|
|

The Route Switch Module (RSM) is capable of being field-upgraded to support an optional
Catalyst Versatile Interface Processor 2 (VIP2) module. Earlier versions of the RSM have a slot restriction that should be taken into consideration when installing the RSM in a Catalyst 5500. This slot restriction is only for RSMs that will be upgraded with the optional Catalyst VIP2.
If you plan on upgrading RSM hardware revision 2.0 (73-2119-05) or earlier with the Catalyst VIP2, you must install the RSM in slots 3 through 8, and leave the slot immediately above it empty. This prevents you from shuffling modules between slots when upgrading the RSM with the Catalyst VIP2.
To determine the hardware revision number, refer to the section "Identifying the RSM Hardware Revision Level" immediately following this section.
If you are not upgrading with the Catalyst VIP2, there are no slot restrictions—you can install the RSM in slots 2 through 12.
Use one of the following two methods to identify the RSM hardware revision level:
The example shows an RSM in slot 4 with a hardware revision level 1.0. This revision level requires that you install the RSM in slots 3 through 8, and leave the slot immediately above the RSM empty.
Installation and configuration procedures are arranged in the order that they should be performed. Hardware installation begins in the "Installing the Route Switch Module" section. However, we recommend that you review the prior sections to get an understanding of the RSM.
If you are reading Cisco product documentation on the World Wide Web, you can submit comments electronically. Click Feedback on the title bar, and then select Documentation. After you complete the form, click Submit to send it to Cisco. We appreciate your comments.
The RSM provides multiprotocol routing for the Catalyst switch Ethernet interfaces. <Xref_Color> Table 1 lists the Cisco IOS features available for the RSM.
Table 2 lists the RSM specifications.
| 1RISC = Reduced Instruction Set Computing
2DRAM = dynamic random-access memory |
The RSM front panel features are shown in Figure 1 and are described in the following sections.
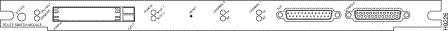
The RSM LEDs in Figure 1 are described in the following sections.
When the RSM is powered up, the switch runs a series of diagnostic tests. The STATUS LED shows the test results as described in Table 3.
| Color | Status |
|---|---|
RSM Status LED
The CPU HALT and ENABLED LEDs indicate RSM status. The ENABLED LED is on when the interface processor microcode is loaded and the RSM is operational. During normal operation, the CPU HALT LED is on. The CPU HALT LED goes off if the system detects a processor hardware failure.
The PCMCIA SLOT 1 and SLOT 0 LEDs light when their respective slot 1 and slot 0 PCMCIA devices are accessed by the RSM. See "Using Flash Memory (PCMCIA) Cards," for detailed information.
The RSM has two channels that transfer packet data between the Catalyst switch backplane and the network VLANs. CHANNEL 0 and CHANNEL 1 transmit (TX) and receive (RX) LEDs indicate transmit and receive activity for each channel. Each channel is associated with a single SAGE ASIC. A VLAN can be mapped to a specific channel to balance the load of each channel.
The Flash memory (PCMCIA) card slots in Figure 1 are for additional system PCMCIA-based Flash memory. You can use this Flash memory to store and run Cisco IOS images, or as a file server for other routers to access as clients. See "Using Flash Memory (PCMCIA) Cards," for detailed information.
The RESET button in Figure 1 causes a nonmaskable interrupt (NMI) and places the RSM in ROM Monitor mode. (Use the Catalyst switch reset command to reset the RSM hardware.)
The AUX port in Figure 1 allows you to connect to a modem for remote access to the RSM. The CONSOLE port allows you to connect a terminal to the RSM for configuration and monitoring. See "Connecting to the Route Switch Module Console and Auxiliary Ports," for detailed information.
Note This section describes the basic operation of the RSM and some terminology used in RSM configuration procedures. Complete step-by-step configuration procedures are provided in "Configuring the Route Switch Module,".
The RSM is a router module running Cisco IOS router software that directly interfaces to (plugs into) the Catalyst switch backplane.
From the perspective of the Catalyst switch, the RSM appears as a module with a single trunked port and one Media Access Control (MAC) address. From the perspective of the user, the RSM has one port. This port is unlike other Catalyst switch line card ports in that it has no external attributes such as media type or speed.
The RSM interface to the Catalyst switch backplane is through two Cisco SAGE ASICs, SAGE 0 and SAGE 1. SAGE 0 corresponds to CHANNEL 0 and SAGE 1 to CHANNEL 1. CHANNEL 0 and CHANNEL 1 are used to transfer data packets between network VLANs on the Catalyst switch backplane.
VLAN 0 is mapped to CHANNEL 0 and VLAN 1 is mapped to CHANNEL 1. VLAN 0 is used for communication between the RSM and the Catalyst switch and is not accessible to the user.
VLAN 1 is the standard Catalyst switch default VLAN. Additional VLANs are toggled between the two channels as they are created. A VLAN can be mapped to a specific channel to balance the load of each channel.
For configured VLANs (other than VLANs 0 and 1) the VLAN number is the VLAN interface number used to create the VLAN. From the perspective of the RSM, the VLAN interface number has two meanings (see "VLAN Configuration Examples," for details):
Each VLAN that the RSM is routing appears as a separate virtual interface. Therefore, the configuration file of the RSM has an interface description for each VLAN. The most common configuration is one subnet per VLAN interface which means that the subnet address is the primary IP address for the interface. Secondary addressing can be used on a VLAN interface as on any other router interface.
Figure 2 shows a three-VLAN configuration that would be configured for interVLAN IP routing as follows:
set vtp domain domain_name
set vtp mode transparent
set port enable 3/1
set vlan 2 3/1
set port enable 3/2
set vlan 3 3/2
set port enable 3/3
set vlan 4 3/3
session mod
configure terminal
interface vlan2
ip address 171.68.195.33 255.255.255.0
no shut
interface vlan3
ip address 171.69.165.34 255.255.255.0
no shut
interface vlan4
ip address 171.67.170.40 255.255.255.0
no shut
end
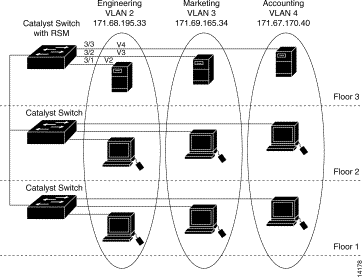
Figure 3 shows a three-router configuration that would be configured for interVLAN IP routing as follows:
set vtp domain domain_name
set vtp mode transparent
set port enable 2/1
set vlan 2 2/1
set vlan 2
set port enable 2/2
set vlan 3 2/2
set vlan 3
session mod
configure terminal
ip routing
router rip
network 2.0.0.0
interface vlan2
ip address 2.0.51.1 255.255.255.0
no shut
interface vlan3
ip address 2.0.61.1 255.255.255.0
no shut
end
configure terminal
ip routing
router rip
network 2.0.0.0
interface E2/2
ip address 2.0.51.2 255.255.255.0
no shut
end
configure terminal
ip routing
router rip
network 2.0.0.0
interface E3/2
ip address 2.0.61.2 255.255.255.0
no shut
end
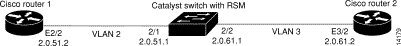
The MAC addresses available to the RSM are assigned as follows:
The RSM supports downloadable system software and microcode for most Cisco IOS and microcode upgrades, enabling you to remotely download, store, and boot from a new image. Flash memory contains the default system software. For system software component locations, see Figure 7 in "Replacing and Upgrading DRAM SIMMs,".
The system configuration and software configuration register settings are stored in the 128-kilobyte (KB) nonvolatile random-access memory (NVRAM).
Two types of Flash memory are on the RSM: a Flash SIMM (also referred to as boot Flash) and PCMCIA Flash cards.
Flash memory allows you to remotely load and store multiple Cisco IOS software and microcode images. You can download a new image over the network or from a local server and then add the new image to Flash or replace the existing files. You can then boot the RSM either manually or automatically from any of the stored images. Flash memory also functions as a Trivial File Transfer Protocol (TFTP) server to allow other servers to remotely boot from stored images or to copy them into their own Flash memory. See "Specifying the Startup System Image,".
PCMCIA Flash memory cards must either be formatted on the RSM or on a Route Switch Processor (RSP)-based 7500 series router running software at the same level, or greater, as the RSM. Flash memory cards previously formatted on an Route Processor (RP)-based Cisco 7000 series router cannot be used on the RSM. Flash memory cards formatted on the RSM can be used on RSP-based 7500 series routers (but not on RP-based 7000 series routers). See "Formatting a Flash Memory Card,".
A 256-KB EPROM stores the ROM monitor program. In the event of both network and Flash memory corruption, specifying a system image to be loaded from Boot ROM provides a final backup boot method. System images stored in ROM are not always as complete as those stored in Flash memory or on network servers.
Note The RSM software configuration register is set at the factory to 0x2102 to boot from PCMCIA Flash slot 0. When the RSM is inserted with this setting, it boots automatically without any user interaction. If the software configuration register setting has been changed to specify a different boot source, the RSM might not automatically boot when inserted. See "Modifying the Configuration Register Boot Field,".
