|
|

This chapter describes the security features built into the Cisco 6400 Service Connection Manager (SCM) application. The Cisco 6400 SCM through the use of Cisco EMF carrier class security mechanisms known as Cisco EMF User Access Control, provides:
 |
Note It might be advisable to restrict the Cisco EMF options available to less experienced personnel. |
Additionally, complex new equipment technologies are being launched into the market by both existing and new equipment providers. Faced with many new equipment features, personnel might make mistakes; for example in equipment configuration, which could affect network uptime.
Service provider organizations might be obligated under law to protect sensitive information contained within management systems. The ability to provide secure customer network management is therefore a valuable service to offer customers.
The Cisco 6400 SCM adds additional security mechanisms or feature lists to the standard Cisco EMF security mechanisms.
In a complex network operations environment, it is advisable to create user roles, so that less experienced and skilled personnel are restricted from accessing service affecting management functions. You might consider creating user categories for "Normal", "Super", and "Administrator" levels of responsibility.
An example is provided (see the "Create a Customized Normal User" section) that describes how to create and configure the various features of your system that can allow or restrict the access allowed by various levels of personnel.
Cisco EMF security allows system administrators to set up Access Manager objects using the Access Manager GUI. Access Manager objects can be classed as either personnel or services as follows:
The Access Manager object is set up to allow or restrict user access to features within Cisco EMF. For example, an administrator could set up users to have access only to those parts of Cisco EMF that are relevant to their specific tasks. Users would only be aware of their own access to the system and the use of their password.
For example, Joe might be the NOC expert on xDSL modems, but he might be a relative ATM novice. Helen, on the other hand, might be the ATM expert but she might know very little about the intricacies of xDSL technologies. With Cisco EMF Access Control, the systems administrator is able to ensure that Joe has read/write access to all xDSL network elements for configuration and test purposes, while Helen can only view the status information for these elements. Helen, on the other hand, can reconfigure ATM equipment, whereas Joe is refused access to the Element Manager windows that permit such reconfiguration.
Three levels of user access are available. These names describe the type of access available to each level:
Cisco EMF Security also enables administrators to define security levels for specific managed object attributes. This is key to restricting access to sensitive or critical parameters of managed equipment (for example, the IP address of an item of equipment.) A user with Read-Write access might be able to apply a new configuration to that piece of equipment, but the user might not be able to modify its IP address, because it might invalidate normal device management. The network topology manager should be responsible for control of the IP address.
Refer to the Cisco Element Management Framework User Guide for further information on the Cisco EMF Access Manager application.
Default access specifications are supplied by the Cisco 6400 SCM application. Default access specifications can be changed or removed by authorized users.
Commonly used features are grouped in the Cisco 6400 SCM applications as described below.
Includes all the feature lists; that is, access to everything in the Cisco 6400 SCM application.
Includes all Service Configuration windows and Service Deployment feature windows.
 |
Note SCM_Service_Profiles does not include service profile access. Service profile access is considered as a superuser "policy definition" feature. |
Includes all Service Profile feature lists (all service profiles, plus Connection Template deployment and configuration).
 |
Note SCM_Service_Profiles does not include service profile access. Service profile access is considered as a superuser "policy definition" feature. |
Includes all Subscriber Provisioning feature lists (Subscriber deployment, configuration, connection and disconnection).
Includes all SCM Element Manager (EM) window feature lists, EM deployment, and all generic feature lists above with the exception of Backup/Restore and IOS Image Download.
Includes Backup and Restore and IOS Image Download feature lists.
The Cisco EMF Access Manager application allows system administrators the opportunity to control the features of their system that can be accessed by the various levels of personnel. This is important for secure network management.
This section provides an example of how to create a new Normal user who can create and configure ATM services and then connect subscribers to the service instance.
Figure 10-1 presents a typical workflow that shows how to first create an access specification, then create a user group; and then create the user.
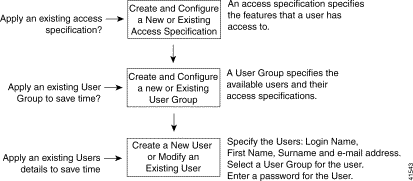
This example describe how to:
 |
Note Access specifications are used to ensure that users are restricted to only be able to carry out the tasks that they are permitted to do (by the selected feature lists). That is, this example does not allow the user to disconnect a subscriber from a service, this task is restricted to users with a higher security level. |
Click the Access icon on the Cisco EMF Launchpad to launch the Access Manager application (Figure 10-2) or choose Access from a pop up menu when using other Cisco EMF applications. The pop up menu is accessed by right-clicking on a selected object.
