|
|

This configuration note describes how to install and configure the Catalyst 5000 series fiber Token Ring module (product number WS-X5031).
For a complete description of commands to configure and maintain Catalyst 5000 series switches, refer to the Catalyst 5000 Series Software Configuration Guide and the Catalyst 5000 Series Command Reference publications. For complete switch hardware configuration and maintenance procedures, refer to the Catalyst 5000 Series Installation Guide. For information on Catalyst 5000 series switching modules, refer to the Catalyst 5000 Series Module Installation Guide. These documents are available on the Cisco Connection Documentation, Enterprise Series CD, or in print.
Cisco documentation and additional literature are available in a CD-ROM package, which ships with your product. The Documentation CD-ROM, a member of the Cisco Connection Family, is updated monthly. Therefore, it might be more current than printed documentation. To order additional copies of the Documentation CD-ROM, contact your local sales representative or call customer service. The CD-ROM package is available as a single package or as an annual subscription. You can also access Cisco documentation on the World Wide Web at http://www.cisco.com, http://www-china.cisco.com, or http://www-europe.cisco.com.
If you are reading Cisco product documentation on the World Wide Web, you can submit comments electronically. Click Feedback in the toolbar and select Documentation. After you complete the form, click Submit to send it to Cisco. We appreciate your comments.
This document contains the following sections:
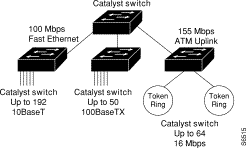
The Catalyst 5000 series switch provides high-density switched Ethernet and Fast Ethernet for both wiring closet and data center applications. The switch includes a single, integrated 1.2-Gbps switching backplane that supports switched Ethernet with repeater connections, Fast Ethernet with backbone connections, Fiber Distributed Data Interface (FDDI), Copper Distributed Data Interface (CDDI), Asynchronous Transfer Mode (ATM), and 4- and 16- Mbps fiber and copper Token Ring. The Catalyst 5000 provides switched connections to individual workstations, servers, LAN segments, backbones, or other Catalyst 5000 switches using shielded twisted-pair (STP), unshielded twisted-pair (UTP), and fiber-optic cable. Figure 1 is an example of a configuration using the Catalyst 5000 series switch.
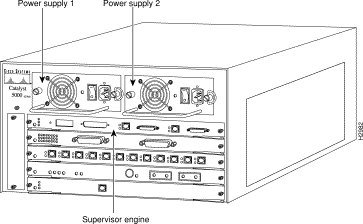
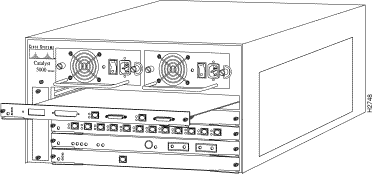
Depending on the Catalyst 5000 series switch model that you are using, there are up to 11 interface slots available on the switch. Regardless of the Catalyst 5000 series switch, interface slot 1 supports a supervisor engine module, which provides Layer 2 switching, local and remote management, and dual Fast Ethernet interfaces. Slot 13 on the Catalyst 5500 switch is reserved for the ATM Switch Processor (ASP) module. The remaining slots are used for any combination of modules for additional Ethernet, Fast Ethernet, CDDI/FDDI, ATM, and Token Ring connections. Figure 2 shows the rear view of the Catalyst 5000 series switch, which provides access to the supervisor engine, all switching modules, power supplies, and fan assembly.
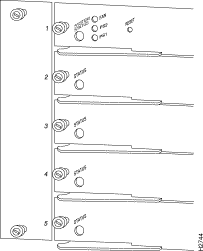
The fiber Token Ring module, shown in Figure 3, provides 16 Token Ring 3M Volition VF-45 sockets for the Catalyst 5000 series switch. The ports on the fiber Token Ring module support multimode fiber connections via 3M Volition VF-45 ST-to-RJ-45 patch cords. For more information on Volition VF-45 cables, see the "Fiber Token Ring Module Requirements" section.

The Catalyst 5000 series fiber Token Ring module provides the following features:
Note The fiber Token Ring module supports the IEEE 802.5j standard for ring in /ring out (RI/RO) compliance as well as for fiber lobe extension. The ports on the Catalyst 5000 series fiber Token Ring module also support the proprietary RI/RO signaling used for attaching to the IBM 8230 and the Olicom OC-2610 Controlled Access Unit.
Note The Catalyst 5000 series fiber Token Ring module requires supervisor engine module software, Release 3.2(1b) or later. Soft error monitoring and remove adapter support requires Token Ring software Release 3.3(1) or later and supervisor engine module software Release 5.1(1) or later.
The Catalyst 5000 series fiber Token Ring module applies the IEEE 802.5 annex K models of Concentrator Relay Functions (CRFs) and Bridge Relay Functions (BRFs). The Token Ring Concentrator Relay Function (TrCRF) and the Token Ring Bridge Relay Function (TrBRF) models support for the following bridging modes:
For more information about bridging modes, please see the "Understanding Token Ring Switching" section. For more information on TrBRFs and TrCRFs, see the "Token Ring VLANs" section.
Each of the 16 Token Ring ports on the Catalyst 5000 series fiber Token Ring module can operate in one of the following modes:
The mode of operation can be configured, or it can be automatically sensed when equipment is connected to the port. The media speed (4 or 16 Mbps) can also be configured or automatically sensed in all port modes.
The ports on the Catalyst 5000 series fiber Token Ring module are designed to enable attachment to a traditional main ring path coming from either an MAU or a controlled access unit (CAU). Any of the 16 ports can be configured to connect to the RI or RO ports of a MAU or CAU.
Note The fiber Token Ring module supports the IEEE 802.5j standard for ring in /ring out (RI/RO) compliance as well as for fiber lobe extension. The ports on the Catalyst 5000 series fiber Token Ring module also support the proprietary RI/RO signaling used for attaching to the IBM 8230 and the Olicom OC-2610 Controlled Access Unit.
A loopback function has been implemented on the fiber module ports so that if the port is disabled or the switch is powered off there will not be a break in the attached main ring. This function means that attaching a cable from the RI port of a MAU port to one of the switch ports in effect joins the primary and the backup ring in a MAU/CAU main ring system. Connecting the other end of the main ring to another switch port creates a redundant path because the two switch ports are connected to the same segment.
Therefore, the STP must be enabled, which will place one port in forward mode and the other in blocked mode. If there is a break in the main ring, the STP will place both ports in forward mode, and all MAC addresses on both segments will be relearned.
Note It is not possible to automatically verify whether the port has been connected according to the configuration. Any errors, such as attaching a port to a normal MAU port when the fiber Token Ring module port has been configured for RI/RO, will cause a complete disruption of the ring to which the port is attached. Therefore, be careful when using the RI/RO feature.
The Catalyst 5000 series fiber Token Ring module supports 4- and 16-Mbps Token Ring transmission speeds. You can configure ports on the Catalyst 5000 series fiber Token Ring module to operate at one of these speeds or to automatically sense the speed of the ring to which it is connected. However, with Token Ring technology, a transmission speed cannot be changed without closing and reopening the port, therefore the following rules apply:
Note If the ports on the fiber Token Ring module are configured to automatically sense the speed of the ring, the first port inserted on the ring will not set the speed, for it will be unable to detect the speed.
Note Closing and opening the port on an existing ring at a different transmission speed from which the ring is currently operating will cause the port to issue a beacon on that ring.
The Catalyst 5000 series fiber Token Ring module supports a new token passing standard called Dedicated Token Ring (DTR). DTR is the IEEE 802.5R standard that:
DTR is particularly useful for providing improved access to central resources, such as network servers, for servers can be directly attached to a switch.
To address the needs of delay-sensitive data, such as multimedia data, each port on the Catalyst 5000 series fiber Token Ring module has two data queues: high priority and low priority.
The queue for a frame is determined by the value of the priority field in the frame control (FC) byte of the frame. If the FC priority is above the user-defined priority level (the default is 3), the frame is put in the high-priority queue and is transmitted using the frame priority. If the FC priority is at or below the user-defined priority level, then the frame is sent to the low-priority queue.
Note The defaults for the priority queue maintain compatibility with current source-route bridges and provide a high-priority queue for Token Ring multimedia traffic (priorities 5 and 6).
For information on defining a priority level, see the "Setting the Frame Priority Levels" section.
Many bridged networks today use filtering to reduce broadcast traffic, block protocols, and provide basic security. The Catalyst 5000 series fiber Token Ring module provides filtering capabilities for the same purpose.
You can filter frames based on the following:
MAC address filters can be configured for only input ports. DSAP/SNAP filters can be configured for both input and output ports. You can configure up to 16 MAC address or DSAP/SNAP filters for each port on the fiber Token Ring module.
To filter data based on MAC address, you specify an address and indicate whether you want to block or allow frames that contain the address as a source or destination address. To filter data based on protocol, specify either a DSAP or SNAP and specify whether to permit or deny frames with that protocol.
For information on configuring filters, see the "Configuring Filters" section.
For parallel SRB or SRT backbones, ARE reduction ensures that the number of ARE frames generated by the switch does not overwhelm the network.
The IEEE 802.1d SRT standard specifies two optional ways of reducing the ARE explosion. The Catalyst 5000 series fiber Token Ring module discards any ARE frames that have already been on a ring that is attached to the switch.
This mechanism is configurable and ensures that only one ARE frame is received on each ring within each VLAN. The number of ARE frames is equal to the number of external parallel paths between the rings. If a port on the switch fails, or is disabled, the switch will no longer check for this ring number in the Routing Information Field (RIF). This bypass allows frames to travel on alternate paths.
By default, ARE reduction is enabled.
For information on enabling and disabling ARE reduction, see the "Enabling and Disabling ARE Reduction" section.
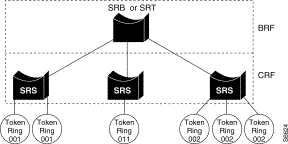
With a VLAN, logical rings can be formed by defining port groups that have the same ring number. The IEEE standard calls such a Token Ring port group a TrCRF. Within the TrCRF, source-route switching is used for forwarding based on either MAC addresses or route descriptors (RDs). If desired, you may configure the entire VLAN to operate as a single ring (for example, a single TrCRF).
Multiple logical rings or TrCRFs can be interconnected via a single TrBRF. The TrBRF provides either the SRB or SRT switching mode. For source routing, the switch, or network of switches, appears as a single bridge between the logical rings. If SRB is used, duplicate MAC addresses can be defined on different logical rings.
For more information on Token Ring VLANs, see the "Token Ring VLANs" section. For information on configuring a VLAN, see the "Configuring VLANs" section.
When creating a fault-tolerant internetwork, a loop-free path must exist between all nodes in a network. A spanning-tree algorithm is used to calculate the best loop-free path through a Catalyst 5000 series switched network. Spanning-tree packets are sent and received by switches in the network at regular intervals. The packets are not forwarded by the switches participating in the STP, but are instead used by the switches to identify the loop-free path. STPs perform this function for Catalyst 5000 series switches.
The Catalyst 5000 series switch uses the IEEE 802.1d or Cisco STP on all TrCRFs. The Catalyst 5000 series switch uses the IBM or IEEE STP on all TrBRFs. For more information on the STPs running on TrCRFs and TrBRFs, see the "Configuring STP" section. By default, spanning-tree support is enabled.
For more information on STPs, see the "Configuring STP" section and the "Understanding Token Ring Switching" section.
With the Catalyst 5000 series fiber Token Ring module, you can preform the following tasks:
The Catalyst 5000 series fiber Token Ring module can be managed via an SNMP manager (such as CiscoView). The fiber Token Ring module supports nine Management Information Bases (MIBs). Six of the MIBs are standard MIBs, which are defined by RFCs and are included with most SNMP management applications. Three of the MIBs are Cisco proprietary MIBs and can be obtained from CCO. See the "Cisco Connection Online" section for access to CCO information.
In addition to the standard MIBs supported the Catalyst 5000 series switch, the fiber Token Ring module supports the following additional MIBs:
The proprietary MIBs supported are:
Most user configurable variables are supported in either the standard MIBs or private MIBs. Configuration settings, such as port attributes, and operational information, such as address tables, are fully accessible through SNMP. Certain other settings, such as passwords and console settings, cannot be viewed or modified via SNMP for security reasons.
CiscoView is a graphical user interface device management software application that provides dynamic status, statistics, and comprehensive configuration information for Cisco System's switched and internetworking products. CiscoView allows you to display configuration and performance information, and perform minor troubleshooting tasks.
RMON is an industry-standard method for providing network statistics monitoring using SNMP. It also collects fault, performance, and configuration statistics. RMON can monitor continuously, even when communication with the management station is not possible or efficient. It can then notify the management station when an exceptional condition occurs.
In typical SNMP management, the SNMP manager has to continuously poll the Catalyst 5000 series switch for fault, performance, and configuration information while waiting for the value to change. This causes increased traffic through the network. With RMON, you can have the switch monitor a particular statistic internally, and when the statistic reaches a threshold the Catalyst 5000 series switch will send a trap to the client. This monitoring method reduces traffic between the SNMP manager and the Catalyst 5000 series switch.
As an option, the Catalyst 5000 series fiber Token Ring module provides RMON support statistics, history, alarms, and events. It also provides support for the following groups of the Token Ring extensions to the Remote Network Monitoring MIB (RFC 1513):
A collection of MAC-layer statistics kept for each Token Ring interface, such as the total number of MAC packets received and the number of times the port entered a beaconing state.
A collection of promiscuous statistics kept for non-MAC packets on each Token Ring interface, such as the total number of good non-MAC frames received that were directed to an LLC broadcast address.
The Catalyst 5000 series Token Ring module supports the ringStationControlTable portion of the Token Ring Ring Station Group. This support allows a Catalyst 5000 series Token Ring module to gather segment information from each ring segment to which it is attached. This segment information includes Ring State, Beacon Sender, Beacon NAUN, and Active Monitor MAC Address, as well as Station Order Changes.
An ordered list of the stations on the monitored rings.
A list of ring station entries. An entry exists for each station that is currently or has previously been detected as being physically present on the ring.
A list of ring station configuration control entries. Each entry controls the management of stations by a probe. One entry exists in this table for each active station in the ring station table.
You can use an external RMON probe for full RMON support.
Access to RMON data is available only via an SNMP management application that supports RFC 1757 and RFC 1513. You cannot access RMON via the Catalyst 5000 series switch console interface; however, the console statistics provide similar information. For full utilization of RMON data, you should use Cisco's TrafficDirector.