There are three possible end results when attempting to boot the system:
1. You end up with a system image running on the RSM (normal case)
2. You end up with an rxboot image running on the RSM in boot mode
3. You end up at the ROM monitor prompt—the system waits for instructions
Two main steps or processes are involved in booting the system, they are described in the following paragraphs (see the "Image Descriptions" section below for additional information on images discussed here).
The ROM monitor looks for the rxboot image first. It looks in the BOOTLDR variable in NVRAM (set using the boot bootldr device:filename command). If it finds the rxboot image where the BOOTLDR variable says it is, it loads that image and then proceeds to the second step.
If it does not find the rxboot image, it looks for the BOOT variable (set using the boot system flash device:filename commands). The BOOT variable is a list of image names. If the ROM monitor finds and successfully loads one of these images, the boot process is complete (end result No. 1).
If the ROM monitor does not find any of the BOOT variable images, it loads the first image in
slot 0. If it does not find an image in slot 0, it loads the first image in boot flash. If it does not find an image in boot flash, it goes to the ROM monitor prompt (end result No. 3).
Step 2 Rxboot Image Process
The rxboot image runs and parses the configuration file looking for boot system commands. Boot system [rcp | tftp] filename [ip-address] commands specify what to boot when netbooting. Boot system flash device:filename commands specify what to boot when booting from flash. The commands are attempted in the order that they appear in the configuration file. If any command succeeds, the boot process is complete (end result No. 1). If none of the commands succeed, the system remains at the rxboot image (end result No. 2).
DRAM stores routing tables, protocols, and network accounting applications. The standard RSM configuration is 32 megabytes (MB) of DRAM, with up to 128 MB available through SIMM upgrades.
Hot swapping lets you remove and replace the RSM while the system is operating. When the system detects that a module has been installed or removed, it automatically runs diagnostic and discovery routines, acknowledges the presence or absence of the module, and resumes system operation without any user intervention.
The Catalyst 5500 switch has 13 slots. Slot 1 is reserved for the supervisor engine module. If a redundant supervisor engine module is used, it would go in slot 2; otherwise, slot 2 can be used for other modules. Slot 13 is a dedicated slot, reserved for the ATM Switch Processor (ASP) module. The RSM can be installed in any of the remaining slots (early versions of the RSM do have slot restrictions when the RSM is used with the optional Catalyst VIP2 [see "Catalyst 5500 Series Switch Slot Restrictions" on page 1 for details]).
Note The maximum number of ATM and RSM modules for the Catalyst 5500 switch is seven. You can use any combination of ATM and RSM modules as long as the total does not exceed seven (for example, you could have four ATM modules and three RSMs).
The Catalyst 5000 and Catalyst 5505 switches have five slots. The first slot is for the supervisor engine module (the Catalyst 5505 supports an optional redundant supervisor engine in slot 2). The remaining slots are available for any combination of Ethernet, Fast Ethernet, Asynchronous Transfer Mode (ATM) LAN emulation, Fiber Distributed Data Interface/Copper Distributed Data Interface (FDDI/CDDI) modules, or the RSM.
Use the following steps to install the RSM:
(a). Use a straight-through EIA/TIA-232 cable with DB-25 male connectors on each end to connect to the data communications equipment (DCE) console port DB-25 female connector and to the DB-25 female connectors used on the data terminal equipment (DTE) ports on most terminals.
(b). Configure the terminal or PC terminal emulation software to the default parameters for the console port:
Note You should not have to connect a terminal to the RSM console port. At the end of the installation procedure, use the session command to access the RSM for router configuration.
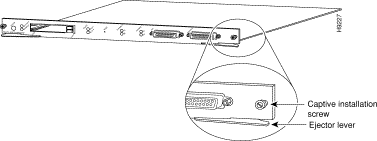
Step 2 Modules are secured with two captive installation screws. Use a 1/4-inch flat-blade screwdriver to loosen the captive installation screws and remove the module filler plate or the existing module from the slot you want to use.
Step 3 Guide the RSM into the slot, aligning the sides of the RSM with the guides in the slot (avoid touching the components on the board).
Step 4 While keeping the module oriented horizontally, carefully slide it into the slot until its front panel contacts the ejector levers (see Figure 4).
Step 5 Using the thumb and forefinger of each hand, simultaneously push the left lever and the right lever in to fully seat the module in the backplane connector.
Step 6 Use a screwdriver to tighten the captive installation screws on the left and right sides of the module (see Figure 4).
Step 7 Check the status of the module as follows:
Step 8 After verifying that the RSM is operational, enter the session mod/num command (mod/num is the RSM slot number) at the Cat5k> prompt. You should now be at the router> prompt. Proceed to the next section, "What to Do after Installing the Route Switch Module."
After you install the RSM into the switch, proceed to one of the following sections:
This section provides procedures to configure the RSM for multiprotocol routing for the Catalyst switch Ethernet interfaces. Perform the procedures in the following sections in the order that they are listed.
You can use the session mod/num command (mod/num is the RSM slot number) to access the RSM from the switch—eliminating the need to connect a terminal directly to the RSM console port.
In some of the configuration procedures, you use both Catalyst switch-specific commands and router-specific commands. Some command names are identical within each command group (for example, show interface). This document uses the following convention to distinguish between commands: If the command is to be entered from the Catalyst switch session, you are instructed to enter it at the Cat5k> prompt. If the command is to be entered from the router session, you are instructed to enter it at the router> prompt. To exit from the router back to the switch, enter exit at the router> prompt.
The RSM is configured at the factory to load a Cisco IOS image (router operating system software) automatically the first time it is powered on (inserted) into the Catalyst switch. The RSM software configuration register, which determines where the RSM loads the image from, is set at the factory to load the image from PCMCIA Flash slot 0 (configuration register setting 0x2102).
After the RSM goes through power-on self-test diagnostics, and the front panel status LED is green, you can access the RSM by entering the session mod/num command at the Cat5k> prompt—this gets you to the router> prompt.
After booting the RSM for the first time, you need to configure the RSM interfaces and then save the configuration to a file in NVRAM. Before configuring the interfaces, review the configuration guidelines in the next section, "Configuring the Route Switch Module for InterVLAN Routing."
Note After booting the RSM for the first time, you can specify a different boot source by changing the software configuration register settings and resetting the RSM (refer to "Modifying the Configuration Register Boot Field," for detailed information).
VLANs are created at the switch level (Cat5k> prompt) using the set vlan command to group ports into virtual LANs. VLANs are controlled at the router level (router> prompt) using the interface command.
Use the following guidelines when configuring the RSM for interVLAN routing:
For configuration instructions, proceed to the next section, "Configuring the Route Switch Module for the First Time."
| 1This enables IPX routing on the VLAN. When you enable IPX routing on the VLAN, you can also specify an encapsulation type. |
RSM Configuration Task List
You can configure the RSM using one of the following procedures:
Note Before you start a configuration procedure in this section, refer to "Configuring the Route Switch Module for InterVLAN Routing,". Use the procedure that best fits the needs of your network configuration and level of Cisco IOS experience.
Note AutoInstall requires the optional Catalyst VIP2 with a serial port adapter.
You can configure the RSM manually if you prefer not to use the System Configuration Dialog (Setup) as follows:
The prompt changes to the privileged EXEC (enable) prompt:
Step 2 Enter the configure terminal command at the enable prompt to enter configuration mode:
You can now enter any changes you want to the configuration. Refer to "Configuring the Route Switch Module for InterVLAN Routing," for configuration specifics.
Step 3 Press Ctrl-Z to exit Configuration mode.
To see the current operating configuration, enter the show running-config command at the enable prompt:
To see the configuration in NVRAM, enter the show startup-config command at the enable prompt:
The results of the show running-config and show startup-config commands will be different if you have made changes to the configuration but have not yet written them to NVRAM.
To make your changes permanent, enter the copy running-config startup-config command at the enable prompt:
The RSM is now configured and will boot with the configuration you entered.
The AutoInstall process allows you to configure the RSM automatically. For AutoInstall to work properly, a Transmission Control Protocol/Internet Protocol (TCP/IP) host on your network must be preconfigured (by your system administrator at the site where the TCP/IP host is located) to provide the required configuration files. The TCP/IP host may exist anywhere on the network as long as the following two conditions are maintained:
1. The host must be on the remote side of the RSM/VIP2 synchronous serial connection to the WAN.
2. User Datagram Protocol (UDP) broadcasts to and from the RSM and the TCP/IP host must be enabled.
Do not attempt to use AutoInstall unless the required files are on the TCP/IP host. For more information, refer to the Access and Communication Servers Configuration Guide.
Take the following steps to prepare your RSM for the AutoInstall process:
Step 2 When the RSM/VIP2 is powered on, it loads the operating system image from Flash memory. If the remote end of the WAN connection is connected and properly configured, the AutoInstall process begins.
Step 3 If AutoInstall completes successfully, enter the copy running-config startup-config command in privileged EXEC mode to write the configuration data to the RSM NVRAM:
This last step saves the configuration settings that the AutoInstall process created to the router's NVRAM. If you do not do this step, the configuration is lost the next time you reload the router.
This concludes the initial RSM configuration.
This dialog helps you navigate through the configuration process by prompting you for the configuration information necessary for the RSM to operate.
Many prompts in the System Configuration Dialog include default answers, which are included in square brackets following the question. To accept a default answer, press Return; otherwise, enter your response.
