C.7 Application Layer
At the top of the TCP/IP protocol architecture is the Application Layer. This layer includes all processes that use the Transport Layer protocols to deliver data. There are many applications protocols. Most provide user services, and new services are always being added to this layer. The most widely known and implemented applications protocols are:
-
Telnet, the Network Terminal Protocol, provides remote login over the network
-
FTP , the File Transfer Protocol, is used for interactive file transfer
-
SMTP , the Simple Mail Transfer Protocol delivers electronic mail
While FTP , SMTP , and Telnet are the most widely implemented TCP/IP applications, you will work with many others as both a user and a system administrator. Some other commonly used TCP/IP applications are:
- Domain Name Service ( DNS )
-
Also called name service , this application maps IP addresses to the names assigned to network devices.
- Routing Information Protocol ( RIP )
-
Routing is central to the way TCP/IP works. RIP is used by network devices to exchange routing information.
- Network File System ( NFS )
-
This protocol allows files to be shared by various hosts on the network.
Some protocols, such as Telnet and FTP , can only be used if the user has some knowledge of the network. Other protocols, like RIP , run without the user even knowing that they exist. As system administrator, you are aware of all these applications and all the protocols in the other TCP/IP layers.
Figure 13.15 shows the hierarchy of protocols in an imaginary computer. As you look at this figure, please remember that reducing the complexity of a protocol stack to a block diagram is, by its very nature, an oversimplification. This illustration is only to help you visualize the relationship of the many protocols in a single host. Not all of the protocols shown in Figure 13.15 have been discussed yet, but it should be helpful to get an idea of the overall structure.
Figure 13.15: TCP/IP protocols inside a sample gateway
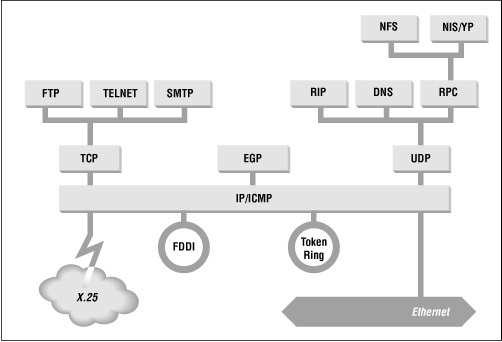
At the top of the figure are the applications protocols, like FTP and Telnet. Lines run from each box to the lower layer service that the protocol uses. We see that FTP , Telnet, and SMTP rely primarily on TCP ; while NFS , DNS , and RIP rely primarily on UDP . A few application-type protocols, like the Exterior Gateway Protocol ( EGP ), another routing protocol, do not use Transport Layer services; they use IP services directly.
Below the applications are the Transport Layer protocols: TCP and UDP . They interface directly with IP . All data, in and out of the system, flows through IP . IP delivers data from the upper layers to the correct network, and it delivers data from the network to the correct transport service. Likewise, the transport services deliver the data they receive from IP to the correct application.




