12.7 Firewalls
A firewall system is a popular way to provide network security. The term "firewall" implies protection from danger, and just as the firewall in your car protects the passengers' compartment from the car's engine, a firewall computer system protects your network from the outside world. A firewall computer provides strict access control between your systems and the outside world.
The concept of a firewall is quite simple. A firewall is a choke point through which all traffic between a secured network and an unsecured network must pass. In practice, it is usually a choke point between an enterprise network and the Internet. Creating a single point through which all traffic must pass allows the traffic to be more easily monitored and controlled and allows security expertise to be concentrated on that single point.
Firewalls are implemented in many ways. In fact, there are so many different types of firewalls, the term is almost meaningless. When someone tells you they have a firewall you really can't know exactly what they mean. Covering all of the different types of firewall architectures requires an entire book - see Building Internet Firewalls (O'Reilly & Associates). Here we cover the screened subnet architecture (probably the most popular firewall architecture), and the multi-homed host architecture, which is essentially a firewall-in-a-box.
The most common firewall architecture contains at least four hardware components: an exterior router, a secure server (called a Bastion Host), an exposed network (called a Perimeter Network), and an interior router. Each hardware component provides part of the complete security scheme. Figure 12.4 illustrates this architecture.
Figure 12.4: Screened subnet firewall
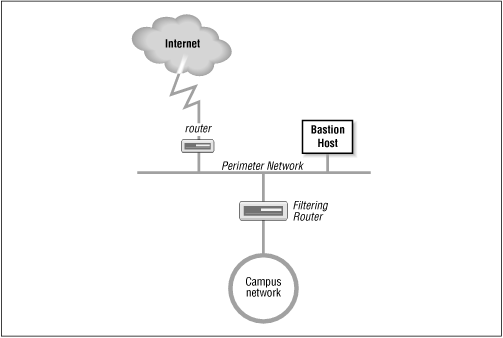
The exterior router is the only connection between the enterprise network and the outside world. This router is configured to do a minimal level of access control. It checks to make sure that no packet coming from the external world has a source address that matches the internal network. If our network number is 172.16, the exterior router discards any packets it receives on its exterior interface that contain the source address 172.16. That source address should only be received by the router on its interior interface. Security people call this type of access control packet filtering . In some ways it is similar to the packet filtering we did in Chapter 11, Troubleshooting TCP/IP because packets are "filtered out" based on IP header information.
The interior router does the bulk of the access control work. It filters packets not only on address but also on protocol and port numbers to control the services that are accessible to and from the interior network. What services are blocked by this router are up to you. If you plan to use a firewall, the services that will be allowed and those that will be denied should be defined in your security policy document. Almost every service can be a threat. These threats must be evaluated in light of your security needs. Services that are intended only for internal users (NIS, NFS, X-Windows, etc.) are almost always blocked. Services that allow writing to internal systems (the r commands, telnet, FTP, SMTP, etc.) are usually blocked. Services that provide information about internal systems (DNS, fingerd, etc.) are usually blocked. This doesn't leave much running! That is where the bastion host and perimeter network come in.
The bastion host is a secure server. It provides an interconnection point between the enterprise network and the outside world for the restricted services. Some of the services that are restricted by the interior gateway may be essential for a useful network. Those essential services are provided through the bastion host in a secure manner. The bastion host provides some services directly, such as DNS, SMTP mail services, and anonymous FTP. Other services are provided as proxy services . When the bastion host acts as a proxy server, internal clients connect to the outside through the bastion hosts and external systems respond back to the internal clients through the host. The bastion host can therefore control the traffic flowing into and out of the site to any extent desired.
There can be more than one secure server, and there often is. The perimeter network connects the servers together and connects the exterior router to the interior router. The systems on the perimeter network are much more exposed to security threats than are the systems on the interior network. This is as it must be. After all, the secure servers are needed to provide service to the outside world as well as to the internal network. Isolating the systems that must be exposed on a separate network lessens the chance that a compromise of one of those systems will lead directly to the compromise of an internal system.
The multi-homed host architecture attempts to duplicate all of these firewall functions in a single box. It works by replacing an IP router with a multi-homed host that does not forward packets at the IP layer. [8] The multi-homed host effectively severs the connection between the interior and exterior networks. To provide the interior network with some level of network connectivity, it performs similar functions to the bastion hosts.
[8] The role that IP routers, also called gateways, play in gluing the Internet together is covered extensively in earlier chapters.
Figure 12.5 shows a comparison between an IP router and a multi-homed host firewall. A router handles packets up through the IP layer. The router forwards each packet based on the packet's destination address, and the route to that destination indicated in the routing table. A host, on the other hand, does not forward packets. The multi-homed host processes packets through the Application Layer, which provides it with complete control over how packets are handled. [9]
[9] See the GATEWAY option in Chapter 5 , for information on how to prevent a multi-homed host from forwarding packets.
