|
|
6.2 File Attributes and PermissionsNow that we have a basic understanding of how filesystems work, we'll turn our attention to understanding how filesystems influence the security of a Unix system. Nearly all of this discussion will be concerned with the metadata that a filesystem contains—the filenames, permissions, timestamps, and access control attributes. 6.2.1 Exploring with the ls CommandYou can use the ls command to list all of the files in a directory. For instance, to list all the files in your current directory, type: % ls instructions invoice letter more-stuff notes stats % Actually, ls alone won't list all of the files. Files and directories beginning with a dot (".") are hidden from the ls command but are shown if you use ls -a: % ls -a . .. .indent instructions invoice letter notes more-stuff stats % The entries for "." and ".." refer to the current directory and its parent directory, respectively. The file .indent is a hidden file. If you use ls -A instead of ls -a, you'll see hidden files, but "." and ".." will not be shown. You can get a more detailed listing by using the ls -lF command: % ls -lF total 161 -rw-r--r-- 1 sian user 505 Feb 9 13:19 instructions -rw-r--r-- 1 sian user 3159 Feb 9 13:14 invoice -rw-r--r-- 1 sian user 6318 Feb 9 13:14 letter -rw------- 1 sian user 15897 Feb 9 13:20 more-stuff -rw-r----- 1 sian biochem 4320 Feb 9 13:20 notes -rwxr-xr-x 1 sian user 122880 Feb 9 13:26 stats* % The first line of output generated by the ls command (total 161 in the example above) indicates the number of KBs taken up by the files in the directory. Each of the other lines of output contains the fields, from left to right, as described in Table 6-2.
The ls -F option makes it easier for you to understand the listing by printing a special character after the filename to indicate what it is, as shown in Table 6-3.
Thus, in the directory shown earlier, the execute bit of the file stats is set; the rest of the files are regular files. The ls command has dozens of options. Because different people typically like to see different pieces of information when they list files, you may wish to read the manual page for the ls command that is on your system and then set up aliases so that you will have these options run by default when you type "ls." For instance, Spaf has an alias "lf" that runs ls with the options -FA, an alias "ll" that runs ls with the options -FAl, and "lb" that runs ls with the options -FAbx (the -b switch shows printable octal representations of nonprinting characters, and the -x switch sorts filenames across rows rather than down columns). 6.2.2 File TimesThe times shown with the ls -l command are the modification times of the file contents, frequently called the file's mtime. You can obtain the time of last access (the atime) by providing the -u option (for example, by typing ls -lu). These times are automatically updated by the Unix operating system. Knowing when a file was last modified or accessed can be important in many circumstances. For example, if a person has been using your account, you can look at the mtimes of files to infer which files the person modified. Unfortunately, the mtime and atime can't strictly be trusted, because they can be changed by the file's owner or the superuser by calling a function (utimes( )) within the Unix kernel. This function exists so that archive programs like tar and unzip can restore a file's modification time in addition to its contents. Additionally, the times reflect the system clock at the time of access or modification, so if the clock is incorrect or is changed, the times may not be accurate. Because a file's mtime and atime cannot be trusted, system administrators and security professionals need to be in the habit of checking the inode change time (ctime) using the ls -c option; for example, ls -lc. As with the mtime and the atime, the ctime is automatically updated by the operating system—in this case, whenever a change is made to the inode of the file. But unlike with mtime and atime, unprivileged users cannot change a file's ctime. The ctime reflects the time of last writing, protection change, or change of owner. An attacker may change the mtime or atime of a file, but the ctime will usually be correct. Note that we said "usually." A clever attacker who gains superuser status can change the system clock and then touch the inode to force a misleading ctime on a file. Furthermore, an attacker can change the ctime by writing to the raw disk device and bypassing the operating system checks altogether. And if you are using Linux with the ext2 filesystem, an attacker can modify the inode contents directly using the debugfs command. For this reason, if the superuser account on your system has been compromised, you should not assume that any of the three times stored with any file or directory are correct. 6.2.3 File PermissionsThe file permissions on each line of the ls listing tell you what the file is and what kind of file access (that is, the ability to read, write, or execute) is granted to various users on your system. Here are two examples of file permissions: -rw------- drwxr-xr-x The first character of the file's mode field indicates the type of file (described in Table 6-4).
