|
|

This chapter describes how Virtual Trunk Protocol (VTP) works, how you configure it, and how you add VLANs to a VLAN network managed by VTP. For complete syntax and usage information on the commands described in this chapter, refer to the Cisco IOS Desktop Switching Command Reference (online only).
These sections describe how to configure VTP and VLANs:
Cisco IOS 11.2(8)SA6 supports the grouping of switches into clusters. A cluster is up to 16 switches that can be managed as a single entity. The command switch is the single point of management for the cluster. Member switches are managed through the command switch.
If you are configuring VLANs on a member switch, you might need to enter an extra command from the command switch CLI to access the member switch. When configuring port parameters, for example, you can use the privileged EXEC rcommand command and the member number to display the member switch CLI.
See the Cisco IOS Desktop Switching Software Configuration Guide for more information on managing clusters.
Before you create VLANs, you must decide whether to use VTP in your network. Using VTP, you can make configuration changes centrally on a single switch, such as a
Catalyst 2900 series XL, and have those changes automatically communicated to all the other switches in the network. Without VTP, you cannot send information about VLANs to other switches.
VTP is a Layer 2 messaging protocol that maintains VLAN configuration consistency by managing the addition, deletion, and renaming of VLANs on a network-wide basis. VTP minimizes misconfigurations and configuration inconsistencies that can cause several problems, such as duplicate VLAN names, incorrect VLAN-type specifications, and security violations.
A VTP domain (also called a VLAN management domain) is one switch or several interconnected switches sharing the same VTP domain. A switch is configured to be in only one VTP domain. You make global VLAN configuration changes for the domain by using the CLI, Cisco Visual Switch Manager (CVSM) software, or Simple Network Management Protocol (SNMP).
By default, a Catalyst 2900 series XL or Catalyst 3500 series XL switch is in the no-management-domain state until it receives an advertisement for a domain over a trunk link or you configure a management domain. The default VTP mode is server mode, but VLANs are not propagated over the network until a management domain name is specified or learned.
If the switch receives a VTP advertisement over a trunk link, it inherits the management domain name and configuration revision number. The switch then ignores advertisements with a different management domain name or an earlier configuration revision number.
When you make a change to the VLAN configuration on a VTP server, the change is propagated to all switches in the VTP domain. VTP advertisements are sent over all trunk connections, including Inter-Switch Link (ISL), IEEE 802.1Q, IEEE 802.10, and Asynchronous Transfer Mode (ATM) LAN Emulation (LANE).
If you configure a switch from VTP transparent mode, you can create and modify VLANs, but the changes are not transmitted to other switches in the domain, and they affect only the individual switch.
When you upgrade from a software version that supports VLANs but does not support VTP, such as Cisco IOS Release 11.2(8)SA3, to a version that does support VTP, ports that belong to a VLAN retain their VLAN membership, and VTP enters transparent mode. The domain name becomes UPGRADE, and VTP does not propagate the VLAN configuration to other switches.
If you want to propagate the VLAN configuration to other switches, configure the switch to operate as a VTP server, and change the domain name.
You can configure a supported switch to be in one of the following VTP modes:
Two configurations can cause a switch running this version of software to automatically change VTP mode:
The "VTP Configuration Guidelines" section provides tips and caveats for configuring VTP.
Each switch in the VTP domain sends these periodic global configuration advertisements from each trunk port to a reserved multicast address. Neighboring switches receive these advertisements and update their VTP and VLAN configurations as necessary.
The following global domain information is distributed in VTP advertisements:
The following VLAN information is distributed in VTP advertisements for each configured VLAN:
VTP version 2 supports the following features not supported in version 1:
Although switches supported by this IOS release are never eligible for VTP pruning, a supported switch does propagate VTP pruning messages. This section describes the role that a supported switch can play in a VTP pruning network.
VTP pruning increases available bandwidth by restricting flooded traffic to those trunk links that the traffic must use to access the appropriate network devices. When VTP pruning is enabled, it can block flooded traffic to VLANs that are included in the pruning-eligible list. Switches supported by this IOS release are never in the pruning-eligible list, and no switch traffic is pruned. Flooding occurs as usual, and switches connected to the
supported switch do not benefit from pruning.
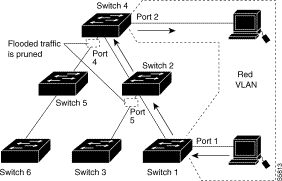
Figure 2-1 shows a switched network with VTP pruning enabled. The broadcast traffic from Switch 1 is not forwarded to Switches 5 and 6 because traffic for the Red VLAN has been pruned on the links indicated (Port 4 on Switch 4). Switch 2 does not prune the traffic destined for Switch 4 or Switch 3.
