|
|

April 4, 2002
This document describes all additions or changes to running the ONS 15190 IP Transport Concentrator with Software Release 3.5. The Cisco ONS 15190 was previously known as the PentaCom RingStar8000.
Introductory information is presented in the following sections:
Release 3.5 for the ONS 15190 is compatible with any existing ONS 15190 hardware platforms.
In software releases below 3.0, use the command system show info to display the currently running release of the software.
admin>system show info
System uptime: 0:08:02.363
Name: ONS 15190
Description: Lab at Cisco Systems
Location:
Contact:
Running image:
Release: 1.2
Created on: Wed Jan 19 21:14:46 2000
Created by: Cisco Systems
Length: 2282376
Signature: 0xEF2BE4F6
Software version: 1.2.15
Software built on: Jan 19 2000, 21:13:45
Bootstrap version: 3.2
Stored image:
Release: 1.0.23
Created on: Tue Feb 01 01:21:56 2000
Created by: Cisco Systems
Length: 2290824
Signature: 0x4E034E21
The running image release should be the same as the stored image release (in this example, Release 1.2). In Release 3.0 or above, use the command show version to display the currently running release of the software.
ons15190#show version
System uptime: 19:34:52.215
System time: MON MAR 19 13:10:36 2001
Name: ons15190
Description:
Location:
Contact:
Running image:
Release: 3.5
Created on: Fri Mar 09 03:22:03 2001
Created by: Cisco Systems
Length: 1099879
Signature: 0x21143E04
Software build: 3.5.4
Software created on: Mar 9 2001, 03:14:26
Bootstrap version: 3.5
Backplane info:
Description: RingStar 8000 chassis
Catalog number: RINGSTAR-8000
Serial number: 1160-001
Board version: B0
PEM 1:
Status: Absent
PEM 2:
Status: Operational
Description: Power Entry Module
Catalog number: RS-PEM
Serial number: 354-025
Board version: B1
Fans:
Fan 1 [Tray 1]: Operational
Fan 2 [Tray 1]: Operational
Fan 3 [Tray 1]: Operational
Fan 4 [Tray 1]: Operational
Fan 5 [Tray 1]: Operational
Fan 6 [Tray 1]: Operational
Instructions for upgrading to Release 3.5 are provided in the "Installation Notes" section.
Following is a list of the new software features supported by the Cisco ONS 15190 IP Transport Concentrator in Release 3.5:
Release 3.5 supports access via SSH or Telnet. Both DES and 3DES encrytion methods are supported for SSH. Use the show ssh EXEC command to display all active SSH sessions. Use the show users EXEC command to display all active sessions, including SSH.
Authentication, authorization and accounting (AAA) is described in the following sections:
 |
Note Authentication and authorization features were supported in Release 3.2. Accounting features are new to Release 3.5. |
AAA authentication is used to restrict access to log in to the ONS 15190 or privileged EXEC command level. AAA authorization limits the use of specific commands according to user, by using the information retrieved from the user's profile on the TACACS+ security server. AAA accounting enables you to track the services users are accessing as well as the amount of network resources they are consuming. When AAA accounting is enabled, the network security server receives reports from the ONS 15190 regarding user activity in the form of accounting records. These records are saved at the security server and can be analyzed for network management purposes.
AAA is automatically enabled on the ONS 15190 and you can configure the security configuration to work with or without a TACACS+ server. Use of a TACACS+ server provides much more flexibility in terms of AAA security configurations.
By default, the ONS 15190 is set to work without a TACACS+ server, and the default login password is the same as the enable secret password. Because of this, you cannot log into the ONS 15190 via a network connection (SSH or Telnet) until the enable secret password has been defined or the AAA configurations have been changed from their default.
 |
Note Use of a TACACS+ server is the only security method provided on the ONS 15190 that allows authentication, authorization and accounting (AAA) definitions by specific user. Authorization can only be defined with the use of a TACACS+ server. |
 |
Note For a complete description of the AAA Cisco model and TACACS+ server functionality, see the Cisco IOS Security Configuration Guide. |
There are two options of AAA security configuration without using a TACACS+ server:
In both of these scenarios, the password (the enable secret) is per ONS 15190 and not dependant on the specific user being authenticated.
