|
|

The Cisco 6510 Service Selection Gateway (Cisco 6510) is a hardware and software solution that allows users with high-speed fixed network connections, such as Asymmetrical Digital Subscriber Line (ADSL) equipment and cable modems, to gain access to intranet and Internet services through an interface similar to Dial-Up Networking.
The Cisco 6510 allows users to connect to and disconnect from multiple services, without having to log off. This offers flexibility and convenience to users and enables service providers to bill users based on connect time and services used, rather than charging a flat rate.
The Cisco 6510 is installed in a network to provide:
The Cisco 6510 contains three Ethernet cards that interface with:
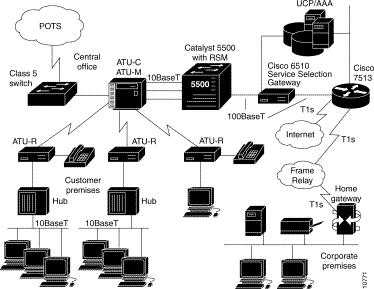
Figure 1-1 shows a diagram of a typical network topology including the Cisco 6510. Users at remote sites access the network using an ADSL modem (ADSL Termination Unit - Remote, or ATU-R). At the service provider's Network Operations Center (NOC), incoming connections are processed by an ADSL System Management Unit (ATU-M) that controls an array of ADSL central office terminal units (ATU-C). This equipment converts the ADSL connections into 10BaseT connections.
The 10BaseT connections are fed into a Cisco Catalyst 5000 with dedicated 10BaseT switched ports. Each 10BaseT port is a unique virtual local area network (VLAN) that is transmitted to a Route Switching Module (RSM) in the Catalyst 5000. The Catalyst 5000 is connected through a 100BaseT connector to the first Ethernet port on the Cisco 6510.
The second Cisco 6510 Ethernet port is connected to the management network where authentication, authorization, and accounting (AAA), RADIUS, Dynamic Host Configuration Protocol (DHCP), and SNMP servers reside.
The third Cisco 6510 Ethernet port is connected to the SP network, which connects to the transparent passthrough services (usually the Internet), corporate home gateways, and value-added services.
The user opens a browser and accesses the Cisco Service Selection Dashboard (Cisco SSD), a web server application. The Cisco SSD forwards user login information to the Cisco 6510, which forwards the information to the AAA server.
The Cisco 6510 ships with the following:
This section describes Cisco 6510 features.
The Cisco 6510 works in conjunction with the Cisco Service Selection Dashboard (Cisco SSD). The Cisco SSD is a specialized web server that allows users to log on to and disconnect from multiple passthrough and tunneled services through a standard web browser.
After the user opens a web browser, the Cisco 6510 allows access to an IP address or range of IP addresses specified by the DefaultServerIP parameters (the IP address of the Cisco SSD). The Cisco SSD prompts the user for a username and password. After the user is authenticated, the Cisco SSD presents a list of available services.
When a user selects a tunneled service, there is another username and password prompt. After authentication, the user can access the service until he or she logs out from the service, logs out from the Cisco SSD, or is timed out.
The Cisco 6510 is designed to work with Cisco User Control Point (UCP) software, which provides RADIUS-based AAA services, DHCP address assignment, and a Domain Name System (DNS) server. The Cisco 6510 can also be used with other vendors' AAA servers and RADIUS implementations.
The Cisco 6510 supports up to 250,000 simultaneous service and transparent passthrough connections. These connections are described in the following sections.
The Cisco 6510 can forward traffic through interface card 2 without modification. Because Network Address Translation (NAT) is not performed for this type of traffic, overhead is reduced. Passthrough service is ideal for standard Internet access.
The Cisco 6510 can establish L2F tunnels on behalf of clients.
Home gateways assign an IP address for each L2F tunnel. However, client PCs running TCP/IP are only allowed one IP address. To overcome this limitation, the Cisco 6510 performs NAT for packets sent between the IP address assigned by the home gateway and the client's actual IP address.