This section describes how to create an access specification (called SCM_PTA_Provisioning) for a "normal" user. We also provide guidelines for creating three user categories:
Creating the access specification ensures that a normal user can gain access to appropriate Cisco EMF functionality.
To create the example access specification, follow these steps:
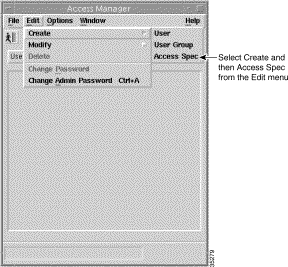
Step 2 Choose Create, then Access Spec from the Edit dropdown menu. The Create Access Specification wizard launches. A window similar to Figure 10-3 appears.
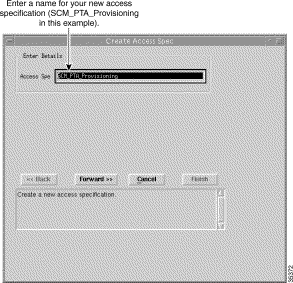
Step 3 Enter a name for the new access specification to be created. In this example, it is SCM_PTA_Provisioning.
 |
Note A valid name must have at least five characters with no spaces. |
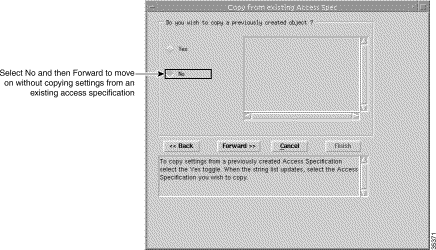
Step 4 Click Forward. The Copy from Existing Access Specification window (Figure 10-4) appears.
 |
Note You are now required to select settings for the new access specification. You can copy settings from a previously created specification and edit the specification (refer to the Cisco Element Management Framework User Guide) or create a new specification without copying settings from an existing access specification. This example creates a new specification without copying settings from an existing access specification. |
Step 5 Click No, because we are creating a new AccessSpec.
Step 6 Click Forward. The Select Permission window appears (Figure 10-5).
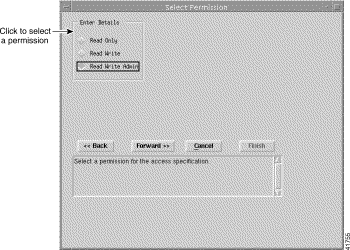
Step 7 Choose a permission level from Read Only, Read Write, or Read Write Admin. In this example, we will accept the default value.
Step 8 Click Forward. The Select User Groups window appears (Figure 10-6).
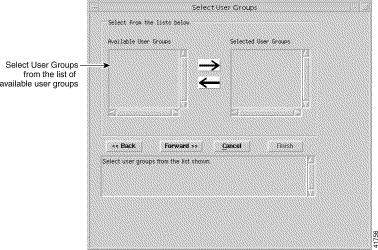
Step 9 Choose the user group that you want to include in the new access specification, then click the right arrow to move the selected user group into the list of selected user groups in the right panel. (An alternative method is to double-click a selected object.) The left arrow moves the selected item back into the left panel.
 |
Note You do not need to select a user group. This is an optional step. When using this application for the first time there will be no user groups in the available user group list. |
Step 10 Click Forward when the list of selected user groups is complete. The Select Feature Lists window appears.
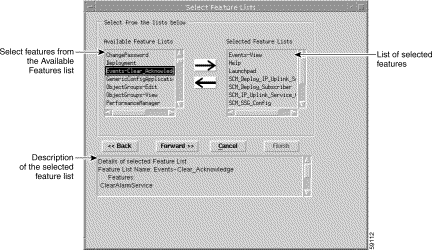
Step 11 Choose the feature list (one at a time) that you want to apply to the new specification (in the Available Feature List), then click the right arrow to include the selected feature list in the list of Selected Feature Lists.