For authentication commands, you can specify more than one authentication method, in case the first method can not be used. For example, if the enable secret has not been defined, using the above commands will not provide access to the ONS 15190. The following commands will allow access even if the enable secret has not been set:
aaa authentication login default enable none
aaa authentication enable default enable none
In this example, authentication only reverts to none if there is no enable secret defined on the ONS 15190. If the user fails to provide the correctly defined enable secret, authentication fails.
To configure security on the ONS 15190 using AAA with TACACS+, follow this process.
1. Use the tacacs-server host command to configure the security parameters for the TACACS+ server. It is advisable to provide more than one server, in the event that the first server is down.
2. Define the method lists for authentication by using the aaa authentication login and aaa authentication enable commands. If you are using a TACACS+ server for authentication, you should provide a second method of authentication (such as enable or none), in the event that the TACACS+ server is down.
3. Optional. Configure authorization using the aaa authorization commands or aaa authorization config-commands commands. You must be logged in to the ONS 15190 as an authenticated user in order to successfully define AAA authorizations.
Make special note of the following items before configuring AAA on the ONS 15190:
The following example shows a sample AAA authentication configuration:
ons15190(config)# tacacs-server host 10.52.19.44
ons15190(config)# tacacs-server host 10.52.19.47 key SpecialKey
ons15190(config)# tacacs-server host 10.52.19.51
ons15190(config)# tacacs-server key myTacacsPassWord
ons15190(config)# tacacs-server timeout 15
ons15190(config)# aaa authentication login default tacacs+ enable
ons15190(config)# aaa authentication enable default tacacs+ enable
This example specifies:
After authentication has been configured, you must log out of the ONS 15190 and log in as an authenticated user before configuring the AAA authorization. The following example shows a sample AAA authorization configuration:
ons15190(config)# aaa authorization commands 1 default tacacs+ if-authenticated
ons15190(config)# aaa authorization commands 15 default tacacs+ if-authenticated
ons15190(config)# aaa authorization config-commands
This example specifies:
Each authentication and authorization command should list several methods to be used if the first method returns an error. Subsequent methods are only used if an error is received; if the previous method fails, authentication or authorization is denied.
There are three types of accounting methods supported on the ONS 15190:
The only accounting method supported on the ONS 15190 is TACACS+. The ONS 15190 reports user activity to the TACACS+ security server in the form of accounting records. Each accounting record contains accounting attribute-value (AV) pairs and is stored on the security server.
There are two accounting record types implemented on the ONS 15190:
Before you can use the accounting features on the ONS 15190, you must configure a TACACS+ server. After AAA accounting is configured on the ONS 15190, the accounting records are saved for all active SSH, Telnet and console sessions.
Following are example AAA accounting configuration scripts. The server IP address and key are examples only; you must provide your own IP address and key.
Use the following commands to configure system accounting using the start-stop record type:
ons15190(config)# tacacs-server host 11.61.12.105
ons15190(config)# tacacs-server key abc13
ons15190(config)# aaa authentication login default tacacs+ enable
ons15190(config)# aaa accounting system default start-stop tacacs+
Use the following commands to configure exec accounting using stop-only record type:
ons15190(config)# tacacs-server host 11.61.12.105
ons15190(config)# tacacs-server key abc13
ons15190(config)# aaa authentication login default tacacs+ enable
ons15190(config)# aaa accounting exec default stop-only tacacs+
Use the following commands to configure the accounting for level 1 commands using start-stop record type (level 1 commands relate to all user EXEC commands):
ons15190(config)# tacacs-server host 11.61.12.105
ons15190(config)# tacacs-server key abc13
ons15190(config)# aaa authentication login default tacacs+ enable
ons15190(config)# aaa accounting commands 1 default start-stop tacacs+
Use the following commands to configure the accounting for level 15 commands using start-stop record type (level 15 commands relate to all EXEC privileged commands including configuration commands):
ons15190(config)# tacacs-server host 11.61.12.105
ons15190(config)# tacacs-server key abc13
ons15190(config)# aaa authentication login default tacacs+ enable
ons15190(config)# aaa accounting commands 15 default start-stop tacacs+
Use the following commands to configure the accounting for all commands using stop-only record type, system and exec accounting using the start-stop record type:
ons15190(config)# tacacs-server host 11.61.12.105
ons15190(config)# tacacs-server key abc13
ons15190(config)# aaa authentication login default tacacs+ enable
ons15190(config)# aaa accounting commands 1 default stop-only tacacs+
ons15190(config)# aaa accounting commands 15 default stop-only tacacs+
ons15190(config)# aaa accounting exec default start-stop tacacs+
ons15190(config)# aaa accounting system default start-stop tacacs+
Following is a list of the new software features supported by the Cisco ONS 15190 IP Transport Concentrator as of Release 3.2:
The Cisco ONS 15190 command line interface (CLI) has been changed to be compatible with Cisco IOS so that using a Cisco IOS command that is implemented in the ONS 15190, performs the same action as that described in the Cisco IOS documentation. In all cases where functionality differs significantly from Cisco IOS, the syntax is also slightly different. In some cases, the results may be less complete than in Cisco IOS. Following is a table that maps all Release 2.5 commands to Release 3.2 commands.