Follow these guidelines when implementing VTP in your network:
 | Caution If you configure a VTP password, the management domain will not function properly if you do not assign the management domain password to each switch in the domain. |
Table 2-1 shows the default VTP configuration.
| Feature | Default Value |
|---|---|
VTP domain name | Null. |
VTP mode | Server. |
VTP version 2 enable state | Version 2 is disabled. |
VTP password | None. |
VTP pruning | Disabled. |
You configure VTP by entering commands from the VLAN database configuration command mode. You display the status of VTP by entering the privileged EXEC mode show vtp status command.
When you enter the exit command in VLAN database mode, it applies to all the commands that you entered. VTP messages are sent to other switches in the management domain, and you are returned to privileged EXEC mode.
For more information about these commands, refer to the Cisco IOS Desktop Switching Command Reference.
When a switch is in VTP server mode, you can change the VLAN configuration and have it propagate throughout the network. To configure the switch as a VTP server, perform this task from privileged EXEC mode:
| Task | Command |
|---|---|
Step 1 Enter VLAN configuration mode. | vlan database |
Step 2 Configure a VTP administrative-domain name. This can be from 1 to 32 characters. | vtp domain domain-name |
Step 3 (Optional) Set a password for the VTP domain. The password can be from 8 to | vtp password password-value |
Step 4 Configure the switch as a server. | vtp server |
Step 5 Return to privileged EXEC mode. | exit |
Step 6 Verify the VTP configuration. | show vtp status |
This example shows how to enter a VTP domain name and configure the switch as a VTP server:
Switch# vlan database
Switch(vlan)# vtp domain Building_A
Setting VTP domain name to Building_A
Switch(vlan)# vtp domain Building_A password LAVA
Domain name already set to Building_A .
Setting device VLAN database password to LAVA.
Switch(vlan)# vtp server
Setting device to VTP SERVER mode.
Switch(vlan)# exit
APPLY completed.
Exiting....
Switch# show vtp status
VTP Version : 2
Configuration Revision : 0
Maximum VLANs supported locally : 68
Number of existing VLANs : 6

VTP Operating Mode : Server

VTP Domain Name : Building_A
VTP Pruning Mode : Disabled
VTP V2 Mode : Disabled
VTP Traps Generation : Disabled
MD5 digest : 0x09 0xF6 0x57 0x1C 0xC9 0x6F 0x75 0x16
When a switch is in VTP client mode, you cannot change its VLAN configuration. The client switch receives VTP updates from a VTP server in the management domain and then modifies its configuration accordingly.
To configure the switch as a VTP client, perform this task from privileged EXEC mode:
| Task | Command |
|---|---|
Step 1 Enter VLAN configuration mode. | vlan database |
Step 2 Place the switch in VTP client mode. | vtp client |
Step 3 Update the VLAN database, propagate it throughout the administrative domain, and return to privileged EXEC mode. | exit |
Step 4 Verify the VTP configuration. | show vtp status |
This example shows how to configure the switch as a VTP client and verify the configuration:
Switch# vlan database
Switch(vlan)# vtp client
Setting device to VTP CLIENT mode.
Switch(vlan)# exit
In CLIENT state, no apply attempted.
Exiting....
Switch# show vtp status
VTP Version : 2
Configuration Revision : 0
Maximum VLANs supported locally : 68
Number of existing VLANs : 6

VTP Operating Mode : Client
VTP Domain Name : Building_A
VTP Pruning Mode : Disabled
VTP V2 Mode : Disabled
VTP Traps Generation : Disabled
MD5 digest : 0x09 0xF6 0x57 0x1C 0xC9 0x6F 0x75 0x16
Configuration last modified by 172.20.130.40 at 3-5-93 22:15:25
When you configure the switch as VTP transparent, you disable VTP on the switch. The switch then does not send VTP updates and does not act on VTP updates received from other switches. However, a VTP transparent switch does forward received VTP advertisements on all of its trunk links.
To put the switch in VTP transparent mode, perform this task from privileged EXEC mode:
| Task | Command |
|---|---|
Step 1 Enter VLAN configuration mode. | vlan database |
Step 2 Place the switch in VTP transparent mode | vtp transparent |
Step 3 Return to privileged EXEC mode. | exit |
Step 4 Verify the VTP configuration. | show vtp status |
This example shows how to configure the switch as VTP transparent and verify the configuration:
Switch# vlan database
Switch(vlan)# vtp transparent
Setting device to VTP TRANSPARENT mode.
