|
|

The CDAT expert interface allows the service-provider administrator to create and maintain the objects and attributes for services, service groups, users, user groups, roles, rules, and Node Route Processor (NRP) information. Before using the CDAT expert interface, read the following:
The CDAT expert interface consists of a set of windows that allow the objects representing services, subscribers, and policy roles and rules to be created and maintained. The following sections describe how to use the CDAT expert interface to define service, subscriber, and policy information:
In addition to creating services, subscribers, and other objects with CDAT, the SSG software must be correctly configured for the services that you create. For information on configuring services on the SSG, see the Service Selection Gateway documentation that is available on Cisco Connection Online (www.cisco.com).
As a simple example of the tasks that an administrator performs when using the CDAT interface, consider the tasks needed to create a user with a set of privileges to access certain resources.
Because the steps outlined below start from the very beginning and assume that no user groups, roles, or rules exist, the tasks may seem a bit complicated. After becoming familiar with RBAC and CDAT, these tasks become fairly intuitive. More importantly, this set of tasks is only performed once—when the directory objects are created for the first time.
The following example outlines the steps that you perform to create a user who is a subscriber to a set of "Gold" services. The steps for this task are as follows:
1. With the Services window, create one or more services (the Gold services that Gold subscribers can access).
2. With the User Groups window, create a user group (GoldSubscriberGroup) for the users who will be granted access to the Gold services.
3. With the Users window, create the user (Joan) and make the user a member of the user group GoldSubscriberGroup.
4. With the Roles window, create a role (GoldSubscriberRole). The role defines the privileges the members of the GoldSubscriberGroup have.
a. Define the role's privileges to include the rights to subscribe to and unsubscribe from Gold services.
b. Make the user group GoldSubscriberGroup a subject (occupant) of the role GoldSubscriberRole.
5. With the Rules window, create a rule (GoldSubscriberRule). The rule will grant, to a specified role (GoldSubscriberRole), the privileges for a set of resources. For a Gold subscriber, the set of resources includes the Gold services.
a. Specify the set of resources (the Gold services) that are defined for the rule.
b. Associate the role GoldSubscriberRole with the rule GoldSubscriberRule.
When you complete the preceding steps, the privileges to subscribe to or unsubscribe from the set of Gold services are granted to the user group GoldSubscriberGroup because it is a subject of the GoldSubscriberRole. The user Joan has the privileges defined by the GoldSubscriberRole because she is a member of the GoldSubscriberGroup. The GoldSubscriberRule is applied to the specified services (the Gold services) and it associates GoldSubscriberRole with these services.
The greatest benefit to using CDAT is that it allows for bulk administration of users. Because the preceding example started from the beginning and created all needed objects for granting a subscriber the privileges to access a set of services, the steps might seem a bit complicated.
However, once these objects (a user group, a role for the group, and a rule granting privileges to resources) are in place, creating a thousand or ten thousand additional subscribers who are members of the GoldSubscriberGroup is simple and involves two steps for each subscriber:
1. Create the user—the new subscriber.
2. Specify that the user is a member of the GoldSubscriberGroup.
In addition to granting access to resources, you can perform other service-provider administration tasks at the group level. For example, because you have already defined the underlying structure of user groups, roles, and rules, adding or removing resources (services) that group members can access, and modifying the set of privileges for group members can be accomplished at the user group level.
With RBAC and CDAT, no user-by-user access control modifications need to be made. Bulk administration of users, services, and privileges makes subscriber provisioning simple and fast.
This section provides some information about getting started with the CDAT expert interface:
This section describes the following:
This section explains how to start CDAT and access the CDAT home page. For detailed information on installing, configuring, and starting CDAT, see the Cisco Subscriber Edge Services Manager Installation and Configuration Guide.
 |
Note Before using CDAT, make sure that cookies are enabled in your browser. CDAT requires a browser that allows cookies. |
To start CDAT and access the CDAT home page, do the following:
Step 1 Start CDAT by executing the CDAT startup script.
Step 2 Open a web browser.
Step 3 Browse to the CDAT URL, which is:
For example:
Port 8081 is the port that is configured, by default, for CDAT. The port number that you specify may be different. This port number is specified in the CDAT startup script (startCDAT.sh or startCDAT.cmd).
Step 4 For SESM/CDAT Release 3.1(7) or later, click Manage LDAP Directory on the CDAT home page to access the login window for the LDAP Directory Manager.
To log in to CDAT for the first time to manage an LDAP directory, use the admin user name and the password of the directory administrator for the Organization and Organizational Unit where SESM is located. This is the user name and password that were specified when the directory was installed.
 |
Note During the directory installation and the CDAT installation, the directory administrator must be specified as the admin user ID. |
To use the admin user name as the first-time CDAT administrator, you must do the following when installing the directory server and the CDAT software:
1. When you install the directory server, set up an admin user with the needed permissions to access and create objects in the directory container (Organization Unit and Organization) where the SPE schema extensions and initial RBAC objects will be installed.
2. When you install the CDAT software, select Install RBAC to install the initial RBAC objects. When you select Install RBAC, the CDAT installation software expects to find an admin user ID so that it can grant that user the needed administrator privileges.
After you log into CDAT as the admin user, you should create a CDAT administrator user who belongs to a user group that has the administrative privileges to set up the objects and attributes for services, subscribers, policy roles and rules, and so on. Because the admin user is a directory administrator for the SESM container, that administrator can create roles, rules, and user groups for CDAT administrators to whom the admin user can grant differing privilege levels.
After you install the RBAC objects, you can use the SUPERVISOR_ROLE and SUPERVISOR_RULE when defining a user group for administrators. For information on the privileges that are needed by a CDAT administrator, see the "Creating and Updating Roles" section.
The CDAT sample data contains examples of users, user groups, services, service groups, roles, and rules. The sample data is contained in one LDIF file, DESSusecasedata.ldf file, which is located in the install_dir\dess-auth\schema\samples directory.
 |
Note A differently formatted DESSusecasedata.ldf file is installed depending on the operating system. For example, the Windows-specific sample data file contains DOS-format line endings. To install a Windows sample data file on a directory server on UNIX, or a UNIX sample data file on a directory server on Windows, use a file-format conversion utility, such as dos2unix or unix2dos, to convert the DESSusecasedata.ldf file to the required format. |
You use the ldapmodify command to install the DESSusecasedata.ldf sample data. The examples that follow show the ldapmodify command line that is used for NDS eDirectory and for iPlanet Directory Server.
The SESM installation software updates the context and the container manager specified in the DESSusecasedata.ldf file. If needed, you can change these manually by replacing all occurrences of the context ou=sesm,o=cisco and of the container manager cn=admin,ou=sesm,o=cisco with the appropriate values.
For the following eDirectory example, assume that:
The following ldapmodify command installs the sample data:
ldapmodify -h 192.10.68.12 -p 389 -c -v -D "cn=admin,ou=sesm,o=cisco" -w cisco
-f DESSusecasedata.ldf
For the following iPlanet example, assume that:
The following ldapmodify command installs the sample data:
ldapmodify -h 192.10.68.12 -c -v -D "uid=admin,ou=sesm,o-cisco" -w cisco
-f DESSusecasedata.ldf
The CDAT expert interface allows you to create or update information for services, service groups, users, user groups, roles, rules, and NRPs. Figure 2-1 shows the Users window of the expert interface.