When enabled, the default user passthrough feature allows a user's packets to be forwarded unmodified if they are not destined for an active service.
When enabled, transparent passthrough allows unauthenticated traffic to pass through the Cisco 6510 in either direction without modification. Some of the applications for this feature include:
The Cisco 6510 supports multicast traffic.
When the Cisco 6510 receives an upstream multicast packet, it checks the source IP to verify whether the host is logged in. If the host is logged in, it sends a copy of the packet to each of the user's active service connections. If the host is not logged in, the Cisco 6510 checks the protocol ID field to see whether the protocol is IGMP. If it is and IGMPHelperEnable is enabled, the packet is copied to each connection. Otherwise, the packet is dropped.
When the Cisco 6510 receives a downstream multicast packet through an L2F tunnel or passthrough, it forwards the packet through interface card 0 using Ethernet multicast. Because the destination IP address is class D, NAT is not performed for tunneled services.
The Cisco 6510 uses the filter attribute to prevent users, services, and passthrough traffic from accessing destinations and applications.
When the filter attribute is added to a service profile, users are prevented from accessing the specified IP address, port, and subnet mask combinations through the service.
When the filter attribute is added to a user profile, the user is completely prevented from accessing the specified IP address, port, and subnet mask combinations.
When the filter attribute is added to the TPTFilter pseudo-service profile, all transparent passthrough traffic is prevented from accessing the specified IP address, port, and subnet mask combinations.
When users are accessing multiple services, the Cisco 6510 must determine the services for which the packets are destined. To do this, the Cisco 6510 uses an algorithm to create a service access order list. This list is stored in the user's host object and contains services that are currently open and the order in which they are searched.
The algorithm that creates this list orders the open services from the smallest network to the largest network. Smallness and largeness are determined by the subnet mask of the Service Route RADIUS attribute. A smaller subnet mask implies a larger network. For example, 255.0.0.0 is a smaller subnet mask than 255.255.255.0 and a larger network.
When creating service profiles, define as small a network as possible. If there is overlapping address space, packets might be forwarded to the wrong service.
The next hop gateway attribute specifies the IP address of a router adjacent (same segment) to interface card 2 of the Cisco 6510 that acts as the next hop for packets destined for the service.
When the Cisco 6510 receives a DNS request, it performs domain name matching using the Domain Name attribute from the service profiles of the currently logged in services.
If a match is found, the request is directed to the DNS server for the matched service.
If a match is not found and the user is logged on to a service that has Internet connectivity, the request is directed to the first service in the user's service access order list that has Internet connectivity.
If a match is not found and the user is not logged on to a service that has Internet connectivity, the request is forwarded unmodified through interface card 2 to the service provider's DNS server (specified in the client's TCP/IP stack).
When the Cisco 6510 receives a DHCPREQUEST, it adds a ReplyToSender DHCP option to the end of the request and changes the source and destination IP addresses to instruct the DHCP server to reply directly to the Cisco 6510. When the Cisco 6510 receives the DHCPOFFER reply from the DHCP server, it performs reverse modification and forwards it to the requesting host.
For a bridged network, where Cisco 6510 interface card 0 will be a default gateway for some hosts, the Cisco 6510 can act as a DHCP Relay agent. When enabled, the Cisco 6510 fills the giaddr field with the Cisco 6510 interface card 0 IP address and sends the request to the DHCP server configured by the DHCPIP parameter.
The Session-Timeout attribute specifies the maximum time a connection can exist. The Idle-Timeout attribute specifies the maximum time a connection can remain idle before being disconnected.
The Session-Timeout and Idle-Timeout attributes can be used in either a user or service profile. In a user profile, the attribute applies to a user session. In a service profile, the attribute individually applies to each service connection.