This section gives an example configuration using the System Configuration Dialog. When you are configuring the RSM, respond as appropriate for your network.
At any time during the System Configuration Dialog, you can request help by typing a question mark (?) at a prompt.
Perform the following steps to configure the RSM using the System Configuration Dialog:
At the privileged EXEC (enable) prompt, enter the setup command:
Information similar to the following is displayed on the console screen.
Note The messages displayed vary, depending on the Cisco IOS release and feature set you selected. The screen displays in this section are for reference only and might not exactly reflect the screen displays on your console.
Step 2 Press Return or enter yes to begin the configuration process.
Step 3 When the System Configuration Dialog asks whether you want to view the current interface summary, press Return or enter yes:
Step 4 Configure the global parameters. Choose which protocols to support on the VLANs. For IP installations, press Return to accept the default values (in brackets) for most of the questions. A typical configuration follows:
Next, you are prompted to enter an enable secret password. There are two types of privileged-level passwords:
The enable password is used when the enable secret password does not exist.
For maximum security, be sure the passwords are different. If you enter the same password for both, the router will accept your entry, but will display a warning message indicating that you should enter a different password.
Step 5 Enter an enable secret password:
Step 6 Enter the enable and virtual terminal passwords:
Step 7 Press Return to accept Simple Network Management Protocol (SNMP) management, or enter no to refuse it:
Step 8 In the following example, the RSM is configured for AppleTalk, IP, and IPX. Configure the appropriate protocols for your RSM:
When modifying your routing environment, you perform some general startup tasks. For example, to modify a configuration file, you enter Configuration mode. You also modify the configuration register boot field to tell the RSM if and how to load a system image upon startup. Also, instead of using the default system image and configuration file to start up, you can specify a particular system image and configuration file that the RSM uses to start up.
This section describes the following tasks:
Before you attempt to upload or retrieve a file from a remote host, ensure that the connection is good between the RSM and the remote server. Use the packet internet groper (ping) program to send a series of echo request packets to the remote device and wait for a reply. If the connection is good, the remote device echoes them back to the local device.
The console terminal displays the results of each message sent: an exclamation point (!) indicates that the local device received an echo, and a period (.) indicates that the server timed out while awaiting the reply. If the connection between the two devices is good, the system displays a series of exclamation points (! ! !) or (ok). If the connection fails, the system displays a series of periods
( . . . ) or (timed out) or (failed).
To verify the connection between the RSM and a remote host, issue the ping command followed by the name or Internet Protocol (IP) address of the remote server, and then press Return. Although the ping command supports configurable options, the defaults, including Internet Protocol (IP) as the protocol, are enabled when you enter a host name or address on the same line as the ping command. For a description of the configurable options, refer to the appropriate software documentation.
The following example shows a successful ping:
The following example shows the results of a failed ping:
If the connection fails, check the physical connection to the remote file server and verify that you are using the correct address or name, and then ping the server again. If you are unable to establish a good connection, contact your network administrator or see "Cisco Connection Online,", for instructions on contacting the technical assistance center.
This section provides procedures for saving, uploading, and downloading the system configuration. Configuration information resides in two places when the RSM is operating: the default (permanent) configuration in NVRAM and the running (temporary) memory in RAM. The default configuration always remains available; NVRAM retains the information even when the power is shut down. The current information is lost if the system power is shut down. The current configuration contains all nondefault configuration information that you added by using the configure command, the setup command facility, or by editing the configuration file.
The copy running-config startup-config command adds the current configuration to the default configuration in NVRAM, so that it is saved if power is shut down. Whenever you make changes to the system configuration, issue the copy running-config startup-config command to ensure that the new configuration is saved.
If you replace the RSM, you need to replace the entire configuration (NVRAM resides in socket U21 on the RSM). If you upload (copy) the configuration file to a remote server before removing the RSM, you can retrieve it later and write it into NVRAM on the new RSM. If you do not upload the configuration file, you need to use the configure command or the setup command facility to reenter the configuration information after you install the new RSM.
Saving and retrieving the configuration file is not necessary if you are temporarily removing an RSM that you are going to reinstall; the lithium batteries retain the configuration in memory. This procedure requires privileged-level access to the EXEC command interpreter, which usually requires a password.
Before you upload (copy) the running configuration to the TFTP file server, ensure the following:
To store information on a remote host, enter the privileged EXEC command write network. The command prompts you for the destination host address and a filename, and then displays the instructions for confirmation. When you confirm the instructions, the RSM sends a copy of the currently running configuration to the remote host. The system default is to store the configuration in a file called by the name of the RSM with -confg appended. You can either accept the default filename by pressing Return at the prompt, or enter a different name before pressing Return.
Follow these steps to upload (copy) the currently running configuration to a remote host:
Step 2 Use the ping command to check the connection between the RSM and the remote host. (See the previous section, "Using the ping Command.")
Step 3 Issue the write term command to display the currently running configuration on the terminal, and ensure that the configuration information is complete and correct. If it is not, use the configure command to add or modify the existing configuration. (Refer to the appropriate software documentation for the configuration options available for the system and individual interfaces and for specific configuration instructions.)
Step 4 Issue the write net command. The EXEC command interpreter prompts you for the name or IP address of the remote host that is to receive the configuration file. (The prompt might include the name or address of a default file server.)
Step 5 Enter the name or IP address of the remote host. In the following example, the name of the remote server is servername:
Step 6 The EXEC command interpreter prompts you to specify a name for the file that is to hold the configuration. By default, the system appends -confg to the RSM name to create the new filename. Press Return to accept the default filename, or enter a different name for the file before pressing Return. In the following example, the default is accepted:
Step 7 Before the RSM executes the copy process, it displays the instructions you entered for confirmation. If the instructions are not correct, enter n (no) and then Return to abort the process. To accept the instructions, press Return or y and then Return, and the system begins the copy process. In the following example, the default is accepted:
While the RSM copies the configuration to the remote host, it displays a series of exclamation points (! ! !) or periods (. . .). The !!!! and [ok] indicate that the operation is successful. A display of . . . [timed out] or [failed] indicates a failure, which would probably be due to a network fault or the lack of a writable, readable file on the remote file server.
Step 8 If the display indicates that the process was successful (with the series of ! ! ! and [ok]), the upload process is complete. The configuration is safely stored in the temporary file on the remote file server.
If the display indicates that the process failed (with the series of . . . as shown in the following example):
your configuration was not saved. Repeat the preceding steps, or select a different remote file server and repeat the preceding steps.
If you are unable to copy the configuration to a remote host successfully, contact your network administrator or see "Cisco Connection Online,", for instructions on contacting the technical assistance center.
After you install the new RSM, you can retrieve the saved configuration and copy it to NVRAM. Enter Configuration mode and specify that you want to configure the RSM from the network. The system prompts you for a host name and address, the name of the configuration file stored on the host, and confirmation to reboot using the remote file.
Follow these steps to download (retrieve) the currently running configuration from a remote host:
Note Until you retrieve the previous configuration, the RSM runs from the default configuration in NVRAM. Therefore, any passwords that were configured on the previous system are not valid until you retrieve the configuration.
Step 2 Use the ping command to verify the connection between the router and the remote host. (See "Using the ping Command,".)
Step 3 At the system prompt, issue the configure network command and press Return to enter Configuration mode. Specify that you want to configure the system from a network device (instead of from the console terminal, which is the default).
Step 4 The system prompts you to select a host or network configuration file. The default is host; press Return to accept the default.
Step 5 The system prompts you for the IP address of the host. Enter the IP address or name of the remote host (the remote file server to which you uploaded the configuration file).
Step 6 The system prompts you for the name of the configuration file. When uploading the file, the default is to use the name of the RSM with the suffix -confg (router-confg in the following example). If you specified a different filename when you uploaded the configuration, enter the filename; otherwise, press Return to accept the default.
Step 7 Before the system reboots with the new configuration, it displays the instructions you entered for confirmation. If the instructions are not correct, enter n (no), and then press Return to cancel the process. To accept the instructions, press Return, or y, and then Return.
While the RSM retrieves and boots from the configuration on the remote host, the console display indicates whether or not the operation was successful. A series of !!!! and [OK] (as shown in the preceding example) indicate that the operation was successful. A series of . . . and [timed out] or [failed] indicate a failure (which would probably be due to a network fault or an incorrect server name, address, or filename). The following is an example of a failed attempt to boot from a remote server:
Step 8 If the display indicates that the process was successful, proceed to the next step.
If the display indicates that the process failed, verify the name or address of the remote server and the filename, and repeat the preceding steps. If you are unable to retrieve the configuration, contact your network administrator or see "Cisco Connection Online,", for instructions on contacting the technical assistance center.
Step 9 Issue the write term command to display the currently running configuration on the terminal. Review the display and ensure that the configuration information is complete and correct. If it is not, verify the filename and repeat the preceding steps to retrieve the correct file, or use the configure command to add or modify the existing configuration. (Refer to the appropriate software documentation for the configuration options available for the system and individual interfaces and specific configuration instructions.)
Step 10 When you have verified that the currently running configuration is correct, issue the copy running-config startup-config command to save the retrieved configuration in NVRAM. Otherwise, the new configuration is lost if you restart the system. This completes the procedure for downloading (retrieving) the configuration file.