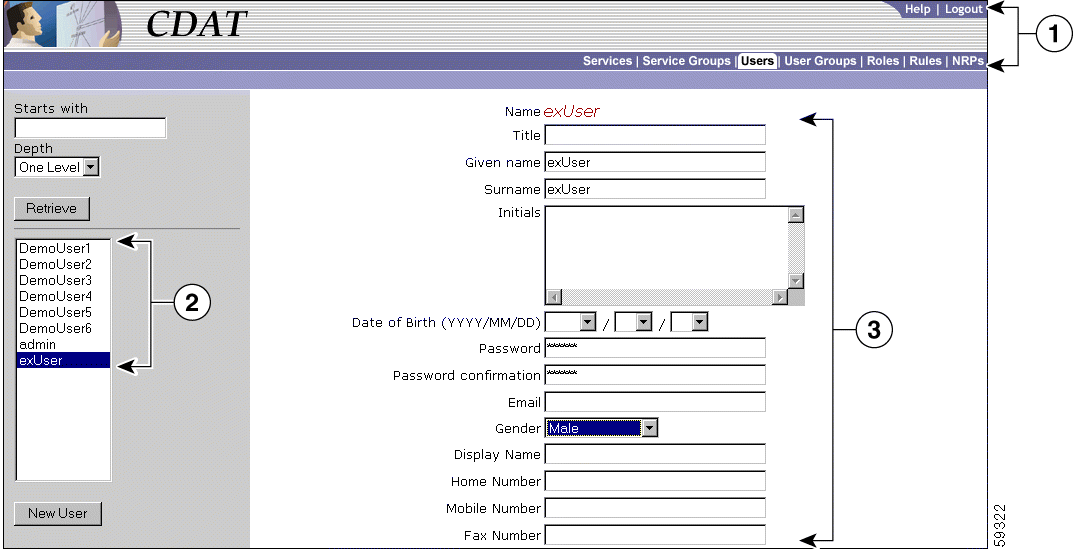
| 1 | Navigation Bar |
| 2 | Navigation List |
| 3 | Object Details |
In the CDAT expert interface, each object-management window contains these areas:
The bottom of the Object Details area contains a set of buttons. Figure 2-2 shows the buttons that appear at the bottom of the Users window.

The buttons shown in Figure 2-2 perform the following actions:
The Local RADIUS Attribute box allows you to specify standard RADIUS attribute names and Cisco SSG vendor-specific attributes, including Cisco attribute-value pairs (Cisco AV pairs). The Local RADIUS Attributes box appears in the following CDAT windows:
 |
Tip The Local RADIUS Attribute box allows you to define an attribute and value that does not appear in the boxes (fields) of a CDAT window. For example, the Users window does not have a box for a RADIUS attribute Calling-Station Id. You can enter this attribute in the Local RADIUS Attributes box. As another example, most Cisco AV pairs do not appear in the boxes of a CDAT window. You can enter Cisco AV pairs in the Local RADIUS Attributes box. |
For information on RADIUS attributes that appear in the boxes of the Services window, see "RDP Service-Profile Translation."
CDAT and other SESM applications internally predefine the standard RADIUS attributes and the Cisco SSG vendor-specific attributes (VSAs).
You can use these predefined RADIUS attributes in subscriber and service profiles whether or not they are defined in an attribute dictionary. (With CDAT and LDAP mode, the attribute dictionary is in the RADIUSDictionary MBean used by the RDP application.)
| RADIUS Attribute Names1 | ||
|---|---|---|
USER_NAME USER_PASSWORD CHAP_PASSWORD NAS_IP_ADDRESS NAS_PORT SERVICE_TYPE FRAMED_PROTOCOL FRAMED_IP_ADDRESS FRAMED_IP_NETMASK FRAMED_ROUTING FILTER_ID FRAMED_MTU FRAMED_COMPRESSION LOGIN_IP_HOST LOGIN_SERVICE LOGIN_TCP_PORT REPLY_MESSAGE CALLBACK_NUMBER CALLBACK_ID FRAMED_ROUTE FRAMED_IPX_NETWORK STATE CLASS VENDOR | SESSION_TIMEOUT IDLE_TIMEOUT TERMINATION_ACTION CALLED_STATION_ID CALLING_STATION_ID NAS_IDENTIFIER PROXY_STATE LOGIN_LAT_SERVICE LOGIN_LAT_NODE LOGIN_LAT_GROUP FRAMED_APPLETALK_LINK FRAMED_APPLETALK_NETWORK FRAMED_APPLETALK_ZONE ACCT_STATUS_TYPE ACCT_DELAY_TIME ACCT_INPUT_OCTETS ACCT_OUTPUT_OCTETS ACCT_SESSION_ID ACCT_AUTHENTIC ACCT_SESSION_TIME ACCT_INPUT_PACKET ACCT_OUTPUT_PACKETS ACCT_TERMINATE_CAUSE ACCT_MULTI_SESSION_ID | ACCT_LINK_COUNT ACCT_INPUT_GIGAWORDS ACCT_OUTPUT_GIGAWORDS EVENT_TIMESTAMP CHAP_CHALLENGE NAS_PORT_TYPE PORT_LIMIT LOGIN_LAT_PORT ARAP_PASSWORD ARAP_FEATURES ARAP_ZONE_ACCESS ARAP_SECURITY ARAP_SECURITY_DATA PASSWORD_RETRY PROMPT CONNECT_INFO CONFIGURATION_TOKEN EAP_MESSAGE MESSAGE_AUTHENTICATOR ARAP_CHALLENGE_RESPONSE ACCT_INTERIM_INTERVAL NAS_PORT_ID FRAMED_POOL |
| 1A hyphen (-) can replace the underscore (_) in RADIUS attribute names. The attribute names are not case-sensitive. |
| RADIUS Attribute | Vendor ID | Subattribute | Name1 | Type |
|---|---|---|---|---|
26 | 9 | 1 | CISCO-AV | String |
26 | 9 | 250 | ACCOUNT-INFO | String |
26 | 9 | 251 | SERVICE-INFO | String |
26 | 9 | 252 | COMMAND-CODE | BINARY |
26 | 9 | 253 | CONTROL-INFO | String |
| 1The hyphen (-) and underscore (_) are interchangeable in RADIUS attribute names. The attribute names are not case-sensitive. |
To specify one of the predefined RADIUS attributes in CDAT's Local RADIUS Attributes box, use the following form:
ATTRIBUTE_NAME is one of the predefined RADIUS attributes, and attribute_value is the value given for the attribute. A colon (:) separates the two elements. Two examples follow:
CALLING_STATION_ID:978123456
CISCO-AV:ip:inacl#101=deny tcp 192.168.1.0 0.0.0.255 any eq 21
In the Local RADIUS Attributes box, you can also dynamically define a new attribute when you first use the attribute in a profile. This feature is intended only for testing, demonstration, and development purposes. With CDAT, use the dynamic attribute feature only in the following circumstances:
For information on dynamically defining a new attribute, see the Cisco Subscriber Edge Services Manager Installation and Configuration Guide.
