 3640 Enterprise Plus 40 feature set 11.2(7)P1 | c3640-js40-mz.112-7a.P | 80201407 | 8 MB | 24 MB |
Cisco 3620 Enterprise Plus feature set 11.2(4)XA | c3620-js-mz.112-4.XA | 80155504 | 8 MB | 24 MB |
Cisco 3640 Enterprise Plus feature set 11.2(4)XA | c3640-js-mz.112-4.XA | 80156304 | 8 MB | 24 MB |
Cisco 3620 Enterprise feature set 11.1(8)AA | c3620-j-mz.111-8.AA | 80131408 | 4 MB | 24 MB |
Cisco 3640 Enterprise feature set 11.1(8)AA | c3640-j-mz.111-8.AA | 80132308 | 4 MB | 24 MB |
| Cisco 3600 Enterprise Plus 56 Feature Pack Release 11.2 and 11.1 (model number CD36-AY-11.2=) |
| |||
Cisco 3620 Enterprise Plus 56 feature set 11.2(7)P2 | c3620-js56-mz.112-7a.P | 80201507 | 8 MB | 24 MB |
Cisco 3640 Enterprise Plus 56 feature set 11.2(7)P2 | c3640-js56-mz.112-7a.P | 80201607 | 8 MB | 24 MB |
Cisco 3620 Enterprise Plus feature set 11.2(4)XA | c3620-js-mz.112-4.XA | 80155504 | 8 MB | 24 MB |
Cisco 3640 Enterprise Plus feature set 11.2(4)XA | c3640-js-mz.112-4.XA | 80156304 | 8 MB | 24 MB |
Cisco 3620 Enterprise feature set 11.1(8)AA | c3620-j-mz.111-8.AA | 80131408 | 4 MB | 24 MB |
Cisco 3640 Enterprise feature set 11.1(8)AA | c3640-j-mz.111-8.AA | 80132308 | 4 MB | 24 MB |
| 1Contains 40-bit encryption feature. 2Contains 56-bit encryption feature. |
| Memory Type | Default | Upgrade Options |
|---|---|---|
Flash memory card | 4 MB | 8-MB upgrade: MEM3600-8FS= |
DRAM1 | 16 MB | Expandable to 64 MB: |
DRAM2 | 16 MB | Expandable to 128 MB: |
| 1On the Cisco 3620 only. 2On the Cisco 3640 only. |
System configurations with multiple ISDN PRI interfaces or 12 or more ISDN BRI interfaces require more I/O memory than the default.
Cisco 3600 series routers ship with a 75/25 I/O memory split. If your router has 2 ISDN PRI interfaces or more than 12 ISDN BRI interfaces, you must change the memory split to 60/40. The following sections provide information about reallocating processor and I/O memory and provide examples of the memory-size iomem command. Note that if you do not reallocate memory, you will get an error code.
DRAM memory in Cisco 3600 series routers is organized as one contiguous address space divided between processor memory and I/O memory. Depending on the type and number of network interfaces you have configured in the router, you may need to reallocate the DRAM memory partitioned to processor memory and I/O memory.
Cisco manufacturing configures most Cisco 3600 series routers to have 25 percent of the address space allocated to I/O memory and 75 percent allocated to processor memory. But for customers that use two or more ISDN PRI interfaces, DRAM memory must be configured to provide 40 percent of the address space for I/O memory and 60 percent for processor memory. See Figure 1.
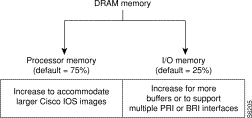
There are cases where you may have to manually reallocate the DRAM memory split between processor memory and I/O memory after you have received a router from Cisco Systems.
For example, suppose your Cisco 3640 router has the following running configuration:
Later on however, you add a 4-port ISDN BRI network module to the router. You now have a total 12 ISDN BRI interfaces running on the router. At this point, you must use the memory-size iomem command to configure 40 percent of the address space for I/O memory and 60 percent for processor memory.
To view your current mix of processor and I/O memory and reassign memory distribution accordingly, enter the following commands beginning in privileged EXEC mode:
| Task | Command |
|---|---|
Step 1. View the total amount of memory loaded on the router. | show version |
Step 2. Determine the amount of free memory. | show memory1 |
Step 3. Enter global configuration mode. | configure terminal |
Step 4. Allocate processor memory and I/O memory. | memory-size iomem I/O-memory-percentage2 |
Step 5. Exit global configuration mode. | Ctrl-Z |
Step 6. Write the new configuration to NVRAM. | copy running-config startup-config or |
Step 7. Reload the router to run the new configuration. | reload |
Valid I/O memory percentage values are 25, 30, 40 (the default), and 50. I/O memory size is the specified percentage of total memory size, rounded down to the nearest multiple of 1 MB. The remaining memory is processor memory.
