|
|

This chapter describes setup and recovery procedures that you may need to perform in the course of operating your LightStream 2020 multiservice ATM switch (LS2020 switch) in your network. These procedures are presented in this chapter in the following sections:
After completing the initial installation of LS2020 switch hardware and software, as described in the chapter entitled "Installing Network Management Software Applications," you may need to perform some or all of the setup procedures described in this chapter. Your network operating requirements determine which procedures you will need to perform. Hence, you should review these procedures to determine their applicability to your network.
Some setup procedures call for you to signal the master management agent (MMA) to re-read configuration data for the affected LS2020 switch. Note, however, that you can perform any or all of the procedures in this chapter without sending interim restart signals to the MMA. Thus, after completing the last of the setup procedures you intend to perform, you need only signal the MMA once to place all the setup procedures into effect.
The secure single-user mode is a feature that you can enable or disable at your discretion. The purpose of this feature is to prevent unauthorized superuser access to the NP of an LS2020 switch.
To enable or disable this feature, perform the following steps at the LS2020 console:
Step 1 Log in to the active NP as root.
Step 2 Using the copy command (cp), save and rename the /etc/starttab file, as shown below:
cp /etc/starttab /etc/starttab.unsecure
 | Warning If you do not save this file, as shown in the command above, you will not be able to access the NP (in the event of password loss) by means of the procedure in the next section entitled "Recovering from Loss of Password for Secure Single-User Mode." Instead, you will have to perform a freshdisk installation to regain access to the NP. |
Step 3 Invoke the vi editor to open the /etc/starttab file:
vi /etc/starttab
Step 4 Locate the following comment line in the /etc/starttab file:
"#Name of single_user shell"
/bin/singleuser_login
/bin/bash
Step 5 Close the file and exit the vi editor by entering ZZ.
To restore multi-user mode after running in the secure single-user mode, you must first log out from the NP (by entering ^D, for example). After logging out, the following sequence occurs:
y,
Mount all filesystems (y/n) [y]
y, the NP is activated, and the system runs the platform software in multi-user mode.
If you press Return or enter n in response to the Mount all filesystems prompt, the file system will not be mounted. In addition, the system will warn you that
"The minimum network management information has not been configured!"
and you will be asked if you want to
"Create a minimal network management configuration? (y/n) [y] "
Enter n in response to this query.
This section presents a recovery procedure to be used if a password is lost when you attempt to log in to the NP with the secure single-user mode enabled.
If the secure single-user mode is enabled and you do not have a password, you cannot gain superuser access to the NP from the console, nor can you gain root access to either NP in a redundant-NP system.
Nevertheless, assuming that your LS2020 chassis contains a floppy disk drive, you can still gain superuser access to the NP, or to the second NP in a redundant-NP system, by performing the following procedure:
Step 1 From the TCS hub prompt, reset and immediately connect to the NP by issuing the following commands:
TCS HUB<<A>> reset <NP_slot>
TCS HUB<<A>> conn <NP_slot>
where <NP_slot> represents the NP to which you wish to gain access.
Step 2 Interrupt the NP boot by pressing Return when the following prompt appears:
System will boot in 5 seconds: hit <RETURN> to interrupt
Step 3 Insert the System Boot floppy diskette into the appropriate floppy drive for the NP in question. For example, if the NP that you wish to recover is in Slot 2, use the topmost disk drive in the LS2020 chassis; if the NP that you wish recover is in Slot 1, use the bottom disk drive.
Step 4 From the "Network Processor bootstrap" menu, select option 2, as shown below:
1 - Boot ATM switch application
2 - Begin full installation with boot from floppy disk
3 - List contents of hard disk root directory
4 - List contents of floppy disk root directory
5 - Boot system single-user
6 - Escape to full set of bootstrap options
Option> 2
Step 5 When the boot process from the floppy diskette completes, perform a file system check for each partition on the NP's hard disk, as indicated below:
single-user$ fsck /dev/sd0a
...(file system messages are displayed to the console)...
single-user$ fsck /dev/sd0b
...(file system messages are displayed to the console)...
single-user$ fsck /dev/sd0c
...(file system messages are displayed to the console)...
single-user$ fsck /dev/sd0d
...(file system messages are displayed to the console)...