Some other considerations that you should be aware of when using the CDAT expert interface are:
All objects created with CDAT share the same name space. You cannot create a CDAT object (service, service group, user, user group, role, rule, or NRP) using the same name as an object of any of these types that already exists. If you try to create an object using a name already in use, CDAT displays a message that the object already exists and asks you to choose a new name.
When a user logs into CDAT, the objects that CDAT displays and the objects and attributes that the user can create, delete, and modify are directly related to the user groups that the CDAT user is a member of and to the following:
As an example, assume a user does not have Cisco_Azn_Super privilege for managing roles and rules. If this user logs in, CDAT does not display any roles or rules in the Roles and Rules windows. To see and manage roles and rules using CDAT, this user must a member of a user group that has Cisco_Azn_Super privilege and must have access to the resources of the container Organization Unit under which the roles and rules reside.
CDAT and the DESS/AUTH software store the user password in Secure Hash Standard encrypted form. After a password is defined for a user account, CDAT displays each password field as a 25-character string, regardless of the length of the defined password. The password encryption does not allow the user or the CDAT administrator to clear the password. Once a password exists, attempting to enter an empty string for the password results in an exception. No update of the password occurs.
When a subaccount is created, the initial password is set to the user name for the subaccount. The password fields in CDAT display a 25-character string because the password is stored in an encrypted form.
Some of the attributes that are in effect for a user or service profile are affected by inheritance.
When you define a service, service group, user, or user group, you can specify some attribute values at both the group level and the individual member level. When certain attribute values are specified at the user group or service group level, they are inherited by individual users and services that are group members. Table 2-3 lists the CDAT inheritable attributes.
When a value for an inheritable attribute is specified for an individual user or service, that value takes precedence over a value that is specified at the group level or container level.
For example, you can specify Idle Timeout and Session Timeout values for a service and for a service group.
To simplify the use of inheritable user and user group attributes, you should define user attributes at the individual user level only when an attribute is specific to the user. You should define all other attributes at the group level. Individual group members then inherit the group value.
CDAT configuration attributes affect the behavior of the CDAT web application (for example, the port number where the web server listens for HTTP requests for CDAT). The configuration attributes also allow you to configure CDAT logging, debugging, and the management console. Other configuration attributes can affect the results that an SESM web application sees when it retrieves profile information from the LDAP directory.
Configuration attributes that affect the behavior of CDAT are defined in the cdat.jetty.xml file located in the install_dir/jetty/config directory, and the cdat.xml file located in the install_dir/cdat/config directory. Configuration attributes in the cdat.xml file include:
The CDAT management console is password protected. The management console's password is defined by the AuthInfo attribute in the cdat.xml file. In a production deployment, changing this password is a common-sense security precaution.
For detailed information on the CDAT configuration files and attributes, see the Cisco Subscriber Edge Services Manager Installation and Configuration Guide.
RADIUS Data Proxy (RDP) configuration attributes can, in some cases, affect the results that an SESM web application sees when it retrieves account profile information. For example, if you use CDAT to make a change to a user profile defining a new account password, the change may not be immediately visible to an SESM web application because the RDP caches profile data. With the default values, it may take as long as 20 minutes for a user profile change to become visible to a SESM web application.
 |
Tip During development and testing, restarting the RDP after modifying account profile data causes the change to be immediately visible in the SESM web application. |
Configuration attributes that affect the caching behavior of RDP are defined in the config.xml file located in the install_dir/dess-auth/config directory. Configuration attributes in the config.xml file include:
For detailed information on the RDP configuration files and attributes, see the Cisco Subscriber Edge Services Manager Installation and Configuration Guide.
Many of the attributes that you define when creating a new service with CDAT are used by the Service Selection Gateway (SSG). The SSG connects the subscriber to the service or provides status information. The SSG is the enforcement point for authentication and service-specific policies such as session timeout, idle timeout, next-hop table, and other Internet Protocol (IP) attributes. The SSG also sends messages to the Cisco SESM web application regarding authentication failures or changes in the state of the SSG as a result of enforcement decisions (such as session timeout).
The following sections provide information on some of the SSG functionality that you can configure when creating a new service using CDAT.
When creating a new service with CDAT, you specify one of these service classes:
The SSG uses IOS access control lists (ACLs) to prevent users, services, and passthrough traffic from accessing specific IP addresses and ports. The ACLs can be configured for services and users by means of Cisco AV pairs.
When users are accessing multiple services, the SSG must determine the services for which the packets are destined. To do this, the SSG uses an algorithm to create a service access order list. This list is stored in the user's host object and contains services that are currently open and the order in which they are searched.
The algorithm that creates this list orders the open services based on the size of the network. Network size is determined by the subnet mask of the Service Route attribute (specified with Service routes box in Services window). A subnet that contains more hosts implies a larger network. If networks are the same size, the services will be listed in the order in which they were last accessed.
When creating services, be sure to define as small a network as possible. If there is overlapping address space, packets might be forwarded to the wrong service.
The Next hop gateway attribute in a service profile specifies the next hop key for a service. Each SSG uses its own next-hop table that associates this key with an actual IP address. Note that this attribute overrides the IP routing table for packets destined to a service. With CDAT, you use the NRPs window to create a next hop gateway table. For information on creating a next-hop table with CDAT, see "Creating and Updating NRP Information" section.
For information on downloading a next hop gateway table with the ssg next-hop command, see the Cisco 6400 Command Reference.
When the SSG receives a DNS request, it performs domain name matching using the Domain Name attribute from the service profiles of the currently logged-in services. For each service, you specify the Domain Name attribute in the Domain names box in the Services window.
The SSG can be configured to work with a single DNS server, or two servers in a fault-tolerant configuration. Based on an internal algorithm, DNS requests will be switched to the secondary server if the primary server begins to perform poorly or fails.
The Session Timeout and Idle Timeout attributes can be used in either a user or service profile. In a user profile, the attribute applies to the user's session. In a service profile, the attribute individually applies to each service connection.
In a dial-up networking or bridged (non-PPP) network environment, a user might disconnect from the NAS and release the IP address without using the SESM web application to log out from the SSG. If this happens, the SSG continues to allow traffic to pass from that IP address, and this might be a problem if the IP address is obtained by another user.
The SSG provides two mechanisms to prevent this problem:
For each service, you specify an access mode in the Access mode box in the Services window. SSG services can be configured for concurrent or sequential access. Concurrent access allows users to log on to this service while simultaneously connected to other services. Sequential access requires that the user log out of all other services before accessing a service configured for sequential access.
Concurrent access is recommended for most services. Sequential access is ideal for services for which security is important, such as corporate intranet access, or for which there is a possibility of overlapping address space.
SSG allows subscribers to choose one or more types of services. Each type of service has its own bandwidth requirements. For example, assume an ISP has two types of services, regular and premium. The regular service is cheaper for customers but is allocated less bandwidth per customer than the premium service, which provides more bandwidth and a higher quality connection. SSG, therefore, requires a mechanism to ensure bandwidth is distributed properly for customers using different types of services.