To aid in network management, the Catalyst 5000 series fiber Token Ring module allows you to perform active port monitoring. Active port monitoring copies traffic from a Token Ring port to a Token Ring SPAN port within the switch. You can then attach an external Token Ring monitor (network analyzer) or RMON probe to the SPAN port.
The Catalyst 5000 series Token Ring module software Release 3.3(1) and later performs error detection and isolation by monitoring the Report Soft Error MAC frames generated by stations on each port. Soft errors occur during normal ring operation and do not typically disrupt traffic on the ring. However, soft errors can occur at a rate that could potentially degrade the performance of the ring.
Using the soft error monitoring feature, you can configure soft error thresholds and sampling intervals for a port. During the interval you define, the Catalyst 5000 series fiber Token Ring module monitors the stations on the port and, if the threshold is exceeded, can be configured to generate a trap indicating the port number and station on which the threshold was exceeded. If necessary, you can issue a Remove Ring Station MAC frame to remove the station from the ring.
In summary, the Catalyst 5000 series fiber Token Ring module performs the following tasks:
Before installing a Catalyst 5000 series fiber Token Ring module, ensure that your existing system components meet the following minimum requirements for compatibility:
Note Soft error monitoring and remove adapter support requires Token Ring software Release 3.3(1) or later and supervisor engine module software Release 5.1(1) or later.
Note The software images containing the latest upgrades and modifications are released regularly to provide the optimum software available. Cisco Systems strongly recommends that you check Cisco Connection Online at http://www.cisco.com for the latest released software image.
In addition, you will need 16 3M Volition VF-45 ST-to-RJ-45 patch cords.
Table 1 shows the technical specifications for the 16-port fiber Token Ring module:
Depending on the Catalyst 5000 series switch model that you are using, there are up to 11 interface slots available on the switch. Regardless of the Catalyst 5000 series switch, interface slot 1 supports a supervisor engine module. Slot 13 on the Catalyst 5500 switch is reserved for the ATM Switch Processor (ASP) module. All other slots support any combination of network interface switching modules or provides maximum port densities of up to 176 Token Ring interfaces.
The Catalyst 5000 series fiber Token Ring module has LEDs that indicate the status and activity of the module and its ports. There is one LED associated with the Token Ring module and two LEDs associated with each of the 16 ports: Status and Activity.
For information on reading the Token Ring module and port LEDs, see the "Troubleshooting the Fiber Token Ring Module" section.
There are two types of fiber-optic cable: single-mode fiber (SMF) and multimode fiber (MMF). The Catalyst 5000 series fiber Token Ring module uses MMF fiber-optic cable. Mode refers to the angle at which light rays (signals) are reflected and propagated through the optical-fiber core, which acts as a waveguide for the light signals. MMF has a relatively thick core (62.5/125 micron) that reflects light rays at many angles. SMF has a narrow core (8.7 to 10/125 micron) that allows light to enter only at a single angle.
Although MMF allows more light signals to enter at a greater variety of angles (modes), the different angles create multiple propagation paths that cause the signals to spread out in time and limit the rate at which data can be accurately received. This distortion does not occur on the single path of the single-mode signal; therefore, SMF is capable of higher bandwidth and greater cable run distances than MMF. Multimode transmitters usually use LEDs as a light source. Single-mode transmitters use a laser diode, which is capable of sustaining faster data rates. Single-mode and multimode interfaces use a photodiode detector at the receiver to translate the light signal into electrical signals. Table 2 shows the transmit power level for fiber Token Ring module media.
Table 2 MMF Token Ring Transmit and Receive Power Levels
| Optical Power | Minimum | Typical | Maximum |
|---|---|---|---|
Before installing the Catalyst 5000 series fiber Token Ring module, read this section carefully, it contains information on pre-installation planning.
Note Before installing the Catalyst 5000 series fiber Token Ring module, read the "Translated Safety Warnings" section on page 139.
This section discusses the following topics:
When preparing your site for network connections to the switch, you need to consider a number of factors related to each type of interface:
Before installing the switch, have all additional external equipment and cables on hand. For ordering information, contact a customer service representative.
Observe the following cautions when installing an expansion module into an expansion slot of a Catalyst 5000 series switch chassis.
Before you begin installing the Catalyst 5000 Token Ring module, review the safety and ESD-prevention guidelines in this section to avoid injuring yourself or damaging the equipment.
Follow these guidelines when working with any equipment powered by electricity:
ESD damage occurs when electronic devices or components are improperly handled. This damage results in complete or intermittent failures. The supervisor engine and switching modules each consist of a printed circuit board fixed in a metal carrier. Electromagnetic interference (EMI) shielding, connectors, and a handle are integral components of the carrier. Although the metal carrier helps protect modules from ESD, use a preventive antistatic strap when you handle the supervisor engine or switching modules. Hold the carriers by the handles and the carrier edges only; never touch the modules or connector pins.
Guidelines for preventing ESD damage are the following:
The Catalyst 5000 series switching modules support hot swapping. The hot-swapping feature enables you to install, remove, replace, and rearrange the switching modules without turning off the system power. When the Catalyst 5000 series switch detects that a switching module has been installed or removed, it automatically runs diagnostic and discovery routines, acknowledges the presence or absence of the switching module, and resumes the system operation without any operator intervention.
The supervisor engine module and each switching module contain a bus-type connector that connects with the system backplane. Each card connector consists of a set of tiered pins, in three lengths. The pins send specific signals to the system as they make contact with the backplane of the Catalyst 5000 series switch. The system assesses the signals it receives and the order in which it receives them to determine what event is occurring and what task it needs to perform, such as reinitializing new interfaces or shutting down removed interfaces.
For example, when inserting your Catalyst 5000 series fiber Token Ring module, the longest pins make contact with the backplane first and the shortest pins make contact last. The system recognizes the signals and the sequence in which it receives them. The system expects to receive signals from the individual pins in this logical sequence, and the ejector levers help to ensure that the pins mate in this sequence.
When you remove or insert a switching module, the backplane pins send signals to notify the system. The system then performs the following tasks:
1. Rapidly scans the backplane for configuration changes.
2. Initializes the newly inserted switching module, notes any removed interfaces, and places them in the administratively shut-down state.
3. Brings all previously configured interfaces on the switching module back to the state they were in when they were removed. Any newly inserted interfaces are put in the administratively shutdown state, as if they were present (but unconfigured) at boot time. If a similar switching module type has been reinserted into a slot, then its ports are configured and brought on line up to the port count of the original switching module.
When you insert a new switching module, the system runs a diagnostic test on the new interfaces and compares them to the existing configuration. If this initial diagnostic test fails, the system remains off line for another 15 seconds while it performs a second set of diagnostic tests to determine whether or not the switching module is faulty and if normal system operation is possible.
If the second diagnostic test passes, which indicates that the system is operating normally and the new switching module is faulty, the system resumes normal operation but leaves the new interfaces disabled. If the second diagnostic test fails, the system crashes, which usually indicates that the new switching module has created a problem in the bus and should be removed.
Use the ejector levers (Figure 5) to align and seat the card connectors in the backplane. Failure to use the ejector levers and insert the switching module properly can disrupt the order in which the pins make contact with the backplane.
Before installing the fiber Token Ring module, carefully review the instructions in the "Installing the Fiber Token Ring Module" section and the "Removing Switching Modules or Module Fillers" section. Also review the following list of examples of incorrect insertion practices and results that you want to avoid when installing the fiber Token Ring module.
When installing the fiber Token Ring module:
It is also important to use the ejector levers when removing a switching module to ensure that the card connector pins disconnect from the backplane in the logical sequence expected by the system. Any supervisor engine module or switching module that is only partially connected to the backplane can hang the bus. Detailed steps for correctly performing hot swap are included in the "Installing the Catalyst 5000 Series Fiber Token Ring Module" section.
This section explains the process you should follow to install the Catalyst 5000 series fiber Token Ring module.
Before installing the fiber Token Ring module, ensure that you have read the information in the "Planning for Installation" section.
This section discusses the following topics:
To install the Catalyst 5000 Token Ring module, you will need the following tools:
If a switching module or filler (blank) module exists in the slot in which you are planning to install the Catalyst 5000 Token Ring module, remove the existing item before installing the Catalyst 5000 Token Ring module. If there is no switching module or switching module filler in the slot in which you are planning to install the Catalyst 5000 Token Ring module, proceed to the "Installing the Fiber Token Ring Module" section.
To remove the existing module or module filler:
Step 2 Determine the slot for the fiber Token Ring module and ensure that there is enough clearance to accommodate any interface equipment that you connect directly to the fiber Token Ring module ports. If possible, place the switching module between empty slots that contain only switching module filler plates.
Step 3 Using a flat-blade screw driver, turn the captive installation screw on the left side of the carrier counter-clockwise for two full turns.
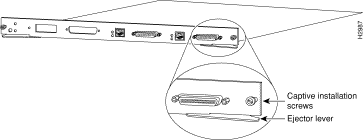
Step 4 Using a flat-blade screw driver, turn the captive installation screw on the right side of the carrier counter-clockwise two full turns.
Step 5 Repeat steps 3 and 4 until you have completely loosened the captive installation screws.
Step 6 Place your thumbs on the left and right ejector levers and simultaneously push both the left and right levers to release the switching module or module filler from the backplane connector.
Step 7 Grasp the switching module or module filler with one hand and place your other hand under the carrier to support and guide the module out of the slot.
Step 8 Keeping the module or module filler at a 90-degree orientation to the backplane, carefully pull the module or module filler straight out of the slot, keeping your other hand under the carrier to guide it.
Note If you are performing a hot swap, the console displays the message "Module n has been removed." However, this message does not appear if you are connected to the Catalyst 5000 through a Telnet session.
Step 9 If you have removed a switching module, place the removed module on an antistatic mat or antistatic foam, or immediately install it in another slot.
Step 10 If you are not installing a switching module in the empty slot immediately, install a switching module filler (part number 800-00292-01) to keep dust out of the chassis and to maintain proper airflow through the switching module compartment.
You can install the Catalyst 5000 series fiber Token Ring module in any of the module slots except slot 1, which is reserved for the supervisor engine module (which is a required system component), or slot 13 on the Catalyst 5500 switch, which is reserved for the ASP module. Depending on the model of the Catalyst 5000 series switch you are using, the module slots are numbered 1 through 13 from the top to bottom when viewing the Catalyst 5000 series switch from the rear (Figure 6).
Switching module fillers, which are blank switching module carriers, are installed in the slots without modules to maintain consistent airflow through the switching module compartment.
To install the fiber Token Ring module:
Step 2 Aligning the notch on the sides of the switching module with the grooves in the slot, place the back of the switching module in the slot (Figure 7).
Step 3 Keep the module at a 90-degree angle to the backplane and carefully slide the switching module into the slot until the module faceplate makes contact with the ejector levers.
Step 4 Using the thumb and forefinger of each hand, simultaneously push in the left and right levers to fully seat the module in the backplane connector.
Note If you are performing a hot swap, the console displays the message, "Module n has been inserted." However, this message does not appear if you are connected to the Catalyst 5000 through a Telnet session.
Step 5 Using a flat-blade screwdriver, turn the captive installation screw on the left side of the carrier clockwise two full turns.
Step 6 With the screwdriver, turn the captive installation screw on the right side of the carrier clockwise two full turns.
Step 7 Repeat steps 5 and 6 until the captive installation screws are tight. Do not use excessive force to tighten the screws.
Step 8 Attach network interface cables or other devices to the interface ports.
Step 9 Use the set interface command facility to configure the new interfaces. This configuration does not have to be done immediately, but the interfaces will not be available until you configure them. For information on configuring the new interfaces, see the Catalyst 5000 Series Advanced Software Configuration Guide.
When you remove and replace the Catalyst 5000 series switching modules, the system provides status messages on the console screen. These messages are for information use only.
In the following display example, using the show system and show module commands, you can follow the events that are logged by the system when a switching module is removed from slot 4. When the show port command is used to query the module, the system reports notconnect. When the module is reinserted, the system marks the module as ok.
This section provides instructions for connecting devices such as hubs, servers, PCs, and workstations to the Catalyst 5000 series fiber Token Ring module. When making a connection, remember the following:
Observe the following warnings and notes when cabling an expansion module with fiber-optic cable.
To connect the cables, perform the following steps:
Step 2 Label each end of the cable so that it will be easy to find the device if you have to troubleshoot a network problem. Suggested information for this label includes the following:
The Catalyst 5000 series fiber Token Ring module is shipped with default configuration parameters and can function with these defaults. Therefore, you may not have to configure the module for it to work in your network. However, if you want or need to alter the configuration of the fiber Token Ring module, you can do so.
This section describes how to use the CLI to configure the ports on the Token Ring switching module. This section also contains information about STPs and Token Ring VLANs. For additional information on the CLI, refer to the Catalyst 5000 Series Command Reference.
Note For definitions of all the commands specific to the fiber Token Ring module and existing Catalyst 5000 series switch commands that have been modified for the fiber Token Ring module, see the "Catalyst 5000 Series Fiber Token Ring Module Command Reference" section.
This section discusses the following topics:
Note If you have not already configured the interface for the fiber Token Ring module, you may want to do so. This configuration does not have to be done immediately, but the interfaces will not be available until you configure them. For information on configuring the new interfaces, see the Catalyst 5000 Series Advanced Software Configuration Guide.
The default values of the fiber Token Ring module features are:
Before you can customize certain parameters of the Token Ring module, you must invoke the privileged mode of the Catalyst 5000 series switch. When in privileged mode, you can issue commands to configure or troubleshoot the system.
Step 2 Type your password and press Enter. The Console> prompt now indicates that you are in enable mode by displaying (enable) next to the console prompt.
For more information on configuring the Token Ring interface parameters, see the "Configuring Token Ring Port Parameters" section.
This section contains information on the following topics:
Note If you change certain configuration parameters of a connected port, the port will close and reopen and you will lose all address information and statistics for that port.
By default, no names are assigned to the ports on the Catalyst 5000 series fiber Token Ring module. However, you can assign names to each of the ports on your Token Ring module using the set port name command.
To assign a name to a port on the Token Ring module, issue the following command in privileged mode:
After entering the set port name command, you see a display similar to the following:
There are two types of frame priorities that you can set for a port.
To set the frame priority levels for a port, issue the following command in privileged mode:
After entering the set tokenring priority command, you see a display similar to the following:
The speed of the port is in megabits per second (Mbps). The Token Ring module ports can be set to 4 or 16 Mbps transmission speeds. The default speed, auto, enables the ports to automatically configure themselves to operate at the proper speed (4 or 16 Mbps). However, you can configure the port speed if necessary.