Step 6 Mount the hard disk's partition containing the starttab file that you want to recover by issuing the following command:
single-user$ mount /dev/sd0a /mnt
This command must be entered exactly as shown; otherwise, Step 7 will fail.
Step 7 Restore the original starttab file by issuing the following commands:
single-user$ rm /mnt/etc/starttab
single-user$ cp /mnt/etc/starttab.unsecure /mnt/etc/starttab
 | Warning If you did not save the starttab file, as described in the preceding section entitled "Enabling/Disabling Secure Single-User Mode," you must perform a freshdisk installation to regain access to this NP. |
Step 8 The starttab file providing unsecure single-user login has now been restored on the NP hard disk. Remove the System Boot floppy disk from the floppy drive and store it in a safe place.
Step 9 Obtain the TCS hub prompt by entering the following command:
single-user$ '.
Step 10 At the TCS hub prompt, reset and connect to the NP, as shown below:
TCS HUB<<A>> reset <NP_slot>
TCS HUB<<A>> conn <NP_slot>
Step 11 From the "Network Processor bootstrap" menu, select Option 2:
1 - Boot ATM switch application
2 - Begin full installation with boot from floppy disk
3 - List contents of hard disk root directory
4 - List contents of floppy disk root directory
5 - Boot system single-user
6 - Escape to full set of bootstrap options
Option> 2
Step 12 When the boot process from the diskette is complete, perform a file system check for each partition on the NP's hard disk:
single-user$ fsck /dev/sd0a
...(file system messages are displayed to the console)...
single-user$ fsck /dev/sd0b
...(file system messages are displayed to the console)...
single-user$ fsck /dev/sd0c
...(file system messages are displayed to the console)...
single-user$ fsck /dev/sd0d
...(file system messages are displayed to the console)...
Step 13 Mount all hard disk partitions, as follows:
single-user$ mount -a
Step 14 When prompted by the /bin/passwd program, enter a new password for each account name (<id>) in the /etc/passwd file by issuing the command shown below. You must repeat this step for each account name.
single-user$ /bin/passwd <id>
Step 15 Reboot the NP. To obtain the boot prompt menu, issue the reboot -n command. To reboot the multiuser LynxOS operating system, press ^D, <CTRL-D>.
This section describes how to create a new user account. The LS2020 switch provides an adduser script to simplify the task of adding a new user account to your system.
To create a new user account, perform the following steps:
Step 1 Log in to the root account on your LS2020 switch to bring up the bash# prompt.
Step 2 Start the adduser script by entering the following at the prompt:
bash# adduser
Step 3 Enter the login name for the new user account at the following prompt:
Enter login name, must be <= 8 characters:
Step 4 Enter the full name for the new user account at the following prompt:
Enter user's full name:
The system then displays the login account information shown below:
Login Name: <login>
User ID: <UID>
Home Directory: /usr/<login>
Password Entry: <login>::<UID>:<GID>:<username>:/usr/
<login>: /bin/bash
where:
<login> is the login name of the user.
<UID> is the user identification number.
<GID> is the group identification number.
<username> is the full name of the user.
Step 5 If the information displayed in Step 4 is correct, respond yes (Y) to the following prompt:
Add the new user to the password database (Y/N)? [Y]
Step 6 Enter a password for the new user at the following prompt:
Adding entry to the /etc/passwd database
Making /usr/<login> home directory
Changing password for <login>
Enter new password:
The password must be unique and at least six alphanumeric characters in length.
Step 7 Re-enter the password at the prompt for confirmation:
Retype new password:
If you entered the new password correctly, the system changes the existing password and displays the following prompt:
bash#
As a result of this procedure, a new user account is created with the attributes you specified. You can then log in to the new user account and begin using it.
Each LS2020 switch has a file detailing the privileges for each switch in the network that has read or read/write access to its MMA. To monitor the network, you need to have only read access privileges to the MMA; however, to make changes to MMA values or to issue control commands, you need to have read/write access privileges to the MMA.