| Release 2.5 Command | Release 3.2 Command | Command Mode |
|---|---|---|
autoconnect | autoconnect | privileged EXEC |
card SLOT reset | hw-module slot reload | privileged EXEC |
card SLOT show status | show hw-module | EXEC |
eips enable | eips enable | global conf |
eips disable | no eips enable | global conf |
eips set wtr DECIMAL | eips wtr-timer | global conf |
eips show | show eips | EXEC |
l-aps all APS-NODE show status | show aps node | EXEC |
l-aps APS-NODE request lockout | l-aps lockout | privileged EXEC |
l-aps APS-NODE request forced | l-aps force | privileged EXEC |
l-aps APS-NODE request manual | l-aps manual | privileged EXEC |
l-aps APS-NODE request clear lockout | no l-aps lockout | privileged EXEC |
l-aps APS-NODE request clear forced | no l-aps force | privileged EXEC |
l-aps APS-NODE request clear manual | no l-aps manual | privileged EXEC |
motd enable | motd-banner | global conf |
motd disable | no motd-banner | global conf |
motd show | show banner motd | EXEC |
port blink DECIMAL | hw-module interface blink | privileged EXEC |
port all clear sonet current | clear counters | privileged EXEC |
port all loopback {facility | none | terminal} | loopback + loopback line + loopback internal | interface conf |
port all reset | clear interface | privileged EXEC |
port PORT clear pos total | clear counters | privileged EXEC |
port PORT loopback {facility | none | terminal} | loopback + loopback line + loopback internal | interface conf |
port PORT reset | clear interface | privileged EXEC |
port all | PORT show pos current | show interfaces data current | EXEC |
port all | PORT show pos history | show interfaces data history | EXEC |
port PORT show pos total | show interfaces data total | EXEC |
port all | PORT show pos total {bytes | frames | errors} | show interfaces data total {byte | frame | errors} | EXEC |
port all | PORT show sonet current | show interfaces performance-monitor current | EXEC |
port all | PORT show sonet history | show interfaces performance-monitor history | EXEC |
port all | PORT show sonet {current | history | indications} | show controllers {srp | pos} | EXEC |
port all | PORT show laser | show interfaces laser | EXEC |
port all | PORT show status | show interfaces | EXEC |
port all | PORT show trace | show interfaces rx-pathtrace | EXEC |
rconf apply | apply | rconf |
rconf discard | discard | rconf |
rconf default | default | rconf |
rconf show applied | 1. display running | rconf |
rconf show applied raw | 1. show rconf running raw | EXEC |
rconf show current | display draft | rconf |
rconf node autodetect | node autodetect | rconf |
rconf node delete NODE | no node create | rconf |
rconf NODE ports PORT1 PORT2 | node interfaces | rconf |
rconf node NODE rename STRING | node rename | rconf |
rconf node NODE show | show node | privileged EXEC |
rconf node new | node create | rconf |
rconf node NODE set ais | node set ais | rconf |
rconf node NODE set clock-source | node set clock-source | rconf |
rconf node NODE set mode | node set framing | rconf |
rconf node NODE set sd-threshold | node set threshold sd-ber | rconf |
rconf node NODE set sf-threshold | node set threshold sf-ber | rconf |
rconf node NODE set switching | node set aps revert | rconf |
rconf pos connect | pos connect | rconf |
rconf pos disconnect | no pos connect | rconf |
rconf ring delete | no ring create | rconf |
rconf ring new | ring create | rconf |
rconf ring RING add all | NODE | ring add | rconf |
rconf ring RING autoorder | ring autoorder | rconf |
rconf ring RING nodes NODE1 | ring nodes | rconf |
rconf ring RING remove all | NODE | no ring add | rconf |
rconf ring RING rename | ring rename | rconf |
rconf sniff connect | sniff connect | rconf |
rconf sniff disconnect | no sniff connect | rconf |
rconf raw enable | raw enable | rconf |
rconf raw disable | no raw enable | rconf |
rconf raw clear | raw clear | rconf |
rconf raw connect | raw connect | rconf |
rconf raw direct | direct | rconf |
rconf raw disconnect | 1. no direct | rconf |
rconf raw set {all | PORT} ais | raw set ais | rconf |
rconf raw set {all | PORT} clock-source | raw set clock-source | rconf |
rconf raw set {all | PORT} mode | raw set framing | rconf |
