C.9 The IP Address
IP moves data between hosts in the form of datagrams. Each datagram is delivered to the address contained in the Destination Address (word 5) of the datagram's header. The Destination Address is a standard 32-bit IP address that contains sufficient information to uniquely identify a network and a specific host on that network.
An IP address contains a network part and a host part, but the format of these parts is not the same in every IP address. The number of address bits used to identify the network, and the number used to identify the host, vary according to the class of the address. The three main address classes are class A , class B, and class C . The following table summarizes the characteristics of each address class.
| Bits in | Range of Network | Network | Host | |
|---|---|---|---|---|
| Class | First Byte | Addresses | Portion | Portion |
| A | 0xxxxxxx | 0.0.0.0 - 127.0.0.0 | 1 byte | 3 bytes |
| B | 10xxxxxx | 128.0.0.0 - 191.255.0.0 | 2 bytes | 2 bytes |
| C | 110xxxxx | 192.0.0.0 - 223.255.255.0 | 3 bytes | 1 byte |
| D & | 111xxxxx | 224.0.0.0 - 255.255.255.0 | Special/ | - |
| E | reserved | |||
| Multicast |
By examining the first few bits of an address, IP software can quickly determine the address' class, and therefore its structure. IP follows these rules to determine the address class; the table below summarizes them:
You can compute the number of nets as follows (not relevant for Class D and E networks):
-
Class A: 128
-
Class B: 64 * 256 = 16,128
-
Class C: 32 * 256 2 = 2,097,152
You can compute the number of hosts per net as follows (not relevant for Class D and E networks):
-
Class A: 256 3 = 16,777,216
-
Class B: 256 2 = 65,536
-
Class C: 256
The following further explains the characteristics of the address classes:
-
If the first bit of an IP address is 0, it is the address of a class A network. The first bit of a class A address identifies the address class. The next seven bits identify the network, and the last 24 bits identify the host. There are fewer than 128 class A network numbers, but each class A network can be composed of millions of hosts.
-
If the first two bits of the address are 1 0, it is a class B network address. The first two bits identify class; the next fourteen bits identify the network; and the last sixteen bits identify the host. There are thousands of class B network numbers, and each class B network can contain thousands of hosts.
-
If the first three bits of the address are 1 1 0, it is a class C network address. In a class C address, the first three bits are class identifiers; the next 21 bits are the network address; and the last eight bits identify the host. There are millions of class C network numbers, but each class C network is composed of fewer than 254 hosts.
-
If the first three bits of the address are 1 1 1, it is a special reserved address. These addresses are sometimes called class D addresses, but they don't really refer to specific networks. The Multicast addresses are used to address groups of computers all at one time. Multicast addresses identify a group of computers that share a common protocol, as opposed to a group of computers that share a common network.
Luckily, this is not as complicated as it sounds. IP addresses are usually written as four decimal numbers separated by dots (periods).[3]
[3] Addresses are occasionally written in other formats (e.g., as hexadecimal numbers). However, the "dot" notation form is the most widely used. Whatever the notation, the structure of the address is the same.
Each of the four numbers is in the range 0-255 (the decimal values possible for a single byte). Because the bits that identify class are contiguous with the network bits of the address, we can lump them together and look at the address as composed of full bytes of network address and full bytes of host address. A first byte value:
-
Less than 128 indicates a class A address; the first byte is the network number, and the next three bytes are the host address.
-
From 128 to 191 is a class B address; the first two bytes identify the network, and the last two bytes identify the host.
-
From 192 to 223 is a class C address; the first three bytes are the network address, and the last byte is the host number.
-
Greater than 223, indicates the address is reserved. We can ignore reserved addresses.