Note If the ports on the Token Ring module are configured to automatically sense the speed of the ring, the first port inserted on the ring will not set the speed, for it will be unable to detect the speed.
To set the transmission speed for a Token Ring module port, issue the following command in privileged mode:
After entering the set port speed command, you see a display similar to the following:
Note Closing and opening the port on an existing ring at a different transmission speed from which the ring is currently operating will cause the port to issue a beacon on that ring.
The ports of the Catalyst 5000 series fiber Token Ring module are capable of operating in half-duplex mode or full-duplex mode. The port can behave as either a concentrator port or an end station. The default mode, auto, enables the port to detect the transmission mode it needs to use. However, you can configure the mode if necessary.
Any of the 16 ports on the fiber Token Ring module can be configured for RI/RO out mode. For more information on RI/RO ports, see the "Ring In/Ring Out Ports" section.
To set the transmission mode being used by a port, issue the following command in privileged mode:
After entering the set tokenring portmode command, you see a display similar to the following:
The Token Ring module interface ports support early token release when transmitting frames. Early token release is a technique used in Token Ring networks that allows a station to release a new token onto the ring immediately after transmitting, instead of waiting for the first frame to return. Early token release increases the total bandwidth on the ring. All ports, by default, are enabled to use Early Token Release.
To enable or disable the early token release feature on a Token Ring module ports, issue the following command in privileged mode:
After entering the set tokenring etr command, you see a display similar to the following:
Note Early Token Release is valid for 16 Mbps media only. If the Early Token Release is enabled and the media speed is 4 Mbps, the switch will force Early Token Release to be disabled.
Using the set tokenring actbits command, you can specify if and how the AC bits should be set on LLC frames. When local address learning is enabled on a Token Ring port, the default is disable. When local address learning is disabled on a Token Ring port, the default is always.
For information on setting AC bits and enabling and disabling local address learning, see the "Handling Frames Transmitted with Invalid Source MAC Addresses" section.
To set the AC bits for a port, issue the following command in privileged mode:
After entering the set tokenring acbits command, you see a display similar to the following:
Configuration loss occurs when a port completes a connection, allows data traffic to flow, and subsequently closes. The configuration loss threshold is used to control the number of configuration losses that can occur within a specified time. When the threshold is exceeded, the port is disabled and must be enabled using the set port enable command or an SNMP manager. The valid range for the configuration loss threshold is 1 through 100. The default is 8.
To set and verify the configuration loss threshold for a port, issue the following command in privileged mode:
After entering the set tokenring configloss command, you see a display similar to the following:
Note To view reason codes and a counter of the current number of configuration loss events, issue the show tokenring command. For a complete description of the show tokenring command and its parameters, see the "Catalyst 5000 Series Fiber Token Ring Module Command Reference" section.
After configuring the Token Ring ports, you can verify the configuration using the following commands:
Note You can verify the ports individually, or as a group. To view the configuration parameters for a specific port, specify the module number and port number.
After entering the show port command and specifying the module and port number, you see a display similar to the following:
Table 3 describes the information returned by the show port command.s
Note For a complete description of the fields displayed if you issue the show port command without specifying a module and port number, see the Catalyst 5000 Series Command Reference.
After entering the show tokenring command and specifying a module and port number, you see a display similar to the following:
Table 3 describes the information returned by the show tokenring command issued with a module and port number specified.
Check the following items to help isolate the possible causes for a port to be in a faulty state.
A speed error occurs if there has been a mismatch of speeds between the switch ports and attached devices (for example, if you have set the port speed to 4 Mbps and the ring is 16 Mbps).
To determine if a speed error has occurred, verify that the speed set for the port, attached devices, and the ring are the same.
Remove station MAC frames are issued by a configuration report server (CRS) running on a LAN management program and are sent to a port to instruct a ring station to remove itself from the ring.
As explained in the "ARE Reduction" section, for parallel SRB or SRT backbones, ARE reduction ensures that the number of ARE frames generated by the switch does not overwhelm the network. Using the set tokenring reduction command, you can enable and disable ARE reduction.
ARE reduction ensures that only one ARE frame is received on each ring within each VLAN (TrBRF and TrCRF). The number of ARE frames is equal to the number of external parallel paths between the rings.
To enable ARE reduction, issue the following command in privileged mode:
To disable ARE reduction, issue the following command in privileged mode:
A VLAN is a logical group of LAN segments, independent of physical location, with a common set of requirements. For example, several end stations might be grouped as a department, such as engineering or accounting. If the end stations are located close to one another, they can be grouped into a LAN segment. If any of the end stations are on a different LAN segment, such as different buildings or locations, they can be grouped into a VLAN that has all the same attributes as a LAN even though the end stations are not all on the same LAN segment. The information identifying a packet as part of a specific VLAN is preserved across a Catalyst 5000 series switch connection to a router or another switch if connected via trunk ports (for example, ISL).
Any VLAN can participate in the STP. Once VLANs have been established, packets are forwarded between ports belonging to the same VLAN only, unless the VLANs are joined by the bridging function to other VLANs. You can partition the ports on a single Catalyst 5000 series fiber Token Ring module into multiple Token Ring VLANs.
Before configuring VLANs, ensure that a VTP management domain exists. For information on configuring management domains and VLANs, Catalyst 5000 Series Advanced Software Configuration Guide.
Within a Token Ring VLAN, logical rings can be formed by defining groups of ports that have the same ring number. In general, a TrCRF is limited to the ports in a Catalyst 5000 series switch. However, there is one exception to this rule, which is discussed in the "Adding or Changing TrCRF Parameters" section. Within the TrCRF, source-route switching is used for forwarding based on either MAC addresses or route descriptors. Frames can be switched between ports within a single TrCRF.
Multiple TrCRFs can be interconnected using a single TrBRF. The connection between the TrCRF and the TrBRF is referred to as a logical port. For source routing, the switch appears as a single bridge between the logical rings. The TrBRF can function as an SRB or SRT bridge running either the IBM or IEEE STP. If SRB is used, duplicate MAC addresses can be defined on different logical rings.
Traditionally, one instance of STP is run for each VLAN to prevent loops in the bridge topology, however, Token Ring runs an instance of STP both at the TrCRF level and the TrBRF level. The STP running at the TrCRF level removes loops in the logical ring. The TrBRF STP functions similar to the Ethernet STP, interacting with external bridges to remove loops from the bridge topology.
For more information about Token Ring VLANs, see the "Token Ring VLANs" section.
Using the set vlan command, you can configure a new TrBRF or change an existing TrBRF.
When configuring a TrBRF, keep the following in mind:
For more information about these configurations and information on manually setting the state of the logical ports of a TrBRF, see the "Setting the Port State" section.
When configuring larger MTUs for the ports or TrBRFs on a Token Ring module, be aware of the following:
If you reduce the MTU for a TrBRF to a value that is less than the MTU currently configured for the individual ports or LAN emulation clients (LECs) in the TrBRF, the MTU for the ports or LECs is automatically reduced to a value (1500, 4472, 8144, or 17800) that is less than that specified for the TrBRF.
To configure a new TrBRF, issue the following version of the set vlan command in privileged mode:
After entering the set vlan command, you see a display similar to the following:
To change an existing TrBRF, issue the following command in privileged mode, changing the appropriate parameters as necessary:
Using the set vlan command, you can configure a new TrCRF or change an existing TrCRF. There are three types of TrCRFs that you can configure in your network: undistributed, distributed, and backup.
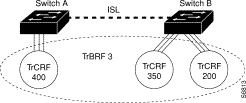
The undistributed TrCRF is the standard type of TrCRF in the Catalyst 5000 series switch. The undistributed TrCRF is located on one switch and has a logical ring number associated with it. Multiple undistributed TrCRFs located on the same or separate switches can be associated with a single parent TrBRF. The parent TrBRF acts as a multiport bridge, forwarding traffic between the undistributed TrCRFs. Figure 8 illustrates the undistributed TrCRF.
A distributed TrCRF contains ports on different switches as illustrated in Figure 9. By default, the Token Ring VLAN configuration of the Token Ring module has all ports assigned to the default TrCRF (1003). The default TrCRF is associated with the default TrBRF (1005). In the situation where a user has not configured the ports of a Token Ring module to be associated with a new TrCRF, traffic will be passed between the default TrCRFs located on separate switches that are connected via ISL.
Before you can configure a distributed TrCRF, you must enable the ability to do so using the set tokenring distrib-crf command. For information on the set tokenring distrib-crf command, see the "Enabling the Ability to Configure a Distributed TrCRF" section.
Note To pass data between rings located on separate switches, you can associate the rings to the same TrBRF and configure the TrBRF for SRB.
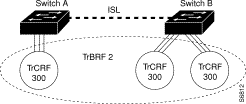
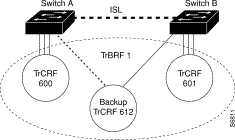
The backup TrCRF enables you to configure an alternate route for traffic between undistributed TrCRFs located on separate switches that are connected by a TrBRF, should the ISL connection between the switches become inactive. Only one port per switch can be configured as part of a backup TrCRF and only one backup TrCRF can be configured for a TrBRF.
To create a backup TrCRF, you assign one port on each switch that the TrBRF traverses to the backup TrCRF. Under normal circumstances, only one port in the backup TrCRF is active. If the ISL connection between the switches become inactive, the port that is a part of the backup TrCRF on each affected switch will automatically become active, rerouting traffic between the undistributed TrCRFs through the backup TrCRF. When the ISL connection is reestablished, all but one port in the backup TrCRF will once again be disabled. Figure 10 illustrates the backup TrCRF.
When configuring a TrCRF, keep the following in mind:
For more information about these configurations and information on manually setting the state of the logical ports of a TrBRF, see the "Setting the Port State" section.
To configure a new TrCRF, issue the following version of the set vlan command in privileged mode, ensuring that you specify each of the parameters that applies to the type of TrCRF you are configuring:
After entering the set vlan command, you see a display similar to the following:
To change an existing TrCRF, issue the following command in privileged mode, changing the appropriate parameters as necessary:
To specify that a TrCRF is a backup TrCRF, issued the following command in privileged mode:
After entering the set vlan command and specifying on for the backupcrf parameter, you see a display similar to the following:
A distributed TrCRF is TrCRF in which ports associated with the TrCRF are located on different Catalyst 5000 series switches. Before you can configure a distributed TrCRF using the set vlan command, you must enable the ability to do so.
To enable or disable the capability to distribute a TrCRF, issue the following command while in privileged mode:
After enabling the distribution of TrCRFs using the set tokenring distrib-crf command, you see a display similar to the following:
You can specify the maximum hop count for ARE and spanning-tree explorer frames for each TrCRF. This limits the maximum number of hops an explorer is allowed to traverse. If a port determines that the explorer frame it is receiving has traversed more than the number of hops specified, it does not forward the frame. The TrCRF determines the number of hops an explorer has traversed based on the number of bridge hops in the route information field.
If you are configuring maximum hop counts for a TrCRF, ensure that you specify values for the aremaxhop and stemaxhop parameters when issuing the set vlan command. Valid values are 1 to 14. The default is 7.
To specify the maximum number of bridge hops to be allowed in explorer packets for a TrCRF, issue the following command in privileged mode:
After entering the set vlan command and specifying hopcount values, you see a display similar to the following:
A TrCRF created in a management domain remains unused until it is associated with ports on the Catalyst 5000 series fiber Token Ring module.
To group Token Ring module ports into a TrCRF, issue the following command in privileged mode:
Note The port numbers can be entered asa range or as individual ports. Entries are separated by a comma. For example, you could enter 1/1,2/1-12,3/1-2,4/1-12.
After entering the set vlan command to group ports to a TrCRF, you see a display similar to the following:
To verify the Token Ring VLANs you have configured, issue the following command:
After entering the show vlan command and specifying a TrBRF, you see a display similar to the following:
After entering the show vlan command and specifying a TrCRF, you see a display similar to the following:
Table 4 describes the information returned by the show vlan command.
To clear the definition of a TrCRF or TrBRF, issue the following command while is privileged mode:
After entering the clear vlan command and specifying a TrCRF, you will be notified that the command will deactivate the ports on the VLAN and be prompted to continue as seen in the following display:
After entering the clear vlan command and specifying a TrBRF, you will see a display similar to the following:
Note You cannot delete a TrBRF without first reassigning or clearing the TrCRFs to which it is a parent.
When creating fault-tolerant internetworks, a loop-free path must exist between all nodes in a network. The algorithm performed by a STP calculates the best loop-free path throughout a switched network. Spanning-tree packets are sent and received by switches in the network at regular intervals.
The packets are not forwarded by the switches participating in the STP, but are instead used by the switches to identify the loop-free path. STP performs this function for Catalyst 5000 series switches.
Traditionally, one instance of STP is run for each VLAN to prevent loops in the bridge topology, however, Token Ring runs an instance of STP both at the TrCRF level and the TrBRF level. The STP running at the TrCRF level removes loops in the logical ring. The TrBRF STP functions similar to the Ethernet STP, interacting with external bridges to remove loops from the bridge topology.
The Catalyst 5000 series fiber Token Ring module supports the following STPs:
The Catalyst 5000 series switch uses the IEEE 802.1D and IBM STPs on TrBRFs. The STP running on the TrCRF is either the Cisco or IEEE STP, depending on the bridging mode configured for the TrCRF using the set vlan command. By default, the spanning-tree support is enabled.
For more information on the STP activity at the TrBRF and TrCRF levels depending upon the TrBRF STP and the TrCRF bridge mode configuration, see the "STP" section.
By default, STP is enabled for VLANs. However, if necessary, you can manually enable and disable the STP support for individual TrBRFs and TrCRFs.
Note If you disable STP participation for a TrBRF, then all TrCRFs with this TrBRF as a parent will be set to forwarding state.
To enable STP, issue the following command in privileged mode:
After enabling STP for a VLAN, you see a display similar to the following:
To disable STP for a VLAN, enter the set spantree disable command:
After disabling STP for a VLAN, you see a display similar to the following:
You can configure the type of STP to be used by a TrBRF.
Note that the following STP and bridge mode configurations are incompatible and result in logical ports being placed in a blocked state:
For more information on these configurations and how to manually set the logical port state, see the "Setting the Port State" section.
To specifying a STP for a TrBRF, issue the following command in privileged mode:
After entering the set vlan command and specifying a STP, you see a display similar to the following:
Using the set spantree command, you can specify for a TrBRF to use the IBM bridge functional address or the IEEE STP address.
