6.6 Encryption Programs Available for UNIX
This section describes three encryption programs that are available today on many UNIX systems:
- crypt
-
The original UNIX encryption application.
- des
-
An implementation of the Data Encryption Standard.
- pgp
-
Phil Zimmermann's Pretty Good Privacy.
Each of these programs offers increasing amounts of security, but the more secure programs have more legal restrictions on their use in the United States.[24] Many other countries have passed legislation severely restricting or outlawing the use of strong cryptography by private citizens.
[24] We don't mean to slight our readers in countries other than the U.S., but we are not familiar with all of the various national laws and regulations around the world. You should check your local laws to discover if there are restrictions on your use of these programs.
6.6.1 UNIX crypt: The Original UNIX Encryption Command
UNIX crypt is an encryption program that is included as a standard part of the UNIX operating system. It is a very simple encryption program that is easily broken, as evidenced by AT&T's uncharacteristic disclaimer on the man page:
BUGS: There is no warranty of merchantability nor any warranty of fitness for a particular purpose nor any other warranty, either express or implied, as to the accuracy of the enclosed materials or as to their suitability for any particular purpose. Accordingly, Bell Telephone Laboratories assumes no responsibility for their use by the recipient. Further, Bell Laboratories assumes no obligation to furnish any assistance of any kind whatsoever, or to furnish any additional information or documentation.
- crypt reference page
Note that the crypt program is different from the more secure crypt() library call, which is described in Chapter 8, Defending Your Accounts .
6.6.1.1 The crypt program
The crypt program uses a simplified simulation of the Enigma encryption machine described in "The Enigma Encryption System" earlier in this chapter. Unlike Enigma, which had to encrypt only letters, crypt must be able to encrypt any block of 8-bit data. As a result, the rotors used with crypt must have 256 "connectors" on each side. A second difference between Enigma and crypt is that, while Enigma used three or four rotors and a reflector, crypt uses only a single rotor and reflector. The encryption key provided by the user determines the placement of the virtual wires in the rotor and reflector.
Partially because crypt has but a single rotor, files encrypted with crypt are exceedingly easy for a cryptographer to break. For several years, noncryptographers have been able to break messages encrypted with crypt as well, thanks to a program developed in 1986 by Robert Baldwin, then at the MIT Laboratory for Computer Science. Baldwin's program, Crypt Breaker's Workbench ( CBW ), decrypts text files encrypted with crypt within a matter of minutes, with minimal help from the user.
CBW breaks crypt by searching for arrangements of "wires" within the "rotor" that cause a file encrypted with crypt to decrypt into plain ASCII text. The task is considerably simpler than it may sound at first, because normal ASCII text uses only 127 of the possible 256 different code combinations (the ASCII codes 0 and 128 through 255 do not appear in normal UNIX text). Thus, most arrangements of the "wires" produce invalid characters when the file is decrypted; CBW automatically discards these arrangements.
CBW has been widely distributed; as a result, files encrypted with crypt should not be considered secure. (They weren't secure before CBW was distributed; fewer people simply had the technical skill necessary to break them.)
6.6.1.2 Ways of improving the security of crypt
We recommend that you do not use crypt to encrypt files more than 1K long. Nevertheless, you may have no other encryption system readily available to you. If this is the case, you are better off using crypt than nothing at all. You can also take a few simple precautions that will decrease the chances that your encrypted files will be decrypted:[25]
[25] In particular, these precautions will defeat CBW's automatic crypt-breaking activities.
-
Encrypt the file multiple times, using different keys at each stage. This essentially changes the transformation.
-
Compress your files before encrypting them. Compressing a file alters the information - the plain ASCII text - that programs such as CBW use to determine when they have correctly assembled part of the encryption key. If your message does not decrypt into plain text, CBW will not determine when it has correctly decrypted your message. However, if your attackers know you have done this, they can modify their version of CBW accordingly.
-
If you use compress or pack to compress your file, remove the 3-byte header. Files compressed with compress contain a 3-byte signature, or header, consisting of the hexadecimal values 1f, 9d and 90 (in that order). If your attacker believes that your file was compressed before it was encrypted, knowing how the first three bytes decrypt can help him to decrypt the rest of the file. You can strip these three bytes with the dd command:[26]
[26] Using dd this way is very slow and inefficient. If you are going to be encrypting a lot of compressed files, you may wish to write a small program to remove the headers more efficiently.