Traffic policing is the concept of limiting the transmission rate of traffic entering or leaving a node. In SSG, traffic policing can be used to allocate bandwidth between subscribers and between services to a particular subscriber to ensure all types of services are allocated a proper amount of bandwidth. SSG uses per-user and per-session policing to ensure bandwidth is distributed properly between subscribers (per-user policing) and between services to a particular subscriber (per-session policing). Because these policing techniques are hierarchical (bandwidth can be first policed between users and then policed again between services to a particular user), this complete feature is called SSG Hierarchical Policing.
In a user or service profile, the Q attribute for Quality of Service (QoS) is used to define per-user or per-session policing. For per-user policing, the format used in the Local RADIUS Attributes box of the CDAT Users window is as follows:
Account-Info:QU;upstream-token-rate;upstream-normal-burst;
[upstream-excess-burst];D;downstream-token-rate;
downstream-normal-burst;[downstream-excess-burst
For per-session policing, the format used in the Local RADIUS Attributes box of CDAT's Services window is as follows:
Service-Info:QU;upstream-token-rate;upstream-normal-burst;
[upstream-excess-burst];D;downstream-token-rate;
downstream-normal-burst;[downstream-excess-burst]
The following example shows how to define per-user policing in a user profile using the Local RADIUS Attributes box in the Users window:
ACCOUNT_INFO:QU;16000;8000;16000;D;24000;12000;24000
For more information on SSG Hierarchical Policing, see the document Service Selection Gateway Hierarchical Policing on Cisco Connection Online (www.cisco.com).
To create a service or update the attributes of an existing service, use the Services window (Figure 2-3).
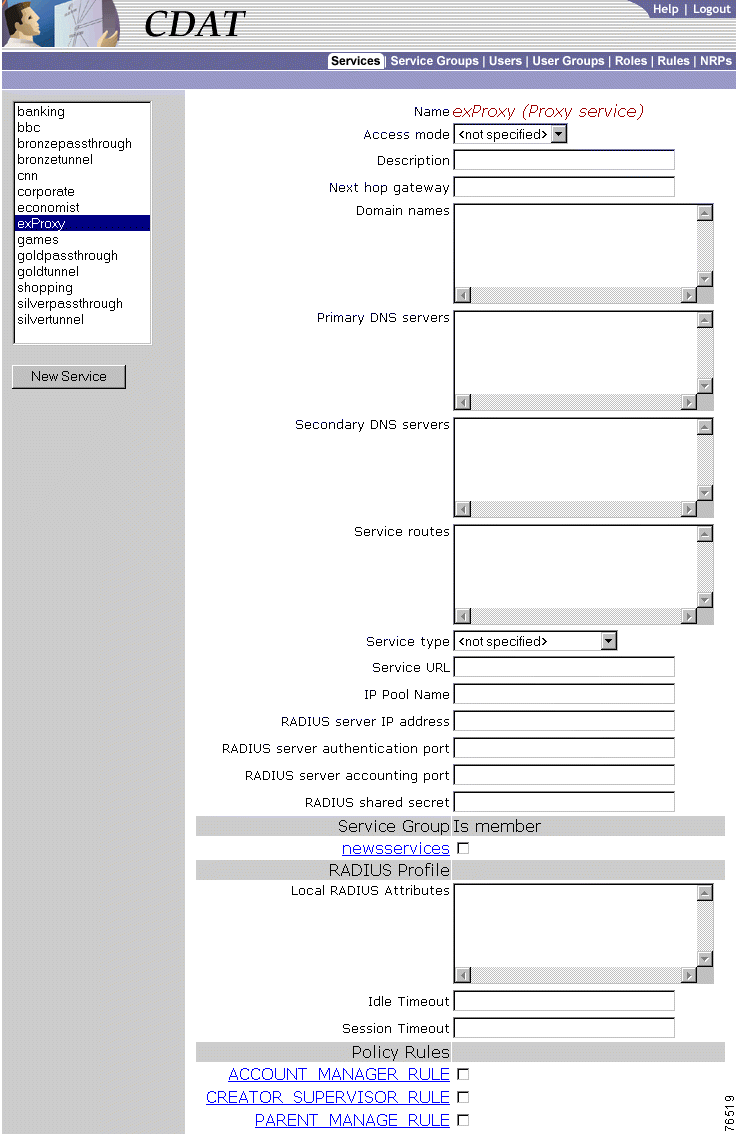
When you first create a service, you click New Service and specify the following:
For a new or existing service, you can specify the following attributes:
Primary DNS servers (Required)
Secondary DNS servers (Optional)
IP Pool Name (Optional for PPP)
For a proxy service, you specify the following attributes that provide information for the RADIUS server that the Service Selection Gateway (SSG) uses to authenticate access to this proxy service:
RADIUS server IP address (Required for a proxy service)
RADIUS server authentication port (Required for a proxy service)
RADIUS server accounting port (Required for a proxy service)
RADIUS shared secret (Required for a proxy service)
For a Layer 2 Tunnel Protocol (L2TP) tunnel service and virtual private dial network (VPDN), you specify the following attributes. For information on configuring L2TP and configuring the L2TP network server (LNS), see the Service Selection Gateway document.
Tunnel identifier (Required for a tunnel service)
Tunnel IP address (Required for a tunnel service)
Tunnel password (Required for a tunnel service)
Tunnel password confirmation (Required for a tunnel service)
Tunnel type (Required for a tunnel service)
CDAT displays the service groups that are currently defined. You indicate whether this service is a member of a service group by checking or unchecking the checkbox for the service group.
 |
Note RADIUS attributes can be specified at the service and the service group level. Service and service group RADIUS attributes are inherited. The set that applies to a service are all RADIUS attributes specified for the service and all RADIUS attributes specified for any service groups of which the service is a member. Therefore, a logical strategy is to specify RADIUS attributes at the individual service level and not at the service-group level. |
Local RADIUS Attributes
 |
Tip The Local RADIUS Attributes box allows you to define an attribute that does not appear in the boxes of a CDAT window. For example, most Cisco AV pairs cannot be specified in the boxes of a CDAT window. For a list of the RADIUS attributes that correspond to the boxes of the Services window, see "RDP Service-Profile Translation." |
CISCO-AV:ip:inacl#101=deny tcp 192.168.1.0 0.0.0.255 any eq 21
CISCO-AV:protocol:attribute=value
:) and equal sign (=) characters. In some cases, spaces are allowed between items within value. For example, spaces separate some of the parts of an access control list:CISCO-AV:ip:addr=10.2.3.4
 |
Note When a non-PPP user, such as in a bridged networking environment, disconnects from a service without logging off, the connection remains open and the user will be able to reaccess the service without going through the logon procedure. This is because no direct connection (PPP) exists between the subscriber and the SSG. To prevent non-PPP users from being logged on to services indefinitely, be sure to configure the Session-Timeout and/or Idle-Timeout attributes. |
CDAT displays the policy rules that are currently defined. You can indicate whether this service is a resource associated with a rule by checking or unchecking the checkbox for the rule. For information on rules, see the "Creating and Updating Rules" section.
To create a service group or update the attributes of an existing service group, use the Service Groups window (Figure 2-4). When creating a service group, you can make a service a member of the group by choosing the group in the Service Group Is member section of the Services window.