To specify for a TrBRF running the IEEE STP to use the IBM bridge functional address instead of the IEEE STP address, issue the following command in privileged mode:
Each logical port (the connection between the TrBRF and TrCRF) of a TrBRF on a switch using STP exists in one of the following five states:
The port states occur as follows:
When STP is enabled, every switch in the network goes through the blocking state and the transitory states at power up. If properly configured, the logical ports then stabilize to the forwarding or blocking state. However, with TrBRFs and TrCRFs, there are two exceptions to this rule that require you to manually set the state of a logical port of a TrBRF. The two exceptions are if the:
Note When the above configurations occur, the logical ports are put in a blocked state and no STP is run.
You can use the set spantree portstate command to manually set the state of a logical port to blocked or forwarding mode if either of the above configurations exists.
To manually set the state of a logical port of a TrBRF, issue the following command in privileged mode:
After entering the set spantree portstate command, you see a display similar to the following:
Note If you disable the STP state for a TrBRF using the set spantree command, the logical ports of the TrBRF will be put in forwarding state regardless of the state you configured using the set spantree portstate command.
The port (physical or logical) with the lowest priority value has the highest priority and will forward the spanning-tree frames. For physical ports, the possible priority range is 0 through 255 (decimal). The default is 128. For logical ports, the possible priority range is 0 through 7. The default is 4. If all ports have the same priority value, the lowest port number forwards the spanning-tree frames.
To configure the priority associated with a logical port, issue the following command in privileged mode:
After entering the set spantree portpri command, you see a display similar to the following:
To configure the priority associated with a physical port, issue the following command in privileged mode:
After entering the set spantree portpri command, you see a display similar to the following:
The STP uses port path costs to determine which port (physical or logical) to select as a forwarding port. Therefore, lower numbers should be assigned to ports attached to faster media (such as full duplex), and higher numbers should be assigned to ports attached to slower media.The possible range is 1 to 65535. The default is 62. A rule of thumb for path cost is 1000 ÷ LAN speed in megabits per second.
To configure the cost associated with a physical port, issue the following command in privileged mode:
To configure the cost associated with a logical port, issue the following command in privileged mode:
After entering the set spantree portcost command and specifying a module number and port number, you see a display similar to the following:
You can configure additional STP parameters using the set spantree command. Table 5 lists the types of spanning tree information you can configure and the command you use.
| Task | Command |
Configure a physical port that is connected to a single workstation or PC to start faster when it is connected. |
Note For a complete description of the set spantree commands that differ for the Token Ring module from those described in the Catalyst 5000 Series Command Reference, see the "Catalyst 5000 Series Fiber Token Ring Module Command Reference" section of the configuration note.
You can display the STP configuration for a specific VLAN, switching module, or port.
To verify the STP configuration information for a TrBRF or TrCRF, issue the following command:
After entering the show spantree command, you will see a display similar to the following:
Table 6 describes the information returned by the show spantree command.
The Catalyst 5000 series Token Ring module software Release 3.3(1) and later performs error detection and isolation by monitoring the Report Soft Error MAC frames generated by stations on each port. Soft errors occur during normal ring operation and do not typically disrupt traffic on the ring. However, soft errors can occur at a rate that could potentially degrade the performance of the ring.
Using the set station softerror command, you can enable or disable soft error monitoring on a Token Ring port and you can configure soft error thresholds and sampling intervals for a port. During the interval you define, the Catalyst 5000 series Token Ring module monitors the stations on the port and, if the threshold is exceeded, can be configured to generate a trap indicating the port number and station on which the threshold was exceeded. If necessary, you can issue a Remove Ring Station MAC frame to remove the station from the ring.
To enable or disable soft error monitoring on a Token Ring port, issue the following command in privileged mode:
Note To enable soft error monitoring on all the ports of the Token Ring module, issue the set station softerror command and specify the module number of the Token Ring module.
After enabling soft error monitoring on a port using the set station softerror command, you see a display similar to the following:
To configure a soft error monitoring error threshold (the number of soft errors reported from a station connected to a port that if exceeded causes a soft error exceeded trap to be issued) and to define a sampling interval (the period, in seconds, during which the number of soft errors is monitored for each station connected to this port) issue the following command while in privileged mode:
The possible values for the error threshold are 1 to 255. The default is 100. The possible values for the sampling interval are 0 to 65534. The default is 60. Setting the interval to zero disables the soft error exceeded traps. Without these traps, soft errors can still be monitored via the console.
Note To set the error threshold and sampling interval for all the ports of the Token Ring module, issue the set station softerror command and specify the module number of the Token Ring module.
After configuring the error threshold and sampling interval using the set station softerror command, you will see a display similar to the following:
To verify your soft error monitoring configuration on a port, issue the following command while in privilege mode:
Note To view the soft error monitoring configuration for all the ports of the Token Ring module, issue the show station softerror config command and specify the module number of the Token Ring module.
After entering the show station softerror config command to verify the configuration on a port, you will see a display similar to the following:
If a station is exceeding soft error thresholds, you can issue a Remove Ring Station MAC frame to remove the station from the ring. When issuing the clear station command, enter the MAC address in non-canonical format (00:11:22:33:44:55).
To aid in network management, the Catalyst 5000 series Token Ring module allows you to configure a SPAN port for monitoring port traffic. This SPAN support allows you to perform active monitoring on any single Token Ring source port. Active port monitoring allows you to copy the traffic being switched by a source port to a destination port. Only the LLC traffic that is being switched by the source port is monitored when you configure active port monitoring. The MAC frames are not monitored.
When configuring SPAN for a single Token Ring source port keep in mind the following:
To configure a SPAN port, issue the following command in privileged mode, specifying the source port, the destination port, and the direction of traffic that you want to monitor that is being switched on the source port.
After entering the set span command and specifying a source port and destination port, you see a display similar to the following:
After configuring a SPAN port, ensure that SPAN is enabled on the switch. If SPAN is not enabled on the switch, you can enable it using the set span command.
To enable SPAN, issue the following command while in privileged mode:
To disable SPAN, issue the following command while in privileged mode:
To verify the SPAN configuration, issue the following command:
After entering the show span command, you see a display similar to the following:
Table 7 describes the information returned by the show span command.
For network security, you can isolate parts of your network by limiting the scope and access of your users. To limit access, you can define filters that:
There are two types of filters that you can configure for the Catalyst 5000 series fiber Token Ring module: protocol filters and MAC address filters. MAC address filters, based on MAC address (source address or destination address), can be configured for only input ports. Protocol (Destination Service Access Point [DSAP]/Subnetwork Access Protocol [SNAP]), filters can be configured for both input and output ports. You can configure up to 16 MAC address or DSAP/SNAP filters for each port on the Token Ring module.
To filter data based on MAC address, you specify an address and indicate whether you want to block or allow frames that contain the address as a source or destination address. To filter data based on protocol, specify either a DSAP or SNAP and specify whether to permit or deny frames with that protocol.
When configuring a MAC address filter, you can enter the MAC address in canonical or non-canonical format. You can also configure a MAC address filter as both a source or a destination for a specified port. Frames received that contain the MAC address specified as a source or destination address are dropped or passed, depending on whether you have specified for the filter to permit or deny the frames.
To add a filter based on MAC addresses, issue the following command in privileged mode:
After entering the set port filter command, you see a display similar to the following:
Note You can define up to 16 MAC address filters per port to be filtered at the port of entry into the Catalyst 5000 series fiber Token Ring module. MAC addresses can be unicast, multicast (group), or broadcast.
For a list of possible Ethertypes that you can specify, see the "Ethertypes" section. You can specify up to 16 DSAPs (in hexadecimal format) separated by spaces. For a list of possible service access points (SAPs), refer to the "Service Access Points" section.
To add a filter based on protocols, issue the following command in privileged mode:
After entering the set port filter command, you see a display similar to the following:
Note You can define up to 16 protocol filters (eight SAP and eight DSAP classes) per port to be filtered at the port of entry into the Catalyst 5000 series fiber Token Ring module.
Using the clear port filter command, you can clear MAC address or protocol filters that have been configured on a specific port. You can also use the clear port filter command to clear all the filters configured for each of the ports on the Token Ring module.
To clear a MAC address filter, protocol filter, or all configured filters, issue the following command in privileged mode:
After entering the clear port filter command to clear a specific MAC address filter on a port, you see a display similar to the following:
After entering the clear port filter command to clear all configured filters, you see a display similar to the following:
To verify the filters you have configured for the Token Ring module or for a specific port on the module, use the show port filter command.
To verify the filters configured on the ports on module 3, issue the following command:
After entering the show port filter command, you see a display similar to the following:
Table 9 describes the information returned by the show port filter command issued with a module specified.s
Use the following show commands to complete the listed tasks:
Note For a description of the fields displayed in the output of the show commands listed above, see the "Catalyst 5000 Series Fiber Token Ring Module Command Reference" section.
As enhancements are made to the Catalyst 5000 series fiber Token Ring module, you may need to update the software or microcode that is contained in the Catalyst 5000 series fiber Token Ring module.
This section includes procedures for updating the software on the Catalyst 5000 series switch. New software to implement enhancements and maintenance releases will be provided periodically.
Perform the following steps to download software from a console using TFTP:
Step 2 On Sun workstations, make sure the /etc/inetd.conf file contains the following line:
Make sure the /etc/services file contains the following line:
Note You must restart the inetd daemon after modifying the /etc/inetd.conf and /etc/services files. To restart the daemon, either kill the inetd process and restart it, or issue a fastboot command (on the SunOS 4.x) or a reboot command (on Solaris 2.x or SunOS 5.x). Refer to your workstation manual for use of TFTP daemons.
Step 3 Copy the new software from the floppy disks to the home directory specified for the TFTP daemon on the workstation (usually /tftpboot). If this directory does not exist, create it before continuing. The file you copy is epsmain.dot1_0_xxx.bin, where xxx is the software revision number.
Step 4 Log in to the Catalyst 5000 through the administrative interface or through a Telnet session.
Step 5 Use the download command. Specify the IP address or host name of the workstation acting as the download server. Also specify the file to download and the number of the Token Ring module. The following is the command syntax:
download host filename [module num]
In the following example, the file is downloaded to module 3:
Note If no module number is specified, the module to which the file is to be downloaded is automatically determined.
Step 6 When the following prompt appears, press y:
Note The Token Ring module will be automatically reset after the image has been downloaded.
Step 7 Use the show version command to check the file you have just downloaded. If the version number is the correct number for the new software, the download was successful. If the version number is not the correct number, the download failed, and you must repeat the download procedure. Refer to the troubleshooting procedures below if the download failed.
Follow the steps below for troubleshooting a failed serial download procedure:
Step 2 Make certain that the software image to be downloaded is in the correct directory.
Step 3 On the Catalyst 5000 series switch, make sure VTP V2 is enabled and at least one Token Ring port is active.
The network portion of the Catalyst 5000 IP address must be the same as the network portion of the TFTP server address. If the network download procedure fails because the power was interrupted during the download procedure, or for some other reason, the Flash code can become corrupted and the boot> prompt appears on the administration port. In that case, you can use the network download procedure to download the Flash code again through an enabled port in VLAN 1. By default, only port 1/1 is enabled. You can use port 1/1 or enable another port.
This section contains the following information:
Because the number of stations that can be connected to any single ring is limited, large Token Ring LANs are divided into smaller rings. Furthermore, because stations must contend for the token with other stations on the same ring, attaching fewer stations to a ring gives each one a greater number of opportunities to transmit and receive information. This results in a larger number of rings, or segments.
The traditional method of connecting multiple Token Ring segments is to use a source-routing bridge. For example, bridges are often used to link workgroup rings to the backbone ring. However, the introduction of the bridge can significantly reduce performance at the user's workstation. Further problems may be introduced by aggregate traffic loading on the backbone ring.
To maintain performance and avoid overloading the backbone ring, you can locate servers on the same ring as the workgroup that needs to access the server. However, this makes the servers more difficult to back up, administer, and secure than if they are located on the backbone ring, and limits the number of servers that particular stations can access.
Collapsed backbone routers offer greater throughput than bridges, and can interconnect a larger number of rings without becoming overloaded. Routers provide both bridging and routing function between ring and have sophisticated broadcast control mechanisms. These mechanisms become increasingly important as the number of devices on the network increase.
The main drawback of using routers as the campus backbone is the relatively high price-per-port and the fact that the throughput typically does not increase as ports are added. A Token Ring switch is designed to provide wire speed throughput regardless of the number of ports in the switch. In addition, the switch can be configured to provide very low latency between Token Ring ports by using cut-through switching.
The Catalyst 5000 series fiber Token Ring module supports the following bridging modes:
SRB is the original method of bridging used to connect Token Ring segments. A source-route bridge makes all forwarding decisions based on data in the RIF. It does not learn or look up MAC addresses. Therefore, SRB frames without a RIF are not forwarded.
Clients or servers that support source routing typically send an explorer frame to determine the path to a given destination. There are two types of explorer frames: ARE and spanning-tree explorer. All SRB bridges copy ARE frames and add their own routing information. For frames that are received from or sent to ports that are in the spanning-tree forwarding state, bridges copy spanning-tree explorer frames and add their own routing information. Because ARE frames will traverse all paths between two devices, they are used in path determination. Spanning-tree explorer frames are used to send datagrams because the spanning tree will ensure that only one copy of an spanning-tree explorer frame is sent to each ring.
Note The spanning tree used with source-routing is different from the IEEE spanning tree used in transparent bridges. The Catalyst 5000 series fiber Token Ring module supports both types of spanning-tree algorithms.
SRT bridging is an IEEE standard that combines source-route bridging and transparent bridging. An SRT bridge forwards frames that do not contain a RIF based on the destination MAC address. Frames that contain a RIF are forwarded based upon source-routing. The SRT bridge only runs the IEEE STP. It does not support the IBM STP.
Similar to a transparent bridge, the Catalyst 5000 series fiber Token Ring module can forward broadcast, multicast, and unicast frames based on MAC address. If, however, you have source-route bridges in your network, the Token Ring module can forward frames based on the RIF. This dual frame-forwarding technology is called source-route switching.
In source-route switching, the switch learns and forwards frames based on source-route descriptors for stations that are one or more source-route bridge hops away. A route descriptor is a portion of a RIF that indicates a single hop. It is defined as a ring number and a bridge number. When a source-routed frame enters the switch, the switch learns the route descriptor for the hop closest to the switch. Frames received from other ports with the same next-hop route descriptor as their destination will be forwarded to that port.
The key difference between SRB and source-route switching is that while a source-route switch looks at the RIF, it never updates the RIF. Therefore, all ports in a source-route switch group have the same ring number.
Source-route switching provides the following benefits:
Classic 4- and 16-Mbps Token Ring adapters must be connected to a port on a concentrator. These adapters are also limited to operating in half-duplex mode. In half-duplex mode, the adapter can only be sending or receiving a frame; it cannot do both simultaneously.