rconf raw set {all | PORT} protocol | raw set protocol | rconf |
rconf raw set {all | PORT} sd-threshold | raw set threshold sd-ber | rconf |
rconf raw set {all | PORT} sf-threshold | raw set threshold sf-ber | rconf |
slot SLOT disable | no hw-module shutdown | global conf |
slot SLOT enable | hw-module shutdown | global conf |
slot all | SLOT show status | show hw-module status | EXEC |
system reset | reload | privileged EXEC |
system tech-support | show tech-support | EXEC |
system set contact | snmp-server contact | global conf |
system set description | snmp-server chassis-id | global conf |
system set location | snmp-server location | global conf |
system set name | hostname | global conf |
system set prompt | hostname | global conf |
system set session timeout | exec-timeout | line conf |
system set temp-protect | temperature-protect disable | global conf |
system set time | 1. calendar set | privileged EXEC |
system set trace-mode {pos | raw | sniff | srp} | pathtrace-mode | global conf |
system set factory default | 1. erase nvram: | privileged EXEC |
system show box | show 15190 | EXEC |
system show chassis | show version | EXEC |
system show info | show version | EXEC |
system show redundancy | show redundancy | EXEC |
system show session | show terminal | EXEC |
system show temp-protect | show temperature-protect (EXEC) | EXEC |
system show time | show calendar (EXEC) | EXEC |
login | enable (EXEC) | EXEC |
logout | 1. disable | privileged EXEC |
password | enable secret | global conf |
net delete sntp server | no sntp server | global conf |
net set arp flush | clear arp-cache | privileged EXEC |
net set dns | ip domain-name + ip name-server | global conf |
net set ip | ip address + | interface conf |
net show arp | show arp | EXEC |
net show ip | show interface ethernet 0 | EXEC |
net show route | show ip route | EXEC |
sntp set server | sntp server | global conf |
sntp delete server | no sntp server | global conf |
sntp show server | show sntp | EXEC |
tnetd abort | clear line vty | privileged EXEC |
tnetd send | send message | privileged EXEC |
tnetd set mirror | tnetd set mirror | privileged EXEC |
tnetd set state | tnetd set state | privileged EXEC |
tnetd show session | show users | EXEC |
tnetd show state | show tnetd | EXEC |
tftp get conf | 1. configure network tftp://.... | privileged EXEC |
tftp get image | copy tftp://.. flash: | privileged EXEC |
tftp get motd | copy tftp://... motd | global conf |
tftp put conf | 1. copy startup-config tftp://... | privileged EXEC |
ping | ping | EXEC |
snmp show | show snmp | EXEC |
snmp trap add | snmp-server host | global conf |
snmp trap remove | no snmp-server host | global conf |
telnet | 1. connect | EXEC |
help | help | EXEC |
history | show history | EXEC |
log set ip | logging host | global conf |
log set DEVICE clear | clear logging | privileged EXEC |
log set DEVICE state on | logging | global conf |
log set DEVICE state off | no logging | global conf |
log set DEVICE threshold | logging | global conf |
log show all | show logging | EXEC |
serial set console baud | speed | line conf |
serial set maintenance baud | speed | line conf |
 |
Note In keeping with the Cisco IOS software convention of limiting access to the global configuration command mode to one concurrent session, Release 3.5 of the ONS 15190 software also limits access to global and rconf configuration command modes to one session only. |
Release 3.5 supports the single ring redundancy (SRR) protocol. For DPT rings that operate in an "inner-outer" fiber topology with two ONS 15190 units, SRR provides redundancy to maintain full connectivity in the event of a failure in one ONS 15190. In this scenario, the inner ring fibers are connected to one ONS 15190 unit, and the outer ring fibers are connected to the second unit, meaning that only half of an SRP node is described in each ONS 15190 unit. For this reason, all configuration commands related to such nodes must be performed on both ONS 15190 units in order for them to operate correctly. If a command, such as a ring definition, is defined on only one unit, the configuration will be incomplete, and results may be unpredictable.
