|
|

This chapter describes how to configure Fast Ethernet and Gigabit Ethernet VLAN trunks on a switch. For information on adding and deleting VLANs, refer to "Configuring VTP and Virtual LANs."
Switches support the following trunking methods for transmitting VLAN traffic over 100BaseT and Gigabit Ethernet ports:
In addition, you can can enable ATM trunking by installing a Catalyst 2900 series XL ATM module in a Catalyst 2900 series XL switch. ATM connectivity is described in the
Catalyst 2900 Series XL ATM Modules Installation and Configuration Guide.
The trunking described in this chapter is not supported on all switches and modules. See the Cisco IOS Desktop Switching Software Configuration Guide for the list of products that support trunking.
This chapter consists of these sections:
A trunk is a point-to-point link that transmits and receives traffic between switches or between switches and routers. Trunks carry the traffic of multiple VLANs and can extend VLANs across an entire network. 100BaseT and Gigabit Ethernet trunks use Cisco ISL (the default protocol) or industry-standard IEEE 802.1Q to carry traffic for multiple VLANs over a single link.
Figure 3-1 shows a network of switches that are connected by ISL trunks.

This section describes how to use the CLI to configure an ISL or IEEE 802.1Q trunk port, how to define the VLANs that can use a port, and how to disable a trunk port.
To define a port as an ISL trunk port, perform this task from privileged EXEC mode:
| Task | Command |
|---|---|
Step 1 Enter global configuration mode. | configure terminal |
Step 2 Enter the interface configuration command mode and the port to be added to the VLAN. | interface interface_id |
Step 3 Configure the port with a VLAN membership mode of trunk. | |
switchport trunk encapsulation isl | |
Step 5 Return to privileged EXEC mode. | end |
Step 6 Verify your entries. | show interface interface-id switchport |
Step 7 Save the configuration. | copy running-config startup-config |
| 1To configure IEEE 802.1 Q, enter this command: switchport trunk encapsulation dotlq |
This example shows how to configure a port as a trunk, verify the trunk configuration, and save the change to the startup configuration file:
Switch# configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
Switch(config)# interface fa0/1
Switch(config-if)# switchport mode trunk
Switch(config-if)# switchport trunk encapsulation isl
Switch(config-if)# end
Switch# show interface fa0/1 switchport
Name: Fa0/1
Switchport: Enabled

Administrative mode: trunk
Operational Mode: trunk
Administrative Trunking Encapsulation: isl

Operational Trunking Encapsulation: isl
Negotiation of Trunking: Disabled
Access Mode VLAN: 0 ((Inactive))
Trunking Native Mode VLAN: 1 (default)
Trunking VLANs Enabled: 1-3,1002-1005
Trunking VLANs Active: 1-3
Pruning VLANs Enabled: NONE
Switch# copy running-config startup-config
Building configuration...
[OK]
Switch#
A trunk port by default sends to and receives traffic from all VLANs in the VLAN database. All VLANs, 1 to 1005, are allowed on each trunk. However, you can remove VLANs from the allowed list, preventing traffic from those VLANs from passing over the trunk. To restrict the traffic a trunk carries, use the remove vlan-list parameter to remove specific VLANs from the allowed list.
To modify the allowed list of a trunk, perform this task from privileged EXEC mode:
| Task | Command |
|---|---|
Step 1 Enter global configuration mode. | configure terminal |
Step 2 Enter the interface configuration command mode and the port to be added to the VLAN. | interface interface_id |
Step 3 Configure the VLAN membership mode for trunks. | switchport mode trunk |
Step 4 Define the VLANs that are not allowed to transmit and receive on the port. The vlan-list parameter is a range of VLAN IDs separated by a hyphen or specific VLAN IDs separated by commas. | switchport trunk allowed vlan remove vlan-list |
Step 5 Return to privileged EXEC. | end |
Step 6 Verify your entries. | show interface interface-id switchport allowed-vlan |
Step 7 Save the configuration. | copy running-config startup-config |
This example shows how to define the allowed VLANs list for trunk port Fa0/1 to allow VLANs 1 to 100, VLAN 250, and VLANs 500 to 1005, and how to verify the allowed VLAN list for the trunk:
Switch(config)# interface fa0/1
Switch(config-if)# switchport mode trunk
Switch(config-if)# switchport trunk allowed vlan remove 101-499
Switch(config-if)# switchport trunk allowed vlan add 250
Switch(config-if)# end
Switch# show interface fa0/1 switchport allowed-vlan

