12.6 Checking Your Security by Using NmapMany users have misconfigured firewalls such that they are all but useless in defending against attacks. You can determine the state of your firewall by using the same tool hackers use to find its weaknesses, Nmap. To install Nmap, use the Package Management Tool to install the System Tools package group, and the extra packages nmap and nmap-frontend. Unfortunately, Nmap doesn't have a place on the GNOME or KDE menus. You can launch Nmap by issuing the command: # xnmap & from a terminal window. The Nmap screen should appear shortly thereafter, as shown in Figure 12-9. Figure 12-9. Nmap Nmap has enough features to be the topic of a book. You can learn more about Nmap from its author's web site, http://www.insecure.org/. A vanilla use of Nmap involves configuring it to send TCP or UDP packets to every important port of a specified system. The target system's responses reveal whether it has services listening on scanned ports. To configure Nmap to perform a TCP port scan, specify the IP address of the host, the connect( ) Scan Option, and the TCP & ICMP General Option. Then, commence scanning by clicking Scan. After a few minutes, you'll see a report like that shown in Figure 12-10. The report shown in the figure indicates that the target host is listening on eight TCP ports. To scan UDP ports, specify the UDP Port Scan Scan Option. UDP port scans are slower than TCP port scans and may take several minutes to complete. Figure 12-10. An Nmap report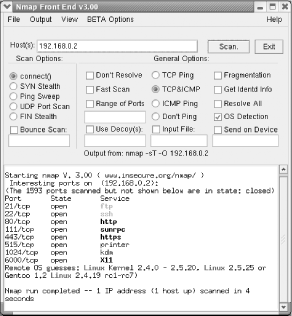 Some ports listed in Nmap's report may not be remotely accessible. Therefore, to accurately determine the state of a system, you must scan it remotely. If a remote scan of your system discloses unexpected open ports, you should check your firewall and service configurations to determine whether anything is amiss. Open ports above port 1023 that come and go with successive scans are not generally cause for concern. Usually, these are associated with established connections and are not really open. However, they can also be an early indication of the presence of a Trojan horse installed by an attacker. It's good practice to scan your hosts after you configure them so that you can later distinguish normal from abnormal behavior. |