Cisco 6510 services can be configured for concurrent or sequential access. Concurrent access allows users to log on to this service while simultaneously connected to other services. Sequential access requires that the user log out of all other services before accessing this service.
Concurrent access is recommended for most services. Sequential access is ideal for tunneled connections to corporate home gateways and services where security is important.
The Cisco 6510 supports two SNMP traps: Failover Switchover and AAA Service Switchover.
When two Cisco 6510s are configured for failover and the active unit fails, the standby unit takes over and becomes the active unit. Whenever this occurs, a Failover Switchover SNMP trap is generated and will appear to the SNMP server as a "Warm Start" trap.
When two AAA servers are configured for failover and the active unit fails, the standby unit takes over and becomes the active unit. Whenever this occurs, a AAA Service Switchover SNMP trap is generated and will appear to the SNMP server as an "Authentication Failure" trap.
The Cisco 6510 provides a failover mechanism that, in the event of system failure, allows itself to be replaced by a standby Cisco 6510. To implement failover, connect the failover ports of two Cisco 6510s using a Cisco failover cable and configure the active unit as required. This unit is considered the "active" unit and the second unit is considered the "standby" unit.
The active unit performs its normal network functions while the standby unit only monitors, ready to take control in case the active unit fails. To ensure that both units are configured exactly the same, configuration replication occurs over the failover cable from the active unit to the standby unit:
Each unit has a presence on the network. The active unit uses its own IP and Media Access Control (MAC) addresses (unless a failover has occurred, the active unit is determined by the unit that has the end of the failover cable labeled "Primary" or "Unit 0" plugged into it) and the standby unit uses its own IP and MAC addresses. If a switchover occurs, the units swap the IP and MAC addresses they are using and transparently replace each other's presence on the network. Because this action is invisible to the network, the IP to MAC address relationships remain exactly the same. No Address Resolution Protocol (ARP) tables in the network will time out or need to be changed. No other piece of network equipment needs to know about the redundancy or that a switchover occurred.
Fault detection is based on the following:
If the active unit fails, a switchover will occur. To restore the units to a normal state, do one of the following:
If a failure still exists, the unit will fail again within the normal time required to detect the failure.
If a network interface card (NIC) is not plugged in to an operational network, the unit will fail. If, at a later time, the NIC is plugged in and detects a valid network, the unit will clear its failed state and resume normally. This is the only condition in which a failed unit will automatically clear its own failure.
The Cisco 6510 acts as a proxy server for any device that sends RADIUS packets directly to the IP address of interface card 0.
When the Cisco 6510 receives a RADIUS packet, it substitutes its own IP address with the source IP address and forwards the packet to the AAA server through the management interface. When the Cisco 6510 receives any reply packets, it forwards them to the sender.
To enable this feature, configure any NASes on the host network to use the Cisco 6510 as the AAA server.
In a dial-up networking environment, a user might disconnect from the network and release the IP address without logging out from the Cisco 6510. If this happens, the Cisco 6510 will continue to allow traffic to pass from that IP address, and this might be a problem if the IP address is obtained by another user.
The Cisco 6510 provides several mechanisms to prevent this problem:
In a dial-up networking environment, a user might disconnect from the network and release an IP address without logging out from the Cisco 6510. If this happens, the Cisco 6510 will continue to allow traffic to pass from that IP address and this might be a problem if the IP address is obtained by another user.
To prevent this from happening, the Cisco 6510 examines RADIUS accounting packets that pass through the Cisco 6510.
The Cisco 6510 supports syslog debugging. Using the debug and logtarget commands, you can control the level of debugging and the logging destination (console or syslog server).
The Cisco 6510 supports configuration file saving and loading through the config save and config load commands. This enables you to back up and restore the Cisco 6510 configuration settings or copy a configuration to another Cisco 6510.
The Cisco 6510 can be configured to work with a single RADIUS or DNS server, two servers in a load-balancing configuration, or two servers in a fault-tolerant configuration. Select from the following:
|
|