 |
Note In order for the SRR protocol to work correctly in the ring and provide complete system redundancy, all routers/devices in the ring must support SRR. SRR is supported in Cisco IOS Release 12.0(16)S for OC-48/STM-16. |
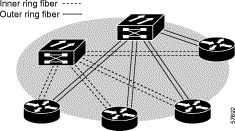
In order to automatically configure two ONS 15190 units that are to work with SRR, use the io-autoconnect privileged EXEC command on both ONS 15190 units. The SRP rings will be defined from the inner and outer nodes in the same order in both units.
If other configuration changes need to be performed, such as reordering the nodes in the ring, adding or removing nodes from the ring, or parameter changes, the commands must be used on both units. When the configuration changes are complete, the apply rconf configuration command must be used on both units.
The following changes were made to the software for Release 3.2 of the ONS 15190:
The autotrack capability is not supported in as of Release 3.2.
The procedure for cascading multiple ONS 15190 units into a single ring is simplified in the following procedure:
Step 2 Enter the autoconnect command on the first ONS 15190 unit.
Step 3 Enter the write command on the first ONS 15190 unit.
Step 4 Repeat steps 2 and 3 for each of the connected ONS 15190 units, in the order that they are physically connected.
The units are now configured into the same ring. All nodes connected to any of the units are now contained within this ring. In the following figure, each line represents a pair of fiber optic cables.
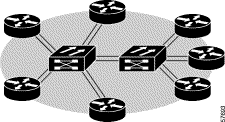
 |
Note If a span of routers is connected to any of the ONS 15190 units, both the span and the cascaced links to other ONS 15190 units will need to be manually defined to be recognized by the cascaded ONS 15190 units. |
 |
Note When cascading multiple ONS 15190 units together, set the trace-mode for SRP nodes to normal (default). |
A message of the day (MOTD) is displayed when the system is accessed via Telnet. This message may now be created by entering the message. To create a new MOTD, use the banner motd global configuration command:
ons15190(config)#banner motd "This is the message-of-the-day banner which will be
displayed"
After the MOTD has been defined, you must enable the display of the MOTD with the motd-banner command.
Release 3.5 currently loads with SNMP functionality disabled. This is in order to prevent security breaches via SNMP. In order to enable SNMP functionality, use the snmp-server community string global configuration command, where string is the community string that acts as a password and permits access to the SNMP protocol. To disable SNMP functionality after it has been enabled, use the no snmp-server EXEC command.
If you are upgrading from a release of the software below Release 2.0, follow the upgrade procedure in the section "Upgrade from Release 1.x". If you are upgrading from Release 2.x, follow the upgrade procedure in the section "Upgrade from Release 2.x". To install the software from Release 3.2 and above, follow the procedure in the section "Upgrade from Release 3.x".
 |
Note Downtime due to the software upgrade will be up to two minutes due to an update in the firmware. |
 |
Note Upgrades to Release 2.5 or above will discard all sniff connections, convert all unidirectional APS nodes to bidirectional nodes and discard all low level (raw) configurations. |
 |
Caution Due to changes in the database made in newer releases, it is not possible, following an upgrade, to revert to earlier versions of the system configuration. For this reason, you are advised to save the current configuration on your system before upgrading. Then if you experience a problem with the new release, you will be able to revert to the previous software revision and reload the old configuration. To upload the configuration to a tftp server, use the privileged EXEC command copy startup-config tftp://host[/dir]/filename, where host is the IP address of the TFTP server where you are saving the configuration file, and filename is the filename of the configuration file. |
To upgrade your ONS 15190 with a new release of software after Release 3.x is installed, do the following:
ons15190#copy tftp://192.168.10.1/ons15190-30.bin image
Retrieving 192.168.10.1:ons15190-30.bin... 1.17MB Done.
Release : 3.2
Created by: Cisco Systems
Created on: Mon Apr 16 13:40:33 2001
Are you sure? y
Checking CRC of image...OK
Storing image ...100%.
