|
|

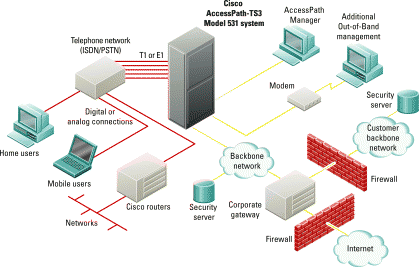
| Gather Information |
Gather and record the system information in
this section prior to configuring the
Cisco AccessPath-TS3 Model 531 system (or
Cisco Accesspath-LS3). Having this information readily available before you begin will simplify the configuration process.
1. Configuration Identification
Example: Cisco. Give a name to the group of systems you are configuring. 
2. Site Identification
Example: sanjose. Give a name to the system you are configuring. This name is used as a prefix appended to each host name in the system (for example: sanjoseas01). 
1. Number of Access Servers
Enter the number of Cisco AS5300s in your system. There can be between 1 and 21 Access Servers in a given system (between 1and 4 for the AccessPath-LS3). 
2. Number of Routers
Enter the number of Cisco 7206s in the system. This will vary according to the size of your system.
| 0 for AP-LS3 |
| 1 (default) for Entry and Midrange AP-TS3 systems |
| 2 for High-End or High-End/Extended systems |
3. Type of System
Specify the switch used in the system. This will vary according to the size of the system.
| AP-TS3 Entry—Cisco 7206 Switch Blade |
| AP-TS3 Midrange to High-End/ Extended— Cisco Catalyst 5002 (default) |
| AP-LS3—None |
4. PRI Density
Select the PRI density for each Cisco AS5300 access server (as) in the system. The Cisco AccessPath-LS3 only allows 4 PRI.
| 8 PRI | 4 PRI |
| 8 PRI | 4 PRI |
as1 | | | as12 | | |
as2 | | | as13 | | |
as3 | | | as14 | | |
as4 | | | as15 | | |
as5 | | | as16 | | |
as6 | | | as17 | | |
as7 | | | as18 | | |
as8 | | | as19 | | |
as9 | | | as20 | | |
as10 | | | as21 | | |
as11 | | |
|
|
|
| Gather Information (continued) |
1. System Channel Type
Choose MultiChannel to configure MMP, or SingleChannel to disallow Multilink PPP.
| SingleChannel(default) |
| MultiChannel |
2. (Optional) System Name
Required for MMP only. Select the SGBP group name that the system components will share. 
3. (Optional) IOS SGBP Password
Required for MMP only. Used by SGBP group members. 
4. System VPDN information
Choose to enable or disable VPDN. The Cisco AccessPath-TS3 Model 531 system will support VPDN, if enabled. However, VPDN requires additional configuration on an AAA server and on a home gateway.
| Disable VPDN (default) |
| Enable VPDN |
5. Allow users to log in to the EXEC level?
| No (default) |
| Yes |
6. External Host Name
Enter the external host name for CHAP to use. This required field is used as the host name that remote CHAP users see. 
7. (Optional) Remote User DNS Servers
Select default DNS servers for the remote users. List their IP addresses, and when you enter IP addresses, separate them with a space.



8. (Optional) Remote User NBNS Servers
Select default NBNS servers for the remote users. List their IP addresses, and when you enter IP addresses, separate them with a space.



| Gather Information (continued) |
1. Trunk Type
Select the trunk type of the incoming lines.
| T1 PRI |
| E1 PRI |
| Channelized T1 (CT1) |
| E1 R2 |
2. Framing
For T1, select SF or ESF.
For E1, select CRC4 or no CRC4.
| SF |
| ESF (default) |
| CRC4 |
| no CRC4 |
3. Line Code
For T1, select B8ZS or AMI.