The next nine characters taken in groups of three indicate who on your computer can do what with the file. There are three kinds of permissions:
Similarly, there are three classes of permissions:
In the ls -l command privileges are illustrated graphically (see Figure 6-2). Figure 6-2. Basic permissions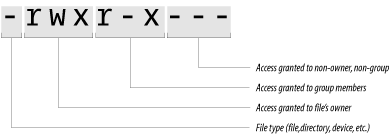 The terms read, write, and execute have very specific meanings for files, as shown in Table 6-5.
File permissions apply to devices, named sockets, and FIFOs exactly as they do for regular files. If you have write access, you can write information to the file or other object; if you have read access, you can read from it; and if you don't have either access, you're out of luck. File permissions do not apply to symbolic links. Whether you can read the contents of a file pointed to by a symbolic link depends on that file's permissions, not the link's. In fact, symbolic links are almost always created with a file permission of "rwxrwxrwx" (or mode 0777, as explained later in this chapter). These file permissions are then ignored by the operating system. Note the following facts about file permissions:
On Solaris systems, there may be an additional character following the permission characters: -rwx--x--x+ 3 spaf spaf 24219 May 17 00:52 example The + symbol indicates that this file (or other item) has an extended ACL associated with it. An Access Control List (ACL) provides a more comprehensive set of permissions on the file than can be described with the single user/single group model. ACLs are discussed later in this chapter. Because file permissions determine who can read and modify the information stored in your files, they are your primary method for protecting the data that you store on your Unix system. Most people think that file permissions are pretty basic stuff. Nevertheless, many Unix systems have had security breaches because their file permissions are not properly set, and several provide automated tools for checking the permissions of important system files on a regular basis.
6.2.3.1 A file permissions exampleConsider the directory listing presented earlier in this chapter: % ls -lF total 161 -rw-r--r-- 1 sian user 505 Feb 9 13:19 instructions -rw-r--r-- 1 sian user 3159 Feb 9 13:14 invoice -rw-r--r-- 1 sian user 6318 Feb 9 13:14 letter -rw------- 1 sian user 15897 Feb 9 13:20 more-stuff -rw-r----- 1 sian biochem 4320 Feb 9 13:20 notes -rwxr-xr-x 1 sian user 122880 Feb 9 13:26 stats* -------r-x 1 sian user 989987 Mar 6 08:13 weird-file % In this example, any user on the system can read the files instructions, invoice, letter, or stats because they all have the letter r in the "other" column of the permissions field. The file notes can be read only by user sian or by users who are in the biochem group. And only sian can read the information in the file more-stuff. A more interesting set of permissions is present on weird-file. User sian owns the file but cannot access it. Members of group user also are not allowed access. However, any user except sian and who is also not in the group user can read and execute the file.[6] Some variant of these permissions is useful in some cases where you want to make a file readable or executable by others, but you don't want to accidentally overwrite or execute it yourself. If you are the owner of the file and the permissions deny you access, it does not matter if you are in the group, or if other bits are set to allow the access.
Of course, the superuser can read any file on the system, and anybody who knows Sian's password can log in as sian and read her files (including weird-file, if sian changes the permissions first). 6.2.4 Directory PermissionsUnix stores the contents of directories in nodes that are similar to the nodes used for regular files, but they are specially marked so that they can be modified only by the operating system. As with other files, directories have a full complement of security attributes: owner, group, and permission bits. But because directories are interpreted in a special way by the filesystem, the permission bits have special meanings (see Table 6-6).
If you want to prevent other users from reading the contents of your files, you have two choices:
Note the following:
|
|
|