Dedicated Token Ring, developed by the IEEE, defines a method in which the switch port can emulate a concentrator port, thereby eliminating the need for an intermediate concentrator. In addition, dedicated Token Ring defines a new full-duplex data passing mode called Transmit Immediate, which eliminates the need for a token and allows the adapter to transmit and receive simultaneously.
Dedicated Token Ring is particularly useful for providing improved access to servers. A server can be attached directly to a switch. This allows the server to take advantage of the full 16 Mbps available for sending and receiving and results in an aggregate bandwidth of 32 Mbps.
Within a Token Ring VLAN, logical rings can be formed by defining groups of ports that have the same ring number. The IEEE calls such a port group a Token Ring Concentrator Relay Function (TrCRF). In general, a TrCRF is limited to the ports in a single Token Ring module on the Catalyst 5000 series switch. However, there is one exception to this rule that is discussed in the "Adding or Changing TrCRF Parameters" section of this configuration note.
Within the TrCRF, source-route switching is used for forwarding based on either MAC addresses or route descriptors. If desired, the entire VLAN can operate as a single ring. Frames can be switched between ports within a single TrCRF.
As shown in Figure 11, multiple TrCRFs can be interconnected using a single Token Ring Bridge Relay Function (TrBRF). For source routing, the switch appears as a single bridge between the logical rings. The TrBRF can function as an SRB or SRT bridge running either the IBM or IEEE STP. If SRB is used, duplicate MAC addresses can be defined on different logical rings.
To accommodate SNA traffic, you can use a combination of SRT and SRB modes. In a mixed mode the TrBRF considers some ports (logical ports connected to TrCRFs) to be operating in SRB mode while others are operating in SRT mode.
The TrBRF can be extended across a network of switches via high-speed uplinks between the switches. These links must have the ability to multiplex multiple VLANs and provide the necessary information to support logical rings.
The STP is a broadcast algorithm used by network bridge connections to dynamically discover a loop-free subset of the network topology while maintaining a path between every pair of LANs or VLANs in the network.
To accomplish this, the STP blocks ports that, if active, would create bridging loops. If the primary link fails, it activates one of the blocked bridge ports to provide a new path through the network.
In a traditional bridged network, there is one STP for each bridge connection. Each bridge maintains its own database of configuration information and transmits and receives only on those ports belonging to the bridge. The type of STP that runs on a bridge depends on the transmission mode of the bridge connection (whether the connection is transparent, SRB, source-source route switched, or SRT).
In a switched network, you can configure virtual networks. A switch can have ports that belong to different VLANs, some of which may span several switches.
As discussed in the "VLAN Support" section, in a Token Ring switch, there are two levels of VLANs. The grouping of ports (TrCRFs) is connected by logical bridges (TrBRFs).
Therefore, in a Token Ring switched network, to ensure loops are removed from the topology you must configure a separate STP for each logical bridge (TrBRF) and for each of the port groupings (TrCRF) configured for a VLAN.
The following is a general summary of how the STP eliminates loops in the network:
1. Each bridge is assigned an 8-byte unique bridge identifier.
The first 2 bytes are a priority field, and the last 6 bytes contain one of the bridge's MAC addresses. The bridge with the lowest bridge identifier among all bridges on all LAN segments is the root bridge. The network administrator can assign a lower bridge priority to a selected bridge to control which bridge becomes the root, or the administrator can use default bridge priorities and allow the STP to determine the root.
2. Each bridge port is associated with a path cost.
The path cost represents the cost of transmitting a frame to a bridged segment through that port. A network administrator typically configures a cost for each port based on the speed of link (for example, the cost of a port connected to a 16-Mbps LAN could be assigned a lower path cost than a port connected to a 4-Mbps LAN).
3. Each bridge determines its root port and root path cost.
The root port is the port that represents the shortest path from itself to the root bridge. The root path cost is the total cost to the root.
All ports on the root bridge have a zero cost.
4. All participating bridges elect a designated bridge from among the bridges on that LAN segment.
A designated bridge is the bridge on each LAN segment that provides the minimum root path cost. Only the designated bridge is allowed to forward frames to and from that LAN segment toward the root.
5. All participating bridges select ports for inclusion in the spanning tree.
The selected ports will be the root port plus the designated ports for the designated bridge. Designated ports are those where the designated bridge has the best path to reach the root. In cases where two or more bridges have the same root path cost, the bridge with the lowest bridge identifier becomes the designated bridge.
6. Using the preceding steps, all but one of the bridges directly connected to each LAN segment are eliminated, thereby removing all multiple LAN loops.
The STP calculation requires that bridges communicate with other bridges in the network that are running the STP. Each bridge is responsible for sending and receiving configuration messages called bridge protocol data units (BPDUs).
BPDUs are exchanged between neighboring bridges at regular intervals (typically 1 to 4 seconds) and contain configuration information that identifies the:
If a bridge fails and stops sending BPDUs, the bridges detect the lack of configuration messages and initiate a spanning-tree recalculation.
Figure 12 shows the format of the fields inside a BPDU.
Note All fields in the BPDU are common to all STPs except for the Port ID field. If the BPDU is an IEEE or Cisco STP BPDU message, the Port ID field specifies the transmitting port number of the originating bridge. If the BPDU is an IBM STP BPDU message, then the Port ID field specifies the ring and bridge number through which the message was sent.
| 2 | 1 | 1 | 1 | 8 | 4 | 8 | 2 | 2 | 2 | 2 | 2 |
|---|---|---|---|---|---|---|---|---|---|---|---|
The Catalyst 5000 series fiber Token Ring module supports the following STPs:
The Catalyst 5000 series switch uses the IEEE 802.1D and IBM STPs on TrBRFs. The STP running on the TrCRF is either the Cisco or IEEE STP, depending upon the STP being run on the TrBRF and the bridging mode configured for the TrCRF using the set vlan command. The default configuration has all STPs enabled.
Table 11 lists the STP activity at the TrBRF and TrCRF levels depending upon the TrBRF STP and the TrCRF bridge mode configuration.
| TrBRF STP Setting | TrCRF Bridge Mode / ISL Port Setting | TrBRF STP | TrCRF STPF |
|---|---|---|---|
None1 |
| 1Logical ports of the TrBRF may be set to forwarding state using the set spantree portstate command. |
TrBRF and TrCRF STPs
The following sections briefly describe the type of transmission mode supported by each STP.
The IEEE STP can be used at the TrCRF or the TrBRF level. This type of spanning tree supports bridge domains and allows the bridge to construct a loop-free topology across an extended LAN. Specifically, the IEEE 802.1d STP supports the following bridge modes:
The IEEE 802.1d STP BPDU format is:
When a bridge connection is transparent mode:
When a bridge connection is source-route switching:
Source-Route Transparent Bridging
When a bridge connection is source-route transparent:
The IBM STP can be used at the TrBRF level. This type of spanning tree was developed to maintain the path for source-route broadcast traffic.
When a bridge connection is source-route:
The Cisco STP was designed for use at the TrCRF level. This type of spanning tree was developed to address a looping problem that can be introduced when you use VLANs in a Token Ring environment.
One of the rules in processing source-route traffic is that a source-route frame should never be forwarded to a ring that it has previously traversed. If the RIF of a source-route frame already contains the ring number for the next hop, the bridge assumes that the frame has already been on that ring and drops the frame.
With Token Ring VLANs, however, this rule can cause a problem. With the existing STP, a frame that originated on one physical ring of a Token Ring VLAN and is processed by an external SRT bridge would not be forwarded to another physical ring of the same Token Ring VLAN. Therefore, the IEEE 802.1d STP was used as a basis to create the Cisco STP. The Cisco STP ensures that traffic from one physical ring of a VLAN is not blocked from the other physical rings that comprise the VLAN.
Table 12 summarizes the activities occurring in the TrCRF and TrBRF when the Cisco STP is run.
Table 12 Cisco STP and Bridging Modes
For the Cisco STP BPDU format, the source address must have the "msp masked" on to indicate the presence of a RIF in the header. The information carried in the RIF for the Cisco STP BPDU is a 2-byte field and must be set to 0x0200.
This section lists and describes commands specific to the Catalyst 5000 series fiber Token Ring module as well as existing Catalyst 5000 series switch commands that have been altered for the Catalyst 5000 series fiber Token Ring module. For a complete description of all the Catalyst 5000 series switch commands and the switch command-line interface, refer to the Catalyst 5000 Series Command Reference.
Use the clear port filter privileged command to clear MAC address or protocol filters, filters configured on a specific port, or to clear all filters that have been configured.
The command has no default setting.
The following example shows clearing a MAC address filter (00:40:0b:01:bc:65) configured on port 2 of module 3:
set port filter
show port filter
Use the clear station privileged command to issue a Remove Ring Station MAC frame to remove a station from the ring.
The command has no default setting.
Issuing the clear station command and specifying the MAC address or ID of a station issues a Remove Station MAC frame to that station and removes the station from the ring. Use this procedure with extreme caution.
The following example shows a station with the MAC address 00:40:0b:01:bc:65 on port 2 of module 3 being removed:
set station softerror
show station softerror config
show station softerror counters
Use the clear station counters privileged command to reset the soft error statistics that display when you issue the show station softerror counters command. You can clear statistics collected for a station on a port, the module, or for a specific port on the module.
The command has no default setting.
The following example shows the soft error statistics collected for stations on port 10 of module 3 being reset:
set station softerror
show station softerror counters
Use the set help normal or privileged command to list the set commands with brief descriptions of their functions.
This command has no arguments or keywords.
This command has no default setting.
In normal mode, the set help command lists the set commands available in normal mode. In privileged mode, the set help command lists the set commands available in privileged mode.
The following example shows how to list the set commands available in normal mode:
The following example shows how to list the set commands available in privileged mode:
disable (Switch Command)
enable (Switch Command)
Use the set port filter privileged command to configure a MAC address filter or a protocol filter for ports on your Token Ring module.
MAC address contained in the packets to be filtered. This address can be entered in canonical format (00-11-33-44-55) or in non-canonical (00:11:22:33:44:55) format. |
|
Protocol type that you want to filter. For a list of the protocol types that you can filter, see the "Codes" section. |
|
Keyword used to specify that the filter can permit packets with the specified MAC address or protocol type. |
|
Keyword used to specify that the filter can deny packets with the specified MAC address or protocol type. |
|
Keyword used to specify to allow any packet with the specified MAC address as the source address. |
|
Keyword used to specify to allow any packet with the specified MAC address as the destination address. |
|
Keyword used to specify to block any packet with the specified MAC address as the source address. |
|
Keyword used to specify to block any packet with the specified MAC address as the destination address. |
|
Keyword used to specify that the Token Ring module is not to learn the specified MAC address as a source address. |
The command has no default setting.
Up to 16 MAC address filters or 16 protocol (eight SAP and eight DSAP) filters can be configured per port on the Token Ring module.
The following example shows configuring a port filter on port 2 MAC address 00:40:0b:01:65) of module 3:
clear port filter
show port filter
Use the set port speed privileged command to configure the speed of a port interface. You can configure the speed of a Fast Ethernet interface and a Token Ring interface.
The default configuration has all Token Ring module ports set to auto.
Token Ring interfaces on the Token Ring module can be configured to either 4 Mbps or 16 Mbps. They can also be set to auto speed detection mode, allowing them to sense and distinguish between 4-Mbps and 16-Mbps port transmission speed. Set at auto speed detection mode, the interfaces automatically configure themselves to operate at the proper speed.
If you change the transmission speed of a port that is open to 4 or 16 Mbps, the port will close and reopen at the new transmission speed. If a port closes and reopens on an existing ring using a transmission speed different from that which the ring is operating, the ring will beacon.
If the ports on the Token Ring module are configured to automatically sense the speed of the ring, the first port inserted on the ring will not set the speed, for it will be unable to detect the speed.
The following example shows how to set ports 3 and 4 on module 3 to 4 Mbps and 16 Mbps:
set port disable
set port enable
set port help
set port name
set port trap
set tokenring portmode
set tokenring priority
show port
Use the set span command to enable or disable SPAN and to set up the switch port and VLAN analyzer for multiple SPAN sessions.
The default has no SPAN configured.
You can configure multiple SPAN sessions to run at the same time. One ingress span session (RX or Both direction) and four egress span sessions (TX direction only) can be configured.
A trunk port can be configured as a source or destination port. If the destination port is a trunk port, the outgoing packets through the SPAN port will carry ISL or 802.1Q VLAN headers.
If SPAN is enabled, and you change the VLAN configuration of the SPAN port (destination), you must disable SPAN before the new configuration will be in effect.
If SPAN is enabled, and you disable a source or destination port, the SPAN function will not work until you enable SPAN on both ports.
You can configure a disabled port to be a source or destination port, but the SPAN function will not work until you enable SPAN on both ports.
If SPAN is enabled for monitoring a particular VLAN, the number of ports being monitored changes when you move a switched port into or out of the specified monitored VLAN.
FDDI port can also be a source port.
Source and destination ports can not be the same port.
After SPAN is enabled, if no parameters were ever set, the first configured SPAN is used as a reference.
You can configure additional SPAN ports which monitor VLANs only. These ports support a source of one or more VLANs and require the destination port to be a trunk-capable port. This port will filter all traffic except traffic from the configured VLAN for that port.
For monitoring inbound traffic, only one ingress session (or both direction) SPAN is allowed regardless of the port-based SPAN. An egress SPAN can coexist with other SPAN sessions.
Use either a dedicated RMON probe (such as the Catalyst 5000 series Network Analysis Module) or a network analyzer to monitor ports.
Use the inpkts keyword with the enable option to allow the SPAN destination port to receive normal incoming traffic in addition to the traffic mirrored from the SPAN source. Use the disable option to prevent the SPAN destination port from receiving normal incoming traffic.
You can specify an RSM port as the SPAN source port. However, you cannot specify an RSM port as the SPAN destination port.
The source and destination ports have to be within the module.
If you are configuring SPAN on the Catalyst 5000 and 2926G series Gigabit EtherChannel switching module, the source and destination ports must be on the same module. This restriction does not apply to the following:
If you are configuring the Gigabit EtherChannel switching module VLAN, only the both argument is allowed, you cannot specify tx or rx.
Catalyst 4000 and 2948G series switches do not support the sc0 keyword.
Catalyst 4000 and 2948G series switches do not permit you to disable multicast on SPAN ports.
The Token Ring port can be a source or destination port. When monitoring the tx direction, only one source port is allowed, and the Token Ring module does not support the inpkts option. A Token Ring port can only monitor another Token Ring port.