LS2020 software maps the SNMP community name and IP address of each LS2020 switch to a set of privileges. Each switch has a default file named /usr/app/base/config/mma.communities that contains details about the SNMP communities and access privileges defined for the switch. Figure 4-1 shows an example of such a file. The lines in this sample file preceded by the number sign (#) are informational comments; the last three lines of this file show the names of the defined SNMP communities (public, trap, and write).
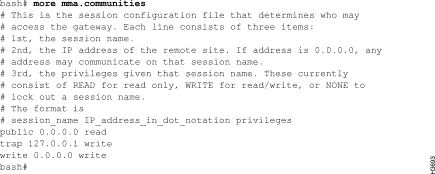
The line public 0.0.0.0 read indicates that a user issuing commands from any IP address (IP address 0.0.0.0) who has set the SNMP community name to public has read access privileges to the MMA for this switch.
The line trap 127.0.0.1 write indicates that a user issuing commands from this local switch (that is, IP address 127.0.0.1) who has set the SNMP community name to trap has read/write access privileges to the MMA for this switch.
The line write 0.0.0.0 write indicates that a user issuing commands from any IP address (that is, IP address 0.0.0.0) who has set the SNMP community name to write has read/write access privileges to the MMA for this switch.
SNMP community names can be used to provide a level of security for each LS2020 switch in the network. For this reason, it is advisable to change the names of the trap and write SNMP communities to names of your choosing. By so doing, you can restrict access to your LS2020 switch to only those users who know your SNMP community name(s).
set snmp community <community_name> command at the CLI prompt.
As a convention, most SNMP devices have a public community name with read-only access privileges. You should not change this name, but you can change its associated privileges, if necessary.
To change the default SNMP community name or the MMA read/write access privileges for your LS2020 switch, edit the file mma.communities according to the following procedure:
Step 1 Log in to the root account on your LS2020 switch.
Step 2 Change to the directory containing the files you want to edit by entering the following command:
bash# cd /usr/app/base/config
Step 3 Move the mma.communities file to a file renamed mma.communities.orig to maintain the symbolic link between the two files, as shown below:
bash# mv mma.communities mma.communities.orig
Step 4 Copy the contents of the linked mma.communities.orig file to a new file named mma.communities by entering the following command:
bash# cp mma.communities.orig mma.communities
As a consequence of Steps 3 and 4, you now have two mma.communities files, containing identical information. Note, however, that the copy operation does not carry the symbolic link forward into the new, renamed mma.communities file. Thus, the resulting mma.communities file is not linked to any other files, while the mma.communities.orig file remains linked to the current /usr/app/dist/base-x.x.x/config/mma.communities file.
There are two reasons for creating a new mma.communities file for the LS2020 switch in the manner described above:
Step 5 Invoke the vi editor to revise the mma.communities file by entering the following command:
bash# vi mma.communities
Change the mma.communities file to reflect your desires for SNMP community names.
If you are not familiar with the vi editor, refer to the LightStream 2020 NP O/S Reference Manual for additional information.
Step 6 Save the changes to the edited mma.communities file and exit the vi editor by entering ZZ.
Step 7 Use either of the following methods to cause the MMA to re-read the mma.communities file:
bash# ps -ax
bash# kill -hup <mma pid #>
<mma pid #> is the PID number determined above for the MMA process in this LS2020 switch.
cli> walk pidName
cli> protected
Enter password:
*cli>). Enter the following command to cause the MMA to re-read the mma.communities file:
*cli> shell "kill -hup <mma pid #>"
Step 8 If you wish to verify your changes to the mma.communities file, enter the following at the protected mode CLI prompt:
*cli> shell "more /usr/app/base/config/mma.communities"
This command displays the mma.communities file for inspection.
If you wish to exit the protected mode CLI at this juncture, issue the following command:
*cli> quit
Step 9 Repeat Steps 2 through 8 for each LS2020 switch in the network whose default SNMP community name or read/write access privileges you wish to change.
At the conclusion of this procedure, you have defined one or more new SNMP community names for one or more LS2020 switches to reflect your particular network operating requirements.