Switch(vlan)# exit
APPLY completed.
Exiting....
Switch# show vtp status
VTP Version : 2
Configuration Revision : 0
Maximum VLANs supported locally : 68
Number of existing VLANs : 6

VTP Operating Mode : Transparent
VTP Domain Name : Building_A
VTP Pruning Mode : Disabled
VTP V2 Mode : Disabled
VTP Traps Generation : Disabled
MD5 digest : 0x09 0xF6 0x57 0x1C 0xC9 0x6F 0x75 0x16
Configuration last modified by 172.20.130.40 at 3-5-93 22:15:25
VTP version 2 is disabled by default on VTP version 2-capable switches. When you enable VTP version 2 on a switch, every VTP version 2-capable switch in the VTP domain enables version 2.
 | Caution VTP version 1 and VTP version 2 are not interoperable on switches in the same VTP domain. Every switch in the VTP domain must use the same VTP version. Do not enable VTP version 2 unless every switch in the VTP domain supports version 2. |
To enable VTP version 2, perform this task from privileged EXEC mode:
| Task | Command |
|---|---|
Step 1 Enter VLAN configuration mode. | vlan database |
Step 2 Enable VTP version 2 on the switch. | vtp v2-mode |
Step 3 Update the VLAN database, propagate it throughout the administrative domain, and return to privileged EXEC mode. | exit |
Step 4 Verify that VTP version 2 is enabled. | show vtp status |
This example shows how to enable VTP version 2 and verify the configuration:
Switch# vlan database
Switch(vlan)# vtp v2-mode
V2 mode enabled.
Switch(vlan)# exit
APPLY completed.
Exiting....
Switch# show vtp status
VTP Version : 2
Configuration Revision : 2
Maximum VLANs supported locally : 68
Number of existing VLANs : 14
VTP Operating Mode : Server
VTP Domain Name : milano
VTP Pruning Mode : Disabled

VTP V2 Mode : Enabled
VTP Traps Generation : Disabled
MD5 digest : 0xAC 0x23 0x2F 0x75 0x52 0xDC 0x17 0x70
Configuration last modified by 172.20.128.178 at 3-6-93 23:46:53
To disable VTP version 2, perform this task from privileged EXEC mode:
| Task | Command |
|---|---|
Step 1 Enter VLAN configuration mode. | vlan database |
Step 2 Disable VTP version 2. | no vtp v2-mode |
Step 3 Update the VLAN database, propagate it throughout the administrative domain, and return to privileged EXEC mode. | exit |
Step 4 Verify that VTP version 2 is disabled. | show vtp status |
This example shows how to disable VTP version 2:
Switch# vlan database
Switch(vlan)# no vtp v2-mode
V2 mode disabled.
Switch(vlan)# exit
In CLIENT state, no apply attempted.
Exiting....
Switch# show vtp status
VTP Version : 2
Configuration Revision : 0
Maximum VLANs supported locally : 68
Number of existing VLANs : 59
VTP Operating Mode : Client
VTP Domain Name : milano
VTP Pruning Mode : Disabled

VTP V2 Mode : Disabled
VTP Traps Generation : Disabled
MD5 digest : 0x53 0x97 0x06 0x02 0xF8 0x6F 0x45 0x85
Configuration last modified by 172.20.128.151 at 3-5-93 01:05:21
You monitor VTP by displaying its configuration information: the domain name, the current VTP revision, and the number of VLANs. You can also display statistics about the advertisements sent and received by the switch.