If you are running a supervisor engine software release prior to release 4.5(1), configure only a single source port to be monitored. With the supervisor engine software release 4.5(1) and later, a single source port will be the standard Token Ring SPAN configuration.
You cannot monitor a VLAN to which none of the ports belong.
This example shows how to configure SPAN so that the transmit traffic on the source port (3/2) is mirrored to the destination port (3/6), and how to verify SPAN configuration:
Use the set spantree help privileged command to list the available set spantree commands.
This command has no arguments or keywords.
This command has no default setting.
The following example shows how to list the set spantree commands:
Use the set spantree multicast-address command to specify for a TrBRF to use the IBM bridge functional address or the IEEE STP address.
The default configuration has IEEE.
This command applies only to a TrBRF that is running IEEE STP.
The following example shows specifying for the bridge functional address to be used:
Use the set spantree portcost privileged command to set the path cost for a physical port or logical port (the connection between a TrCRF and TrBRF).
The default configuration is as follows:
The STP uses port path costs to determine which port to select as a forwarding port. Therefore, lower numbers should be assigned to ports attached to faster media (such as full duplex) and higher numbers should be assigned to ports attached to slower media. The possible range is 1 to 65535. The default for the Token Ring module ports is 62. The recommended path cost is 1000/LAN speed in Mbps.
The following example shows how to set the port cost for port 4 on module 3 to 100:
Use the set spantree portpri privileged command to set the bridge priority for a spanning-tree port or TrCRF.
The default configuration has all physical Token Ring ports with bridge priority set to 128. Logical ports are set to 4 by default.
The specified bridge priority on an ATM port applies to all emulated LANs on that port.
The following example shows how to set the priority of port 1 on module 4 to 63:
Use the set spantree portstate privileged command to manually set the state of a logical port (the connection between a TrCRF and TrBRF).
There is no default configuration for this command.
This command can only be used to set the port state when the TrCRF is in SRT mode and the TrBRF is running the IBM STP, or, the TrCRF is in SRB mode and the TrBRF is running the IEEE STP.
When STP is enabled, every switch in the network goes through the blocking state and the transitory states at power up. The ports then stabilize to the forwarding or blocking state. With TrBRFs and TrCRFs, there are two exceptions to this rule that require you to manually set the state of the logical ports of a TrBRF. The two exceptions are if:
The following example shows the manual setting of TrCRF 900 to a forwarding state:
Use the set station softerror privileged command to enable or disable the collection of soft error statistics on the ports on a Token Ring module or on a specific port on the module. Also, use the set station softerror command to define error thresholds and sampling intervals for the ports on the Token Ring module or for a specific port on the module.
The default configuration has soft error monitoring disabled. The default error threshold is 100. The default interval is 60.
The following example shows how to enable the collection of soft error statistics for port 10 on module 3:
The following example shows the error threshold and sampling interval for port 10 on module 3 being set:
clear station counters
show station softerror config
show station softerror counters
Use the set tokenring acbits privileged command to specify whether AC bits shall be set unconditionally when a port forwards certain LLC frames.
The default configuration is disable.
Using the set tokenring actbits command, you can specify if and how the AC bits should be set on LLC frames. When local address learning is enabled on a Token Ring port, the default is disable. When local address learning is disabled on a Token Ring port, the default is always.
The following examples show port 4 on module 4 being enabled to unconditionally set the AC bits when forwarding certain LLC frames and then being disabled.
set tokenring locallearning
set tokenring portaging
show tokenring
Use the set tokenring configloss privileged command to specify thresholds that, when exceeded during the user-specified interval, will cause the port to be administratively disabled.
The default threshold configuration is 8. The default interval is 10.
Configuration loss occurs when a port completes a connection, allows data traffic to flow, and subsequently closes. The configuration loss threshold is used to control the number of configuration losses that can occur within a specified time. When the threshold is exceeded, the port is disabled and must be enabled using the set port enable command or an SNMP manager.
The following shows how to set a configuration loss threshold of 25 and an interval of 5 minutes for port 1 on module 4.
Use the set tokenring distrib-crf command to enable or disable the ability to configure a distributed TrCRF.
The default is for the ability to configure a distributed TrCRF to be disabled.
Use extreme caution when configuring a distributed TrCRF in your network. Ensure that no loops are configured in the network before configuring a distributed TrCRF.
The following example shows how to enable the ability to configure a distributed TrCRF:
Use the set tokenring etr privileged command to enable or disable a Token Ring port's use of the Early Token Release procedure when transmitting frames.
For 16 Mbps and auto speed-detection ports, the default configuration is enable Early Token Release.
Early Token Release cannot be enabled for 4 Mbps ports. Enabling or disabling Early Token Release on a port will cause the port to be closed and reopened.
The following example shows how to enable Early Token Release on port 2 on module 3:
The following example shows how to disable Early Token Release on port 2 on module 3:
Use the set tokenring help privileged command to list the Token Ring-specific set commands with brief descriptions of their functions.
This command has no arguments or keywords.
This command has no default setting.
The set tokenring help command lists the Token Ring set commands that are available in privileged mode.
The following example shows how to list the Token Ring set commands that are available in privileged mode:
Use the set tokenring locallearning privileged command to enable or disable local MAC address learning on a Token Ring port.
The default configuration is enable.
We recommend that you use the set tokenring locallearning command only in those rare circumstances in which network communications are disrupted because of invalid frames. This command should be used in conjunction with the set tokenring portaging and set tokenring acbits commands.
The set tokenring locallearning command allows you to enable or disable local MAC address learning on a Token Ring port. The default is for local address learning to be enabled.
When local address learning is enabled, the value of the address recognized (A) bit and the frame copied (C) bit in LLC frames is set by the ports on the Token Ring module based on whether the frame was actually forwarded. However, when local address learning is disabled, the AC bits cannot be set by the ports on the Token Ring module based on whether the frame was forwarded because all frames are forwarded to the Catalyst 5000 series switching backplane.
Therefore, when local address learning is disabled on a Token Ring port, the AC bits must be set based on the type of frame that has been received. When you disable local address learning on a Token Ring port, the default is for the AC bits to always be set on LLC frames, however you can configure how the AC bits are to be set using the set tokenring acbits command.
The following example shows how to disable local MAC address learning port 2 on module 3:
set tokenring acbits
set tokenring portaging
Use the set tokenring portaging privileged command to configure fast port aging on a Token Ring port.
We recommend that you use the set tokenring portaging command only in those rare circumstances in which network communications are disrupted because of invalid frames. This command should be used in conjunction with the set tokenring locallearning and set tokenring acbits commands.
When in a network environment in which a device is sending invalid frames, you can ensure that the Token Ring module port address tables contain correct MAC address entries by rapidly aging out the erroneous entries using the set tokenring portaging command. Rapidly aging out the Token Ring module port address table ensures that the Token Ring module port address tables do not contain invalid entries which might affect the Catalyst 5000 series switch and network communication.
The aging limit you define determines when inactive MAC addresses are removed from a port address table. The aging limit is the time (in seconds) a MAC address remains in the port's address table. Possible values are 0 and 5 through 65535 seconds. The default is 0. Zero indicates the Token Ring module port address table entries are aged out using the CAM aging time for the corresponding VLAN that has been configured using the set cam agingtime command. For more information about the set cam agingtime command, see the Catalyst 5000 Series Command Reference.
To use the fast port aging feature effectively, we recommend that you configure an aging limit of 10.
The following example shows how to specify address aging limits for port 2 on module 3:
set tokenring acbits
set tokenring locallearning
Use the set tokenring portmode privileged command to specify the connection type and access protocol being used by a port.
The default configuration is auto.
The following example shows how to set the port mode to autosensing on port 1 on module 4 and to set port 2 on module 4 to operate as a concentrator port in full-duplex mode:
Use the set tokenring priority privileged command to specify the highest Token Ring frame priority that shall go to the low-priority transmit queue and the minimum Token Ring frame priority that will be used when requesting a token.
The default configuration for threshold is 3. The default configuration for minxmit is 4.
The following example shows how to set the priority threshold and minimum priority levels on port 2 on module 4:
Use the set tokenring reduction privileged command to reduce broadcast storms in an externally looped network.
The default configuration is enabled.
The following example shows how to enable and disable ARE reduction:
Use the set vlan privileged command to group ports into a virtual LAN.
The default configuration has all switched Ethernet ports and Ethernet repeater ports in VLAN 1. The default SAID is 100001 for VLAN 1, 100002 for VLAN 2, 100003 for VLAN 3, and so on. The default type is ethernet. The default mtu is 1500 bytes. The default state is active.
The default TrBRF is 1005 and the default TrCRF is 1003. The default mtu for TrBRFs and TrCRFs is 4472. The default state is active.
Valid MTU values for Token Ring VLANs are 1500, 4472, 8144, or 18190. For Token Ring VLANs, the default is 4472. While a user can enter any value for the MTU value, the value they enter will default to the next lowest valid value. You cannot configure a Token Ring port MTU that is greater than the MTU configured for the TrBRF to which the port belongs.
You cannot set multiple VLANs for ISL ports using this command. The VLAN name can be from 1 to 32 characters in length. If adding a new VLAN, the VLAN number must be within the range 2 to 1001. When modifying a VLAN, the valid range for the VLAN number is 2 to 1005.
In the case of a new Token Ring VLAN, if the parent parameter is not specified for a TrCRF, the default TrBRF (1005) is used.
The following example shows how to set VLAN 850 to include ports 4 through 7 on module 3. Ports 3 through 7 were assigned to TrCRF 1003, therefore, the message reflects the modification of VLAN 1003:
clear vlan
show vlan
Use the show counters privileged command to display hardware counters for a port.
This command has no default setting.
The following example shows how to display the counters for port 1 on module 3:
Table 12 describes the fields shown in the show counters command output when the command has been issued against a Token Ring module port.
Use the show mac normal command to display MAC counters.
This command has no default setting.
The following example shows how to display MAC information for port 4 on module 3:
Table 13 describes the fields in the show mac command output when the command is issued against a Token Ring module and port.
Use the show module normal command to display module status and information.
This command has no default setting.
The following example shows how to display status and information for module 5:
Table 14 describes the fields shown in the show module command output.
Use the show port normal command to display port status and counters.
This command has no default setting.
The following example shows how to display the status and counters for port 10 on module 3:
Table 15 describes the fields shown in the show port command output.
Use the show port filter normal command to view MAC address and protocol filters that have been configured on the ports on your Token Ring module or configured on a specific port on the Token Ring module.
(Optional) Number of the port on the module. If a number is not specified, filters configured on all the ports on the module are shown. |
This command has no default setting.
The following example shows how to display the filters configured for a port on the Token Ring module:
Table 16 describes the fields shown in the show port filter command output.
clear port filter
set port filter
Use the show rif normal command to display RIF information.
This command has no default setting.
The following example shows how to display RIF information for the system and for a VLAN:
Use the show spantree normal command to display spanning-tree information for a VLAN.
This command has no default setting.
The following example shows how to display the spanning tree configuration for VLAN 1005:
Table 17 describes the fields shown in the show spantree command output when issued against a TrBRF.
Use the show spantree portstate normal command to view the STP state of a logical port (the connection between a TrBRF and a TrCRF).
This command has no default setting.
The following example shows how to display the spanning tree configuration for VLAN 1005:
Table 18 describes the fields shown in the show spantree portstate command output.
Use the show station controltable normal command to display a collection of statistics and status information associated with each Token Ring station on the local ring. In addition, this command provides status information for each ring being monitored.
This command has no default setting.
The following example shows how to display a collection of statistics and status information associated with each Token Ring station on Token Ring module 3:
Table 19 describes the fields shown in the show station controltable command output.
show counters
show station ordertable
Use the show station ordertable normal command to display an ordered list of the stations on the monitored rings.
This command has no default setting.
The following example shows how to display an ordered list of the stations on a ring being monitored via the ports on module 3:
Table 20 describes the fields shown in the show station ordertable command output. s
| Field | Description |
Location of the station with respect to other stations on the ring. |
|
show counters
show station controltable
Use the show station softerror config normal command to view the soft error monitoring configuration for a port, module, or for all the Token Ring modules in a switch.
This command has no default setting.
The following example shows how to display the soft error monitoring configuration for module 3:
Table 22 describes the fields shown in the show station softerror config command output.
Table 22 Show station softerror config Command Field Descriptions
Use the show station softerror counters normal command to view the soft error statistics collected for all the stations on a Token Ring port or for a specific station.
This command has no default setting.
The following example shows how to display the soft error statistics collected for:
Table 22 describes the fields shown in the show station softerror counters command output.
Use the show tokenring normal command to display the current values of various Token Ring specific configuration parameters.
This command has no arguments or keywords.
This command has no default setting.
The following example shows how to display the Token Ring settings:
Table 24 describes the fields shown in the show tokenring command output.
Use the show vlan normal command to display VLAN information.
This command has no default setting.
The following example shows how to display information for all VLANs:
Table 25 describes the fields shown in the show vlan command output.
Table 25 Show vlan Command Field Descriptions
This section contains information that can help you troubleshoot problems with a Catalyst 5000 series Token Ring module.
LEDs are located on the fiber Token Ring module and below the left and right corners of each of the Volition VF-45 socket connectors. The module LED indicates the status of the module. The port LEDs indicate the status and activity occurring on a port.
The LED that indicates the status of the module is located on the left side of the front of the module and is labeled Status. A green module LED indicates that the module is operational. It does not, however, indicate the operational status of the individual ports.
Table 26 lists the meanings of the module Status LED.
Table 26 Module LED Description
The port LEDs are located below the left and right corners of each of the Volition VF-45 socket connectors. The port LEDs indicate the status or activity occurring on a specific port.
Table 27 lists the meanings of the fiber Token Ring module INS and ACT port LEDs.
Table 27 Port LED Descriptions
| LED | State | Meaning |
|---|---|---|
Port is inserted into the ring. |
||
Data is being transmitted by the port. |
In the event of a corrupted Flash, a Catalyst 5000 series switch can operate in boot mode. However, when the switch is operating in boot mode, a version 3.1 boot ROM is required for the supervisor module to recognize the Token Ring module.
If the Flash becomes corrupted and the supervisor engine module is running a version 3.1 boot ROM, you can download a new image through a Token Ring module while the switch is in boot mode.
If the Flash becomes corrupted and the supervisor engine module is not running a version 3.1 boot ROM, you can download a new Flash image to the switch while in boot mode via either of the following methods:
If you do need to upgrade your boot ROM, please contact the Cisco TAC.