"1-100,250,500-1005"
Switch#
You can disable trunking on a port by returning it to its default static-access mode. To disable trunking on a port, perform the following tasks from privileged EXEC mode:
| Task | Command |
|---|---|
Step 1 Enter global configuration mode. | configure terminal |
Step 2 Enter the interface configuration command mode and the port to be added to the VLAN. | interface interface_id |
Step 3 Return the port to its default static-access mode. | no switchport mode |
Step 4 Return to privileged EXEC. | end |
Step 5 Verify your entries. | show interface interface-id switchport |
This example shows how to disable trunking on a port:
Switch# configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
Switch(config)# interface fa0/1
Switch(config-if)# no switchport mode
Switch(config-if)# end
Switch# show interface fa0/1 switchport
Name: Fa0/1
Switchport: Enabled
Administrative mode: static access

Operational Mode: static access
Administrative Trunking Encapsulation: isl
Operational Trunking Encapsulation: isl
Negotiation of Trunking: Disabled
Access Mode VLAN: 1 (default)
Trunking Native Mode VLAN: 1 (default)
Trunking VLANs Enabled: NONE
Pruning VLANs Enabled: NONE
Load sharing divides the bandwidth supplied by parallel trunks connecting switches. To avoid loops, Spanning-Tree Protocol (STP) normally blocks all but one parallel link between switches. With load sharing, you divide the traffic between the links according to which VLAN the traffic belongs to.
There are two ways to configure load sharing by using trunk ports: using STP port priorities or using STP path costs. If you configure load sharing using STP port priorities, both load-sharing links must be connected to the same switch. If you configure load sharing using STP path costs, each load-sharing link can be connected to the same switch or to two different switches.
When two ports on the same switch form a loop, the port priority setting determines which port is enabled and which port is in standby mode. You can set the priorities on a parallel trunk port so that the port carries all the traffic for a given VLAN. The trunk port with the higher priority (lower values) for a VLAN is forwarding traffic for that VLAN. The trunk port with the lower priority (higher values) for the same VLAN remains in a blocking state for that VLAN. One trunk port transmits or receives all traffic for the VLAN.
Figure 3-2 shows two trunks connecting supported switches. In this example, the switches are configured as follows:
In this way, trunk 1 carries traffic for VLANs 8 through 10, and trunk 2 carries traffic for VLANs 3 through 6. If the active trunk fails, the trunk with the lower priority takes over and carries the traffic for all of the VLANs. There is no duplication of traffic over any trunk port.
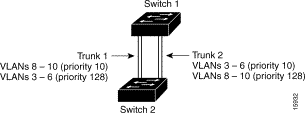
Follow these steps to configure the network shown in Figure 3-2:
Step 1 Configure a VTP domain on Switch 1, and configure Switch 1 as a VTP server.
Switch_1# vlan database
Switch_1(vlan)# vtp domain milano
Changing VTP domain name from test to milano
Switch_1(vlan)# vtp server
Device mode already VTP SERVER.
Step 2 Verify the VTP information by exiting to privileged EXEC mode and displaying the VTP information for both switches.
Switch_1(vlan)# exit
APPLY completed.
Exiting....
Switch_1# show vtp status
VTP Version : 2
Configuration Revision : 0
Maximum VLANs supported locally : 68
Number of existing VLANs : 59
VTP Operating Mode : Server