To enter Configuration mode, enter the configure command at the privileged EXEC prompt. The RSM responds with the following prompt asking you to specify the terminal or memory, or a file stored on a network server (network) as the source of configuration commands:
Each of these three methods is described in the following sections:
The RSM accepts one configuration command per line. You can enter as many configuration commands as you want.
You can add comments to a configuration file describing the commands you have entered. Precede a comment with an exclamation point (!). Because comments are not stored in NVRAM or in the active copy of the configuration file, comments do not appear when you list the active configuration with the show running-config EXEC command. Also, when the startup configuration is NVRAM, comments do not show up when you list the startup configuration with the show startup-config EXEC command. Comments are stripped out of the configuration file when it is loaded onto the RSM. However, you can list the comments in configuration files stored on a TFTP or rcp server.
When you configure the RSM from the terminal, the RSM executes the commands you enter at the system prompts. To configure the RSM from the terminal, complete the following steps:
In the following example, the RSM is configured from the terminal. The comment "The following command provides the router host name" identifies the purpose of the next command line. The hostname command changes the RSM name from router1 to router2. Press Ctrl-Z (^Z) to quit Configuration mode. Finally, the copy running-config startup-config command saves the current configuration to the startup configuration.
The RSM startup software uses the configuration pointed to by the CONFIG_FILE environment variable to start up. When the CONFIG_FILE environment variable does not exist or is null (such as a first-time startup), the RSM uses NVRAM as the default startup device. When the RSM uses NVRAM to start up and the system detects a problem with NVRAM or the configuration it contains, the RSM enters setup mode. Refer to the Router Products Getting Started Guide for more information on the setup command facility. For more information on environment variables, refer to "Cisco's Implementation of Environment Variables,".
The following command configures the RSM to execute the configuration specified by the CONFIG_FILE environment variable.
To configure the RSM to execute the configuration specified by the CONFIG_FILE environment variable, complete the following task in privileged EXEC mode:
| Task | Command |
|---|---|
Configure the RSM to execute the configuration specified by the CONFIG_FILE environment variable. |
You can configure the RSM by retrieving and modifying a configuration file stored on one of your network servers. To do so, complete the following steps:
In the following example, the RSM is configured from the file tokyo-config at IP address 131.108.2.155:
This task loads a configuration file directly into the location specified by the CONFIG_FILE environment variable without affecting the running configuration.
To copy a configuration file directly to the startup configuration, perform the following task in EXEC mode:
| Task | Command |
|---|---|
Load a configuration file directly into the location specified by the CONFIG_FILE environment variable. |
The configuration register boot field determines whether or not the RSM loads an operating system image, and if so, where it obtains this system image. The following sections describe the RSM's process for using the configuration register boot field, your process for setting this field, and the tasks you must perform to modify the configuration register boot field.
The lowest four bits of the 16-bit configuration register (bits 3, 2, 1, and 0) form the boot field. The following boot field values determine if the RSM loads an operating system and where the RSM obtains the system image:
When loading a default system image from a network server, the RSM uses the configuration register settings to determine the default system image filename for booting from a network server. The RSM forms the default boot filename by starting with the word cisco and then appending the octal equivalent of the boot field number in the configuration register, followed by a hyphen (-) and the processor type name (cisconn-cpu).
Use the procedure in this section to modify the current configuration register setting to reflect the way in which you want the RSM to boot a system image. In the procedure you are asked to change the least significant hexadecimal digit to one of the following:
For example, if the current configuration register setting is 0x101 and you want to load a system image from boot system commands in the startup configuration file, you would change the configuration register setting to 0x102.
To modify the software configuration register boot field, complete the following procedure:
Use the show version EXEC command to display the current configuration register setting. In ROM Monitor mode, use the o command to list the value of the configuration register boot field.
In the following example, the show version command indicates that the current configuration register is set so that the RSM does not automatically load an operating system image (configuration register is 0x0). Instead, it enters ROM Monitor mode and waits for user-entered ROM monitor commands. The new setting instructs the RSM to load a system image from commands in the startup configuration file or from a default system image stored on a network server.
You can enter multiple boot commands in the startup configuration file or in the BOOT environment variable to provide backup methods for loading a system image onto the RSM. The two ways to load a system image follow:
You can enter the different types of boot commands in any order in the startup configuration file or in the BOOT environment variable. If you enter multiple boot commands, the RSM tries them in the order they are entered.
Flash memory is located on the onboard Flash SIMM or on a Flash memory card inserted in one of the PCMCIA slots (slot 0 or slot 1). You can store or boot software images in Flash memory as necessary. Flash memory can reduce the effects of network failure by reducing dependency on files that can only be accessed over the network.
When you receive your RSM from the factory, bootflash contains the rxboot image. You can change the location of this image to a Flash memory card inserted in a PCMCIA slot. To specify the rxboot image Flash device, you set the BOOTLDR environment variable. See "Cisco's Implementation of Environment Variables,", for more information.
Note When no BOOTLDR environment variable exists, the default rxboot image is the first image file in bootflash (see "System Software Description,", for more information on the rxboot image).
The configuration process is as follows:
Step 2 Optionally, use rcp or TFTP to update the system image that resides in bootflash or on one of the Flash memory cards inserted in a PCMCIA slot. Performing this step allows you to update a degraded system image with one that is not degraded.
Step 3 Configure your system to automatically boot from the desired file in Flash memory. You might need to change the configuration register value. See "Modifying the Configuration Register Boot Field,".
Step 4 Save your configurations.
Step 5 Power-cycle and reboot your system to ensure that all is working as expected.
Flash memory configuration tasks discussed in this section include the following:
To set the BOOTLDR environment variable on your RSM, perform the following steps beginning in privileged EXEC mode:
The following example sets the BOOTLDR environment to change the location of the rxboot image from bootflash to slot 0.
To configure the RSM to automatically boot from an image in Flash memory, perform the following steps:
| 1Refer to "Modifying the Configuration Register Boot Field," for information on using this command to modify the software configuration register. |
If you enter more than one image filename, the RSM tries them in the order entered. If a filename already appears in the configuration file and you want to specify a new filename, remove the existing filename with the no boot system flash filename command.
Note The no boot system configuration command disables all boot system configuration commands regardless of argument. Specifying the flash keyword or the filename argument with the no boot system command disables only the commands specified by these arguments.
The following example shows how to configure the RSM to automatically boot from an image in Flash memory:
Once you successfully configure Flash memory, you might want to configure the system with the no boot system flash command to revert to booting from bootflash. You might want to revert to booting from bootflash if you do not yet need this functionality or if you do not have the proper image in Flash memory.
Following are additional commands related to the Flash memory on the RSM and the Flash memory cards. You can determine which memory media you are accessing using the pwd command as follows:
You can move between Flash memory media using the cd [bootflash | slot0 | slot1 ] command as follows:
You can list the directory of Flash memory media using the dir [bootflash | slot0 | slot1 ] command as follows:
You can delete a file from any Flash memory media using the delete command as follows:
Files that are deleted are simply marked as deleted, but they still occupy space in Flash memory. The squeeze command removes them permanently and pushes all other undeleted files together to eliminate spaces between them. Following is the syntax of the squeeze command:
To prevent loss of data due to sudden power loss, the "squeezed" data is temporarily saved to another location of Flash memory, which is specially used by the system.
In the previous command display output, an "e" means this special location has been erased (which must be performed before any write operation). A "b" means that the data that is about to be written to this special location has been temporarily copied. An "E" signifies that the sector that was temporarily occupied by the data has been erased. An "S" signifies that the data was written to its permanent location in Flash memory.
The squeeze command operation keeps a log of which of these functions has been performed so if the power fails suddenly, it can come back to the right place and continue with the process. "Z" means this log was erased after the successful squeeze command operation.
The configuration register setting 0x0101 tells the system to boot the default image (the first image) from onboard Flash memory, but does not reset the Break disable or check for a default netboot filename. The configuration register setting 0x0102 tells the system to boot from Flash memory if netboot fails, disable Break, and check for a default netboot filename. For more information on the copy tftp:filename [bootflash | slot0 | slot1]:filename command, and other related commands, refer to the Access and Communication Servers Configuration Guide and Access and Communication Servers Command Reference publications.
You can configure the RSM to load a system image from a network server using TFTP or rcp to copy the system image file. To do so, you must set the configuration register boot field to the correct value. See "Modifying the Configuration Register Boot Field,".
If you do not specify either TFTP or rcp, by default the system image that you specify is booted from a network server via TFTP.
Note If you are using a Sun workstation as a network server and TFTP to transfer the file, set up the workstation to enable verification and generation of User Datagram Protocol (UDP) checksums. See the Sun documentation for details.
For increased performance and reliability, use rcp to boot a system image from a network server. The rcp implementation uses the Transmission Control Protocol (TCP), which ensures reliable delivery of data.
You cannot explicitly specify a remote username when you issue the boot command. Instead, the RSM host name is used. If the remote server has a directory structure, as do UNIX systems, and you boot the RSM from a network server using rcp, the Cisco IOS software searches for the system image on the server relative to the directory of the remote username.
If there is not enough room in memory to boot a regular image from a network server, you can produce a compressed software image on any UNIX platform using the compress command. Refer to your UNIX platform's documentation for the exact usage of the compress command.