Table 11-1 details the feature lists available for the different types of users. It displays the available feature lists that should be selected for a normal user and describes what each feature list allows the user to do. It also lists the recommended SuperUser and Administrator settings
| Selected Feature List | Allows The User To | Normal User | Super User | Admin |
AccessMangement | Access to the Access Manager application (to change their own passwords) | Yes | Yes | Yes |
AutoDiscovery | Perform Auto Discovery | No | Yes | Yes |
ChangePassword | Change the Cisco EMF login passwords | Yes | Yes | Yes |
Deployment | Deploy new devices | Yes | Yes | Yes |
Events-Clear_Acknowledge | Acknowledge and clear events | Yes | Yes | Yes |
Events-View | View events using Event Browser | Yes | Yes | Yes |
GenericConfigApplication | Object Configuration Dialog | No | No | Yes |
Help | Access Online-Help | Yes | Yes | Yes |
Launchpad | Access the Cisco EMF Launchpad | Yes | Yes | Yes |
ObjectGroups-Edit | Edit object groups | No | No | Yes |
ObjectGroups-View | View object groups | No | Yes | Yes |
PerformanceManager | Performance Manager | Yes | Yes | Yes |
SCM_ATM_Service_Config | ATM Service Configuration | Yes | Yes | Yes |
SCM_Chassis_Backup_Restore | Chassis Backup/Restore | Yes | Yes | Yes |
SCM_Chassis_Command_Log | Chassis Command Log | Yes | Yes | Yes |
SCM_Chassis_Configuration | Chassis Configuration | Yes | Yes | Yes |
SCM_Chassis_IOS_Image_Download | Chassis IOS Image Download | No | Yes | Yes |
SCM_Chassis_Mgmt_Info | Chassis Management Information | Yes | Yes | Yes |
SCM_Chassis_SNMP_Management | Chassis SNMP Management | Yes | Yes | Yes |
SCM_Chassis_SysLog | Chassis System Log | Yes | Yes | Yes |
SCM_Connection_Status | Connection Status | Yes | Yes | Yes |
SCM_Connection_Template_Config | Connection Template Configuration | No | Yes | Yes |
SCM_Deploy_ATM_Service | ATM Service Deployment | Yes | Yes | Yes |
SCM_Deploy_Chassis_NSP | 6400 Chassis/NSP/Shelf Manual Deployment, Quick Start Deployment | No | Yes | Yes |
SCM_Deploy_Connection_Template | Connection Template Deployment | No | Yes | Yes |
SCM_Deploy_DS3 | DS3 Line Card Manual Deployment | Yes | Yes | Yes |
SCM_Deploy_IP_Uplink_Service | IP Uplink Service Deployment | No | Yes | Yes |
SCM_Deploy_L2TP_Service | L2TP Service Deployment | No | Yes | Yes |
SCM_Deploy_NRP | 6400 NRP Manual Deployment | No | Yes | Yes |
| Selected Feature List | Allows The User To | Normal User | Super User | Admin |
SCM_Deploy_OC12 | OC12 Line Card Manual Deployment | Yes | Yes | Yes |
SCM_Deploy_OC3 | OC3 Line Card Manual Deployment | Yes | Yes | Yes |
SCM_Deploy_PPPoA_SD_Service | PPPoA-SD Service Deployment | No | Yes | Yes |
SCM_Deploy_RFC1483_Bridged_Service | RFC1483 Bridged Service Deployment | No | Yes | Yes |
SCM_Deploy_RFC1483_IRB_Service | RFC1483 IRB Service Deployment | No | Yes | Yes |
SCM_Deploy_RFC1483_Routed_Service | RFC1483 Routed Service Deployment | No | Yes | Yes |
SCM_Deploy_Subscriber | Deploy new subscribers | Yes | Yes | Yes |
SCM_Element_Management | All Element Manager windows (plus the Cisco 6400 UAC, Chassis, State, Commission/Decommission menu option) but not including the SSG Configuration and SONET APS Configuration windows | Yes | Yes | Yes |
SCM_IP_Uplink_Service_Config | IP Uplink Service Configuration | No | Yes | Yes |
SCM_IP_Uplink_Service_Profile | IP Uplink Service Profile Configuration | No | Yes | Yes |
SCM_Interface_Configuration | Interface Configuration | No | Yes | Yes |