Updating image information (might take a while) Done.
In this example, the TFTP server IP address is 192.168.10.1, and the remote filename of the software update is ver30. When prompted with the release to be saved, enter y to continue the process. After the file is downloaded, it is stored within the Flash memory of both controller cards of the ONS 15190. A reset is performed automatically to the standby controller card such that the new software release will be up and running on the standby controller, but not on the active controller.
You will be prompted to reset the active controller in order to begin running the new software release.
Step 2 Enter y to continue.
Control will be transferred to the previous standby controller that is already running the new software, and the active controller is reset with the new software as well.
Changes will take affect only after controller reset
Do you want to reset now? y
Resetting...
SUN APR 29 15:29:15 2001 Controller reset
0:00:00.270 System powered on.
When the system is reset, communication will be lost to the controller and one of the following occurs:
Step 3 Log in to the system again. The software upgrade procedure is now complete.
To upgrade your ONS 15190 to Release 3.x after Release 2.x is installed, do the following:
admin>tftp get 192.168.10.185 ons15190-30.bin image
Retrieving 192.168.10.185:ons15190-30.bin... 2.91MB Done.
Release : 3.2
Created by: Cisco Systems
Created on: Mon May 01 20:55:40 2000
Are you sure? y
Storing image ...100%.
Updating image information (might take a while) Done.
synchronizing Image OK
In this example, the TFTP server IP address is 192.168.10.185, and the remote filename of the software update is ver30. When prompted with the release to be saved, enter y to continue the process. After the file is downloaded, it is stored within the Flash memory of both controller cards of the ONS 15190. A reset is performed automatically to the standby controller card such that the new software release will be up and running on the standby controller, but not on the active controller.
You will be prompted to reset the active controller in order to begin running the new software release.
Step 2 Enter y to continue.
Control will be transferred to the previous standby controller that is already running the new software, and the active controller will be reset with the new software as well.
Changes will take affect only after controller reset
Do you want to reset now? y
resetting...
When the system is reset, communication will be lost to the controller and one of the following occurs:
Step 3 Log into the system again via the console interface.
The system will now be running the new software release. If you perform the EXEC command show version, you will see that the new software release is currently running.
ons15190#show version
System uptime: 18:00:15.014
System time: THU MAR 15 10:44:11 2001
Name: ons15190
Description: Description
Location: Location
Contact:
Running image:
Release: 3.2
Created on: Fri Mar 09 03:22:03 2001
Created by: Cisco Systems
Length: 1099879
Signature: 0x21143E04
Software build: Private
Software created on: Mar 9 2001, 03:14:26
Bootstrap version: 3.2
Backplane info:
Description: ons15190 series chassis
Catalog number: ons15190
Serial number: 1377-004
Board version: B1
PEM 1:
Status: Faulty
Description: POWER ENTRY MODULE CARD WITH SWITCH
Catalog number: RS-PEM-SWT
Serial number: 1175-078
Board version: C1
PEM 2:
Status: Operational
Description: POWER ENTRY MODULE CARD WITH SWITCH
Catalog number: RS-PEM-SWT
Serial number: 1175-072
Board version: C1
Fans:
Fan 1 [Tray 1]: Operational
Fan 2 [Tray 1]: Operational
Fan 3 [Tray 1]: Operational
Fan 4 [Tray 1]: Operational
Fan 5 [Tray 1]: Operational
Fan 6 [Tray 1]: Operational
The software download procedure is now successfully completed.
Step 4 Before you can access the box via Telnet you will need to configure the security parameters. See TACACS AAA.
To upgrade the software on your ONS 15190 to Release 3.x from Release 1.x, do the following:
Step 2 Use the tftp get command to download the new software image file into the ONS 15190.
You need the TFTP server IP address where the file is located, as well as the name of the file. For example:
admin>tftp get 192.168.10.27 ons15190-32.bin image
Retrieving 192.168.10.27:ons15190-32.bin... 2.18MB Done.
Release : 3.2
Created by: Cisco Systems
Created on: Tue Feb 01 01:21:56 2000
Are you sure? y
Storing image ...100%.
Validating image Done.
Updating image information (might take a while) Done.
Synchronizing image...
waiting for standby controller to save image information....
........image synchronized OK
done
In this example, the TFTP server IP address is 192.168.10.27, and the remote file name of the software update is ver3.2.
Step 3 Enter y when prompted for the release to be downloaded.