When you start the CLI, the LS2020 switch finds the addresses for trap delivery in the /usr/app/base/config/mma.trap_communities file. By default, LS2020 switches send traps only to their local network processor (NP) card. However, by editing the mma.trap_communities file, you can cause traps to be sent to as many as 25 different destinations. Similarly, by editing this file, you can also cause traps for all LS2020 switches in the network to be sent to the same device.
For additional information about trap-handling mechanisms, refer to the LightStream 2020 Traps Reference Manual.
This section tells you how to edit the mma.trap_communities file. Before proceeding, however, note that each line in the mma.trap_communities file consists of three elements:
Figure 4-2 shows a sample mma.trap_communities file. The first entry in each line is the community name (trap); the second entry is an IP address (the default IP address, the NP IP address, the NMS IP address, or the IP address of a destination device); the third entry (162) identifies the UDP port number for delivering traps.

To change the trap delivery IP address(es) for an LS2020 switch, edit the file mma.trap_communities according to the following procedure:
Step 1 Determine the IP addresses where you want traps to be sent (any one or more of up to 25 different IP address, including another NP, an NMS, or a designated destination device).
Step 2 Log in to the root account on your LS2020 switch.
Step 3 Change to the directory containing the mma.trap_communities file you want to edit by entering the following command:
bash# cd /usr/app/base/config
Step 4 Move the mma.trap_communities file to a file renamed mma.trap_communities.orig to maintain the symbolic link between the two files, as shown below:
bash# mv mma.trap_communities mma.trap_communities.orig
Step 5 Copy the contents of the now linked mma.trap_communities.orig file to a new file named mma.trap_communities by entering the following command:
bash# cp mma.trap_communities.orig mma.trap_communities
As a consequence of Steps 4 and 5, you now have two mma.trap_communities files, each containing identical information. Note, however, that the copy operation does not carry the symbolic link forward into the new, renamed mma.trap_communities file. Thus, the resulting mma.trap_communities file is not linked to any other files, and the mma.trap_communities.orig file remains linked to the current operational /usr/app/dist/base-x.x.x/config/mma.trap_communities file for your LS2020 switch.
There are two reasons for creating a new mma.trap_communities file in the manner described above:
Step 6 Invoke the vi editor to edit the mma.trap_communities file by entering the following command:
bash# vi mma.trap_communities
Change the mma.trap_communities file to reflect your desires for LS2020 trap delivery. Do this by defining the community name (trap), the IP address for trap delivery (to another NP, an NMS, or a destination device), and the UDP port number through which the SNMP protocol will send traps from your LS2020 switch.
If you are not familiar with the vi editor, refer to the LightStream 2020 NP O/S Reference Manual for additional information.
Step 7 Save the changes to the mma.trap_communities file and exit the vi editor by entering the following:
ZZ
Step 8 Use either of the following methods to cause the MMA to re-read the mma.trap_communities file:
bash# ps -ax
bash# kill -hup <mma pid #>
<mma pid #> is the PID number determined above for the MMA process in the LS2020 switch.
cli> walk pidName
cli> protected
Enter password:
*cli>), at which you enter the following command to cause the MMA to re-read the mma.trap_communities file:
*cli> shell "kill -hup <mma pid #>"
Step 9 If you wish to verify your changes to the mma.trap_communities file, enter the following at the protected mode CLI prompt to examine the contents of the file:
*cli> shell "more /usr/app/base/config/mma.trap_communities"
If you wish to exit the protected mode CLI at this point, issue the following command:
*cli> quit
Step 10 Repeat Steps 3 through 9 for each LS2020 switch in the network whose trap delivery IP address(es) you wish to change.
At the conclusion of the above procedure, traps will be sent to the IP address(es) specified in the revised mma.trap_communities file.
Whenever you log in to the CLI, the default terminal type of each user account (oper, npadmin, fldsup, and root) is set to vt100. If you do not use a VT100 terminal, you may change the default terminal type in your .profile file to preclude having to change the vt100 setting at each log in. The procedures described in this section enable you to change the default terminal type in the .profile file for each LS2020 user account. You can change the default terminal type from either the bash# prompt or the CLI prompt, as described in the following sections.