The memory-size iomem command does not take effect until you save it to NVRAM using the copy running-config startup-config EXEC command and reload the router. However, when you enter the command, the software checks whether the new memory distribution leaves enough processor memory for the currently running Cisco IOS image. If not, the following message appears:
Warning: Attempting a memory partition that does not provide enough Processor memory for
the current image.If you write memory now, this version of software may not be able to run.
When you enter the reload command to run a new image, the software calculates the new processor and I/O memory split. If there is not enough processor memory, it automatically reduces I/O memory to an alternative setting to load the image. If there is still not enough processor memory for the image to run, then you do not have enough DRAM.
See the next section for an example of how to configure the memory-size iomem command.
The percentage of DRAM allocated to I/O memory and processor memory is configurable.
The following example allocates 40 percent of DRAM to I/O memory and the remaining 60 percent to processor memory:
Step 1 From EXEC mode, enter the show memory command to see whether you need to allocate different percentages of processor and I/O memory. The Free(b) column shows how much I/O memory is available:
Router# show memory
Head Total(b) Used(b) Free(b) Lowest(b) Largest(b)
Processor 60913730 3066064 970420 2095644 2090736 2090892
I/O C00000 4194304 1382712 2811592 2811592 2805492
--More--
Step 2 Enter global configuration mode and configure the memory-size iomem command.
Router# configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
Router(config)# memory-size iomem 40
Router(config)# Ctrl-Z
Router#
Step 3 Write the new configuration to NVRAM:
Router# copy running-config startup-config
Building configuration...
[OK]
Step 4 Enter the reload command to run the new image and boot the router from ROM monitor mode:
Router# reload
program load complete, entry point: 0x80008000, size: 0x32ea24
Self decompressing the image :
################################################################################
################################################################################
################################################################################
###### [OK]
To reallocate the percentage of DRAM memory to use for I/O memory and processor memory on Cisco 3600 series routers, use the memory-size iomem global configuration command. The no form of this command reverts to the default allocation of 25 percent I/O memory and 75 percent processor memory.
memory-size iomem I/O-memory-percentage
I/O-memory-percentage | The percentage of DRAM allocated to I/O memory. The values permitted are 25, 30, 40, and 50 percent. |
The default allocation is 25 percent I/O memory and 75 percent processor memory.
Global configuration
This command first appeared in Cisco IOS Release 11.2 P.
Once you specify the percentage of I/O memory in the command line, processor memory automatically takes on the remaining percentage of DRAM memory.
The following configuration allocates 40 percent of the DRAM memory to I/O memory and the remaining 60 percent to processor memory.
Router# configure terminal
Router(config)# memory-size iomem 40
Router(config)# Ctrl-Z
Router# copy running-config startup-config
Building configuration...
[OK]
Router# reload
program load complete, entry point: 0x80008000, size: 0x32ea24
Self decompressing the image :
#######################################################################################
#######################################################################################
######################################################################## [OK]
This section describes several solutions to problems you might encounter when using RSL. These solutions are additions to RSL's online help.
This installation tip provides a possible recovery solution in the event that you are unable to connect to your router. You can skip this section unless you are experiencing a connection error.
In some cases, you might receive the following error message while connecting to the target router:
"Failed to configure the router to enable the Cisco IOS software image and configuration
file upload and download operations. You may want to check the router to make sure that
the selected interface exists."
If you encounter this message, try increasing the Short Timeout value in the Options dialog box, especially if one of the following situations applies:
In some cases, RSL is unable to restore the startup configuration. If this happens, take the following steps:
Step 1 Ensure that all cables are properly attached to both the router and the PC.
Step 2 Restart RSL and connect using the Preconfigured router option.
Step 3 When asked if you want to overwrite the existing startup configuration file, choose NO.
Step 4 When asked if you want to continue, choose YES.
Step 5 When connected, select Download Router Configuration in the Router Software Loader dialog box.
Step 6 Select the appropriate file, and click the radio button beside Copy configuration to the router's nonvolatile memory.
The router should now contain the startup configuration it had before the initial RSL connection. You can now exit RSL.
The following information about RSL operations can help you with the installation process:
This section identifies specific features, within a category of features, supported on Cisco 3600 series routers. You can use the information given in the table provided in this section in conjunction with the information provided in the section "Cisco Feature Pack Descriptions,", to determine which features a particular feature set supports on a given platform.
Table 3 shows specific features supported for Cisco IOS Release 11.2 feature sets.