Figure 12.5: Firewalls versus routers
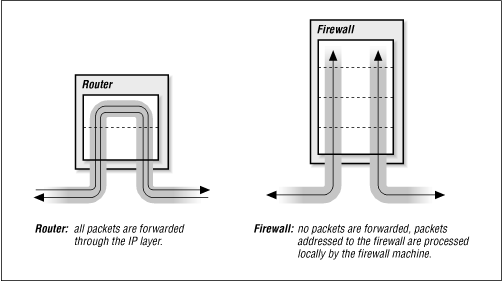
This definition of a firewall - as a device completely distinct from an IP router - is not universally accepted. Some people refer to routers with special security features as firewalls, but this is really just a matter of semantics. In this book, routers with special security features are called "secure routers" or "secure gateways." Firewalls, while they may include routers, do more than just filter packets.
12.7.1 Functions of the firewall
An intruder cannot mount a direct attack on any of the systems behind a firewall. Packets destined for hosts behind the firewall are simply delivered to the firewall. The intruder must instead mount an attack directly against the firewall machine. Because the firewall machine can be the target of break-in attacks, it employs very strict security guidelines. But because there is only one firewall versus many machines on the local network, it is easier to enforce strict security on the firewall.
The disadvantage of a firewall system is obvious. In the same manner that it restricts access from the outside into the local network, it restricts access from the local network to the outside world. To minimize the inconvenience caused by the firewall, the system must do many more things than a router does. Some firewalls provide:
-
DNS name service for the outside world
-
Email forwarding
-
Proxy services
Only the minimal services truly needed to communicate with external systems should be provided on a firewall system. Other common network services (NIS, NFS, rsh , rcp , finger , etc.) should generally not be provided. Services are limited to decrease the number of holes through which an intruder can gain access. On firewall systems, security is more important than service.
The biggest problems for the firewall machine are ftp service and remote terminal service. To maintain a high level of security, user accounts are discouraged on the firewall machine; however, user data must pass through the firewall system for ftp and remote terminal services. This problem can be handled by creating special user accounts for ftp and telnet that are shared by all internal users. But group accounts are generally viewed as security problems. A better solution is to provide proxy services on the firewall. To do this you need to run a proxy server on the firewall and proxy clients on your internal system. Most commercial client software includes support for proxy services. Many packages are compatible with SOCKS, a freely available proxy service package that can be downloaded from the Internet.
Because to be effective a firewall must be constructed with great care, and because there are many configuration variables for setting up a firewall machine, vendors offer special firewall software. Some vendors sell special-purpose machines designed specifically for use as firewall systems. Before setting up your own firewall, investigate the options available from your hardware vendor.
The details of setting up a firewall system are beyond the scope of this book. Before you proceed, I recommend you read Building Internet Firewalls and Firewalls and Internet Security , listed in the bibliography at the end of this chapter. Unless you have skilled UNIX systems administrators with adequate free time, a do-it-yourself firewall installation is a mistake. Hire a company that specializes in firewall design and installation. If your information is valuable enough to protect with a firewall, it must be valuable enough to protect with a professionally installed firewall.
Firewall systems are useful to many sites, but for some others they are not appropriate. The restrictions they place on individual users are not acceptable to some organizations, and these restrictions can drive independent-minded users to find other ways to handle their communications needs. Think seriously about your real security needs before selecting a solution.
12.7.2 Routing control
A firewall system works by controlling routing between the protected system and the rest of the world. A carefully modified static routing table can be used to provide a similar type of protection between internal systems on an enterprise network.
As we discussed in the chapters on routing and troubleshooting, it is necessary for your system to have a routing table entry for every network with which it will communicate. This can be either an explicit route for an individual network, or a default route for all networks. Without the proper routes, your system cannot communicate with remote networks, and the remote networks cannot communicate with your system. Regardless of how the remote site sets up its routing, it cannot communicate with your host if your host does not have a route back to the remote site. Because of this, you can control which remote sites are able to communicate with your system by controlling the contents of the routing table.
For example, assume that the nuts.com personnel department is on subnet 172.16.9.0, and that the router for their subnet is 172.16.9.1. They want to talk only to other hosts on their subnet and to a management system named hickory.nuts.com (172.16.18.7). To implement this policy with the routing table, each host administrator on the personnel subnet:
-
Makes sure that no routing protocol is running, and that none is started automatically at boot time.
-
Disables source routing.
-
Makes sure that there is no default route in the routing table, and that a default route is not added automatically at boot time.
-
Adds a host-specific route to 172.16.18.7 ( hickory.nuts.com ), and makes sure that this static route is added each time the system boots.
Using netstat to display this limited routing table on host 172.16.9.14 shows the following:
#netstat -nrRouting tables Destination Gateway Flags Refcnt Use Interface 127.0.0.1 127.0.0.1 UH 2 7126 lo0 172.16.18.7 172.16.9.1 UGH 1 1285 le0 172.16.9.0 172.16.9.14 U 30 89456 le0
The display shows the loopback route, a route to the local subnet (172.16.9.0), and a host route to hickory.nuts.com (172.16.18.7). There are no other routes, so there are no other locations with which this host can communicate. Therefore, if an intruder launched an attack against this system, he would receive no response.
This security technique is less restrictive than an internal firewall, because it affects only the systems that contain the data or processes that are being protected. This technique is easy to implement and does not require special equipment or software. However, it is also much less secure than a firewall. If any of these systems is successfully attacked, all of the systems could be compromised. Each system being protected this way must be properly configured, while one firewall can protect a group of systems. This works only when there are a small number of systems and they are all under the control of a single network administrator. In a few situations, this is a possible alternative to an internal firewall..