SCM_Interface_Performance | Interface Performance | No | Yes | Yes |
SCM_Interface_Status | Interface Status | No | Yes | Yes |
SCM_L2TP_Service_Config | L2TP Service Configuration | No | Yes | Yes |
SCM_L2TP_Service_Profile | L2TP Service Profile Configuration | No | Yes | Yes |
SCM_Module_Backup_Restore | Module Backup/Restore | Yes | Yes | Yes |
SCM_Module_Command_Log | Module Command Log | Yes | Yes | Yes |
SCM_Module_Configuration | Module Configuration | Yes | Yes | Yes |
SCM_Module_IOS_Image_Download | Module IOS Image Download | Yes | Yes | Yes |
SCM_Module_Mgmt_Info | Module Management Information | Yes | Yes | Yes |
SCM_Module_Performance | Module Performance | Yes | Yes | Yes |
SCM_Module_SysLog | Module System Log | Yes | Yes | Yes |
SCM_PPPoA_SD_Service_Config | PPPoA-SD Service Configuration | No | Yes | Yes |
SCM_PPPoA_SD_Service_Profile | PPPoA-SD Service Profile Configuration | No | Yes | Yes |
SCM_RFC1483_Bridged_Service_Config | RFC1483 Bridged Service Configuration | No | Yes | Yes |
SCM_RFC1483_Bridged_Service_Profile | RFC1483 Bridged Service Profile Configuration | No | Yes | Yes |
SCM_RFC1483_IRB_Service_Config | RFC1483 IRB Service Configuration | No | Yes | Yes |
SCM_RFC1483_IRB_Service_Profile | RFC1483 IRB Service Profile Configuration | No | Yes | Yes |
SCM_RFC1483_Routed_Service_Config | RFC1483 Routed Service Configuration | No | Yes | Yes |
SCM_SONET_APS_Config | SONET APS Configuration | No | Yes | Yes |
SCM_SSG_Config | SSG Configuration | No | Yes | Yes |
SCM_Service_Status | Service Status | Yes | Yes | Yes |
| Selected Feature List | Allows The User To | Normal User | Super User | Admin |
SCM_Service_Uplink_Service_Profile | Service Uplink Profile Configuration (for RFC1483 Routed Service Uplinks) | Yes | Yes | Yes |
SCM_Subscriber_Config | Configure subscribers information | Yes | Yes | Yes |
SCM_Subscriber_Connection | Connect subscribers | Yes | Yes | Yes |
SCM_Subscriber_Disconnection | Disconnect subscribers | No | Yes | Yes |
SCM_Third_Party_Tools | e.g. Telnet access | No | Yes | Yes |
Viewer-Edit | Access the Map Viewer window to edit Maps | No | Yes | Yes |
Viewer-View | Access the Map Viewer window but does not allow the user to edit the Map Viewer window. | Yes | Yes | Yes |
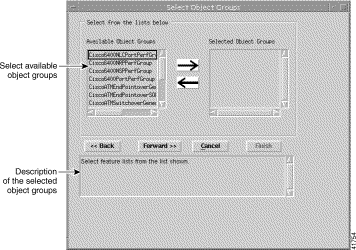
Step 12 Click Forward when Selected Feature Lists is complete. The Select Object Groups window appears (Figure 10-8).
The Select Object Group window allows you to assign management responsibility for a network region as determined by an Object Group. For an example, you might want to restrict access for SCM_PTA_Provisioning to a specific geographical area.
 |
Note You can create an access specification without associating it with an object group. This allows unlimited geographical access. |
Step 13 Click Forward. The Summary Details window, similar to Figure 10-9 appears.
If any details are incorrect, you can click Cancel to exit the wizard or click Back to return to the appropriate window and correct the details.
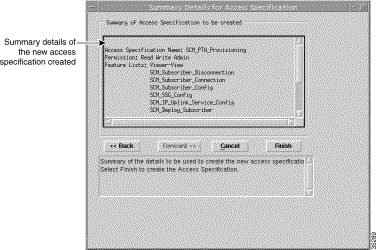
Step 14 Click Finish to create the access specification. The Access Manager window appears with the name of the new access specification displayed at the bottom of the list of access specifications.
To use the newly created access specification as a basis for defining a new group of users, follow these steps:
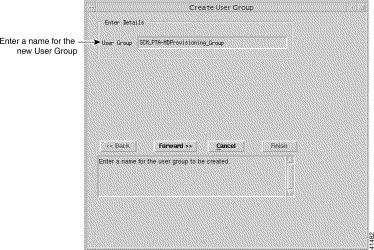
 |
Note A valid name must have at least five characters with no spaces. |
Step 2 Click Forward. The Copy from Existing User Group window appears (Figure 10-11).