The table uses these conventions to identify features:
Cisco IOS images with 40-bit Data Encryption Standard (DES) support may legally be distributed to any party eligible to receive Cisco IOS software. 40-bit DES is not a cryptographically strong solution and should not be used to protect sensitive data.
Cisco IOS images with 56-bit DES are subject to International Traffic in Arms Regulations (ITAR) controls and have a limited distribution. Images to be installed outside the U.S. require an export license. Customer orders may be denied or subject to delay because of U.S. government regulations. Contact your sales representative or distributor for more information, or send e-mail to export@cisco.com.
| Feature Sets | |||
|---|---|---|---|
| Features | IP Routing | Desktop (IP/IPX/AppleTalk/DEC) | Enterprise |
| LAN Support | |||
Apollo Domain | - | - | Yes |
AppleTalk 1 and 2 | - | Yes | Yes |
Banyan VINES | - | - | Yes |
Concurrent routing and bridging | Yes | Yes | Yes |
DECnet IV | - | Yes | Yes |
DECnet V | - | - | Yes |
GRE | Yes | Yes | Yes |
Integrated routing and bridging (RB) | Yes | Yes | Yes |
IP | Yes | Yes | Yes |
LAN extension host | Yes | Yes | Yes |
Multiring | Yes | Yes | Yes |
Novell IPX | - | Yes | Yes |
OSI | - | - | Yes |
Source-route bridging | - | - | - |
Transparent and translational bridging | Yes | Yes | Yes |
XNS | - | - | Yes |
| WAN Services | |||
Combinet packet protocol | Yes | Yes | Yes |
Dialer profiles | Yes | Yes | Yes |
Frame Relay | Yes | Yes | Yes |
Frame Relay SVC support (DTE) | - | - | Yes |
Frame Relay traffic shaping1 | - | - | - |
Half bridge/half router for CPP and PPP | Yes | Yes | Yes |
Multichassis Multilink PPP (MMP) | Plus | Plus | Plus |
Virtual Private Dial-up Network (VPDN) | - | Yes | Yes |
HDLC | Yes | Yes | Yes |
IPXWAN 2.0 | - | Yes | Yes |
ISDN2 | Yes | Yes | Yes |
PPP3 | Yes | Yes | Yes |
SMDS | Yes | Yes | Yes |
Switched 56 | Yes | Yes | Yes |
X.254 | Yes | Yes | Yes |
| WAN Optimization | |||
Bandwidth-on-demand | Yes | Yes | Yes |
Custom and priority queuing | Yes | Yes | Yes |
Dial backup | Yes | Yes | Yes |
Dial-on-demand | Yes | Yes | Yes |
Yes | Yes | Yes | |
Snapshot routing | Yes | Yes | Yes |
Weighted fair queuing | Yes | Yes | Yes |
| IP Routing | |||
BGP | Yes | Yes | Yes |
BGP4 | Yes | Yes | Yes |
EGP | Yes | Yes | Yes |
Enhanced IGRP | Yes | Yes | Yes |
Enhanced IGRP optimizations | Yes | Yes | Yes |
ES-IS | - | - | Yes |
IGRP | Yes | Yes | Yes |
IS-IS | - | - | Yes |
Named IP access control list | Yes | Yes | Yes |
Network Address Translation (NAT) | Plus | Plus | Plus |
NHRP | Yes | Yes | Yes |
OSPF | Yes | Yes | Yes |
OSPF Not-So-Stubby-Areas (NSSA) | Yes | Yes | Yes |
OSPF On Demand Circuit (RFC 1793) | Yes | Yes | Yes |
PIM | Yes | Yes | Yes |
Policy-based routing | Yes | Yes | Yes |
RIP | Yes | Yes | Yes |
RIP Version 2 | Yes | Yes | Yes |
| Other Routing | |||
AURP | - | Yes | Yes |
IPX RIP | - | Yes | Yes |
NLSP | - | Yes | Yes |
RTMP | - | Yes | Yes |
SMRP | - | Yes | Yes |
SRTP | - | - | Yes |
| Multimedia and Quality of Service |
|
|
|
Generic traffic shaping | Yes | Yes | Yes |
Random Early Detection (RED) | Yes | Yes | Yes |
Resource Reservation Protocol (RSVP) | Yes | Yes | Yes |
| Management | |||
AutoInstall | Yes | Yes | Yes |
Automatic modem configuration7 | Yes | Yes | Yes |
HTTP server | Yes | Yes | Yes |
RMON events and alarms8 | Yes | Yes | Yes |
SNMP | Yes | Yes | Yes |
Telnet | Yes | Yes | Yes |
| Security | |||
Access lists | Yes | Yes | Yes |
Access security | Yes | Yes | Yes |
Extended access lists | Yes | Yes | Yes |
Kerberized login | - | - | Yes |
Kerberos V client support | - | - | Yes |
Lock and key | - | - | Yes |
MAC security for hubs | Yes | Yes | Yes |
MD5 routing authentication | Yes | Yes | Yes |
Network layer encryption (40-bit or export controlled 56-bit DES) | Encrypt | Encrypt | Encrypt |
RADIUS | Yes | Yes | Yes |
Router authentication | Encrypt | Encrypt | Encrypt |