To monitor VTP activity, perform this task from privileged EXEC mode:
| Task | Command |
|---|---|
Step 1 Display the VTP switch configuration information. | show vtp status |
Step 2 Display counters about VTP messages being sent and received. | show vtp counters |
This example shows how to display the switch VTP status:
Switch# show vtp status
VTP Version : 2
Configuration Revision : 2
Maximum VLANs supported locally : 68
Number of existing VLANs : 6
VTP Operating Mode : Transparent
VTP Domain Name : Building_A
VTP Pruning Mode : Disabled
VTP V2 Mode : Disabled
VTP Traps Generation : Disabled
MD5 digest : 0xB9 0xC7 0x8D 0xB3 0xD4 0xBA 0x94 0x03
Configuration last modified by 172.20.130.40 at 3-9-93 20:12:24
This example shows how to display the VTP statistics:
Switch# show vtp counters
VTP statistics:
Summary advertisements received : 3
Subset advertisements received : 2
Request advertisements received : 0
Summary advertisements transmitted : 10
Subset advertisements transmitted : 10
Request advertisements transmitted : 1
Number of config revision errors : 0
Number of config digest errors : 0
Number of V1 summary errors : 0
VTP pruning statistics:
Trunk Join Transmitted Join Received Summary advts received from
non-pruning-capable device
---------------- ---------------- ---------------- ---------------------------
Fa1/1 8 6 0
Fa1/2 6 0 0
Fa1/3 6 0 0
Fa1/4 6 0 0
A VLAN is a group of end stations with a common set of requirements, independent of physical location. VLANs have the same attributes as a physical LAN, but you can group end stations even if they are not physically located on the same LAN segment.
VLANs on supported switches and other supported devices limit unicast, multicast, and broadcast traffic flooding. Flooded traffic originating from a particular VLAN is only flooded out other ports belonging to that VLAN.
Cisco IOS Release 11.2(8)SA6 supports the grouping of switches into clusters. A cluster is up to 16 switches that can be managed as a single entity. The command switch is the single point of management for the cluster. Member switches are managed through the command switch.
Switches in a cluster must be connected through ports that belong to VLAN 1, the default management VLAN.
If you are configuring VLANs on a member switch, you might need to enter an extra command from the command switch CLI to access the member switch. When configuring port parameters, for example, you can use the privileged EXEC rcommand command and the number of the member switch to display the member switch CLI. Once you have accessed the member switch, command mode changes and IOS commands operate as usual. Enter exit on the member switch in privileged EXEC mode to return to the command switch CLI.
See the Cisco IOS Desktop Switching Software Configuration Guide and the Cisco IOS Desktop Switching Command Reference for more information on managing clusters.
Ports that belong to VLANs are configured with a membership mode that determines what kind of traffic each port carries and how many VLANs it can belong to. Table 2-2 lists the membership modes and characteristics.
| Membership Mode | VLAN Membership Characteristics |
|---|---|
Can belong to one VLAN and is manually assigned. This is the default. | |
Can belong to up to 250 VLANs (some models only support 64 VLANs) and is manually assigned. A multi-VLAN port cannot be configured when there is a trunk configured on the switch. VLAN traffic on the multi-VLAN port is not encapsulated. | |
Can belong to one VLAN and is dynamically assigned by a VLAN Membership Policy Server (VMPS). | |
A trunk is a member of all VLANs in the VLAN database by default, but membership can be limited by configuring the allowed-VLAN list. |
Before you create VLANs, you must decide whether to use VTP to maintain global VLAN configuration information for your network. For complete information on VTP, refer to the "Understanding How VTP Works" section .
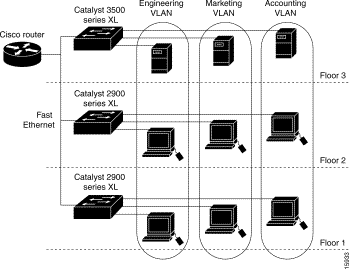
Figure 2-2 shows an example of VLANs segmented into logically defined networks.
You can set the following parameters when you add a VLAN to a VTP database:
The "Default VLAN Configurations" section lists the default values and possible ranges for each VLAN media type.
Although the Catalyst 2900 series XL and the Catalyst 3500 series XL do not support Token Ring connections, a remote device such as a Catalyst 5000 series switch with Token Ring connections could be managed from one of the supported switches. Switches running this IOS release advertise information about Token Ring VLANs when running VTP
version 2. The following Token Ring VLAN types are supported on the supported switches running VTP version 2:
For more information on configuring Token Ring VLANs, see the Catalyst 5000 Series Software Configuration Guide.
