STARTTLS and stream encryption are discussed in detail in Section 10.10. Among the items you must provide is a
directory that contains the certificate of the authority for the
server (ServerCertFile) and client (ClientCertFile), as well as other certificates of authority
you wish to trust. This directory contains both the certificates of
authority and hashes of those certificates (more about this soon).
The location of the CA certificate directory is specified with this
CACertPath option, with declarations that look
like this:
O CACertPath=dir 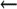 configuration file (V8.12 and later)
-OCACertPath=dir
configuration file (V8.12 and later)
-OCACertPath=dir 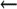 command line (V8.12 and later)
define(`confCACERT_PATH',`dir')
command line (V8.12 and later)
define(`confCACERT_PATH',`dir')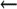 mc configuration (V8.12 and later
mc configuration (V8.12 and later
Here, dir is a full path specification of
the directory containing the CA certificate files and their hashes.
The dir can contain
sendmail macros, and if so, those macros will be
expanded (their values used) when the configuration file, or command
line, is read:
define(`confCACERT_PATH', `${MyCERTPath}')
The dir must be a full pathname (must
begin with a slash), or the directory will be rejected and the
following error logged:
STARTTLS=server: file dir unsafe: reason
STARTTLS=client: file dir unsafe: reason
Here, dir is the directory specified by
the CACertPath option (CACertPath), and path is the file
specified by this option. The num is the error
number returned by the ssl(8) software.
The dir must contain the hashes of each
certificate of authority, where each hash is either a file, or a link
to the certificate. Symbolic links can be generated with a command
such as the following:
% ln -s cert_file `openssl x509 -noout -hash < cert_file`.0
The CACertFile option is not safe. If specified
from the command line, it can cause sendmail to
relinquish its special privileges.