TACACS+ | Yes | Yes | Yes |
| IBM Support | |||
BAN for SNA Frame Relay support | Plus | Yes | Yes |
Bisync9 | Plus | Yes | Yes |
Caching and filtering | Plus | Yes | Yes |
DLSw+ | Plus | Yes | Yes |
Downstream PU concentration (DSPU) | Plus | - | Yes |
Frame Relay SNA Support (RFC 1490) | Plus | Yes | Yes |
NetView Native Service Point | Plus | Yes | Yes |
QLLC9 | Plus | Yes | Yes |
SDLC integration | Plus | Yes | Yes |
SDLC transport (STUN) | Plus | Yes | Yes |
SDLC-to-LAN conversion (SDLLC) | Plus | Yes | Yes |
SNA and NetBIOS WAN optimization | Plus | Yes | Yes |
SRB/RSRB | Plus | Yes | Yes |
SRT | Plus | Yes | Yes |
TG/COS | - | - | Yes |
| Protocol Translation | |||
LAT | - | - | Yes |
Rlogin | - | - | Yes |
| Remote Node | |||
ARAP 1.0/2.0 | - | Yes | Yes |
Asynchronous master interfaces | Yes | Yes | Yes |
ATCP | - | Yes | Yes |
CPPP | Yes | Yes | Yes |
CSLIP | Yes | Yes | Yes |
DHCP | Yes | Yes | Yes |
IP pooling | Yes | Yes | Yes |
IPX and ARAP on virtual asynch interfaces | - | - | Yes |
IPXCP | - | Yes | Yes |
MacIP | - | Yes | Yes |
NASI10 | - | Yes | Yes |
NetBEUI over PPP | Yes | Yes | Yes |
PPP | Yes | Yes | Yes |
SLIP | Yes | Yes | Yes |
| Terminal Services |
|
|
|
LAT11 | - | - | Yes |
Rlogin | Yes | Yes | Yes |
Telnet | Yes | Yes | Yes |
TN3270 | - | - | Yes |
X.25 PAD | Yes | Yes | Yes |
Xremote | - | - | Yes |
For a list of features supported by the back rev feature sets, see the release notes available on the Documentation CD-ROM or the World Wide Web (www.cisco.com). See the section "About Cisco IOS Software Electronic Documentation,". For example, to find a feature set list for Cisco IOS Release 11.1(8), locate the Cisco IOS Software Configuration database. Then select Cisco IOS Release 11.1, and then select Release Notes for Cisco IOS Release 11.1.
RSL, contained on the feature pack CD, is designed to work with a PC running Microsoft Windows 95. The booklet included with the CD explains how to perform this simple process. However, two alternatives are available to download software in systems that do not use Windows 95:
This type of installation uses the copy xmodem flash command. You can also use the ROMMON command xmodem [-cyrx] [filename], but on the console port only.
The following example shows how to use the copy xmodem flash command on a Cisco 3600 series router:
Router#copy xmodem flash
**** WARNING ****
x/ymodem is a slow transfer protocol limited to the current speed
settings of the auxiliary/console ports. The use of the auxilary
port for this download is strongly recommended.
During the course of the download no exec input/output will be
available.
---- ******* ----
Proceed? [confirm]y
Use crc block checksumming? [confirm]y
Max Retry Count [10]:
Perform image validation checks? [confirm]y
Xmodem download using crc checksumming with image validation
Continue? [confirm]y
Partition Size Used Free Bank-Size State Copy Mode
1 4096K 3259K 836K 4096K Read/Write Direct
2 4096K 0K 4095K 4096K Read/Write Direct
[Type ?<no> for partition directory; ? for full directory; q to abort]
Which partition? [default = 1] 2
System flash directory, partition 2:
File Length Name/status
1 68 TESTFILE
[132 bytes used, 4194172 available, 4194304 total]
Destination file name? c3620-i-mz.0918
Erase flash device before writing? [confirm]y
Flash contains files. Are you sure you want to erase? [confirm]y
Copy '' from server
as 'c3620-i-mz.0918' into Flash WITH erase? [yes/no]yes
Erasing device... eeeeeeeeeeeeeeee ...erased
Ready to receive file...........C
Verifying checksum... OK (0x5DE8)
Flash device copy took 00:12:06 [hh:mm:ss]
You can also download an image to the 3600 series router using the console port via the ROMMON command:
xmodem [-cyrx] [filename]
-c use CRC-16
-y use YMODEM protocol
-r copy image to RAM (default is first Flash memory partition)
-x do not launch image on completion of download to DRAM (dangerous!)