For E1, select HDB3 or AMI.
| AMI |
| B8ZS (default) |
| HDB3 |
4. (T1 or E1 PRI only) ISDN Switch Type
Select the ISDN switch type used.
| AT&T 5ess (default) |
| AT&T 4ess |
| NorTel DMS100 |
| NET5 (Europe) |
| NTT (Japan) |
| TS014 (Australia) |
| National ISDN |
5. (For CT1 only) CT1 Signaling Options
Choose the Channelized T1 signaling type appropriate for the incoming lines.
| Foreign Exchange Station—Loop Start (default) |
| Foreign Exchange Station—Ground Start |
| E&M Feature Group B DTMF |
| E&M Feature Group B DTMF DNIS |
| E&M Feature Group B MF |
| E&M Feature Group B MF DNIS |
| E&M Feature Group D DTMF |
| E&M Feature Group D DTMF DNIS |
| E&M Feature Group D MF |
| E&M Feature Group D MF DNIS |
| E&M Immediate Start |
| Specific Attach Station—Ground Start |
| Specific Attach Station—Loop Start |
6. (For E1 R2 only) E1 R2 Signaling Options
Choose the E1 R2 signaling type appropriate for the incoming lines.
| Foreign Exchange Station—Loop Start (default) |
| Foreign Exchange Station—Ground Start |
| E&M Feature Group B |
| E&M Feature Group D |
| E&M Immediate Start |
| P7 Switch |
| R2 ITU Q411- R2 analog |
| R2 ITU Q421- R2 digital |
| R2 ITU Supplement 7—Pulse |
| Specific Attach Station—Loop Start |
| Specific Attach Station—Ground Start |
| Gather Information (continued) |
7. (For E1 R2 only) Custom E1 R2 Country
Select the appropriate country for R2 CAS-custom country options. If no country is selected, ITU defaults are assumed.
| ITU (default) |
| Argentina |
| Brazil |
| China |
| Colombia |
| Costa Rica |
| Indonesia |
| Israel |
| Malaysia |
| Phillipines |
| Telemex - Mexico |
| Telnor - Norway |
| Thailand |
| Venezuela |
1. Internal Routing Protocol
Select the internal routing protocol for the Cisco AccessPath-TS3 Model 531 stystem.
| OSPF (Open Shortest Path First) |
| EIGRP (Enhanced Internal Gateway Routing Protocol) |
2. (Optional) EIGRP Autonomous System Number
This should be a number from 1 to 65535 and is globally significant. 
3. (Optional) OSPF Process ID
This should be a number from 1 to 65535 and is only locally significant. 
4. (Optional) OSPF Area Number
This should be a number from 0 to 100000. It is globally significant if your backhaul is also running OSPF.
5. Primary Network IP Address
The Cisco AccessPath-TS3 Model 531 system uses Variable-Length Subnet Masking (VLSM) for internal routing. Enter the 4 octets of the 26-bit subnet for the primary (Fast Ethernet and Loopback) interfaces in the system. Although this subnet can be of any size greater than 26 bits, enter it as a 26-bit subnet. The fourth octet must be 0, 64, 128, or 192.
6. Secondary Network IP Address
Enter the four octets of the 26-bit subnet for the secondary (Ethernet and Loopback) interfaces. The 4th octet must be 0, 64, 128, or 192.
7. Network IP Address - Pools
Enter the starting network number of the range of Class C IP addresses used to populate dial-in pools for end users. The 4th octet must be 0.
| Gather Information (continued) |
1. SNMP Access
Enable or disable SNMP access and trap logging. If SNMP is disabled, options 2 through 7 that follow are unnecessary.
| Access Disabled (default) |
| Access Enabled |
2. (Optional) SNMP Server IP Address
Enter the management workstation IP Address.
3. (Optional) Location
Name the physical location of the system (no spaces allowed). Example: sanjose
4. (Optional) Contact Name
Name the person responsible for the system (no spaces allowed). Example: tedsmith
5. (Optional) Read Only Community String
A "password" allowing SNMP read-only access. SNMP community strings are typically words like "private" or "public."
6. (Optional) Write Community String
A "password" allowing SNMP write access.