To specify the loading of a system image from a network server, complete the following steps:
| 1Refer to "Modifying the Configuration Register Boot Field,". |
In the following example, the RSM uses rcp to boot from the testme5.tester system image file on a network server at IP address 131.108.0.1:
Occasionally network failures make booting from a network server impossible. To lessen the effects of network failure, consider the following booting strategy. After Flash is installed and configured, you might want to configure the RSM to boot in the following order:
2. Boot an image from a system file on a network server.
This boot order provides the most fault-tolerant booting strategy. Perform the following steps to allow the RSM to boot first from Flash, and then from a system file from a network serve
| 1Refer to "Modifying the Configuration Register Boot Field,". |
r.
The following example illustrates the order of the commands needed to implement this strategy. In the example, the RSM is configured to first boot an internal Flash image called gsxx. Should that image fail, the RSM boots the configuration file gsxx from a network server.
Configuration files can be stored on network servers. You can configure the RSM to automatically request and receive two configuration files from the network server at startup:
The first file the server attempts to load is the network configuration file. This file contains information that is shared among several routers. For example, you can use this file to provide mapping between IP addresses and host names.
The second file the server attempts to load is the host configuration file. This file contains commands that apply to one router in particular. Both the network and host configuration files must reside on a network server reachable via TFTP or rcp.
You can specify an ordered list of network configuration and host configuration filenames. The RSM scans this list until it successfully loads the appropriate network or host configuration file.
In addition to storing configuration files on network servers, you can store configuration files in NVRAM and on Flash memory cards. The CONFIG_FILE environment variable specifies the device and filename of the configuration file to use during initialization. For more information on environment variables, see "Cisco's Implementation of Environment Variables,".
You can set the CONFIG_FILE environment variable to specify the startup configuration.
To specify a startup configuration file, perform either the first two tasks or the third task:
To configure the RSM to download a network configuration file from a server at startup, complete the following steps:
In Step 2, if you do not specify a network configuration filename, the RSM uses the default filename network-confg. If you omit both the tftp and the rcp keywords, the RSM assumes that you are using TFTP to transfer the file and that the server whose IP address you specify supports TFTP.
If you configure the RSM to download the network configuration file from a network server using rcp and the server has a directory structure as do UNIX systems, the RSM software searches for the system image on the server relative to the directory of the remote username. The RSM host name is used as the remote username.
You can specify more than one network configuration file. The RSM tries them in order until it loads one successfully. This procedure can be useful for keeping files with different configuration information loaded on a network server.
To configure the RSM to download a host configuration file from a server at startup, complete the following steps. Step 2 is optional. If you do not specify a host configuration filename, the RSM uses its own name to form a host configuration filename by converting the RSM name to all lowercase letters, removing all domain information, and appending -confg. If no host name information is available, the RSM uses the default host configuration filename router-confg.
You can specify more than one host configuration file. The RSM tries them in order until it loads one successfully. This procedure can be useful for keeping files with different configuration information loaded on a network server.
In the following example, the RSM is configured to boot from the host configuration file hostfile1 and from the network configuration file networkfile1:
If the network server fails to load a configuration file during startup, it tries again every ten minutes (the default setting) until a host provides the requested files. With each failed attempt, the network server displays a message on the console terminal. If the network server is unable to load the specified file, it displays the following message:
Refer to the Troubleshooting Internetworking Systems publication for troubleshooting procedures. If there are any problems with the startup configuration file, or if the configuration register is set to ignore NVRAM, the RSM enters the setup command facility. See the Router Products Getting Started Guide for details on the setup command.
In addition to loading startup configuration files from a server, you can configure the RSM to load a startup configuration file specified by the CONFIG_FILE environment variable. To do so, complete the following steps, beginning in EXEC mode:
When saving the runtime CONFIG_FILE environment variable to the startup configuration, the RSM saves a complete version of the configuration file to the location specified by the CONFIG_FILE environment variable and a distilled version to NVRAM. A distilled version is one that does not contain access list information. If NVRAM contains a complete configuration file, the RSM prompts you to confirm your overwrite of the complete version with the distilled version. If NVRAM contains a distilled configuration, the RSM does not prompt you for confirmation and proceeds with overwriting the existing distilled configuration file in NVRAM.
The following example copies the running configuration file to the first PCMCIA slot (slot0). This configuration is then used as the startup configuration when the system is restarted.
The PCMCIA Flash memory card slots on your RSM can store executable images and configuration files. The RSM can boot images and load configuration files from Flash memory cards as well as from internal flash (bootflash), NVRAM, and the network.
Because the RSM can boot images and load configuration files from several locations, it uses ROM monitor environment variables to specify the location and filename of images and configuration files. These special environment variables are as follows:
The BOOT environment variable specifies a list of bootable images on various devices. The valid devices are internal Flash (bootflash:), the first PCMCIA slot (slot0:), the second PCMCIA slot (slot1:), and tftp. Once you save the BOOT environment variable to your startup configuration, the RSM checks the variable upon startup to determine the device and filename of the image to boot.
The RSM tries to boot the first image in the BOOT environment variable list. If the RSM is unsuccessful at booting that image, it tries to boot the next image specified in the list. The RSM tries each image in the list until it successfully boots. If the RSM cannot boot any image in the BOOT environment variable list, it then attempts to boot the rxboot image.
If an entry in the BOOT environment variable list does not specify a device, the RSM assumes the device is tftp. If an entry in the BOOT environment variable list specifies an invalid device, the RSM skips that entry.
The BOOTLDR environment specifies the Flash device and filename containing the rxboot image that the ROM monitor uses. The valid devices are bootflash:, slot0:, and slot1:.
This environment variable allows you to have several rxboot images. Moreover, you can instruct the ROM monitor to use a specific rxboot image without having to switch out ROMs. Once you save the BOOTLDR environment variable to your startup configuration, the RSM checks the variable upon startup to determine which rxboot image to use.
The CONFIG_FILE environment variable specifies the device and filename of the configuration file to use for initialization (startup). The valid devices are bootflash:, nvram:, slot0:, and slot1:. Once you save the CONFIG_FILE environment variable to your startup configuration, the RSM checks the variable upon startup to determine the location and filename of the configuration file to use for initialization.
The RSM uses the NVRAM configuration during initialization when the CONFIG_FILE environment variable does not exist or when it is null (such as at first-time startup). If the RSM detects a problem with NVRAM or the configuration it contains, the RSM enters setup mode.
Although the ROM monitor controls environment variables, you can create, modify, or view them with certain system image commands. To create or modify the BOOT, BOOTLDR, and CONFIG_FILE environment variables, use the boot system, boot bootldr, and boot config system image commands, respectively.
Note When you use these three global configuration commands, you affect only the running configuration. You must save the environment variable settings to your startup configuration to place the information under ROM monitor control and to ensure the environment variables function as expected. Use the copy running-config startup-config command to save the environment variables from your running configuration to your startup configuration.
You can view the contents of the BOOT, BOOTLDR, and the CONFIG_FILE environment variables by issuing the show boot command. This command displays the settings for these variables as they exist in the startup configuration as well as in the running configuration if a running configuration setting differs from a startup configuration setting.
Use the show startup-config command to display the contents of the configuration file pointed to by the CONFIG_FILE environment variable.
For complete information on the commands presented in this section, refer to the Access and Communication Servers Command Reference publication.
An overview for recovering a lost password follows:
Note A key to recovering a lost password is to set the configuration register so that the contents of NVRAM are ignored (0x0040), allowing you to see your password.
To recover a lost password, follow these procedures.
Step 2 Configure the terminal to operate at 9600 baud, 8 data bits, no parity, 2 stop bits (or to the existing RSM settings).
Step 3 Enter the show version command to display the existing configuration register value. Note this value for later use in Step 13.
Step 4 If Break is disabled, power-cycle the RSM. (To power-cycle, remove the RSM from the switch backplane, wait five seconds, and then reinsert the RSM.) If Break is enabled on the RSM, press the Break key or send a break (^[) and then proceed to Step 5.
Step 5 Within 60 seconds of turning on the RSM, press the Break key. This action causes the terminal to display the bootstrap program prompt:
Step 6 Set the configuration register to ignore the configuration file information as follows:
Step 7 Initialize the RSM by entering the i command as follows:
The RSM will power-cycle, the configuration register will be set to ignore the configuration file, and the RSM will boot the boot system image and prompt you with the system configuration dialog as follows:
Step 8 Enter no in response to the system configuration dialog prompts until the following system message is displayed:
Step 9 Press Return. After some interface information, the prompt appears as follows:
Step 10 Enter the enable command to enter the enabled mode. The prompt changes to the following:
Step 11 Enter the show configuration EXEC command to display the enable password in the configuration file.
Step 12 Enter the configure terminal command at the EXEC prompt. You are prompted as follows:
Step 13 Using the config-register 0x<value> command, change the configuration register value back to its original value (noted from Step 3) or change it to a value of 0x2102 (factory default).
Step 14 Exit Configuration mode by entering Ctrl-Z.
Step 15 Reboot the RSM and enable it using the recovered password.
This completes the procedure for recovering from a lost password.
Note Some of the Cisco IOS features that appear in the software and are described in this section, are not available for this release of the RSM. Refer to "Features," for a complete list of supported features.
The Cisco IOS software user interface has several different command modes (see Figure 5). Each command mode has a group of related commands. This section describes how to access and list the commands available in each command mode.