The following example shows how to use the xmodem [-cyrx] [filename] command on a Cisco 3600 series router:
rommon 1 > xmodem -c c3620-i-mz.0918
Do not start the sending program yet...
File size Checksum File name
1910476 bytes (0x1d26cc) 0x5de8 c3620-i-mz.0918
WARNING: All existing data in bootflash will be lost!
Invoke this application only for disaster recovery.
Do you with to continue? y/n [n]: y
Ready to receive file c3620-i-mz.0918 ...
Erasing flash at 0x307c0000
Download Complete!
program load complete, entry point: 0x80008000, size: 0x1d25b0
Self decompressing the image : ################################################
This section describes an alternative method you can use to install the router software from the CD-ROM using a PC running Windows 3.1, a Macintosh, or a UNIX system. The process requires that you first obtain a TFTP application or a remote copy protocol (rcp) application, which you can use to set up your computer as a TFTP server or an rcp server. You can use either the copy tftp flash or copy rcp flash command to download the router software to the router.
You can load router software with this alternative method in the following circumstances:
This section describes how to install the router software using a Microsoft Windows 3.1 PC with a TFTP server application. You can also set up your Macintosh or UNIX workstation as a TFTP server and follow the same steps.
To install the software using an rcp application, follow the same procedure and substitute rcp for TFTP in the instructions. You must also substitute the copy rcp flash command for the copy tftp flash command.
Step 1 Install any TFTP server application on the PC. (Not provided by Cisco.)
Step 2 Launch the TFTP server application on the PC. You commonly do this by double-clicking the application icon or its filename.
Step 3 Set up the PC as a TFTP server using the TFTP server application setup or configuration facility.
The user interface of most TFTP server applications includes a setup facility that allows you to specify the PC as a server. For example, from the TFTP menu of one application, you can select Settings to display a panel that includes a checkbox beside the word Server. To configure the local PC as a server, click in this checkbox.
The TFTP server also allows selection of a "root" directory. You must select the directory in which the Cisco IOS files reside, for example d:\cpswinst\images.
 | Caution Make sure you set up your local PC as a TFTP server. If you overlook this step, you will not be able to perform the copy procedure. This reminder also applies if you are using rcp on your system instead of TFTP. |
Step 4 Establish a console session from your local PC (which is now configured as a TFTP server), to the Cisco router.
You can do this in two ways:
Step 5 Connect your PC's Ethernet, Fast Ethernet, or Token Ring port to the router's corresponding LAN port. Use the 10BaseT crossover cable provided if connecting to an Ethernet or Fast Ethernet port. You must use Category 5 cable for Fast Ethernet routers.
For systems without a LAN interface, make sure that the router and the PC have IP connectivity through the available interface (that is, the router and PC can ping each other with IP traffic).
Step 6 From the console, enter the copy tftp flash command.
Step 7 When prompted, enter the PC's IP address.
Step 8 When prompted, enter the filename of the Cisco IOS Release 11.2 image to be copied to the router as in the following example:
Source file name? 80155204.bin
This example specifies the IP feature set for Cisco 3620 routers.
Step 9 In response to the prompt, enter the destination filename and press Enter to indicate that you want to copy the image.
This is the name you select for the image file on the router, not the full pathname of the image on the CD-ROM attached to the PC. In this example, the UNIX filename is used:
Destination file name [80155204.bin]? c3620-i-mz.112-4.xa
During the transfer process, the software displays messages indicating that it has accessed the file you have specified and is loading it.
If the file is not found, check the following: filename; TFTP server is enabled; correct root directory is selected; IP connectivity between the router and TFTP server.
Step 10 Enter yes or no in response to the prompt asking if you want to erase the existing image copy resident in the router's Flash memory before copying the new one:
Erase flash device before writing? [confirm] yes
When copying to internal Flash memory, the system provides an option to erase existing internal Flash memory before writing onto it. Answer yes to the questions. The entire copying process takes several minutes and differs from network to network.
The exclamation point (!) indicates that the copy process is taking place. Each exclamation point (!) indicates that ten packets have been transferred successfully. If you see three periods (...), the transfer failed. Check IP connectivity between the router and TFTP server using the ping command.
