
 |  |
21.7. Remote Authentication Dial-in User Service (RADIUS)
RADIUS is a protocol normally used to authenticate dial-in users. It provides both authentication and accounting data and is widely supported by dial-in terminal servers and other devices designed to support remote access over telephone lines.When you are using RADIUS, a user dials up or otherwise contacts some sort of server that is giving out connections. That server is a RADIUS client; it holds a dialog with the user and passes information back and forth to a RADIUS client. Remember that it is the terminal server that is the RADIUS client, not the remote machine. The remote machine won't be able to join the network until after the RADIUS dialog is complete. Figure 21-5 shows the pattern of connections involved in RADIUS.
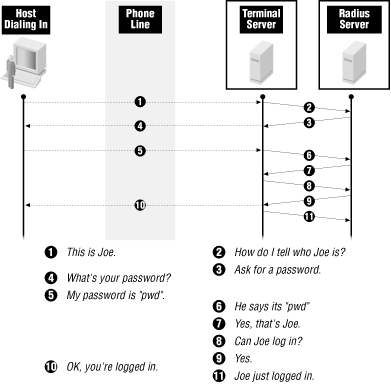
Figure 21-5. RADIUS connections
RADIUS encrypts password data but sends all other information unencrypted. This includes information about usernames and associated capabilities that you do not want hostile people to be able to read. RADIUS protects the data from tampering by including an authenticator that is an MD5 hash of the RADIUS data and a secret that is shared by the server and the client. (See Appendix C, "Cryptography", for more information about cryptographic hashing and MD5.) This provides integrity protection, client authentication, and server authentication.This system makes life difficult for proxying and network address translation systems. The RADIUS server has a different secret for each client, and it uses the source IP address of the RADIUS packet to choose which secret to add to the data before hashing. Similarly, if a client can talk to more than one server, it will use the source IP address to choose the secret to put into the hash at its end. This means that there must be a reliable one-to-one mapping between source IP addresses and RADIUS speakers; you cannot put multiple clients or servers behind the same proxy, or the server will not be able to tell them apart. For the same reason, you cannot put clients or servers behind a network address translation system unless they are statically mapped so that they will always appear with the same distinct source address.
21.7.1. Packet Filtering Characteristics of RADIUS
RADIUS authentication uses UDP port 1812, while accounting uses UDP port 1813. Early implementations of RADIUS used ports 1645 and 1646, but that usage is obsolete.| Direction | SourceAddr. | Dest.Addr. | Protocol | SourcePort | Dest.Port | ACKSet | Notes |
|---|---|---|---|---|---|---|---|
| In | Ext | Int | UDP | >1023 |
1812[139]
|
[140]
|
Authentication query, external client to internal RADIUS server |
| Out | Int | Ext | UDP | 1812[139] | >1023 | [140] | Authentication response, internal RADIUS server to external client |
| In | Ext | Int | UDP | >1023 |
1813[141]
|
[140] | Accounting notification, external client to internal RADIUS server |
| Out | Int | Ext | UDP | 1813[141] | >1023 | [140] | Accounting response, internal RADIUS server to external client. |
| Out | Int | Ext | UDP | >1023 | 1812[139] | [140] | Authentication query, internal client to external RADIUS server |
| In | Ext | Int | UDP | 1812[139] | >1023 | [140] | Authentication response, external RADIUS server to internal client |
| Out | Int | Ext | UDP | >1023 | 1813[141] | [140] | Accounting notification, internal client to external RADIUS server |
| In | Ext | Int | UDP | 1813[141] | >1023 | [140] | Accounting response, external RADIUS server to internal client. |
[139]Early implementations may use 1645.
[140]UDP has no ACK equivalent.
[141]Early implementations may use 1646.
21.7.2. Proxying Characteristics of RADIUS
There are numerous RADIUS proxy servers. However, the term is used to refer to two different kinds of server. One of them is a standard RADIUS server speaking to another authentication server (for instance, a RADIUS server that uses NIS or Windows NT domain authentication to determine whether or not users can actually be authenticated). The other is a RADIUS server that will actually route requests via RADIUS to other RADIUS servers.As we discussed earlier, the way that RADIUS authenticates clients and servers means that RADIUS will not work straightforwardly through generic proxy systems. RADIUS servers that do proxying do not pass the original authentication through; instead, the client and the proxy server authenticate each other, and then the proxy server recalculates the authenticator and separately authenticates to the next server. A generic proxy system cannot do this; if you need to proxy RADIUS, you should use a dedicated RADIUS proxy server.
21.7.3. Network Address Translation Characteristics of RADIUS
As mentioned, RADIUS uses source IP addresses as part of its authentication scheme and will not work if either the client or the server has a variable IP address. In order to use RADIUS through a network address translation system, you will need to set up static mappings, and make sure that the shared secret is assigned to the mapped address instead of the real address.


