6.2 What Is Encryption?
Encryption is a process by which a message (called plaintext ) is transformed into another message (called ciphertext ) using a mathematical function[5] and a special encryption password, called the key .
[5] Although it may not be expressed as such in every case.
Decryption is the reverse process: the ciphertext is transformed back into the original plaintext using a mathematical function and a key.
Figure 6.1: A simple example of encryption
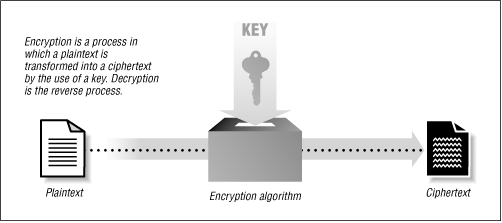
The process of encryption and decryption is shown in basic terms in Figure 6.1 . Here is a simple piece of plaintext:
Encryption can make
UNIX
more secure.
This message can be encrypted with an encryption algorithm known as the Data Encryption Standard ( DES ), which we describe in a later section, and the key nosmis to produce the following encrypted message:[6]
[6] Encrypted messages are inherently binary data. Because of the limitations of paper, control characters are printed preceded by a caret (^), while characters with their most significant bit set are preceded by a M-.
M-itM-@g^B^?^B?^NM-XM-vZIM-U_h^X^$kM-^^sI^^M-f1M-^ZM-jM-gBM-6M->^@M-"=^M-^JM-7M--M-^T
When this message is decrypted with the key nosmis, the original message is produced:
Encryption can make
UNIX
more secure.
If you tried to decrypt the encrypted message with a different key, such as gandalf, you might get the following:
M-&u=:;M-X^G?M-MM-^MM- M-,M-kM-^?M-R8M-}}pM-?^M^^M-l^ZM-IM-^U0M-D^KM-eM- hM-yM-^M-^]M-mM-UM-^ZM-@^^N
Indeed, the only way to decrypt the encrypted message and get printable text is by knowing the secret key nosmis . If you don't know the key, and you don't have access to a supercomputer, you can't decrypt the text. If you use a strong encryption system, even the supercomputer won't help you.
6.2.1 What You Can Do with Encryption
Encryption can play a very important role in your day-to-day computing and communicating:
-
Encryption can protect information stored on your computer from unauthorized access - even from people who otherwise have access to your computer system.
-
Encryption can protect information while it is in transit from one computer system to another.
-
Encryption can be used to deter and detect accidental or intentional alterations in your data.
-
Encryption can be used to verify whether or not the author of a document is really who you think it is.
Despite these advantages, encryption has its limits:
-
Encryption can't prevent an attacker from deleting your data altogether.
-
An attacker can compromise the encryption program itself. The attacker might modify the program to use a key different from the one you provide, or might record all of the encryption keys in a special file for later retrieval.
-
An attacker might find a previously unknown and relatively easy way to decode messages encrypted with the algorithm you are using.
-
An attacker could access your file before it is encrypted or after it is decrypted.
For all these reasons, encryption should be viewed as a part of your overall computer security strategy, but not as a substitute for other measures such as proper access controls.
6.2.2 The Elements of Encryption
There are many different ways that you can use a computer to encrypt or decrypt information. Nevertheless, each of these so-called encryption systems share common elements:
- Encryption algorithm
-
The encryption algorithm is the function, usually with some mathematical foundations, which performs the task of encrypting and decrypting your data.
- Encryption keys
-
Encryption keys are used by the encryption algorithm to determine how data is encrypted or decrypted. Keys are similar to computer passwords: when a piece of information is encrypted, you need to specify the correct key to access it again. But unlike a password program, an encryption program doesn't compare the key you provide with the key you originally used to encrypt the file, and grant you access if the two keys match. Instead, an encryption program uses your key to transform the ciphertext back into the plaintext. If you provide the correct key, you get back your original message. If you try to decrypt a file with the wrong key, you get garbage.[7]
[7] Of course, we are assuming that your original message wasn't garbage, too. Otherwise, everything you would decrypt would probably appear as garbage!
- Key length
-
As with passwords, encryption keys have a predetermined length. Longer keys are more difficult for an attacker to guess than shorter ones because there are more of them to try in a brute-force attack. Different encryption systems allow you to use keys of different lengths; some allow you to use variable-length keys.
- Plaintext
-
The information which you wish to encrypt.
- Ciphertext
6.2.3 Cryptographic Strength
Different forms of cryptography are not equal. Some systems are easily circumvented, or broken . Others are quite resistant to even the most determined attack. The ability of a cryptographic system to protect information from attack is called its strength . Strength depends on many factors, including:
-
The secrecy of the key.
-
The difficulty of guessing the key or trying out all possible keys (a key search). Longer keys are generally harder to guess or find.
-
The difficulty of inverting the encryption algorithm without knowing the encryption key ( breaking the encryption algorithm).
-
The existence (or lack) of back doors , or additional ways by which an encrypted file can be decrypted more easily without knowing the key.
-
The ability to decrypt an entire encrypted message if you know the way that a portion of it decrypts (called a known text attack ).
-
The properties of the plaintext and knowledge of those properties by an attacker. (For example, a cryptographic system may be vulnerable to attack if all messages encrypted with it begin or end with a known piece of plaintext. These kinds of regularities were used by the Allies to crack the German Enigma cipher during the Second World War.)
The goal in cryptographic design is to develop an algorithm that is so difficult to reverse without the key that it is at least roughly equivalent to the effort required to guess the key by trying possible solutions one at a time. We would like this property to hold even when the attacker knows something about the contents of the messages encrypted with the cipher. Some very sophisticated mathematics are involved in such design.
6.2.4 Why Use Encryption with UNIX?
You might wonder why you need encryption if you are already using an operating system similar to UNIX that has passwords and uses file permissions to control access to sensitive information. The answer to this question is a single word: the superuser .
A person with access to the UNIX superuser account can bypass all checks and permissions in the computer's filesystem. But there is one thing that the superuser cannot do: decrypt a file properly encrypted by a strong encryption algorithm without knowing the key.
The reason for this limitation is the very difference between computer security controls based on file permissions and passwords, and controls based on cryptography. When you protect information with the UNIX filesystem, the information that you are trying to protect resides on the computer "in the clear." It is still accessible to your system manager (or someone else with superuser access), to a malicious computer hacker who manages to find a fault with your computer's overall security, or even to a thief who steals your computer in the night. You simply can't ensure that the data on your computer will never fall into the wrong hands.
When you protect information with encryption, the information is protected by the secrecy of your key, the strength of the encryption algorithm, and the particular encryption implementation that you are using. Although your system manager (or someone who steals your computer) can access the encrypted file, they cannot decrypt the information stored inside that file.