7. (Optional) Read/Write/All Community String
A "password" allowing all SNMP access. This is used only in the Cisco Catalyst 5002 Switch.
1. Message Logging
Enable or disable logging of system error messages to a UNIX-based syslog server. If logging is disabled, all other options are unnecessary.
| Logging Disabled (default) |
| Logging Enabled |
2. (Optional) Syslog Server IP Address
Specify the IP address of the syslog server.
3. (Optional) Log Level
Messages at or below the chosen severity level will be sent to the syslog server.
| Debugging messages (7) |
| Informational messages only (6) (default) |
| Normal but significant condition (5) |
| Warning conditions (4) |
| Error conditions (3) |
| Critical conditions (2) |
| Immediate action needed(1) |
| System unusable (0) |
| Gather Information (continued) |
4. (Optional) Log Facility
Configure the syslog server facility that handles error messages. The syslog server will pass error messages differently, based on the message class (which is based on Log Level and Log Facility) and the /etc/syslog.conf file.
| Authorization system |
| Chron/at facility |
| System daemons |
| Kernel |
| Local Use 0 |
| Local Use 1 |
| Local Use 2 |
| Local Use 3 |
| Local Use 4 |
| Local Use 5 |
| Local Use 6 |
| Local Use 7 (default) |
| Line Printer system |
| Mail System |
| Usenet news |
| System Use 10 |
| System Use 11 |
| System Use 12 |
| System Use 13 |
| System Use 14 |
| System Use 9 |
| Syslog |
| User Process |
| UNIX-to-UNIX copy system |
1. Security Server
Specify the security used by the Access Servers.
| none (default) |
| RADIUS |
| TACACS+ |
2. (Optional) Primary AAA Server IP
Enter the IP address for the primary AAA server (if used).
3. (Optional) Secondary AAA Server IP
Enter the IP address for the secondary AAA server (if used).
4. (Optional) Separate Accounting Server
This is a RADIUS feature reserving one server for accounting only, and forcing the other AAA servers (configured in AAA options 2 and 3) to only handle authentication and authorization. Choose whether to use this feature.
| Yes |
| No (default) |
5. (Optional) Separate Accounting Server IP
Enter the IP address of the separate accounting server (if used).
6. (Optional) AAA Server Key
Enter the AAA server key—a "password" needed for access.
| Gather Information (continued) |
1. (Optional) Primary NTP Server
Enter the IP address for the primary Network Time Protocol (NTP) server the system will use.
2. (Optional) Secondary NTP Server
Enter the IP address for the secondary NTP server the system will use.
3. (Optional) Domain Name Servers
Enter the IP addresses of up to six domain name servers for the system to use.


4. (Optional) Time Zone
Select the Time Zone and the Offset from GMT.
| No Time Zone configured |
| GMT-- U.K., Ireland (+0) |
| UTC -- Iceland, Portugal, West Africa (+0) |
| Middle Europe Time (Spain - Poland) (+1) |
| Mitteleuropaeische Zeit (+1) |
| UTC +1 (+1) |
| Eastern Europe (Athens, Helsinki, Istanbul, Kiev) (+2) |
| Israel (+2) |
| UTC +2 (+2) |
| South Africa (+2) |
| Russia (Moscow) (+3) |
| UTC +3 (Mecca) (+3) |
| UTC +4 (+4) |
| UTC +5 (Pakistan) (+5) |
| India (+5:30) |
| UTC +6 (+6) |
| UTC +7 (Bangkok, Jakarta, Hanoi, Kuala Lumpur) (+7) |
| UTC +8 (Singapore, Manila) (+8) |
| China (Beijing, Hong Kong, Taipei) (+8) |
| Western Australia (+8) |
| Japan (+9) |
| Korea (+9) |
| UTC +9 (+9) |
| Central Australia (+9:30) |
| Eastern Australia (+10) |
| UTC +10 (+10) |
| UTC +11 (+11) |
| New Zealand (+12) |
| UTC +13 (+13) |
| Dateline (-12) |
| Samoa (-11) |
| Hawaii (-10) |
| Alaska (-9) |
| Yukon (-9) |
| Pacific Time (US & Canada), Tijuana (-8) |
| Mountain Time (US & Canada), Mazatlan (-7) |
| Central Time (US & Canada) (-6) |
| UTC -6 (Mexico, Costa Rica) (-6) |
| Eastern Time (US & Canada) (-5) |
| UTC -5 (Columbia, Jamaica, Peru) (-5) |
| Atlantic Time (Canada) (-4) |
| UTC - 4 (Chile, Venezuela) (-4) |
| Newfoundland (-3:30) |
| UTC -3 (Eastern Brazil, Argentina)(-3) |
| UTC -2 (-2) |
| UTC -1 (-1) |
| Gather Information (continued) |
5. (Optional) Daylight Savings
Select the daylight savings zone for the system's location.