Step 11 Enter the reload command to reload the router:
# reload
You do not need to save the system configuration when prompted here. After reload is complete, the router should be running the required Cisco IOS image. Use the show version command to verify.
This section includes reference pages providing detailed information about the copy rcp flash and copy tftp flash commands. This information supplements the information provided in the steps described earlier in the section "Installing the Router Software Using a TFTP Server Application,".
To copy a file from a network server to the router or to another destination using rcp, use the copy rcp flash EXEC command.
copy rcp flash
flash | Specifies internal Flash memory as the destination of the copy operation. |
EXEC
The rcp protocol requires that a client send the remote username of an rcp request to the server. When you issue the copy rcp flash command, by default the Cisco IOS software sends the username associated with the current teletype (TTY), if that name is valid. For example, if the user is connected to the router through Telnet and the user was authenticated through the username command, then the software sends that username as the remote username.
If the TTY username is invalid, the software uses the host name as both the remote and local usernames. To specify a different remote username to be sent to the rcp server, use the ip rcmd remote-username command, and possibly the ip rcmd remote-host command. You can also specify the path of an existing directory along with the remote username.
 | Caution The remote username must be associated with an account on the destination server. If you do not use the ip rcmd remote-username command, and possibly the ip rcmd remote-host command, to specify the name of a remote user associated with an account on the server, then the remote username associated with the current TTY process must be associated with an account on the server. If there is no username for the current TTY process, then the host name must be associated with an account on the server. If the network administrator of the destination server did not establish accounts for the remote username used, this command will not execute successfully when a default remote username is used. |
If you copy a system image from a personal computer used as a file server, the remote host computer must support the remote shell (rsh) protocol.
Use the copy rcp flash to copy a system image from a network server to the router's internal Flash memory using rcp. The Cisco IOS software prompts for the address of the rcp server and rcp filename. When you issue this command, the system provides an option to erase existing Flash memory before writing onto it. The entire copying process takes several minutes and differs from network to network.
Before booting from Flash memory, verify that the checksum of the image in internal Flash memory matches the checksum listed in the README file distributed with the system software image. The checksum of the image in Flash memory is displayed at the bottom of the screen when you issue the copy rcp flash command. The README file was copied to the rcp server automatically when you installed the system software image.
The following example shows how to use the copy rcp flash command on a Cisco 3600 series router. The interface might differ slightly on other systems. This example copies a system image named file1 from the netadmin1 directory on the remote server named SERVER1.CISCO.COM with an IP address of 131.108.101.101 to Flash memory. To ensure that enough Flash memory is available to accommodate the system image to be copied, the Cisco IOS software allows you to erase the contents of Flash memory first.
Router1# configure terminal
Router1(config)# ip rcmd remote-username netadmin1
Router(config)# Ctrl-Z
Router# copy rcp flash
System flash directory, partition 2:
File Length Name/status
1 984 file1 [deleted]
2 984 file1
[2096 bytes used, 8386512 available, 8388608 total]
Address or name of remote host [255.255.255.255]? 131.108.101.101
Source file name? file1
Destination file name [file1]?
Accessing file 'file1' on 131.108.101.101...
Loading dirt/ssangiah/file1 .from 131.108.101.101 (via Ethernet0): ! [OK]
Erase flash device before writing? [confirm]
Flash contains files. Are you sure you want to erase? [confirm]
Copy 'file1' from server
as 'file1' into Flash WITH erase? [yes/no] yes
Erasing device... eeeeeeeeeeeeeeeeeeeeeeeeeeeeeeee ...erased
Loading file1 from 131.108.101.101 (via Ethernet0): !
[OK - 984/8388608 bytes]
Verifying checksum... OK (0x14B3)
Flash copy took 0:00:01 [hh:mm:ss]
The following example shows sample output resulting from copying a system image into a partition of Flash memory. The system prompts only if there are two or more read/write partitions or one read-only and one read/write partition and dual Flash memory bank support in boot ROMs. If the partition entered is not valid, the process terminates. You have the option to enter a partition number, a question mark (?) for a directory display of all partitions, or a question mark and a number (?number) for a directory display of a particular partition. The default is the first read/write partition.
Router# copy rcp flash
System flash partition information:
Partition Size Used Free Bank-Size State Copy-Mode
1 4096K 2048K 2048K 2048K Read Only RXBOOT-FLH
2 4096K 2048K 2048K 2048K Read/Write Direct
[Type ?<no> for partition directory; ? for full directory; q to abort]
Which partition? [default = 2]
If the partition is read-only and has dual Flash memory bank support in boot ROMs, the session continues as follows. Note that the examples show a Cisco 2500 router.