% compress -c <plaintext | dd bs=3 skip=1 | crypt >encrypted
Of course, you must remember to replace the 3-byte header before you attempt to uncompress the file:
% (compress -cf /dev/null;crypt <encrypted) | uncompress -c >plaintext
If you do not have compress , use tar to bundle your file to be encrypted with other files containing random data; then encrypt the tar file. The presence of random data will make it more difficult for decryption programs such as CBW to isolate your plaintext.
As encrypted files contain binary information, you must process them with uuencode if you wish to email them.
6.6.1.3 Example
To compress , encrypt , unencode , and send a file with electronic mail:
% ls -l myfile -rw-r--r-- 1 fred 166328 Nov 16 15:25 myfile % compress myfile % ls -l myfile.Z -rw-r--r-- 1 fred 78535 Nov 16 15:25 myfile.Z % dd if=myfile.Z of=myfile.Z.strip bs=3 skip=1 26177+1 records in 26177+1 records out % crypt akey < myfile.Z.strip | uuencode afile | mail spook@nsa.gov
To decrypt a file that you have received and saved in the file text file:
% head -3 file begin 0600 afile M?Z/#V3V,IGO!](D!175:;S9_IU\A7K;:'LBB,8363R,T+/WZSOC4PQ,U/6Q MX,T8&XZDQ1+[4Y[*N4W@A3@9YM*4XV+U\)X9NT.7@Z+W"WY^9-?(JRU,-4% % uudecode file % ls -l afile -rw-r--r-- 1 fred 78532 Nov 16 15:32 afile % (compress -cf /dev/null;crypt < afile) | uncompress -c > myfile
6.6.2 des: The Data Encryption Standard
There are several software implementations of the Data Encryption Standard that are commonly available for UNIX computers. Several of the most popular implementations are based on the des code written by Phil Karn, a UNIX guru (and ham radio operator whose call sign is KA9Q). In the past, some UNIX vendors have included des commands as part of their operating system, although many of these implementations have been removed so that the companies can maintain a single version of their operating system for both export and domestic use.[27] Nevertheless, des software is widely available both inside and outside the United States.
[27] For example, Sun Microsystems ships the easily broken crypt encryption program with Solaris, and sells a "US Encryption Kit" which contains the des program at a nominal cost.
The des command is a filter that reads from standard input and writes to standard output. It usually accepts the following command-line options:
% des -e|-d [-h] [-k key] [-b]
When using the DES , encryption and decryption are not identical operations, but are inverses of each other. The option -e specifies that you are encrypting a file. For example:
% des -e <message > message.des Enter key: mykey Enter key again: mykey % cat message.des "UI}mE8NZlOi\Iy|
(The Enter key: prompt is from the program; the key is not echoed.)
Use the -d option to decrypt your file:
% des -d < message.des Enter key: mykey Enter key again: mykey This is the secret message.
You can use the -k option to specify the key on the command line. On most versions of UNIX , any user of the system can use the ps command to see what commands other users are running. Karn's version of des tries to mitigate the danger of the ps command by making a copy of its command line arguments and erasing the original. Nevertheless, this is a potential vulnerability, and should be used with caution.
NOTE: You should never specify a key in a shell script: anybody who has access to read the script will be able to decode your files.
A -b option to the command selects Electronic Code Book ( ECB ) mode. The default is Cipher Block Chaining ( CBC ). As described in "DES modes" earlier in this chapter, ECB mode encodes a block at a time, with identical input blocks encoding to identical output blocks. This encoding will reveal if there is a pattern to the input. However, it will also be able to decrypt most of the file even if parts of it are corrupted or deleted. CBC mode hides repeated patterns, and results in a file that cannot be decrypted after any point of change or deletion.
If you use the -h option, des will allow you to specify a key in hexadecimal. Such keys should be randomly generated. If you do not specify a key in hexadecimal, then your key will most likely be restricted to characters that you can type on your keyboard. Many people further restrict their keys to words or phrases that they can remember (see the sidebar entitled "Number of Passwords" in Chapter 3, Users and Passwords ). Unfortunately, this method makes it dramatically easier for an attacker to decrypt a DES -encrypted file by doing a key search. To see why, consider the following table:
|
Key Choice Algorithm |
Keyspace |
Number of Possible Keys |
|---|---|---|
|
Random DES key |
128 8 = 2 56 |
7.2 x 10 16 |
|
Typeable characters[28] |
127 8 |
6.8 x 10 16 |
|
Printable characters |
96 8 |
7.2 x 10 15 |
|
Two words |
1,000,000 2 |
10 12 |
|
One word |
1,000,000 |
10 6 |
[28] You can't enter null as a character in your key.