| No Summer Daylight Savings Time Configured |
| British Summer Time |
| Irish Summer Time |
| Middle Europe Summer Time |
| Mitteleuropaeische Sommerzeit |
| Israel Daylight time |
| Central Daylight Time (Australia) |
| Eastern Daylight Time (Australia) |
| New Zealand Daylight time |
| Alaska Daylight Time |
| Pacific Daylight Time |
| Mountain Daylight Time |
| Central Daylight Time (US) |
| Eastern Daylight Time (US) |
| Atlantic Daylight Time |
| Chile Daylight Time |
| UTC+DST (Eurasia: March - October) |
| UTC+DST (Brazil: October - February) |
These are the preselected passwords. You will need to edit the passwords in the configuration files before you load them on the system components to properly secure the system.
1. (Optional) Cisco IOS Enable Password
| cisco1 |
2. (Optional) Cisco IOS Enable Secret Password
| secret123 |
3. (Optional) Cisco IOS Line Password
(Used only in the System Controller configuration.)
| cisco2 |
1. Backhaul Routing Protocol
Select the routing protocol the Cisco 7206 will use to connect to the backbone network.
| none |
| OSPF |
| EIGRP |
| RIPv2 (Routing Information Protocol version 2) |
2. (Optional) EIGRP Autonomous System Number
This should be a number from 1 to 65535 and is globally significant. Required if EIGRP is selected.
3. (Optional) OSPF Process ID
Select a number from 1 to 65535. It is only locally significant. Required if the backhaul is running OSPF.
4. (Optional) OSPF Area Number
Select a number from 0 to 100000. It is globally significant if your internal routing is also OSPF. Required if the backhaul is running OSPF.
5. Backhaul Network
Enter the backhaul network IP address.

| Gather Information (continued) |
6. Backhaul Network Mask
Select the last octet of the backhaul network interface subnet mask.
| 0 |
| 128 |
| 192 |
| 224 |
| 240 |
| 248 |
| 252 |
| 254 |
7. Backhaul Interface Type
Select the backhaul interface type.
| None (default) |
| Fast Ethernet |
| HSSI |
| Synchronous Serial |
| Frame Serial |
8. Backhaul Interface Address
Enter the backhaul interface IP address. The second Cisco 7206 (if used) will get the next sequential address:

If you choose, you can download the default templates and modify them into custom templates for any system component, and then use the Cisco AccessPath-TS3 Configurator to enter data into these custom templates.
1. Customized Cisco 7206 Router Template
Give the local file path for the customized template to be uploaded and used to generate the configurations. (For regular Cisco 7206 routers only.)
2. Customized Cisco 7206 Router Template
(Entry systems only)
Give the local file path for the customized template to be uploaded and used to generate the configurations. (For Cisco 7206 routers with an additional port adapter.)
3. Customized Cisco AS5300 Access Server Template (8 PRI ISDN)
Give the local file path for the customized template to be uploaded and used to generate the configurations. 
| Gather Information (continued) |
4. Customized Access Server Template
(8 PRI Channelized)
Give the local file path for the customized template to be uploaded and used to generate the configurations. 