For a complete description of the commands mentioned in this section, refer to the "User Interface Commands" chapter in the Access and Communication Servers Command Reference publication.
The EXEC command interpreter interprets the commands you type and carries out the corresponding operations. You must log in to the RSM before you can enter an EXEC command. For security purposes, the EXEC has two levels of access to commands: user and privileged. The EXEC commands available at the user level are a subset of the EXEC commands available at the privileged level. From the privileged level, you can also access global configuration mode and six specific configuration modes: interface, subinterface, line, router, ipx-router, and route-map configuration.
Almost every system configuration command also has a no form. In general, use the no form to disable a feature or function. Use the command without the keyword no to reenable a disabled feature or enable a feature that is disabled by default. For example, IP routing is enabled by default. Specify the command no ip routing to disable IP routing and specify ip routing to reenable it. The Access and Communication Servers Command Reference publication provides the complete syntax for every command and describes what the no form of a command does.
If your RSM does not find a valid system image, or if its configuration file is corrupted at startup, the system might enter ROM Monitor mode.
Entering a question mark (?) at the system prompt allows you to obtain a list of commands available for each command mode.
This section describes how to access each of the RSM command modes:
Figure 5 tracks how you move from the login prompt to specific configuration modes. To access the level you want, enter the command (or a form of the command) shown below the level. For example, to enter Global Configuration mode, enter configure command. To quit this mode and go back to Privileged EXEC (denoted by the backward arrow over Global Config), enter exit or ^z. To move forward (denoted by the forward arrow over Global Config) to interface configuration, enter interface command. To move backward to Global Config, enter exit or ^z.
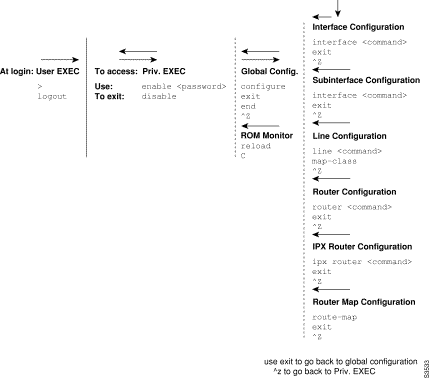
Table 5 lists the command modes, how to access each mode, the prompt you will see while you are in that mode, and the method to exit a mode. The prompts listed assume the default RSM name, router.
Table 5 Summary of Command Modes
After you log in to the RSM, you are automatically in user EXEC command mode. The EXEC commands available at the user level are a subset of those available at the privileged level. In general, the user EXEC commands allow you to establish connections, change terminal settings on a temporary basis, perform basic tests, and list system information.
To list the user EXEC commands, complete the following task:
The user-level prompt consists of the RSM host name followed by an angle bracket (>):
You can change the RSM name using the hostname global configuration command described in the "System Management Commands" chapter in the Access and Communication Servers Command Reference publication.
Because many of the privileged commands set operating parameters, privileged access should be password-protected to prevent unauthorized use. The privileged command set includes those commands contained in user EXEC mode, as well as the configure command through which you can access the remaining command modes. Privileged EXEC mode also includes high-level testing commands, such as debug. For details on the debug command, see the Debug Command Reference publication.
To access and list the privileged EXEC commands, complete the following steps:
If the system administrator has set a password, you are prompted to enter it before being allowed access to privileged EXEC mode. The password is not displayed on the screen and is case sensitive. The system administrator uses the enable password global configuration command to set the password that restricts access to privileged mode. This command is described in the "System Management Commands" chapter in the Access and Communication Servers Command Reference publication.
The privileged-level prompt consists of the RSM host name followed by the pound sign (#). (If the RSM was named with the hostname command, that name would appear as the prompt instead of "router.")
From the privileged level, you can access Global Configuration mode. For instructions, see "Global Configuration Mode," which follows this section.
To return from privileged EXEC mode to user EXEC mode, perform the following task:
Global configuration commands apply to features that affect the system as a whole. Use the configure privileged EXEC command to enter Global Configuration mode. When you enter this command, the EXEC prompts you for the source of the configuration commands:
Configuring from terminal, memory, or network [terminal]?
You can then specify either the terminal, NVRAM, or a file stored on a network server as the source of configuration commands (see the "System Image and Configuration File Load Commands" chapter in the Access and Communication Servers Command Reference publication). The default is to enter commands from the terminal console. Pressing the Return key begins this configuration method.
To access and list the global configuration commands, complete the following tasks:
| Task | Command |
|---|---|
| Step 1. At the terminal, from the privileged EXEC mode, enter Global Configuration mode. | |
| Step 2. List the Global Configuration commands. |
| 1This command is documented in the "System Image and Configuration File Load Commands" chapter in the Access and Communication Servers Command Reference publication. |
To exit Global Configuration mode and return to privileged EXEC mode, use one of the following commands:
From Global Configuration mode, you can access seven configuration sublevels: interface, subinterface, line, router, ipx-router, route-map, and ROM monitor configuration commands. These command modes are described in the following sections.
Many features are enabled on a per-interface basis. Interface configuration commands modify the operation of an interface such as a VLAN interface. Interface configuration commands always follow an interface command, which defines the interface type.
To access and list the interface configuration commands, complete the following steps:
| Task | Command |
|---|---|
| Step 1. From Global Configuration mode, enter Interface Configuration mode. | |
| Step 2. List the interface configuration commands. |
| 1This command is documented in the "Interface Commands" chapter in the Access and Communication Servers Command Reference publication. |
To exit Interface Configuration mode and return to Global Configuration mode, enter the exit command. To exit Configuration mode and return to privileged EXEC mode, press Ctrl-Z.
Router configuration commands configure a routing protocol and always follow a router command. To access and list the router configuration commands, complete the following steps:
| Task | Command |
|---|---|
| Step 1. From Global Configuration mode, enter router configuration mode. | |
| Step 2. List the router configuration commands. |
| 1This command is documented in the "IP Routing Protocols Commands" chapter in the Access and Communication Servers Command Reference publication. |
To list the available router configuration keywords, enter the router command followed by a space and a question mark (?) at the global configuration prompt:
In the following example, the RSM is configured to support the Routing Information Protocol (RIP). The new prompt is router(config-router)#. Enter a question mark (?) to list router configuration commands.
The list of commands might vary slightly from this example, depending upon how your RSM has been configured.
To exit Router Configuration mode and return to Global Configuration mode, enter the exit command. To exit Configuration mode and return to privileged EXEC mode, press Ctrl-Z.
Internet Packet Exchange (IPX) is a Novell network-layer protocol. To access and list the IPX routing configuration commands, complete the following steps:
| Task | Command |
|---|---|
| Step 1. From Global Configuration mode, enter IPX-Router Configuration mode. | |
| Step 2. List the IPX-Router configuration commands. |
| 1This command is documented in the "Novell IPX Commands" chapter in the Access and Communication Servers Command Reference publication. |
In the following example, IPX RIP routing is configured. The new prompt is Router(config-ipx-router):
To exit IPX-Router Configuration mode and return to Global Configuration mode, enter the exit command. To exit Configuration mode and return to privileged EXEC mode, press Ctrl-Z.
Use the Route-Map Configuration mode to configure routing table and source and destination information. To access and list the route-map configuration commands, complete the following tasks:
| Task | Command |
|---|---|
| Step 1. From Global Configuration mode, enter Route-Map Configuration mode. | |
| Step 2. List the route-map configuration commands. |
| 1This command is documented in the "IP Routing Protocols Commands" chapter in the Access and Communication Servers Command Reference publication. |
In the following example, a route map named arizona1 is configured. The new prompt is
Router(config-route-map). Enter a question mark (?) to list route-map configuration commands.
To exit Route-Map Configuration mode and return to Global Configuration Mode, enter the exit command. To exit Configuration mode and return to privileged EXEC mode, press Ctrl-Z.
If your RSM does not find a valid system image, or if its configuration file is corrupted at startup, the system might enter ROM Monitor mode. From ROM Monitor mode, you can boot the router or perform diagnostic tests.
You can also enter ROM Monitor mode by entering the reload EXEC command and then pressing the Break key during the first 60 seconds of startup. To save changes to the configuration file before reloading, use the copy running-config startup-config command before issuing the reload command.
To access and list the ROM monitor configuration commands, complete the following tasks:
| Task | Command |
|---|---|
| Step 1. Enter ROM Monitor mode from privileged EXEC mode. |
reload1 |
| Step 2. List the ROM monitor commands. |
| 1This command is documented in the "System Image and Configuration File Load Commands" chapter of the Access and Communication Servers Command Reference publication. |
The ROM monitor prompt is an angle bracket (>). The following example shows how to list the ROM monitor commands.
To return to user EXEC mode, enter c to continue. To boot the system image file, use the b command (described in the "System Image and Configuration File Load Commands" chapter in the Access and Communication Servers Command Reference publication).
This section describes how Catalyst switch commands work with the RSM. Included are those commands that have no effect on the RSM.
Screen displays that show ports in <module>/<port> format, such as show vlan, show the RSM port as <module>/1.
In the following examples, the Catalyst switch has the supervisor engine in slot 1, a 24-port Ethernet line card in slot 2, the RSM in slot 4, and an ATM card in slot 5.