To change the default terminal type from the bash# prompt, perform the following steps:
Step 1 Verify that the terminal type you want to use is defined in the /etc/termcap file.
Step 2 Log in to the fldsup account or the root account for the LS2020 switch whose default terminal type you wish to change.
Step 3 Edit the terminal type for the oper account by entering the following:
bash# vi /usr/oper/.profile
The vi editor opens, enabling you to edit the .profile file.
Step 4 Change the default terminal type for the oper account by editing the line that reads
TERM=vt100
You should change this line to reflect the terminal type that you intend to use. (The terminal type you enter must be defined in the /etc/termcap file.)
If the line TERM=vt100 does not appear in the .profile file, add this line to the file in the following format:
TERM=<your default terminal type>
Step 5 Save your changes to the .profile file and exit from the vi editor by entering the following:
ZZ
Step 6 Repeat Steps 3 through 5 for each remaining LS2020 login account (npadmin, fldsup, and root) by editing the following files, as appropriate:
/usr/npadmin/.profile
/usr/fldsup/.profile
/usr/root/.profile
Step 7 Repeat this procedure for any other user accounts that you may have created, in addition to the four user accounts referenced above (oper, npadmin, fldsup, and root).
The new terminal type does not take effect until you log in again.
To change the default terminal type from the CLI prompt, perform the following steps:
Step 1 Verify that the terminal type you want to use is defined in the /etc/termcap file.
Step 2 Enter the following at the CLI prompt:
cli> protected
*cli>), at which you enter the protected mode password:
*cli> <password>
Step 3 Open the oper account by entering the following:
*cli> shell "vi /usr/oper/.profile"
The vi editor opens, enabling you to edit the .profile file.
Step 4 Change the default terminal type for the oper account by editing the line that reads:
TERM=vt100
You should change the line to reflect the terminal type you intend to use. (The terminal type you enter must be defined in the /etc/termcap file.)
If the line TERM=vt100 does not appear in the .profile file, add this line to the file in the following format:
TERM=<your default terminal type>
Step 5 Save your changes to the .profile file and exit from the vi editor by entering the following:
ZZ
Step 6 Repeat Steps 3 through 5 for each remaining LS2020 login account (npadmin, fldsup, and root) by editing the following files, as appropriate:
/usr/npadmin/.profile
/usr/fldsup/.profile
/usr/root/.profile
Step 7 Repeat this procedure for any other user accounts that you may have created, in addition to the four user accounts referenced above (oper, npadmin, fldsup, and root).
The new terminal type for the LS2020 switch does not take effect until you log out and log in again.
As the network administrator, you must maintain the /usr/etc/hosts file for each network processor (NP) in your network. This file, which serves as a repository for the names and IP addresses of all NPs in the network, is created at installation time, but you must ensure that an entry exists in this file for each NP in, or being added to, your network. Figure 4-3 shows typical content of a /usr/etc/hosts file.

To edit the /usr/etc/hosts file, perform the following steps:
Step 1 Log in to the LS2020 switch as root.
Step 2 At the bash# prompt, change to the /usr/etc directory by entering the following command:
bash# cd /usr/etc
Step 3 Enter the following command to open the hosts file for editing with the vi editor:
bash# vi hosts
If you are unfamiliar with the vi editor, refer to the LightStream 2020 NP O/S Reference Manual for additional information.
Step 4 Append to the end of the hosts file the names and IP addresses of the network processors being added to your network. Use the format shown in Figure 4-3 in making these entries.
Step 5 Save your changes to the hosts file and exit the vi editor by entering ZZ. This action returns you to the bash# prompt.
Editing of the /usr/etc/hosts file is now complete.
 | Caution The /usr/etc/hosts file on each LS2020 network processor contains chassis-specific information that is entered automatically and modified each time the LS2020 switch is booted. Therefore, do not copy the /usr/etc/hosts file from one LS2020 switch or network processor to another such device in your network. |
|
|