5.6 Selecting Services Provided by the Bastion Host
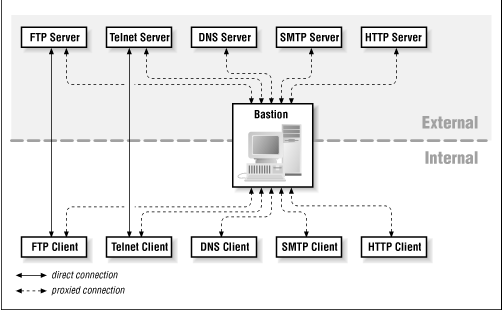
The bastion host provides any services your site needs to access the Internet, or wants to offer to the Internet - services you don't feel secure providing directly via packet filtering. ( Figure 5.1 shows a typical set.) You should not put any services on the bastion host not intended to be used to or from the Internet. For example, it shouldn't provide booting services for internal hosts (unless, for some reason, you intend to provide booting services for hosts on the Internet). You have to assume that the bastion host will be compromised, and that all services on it will be available to the Internet.
Figure 5.1: The bastion host may run a variety of Internet services
You can divide services into four classes:
- Services that are secure
-
Services in this category can be provided via packet filtering, if you're using this approach. (In a pure-proxy firewall, everything must be provided on the bastion host or not provided at all.)
- Services that are insecure as normally provided but can be secured
-
Services in this category can be provided on the bastion host.
- Services that are insecure as normally provided and can't be secured
-
These will have to be disabled and provided on a victim host (discussed above) if you absolutely need them.
- Services that you don't use, or that you don't use in conjunction with the Internet
-
You must disable services in this category.
We'll discuss individual services in detail in Chapter 8, Configuring Internet Services , but here we cover the most commonly provided and denied services for bastion hosts.
Electronic mail ( SMTP ) is the most basic of the services bastion hosts normally provide. You may also want to access or provide information services such as:
-
FTP - file transfer
-
Gopher - menu-based information retrieval
-
WAIS - keyword-search information retrieval
-
HTTP - hypertext-driven information retrieval (the World Wide Web)
-
NNTP - Usenet news
In order to support any of these services (including SMTP ), you must access and provide domain name service ( DNS ). DNS is seldom used directly, but it underlies all the other protocols by providing the means to translate hostnames to IP addresses and vice versa, as well as providing other distributed information about sites and hosts.
You may also want to provide some version of the finger service, to provide information about your site and the people at it. However, you should decide what information you want people to have, and use a modified finger daemon that provides only that. It is generally not desirable to tell the world which accounts are available on the bastion host and which are in use. Not only is this information useful to attackers, it's useless to genuine inquirers, who want to know information about your site as a whole, not about the bastion host in particular. The section on finger in Chapter 8 discusses some possible modified finger daemons.
The book Managing Internet Information Services , referenced above, has a good chapter on providing information services through finger , inetd , and Telnet. One particular technique described, that of creating "captured" or "no-break" shells, creates site-specific modified-procedure proxy services fairly easily. These services are a way for users within your network to be able to run ping or traceroute against external hosts, from a captured shell on the bastion host.
Many LAN -oriented services include vulnerabilities that attackers can exploit from outside, and all of them are opportunities for an attacker who has succeeded in compromising the bastion host. Basically, you should disable anything that you aren't going to use, and you should choose what to use very carefully.