5. Customized Access Server Template
(4 PRI ISDN)
Give the local file path for the customized template to be uploaded and used to generate the configurations. 
6. Customized Cisco AS5300 Access Server Template (4 PRI Channelized)
Give the local file path for the customized template to be uploaded and used to generate the configurations. 
7. Customized 3640 System Controller Template
Give the local file path for the customized template to be uploaded and used to generate the configurations. 
8. Customized 3640 System Controller Template (AP-LS3 only)
Give the local file path for the customized template to be uploaded and used to generate the configurations. 
9. Customized Catalyst 5002 Switch Template
Give the local file path for the customized template to be uploaded and used to generate the configurations. 
All parameters needed to configure a Cisco AccessPath-TS3 Model 531 system can be saved in a separate file (called saved-parameters_ts3_ConfigID _SiteID), and the Configurator can use this file to set the parameters in the configuration files it generates. This may be convenient when configuring multiple systems in the same group.
1. Saved Configuration File
Give the local file path for the file to upload and use to initialize current parameter values. After uploading the file, you must confirm (by clicking OK on each Configurator screen) or modify parameters before generating a new configuration file set.
| Create Configuration Files |
The Cisco AccessPath-TS3 Model 531 system is shipped with a standard software configuration. Using the information gathered in Section 1 and the AccessPath-TS3 Configurator, create configuration files to apply to your system. The AccessPath-TS3 Configurator is a web-based application that creates text files you will later download into your AccessPath-TS3 system components (it also supports the Cisco AccessPath-LS3). To use it, you will need a web browser that supports javascript (Netscape Navigator or Microsoft Internet Explorer are ideal).
www.cisco.com/support/toolkit/AccessPathTS3
and follow the link provided to the AccessPath TS-3 Configurator.
Step 2 Enter the site information.
Step 3 Enter the general system information.
Step 4 Enter the dial-in information.
Step 5 Enter the trunk information.
Step 6 Enter the routing information.
Step 7 Enter the SNMP information.
Step 8 Enter the logging information.
Step 9 Enter the AAA information.
Step 10 Enter miscellaneous information.
Step 11 Enter the password information.
Step 12 Enter the backhaul information.
You also have the option of uploading custom configurations that the Configurator will collect new parameter values for, or a file that will provide input values for your units. After the information has been submitted and verified, the Configurator generates a configuration file for each component in the system and a web page that links to ways to download these files.
The Configurator provides three ways to get the configuration files:
Modify passwords before loading the configuration files. Open each file and look for lines like the following (default passwords are shown in bold):
enable password cisco1
enable secret secret123
line vty 0 31
password cisco2
| Connect to the System |
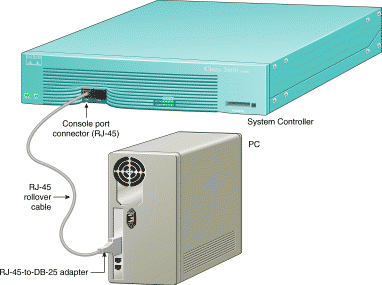
For the initial configuration, you must establish a direct terminal connection to the Cisco AccessPath-TS3 Model 531 system to download your new configuration files. Terminal connnection to the AccessPath-TS3 requires the following:
The System Controller provides console management services for each of the Cisco AccessPath-TS3 Model 531 system components. You will need to establish a direct connection to the System Controller, and from there you can connect to the other system components via reverse Telnet.
Take the following steps to connect a local terminal (an ASCII terminal or a PC running terminal emulation software) to the console port on the System Controller:
Step 2 Configure your terminal or PC terminal emulation software for 9600 baud, 8 data bits, no parity, and 1 stop bit.
The terminal should now show the following:
cms01>
| Download Configuration Files |
You can configure a system component via TFTP or by copying and pasting configuration file contents to the component's CLI. Use the "copy and paste" method for the initial setup, and TFTP to update a configuration.
cms01>enable
Password: secret123
cms01#
Step 2 Copy the contents of the CMS01 configuration file using your text editor, and paste them to the CLI for the System Controller.