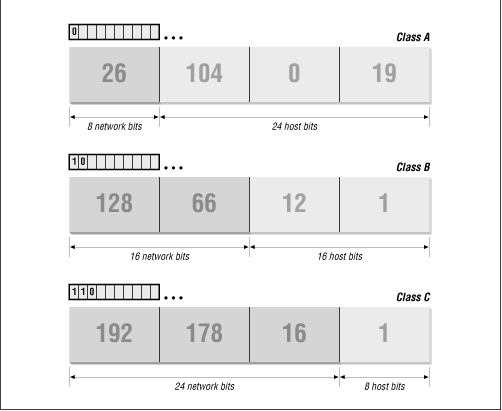
Figure 13.17 illustrates how the address structure varies with address class. The class A address is 26.104.0.19. The first bit of this address is 0, so the address is interpreted as host 104.0.19 on network 26. One byte specifies the network, and three bytes specify the host. In the address 128.66.12.1, the two high-order bits are 1 0 so the address refers to host 12.1 on network 128.66. Two bytes identify the network, and two identify the host. Finally, in the class C example, 192.178.16.1, the three high-order bits are 1 1 0, so this is the address of host 1 on network 192.178.16: three network bytes and one host byte.
Figure 13.17: IP address structure
Not all network or host addresses are available for use. We have already said that addresses with a first byte greater than 223 are reserved. There are also two class A addresses, 0 and 127, that are reserved for special uses. Network 0 designates the default route and network 127 is the loopback address . The default route is used to simplify the routing information IP must handle. The loopback address simplifies network applications by allowing the local host to be addressed in the same manner as a remote host. We use these special network addresses when configuring a host.
There are also some host addresses reserved for special uses. In all network classes, host numbers 0 and 255 are reserved. An IP address with all host bits set to zero identifies the network itself. For example, 26.0.0.0 refers to network 26, and 128.66.0.0 refers to network 128.66. Addresses in this form are used in routing table listings to refer to entire networks.
An IP address with all bits set to one is a broadcast address .[4] A broadcast address is used to simultaneously address every host on a network. The broadcast address for network 128.66 is 128.66.255.255. A datagram sent to this address is delivered to every individual host on network 128.66.
[4] Unfortunately there are implementation-specific variations in broadcast addresses.
IP addresses are often called host addresses. While this is common usage, it is slightly misleading. IP addresses are assigned to network interfaces, not to computer systems. A gateway, such as almond (see Figure 13.16 ), has a different address for each network it is connected to. The gateway is known to other devices by the address associated with the network that it shares with those devices. For example, peanut addresses almond as 128.66.12.1, while Milnet hosts address it as 26.104.0.19.
IP uses the network portion of the address to route the datagram between networks. The full address, including the host information, is used to make final delivery when the datagram reaches the destination network.
C.9.1 Address Depletion
The IP address, which provides universal addressing across all networks of the Internet, is one of the great strengths of the TCP/IP protocol suite. However, the structure of the IP address does have some problems. The TCP/IP designers did not envision the enormous scale of today's network. When TCP/IP was being designed, networking was limited to large organizations that could afford substantial computer systems. The idea of a powerful UNIX system on every desktop did not exist. At that time, a 32-bit address seemed so large that it was divided into classes to reduce the processing load on routers, even though dividing the address into classes sharply reduced the number of host addresses actually available for use. For example, assigning a large network a single class B address, instead of six class C addresses, reduces the load on the router because the router only needs to keep one route for that entire organization. However, the organization that was given the class B address probably does not have 64,000 computers, so most of the host addresses available to the organization will never be assigned.
The current address design, which favors routers over growth, is under critical strain from the rapid growth of the Internet. This is a major factor in the move from the current IP version 4 towards IP version 6 (IPv6).
C.9.2 Subnets
The standard structure of an IP address can be locally modified by using host address bits as additional network address bits. Essentially, the "dividing line" between network address bits and host address bits is moved, creating additional networks, but reducing the maximum number of hosts that can belong to each network. These newly designated network bits define a network within the larger network, called a subnet.