From the standpoint of the user, the RSM has one port. Therefore, all encoded address recognition logic (EARL) entries that refer to an RSM show m/1, where m is the slot number of the RSM. For example, show cam <mac>, where <mac> is an RSM MAC address, displays:
show cdp neighbor shows information received on an RSM port. Since the RSM port connects only to the RSM, only information about the RSM is displayed. Any information received by the RSM on its external port is visible only from the RSM.
show cdp port functions the same on an RSM port as on other trunking ports.
The RSM LCP firmware is specific to the RSM. The LCP firmware version is displayed on the
lcp c5ip line below.
Displays the system error log.
Displays the following message for the RSM switch slot: "Use `session' command to see ATM and router counters."
"FW" is the RSM Catalyst switch interface processor version and "SW" is the Cisco IOS version.
Functions the same on an RSM port as on other trunking ports.
Functions the same on an RSM port as on other trunking ports.
Does not provide information on the RSM port.
Displays the message: "Use `session' command to see ATM and router counters."
Displays the message: "Use `session' command to see router counters."
Shows the power-up diagnostic results:
The RSM port displays as a port that is always trunking, with allowed and active VLANs for each VLAN configured on the RSM. The following example shows the RSM configured on
VLANs 2 and 3:
Shows the current hardware and software versions:
"FW" is the RSM Catalyst switch interface processor version, "SW" is the Cisco IOS version, and "FW1" is the RSM local control processor (LCP) boot code version.
Displays VLAN information about the RSM port. Using show with no parameters does not list the RSM port as part of the VLANs, but show n includes the RSM port if the RSM is active on port n.
Functions the same on an RSM port as on other trunking ports.
Displays the message: "Feature not supported on module n."
Functions the same on an RSM port as on other trunking ports.
Sets the module name for the RSM. All other set module commands display the message:
"Feature not supported on module n."
Sets the port name for the RSM. All other set port commands display the message:
"Feature not supported on module n."
Specifying an RSM port as a source port in set span is allowed, but specifying an RSM port as the destination port displays the message: "Route switch port cannot be a Monitor Port."
set spantree (portcost|portmode|portpri) functions the same on an RSM port as on other trunking ports.
set spantree (portfast|portvlanpri) displays the message:
"Feature not supported on module n."
Displays the message: "Feature not supported on module n."
You cannot change the set of VLANs allowed on the RSM port. Any use of the set trunk command displays the message: "Feature not supported on module n."
Specifiying an RSM port in set vlan displays the message: "Use `session' command to configure Vlan router."
Clears the portion of the RSM configuration kept by the Catalyst switch supervisor engine. The portion of the configuration kept by the RSM must be cleared at the router level (router> prompt).
Use the session command to toggle between the router and switch sessions (mod/num is the RSM slot number).
Where n is the RSM, causes a complete reset of the RSM hardware and software.
Displays the message: "Use `session' command to download to or upload from Route Switch."
This section provides basic VLAN configuration information for configuring VLANs on your Catalyst switch. For configuring the VLANs for routing, refer to "Configuring the Route Switch Module for InterVLAN Routing,".
For more extensive VLAN information, refer to the Catalyst 5000 Series Software Configuration Guide and the Catalyst 5000 Series Command Reference publications.
A VLAN is a group of end stations, independent of physical location, with a common set of requirements. For example, several end stations might be grouped as a department, such as engineering or accounting. If the end stations are located close to one another, they can be grouped into a LAN segment. If any of the end stations are on a different LAN segment, such as different buildings or locations, they can be grouped together into a VLAN that has all the same attributes as a LAN even though the end stations are not all on the same LAN segment. The information identifying a packet as part of a specific VLAN is preserved across a Catalyst switch connection to a router or other Catalyst switch with an RSM.
Note The commands used to set up and configure VLANs are Catalyst switch-specific commands and are to be entered at the Cat5k> prompt.
To define the VLAN, indicate the VLAN number, name, type, maximum transmission unit, SAID, state, ring number, bridge identification number, and number to indicate whether source routing should be set to transparent or bridging.
To create a VLAN across a management domain, perform the following steps in privileged mode:
A VLAN created in a management domain remains unused until it is mapped to Catalyst switch ports. The set vlan command maps VLANs to ports. The default configuration has all switched Ethernet ports on VLAN 1. However, you can enter groups of ports as individual entries, for example, 2/1,3/3,3/4,3/5. You can also use a hyphenated format, for example, 2/1,3/3-5. Figure 6 shows a local VLAN configuration that groups switch ports into VLAN 10 and VLAN 20.
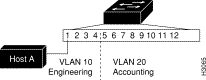
To create a VLAN, perform the following task in privileged mode:
After entering the set vlan command, you see the following screen:
To verify that the VLAN configuration is correct, use the show vlan command. After entering the show vlan command, you see the following screen:
The DRAM resides on up to four SIMMs on the RSM. The DRAM SIMM sockets are U31 and U20 for bank 0, and U14 and U6 for bank 1. The default DRAM configuration is 32 MB (two 16-MB SIMMs in bank 0 with bank 1 left empty). (See Figure 7.)
Note The total number of memory devices per SIMM differs for each manufacturer. The SIMMs in the following illustrations are generic representations of the actual DRAM SIMMs for your RSM.
This section describes the steps for increasing the amount of DRAM by replacing up to four SIMMs that you obtain from an approved vendor.
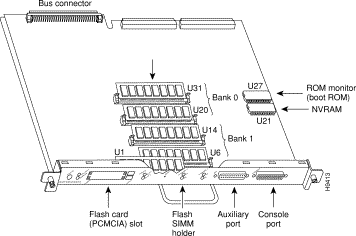
The SIMM sockets use the thumb tabs that are often used in PCs and other computer equipment. Each RSM SIMM socket has two metal retaining springs, one at each end. (See Figure 8.) When a SIMM is fully seated in the socket, the retaining springs snap over the ends of the SIMM to lock it in the socket.
Table 6 lists the various configurations of DRAM SIMMs that are available. Note that you must have either 32-MB, 64-MB, or 128-MB DRAM; you cannot use any other combinations. SIMMs must be 60 ns or faster and no taller than one inch.
Table 6 DRAM SIMM Configurations
| DRAM Bank 0 | Quantity | DRAM Bank 1 | Quantity | Total DRAM |
Place removed SIMMs on an antistatic mat and store them in an antistatic bag. You can use the SIMMs that you remove in compatible equipment.
Follow these steps to remove the existing SIMMs:
Step 2 The RSM is secured with two captive installation screws. Use a 1/4-inch flat-blade screwdriver to loosen the captive installation screws, and then remove the RSM using the ejector levers. Place the RSM on an antistatic mat.
Step 3 Position the RSM so that the front panel is away from you and the edge connector is toward you.
Step 4 Locate the SIMMs. The DRAM SIMMs occupy U31 and U20 in bank 0, and U14 and U6 in bank 1. (See Figure 7.)
Step 5 Release the spring clips from the SIMM that you want to remove and release the SIMM from the socket. (See Figure 8.)

Step 6 When both ends of the SIMM are released from the socket, grasp the ends of the SIMM with your thumb and forefinger and pull the SIMM completely out of the socket. Handle the edges of the SIMM only; avoid touching the memory module or pins, and the metal traces, or fingers, along the socket edge.
Step 7 Place the SIMM in an antistatic bag.
Step 8 Repeat Steps 4 through 7 for the remaining SIMMs, as required for your upgrade.
This completes the SIMM removal procedure. Proceed to the next section to install the new SIMMs.
Following is the procedure for installing new SIMMs.
Follow these steps to install the new SIMMs:
Step 2 Remove a new SIMM from the antistatic bag.
Step 3 Hold the SIMM component side up, with the connector edge (the metal fingers) closest to you. Hold the sides of the SIMM between your thumb and middle finger, with your forefinger against the far edge, opposite the connector edge. (See Figure 9.)
Step 4 Tilt the SIMM to approximately the same angle as the socket and insert the entire connector edge into the socket. (Install the first SIMM in the slot farthest away from you. Install the last SIMM in the slot closest to you.)
Step 5 Gently push the SIMM into the socket until the spring clips snap over the ends of the SIMM. If necessary, rock the SIMM gently back and forth to seat it properly.
Step 6 Repeat Steps 2 through 5 for the remaining SIMMs.
Step 7 When all SIMMs are installed, check all alignment holes (two on each SIMM) and ensure that the spring retainer is visible. If it is not, the SIMM is not seated properly. If any SIMM appears misaligned, carefully remove it and reseat it in the socket. Push the SIMM firmly back into the socket until the retainer springs snap into place.
Step 8 Guide the RSM back into the switch slot, aligning the sides of the RSM with the guides in the slot (avoid touching the components on the RSM). While keeping the RSM oriented horizontally, carefully slide it into the slot until its front panel contacts the ejector levers.
Step 9 Using the thumb and forefinger of each hand, simultaneously push the left lever and the right lever in to fully seat the RSM in the backplane connector.
Step 10 Use a screwdriver to tighten the captive installation screws on the left and right sides of the module.
Step 11 Check the status of the module as follows:
If the system fails to boot properly, or if the console terminal displays a checksum or memory error, check the following:
If after several attempts the system fails to restart properly, contact a service representative for assistance. Before you call, make note of any error messages, unusual LED states, or any other indications that might help solve the problem.