In some rare circumstances, certain devices (such as a faulty protocol analyzer) might transmit a frame that contains the source MAC address of another device. Because MAC addresses are used by the switch to determine where to forward a frame, an invalid frame (one that contains the source MAC address of another device) can cause the valid frames to be forwarded to the wrong port. If this situation occurs, communication to the device to which the MAC address actually belongs can be disrupted for as long as the invalid address entry is in the Token Ring port address table.
If you are experiencing network communication problems due to a device erroneously sending frames with the source MAC address of another device, you can either choose to rapidly age the entries out of the Token Ring module port address tables using the set tokenring portaging command or you can ensure that the Token Ring module port address tables do not contain erroneous entries by disabling address learning entirely on the Token Ring module using the set tokenring locallearning command.
When in a network environment in which a device is sending invalid frames, you can ensure that the Token Ring module port address tables contain correct MAC address entries by rapidly aging out the erroneous entries using the set tokenring portaging command. Rapidly aging out the Token Ring module port address table ensures that the Token Ring module port address tables do not contain invalid entries that might affect the Catalyst 5000 series switch and network communication.
The aging limit you define determines when inactive MAC addresses are removed from a port address table. The aging limit is the time (in seconds) a MAC address remains in the port's address table. Possible values are 0 and 5 through 65535 seconds. The default is 0. Zero indicates the Token Ring module port address table entries are aged out using the CAM aging time for the corresponding VLAN that has been configured using the set cam agingtime command. For more information about the set cam agingtime command, see the Catalyst 5000 Series Command Reference.
Note To use the fast-port aging feature effectively, we recommend that you configure an aging limit of 10.
To define the address aging limits for a Token Ring port, issue the following command while in privileged mode:
After entering the set tokenring portaging command, you see a display similar to the following:
The set tokenring locallearning command enables you to enable or disable local MAC address learning on a Token Ring port. The default is for local address learning to be enabled.
When local address learning is enabled, the value of the address recognized (A) bit and the frame copied (C) bit in LLC frames is set by the ports on the Token Ring module based on whether the frame was actually forwarded. However, when local address learning is disabled, the AC bits cannot be set by the ports on the Token Ring module based on whether the frame was forwarded because all frames are forwarded to the Catalyst 5000 series switching backplane.
Therefore, when local address learning is disabled on a Token Ring port, the AC bits must be set based on the type of frame that has been received. When you disable local address learning on a Token Ring port, the default is for the AC bits to always be set on LLC frames, however you can configure how the AC bits are to be set using the set tokenring acbits command. For more information on configuring for the setting of AC bits on frames, see the "Setting Address Recognized/Frame Copied Bits" section.
Note When local address learning is disabled on a port, the port aging limits configured using the set tokenring portaging command are not used.
To enable or disable local address learning, issue the following command while in privilege mode:
After disabling local address learning using the set tokenring locallearning command, you see a display similar to the following:
The Catalyst 5000 series fiber Token Ring module comes with a default configuration that allows you to use the switch without modification in many small networks. By default, the module is configured as a single VLAN. All ports are assigned to the default TrCRF (trcrf-default) and the default TrCRF is assigned to the default TrBRF (trbrf-default).
Note The Catalyst 5000 series Token Ring module default VLAN configuration requires VTP V2 to be enabled. For information on enabling and disabling VTP V2, refer to the latest release of the Catalyst 5000 Series Command Reference.
To assist users in understanding how to configure VLANs, this section provides an example of configuring two additional VLANs for a Catalyst 5000 series fiber Token Ring module.
Figure 13 illustrates the initial VLAN configuration of the Catalyst 5000 series fiber Token Ring module. We want to add a new VLAN that includes ports 1 and 2 to for some of our accounting department and another VLAN that includes ports 3 and 4 for some of our marketing department. Our Token Ring module is inserted in slot 3 of our Catalyst 5000.
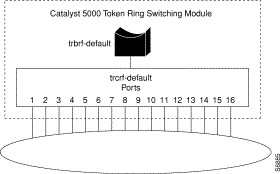
Only the default TrCRF can be assigned to the default TrBRF. You cannot assign new TrCRFs to the default TrBRF. Therefore, we must first define a new TrBRF, then we can define our TrCRFs and assign ports to them.
To define a TrBRF, do the following:
Step 2 At the enable prompt, enter set vlan 100 name brf100a type trbrf bridge 1.
Step 3 To verify the configuration of the new VLAN, enter show vlan.
The output indicates that brf100a has been added but that it does not have any TrCRFs assigned to it yet.
To define the TrCRF for the NetBIOS users, do the following:
Step 2 To verify the configuration of the new VLAN, enter show vlan.
The output indicates that crf110b has been added but that it does not have any ports assigned to it yet. It also shows that brf100a is the parent of the VLAN with the ID of 110.
To define the TrCRF for the IPX users, do the following:
Step 2 To verify the configuration of the new VLAN, enter show vlan.
The output indicates that crf120b has been added but that it does not have any ports assigned to it yet. It also shows that brf100a is the parent of the VLAN with the ID of 120.
To assign the ports to the TrCRFs, do the following:
Step 2 At the enable prompt, enter set vlan 120 3/3-4.
The output shows that ports 1 and 2 on module 3 are assigned to crf110a and that ports 3 and 4 on module 3 are assigned to crf120a.
Figure 14 illustrates the resulting VLAN configuration for the Catalyst 5000 Token Ring module.
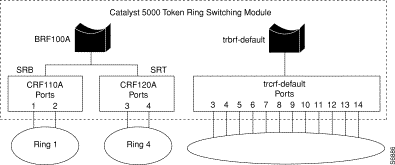
By default, the TrBRF runs the IBM STP. The STP run on the TrCRFs is determined by the specified bridging mode. TrCRFs with a bridge mode of SRB will run the IEEE STP and TrCRFs with a bridge mode of SRT will run the Cisco STP.
The Catalyst 5000 Token Ring module considers the combination of the IBM STP at the TrBRF and the bridge mode of SRT to be incompatible. As a result, it automatically blocks the logical port of the TrCRF that is configured for SRT. You can use the show spantree command to view the state of the logical ports. You can then use the set spantree portstate command to change the forwarding mode of the logical port.
This section includes information about the codes for Service Access Points and Ethertypes that you can use when defining protocol filters. For information on configuring filters, see the "Configuring Filters" section.
Table 28 and Table 29 list the SAPs that may be used in defining protocol classes.
| Hexadecimal Value | Description |
|---|---|
| Hexadecimal Value | Description |
|---|---|
Table 29 lists the possible Ethertypes that you can use in defining protocol filters.
| Hexadecimal Value | Description |
|---|---|
This section repeats in multiple languages the warnings in this guide. These translated warnings can be used with other documents related to this guide.
Waarschuwing Dit waarschuwingssymbool betekent gevaar. U verkeert in een situatie die lichamelijk letsel kan veroorzaken. Voordat u aan enige apparatuur gaat werken, dient u zich bewust te zijn van de bij elektrische schakelingen betrokken risico's en dient u op de hoogte te zijn van standaard maatregelen om ongelukken te voorkomen. Het waarschuwingssymbool betekent ook dat u de waarschuwing in meerdere talen in "Translated Safety Warnings" kunt vinden.
Varoitus Tämä varoitusmerkki merkitsee vaaraa. Olet tilanteessa, joka voi johtaa ruumiinvammaan. Ennen kuin työskentelet minkään laitteiston parissa, ota selvää sähkökytkentöihin liittyvistä vaaroista ja tavanomaisista onnettomuuksien ehkäisykeinoista. Varoitusmerkki tarkoittaa myös sitä, että varoitus esiintyy useilla kielillä osassa "Translated Safety Warnings".
Attention Ce symbole d'avertissement indique un danger. Vous vous trouvez dans une situation pouvant causer des blessures ou des dommages corporels. Avant de travailler sur un équipement, soyez conscient des dangers posés par les circuits électriques et familiarisez-vous avec les procédures couramment utilisées pour éviter les accidents. Le symbole d'avertissement signifie également que cet avis se trouve traduit dans plusieurs langues dans la section «Translated Safety Warnings».
Warnung Dieses Warnsymbol bedeutet Gefahr. Sie befinden sich in einer Situation, die zu einer Körperverletzung führen könnte. Bevor Sie mit der Arbeit an irgendeinem Gerät beginnen, seien Sie sich der mit elektrischen Stromkreisen verbundenen Gefahren und der Standardpraktiken zur Vermeidung von Unfällen bewußt. Das Warnsymbol bedeutet auch, daß Sie die Warnung in verschiedenen Sprachen unter "Translated Safety Warnings" lesen können.
Avvertenza Questo simbolo di avvertenza indica un pericolo. La situazione potrebbe causare infortuni alle persone. Prima di lavorare su qualsiasi apparecchiatura, occorre conoscere i pericoli relativi ai circuiti elettrici ed essere al corrente delle pratiche standard per la prevenzione di incidenti. Il simbolo di avvertenza indica inoltre che l'avvertenza viene presentata in diverse lingue in "Translated Safety Warnings".
Advarsel Dette varselsymbolet betyr fare. Du befinner deg i en situasjon som kan føre til personskade. Før du utfører arbeid på utstyr, må du vare oppmerksom på de faremomentene som elektriske kretser innebærer, samt gjøre deg kjent med vanlig praksis når det gjelder å unngå ulykker. Dette varselsymbolet betyr også at du kan lese advarselen på flere språk i «Translated Safety Warnings».
Aviso Este símbolo de aviso indica perigo. Encontra-se numa situação que lhe poderá causar danos físicos. Antes de começar a trabalhar com qualquer equipamento, familiarize-se com os perigos relacionados com circuitos eléctricos, e com quaisquer práticas comuns que possam prevenir possíveis acidentes. Este símbolo serve também para indicar que poderá ler este tipo de aviso em várias línguas na secção: "Translated Safety Warnings."
¡Atención! Este símbolo de aviso significa peligro. Existe riesgo para su integridad física. Antes de manipular cualquier equipo, considerar los riesgos que entraña la corriente eléctrica y familiarizarse con los procedimientos estándar de prevención de accidentes. Este símbolo de aviso también significa que la misma advertencia aparece en varios idiomas bajo el título "Translated Safety Warnings."
Varning! Denna varningssymbol signalerar fara. Du befinner dig i en situation som kan leda till personskada. Innan du utför arbete på någon utrustning måste du vara medveten om farorna med elkretsar och känna till vanligt förfarande för att förebygga skador. Denna varningssymbol innebär också att du kan se varningsmeddelandet på flera språk i "Translated Safety Warnings."
Waarschuwing Laserstraling wanneer geopend.
Varoitus Lasersäteitä aukkojen ollessa avoinna.
Attention Production d'un rayonnement laser en position ouverte.
Warnung Laserstrahlung in geöffnetem Zustand
Avvertenza Emette radiazioni laser quando è aperto.
Advarsel Laserstråling er til stede når enheten er åpen.
Aviso Radiação laser presente quando aberto.
¡Advertencia! Radiación láser cuando está abierto.
Varning! Rikta inte blicken in mot strålen.
Waarschuwing Niet in de straal staren.
Attention Ne pas fixer le faisceau des yeux.
Warnung Nicht direkt in den Strahl blicken.
Avvertenza Non fissare il raggio con gli occhi.
Advarsel Stirr ikke på strålen.
Aviso Não olhe fixamente para o raio.
¡Advertencia! No mirar fijamente el haz.
Varning! Laserstrålning när enheten är öppen.
Waarschuwing Tijdens onweer dat gepaard gaat met bliksem, dient u niet aan het systeem te werken of kabels aan te sluiten of te ontkoppelen.
Varoitus Älä työskentele järjestelmän parissa äläkä yhdistä tai irrota kaapeleita ukkosilmalla.
Attention Ne pas travailler sur le système ni brancher ou débrancher les câbles pendant un orage.
Warnung Arbeiten Sie nicht am System und schließen Sie keine Kabel an bzw. trennen Sie keine ab, wenn es gewittert.
Avvertenza Non lavorare sul sistema o collegare oppure scollegare i cavi durante un temporale con fulmini.
Advarsel Utfør aldri arbeid på systemet, eller koble kabler til eller fra systemet når det tordner eller lyner.
Aviso Não trabalhe no sistema ou ligue e desligue cabos durante períodos de mau tempo (trovoada).
¡Atención! No operar el sistema ni conectar o desconectar cables durante el transcurso de descargas eléctricas en la atmósfera.
Varning! Vid åska skall du aldrig utföra arbete på systemet eller ansluta eller koppla loss kablar.
Waarschuwing U dient de voeding niet aan te raken zolang het netsnoer aangesloten is. Bij systemen met een stroomschakelaar zijn er lijnspanningen aanwezig in de voeding, zelfs wanneer de stroomschakelaar uitgeschakeld is en het netsnoer aangesloten is. Bij systemen zonder een stroomschakelaar zijn er lijnspanningen aanwezig in de voeding wanneer het netsnoer aangesloten is.
Varoitus Älä kosketa virtalähdettä virtajohdon ollessa kytkettynä. Virrankatkaisimella varustetuissa järjestelmissä on virtalähteen sisällä jäljellä verkkojännite, vaikka virrankatkaisin on katkaistu-asennossa virtajohdon ollessa kytkettynä. Järjestelmissä, joissa ei ole virrankatkaisinta, on virtalähteen sisällä verkkojännite, kun virtajohto on kytkettynä.
Attention Ne pas toucher le bloc d'alimentation quand le cordon d'alimentation est branché. Avec les systèmes munis d'un commutateur marche-arrêt, des tensions de ligne sont présentes dans l'alimentation quand le cordon est branché, même si le commutateur est à l'arrêt. Avec les systèmes sans commutateur marche-arrêt, l'alimentation est sous tension quand le cordon d'alimentation est branché.
Warnung Berühren Sie das Netzgerät nicht, wenn das Netzkabel angeschlossen ist. Bei Systemen mit Netzschalter liegen Leitungsspannungen im Netzgerät vor, wenn das Netzkabel angeschlossen ist, auch wenn das System ausgeschaltet ist. Bei Systemen ohne Netzschalter liegen Leitungsspannungen im Netzgerät vor, wenn das Netzkabel angeschlossen ist.
Avvertenza Non toccare l'alimentatore se il cavo dell'alimentazione ècollegato. Per i sistemi con un interruttore di alimentazione, tensioni di linea sono presenti all'interno dell'alimentatore anche quando l'interruttore di alimentazione è en posizione di disattivazione (off), se il cavo dell'alimentazione è collegato. Per i sistemi senza un interruttore, tensioni di linea sono presenti all'interno dell'alimentatore quando il cavo di alimentazione è collegato.