Organizations usually decide to subnet in order to overcome topological or organizational problems. Subnetting allows decentralized management of host addressing. With the standard addressing scheme, a single administrator is responsible for managing host addresses for the entire network. By subnetting, the administrator can delegate address assignment to smaller organizations within the overall organization, which may be a political expedient, if not a technical requirement. If you don't want to deal with the data processing department, assign them their own subnet and let them manage it themselves.
Subnetting can also be used to overcome hardware differences and distance limitations. IP routers can link dissimilar physical networks together, but only if each physical network has its own unique network address. Subnetting divides a single network address into many unique subnet addresses, so that each physical network can have its own unique address.
A subnet is defined by applying a bit mask, the subnet mask , to the IP address. If a bit is on in the mask, that equivalent bit in the address is interpreted as a network bit. If a bit in the mask is off, the bit belongs to the host part of the address. The subnet is only known locally. To the rest of the Internet, the address is still interpreted as a standard IP address.
For example, the subnet mask that would be associated with standard class B addresses is 255.255.0.0. The most commonly used subnet mask extends the network portion of a class B address by an additional byte. The subnet mask that does this is 255.255.255.0; all bits on in the first three bytes, and all bits off in the last byte. The first two bytes define the class B network; the third byte defines the the subnet address; the fourth byte defines the host on that subnet.
Many network administrators prefer to use byte-oriented masks because they are easier to read and understand. However, defining subnet masks on byte boundaries is not a requirement. The subnet mask is bit-oriented and can be applied to any address class. For example, a small organization could subdivide a class C address into four subnets with the mask 255.255.255.192.[5] Applying this mask to a class C address defines the two high-order bits of the fourth byte as the subnet part of the address. This same mask, applied to a class B address, creates more than a thousand subnets because ten bits (the full third byte, and two bits of the fourth byte) are used to define the subnets (2^10=1024).
[5] This is just an illustration. A mask that creates four subnets is not a good idea because a subnet address of all ones and an address of all zeros are reserved addresses. Therefore two of the four subnets could not be used.
As subnets become more and more common, an alternative way of writing subnet masks is becoming popular: as "/bits" instead of as the four-octet netmask. For instance, "/24" specifies a 24-bit netmask, equivalent to 255.255.255.0, but much faster to write. The new nomenclature makes the assumption that your netmasks are made up of contiguous bits (i.e., that you never use a netmask of something like 255.0.255.0), but that's standard practice anyway.
You will also sometimes hear people talk about wildcard masks, particular with respect to Cisco routers and packet filtering specifications. Wildcard masks are essentially the inverse of subnet masks; where subnet masks use 1 bit to specify the significant bits (the bits to be looked at), wildcard masks use 1 bit to specify the insignificant bits (the bits to be ignored). Thus, a subnet mask of 255.255.0.0 is equivalent to a wildcard mask of 0.0.255.255, and a subnet mask of 255.255.240.0 is equivalent to a wildcard mask of 0.0.15.255. The table below shows the effect of various subnet masks on different network addresses.
| UNIX Subnet | Equiv. Cisco | Equiv. /bits | ||
|---|---|---|---|---|
| IP Address | Mask | Wildcard | Mask | Interpretation |
| 128.66.12.1 | 255.255.255.0 | 0.0.0.255 | /24 | host 1 on subnet |
| 128.66.12.0 | ||||
| 130.97.16.132 | 255.255.255.192 | 0.0.0.63 | /26 | host 4 on subnet |
| 130.97.16.128 | ||||
| 192.178.16.66 | 255.255.255.192 | 0.0.0.63 | /26 | host 2 on subnet |
| 192.178.16.64 | ||||
| 132.90.132.5 | 255.255.240.0 | 0.0.15.255 | /20 | host 4.5 on subnet |
| 132.90.128.0 | ||||
| 18.20.16.91 | 255.255.0.0 | 0.0.255.255 | /16 | host 16.91 on subnet |
| 18.20.0.0 |