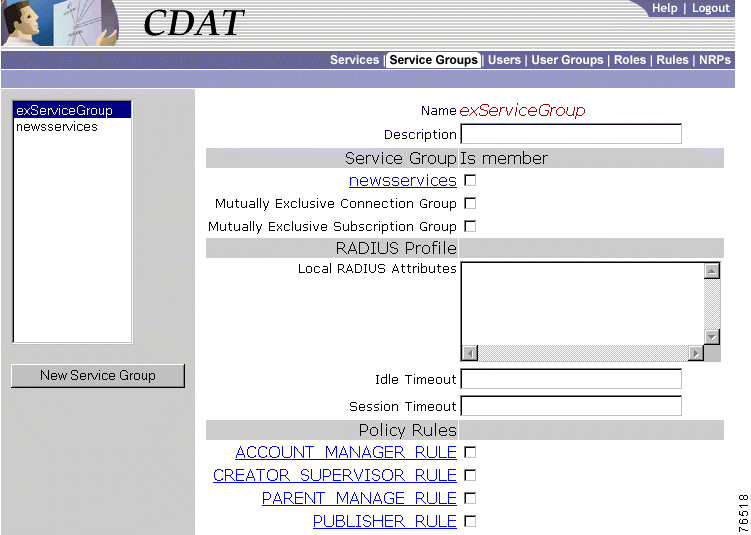
When you first create a service group, you click New Service Group and specify the following:
Name (Required)
For a new or existing service group, you can specify the following attributes:
Description (Optional)
CDAT displays the other service groups that are currently defined. You indicate if this service group is a member of another service group by checking or unchecking the checkbox for the other service group.
Mutually Exclusive Connection Group
Mutually Exclusive Subscription Group
 |
Note RADIUS attributes can be specified at the service and the service group level. Service and service group RADIUS attributes are inherited. The set that applies to a service are all RADIUS attributes specified for the service and all RADIUS attributes specified for any service groups of which the service is a member. Therefore, a logical strategy is to specify RADIUS attributes at the individual service level and not at the service-group level. |
Local RADIUS Attributes (Optional)
CISCO-AV:ip:inacl#101=deny tcp 192.168.1.0 0.0.0.255 any eq 21
 |
Note When a nonPPP user, such as in a bridged networking environment, disconnects from a service without logging off, the connection remains open and the user will be able to reaccess the service without going through the logon procedure. This is because no direct connection (PPP) exists between the subscriber and the SSG. To prevent nonPPP users from being logged on to services indefinitely, be sure to configure the Session-Timeout and Idle-Timeout attributes. |
CDAT displays the policy rules that are currently defined. You can indicate whether this service group is a resource associated with a rule by checking or unchecking the checkbox for the rule. For information on rules, see the "Creating and Updating Rules" section.
In CDAT, a user can be any one of the following:
For each category of user, the CDAT administrator creates an account for the user with the Users window. In addition, the CDAT administrator must create one or more user groups for each category of user because roles and privileges are specified for user groups, not individual users.
For the CDAT administrator, creating a user who has access to resources (services or objects and attributes in the LDAP directory) involves these steps:
1. Create a user group with the User Groups window.
2. Create a role with the Roles window and make the user group a subject (occupant) of the role. The role defines the privileges that user group members have.
3. Create a rule with the Rules window and associate the role with the rule. The rule will grant the privileges associated with specified roles to a set of resources defined in the rule. For a subscriber, the set of resources includes one or more services.
4. Create the user with the Users window and make the user a member of one or more user groups.
Creating user groups, roles, and rules is usually done once when the initial set of objects is being defined. Once these objects are defined, creating a user who actually has access to resources typically requires only Step 4.
When you define a user account for a subscriber to connect through a PPP connection, you can also define a primary service for the subscriber.
A user account for a PPP subscriber can have one primary service from which the SSG software determines an IP address range (sometimes called a local address pool). The user receives a primary IP address from this address range. This primary-service addressing mechanism allows the subscriber's IP address to be associated with a primary service, which is usually the subscriber's Internet service. If the subscriber switches to another ISP (primary service), the IP address range from which subscriber's address is obtained changes to the address pool of the new ISP.
The IP Pool Name attribute specifies the name of a local address pool. On the NAS, the deployer must use the ip local pool command to define the range of addresses for the local address pool.
As an example of the primary-service addressing mechanism, assume the following:
With the preceding conditions in place, the IP address for the user whose primary service is Internet-Blue is taken from the local pool of addresses defined on the NAS for the local address pool Blue.
CDAT allows you to define a primary service at the user and user group level. In addition, you can also define a local address pool at the user and user group level. The precedence for these definitions is as follows (item 1 having the highest precedence):
1. Pool name in the Users window
2. Primary Service in the Users window
3. Pool name in the User Groups window
4. Primary Service in the User Groups window
 |
Note When a Pool name and Primary Service are specified in the Users or User Groups window, this local address pool name takes precedence over any pool name defined for the user's primary service (IP Pool Name in the Services window). |
To create a subscriber or administrator account or to update information in an existing subscriber or administrator account, use the Users window (Figure 2-5). Service subscriptions and service-group subscriptions are not shown in the figure.
After a subscriber account is created, you can use the Create subaccount button (at the bottom of the Users window) to create a subaccount. The attributes that define a subaccount are identical to the attributes for a parent account.