Note The time required for the system to initialize varies with different router configurations. Routers with 128-MB DRAM take longer to boot than those with 32-MB DRAM.
This completes the SIMM replacement procedure.
The Flash memory (PCMCIA) card slots on the front panel of the RSM are for additional PCMCIA-based Flash memory. You can use this Flash memory to store and run Cisco IOS images, or as a file server for other routers to access as clients. Occasionally, it might be necessary to remove and replace Flash memory cards; however, removing Flash memory cards is not required and is not recommended after the cards are installed in the slots.
It might become necessary for you to replace or install a Flash memory card in your RSM. The RSM has two PCMCIA slots: slot 0 (bottom) and slot 1 (top). (See Figure 10.) The following procedure is generic and can be used for a Flash memory card in either slot position.
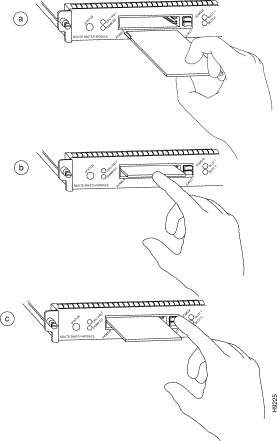
Before you install a card, verify that the Flash memory card is set with write protection off. The write protect switch is located on the front edge of the card when oriented with the printing right side up and the edge connector end away from you. (See Figure 11.)
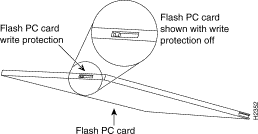
Following is the procedure for installing and removing a Flash memory card:
Step 2 Insert the card into the appropriate slot until the card completely seats in the connector at the back of the slot and the eject button pops out toward you (See Figure 10b.) Note that the card does not insert all the way inside the RSM; a portion of the card remains outside the slot. Do not attempt to force the card past this point.
Step 3 To eject a card, press the appropriate ejector button until the card is free of the connector at the back of the slot. (See Figure 10c.)
Step 4 Remove the card from the slot and place it in an antistatic bag.
The Flash memory (PCMCIA) card that shipped with your RSM contains the Cisco IOS software image. In some cases, you might need to insert a new Flash memory card and copy images or back up configuration files onto it. Before you can use a new Flash memory card, you must format it.
PCMCIA Flash memory cards must either be formatted on the RSM or on an RSP-based 7500 series router running software at the same level, or greater, as the RSM. Flash memory cards previously formatted on an RP-based Cisco 7000 series router cannot be used on the RSM. Note that Flash memory cards formatted on the RSM can be used on RSP-based 7500 series routers (but not on RP-based 7000 series routers).
Use the following procedure to format a new Flash memory card:
Step 2 To format the Flash memory card, use the format slot0: (or format slot1:) command as follows. (Use only Intel Series 2+ Flash memory cards.)
Note For this example, a 16-MB Flash memory card was used, and at the line "Formatting sector," the system counted the card sectors backwards from 128 to 1 as it formatted them. For 20-MB Flash memory cards, the system counts backwards from 160 to 1.
The new Flash memory card is now formatted and ready to use.
Use the following series of commands to make the image (the file named new.image) bootable. Note that, since the configuration register must be set to 0x2102, the config-register command is part of the sequence.
When the system reloads, it will boot the image new.image from the Flash memory card in slot 0.
With the Flash memory card formatted, you can now copy a bootable image into it. To copy an image, use the following procedure, which assumes the following:
Note To assure access to a TFTP sever, you need to configure at least one interface using the setup command facility. For instructions on using this procedure, refer to the Configuration Fundamentals Configuration Guide.
Following is the procedure for copying a bootable file (called new.image) into the Flash memory card:
Step 2 Insert an unformatted Flash memory card and format it using the procedure in "Formatting a Flash Memory Card," and then proceed to Step 3.
Note If you have already formatted a Flash memory card, you can use it instead; however, you cannot boot from or use a Flash memory card formatted on another type of system. You must reformat it to use it as a boot or storage source.
Step 3 To enable the RSM, copy the image new.image to the Flash memory card, make this image in the Flash memory card (in slot 0) the default boot image, and reboot the RSM, using the following series of commands:
Note In the preceding example, the exclamation points (!!!) appear as the file is downloaded and the "C" characters signify calculation of the checksum, which is a verification that the file has been correctly downloaded to the Flash memory card.
When the system reloads, it boots the image new.image from the Flash memory card in slot 0.
As future releases of Cisco IOS images become available, you receive these images either as a netbooted file, a file on floppy disk, or a file on a Flash memory card.
The following scenario describes how to use a newly released image on a Flash memory card in a system that has an older image on a Flash memory card in slot 0 (and a default boot image in the onboard Flash SIMM).
For this scenario, the filenames are as follows:
Copy the new image from the new Flash memory card onto the Flash memory card that contains the old image.
Note This scenario assumes that the new image will fit on the Flash memory card in slot 0, next to the old image. If there is not enough available space, use the delete command to delete files from the Flash memory card to make sufficient room for the new image; however, do not delete the image.old file. Then use the squeeze command to remove these deleted files from the Flash memory card. If, after you have deleted files and used the squeeze command, the two files cannot coexist on the Flash memory card in slot 0, remove this card (place it in an anti-static bag and store it in a safe place), and then insert the new Flash memory card (with the file image.new) in slot 0. Proceed to Step 5 and use the command boot system flash slot0:image.new to designate the file image.new as the default boot image.
Step 2 Enable the RSM as follows:
Step 3 Insert the new Flash memory card in slot 1.
Step 4 Use the following command to copy the file image.new in slot 1 to the Flash memory card in slot 0 only if there is enough memory space for the two images to coexist. If there is not enough memory space, proceed to Step 5.
Step 5 Use the following series of commands to designate the file image.new (which is in the Flash memory card in slot 0) as the default boot image:
When the system reloads, it boots the file image.new from the Flash memory card in slot 0.
A locked block of Flash memory occurs when power is lost or a Flash memory card is unplugged during a write or erase operation. When a block of Flash memory is locked, it cannot be written to or erased, and the operation consistently fails at a particular block location. The only way to recover from locked blocks is by reformatting the Flash memory card with the format command.
This section provides procedures to connect a terminal to the console port and a modem to the auxiliary port. (See Figure 12.)
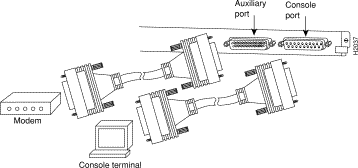
Note Both the console and auxiliary ports are asynchronous serial ports; any devices connected to these ports must be capable of asynchronous transmission. This is the most common type of serial device; for example, most modems are asynchronous devices.
The console port on the RSM is an EIA/TIA-232, DCE, DB-25 receptacle for connecting a data terminal. Both DSR and DCD are active when the RSM is running. The RTS signal tracks the state of the CTS input. The console port requires a straight-through EIA/TIA-232 cable. Table 7 lists the signals used on this port.
Before connecting the console port, check your terminal's documentation to determine its baud rate, which must match the default baud rate (9600 baud) of the console port on the RSM. Set up the terminal as follows: 9600 baud, 8 data bits, no parity, 2 stop bits.
Table 7 RSM Console Port Signals
| Pin | Signal | Direction | Description |
|---|---|---|---|
The auxiliary port on the RSM is an EIA/TIA-232 DTE, DB-25 plug to which you can attach a modem or other DCE device such as a channel service unit/data service unit (CSU/DSU) or router. Table 8 lists the EIA/TIA-232 signals used on this port.
Table 8 Auxiliary Port Signals
| Pin | Signal | Direction | Description |
|---|---|---|---|
Cisco Connection Online (CCO) is Cisco Systems' primary, real-time support channel. Maintenance customers and partners can self-register on CCO to obtain additional information and services.
Available 24 hours a day, 7 days a week, CCO provides a wealth of standard and value-added services to Cisco's customers and business partners. CCO services include product information, product documentation, software updates, release notes, technical tips, the Bug Navigator, configuration notes, brochures, descriptions of service offerings, and download access to public and authorized files.
CCO serves a wide variety of users through two interfaces that are updated and enhanced simultaneously: a character-based version and a multimedia version that resides on the World Wide Web (WWW). The character-based CCO supports Zmodem, Kermit, Xmodem, FTP, and Internet e-mail, and it is excellent for quick access to information over lower bandwidths. The WWW version of CCO provides richly formatted documents with photographs, figures, graphics, and video, as well as hyperlinks to related information.
You can access CCO in the following ways:
For a copy of CCO's Frequently Asked Questions (FAQ), contact cco-help@cisco.com. For additional information, contact cco-team@cisco.com.
Note If you are a network administrator and need personal technical assistance with a Cisco product that is under warranty or covered by a maintenance contract, contact Cisco's Technical Assistance Center (TAC) at 800 553-2447, 408 526-7209, or tac@cisco.com. To obtain general information about Cisco Systems, Cisco products, or upgrades, contact 800 553-6387, 408 526-7208, or cs-rep@cisco.com.
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
Posted: Sat Jan 18 12:48:24 PST 2003
All contents are Copyright © 1992--2002 Cisco Systems, Inc. All rights reserved.
Important Notices and Privacy Statement.