**** NOTICE ****
Flash load helper v1.0
This process will accept the copy options and then terminate
the current system image to use the ROM based image for the copy.
Routing functionality will not be available during that time.
If you are logged in via telnet, this connection will terminate.
Users with console access can see the results of the copy operation.
---- ******** ----
Proceed? [confirm]
System flash directory, partition 1:
File Length Name/status
1 3459720 master/igs-bfpx.100-4.3
[3459784 bytes used, 734520 available, 4194304 total]
Address or name of remote host [255.255.255.255]? 131.108.1.1
Source file name? master/igs-bfpx-100.4.3
Destination file name [default = source name]?
The file will be copied into the partition given earlier by the user:
Loading master/igs-bfpx.100-4.3 from 131.108.1.111: !
Erase flash device before writing? [confirm]
Flash contains files. Are you sure? [confirm]
Copy 'master/igs-bfpx.100-4.3' from TFTP server
as 'master/igs-bfpx.100-4.3' into Flash WITH erase? [yes/no] yes
If the partition is read/write, the session continues as follows:
System flash directory, partition 2:
File Length Name/status
1 3459720 master/igs-bfpx.100-4.3
[3459784 bytes used, 734520 available, 4194304 total]
Address or name of remote host [255.255.255.255]? 131.108.1.1
Source file name? master/igs-bfpx.100-4.3
Destination file name [default = source name]?
The file will be copied into the partition given earlier by the user:
Accessing file 'master/igs-bfpx.100-4.3' on ABC.CISCO.COM...
Loading master/igs-bfpx.100-4.3 from 131.108.1.111: !
Erase flash device before writing? [confirm]
Flash contains files. Are you sure? [confirm]
Copy 'master/igs-bfpx.100-4.3' from TFTP server
as 'master/igs-bfpx.100-4.3' into Flash WITH erase? [yes/no] yes
boot config
boot system flash
cd
copy flash rcp
ip rcmd remote-username
verify flash
To copy a file from a TFTP server to the router or to another destination, use the copy tftp flash EXEC command.
copy tftp flash
flash | Specifies internal Flash memory as the destination of the copy operation. |
EXEC
The system prompts for the address of the TFTP server and TFTP filename if you do not provide them at the command line. When copying to internal Flash memory, the system provides an option to erase existing internal Flash memory before writing onto it. The entire copying process takes several minutes and differs from network to network.
Before booting from Flash memory, verify that the checksum of the image in Flash memory matches the checksum listed in the README file distributed with the system software image. The checksum of the image in Flash memory is displayed at the bottom of the screen when you issue the copy tftp flash command. The README file was copied to the TFTP server automatically when you installed the system software image.
Examples
The following example shows sample output of copying a system image named file1 into Flash memory:
Router# copy tftp flash
System flash directory, partition 2:
File Length Name/status
1 984 file1 [deleted]
2 984 file1
[2096 bytes used, 8386512 available, 8388608 total]
Address or name of remote host [255.255.255.255]? 223.255.254.254
Source file name? file1
Destination file name [file1]?
Accessing file 'file1' on 223.255.254.254...
Loading dirt/ssangiah/file1 .from 223.255.254.254 (via Ethernet0): - [OK]
Erase flash device before writing? [confirm]
Flash contains files. Are you sure you want to erase? [confirm]
Copy 'file1' from server
as 'file1' into Flash WITH erase? [yes/no] yes
Erasing device... eeeeeeeeeeeeeeeeeeeeeeeeeeeeeeee ...erased
Loading file1 from 223.255.254.254 (via Ethernet0): !!!!(etc.)
[OK - 984/8388608 bytes]
Verifying checksum... OK (0x14B3)
Flash copy took 0:00:01 [hh:mm:ss]
The exclamation point (!) indicates that the copy process is taking place. Each exclamation point (!) indicates that ten packets have been transferred successfully.
The following example shows sample output resulting from copying a system image into a partition of Flash memory. The system will prompt only if there are two or more read/write partitions or one read-only and one read/write partition and dual Flash bank support in boot ROMs. If the partition entered is not valid, the process terminates. You can enter a partition number, a question mark (?) for a directory display of all partitions, or a question mark and a number (?number) for directory display of a particular partition. The default is the first read/write partition.