Some versions of des will encrypt a file if it is specified on the command line. Input and output filenames are optional. If only one filename is given, it is assumed to be the input file.
Some versions of UNIX designed for export include a des command that doesn't do anything. Instead of encrypting your file, it simply prints an error message explaining that the software version of des is not available.
6.6.3 PGP: Pretty Good Privacy
In 1991, Phil Zimmermann wrote a program called PGP which performs both private key and public key cryptography. That program was subsequently released on the Internet and improved by numerous programmers, mostly outside of the United States.[29] In 1994, Zimmermann turned the distribution of PGP over to the Massachusetts Institute of Technology, which makes the software available for anonymous FTP from the computer net-dist.mit.edu .
[29] Get the whole story! Although this section presents a good introduction to PGP, the program is far too complicated to describe here. For a full description of PGP, we recommend the book PGP: Pretty Good Privacy by Simson Garfinkel (O'Reilly & Associates, 1995).
The version of PGP that is distributed from MIT uses the RSA Data Security software package RSAREF . This software is only available for noncommercial use. If you wish to use PGP for commercial purposes, you should purchase it from ViaCrypt International (whose address is listed in Appendix D ).
PGP Version 2 uses IDEA as its private key encryption algorithm and RSA for its public key encryption. (Later versions of PGP may allow a multiplicity of encryption algorithms to be used, such as Triple DES .) PGP can also seal and verify digital signatures, and includes sophisticated key-management software. It also has provisions for storing public and private keys in special files called key rings (illustrated in Figure 6.5 ). Finally, PGP has provisions for certifying keys, again using digital signatures.
Figure 6.5: PGP key rings
6.6.3.1 Encrypting files with IDEA
You can use PGP to encrypt a file with the IDEA encryption cipher with the following command line:
% pgp -c message Pretty Good Privacy(tm) 2.6.1 - Public-key encryption for the masses. (c) 1990-1994 Philip Zimmermann, Phil's Pretty Good Software. 29 Aug 94 Distributed by the Massachusetts Institute of Technology. Uses RSAREF. Export of this software may be restricted by the U.S. government. Current time: 1995/02/12 03:32 GMT You need a pass phrase to encrypt the file. Enter pass phrase: some days green tomatoes Enter same pass phrase again: some days green tomatoes Just a moment.... Ciphertext file: message.pgp %
Rather than using your pass phrase as the cryptographic key, PGP instead calculates the MD5 hash function and uses the hash. This means that you can use a pass phrase of any length. Because IDEA uses a 128-bit key, key-search attacks are not feasible.
PGP automatically compresses everything that it encrypts, which is fortunate, because after a file is encrypted, it cannot be compressed further: the output will appear random, and file compression requires some repeated patterns to compress.
If you want to decrypt your file, run PGP with the encrypted file as its sole argument:
% pgp message.pgp Pretty Good Privacy(tm) 2.6.1 - Public-key encryption for the masses. (c) 1990-1994 Philip Zimmermann, Phil's Pretty Good Software. 29 Aug 94 Distributed by the Massachusetts Institute of Technology. Uses RSAREF. Export of this software may be restricted by the U.S. government. Current time: 1995/02/12 03:47 GMT File is conventionally encrypted. You need a pass phrase to decrypt this file. Enter pass phrase: some days green tomatoes Just a moment....Pass phrase appears good. . Plaintext filename: message %
If you do not type the correct pass phrase, PGP will not decrypt your file:
% pgp message.pgp Pretty Good Privacy(tm) 2.6.1 - Public-key encryption for the masses. (c) 1990-1994 Philip Zimmermann, Phil's Pretty Good Software. 29 Aug 94 Distributed by the Massachusetts Institute of Technology. Uses RSAREF. Export of this software may be restricted by the U.S. government. Current time: 1995/02/12 03:48 GMT File is conventionally encrypted. You need a pass phrase to decrypt this file. Enter pass phrase: I am the walrus Just a moment... Error: Bad pass phrase. You need a pass phrase to decrypt this file. Enter pass phrase: Love will find a way Just a moment... Error: Bad pass phrase. For a usage summary, type: pgp -h For more detailed help, consult the PGP User's Guide. %
6.6.3.2 Creating your PGP public key
The real power of PGP is not the encryption of files, but the encryption of electronic mail messages. PGP uses public key cryptography, which allows anybody to create a message and encrypt it using your public key. After the message is encrypted, no one can decrypt it unless someone has your secret key. (Ideally, nobody other than you should have a copy of your key.) PGP also allows you to electronically "sign" a document with a digital signature, which other people can verify.