Advarsel Berør ikke strømforsyningsenheten når strømledningen er tilkoblet. I systemer som har en strømbryter, er det spenning i strømforsyningsenheten selv om strømbryteren er slått av og strømledningen er tilkoblet. Når det gjelder systemer uten en strømbryter, er det spenning i strømforsyningsenheten når strømledingen er tilkoblet.
Aviso Não toque na unidade abastecedora de energia quando o cabo de alimentação estiver ligado. Em sistemas com interruptor, a corrente eléctrica estará presente na unidade abatecedora, sempre que o cabo de alimentação de energia estiver ligado, mesmo quando o interruptor se encontrar desligado. Para sistemas sem interruptor, a tensão eléctrica dentro da unidade abatecedora só estará presente quando o cabo de alimentação estiver ligado.
¡Atención! No tocar la fuente de alimentación mientras el cable esté enchufado. En sistemas con interruptor de alimentación, hay voltajes de línea dentro de la fuente, incluso cuando el interruptor esté en Apagado (OFF) y el cable de alimentación enchufado. En sistemas sin interruptor de alimentación, hay voltajes de línea en la fuente cuando el cable está enchufado.
Varning! Vidrör inte strömförsörjningsenheten när nätsladden är ansluten. För system med strömbrytare finns det nätspänning i strömförsörjningsenheten även när strömmen har slagits av men nätsladden är ansluten. För system utan strömbrytare finns det nätspänning i strömförsörjningsenheten när nätsladden är ansluten.
Waarschuwing Installatie en reparaties mogen uitsluitend door getraind en bevoegd personeel uitgevoerd worden.
Varoitus Ainoastaan koulutettu ja pätevä henkilökunta saa asentaa tai vaihtaa tämän laitteen.
Avertissement Tout installation ou remplacement de l'appareil doit être réalisé par du personnel qualifié et compétent.
Achtung Gerät nur von geschultem, qualifiziertem Personal installieren oder auswechseln lassen.
Avvertenza Solo personale addestrato e qualificato deve essere autorizzato ad installare o sostituire questo apparecchio.
Advarsel Kun kvalifisert personell med riktig opplæring bør montere eller bytte ut dette utstyret.
Aviso Este equipamento deverá ser instalado ou substituído apenas por pessoal devidamente treinado e qualificado.
¡Atención! Estos equipos deben ser instalados y reemplazados exclusivamente por personal técnico adecuadamente preparado y capacitado.
Varning Denna utrustning ska endast installeras och bytas ut av utbildad och kvalificerad personal..
Waarschuwing Metalen voorwerpen worden heet als ze met een voedingsbron en aarde verbonden zijn; in deze gevallen kunnen dergelijke voorwerpen ernstige brandwonden veroorzaken.
Varoitus Virtalähteeseen yhdistetyt ja maadoitetut metalliesineet kuumentuvat ja voivat aiheuttaa vakavia palovammoja.Seuraavassa on vielä yksi lauseen n:o 22 (SELV-piiriä koskeva varoitus) muunnos:
Avertissement Les objets métalliques s'échauffent lorsqu'ils sont sous tension et connectés à la terre. Ils risquent alors de provoquer de graves brûlures.
Achtung Metallteile erwärmen sich, wenn sie an Strom und Erde angeschlossen werden, und können schwere Verbrennungen verursachen.
Avvertenza Gli oggetti metallici collegati alle fasi e alla terra raggiungono temperature elevate e possono causare ustioni gravi.
Advarsel Metallgjenstander blir varme når de kobles til strøm og jord, og kan forårsake alvorlige brannskader.
Aviso Os objectos de metal aquecem quando ligados à corrente e à terra, e poderão causar queimaduras graves.
¡Atención! Los objetos de metal se calientan al estar conectados entre alimentación y tierra, con lo que pueden producir quemaduras graves.
Varning Metallföremål värms upp när de ansluts till spänning och jord och kan orsaka allvarliga brännskador.
Waarschuwing Voordat u aan een systeem werkt dat geen aan/uit schakelaar heeft, dient u de stekker van het netsnoer uit het stopcontact te halen.
Varoitus Ennen kuin teet mitään sellaiselle järjestelmälle, jossa ei ole kaksiasentokytkintä, kytke irti virtajohto.
Attention Avant de travailler sur un système non équipé d'un commutateur marche-arrêt, débrancher le cordon d'alimentation.
Warnung Bevor Sie an einem System ohne Ein/Aus-Schalter arbeiten, ziehen Sie das Netzkabel heraus.
Avvertenza Prima di lavorare su un sistema che non è dotato di un interruttore on/off, scollegare il cavo di alimentazione.
Advarsel Før det skal utføres arbeid på et system som ikke har en av/på-bryter, skal strømledningen trekkes ut.
Aviso Antes de começar a trabalhar num sistema que não possua um interruptor ON/OFF, desligue o cabo de alimentação.
¡Advertencia! Antes de trabajar sobre cualquier sistema que carezca de interruptor de Encendido/Apagado (ON/OFF), desenchufar el cable de alimentación.
Varning! Dra ur nätsladden innan du utför arbete på ett system utan strömbrytare.
Waarschuwing Deze apparatuur hoort geaard te worden Zorg dat de host-computer tijdens normaal gebruik met aarde is verbonden.
Varoitus Tämä laitteisto on tarkoitettu maadoitettavaksi. Varmista, että isäntälaite on yhdistetty maahan normaalikäytön aikana.
Attention Cet équipement doit être relié à la terre. S'assurer que l'appareil hôte est relié à la terre lors de l'utilisation normale.
Warnung Dieses Gerät muß geerdet werden. Stellen Sie sicher, daß das Host-Gerät während des normalen Betriebs an Erde gelegt ist.
Avvertenza Questa apparecchiatura deve essere collegata a massa. Accertarsi che il dispositivo host sia collegato alla massa di terra durante il normale utilizzo.
Advarsel Dette utstyret skal jordes. Forviss deg om vertsterminalen er jordet ved normalt bruk.
Aviso Este equipamento deverá estar ligado à terra. Certifique-se que o host se encontra ligado à terra durante a sua utilização normal.
¡Advertencia! Este equipo debe conectarse a tierra. Asegurarse de que el equipo principal esté conectado a tierra durante el uso normal.
Varning! Denna utrustning är avsedd att jordas. Se till att värdenheten är jordad vid normal användning.
Waarschuwing Dit produkt dient volgens alle landelijke wetten en voorschriften te worden afgedankt.
Varoitus Tämän tuotteen lopullisesta hävittämisestä tulee huolehtia kaikkia valtakunnallisia lakeja ja säännöksiä noudattaen.
Attention La mise au rebut définitive de ce produit doit être effectuée conformément à toutes les lois et réglementations en vigueur.
Warnung Dieses Produkt muß den geltenden Gesetzen und Vorschriften entsprechend entsorgt werden.
Avvertenza L'eliminazione finale di questo prodotto deve essere eseguita osservando le normative italiane vigenti in materia.
Advarsel Endelig disponering av dette produktet må skje i henhold til nasjonale lover og forskrifter.
Aviso A descartagem final deste produto deverá ser efectuada de acordo com os regulamentos e a legislação nacional.
¡Advertencia! El desecho final de este producto debe realizarse según todas las leyes y regulaciones nacionales.
Varning! Slutlig kassering av denna produkt bör skötas i enlighet med landets alla lagar och föreskrifter.
Waarschuwing Alvorens aan apparatuur te werken die met elektrische leidingen is verbonden, sieraden (inclusief ringen, kettingen en horloges) verwijderen. Metalen voorwerpen worden warm wanneer ze met stroom en aarde zijn verbonden, en kunnen ernstige brandwonden veroorzaken of het metalen voorwerp aan de aansluitklemmen lassen.
Varoitus Ennen kuin työskentelet voimavirtajohtoihin kytkettyjen laitteiden parissa, ota pois kaikki korut (sormukset, kaulakorut ja kellot mukaan lukien). Metalliesineet kuumenevat, kun ne ovat yhteydessä sähkövirran ja maan kanssa, ja ne voivat aiheuttaa vakavia palovammoja tai hitsata metalliesineet kiinni liitäntänapoihin.
Attention Avant d'accéder à cet équipement connecté aux lignes électriques, ôter tout bijou (anneaux, colliers et montres compris). Lorsqu'ils sont branchés à l'alimentation et reliés à la terre, les objets métalliques chauffent, ce qui peut provoquer des blessures graves ou souder l'objet métallique aux bornes.
Warnung Vor der Arbeit an Geräten, die an das Netz angeschlossen sind, jeglichen Schmuck (einschließlich Ringe, Ketten und Uhren) abnehmen. Metallgegenstände erhitzen sich, wenn sie an das Netz und die Erde angeschlossen werden, und können schwere Verbrennungen verursachen oder an die Anschlußklemmen angeschweißt werden.
Avvertenza Prima di intervenire su apparecchiature collegate alle linee di alimentazione, togliersi qualsiasi monile (inclusi anelli, collane, braccialetti ed orologi). Gli oggetti metallici si riscaldano quando sono collegati tra punti di alimentazione e massa: possono causare ustioni gravi oppure il metallo può saldarsi ai terminali.
Advarsel Fjern alle smykker (inkludert ringer, halskjeder og klokker) før du skal arbeide på utstyr som er koblet til kraftledninger. Metallgjenstander som er koblet til kraftledninger og jord blir svært varme og kan forårsake alvorlige brannskader eller smelte fast til polene.
Aviso Antes de trabalhar em equipamento que esteja ligado a linhas de corrente, retire todas as jóias que estiver a usar (incluindo anéis, fios e relógios). Os objectos metálicos aquecerão em contacto com a corrente e em contacto com a ligação à terra, podendo causar queimaduras graves ou ficarem soldados aos terminais.
¡Advertencia! Antes de operar sobre equipos conectados a líneas de alimentación, quitarse las joyas (incluidos anillos, collares y relojes). Los objetos de metal se calientan cuando se conectan a la alimentación y a tierra, lo que puede ocasionar quemaduras graves o que los objetos metálicos queden soldados a los bornes.
Varning! Tag av alla smycken (inklusive ringar, halsband och armbandsur) innan du arbetar på utrustning som är kopplad till kraftledningar. Metallobjekt hettas upp när de kopplas ihop med ström och jord och kan förorsaka allvarliga brännskador; metallobjekt kan också sammansvetsas med kontakterna.
Note This equipment has been tested and found to comply with the limits for a Class A digital device, pursuant to Part 15 of the FCC Rules. These limits are designed to provide reasonable protection against harmful interference when the equipment is operated in a commercial environment. This equipment generates, uses, and can radiate radio frequency energy and, if not installed and used in accordance with the instruction manual, may cause harmful interference to radio communications. Operation of this equipment in a residential area is likely to cause harmful interference, in which case the user will be required to correct the interference at his own expense.
Properly shielded and grounded cables and connectors must be used in order to meet FCC emission limits. This company is not responsible for any radio or television interference caused by using other than recommended cables and connectors or by unauthorized changes or modifications to this equipment. Unauthorized changes or modifications could void the user's authority to operate the equipment.
This device complies with Part 15 of the FCC Rules. Operation is subject to the following two conditions: (1) this device may not cause harmful interference, and (2) this device must accept any interference received, including interference that may cause undesired operation.
This Class A digital apparatus meets the requirements of the Canadian Interference-Causing Equipment Regulations.
Cet appareil numerique de la classe A respecte toutes les exigences du Reglement sur le materiel brouilleur du Canada.
This product is in conformity with the protection requirements of EU Council Directive 89/336/EEC on the approximation of the laws of the Member States relating to electromagnetic compatibility. This company cannot accept responsibility for any failure to satisfy the protection requirements resulting from a non-recommended modification of the product, including the fitting of non-IBM option cards.
This product has been tested and found to comply with the limits for Class B Information Technology Equipment according to CISPR 22 / European Standard EN 55022. The limits for Class B equipment were derived for typical residential environments to provide reasonable protection against interference with licensed communication devices.
Dieses Geraet ist berechtigt in Uebereinstimmung mit dem deutschen EMVG vom 9.Nov.92 das EG-Konformitaetszeichen zu fuehren. Der AuToken Ring WorkGroup Switchteller der Konformitaetserklaerung ist die IBM United Kingdom Laboratories Limited, Mail Point 147, Hursley Park Winchester, Hampshire S021 2JN, England.
Dieses Geraet erfuellt die Bedingungen der EN 55022 Klasse B.
This equipment is in the 1st Class category (information equipment to be used in commercial and/or industrial areas) and conforms to the standards set by the Voluntary Control Council for Interference by Information Technology Equipment aimed at preventing radio interference in commercial and industrial areas.
Consequently, when used in a residential area or in an adjacent area thereto, radio interference may be caused to radios and TV receivers, etc.
Cisco Connection Online (CCO) is Cisco Systems' primary, real-time support channel. Maintenance customers and partners can self-register on CCO to obtain additional information and services.
Available 24 hours a day, 7 days a week, CCO provides a wealth of standard and value-added services to Cisco's customers and business partners. CCO services include product information, product documentation, software updates, release notes, technical tips, the Bug Navigator, configuration notes, brochures, descriptions of service offerings, and download access to public and authorized files.
CCO serves a wide variety of users through two interfaces that are updated and enhanced simultaneously: a character-based version and a multimedia version that resides on the World Wide Web (WWW). The character-based CCO supports Zmodem, Kermit, Xmodem, FTP, and Internet e-mail, and it is excellent for quick access to information over lower bandwidths. The WWW version of CCO provides richly formatted documents with photographs, figures, graphics, and video, as well as hyperlinks to related information.
You can access CCO in the following ways:
For a copy of CCO's Frequently Asked Questions (FAQ), contact cco-help@cisco.com. For additional information, contact cco-team@cisco.com.
Note If you are a network administrator and need personal technical assistance with a Cisco product that is under warranty or covered by a maintenance contract, contact Cisco's Technical Assistance Center (TAC) at 800 553-2447, 408 526-7209, or tac@cisco.com. To obtain general information about Cisco Systems, Cisco products, or upgrades, contact 800 553-6387, 408 526-7208, or cs-rep@cisco.com.
Documentation for Cisco products is available in three forms: in a CD-ROM package, printed books, and on the World Wide Web. You have the option of subscribing to the CD ROM package through an update service. Or you can order printed documentation at an additional cost. Refer to the information packet included with the router for detailed ordering information. You can also access Cisco documentation on the World Wide Web URL http://www.cisco.com.
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
Posted: Sat Jan 18 06:42:30 PST 2003
All contents are Copyright © 1992--2002 Cisco Systems, Inc. All rights reserved.
Important Notices and Privacy Statement.