VTP Domain Name : milano

VTP Pruning Mode : Disabled
VTP V2 Mode : Disabled
VTP Traps Generation : Disabled
MD5 digest : 0x53 0x97 0x06 0x02 0xF8 0x6F 0x45 0x85
Configuration last modified by 172.20.128.151 at 3-5-93 01:05:21
Step 3 From privileged EXEC mode, verify that the VLANs exist in the database on Switch 1.
Switch_1# show vlan
VLAN Name Status Ports
---- -------------------------------- --------- ---------------------------
1 default active Fa0/2, Fa0/3, Fa0/4, Fa0/5,
Fa0/10, Fa0/11, Fa0/12
2 VLAN0002 active
3 VLAN0003 active
4 VLAN0004 active
5 VLAN0005 active
6 VLAN0006 active
7 VLAN0007 active
8 VLAN0008 active
9 VLAN0009 active
10 VLAN0010 active
Step 4 Beginning from privileged EXEC mode, configure the trunks on Switch 1 ports. The trunks default to ISL trunking.
Switch_1# configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
Switch_1(config)# interface fa0/1
Switch_1(config-if)# switchport mode trunk
Switch_1(config-if)# end
Switch_1# show interface fa0/1 switchport
Name: Fa0/1
Switchport: Enabled
Administrative mode: trunk

Operational Mode: trunk
Administrative Trunking Encapsulation: isl
Operational Trunking Encapsulation: isl
Negotiation of Trunking: Disabled
Access Mode VLAN: 0 ((Inactive))
Trunking Native Mode VLAN: 1 (default)
Trunking VLANs Enabled: ALL
Trunking VLANs Active: 1-55
Pruning VLANs Enabled: NONE
Repeat this procedure to define the trunk ports on Switch 1 and Switch 2.
Step 5 When the trunk links come up, VTP passes the VTP and VLAN information to Switch 2. Verify that switch 2 has learned the VLAN configuration.
Switch_2# show vlan
VLAN Name Status Ports
---- -------------------------------- --------- ---------------------------
1 default active Fa0/2, Fa0/3, Fa0/4, Fa0/5,
Fa0/10, Fa0/11, Fa0/12
2 VLAN0002 active
3 VLAN0003 active
4 VLAN0004 active
5 VLAN0005 active
6 VLAN0006 active
7 VLAN0007 active
8 VLAN0008 active
9 VLAN0009 active
10 VLAN0010 active
Step 6 Use the spanning-tree command to assign the different port priorities on the different VLANs.
Switch_1# configure terminal
Enter configuration commands, one per line. End with CNTL/Z
Switch_1(config-if)# interface fa0/1
Switch_1(config-if)# spanning-tree vlan 8 9 10 port-priority 10
Switch_1(config-if)# end
Switch_1(config)# interface fa0/2
Switch_1(config-if)# spanning-tree vlan 3 4 5 6 port-priority 10
Switch_1(config-if)# end
Step 7 Verify the entries by entering the privileged EXEC show running-config command:
Switch_1# show running-config
.

interface FastEthernet0/1
switchport mode trunk
spanning-tree vlan 8 priority 10
spanning-tree vlan 9 priority 10
spanning-tree vlan 10 priority 10
!

interface FastEthernet0/2
switchport mode trunk
spanning-tree vlan 3 priority 10
spanning-tree vlan 4 priority 10
spanning-tree vlan 5 priority 10
spanning-tree vlan 6 priority 10
!
interface FastEthernet0/3
!
interface FastEthernet0/4
port group 11
.
.
You can configure parallel trunks to share VLAN traffic by setting different path costs on a trunk and associating the path costs with different sets of VLANs. The VLANs keep the traffic separate, STP does not disable a port because there are no loops, and redundancy is maintained in the event of a lost link.
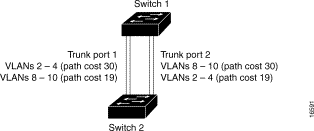
In this example, trunk ports 1 and 2 are 100BaseT ports. The path costs for the VLANs are assigned as follows:
Follow these steps to configure two parallel trunks to load share based on the STP path cost parameter:
Step 1 From privileged EXEC mode, configure the two ports as trunk ports. The trunk defaults to ISL trunking.
Switch_1# configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
Switch_1(config)# interface fa0/1
Switch_1(config-if)# switchport mode trunk
Switch_1(config-if)# end
Switch_1# configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
Switch_1(config)# interface fa0/2
Switch_1(config-if)# switchport mode trunk
Switch_1(config-if)# end
Step 2 Verify the entries by entering the privileged EXEC show running-config command:
Switch# show running-config
Building configuration...
Current configuration:
!
version 11.2
no service pad
no service udp-small-servers
no service tcp-small-servers
!
hostname Switch
!
enable password grandkey
!
interface VLAN1
ip address 172.20.128.178 255.255.255.0
no ip route-cache
!
interface FastEthernet0/1