To make use of these features, you will first need to create a public key for yourself and distribute it among your correspondents. Do this with PGP 's -kg option:
% pgp -kg
Pretty Good Privacy(tm) 2.6.1 - Public-key encryption for the masses.
(c) 1990-1994 Philip Zimmermann, Phil's Pretty Good Software. 29 Aug 94
Distributed by the Massachusetts Institute of Technology. Uses RSAREF.
Export of this software may be restricted by the U.S. government.
Current time: 1995/02/12 04:01 GMT
Pick your RSA key size:
1) 512 bits- Low commercial grade, fast but less secure
2) 768 bits- High commercial grade, medium speed, good security
3) 1024 bits- "Military" grade, slow, highest security
Choose 1, 2, or 3, or enter desired number of bits: 3
Generating an RSA key with a 1024-bit modulus.
You need a user ID for your public key. The desired form for this
user ID is your name, followed by your E-mail address enclosed in
<angle brackets>, if you have an E-mail address.
For example: John Q. Smith <12345.6789@compuserve.com>
Enter a user ID for your public key:
Michelle Love <love@michelle.org>
You need a pass phrase to protect your RSA secret key.
Your pass phrase can be any sentence or phrase and may have many
words, spaces, punctuation, or any other printable characters.
Enter pass phrase:
every thought burns into substance
Enter same pass phrase again:
every thought burns into substance
Note that key generation is a lengthy process.
We need to generate 720 random bits. This is done by measuring the
time intervals between your keystrokes. Please enter some random text
on your keyboard until you hear the beep:
Here you type a lot of random data that nobody else really sees. It doesn't really matter what you type, just don't hold down the key.
0 * -Enough, thank you.
..........................++++ ..........++++
Key generation completed.
%
The passphrase is used to encrypt the secret key that is stored on your computer. In this manner, if somebody breaks into your account or steals your computer, they won't be able to read your encrypted messages.
After you've generated your key, you should do two things with it immediately:
-
Sign it yourself. You should always sign your own key right away. Do this as:
% pgp -ks love@michelle.org
There are some obscure ways that your key might be abused if it is circulated without a signature in place, so be sure that you sign it yourself.
-
Generate a revocation certificate and store it offline somewhere. Don't send it to anyone! The idea behind generating the revocation right now is that you still remember the passphrase and have the secret key available. If something should happen to your stored key, or you forget the passphrase, the public/private key pair becomes useless. Having the revocation certificate ready in advance allows you to send it out if that should ever happen. You generate the certificate by:
% pgp -kx Michelle revoke.pgp Pretty Good Privacy(tm) 2.6.1 - Public-key encryption for the masses. (c) 1990-1994 Philip Zimmermann, Phil's Pretty Good Software. 29 Aug 94 Uses the RSAREF(tm) Toolkit, which is copyright RSA Data Security, Inc. Distributed by the Massachusetts Institute of Technology. Export of this software may be restricted by the U.S. government. Current time: 1995/02/12 04:06 GMT Extracting from key ring: `/Users/simsong/Library/pgp/pubring.pgp', userid "Michelle". Key for user ID: Michelle Love <love@michelle.org> 1024-bit key, Key ID 0A965505, created 1995/02/12 Key extracted to file `revoke.pgp'. % pgp -kd Michelle revoke.pgp Pretty Good Privacy(tm) 2.6.1 - Public-key encryption for the masses. (c) 1990-1994 Philip Zimmermann, Phil's Pretty Good Software. 29 Aug 94 Uses the RSAREF(tm) Toolkit, which is copyright RSA Data Security, Inc. Distributed by the Massachusetts Institute of Technology. Export of this software may be restricted by the U.S. government. Current time: 1995/02/12 04:07 GMT Key for user ID: Michelle Love <love@michelle.org> 1024-bit key, Key ID 0A965505, created 1995/02/12 Do you want to permanently revoke your public key by issuing a secret key compromise certificate for "Michelle" (y/N)? y You need a pass phrase to unlock your RSA secret key. Key for user ID "Michelle" Enter pass phrase: every thought burns into substance Pass phrase is good. Just a moment.... Key compromise certificate created. Warning: `revoke.pgp' is not a public keyring
Now, save the revoke.pgp file in a safe place, off line. For example, you might put it on a clearly labeled floppy disk, then place the disk inside a clearly labeled envelope. Write your signature across the envelope's flap. Then store the envelope in your safe-deposit box.