Router# copy tftp flash
System flash partition information:
Partition Size Used Free Bank-Size State Copy-Mode
1 4096K 2048K 2048K 2048K Read Only RXBOOT-FLH
2 4096K 2048K 2048K 2048K Read/Write Direct
[Type ?<no> for partition directory; ? for full directory; q to abort]
Which partition? [default = 2]
If the partition is read-only and has dual Flash bank support in boot ROMs, the session continues as follows:
**** NOTICE ****
Flash load helper v1.0
This process will accept the copy options and then terminate
the current system image to use the ROM based image for the copy.
Routing functionality will not be available during that time.
If you are logged in via telnet, this connection will terminate.
Users with console access can see the results of the copy operation.
---- ******** ----
Proceed? [confirm]
System flash directory, partition 1:
File Length Name/status
1 3459720 master/igs-bfpx.100-4.3
[3459784 bytes used, 734520 available, 4194304 total]
Address or name of remote host [255.255.255.255]? 131.108.1.1
Source file name? master/igs-bfpx-100.4.3
Destination file name [default = source name]?
The file will be copied into the partition given earlier by the user:
Loading master/igs-bfpx.100-4.3 from 131.108.1.111: !
Erase flash device before writing? [confirm]
Flash contains files. Are you sure? [confirm]
Copy 'master/igs-bfpx.100-4.3' from TFTP server
as 'master/igs-bfpx.100-4.3' into Flash WITH erase? [yes/no] yes
If the partition is read/write, the session continues as follows:
System flash directory, partition 2:
File Length Name/status
1 3459720 master/igs-bfpx.100-4.3
[3459784 bytes used, 734520 available, 4194304 total]
Address or name of remote host [255.255.255.255]? 131.108.1.1
Source file name? master/igs-bfpx.100-4.3
Destination file name [default = source name]?
The file will be copied into the partition given earlier by the user:
Accessing file 'master/igs-bfpx.100-4.3' on ABC.CISCO.COM...
Loading master/igs-bfpx.100-4.3 from 131.108.1.111: !
Erase flash device before writing? [confirm]
Flash contains files. Are you sure? [confirm]
Copy 'master/igs-bfpx.100-4.3' from TFTP server
as 'master/igs-bfpx.100-4.3' into Flash WITH erase? [yes/no] yes
copy flash tftp
verify
verify flash
Cisco IOS software documentation is provided on the Documentation CD-ROM that is included with your feature pack. To locate the correct documentation, first determine the Cisco IOS release level of the image you loaded (see Table 1, the Description column).
You can either use the Documentation CD or go to www.cisco.com (select Products & Ordering, Documentation, Cisco Product Documentation, Cisco IOS Software Configuration, then select the level of release). Typical documentation consists of the following:
Cisco IOS configuration guides describe system configuration and maintenance tasks and provide comprehensive configuration examples. The configuration guides do not include command syntax for every command, so you should use them in conjunction with the command references. The Cisco configuration guides give in-depth descriptions of configuration tasks.
Cisco IOS command references describe the commands necessary for configuring and maintaining your system. If you are new to Cisco software, you should use the Cisco command references in conjunction with the configuration guides to reference commands and detailed information pertaining to their use. If you are an experienced network administrator, you might want to use the Cisco command references as standalone manuals.
Cisco Connection Online (CCO) is Cisco Systems' primary, real-time support channel. Maintenance customers and partners can self-register on CCO to obtain additional information and services.
Available 24 hours a day, 7 days a week, CCO provides a wealth of standard and value-added services to Cisco's customers and business partners. CCO services include product information, product documentation, software updates, release notes, technical tips, the Bug Navigator, configuration notes, brochures, descriptions of service offerings, and download access to public and authorized files.
CCO serves a wide variety of users through two interfaces that are updated and enhanced simultaneously: a character-based version and a multimedia version that resides on the World Wide Web (WWW). The character-based CCO supports Zmodem, Kermit, Xmodem, FTP, and Internet e-mail, and it is excellent for quick access to information over lower bandwidths. The WWW version of CCO provides richly formatted documents with photographs, figures, graphics, and video, as well as hyperlinks to related information.
You can access CCO in the following ways:
For a copy of CCO's Frequently Asked Questions (FAQ), contact cco-help@cisco.com. For additional information, contact cco-team@cisco.com.
If you are a network administrator and need personal technical assistance with a Cisco product that is under warranty or covered by a maintenance contract, contact Cisco's Technical Assistance Center (TAC) at 800 553-2447, 408 526-7209, or tac@cisco.com. To obtain general information about Cisco Systems, Cisco products, or upgrades, contact 800 553-6387, 408 526-7208, or cs-rep@cisco.com.
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
Posted: Tue Dec 17 19:31:46 PST 2002
All contents are Copyright © 1992--2002 Cisco Systems, Inc. All rights reserved.
Important Notices and Privacy Statement.