Follow these guidelines when creating and modifying VLANs in your network:
Table 2-3 through Table 2-7 shows the default configurations for the different VLAN media types.
| Parameter | Default | Range |
|---|---|---|
VLAN ID | 1 | 1-1005 |
VLAN name | VLANxxxx, where xxxx is the VLAN ID | No range |
802.10 SAID | 100000+VLAN ID | 1-4294967294 |
MTU size | 1500 | 1500-18190 |
Translational bridge 1 | 0 | 0-1005 |
Translational bridge 2 | 0 | 0-1005 |
VLAN state | active | active, suspend |
| Parameter | Default | Range |
|---|---|---|
VLAN ID | 1002 | 1-1005 |
VLAN name | VLANxxxx, where xxxx is the VLAN ID | No range |
802.10 SAID | 100000+VLAN ID | 1-4294967294 |
MTU size | 1500 | 1500-18190 |
Ring number | None | 1-4095 |
Parent VLAN | 0 | 0-1005 |
Translational bridge 1 | 0 | 0-1005 |
Translational bridge 2 | 0 | 0-1005 |
VLAN state | active | active, suspend |
| Parameter | Default | Range |
|---|---|---|
VLAN ID | 1004 | 1-1005 |
VLAN name | VLANxxxx, where xxxx is the VLAN ID | No range |
802.10 SAID | 100000+VLAN ID | 1-4294967294 |
MTU size | 1500 | 1500-18190 |
Bridge number | 0 | 0-15 |
STP type | ieee | auto, ibm, ieee |
Translational bridge 1 | 0 | 0-1005 |
Translational bridge 2 | 0 | 0-1005 |
VLAN state | active | active, suspend |
| Parameter | Default | Range |
|---|---|---|
VLAN ID | 1005 | 1-1005 |
VLAN name | VLANxxxx, where xxxx is the VLAN ID | No range |
802.10 SAID | 100000+VLAN ID | 1-4294967294 |
MTU size | VTPv1 1500; VTPv2 4472 | 1500-18190 |
Bridge number | VTPv1 0; VTPv2 user-specified | 0-15 |
STP type | ibm | auto, ibm, ieee |
Translational bridge 1 | 0 | 0-1005 |
Translational bridge 2 | 0 | 0-1005 |
VLAN state | active | active, suspend |
| Parameter | Default | Range |
VLAN ID | 1003 | 1-1005 |
VLAN name | VLANxxxx, where xxxx is the VLAN ID | No range |
802.10 SAID | 100000+VLAN ID | 1-4294967294 |
Ring Number | VTPv1 default 0; VTPv2 user-specified | 1-4095 |
Parent VLAN | VTPv1 default 0; VTPv2 user-specified | 0-1005 |
MTU size | VTPv1 default 1500; VTPv2 default 4472 | 1500-18190 |
Translational bridge 1 | 0 | 0-1005 |
Translational bridge 2 | 0 | 0-1005 |
VLAN state | active | active, suspend |
Bridge mode | srb | srb, srt |
ARE max hops | 7 | 0-13 |
STE max hops | 7 | 0-13 |
Backup CRF | disabled | disable; enable |
You use the VLAN database command mode to add, change, and delete VLANs. In VTP server or transparent mode, commands to add, change, and delete VLANs are written to the file vlan.dat, and you can display them by entering the privileged EXEC mode show vlan command. The vlan.dat file is stored in nonvolatile memory.
This IOS release increases the number of possible VLANs from 64 to 250 on some switch models. The vlan.dat file is upgraded automatically, but you cannot go back to an earlier version of Cisco IOS after you upgrade to this release.
 | Caution You can cause inconsistency in the VLAN database if you attempt to manually delete the vlan.dat file. If you want to modify the VLAN configuration or VTP, use the VLAN database commands described in the Cisco IOS Desktop Switching Command Reference. |
You use the interface configuration command mode to define the port membership mode and add and remove ports from VLAN. The results of these commands are written to the running-configuration file, and you can display the file by entering the privileged EXEC mode show running-config command.
Each VLAN has a unique, 4-digit ID that can be a number from 1 to 1001. To add a VLAN to the VLAN database, assign a number and name to the VLAN. See the "Default VLAN Configurations" section for the list of default parameters that are assigned when you add a VLAN.
If you do not specify the VLAN type, the VLAN is an Ethernet VLAN. To add a VLAN, perform this task from privileged EXEC mode:
| Task | Command |
|---|---|
Step 1 Enter VLAN configuration mode. | vlan database |
Step 2 Add an Ethernet VLAN by assigning a number to it. If no name is entered for the VLAN, the default is to append the vlan-id to the word VLAN. For example, VLAN0004 could be a default VLAN name. | vlan vlan-id name vlan-name |
Step 3 Update the VLAN database, propagate it throughout the administrative domain, and return to privileged EXEC mode. | exit |
Step 4 Verify the VLAN configuration. | show vlan name vlan-name |
This example shows how to create an Ethernet VLAN and verify the configuration:
Switch# vlan database
Switch(vlan)# vlan 0003 name marketing
VLAN 3 added:
Name: marketing
Switch(vlan)# exit
APPLY completed.