To extract a printable, ASCII version of your key, use PGP 's -kxaf (Key extract ASCII filter) command:
% pgp -kxaf Michelle Pretty Good Privacy(tm) 2.6.1 - Public-key encryption for the masses. (c) 1990-1994 Philip Zimmermann, Phil's Pretty Good Software. 29 Aug 94 Distributed by the Massachusetts Institute of Technology. Uses RSAREF. Export of this software may be restricted by the U.S. government. Current time: 1995/02/12 04:11 GMT Extracting from key ring: '/Users/simsong/Library/pgp/pubring.pgp', userid "Mic. Key for user ID: Michelle Love <love@michelle.org> 1024-bit key, Key ID 0A965505, created 1995/02/12 Key extracted to file 'pgptemp.$00'. -----BEGIN PGP PUBLIC KEY BLOCK----- Version: 2.6.1 mQCNAy89iJMAAAEEALrXJQpVmkTCtjp5FrkCvceFZydiEq2xGgoBvDUOn92XtJiH PVvope9VA4Lw2wDAbZDD5oucpGg8I1E4luvHVsvF0mpk2JzzWE1hVxWv4rpYIM+x qSbCryUU5iSneFGPBI5D3nue4wC3XbvQmvYYp5LR6r2eyHU3ktazHzgKllUFAAUR tCFNaWNoZWxsZSBMb3ZlIDxsb3ZlQG1pY2hlbGxlLm9yZz4= =UPJB -----END PGP PUBLIC KEY BLOCK----- %
You can redirect the output of this command to a file, or simply use your window system's cut-and-paste feature to copy the key into an email message.
If you get somebody else's PGP key, you can add it to your keyring with the PGP -ka (key add) option. Simply save the key in a file, then type:
% pgp -ka michelle.pgp Pretty Good Privacy(tm) 2.6.1 - Public-key encryption for the masses. (c) 1990-1994 Philip Zimmermann, Phil's Pretty Good Software. 29 Aug 94 Distributed by the Massachusetts Institute of Technology. Uses RSAREF. Export of this software may be restricted by the U.S. government. Current time: 1995/02/12 04:15 GMT Looking for new keys... pub 1024/0A965505 1995/02/12 Michelle Love <love@michelle.org> Checking signatures... Keyfile contains: 1 new key(s) One or more of the new keys are not fully certified. Do you want to certify any of these keys yourself (y/N)? y Key for user ID: Michelle Love <love@michelle.org> 1024-bit key, Key ID 0A965505, created 1995/02/12 Key fingerprint = 0E 8A 9C C4 CE 44 96 60 83 79 CB F1 F3 02 0C 7E This key/userID association is not certified. Do you want to certify this key yourself (y/N)? n %
6.6.3.3 Encrypting a message
After you have somebody's public key, you can encrypt a message using the PGP 's -eat command. This will encrypt the message, save it in ASCII (so you can send it with electronic mail), and properly preserve end-of-line characteristics (assuming that this is a text message). You can sign the message with your own digital signature by specifying -seat instead of -eat . If you want to use PGP as a filter, add the letter " f " to your command. This process is shown graphically in Figure 6.6 .