When the download is complete, the file is stored within the Flash memory of both controller cards of the ONS 15190, but is not the currently running release of the software.
Step 4 Reset the system to run the newer release of the software. This reset may be done via the management software (as in the following example) or physically.
admin>sys reset
Controller will be reset.
Are you sure? y
bye
User Name:
Password:
admin>
When the system is reset, communication will be lost to the controller and one of the following occurs:
When the system reboots, the now active controller (which was previously the standby controller) will still be running the old software release. However, the standby controller will be running the new software release. Use the command system show info, to verify that the old software release is currently running. For example:
admin> system show info
System uptime: 0:08:02.363
Name: ONS 15190
Description: Lab at Cisco Systems
Location:
Contact:
Running image:
Release: 1.0.23
Created on: Wed Jan 19 21:14:46 2000
Created by: Cisco Systems
Length: 2282376
Signature: 0xEF2BE4F6
Software version: Build 23
Software built on: Jan 19 2000, 21:13:45
Bootstrap version: 3.2
Stored image:
Release: 3.2
Created on: Tue Feb 01 01:21:56 2000
Created by: Cisco Systems
Length: 2290824
Signature: 0x4E034E21
Note that the stored release is 3.2, but the current running software release is only release 1.0.23.
Step 5 Reset the system once again in order to complete the procedure so that the new release will be running on the active controller card.
This reset will transfer control back to the original active controller which is already running the new release. The standby controller will now be reset to the new release as well. Once again, communication to the controller will be lost.
Step 6 Log into the system again via the console interface.
When the system boots, it will be running Release 3.2. The software download procedure is now successfully completed.
Step 7 Before you can access the box via Telnet you will need to configure the security parameters. See TACACS AAA.
All features specified in this document are supported in Release 3.5.
If you must revert to a previous release of the software, do the following:
Step 2 Download the software image file into the ONS 15190. You need the TFTP server IP address where the file is located, as well as the name of the file. For example:
ons15190#copy tftp:\\192.168.10.27\ons15190-25.bin image:
In this example, the TFTP server IP address is 192.168.10.27, and the remote filename of the software update is ons15190-25.bin.
Step 3 When the image is downloaded and running on your system, you must either download a previously saved release of the configuration file, or execute the command system set factory-default. The factory default will provide a blank configuration for which you to begin defining your own configuration definitions.
To download a previously saved release of the configuration file, use the command tftp get IP fname conf, where IP is the IP address where you have saved the configuration file, and fname is the name of the file.
Step 4 Power down the unit and restart it before beginning to work with the new software release.
Limitations and restrictions of this software release are presented in the following sections:
The enable password command is not supported, so you cannot view unencrypted passwords using the show running command. The enable secret global configuration command is the only command you can use to define the enable password (secret).
In order to revert to a older software release, follow the upgrade procedure to download the proper software release. When the upgrade is completed, set the factory defaults with the command system set factory default. To set the system configuration, you can do one of the following:
Release 3.5 supports the connection of only one sniff node at a time. All previously defined sniff connections will be disconnected when Release 3.5 is installed.
Release 3.5 supports only bidirectional APS nodes. Any previously defined unidirectional nodes will be converted to bidirectional mode when Release 3.5 is installed.
If fiber loops are present on the system, the path trace mode must be set to normal in order for features such as autoconnect, and autodetect to function correctly.
When using OC-48c/STM-16 cards and traffic is comprised of minimally-sized packets (64 bytes), throughput may drop to 98 percent. Specifically, in the event of a burst of 2000 minimally-sized packets, about 2 packets may be dropped. Such scenarios are very unlikely in real networks, so this limitation is not expected to cause any impact on throughput.
Sniff nodes do not automatically receive the characteristics of the sniffed node, so they must be manually configured to be compatible with the node being sniffed.
Caveats in using the ONS 15190 as of Release 3.5 are presented in the following sections:
When using the reload command, you may be prompted with the following message, even though no configuration changes were made.
Running-config is different from startup-config.
Save running to startup?[Yes/No]:No
Choose either Yes or No. In either case, all previously saved configurations will be retained.
Although the hw-module slot shutdown command appears in the global configuration command mode, it is not saved to Flash memory when a write command is used, so this configuration command does not survive a reload.