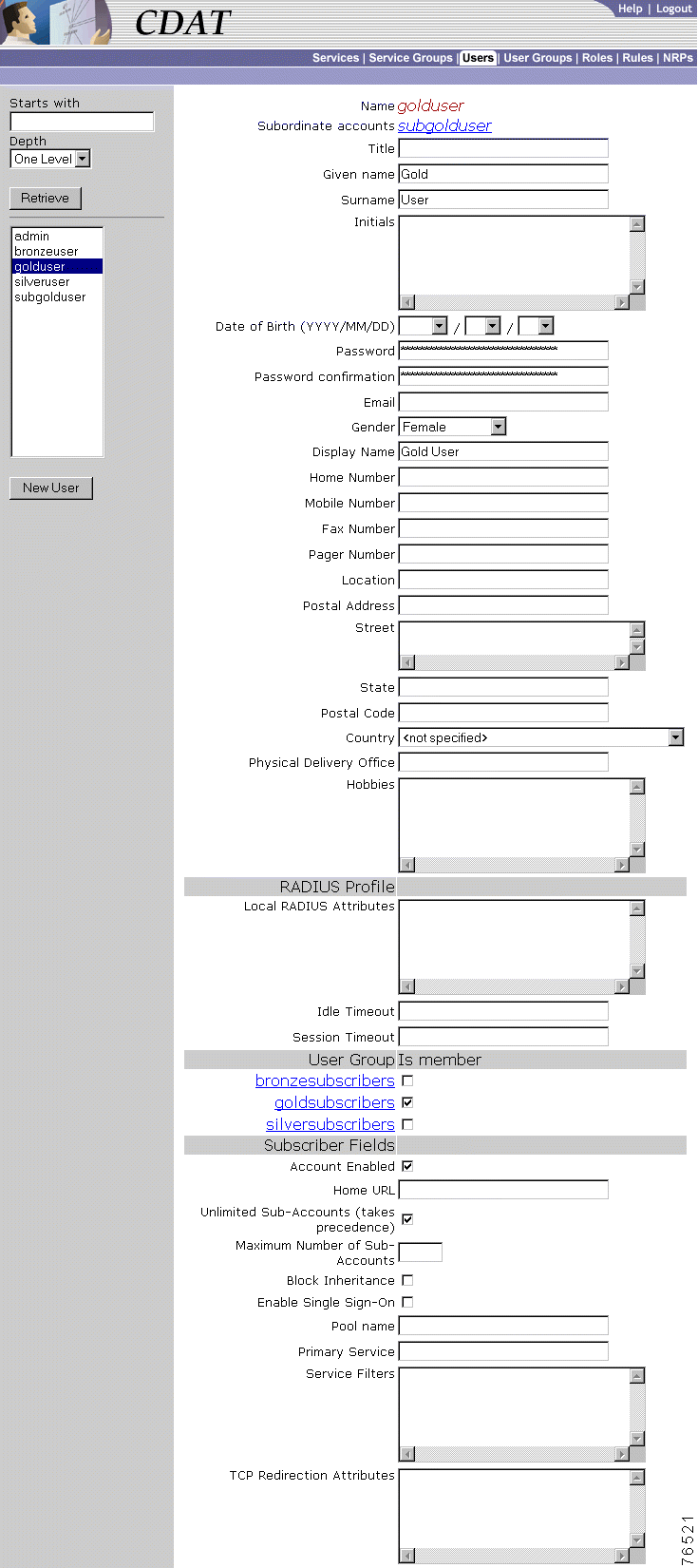
When you first create a user, you click New User and specify the following:
Name (Required)
If the user has subaccounts, CDAT displays the following:
Subordinate accounts
For a new or existing user, you can specify the following attributes:
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
 |
Note A password must contain at least one character (letter or number). |
 |
Note RADIUS attributes can be specified at the user and the user group level. User and user group RADIUS attributes are inherited. The set that applies to a user are all RADIUS attributes specified for the user and all RADIUS attributes specified for any user groups of which the user is a member. |
Local RADIUS Attributes (Optional)
CALLING-STATION-ID:123456789
number | Access list identifier. |
standard-access-control-list | Standard access control list. |
extended-access-control-list | Extended access control list. |
 |
Note The SESM web portal application uses extended access control lists for its firewall functionality. The SSG does not allow a mix of standard and extended access control lists. |
CISCO-AV:ip:inacl#101=deny tcp 192.168.1.0 0.0.0.255 any eq 21
CISCO-AV:ip:outacl#101=deny tcp 192.168.1.0 0.0.0.255 any eq 21
Idle Timeout (Optional and for Subscribers Only)
 |
Note When a non-PPP user, such as in a bridged networking environment, disconnects from a service without logging off, the connection remains open and the user will be able to reaccess the service without going through the logon procedure. This is because no direct connection (PPP) exists between the subscriber and the SSG. To prevent non-PPP users from being logged on to services indefinitely, be sure to configure the Session-Timeout and/or Idle-Timeout attributes. |
Session Timeout (Optional and for Subscribers Only)
CDAT displays the user groups that are currently defined. You can indicate whether the user is a member of a user group by checking or unchecking the checkbox for the group. For information on user groups, see the "User Groups Window" section.
Home URL (For Subscribers Only)
Unlimited Sub-Accounts (Subscribers Only)
 |
Note If you uncheck Unlimited Sub-Accounts and specify no value for Maximum Number of Sub-Accounts, the value for subaccount-creation limits defined at the user-group level takes effect. |
Maximum Number of Sub-Accounts (Optional and for Subscribers Only)
Block Inheritance (For Subscribers Only)
Enable Single Sign-On (Optional)
 |
Note For the single-sign-on feature to work in LDAP mode, the singleSign-On attribute in an SESM web portal application configuration file, such as nwsp.xml, must be set to true. For information on setting the singleSign-On attribute, see the Cisco Subscriber Edge Services Manager Installation and Configuration Guide. |
Pool name (Optional and for PPP Subscribers Only)
Primary Service (Optional and for PPP Subscribers Only)
Service Filters (Optional and for Subscribers Only)
 |
Note When a subaccount inherits service filters, the service names do not appear in the Service Filters box of the subaccount but are applied by the DESS/AUTH software at run time. |
TCP Redirection Attributes (Optional and for Subscribers Only)
For each service and service group to which the user can subscribe, CDAT displays one of the following subscription scopes:
If CDAT does not display a service or service group in the Users window, the user does not have the privileges needed to subscribe to the service or group. For each service or service group to which the user has access, you can specify the following information:
Subscribe (For Subscribers Only)
 |
Note If the subscriber has been given subscription privileges by the administrator, the subscriber can then use the SESM account-management pages to subscribe to or unsubscribe from the service or service group if desired. |
Auto-logon (For Subscribers Only)
A user group is a set of users. With CDAT, individual users—subscribers, publishers, account managers, and administrators—must be associated with one or more user groups in order to get access to resources. After creating a user group, you can make a user a member of the group by choosing the group in the User Group Is member section of the Users window.
Privileges are granted to a user group through a role. The resources to which the user group has access are defined in a rule. With RBAC, both privileges and access to resources are managed at the group level. For example, a user group made up of subscribers can be given access at the group level to a new service.
For inheritable user and user group attributes, you should define user attributes at the individual user level only when an attribute is specific to the user. You should define all other attributes at the group level. Individual group members then inherit the group value. For more information on inheritable attributes, see the "Attribute Values and Inheritance" section.
To create a new user group or update the attributes of an existing user group, use the User Groups window (Figure 2-6).

When you first create a user group, you click New User Group and specify the following:
Name (Required)
For a new or existing user group, you can specify the following attributes:
Description (Optional)
CDAT displays the roles that are currently defined. You can indicate whether the user group is an occupant of a role by checking or unchecking the checkbox for the role. For information on roles, see the "Roles Window" section.
CDAT displays the roles that are currently defined. You currently do not use the Blocked Roles attribute at the user-group level.