Figure 6.6: Encrypting email with PGP
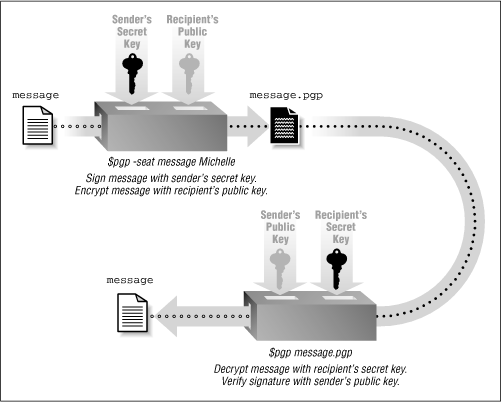
For example, you can take the file message, sign it with your digital signature, encrypt it with Michelle's public key, and send it to her, by using the command:
% cat message | pgp -seatf message Michelle | mail -s message :w love@michelle.org
6.6.3.4 Adding a digital signature to an announcement
With PGP , you can add a digital signature to a message so that people who receive the message can verify that it is from you (provided that they have your public key).
For example, if you wanted to send out a PGP -signed message designed to warm the hearts but dull the minds of your students, you might do it like this:
% pgp -sat classes Pretty Good Privacy(tm) 2.6.1 - Public-key encryption for the masses. (c) 1990-1994 Philip Zimmermann, Phil's Pretty Good Software. 29 Aug 94 Distributed by the Massachusetts Institute of Technology. Uses RSAREF. Export of this software may be restricted by the U.S. government. Current time: 1995/02/12 04:30 GMT A secret key is required to make a signature. You need a pass phrase to unlock your RSA secret key. Key for user ID "simson" Enter pass phrase: all dogs go to heaven Pass phrase is good. Key for user ID: Simson L. Garfinkel <simsong@acm.org> 1024-bit key, Key ID 903C9265, created 1994/07/15 Also known as: simsong@pleasant.cambridge.ma.us Also known as: simsong@next.cambridge.ma.us Also known as: simsong@mit.edu Just a moment.... Clear signature file: classes.asc %
The signed message itself looks like this:
% cat classes.asc -----BEGIN PGP SIGNED MESSAGE----- Classes are cancelled for the following two months. Everybody enrolled in the course will get an A. - -Your Professor -----BEGIN PGP SIGNATURE----- Version: 2.6.1 iQCVAwUBLz2Ow3D7CbCQPJJlAQH7CAP/V5COuOPGTDhSeGl6XkxKiVAPD9JDfeNd 5mFr8K/N7W9tyj7THiS/eI92e5/cRI/5z6KzxbSNIx8gGe4h9/bjO5a6rUfa3C+K j0zCIwETQzSE3tVWXxQv7it4HBZY+xJL8C1CinEckZZc09PvGwyYbPe4tSF8GHHl 0zyTTtueqLg= =3ihy -----END PGP SIGNATURE----- %
6.6.3.5 Decrypting messages and verifying signatures
To decrypt a message or verify a signature on a message, simply save the message into a file. Then run PGP , specifying the filename as your sole argument. If you are decrypting a message, you will need to type your pass phrase. For example, to decrypt a message that has been sent you, use the following command:
% cat message.asc -----BEGIN PGP MESSAGE----- Version: 2.6.1 hIwDcPsJsJA8kmUBBACN/HinvYo1GRL+p6pT14OV3L50q/v1aqGsHHSOa37t89O1 23/jm6lzTuh83Qy5KbMpLkMbRg/5FqTD56GX9MoyP4IuLzKxtuA87n9j/pYv4ES3 I0aCUMOvU8SqNTM1qC+ZV7j6NeseCUiRrMFVVlr5uZ2TH8kkDiQBd0x1/h7LNaYA AACFsT5sa/rd1uh/1A7yDSqZZNGzlCn0aC55o8lgSoPKOgvT0JGZFFOS5h+v3wxw /U752OaQaSIIj0rVK8UT0thSxyM8xoMIRmBJgmwoloKI+/THy5/Toy8FIqS5taHu o0wkuhDwcjNg4PJ3dZkoLwnGWwwM3y5vKqrMFHQfNnO6xJ9qBqnKLg== =EEko -----END PGP MESSAGE----- %
Process the file with PGP :
% pgp message.asc Pretty Good Privacy(tm) 2.6.1 - Public-key encryption for the masses. (c) 1990-1994 Philip Zimmermann, Phil's Pretty Good Software. 29 Aug 94 Distributed by the Massachusetts Institute of Technology. Uses RSAREF. Export of this software may be restricted by the U.S. government. Current time: 1995/02/12 04:54 GMT File is encrypted. Secret key is required to read it. Key for user ID: simson 1024-bit key, Key ID 903C9265, created 1994/07/15 Also known as: simsong@pleasant.cambridge.ma.us Also known as: simsong@next.cambridge.ma.us Also known as: simsong@mit.edu Also known as: Simson L. Garfinkel <simsong@acm.org> You need a pass phrase to unlock your RSA secret key. Enter pass phrase: subcommander marcos Pass phrase is good. Just a moment...... Plaintext filename: message % cat message Hi Simson! Things are all set. We are planning the military takeover for next Tuesday. Bring your lasers. -Carlos %
You can also specify the " f " option, which causes PGP to simply send the decrypted file to stdout.