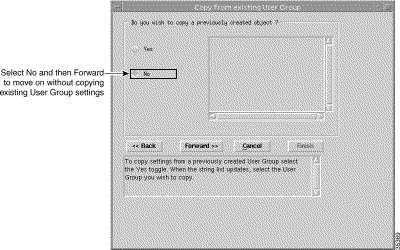
 |
Note You can copy settings from a previously created user group and edit the specification (refer to the Cisco Element Management Framework User Guide) or create a new user group without copying settings from an existing access specification. This example creates a new user group without copying settings from an existing user group. |
Step 3 Click No.
Step 4 Click Forward. The Select User Groups window appears (Figure 11-12).
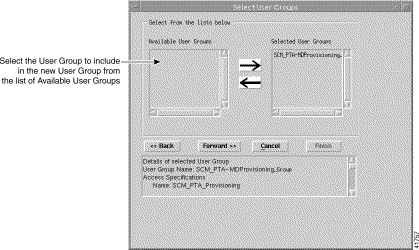
Step 5 Choose the user groups that you want to include in the new user group, then click the right arrow. This moves the selected user group into the list of selected users in the right panel. (An alternative method is to double-click an item in Available User Groups.) The left arrow moves the selected item (in the right list) back into the left panel.
Step 6 Click Forward when the list of selected user groups is complete. The Select Access Specifications window appears (Figure 10-13).
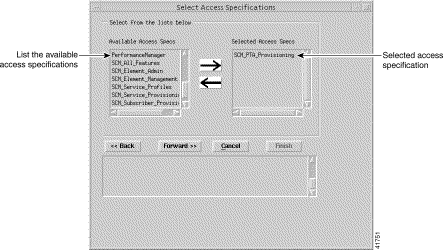
Step 7 Choose the access specification that you want to apply to the new User Group, then click the right arrow. In this example, the SCM_PTAProvisioning access specification that was created earlier is selected.
Step 8 Click Forward. A Summary Details for User Group window, similar to Figure 10-14 appears. When any details are incorrect, you can click Cancel to exit the wizard or click Back to return to the appropriate window and correct the details.
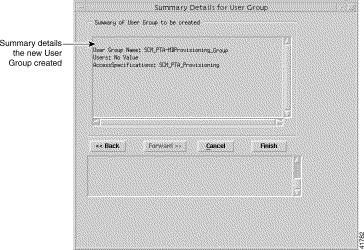
Step 9 Click Finish to create the User Group. The Access Manager window appears with the name of the new User Group displayed at the bottom of the User Groups list.
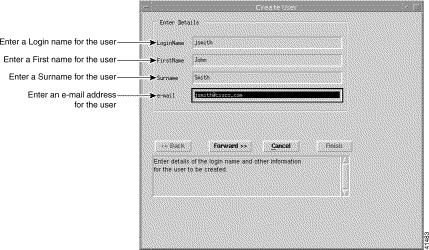
Step 2 Enter details for the new user into the Enter Details panel.
Step 3 Click Forward. The Copy from Existing User window appears (Figure 10-16).
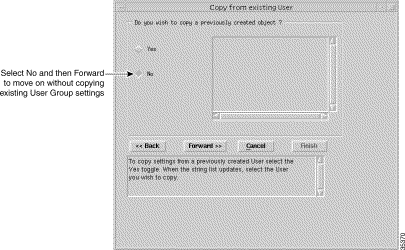
 |
Note You can copy settings from a previously created user and edit the specification (refer to the Cisco Element Management Framework User Guide) or create a new user without copying settings from an existing access specification. This example creates a new user without copying settings from an existing user. |
Step 4 Click No.
Step 5 Click Forward. The Select User Groups window appears (Figure 10-17).
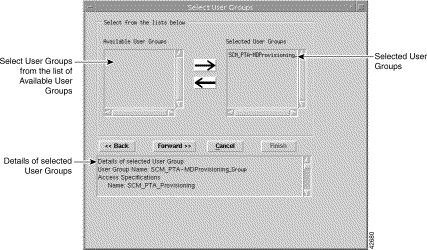
Step 6 Choose the user groups that you want your new user to belong to, then click the right arrow. This moves the selected user group into the list of selected user groups in the right panel. (An alternative method is to double-click an available user group.) The left arrow moves the selected item (in the right list) back into the left panel.
Step 7 Click Forward when the list of selected user groups is complete. The User Password Entry window appears (Figure 10-18).