Node names cannot exceed 15 characters. If a node is given a name exceeding 15 characters, this command fails. In addition, the interfaces used in the failed command are not available for further use. If this occurs, use the discard rconf configuration command to discard all current draft configuration changes, and then begin the node configurations anew.
When running OC-12/STM-4 traffic on 4-port line cards, sometimes errors of type too short or too long Upgrade from Release 1.x
The active controller card must be reset before beginning the software download with the system reset command. This may result in a subsequent reset of the standby controller as well. When the controller(s) complete the reset, follow the standard upgrade procedure as described in "Upgrade from Release 1.x" section.
 |
Note Resetting the controllers does not effect the flow of traffic. |
In standard Cisco IOS releases, any configuration command can be preceded by the keyword no to revert to the default configuration. Release 3.5 of the ONS 15190 software does not support the full parameter list following the no command. For example, if the configuration contains the following command
ip default-gateway 190.10.12.1
then the following command
no ip default-gateway 190.10.12.1
is not acceptable. However, the command
no ip default-gateway
is acceptable and will result in the default gateway being set to its default value.
DOC-7811392 is the updated ONS 15190 Installation and Configuration Guide for Release 3.0.
DOC-7811392, the ONS 15190 Installation and Configuration Guide describes all new and existing features of the product, including all new CLI syntax.
The following sections provide sources for obtaining documentation from Cisco Systems.
You can access the most current Cisco documentation on the World Wide Web at the following sites:
Cisco documentation and additional literature are available in a CD-ROM package, which ships with your product. The Documentation CD-ROM is updated monthly and may be more current than printed documentation. The CD-ROM package is available as a single unit or as an annual subscription.
Cisco documentation is available in the following ways:
If you are reading Cisco product documentation on the World Wide Web, you can submit technical comments electronically. Click Feedback in the toolbar and select Documentation. After you complete the form, click Submit to send it to Cisco.
You can e-mail your comments to bug-doc@cisco.com.
To submit your comments by mail, use the response card behind the front cover of your document, or write to the following address:
Attn Document Resource Connection
Cisco Systems, Inc.
170 West Tasman Drive
San Jose, CA 95134-9883
We appreciate your comments.
Cisco provides Cisco.com as a starting point for all technical assistance. Customers and partners can obtain documentation, troubleshooting tips, and sample configurations from online tools. For Cisco.com registered users, additional troubleshooting tools are available from the TAC website.
Cisco.com is the foundation of a suite of interactive, networked services that provides immediate, open access to Cisco information and resources at anytime, from anywhere in the world. This highly integrated Internet application is a powerful, easy-to-use tool for doing business with Cisco.
Cisco.com provides a broad range of features and services to help customers and partners streamline business processes and improve productivity. Through Cisco.com, you can find information about Cisco and our networking solutions, services, and programs. In addition, you can resolve technical issues with online technical support, download and test software packages, and order Cisco learning materials and merchandise. Valuable online skill assessment, training, and certification programs are also available.
Customers and partners can self-register on Cisco.com to obtain additional personalized information and services. Registered users can order products, check on the status of an order, access technical support, and view benefits specific to their relationships with Cisco.
To access Cisco.com, go to the following website:
The Cisco TAC website is available to all customers who need technical assistance with a Cisco product or technology that is under warranty or covered by a maintenance contract.
If you have a priority level 3 (P3) or priority level 4 (P4) problem, contact TAC by going to the TAC website:
P3 and P4 level problems are defined as follows:
In each of the above cases, use the Cisco TAC website to quickly find answers to your questions.
To register for Cisco.com, go to the following website:
http://www.cisco.com/register/
If you cannot resolve your technical issue by using the TAC online resources, Cisco.com registered users can open a case online by using the TAC Case Open tool at the following website:
http://www.cisco.com/tac/caseopen
If you have a priority level 1 (P1) or priority level 2 (P2) problem, contact TAC by telephone and immediately open a case. To obtain a directory of toll-free numbers for your country, go to the following website:
http://www.cisco.com/warp/public/687/Directory/DirTAC.shtm l
P1 and P2 level problems are defined as follows:
This document is to be used in conjunction with the documents listed in the "Related Documentation" section.

Copyright © 2002, Cisco Systems, Inc.
All rights reserved.
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
Posted: Mon Apr 22 12:46:06 PDT 2002
All contents are Copyright © 1992--2002 Cisco Systems, Inc. All rights reserved.
Important Notices and Privacy Statement.