6.6.3.6 PGP detached signatures
PGP has the ability to store digital signatures in a separate file from the original document. Such a signature is called a detached signature . Detached signatures are recommended for binary files, such as programs, because the signature will not change the data.
For the UNIX system administrator, one of the truly valuable things that you can do with PGP is to create detached signatures of your critical system files. These signatures will be signed by you, the system administrator. You (or other users on your system) can then use these signatures to detect unauthorized modification in the critical system files: if the files that you sign are ever modified, the signature will no longer validate.
For example, to create a detached signature for the /bin/login program, you could use PGP 's -sb flags:
# pgp -sb /bin/login -u simsong Pretty Good Privacy(tm) 2.6.1 - Public-key encryption for the masses. (c) 1990-1994 Philip Zimmermann, Phil's Pretty Good Software. 29 Aug 94 Distributed by the Massachusetts Institute of Technology. Uses RSAREF. Export of this software may be restricted by the U.S. government. Current time: 1995/09/12 15:28 GMT A secret key is required to make a signature. You need a pass phrase to unlock your RSA secret key. Key for user ID "simsong@pleasant.cambridge.ma.us" Enter pass phrase: nobody knows my name Pass phrase is good. Key for user ID: Simson L. Garfinkel <simsong@acm.org> 1024-bit key, Key ID 903C9265, created 1994/07/15 Also known as: simsong@pleasant.cambridge.ma.us Also known as: simsong@next.cambridge.ma.us Also known as: simsong@mit.edu Just a moment.... Signature file: /bin/login.sig #
In this example, the superuser ran PGP so that the signature for /bin/login could be recorded in /bin/login.sig (the default location). You could specify a different location to save the signature by using PGP 's - o filename option.
To verify the signature, simply run PGP , supplying the signature and the original file as command line arguments:
% pgp /bin/login.sig /bin/login Pretty Good Privacy(tm) 2.6.1 - Public-key encryption for the masses. (c) 1990-1994 Philip Zimmermann, Phil's Pretty Good Software. 29 Aug 94 Distributed by the Massachusetts Institute of Technology. Uses RSAREF. Export of this software may be restricted by the U.S. government. Current time: 1995/09/12 15:32 GMT File has signature. Public key is required to check signature. File '/bin/login.sig' has signature, but with no text. Text is assumed to be in file '/bin/login'. . Good signature from user "Simson L. Garfinkel <simsong@acm.org>". Signature made 1995/09/12 15:28 GMT Signature and text are separate. No output file produced. %
Using digital signatures to validate the integrity of your system's executables is a better technique than using simple cryptographic checksum schemes, such as MD5. Digital signatures are better because with a simple MD5 scheme, you risk an attacker's modifying both the binary file and the file containing the MD5 checksums. With digital signatures, you don't have to worry about an attacker's recreating the signature, because the attacker does not have access to the secret key. (However, you still need to worry about someone altering the source code of your checksum program to make a copy of your secret key when you type it.)
NOTE: Protect your key! No matter how secure your encryption system is, you should take the same precautions with your encryption key that you take with your password: there is no sense in going to the time and expense of encrypting all of your data with strong ciphers such as DES or RSA if you keep your encryption keys in a file in your home directory, or write them on a piece of paper attached to your terminal.
Finally, never use any of your passwords as an encryption key! If an attacker learns your password, your encryption key will be the only protection for your data. Likewise, if the encryption program is weak or compromised, you do not want your attacker to learn your password by decrypting your files. The only way to prevent this scenario is by using different words for your password and encryption keys.