switchport mode trunk
!
interface FastEthernet0/2

switchport mode trunk
Step 3 When the trunk links come up, Switch 1 receives the VTP information from the other switches. Verify that Switch 1 has learned the VLAN configuration.
Switch_1# show vlan
VLAN Name Status Ports
---- -------------------------------- --------- ---------------------------
1 default active
2 VLAN0002 active
3 VLAN0003 active
4 VLAN0004 active
5 VLAN0005 active
6 VLAN0006 active
7 VLAN0007 active
8 VLAN0008 active
9 VLAN0009 active
10 VLAN0010 active
Step 4 Use the spanning-tree command to assign the cost parameter to the VLANs that use the trunk on Switch 1.
Switch_1# configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
Switch_1(config)# interface fa0/1

Switch_1(config-if)# spanning-tree vlan 2 3 4 cost 30
Switch_1(config-if)# end
Switch_1# configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
Switch_1(config)# interface fa0/2

Switch_1(config-if)# spanning-tree vlan 8 9 10 cost 30
Switch_1(config-if)# end
Step 5 Verify the entry by entering the privileged EXEC show running-config command:
Switch# show running-config
Building configuration...
Current configuration:
!
version 11.2
no service pad
no service udp-small-servers
no service tcp-small-servers
!
hostname Switch
!
enable password grandkey
!
interface VLAN1
ip address 172.20.128.179 255.255.255.0
no ip route-cache
!
interface FastEthernet0/1
switchport mode trunk

spanning-tree vlan 2 cost 30
spanning-tree vlan 3 cost 30
spanning-tree vlan 4 cost 30
!
interface FastEthernet0/2

spanning-tree vlan 8 cost 30
spanning-tree vlan 9 cost 30
spanning-tree vlan 10 cost 30
!
interface FastEthernet0/3
!
interface FastEthernet0/4
Switches in hierarchical networks can be grouped into backbone switches, distribution switches, and access switches. Figure 3-4 shows a complex network where distribution switches and access switches each have at least one redundant link that is blocked by STP to prevent loops.
If a switch looses connectivity, the switch begins using the alternate paths as soon as STP selects a new root port. When STP reconfigures the new root port, other ports flood the network with multicast packets, one for each address that was learned on the port. You can limit these bursts of multicast traffic by reducing the max-update-rate parameter (the default for this parameter is 150 packets per second). However, if you enter zero, station-learning frames are not generated, so the STP topology converges more slowly after a loss of connectivity.
STP UplinkFast is an enhancement that accelerates the choice of a new root port when a link or switch fails or when STP reconfigures itself. The root port transitions to the forwarding state immediately without going through the listening and learning states, as it would do with normal STP procedures. UplinkFast is most useful in edge or access switches and might not be appropriate for backbone devices.
When you enable UplinkFast, it is enabled for the entire switch and cannot be enabled for individual VLANs.
Enter this command in global configuration mode to configure UplinkFast:
Switch(config)# spanning-tree uplinkfast [max-update-rate pkts-per-second]

ISL, IEEE 802.1Q, and ATM trunking interacts with other switch features in the following ways:
A trunk cannot be a monitor port. A static-access port can monitor the traffic of its VLAN on a trunk port. | |
ISL and 802.1Q trunks can be grouped into EtherChannel port groups, but all trunks in the group must have the same configuration. ATM ports are always trunks but cannot be part of an EtherChannel port group. When a group is first created, all ports follow the parameters set for the first port to be added to the group. If you change the configuration of one of the following parameters, the switch propagates the setting you entered to all ports in the group: | |
A trunk cannot be a secure port. | |
Blocking unicast and multicast packets on a trunk | The port block command can be used to block the forwarding of unknown unicast and multicast packets to VLANs on a trunk. However, if the trunk is acting as a network port, unknown unicast packets cannot be blocked. |
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
Posted: Wed May 26 12:03:02 PDT 1999
Copyright 1989-1999©Cisco Systems Inc.