Step 3 Enter the following command to save your configuration changes so that they will not be lost if there is a system reload or power outage:
cms01# copy running-config
startup-config
Building configuration...
It might take a minute or two to save the configuration. After the configuration has been saved, the following appears:
[OK]
cms01#
cms01# show running-config
Note the loopback1 IP address for the System Controller.
Step 2 Connect to the other system components in the following order:
1 Switch
2 Router(s)
3 Access Servers
To connect to other system components, specify the loopback 1 IP address and the port corresponding to each component, as shown:
cms01# telnet loopback1_Address Port
Replace loopback1_ Address with the actual loopback1 IP, and Port with the port number for the component. Refer to the port mappings table on page 14.
| Download Configuration Files (continued) |
| Port | Component | Configuration File |
|---|---|---|
2001 | Access Server 1 | AS01 |
2002 | Access Server 2 | AS02 |
2003 | Access Server 3 | AS03 |
2004 | Access Server 4 | AS04 |
2005 | Access Server 5 | AS05 |
2006 | Access Server 6 | AS06 |
2007 | Access Server 7 | AS07 |
2008 | Router 1 | RS01 |
2009 | Router 2 | RS02 |
2010 | - | - |
2011 | Switch | SW01 |
2012-2018 | - | - |
2019 | Access Server 8 | AS08 |
2020 | Access Server 9 | AS09 |
2021 | Access Server 10 | AS10 |
2022 | Access Server 11 | AS11 |
2023 | Access Server 12 | AS12 |
2024 | Access Server 13 | AS13 |
2025 | Access Server 14 | AS14 |
2026 | Access Server 15 | AS15 |
2027 | Access Server 16 | AS16 |
2028 | Access Server 17 | AS17 |
2029 | Access Server 18 | AS18 |
2030 | Access Server 19 | AS19 |
2031 | Access Server 20 | AS20 |
2032 | Access Server 21 | AS21 |
Step 3 Copy and paste the appropriate configuration file for the component.
Step 4 Save the configuration changes.
Step 5 Repeat this process for all system components, in the proper order (see page 13), until all system components are configured.
Your configuration is now complete.
To modify the configurations in more detail, download the default templates and modify them as desired. For a discussion of possible modifications, refer to http://www.cisco.com/univercd/cc/td/doc/product/ access/ap/ap_ts3/ap_ts3sw/config/index.htm
| Download Configuration Files (continued) |
To copy a configuration file from a TFTP server to a system component (this example uses the System Controller) while connected to that component:
CMS01# copy tftp startup-config
Step 2 Enter or confirm the IP address of the remote TFTP server:
Address of remote host
[255.255.255.255]? 192.168.245.2
Step 3 Specify the source filename. This example uses the UNIX filename cms01-confg to copy the cms01-confg file:
Name of configuration file
[router-confg]? cms01-confg
Configure using cms01-confg from
192.168.245.2? [confirm] y
Loading cms01-confg from
192.168.245.2 (via Ethernet1/0): !
[OK - 3147/128975 bytes]
[OK]
CMS01#
%SYS-5-CONFIG_NV: Non-volatile store
configured from cms01-confg by
console
tftp from 192.168.245.2
Step 4 Review the configuration to confirm it is really what you want to load:
CMS01# show startup-config
The System Controller displays the configuration loaded from the TFTP server.
Step 5 Reload the System Controller, as follows:
CMS01# reload
Proceed with reload? [confirm] y
*Feb 28 16:00:46.507 PST:
%SYS-5-RELOAD: Reload requested
Watch for error messages during the configuration load. The reload is done over a copy to prevent the configurations from merging. This ensures a clean reload and configuration.
Step 6 Repeat this process for all system components, in the proper order (see page 13), until all system components are configured.
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
Posted: Wed Jul 17 02:21:48 PDT 2002
All contents are Copyright © 1992--2002 Cisco Systems, Inc. All rights reserved.
Important Notices and Privacy Statement.