Local RADIUS Attributes (Optional)
CISCO-AV:ip:inacl#101=deny tcp 192.168.1.0 0.0.0.255 any eq 23
 |
Note RADIUS attributes can be specified at the user and the user group level. User and user group RADIUS attributes are inherited. The set that applies to a user are all RADIUS attributes specified for the user and all RADIUS attributes specified for any user groups of which the user is a member. |
Idle Timeout (Optional and for Subscriber Groups Only)
 |
Note When a non-PPP user, such as in a bridged networking environment, disconnects from a service without logging off, the connection remains open and the user will be able to reaccess the service without going through the logon procedure. This is because no direct connection (PPP) exists between the subscriber and the SSG. To prevent non-PPP users from being logged on to services indefinitely, be sure to configure the Session-Timeout and/or Idle-Timeout attributes. |
Session Timeout (Optional and for Subscriber Groups Only)
Account Enabled (For Subscriber Groups Only)
Home URL (For Subscriber Groups Only)
Unlimited Sub-Accounts (Subscriber Groups Only)
Maximum Number of Sub-Accounts (Optional and for Subscriber Groups Only)
Block Inheritance (Not Currently Used)
 |
Note For the single-sign-on feature to work in LDAP mode, the singleSignOn attribute in an SESM web portal application configuration file, such as nwsp.xml, must be set to true. For information on setting the singleSign-On attribute, see the Cisco Subscriber Edge Services Manager Installation and Configuration Guide. |
Pool name (Optional and for PPP Subscriber Groups Only)
Primary Service (Optional and for PPP Subscriber Groups Only)
Service Filters (Optional and for Subscriber Groups Only)
 |
Note When a subaccount inherits service filters, the service names do not appear in the CDAT Services window but are applied by the DESS/AUTH software at run time. |
TCP Redirection Attributes (Optional and for Subscriber Groups Only)
For each service and service group to which the users in the user group can subscribe, CDAT displays one of the following subscription scopes:
If CDAT does not display a service or service group in the User Groups window, the user group does not have the privileges needed to subscribe to the service or service group. For each service or service group to which the user has access, you can specify the following information:
Subscribe (For Subscriber Groups Only)
 |
Note If the user group of subscribers has been given subscription privileges by the administrator, the subscriber can then use the SESM account-management pages to subscribe to or unsubscribe from the service or service group if desired. |
Auto-logon (For Subscriber Groups Only)
In the RBAC model, a role is a collection of associated privileges. With CDAT, a user group may be assigned to multiple roles. In the context of Cisco SESM and CDAT, user groups fall into the following general categories:
With RBAC and CDAT, the underlying directory and SPE software determines the roles for a given user in these ways:
For a subaccount, roles are inherited from the parent account as determined in the preceding ways. Service filters that are defined for the parent account also apply to the subaccount.
If the RBAC objects were installed when the SPE software was installed, a set of predefined roles appear in the list of roles. For information on the predefined roles, see "Predefined Roles and Rules."
This section provides two examples of subscriber roles and the privileges that you might grant to a subscriber.
For a subscriber who requires self-care privileges (managing account attributes such as passwords and addresses) and subaccount-creation privileges, you can use the privilege Cisco_Dess_Manage and as role occupant specify the dynamic subject Self. The dynamic subject Self defines the role occupant when the accessed resource name is the same as the subject name in the submitted privilege token. The dynamic subject Self allows a subscriber to be a role occupant only for objects and attributes that are related to the specific user account.
The predefined role SELF_MANAGE_ROLE provides an example of how you can define privileges for subscriber self-care and subaccount creation with the privilege Cisco_Dess_Manage and the dynamic subject Self. The predefined roles are optionally installed with the RBAC objects as part of the SPE software installation.
In the associated rule SELF_MANAGE_RULE that defines resources for SELF_MANAGE_ROLE, the resources are specified as the container that holds the SESM/CDAT objects. In this way, a subscriber who is a member of a group occupying the SELF_MANAGE_ROLE has access to all objects and attributes that are related to this specific subscriber account.
For a subscriber to subscribe to and unsubscribe from services with the SESM web application, you must grant the user the following privileges through one or more roles:
In addition, the subscriber must be associated with a role that has Cisco_Dess_Manage privilege for the dynamic subject Self, and with a rule where the resources are specified as the container that holds the SESM/CDAT objects. In this way, the user can manage all objects and attributes that are related to the specific subscriber account. For information on this type of role and rule, see the explanation of the SELF_MANAGE_ROLE and SELF_MANAGE_RULE in the "Self-Care and Subaccount-Creation Subscriber Roles" section.
The SESMSubscribe privilege causes the SESM web application to display the navigation-bar button (MY SERVICES) that is linked to the page that allows service subscription and unsubscription.
 |
Tip To remove subscription privileges from a subscriber, remove the SESMSubscribe privilege so that SESM web application does not display the MY SERVICES button. Do not remove the privilege Cisco_Dess_Subscribe. If a subscriber does not have Cisco_Dess_Subscribe privilege, services will not be available for the SESM web application to display in the service list (where the subscriber clicks a service to connect to the service). |
For a subscriber to deploy a firewall with the SESM web application's My Firewall page, you must grant the user the following privileges through one or more roles:
In addition, the subscriber must be associated with a role that has Cisco_Dess_Manage privilege for the dynamic subject Self, and with a rule where the resources are specified as the container that holds the SESM/CDAT objects. In this way, the user can manage all objects and attributes that are related to the specific subscriber account. For information on this type of role and rule, see the explanation of the SELF_MANAGE_ROLE and SELF_MANAGE_RULE in the "Self-Care and Subaccount-Creation Subscriber Roles" section.
Roles for subscribers can require that you create two or more roles that are associated with specific privileges. As an example, consider an SESM deployment that allows only the parent user account (not the subaccount users) to create subaccounts. This model could be implemented with two distinct roles: one role for the parent user and one role for the subaccount user.
As an example of this model, assume that the parent user group is GoldSubscriberParent and is associated with a GoldSubscriberParentRole having these privileges:
The subaccount user group is GoldSubscriberSubaccount and is associated with a GoldSubscriberSubaccountRole having all of the preceding privileges except for Cisco_Dess_CreateSubAccount and Cisco_Dess_DeleteSubaccount. Not granting these two privileges to the subaccount role makes it impossible for the subaccount user to create or delete a subaccount.
To create a new role or update the attributes of an existing role, use the Roles window (Figure 2-7).