Exiting....
Switch# show vlan name marketing
VLAN Name Status Ports
---- -------------------------------- --------- ---------------------
3 marketing active
VLAN Type SAID MTU Parent RingNo BridgeNo Stp Trans1 Trans2
---- ----- ---------- ----- ------ ------ -------- ---- ------ ------
3 enet 100003 1500 - - - - 0 0
The following task table illustrates how to modify VLAN parameters. You must perform this task from privileged EXEC mode:
| Task | Command |
|---|---|
Step 1 Enter VLAN configuration mode. | vlan database |
Step 2 Identify the VLAN, and change the MTU size. | vlan vlan-id mtu mtu-size |
Step 3 Update the VLAN database, propagate it throughout the administrative domain, and return to privileged EXEC mode. | exit |
Step 4 Verify the VLAN configuration. | show vlan vlan-id |
This example shows how to modify an Ethernet VLAN and verify the configuration:
Switch# vlan database
Switch(vlan)# vlan 0003 mtu 4000
VLAN 3 modified:
MTU 4000
Switch(vlan)# exit
APPLY completed.
Exiting....
Switch# show vlan 0003
VLAN Type SAID MTU Parent RingNo BridgeNo Stp Trans1 Trans2
---- ----- ---------- ----- ------ ------ -------- ---- ------ ------
3 enet 100003 4000 - - - - 0 0
When you delete a VLAN from a switch that is in VTP server mode, the VLAN is removed from all switches in the VTP domain. When you delete a VLAN from a switch that is in VTP transparent mode, the VLAN is deleted only on that specific switch.
You cannot delete the default VLANs for the different media types: Ethernet VLAN 1 and FDDI or Token Ring VLANs 1002 to 1005.
 | Caution When you delete a VLAN, any ports assigned to that VLAN become inactive. They remain associated with the VLAN (and thus inactive) until you assign them to a new VLAN. |
To delete a VLAN on the switch, perform this task from privileged EXEC mode:
| Task | Command |
|---|---|
Step 1 Enter VLAN configuration mode. | vlan database |
Step 2 Remove the VLAN by using the VLAN ID. | no vlan vlan-id |
Step 3 Update the VLAN database, propagate it throughout the administrative domain, and return to privileged EXEC mode. | exit |
Step 4 Verify the VLAN removal. | show vlan brief |
This example shows how to delete a VLAN:
Switch# vlan database
Switch(vlan)# no vlan 3
Deleting VLAN 3...
Switch(vlan)# exit
APPLY completed.
Exiting....
Switch# show vlan brief
VLAN Name Status Ports
---- -------------------------------- --------- ---------------------
1 default active Fa0/2, Fa0/3, Fa0/4, Fa0/5,
Fa0/6, Fa0/7, Fa0/8, Fa0/9,
Fa0/10, Fa0/11, Fa0/12, Fa0/13,
Fa0/14, Fa0/15, Fa0/16
2 VLAN0002 active
4 VLAN0004 active
1002 fddi-default active
1003 token-ring-default active
1004 fddinet-default active
1005 trnet-default active
A static-access port belongs to one VLAN. To assign a port to a VLAN, perform this task from privileged EXEC mode:
| Task | Command |
|---|---|
Step 1 Enter global configuration mode. | configure terminal |
Step 2 Enter interface configuration mode, and define the interface to be added to the VLAN. | interface interface |
Step 3 Define the VLAN membership mode for this port. | switchport mode access |
Step 4 Assign the port to the VLAN. | switchport access vlan 3 |
Step 5 Return to privileged EXEC mode. | exit |
Step 6 Verify the VLAN configuration. | show interface interface-id switchport |
This example shows how to assign switch ports to a VLAN and verify the assignment:
Switch# configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
Switch(config)# interface fa0/1
Switch(config-if)# switchport mode access
Switch(config-if)# switchport access vlan 0003
Switch(config-if)# end
Switch# show interface fa0/1 switchport
Name: Fa0/1
Switchport: Enabled
Administrative mode: static access

Operational Mode: static access
Administrative Trunking Encapsulation: isl
Operational Trunking Encapsulation: isl
Negotiation of Trunking: Disabled

Access Mode VLAN: 3 (marketing)
Trunking Native Mode VLAN: 1 (default)
Trunking VLANs Enabled: NONE
Pruning VLANs Enabled: NONE
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
Posted: Wed May 26 12:04:32 PDT 1999
Copyright 1989-1999©Cisco Systems Inc.