For Ephemeral Diffie-Hellman encoding, the
server first sends either a RSA or a DSA public key. The server then
generates, signs, and sends the Diffie-Hellman
(DH) parameters and the DH public value.
The DH parameters that are sent are generated or read from a file.
The location of that file is defined with this
DHParameters option:
O DHParameters=param 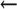 configuration file (V8.11 and later)
-ODHParameters=param
configuration file (V8.11 and later)
-ODHParameters=param 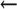 command line (V8.11 and later)
define(`confDH_PARAMETERS',`param')
command line (V8.11 and later)
define(`confDH_PARAMETERS',`param') 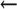 mc configuration (V8.11 and later)
mc configuration (V8.11 and later)
Here, param is one of the items shown in
Table 24-17. Note that only the first character is
examined, so 5 and 512 are
equivalent. Also note that the default is 1024 for the server, and
512 for the client.
Table 24-17. DHParameters parameter items
|
none
|
No parameters, so don't use DH
|
|
512
|
Generate 512-bit fixed parameters
|
|
1024
|
Generate 1024-bit fixed parameters
|
|
/path/file
|
Read the parameters from a file
|
If you list the /path/file item, the file
referenced must live in a safe path, one that is writable only by
root.
If you use an item that is not in the table, one of the following
errors will print and be logged, depending on whether
sendmail is in the role of a client or server:
STARTTLS=client, error: illegal value 'bad item' for DHParam
STARTTLS=server, error: illegal value 'bad item' for DHParam
This option should be defined only if a cipher suite containing
DSA/DH is used. Otherwise, you should leave it undefined.
The DHParameters option is not safe. If specified
from the command line, it can cause sendmail to
relinquish its special privileges.