When you first create a role, you click New Role and specify the following:
Name (Required)
For a new or existing role, you can specify the following:
Description (Optional)
 |
Note The SESMFirewall and SESMSubscribe privileges (shown in Table 2-6) pertain to and are enforced by an SESM web application such as NWSP. These two privileges are not DESS/AUTH privileges that are enforced by SPE. |
 |
Tip For some examples of the privileges that subscribers require, read the section "Subscriber Role Examples" section. |
| Privilege | Description | Who Is Granted? |
|---|---|---|
Allows access to, creation, deletion, modification of a role or rule. Also allows assigning roles to subjects, policy rules to resources, and allows checking access on resources. | Administrators | |
Allows creation of user groups. Implied privileges: None | Administrators | |
Cisco_Dess_CreateAccount | Allows creation of users. Implied privileges: Cisco_Dess_CreateSubAccount | Account Managers |
Cisco_Dess_CreateService | Allows creation of services. Implied privileges: None | Publishers |
Cisco_Dess_CreateServiceGroup | Allows creation of service groups. Implied privileges: None | Publishers |
Cisco_Dess_CreateSubAccount | Allows creation of subaccounts. Implied privileges: None | Subscribers |
Cisco_Dess_Delete | Allows deletion of user groups. Implied privileges: None | Administrators |
Cisco_Dess_DeleteAccount | Allows deletion of user accounts. Implied privileges: Cisco_Dess_DeleteSubAccount | Account Managers |
Cisco_Dess_DeleteService | Allows deletion of services. Implied privileges: None | Publishers |
Cisco_Dess_DeleteSubAccount | Allows deletion of subaccounts. Implied privileges: None | Subscribers |
Cisco_Dess_Manage | Allows managing of DESS objects, including changing the set of attributes associated with these objects. Implied privileges: Cisco_Dess_Create, Cisco_Dess_CreateAccount, Cisco_Dess_CreateService, Cisco_Dess_CreateServiceGroup, Cisco_Dess_CreateSubAccount, Cisco_Dess_Delete, Cisco_Dess_DeleteAccount, Cisco_Dess_DeleteService, Cisco_Dess_DeleteSubaccount, Cisco_Dess_ManagePassword, Cisco_Dess_Modify, Cisco_Dess_Read, Cisco_Dess_Subscribe, Cisco_Dess_Unsubscribe | Administrators |
Cisco_Dess_Manage_Password | Allows reading and changing of passwords on user objects. This privilege grants modify rights to the set of attributes associated with the passwords. Implied privileges: None | Subscribers |
Cisco_Dess_Modify | Allows changes to attributes for DESS objects. Implied privileges: None | Subscribers |
Cisco_Dess_Read | Allows reading of DESS objects and their attributes. Cisco_Dess_Read privilege is needed for displaying services and, therefore, is needed for service subscription. For information on service-subscription privileges, see the "Service Subscription Roles" section. Implied privileges: None | Subscribers |
Cisco_Dess_Subscribe | Allows subscription to a service. For information on service-subscription privileges, see the "Service Subscription Roles" section. Implied privileges: Cisco_Dess_Unsubscribe | Subscribers |
Cisco_Dess_Supervisor | Allows management of DESS objects, including changing the set of attributes associated with these objects. Cisco_Dess_Supervisor and Cisco_Dess_Manage are identical. Implied privileges: Cisco_Dess_Create, Cisco_Dess_CreateAccount, Cisco_Dess_CreateService, Cisco_Dess_CreateServiceGroup, Cisco_Dess_CreateSubAccount, Cisco_Dess_Delete, Cisco_Dess_DeleteAccount, Cisco_Dess_DeleteService, Cisco_Dess_DeleteSubaccount, Cisco_Dess_Manage, Cisco_Dess_ManagePassword, Cisco_Dess_Modify, Cisco_Dess_Read, Cisco_Dess_Subscribe, Cisco_Dess_Unsubscribe | Administrators |
Cisco_Dess_Unsubscribe | Allows unsubscription to a service. For information on service-subscription privileges, see the "Service Subscription Roles" section. Implied privileges: None | Subscribers |
SESMFirewall | Allows an SESM web application to display the MY FIREWALL button that the user clicks for firewall management. For information firewall-related privileges, see the "Firewall-related Roles" section. Implied privileges: None | Subscribers |
SESMSubscribe | Allows an SESM web application to display the MY SERVICES button that the user clicks for service subscriptions. For information on service-subscription privileges, see the "Service Subscription Roles" section. Implied privileges: None | Subscribers |
A rule defines the set of conditions under which a role is associated with one or more resources. User groups can be made occupants of one or more roles. In this way, an administrator can define the resources that can be accessed by members of a user group.
If the RBAC objects were installed when the DESS software was installed, CDAT displays a set of predefined rules in the list of rules. For information on the predefined rules, see "Predefined Roles and Rules."
To create a new rule or update the attributes of an existing rule, use the Rules window (Figure 2-8).

When you first create a rule, you click New Rule and specify the following:
Name (Required)
For a new or existing rule, you can specify the following:
Description (Optional)
CISCO_AZN indicates authorization policies and is the only keyword used.Variable Operator Value
ResourceClass==top
ResourceClass is the only variable used.== operator is the only operator used.top is the only value used.CDAT allows creation of NRP-related information in an NRP object. Currently, NRP-related information is for a next-hop table.
Because multiple NRP-SSGs might access services from different networks, each service profile can specify a next-hop key, which is a string identifier, rather than an actual IP address. For each service, use the Services window's Next hop gateway box to specify the next-hop key for the service.
For each NRP-SSG to determine the IP address associated with the next-hop key, each NRP-SSG downloads its own next-hop table that associates keys with IP addresses. In the NRPs window, you use the Next Hop Table box to define the entries in the next-hop table for each NRP-SSG. The name of the next-hop table is the name that you give when you click New NRP.
To create and download a next-hop table that an NRP-SSG can use to access services from different networks, do the following:
Step 1 For each service, use CDAT and the Next hop gateway box in the Services window to specify the next-hop key for the service.
Step 2 For each NRP-SSG, use CDAT to create a next-hop table.
a. In the NRPs window, click New NRP to create a next-hop table for the NRP, and specify the name for the next-hop table in the Name box. With CDAT, the next-hop table takes its name from the name of the NRP.
b. In the Next Hop Table box, define the entries in the next-hop table for the NRP-SSG. For example:
service3=192.168.103.3
service2=192.168.103.2
service1=192.168.103.1
Worldwide_Gaming=192.168.4.2
Step 3 On the RADIUS Data Proxy (RDP) server, specify the next-hop table password that will be used to access the next-hop table. The next-hop table password is specified in the \rdp\config\rdp.xml file:
<!-- Following attribute and type handle next hop profiles -->
<Call name="setAttribute">
<Arg>PASSWORD:nexthopcisco</Arg>
<Arg>NextHopRequest</Arg>
</Call>
By default, the password is nexthopcisco.
Step 4 On each NRP-SSG, use the following command to download the appropriate next-hop table:
In the preceding command, next-hop_table_name is the name you specified when creating the next-hop table (Step 2a). The next-hop_table_password is the password that is defined in the rdp.xml file (Step 3). For information on the ssg next-hop command, see the Service Selection Gateway document.
To create or update information for an NRP, use the NRPs window (Figure 2-9). Currently, the only information you can create is a next-hop table.
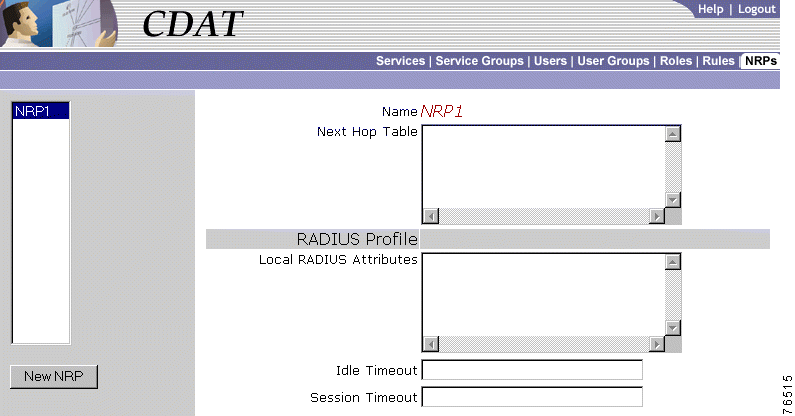
The NRPs window allows you to create a next-hop table. When you first create a next-hop table, you click New NRP and specify the following:
Name (Required)
For a new or existing next-hop table, you can specify the following:
Next Hop Table (Required)
service3=192.168.103.3
service2=192.168.103.2
service1=192.168.103.1
Worldwide_Gaming=192.168.4.2
Local RADIUS Attributes (Not Currently Used)
Idle Timeout (Not Currently Used)
Session Timeout (Not Currently Used)
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
Posted: Mon Dec 16 08:45:54 PST 2002
All contents are Copyright © 1992--2002 Cisco Systems, Inc. All rights reserved.
Important Notices and Privacy Statement.