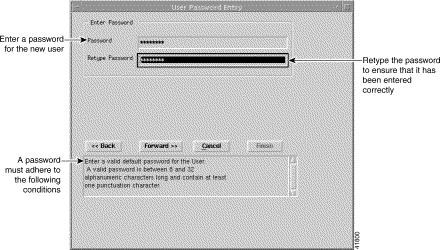
Step 8 Enter a password for the new user following the conditions specified in the panel (below the Back, Forward, Cancel, and Finish buttons). You will be alerted when you enter an invalid password.
 |
Note Passwords must be at least eight characters long and contain at least one numeric characters and one punctuation character. |
Step 9 Retype the password to confirm that you have entered the password correctly.
Step 10 Click Forward. A Summary Details for User window, similar to Figure 10-19, appears. When any details are incorrect, you can click Cancel to exit the wizard or click Back to return to the appropriate window and correct the details.
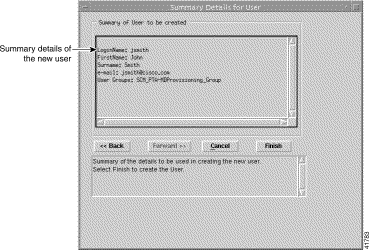
Step 11 Click Finish to create the user. The Access Manager window appears with the name of the new User displayed at the bottom of the user's list.
Using the principles described in the example you should now be able to create users with different access security levels.
This section describes a number of checks that you should carry out after you have created a new User.
Be certain that:
To check that you have associated the correct user group with the user group, proceed as follows:
Step 2 Double-click on the appropriate user in the list. The User Editor window appears.
Step 3 Check the user details displayed in the User Details tab.
Step 4 Click the Select User Groups tab.
Step 5 Check that the appropriate User Group is selected in the list of Selected User Groups.
Step 6 Click Close to close the window.
To check that you have associated the correct user with a specific user group, proceed as follows:
Step 2 Double-click on the appropriate user group in the list of user groups displayed. The User Groups Editor window appears.
Step 3 Check the appropriate user is selected in the Select Users tab.
Step 4 Click the Select Access Specifications tab.
Step 5 Check that the appropriate access specifications is displayed in the list of Selected Access Specs.
Step 6 Click Close to close the window.
To check the selected access specification, proceed as follows:
Step 2 Double-click on the appropriate access specification from the list displayed. The Access Specification Editor window appears.
Step 3 Check that the Read Write Admin option is selected in the Select Permissions tab.
Step 4 Click the Select User Groups tab.
Step 5 Check that the appropriate user group is displayed in the list of Selected User Groups.
Step 6 Click the Select Feature Lists tab.
Step 7 Check that all of the appropriate feature lists are displayed in the list of Selected Feature Lists.
 |
Note As a minimum you must have the Launchpad, Events-View, Viewer-View feature lists selected. A normal user whose focus was ATM Provisioning would also have subscriber connection, ATM related feature lists, and various deployment feature lists. |
Step 8 Click the Select Object Groups tab. Object Groups are normally not selected unless you are using advanced features.
Step 9 Click Close to close the window.
You should check that the new user has been set up correctly by logging into the system as the new user and checking the functionality available to the user.
To check the new user, proceed as follows:
Step 2 Login as the new user using the passwords set when the new user was created. The Map Viewer window appears.
Step 3 Check the menu options available by right clicking on a number of objects. Options are greyed out when the corresponding feature lists were not selected. For example, when we were setting up our example normal user earlier, we decided that we would not allow a normal user to be able to disconnect subscribers. We stopped the normal user from being able disconnecting subscribers by making sure that we did not select the SCM_Subscriber_Disconnection feature list.
Figure 10-20 shows the Disconnect option greyed out in the Subscriber menu option as expected.
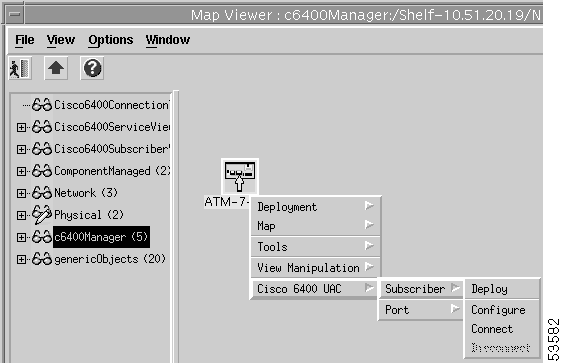
Step 4 Close the Map Viewer window and exit the Cisco EMF session.
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
Posted: Tue May 29 10:37:08 PDT 2001
All contents are Copyright © 1992--2001 Cisco Systems, Inc. All rights reserved.
Important Notices and Privacy Statement.