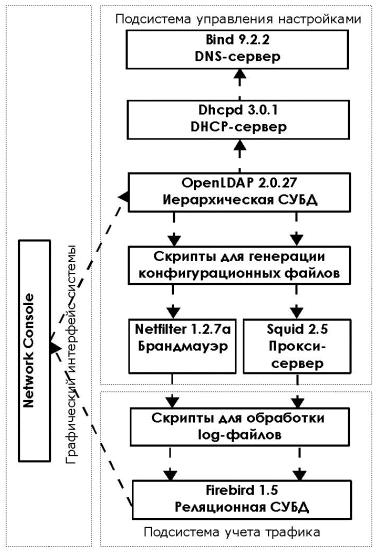

# Включение необходимых схем. В каждой схеме описан набор классов
и их атрибутов.
# В дереве LDAP могут присутствовать только такие записи, которые
являются экземлярами
# классов, описанных в схемах, и удовлетворяют ограничениям этих классов
include /etc/openldap/schema/core.schema
include /etc/openldap/schema/cosine.schema
include /etc/openldap/schema/inetorgperson.schema
include /etc/openldap/schema/misc.schema
include /etc/openldap/schema/nis.schema
include /etc/openldap/schema/openldap.schema
# pid-файл и файл с аргументами запуска
pidfile
/var/run/slapd.pid
argsfile /var/run/slapd.args
# Права доступа к дереву LDAP
access to attr=userPassword
by users write
by anonymous auth
by * none
access to *
by users write
by anonymous read
by * none
# Используемый backend для хранения дерева
database ldbm
# Суффикс дерева
suffix
"dc=myserver,dc=myprovider,dc=ru"
# Администратор дерева
rootdn
"cn=manager,dc=myserver,dc=myprovider,dc=ru"
# Пароль администратора. Желательно хранить его не в открытом виде,
# а генерировать с помощью slappasswd
rootpw secret
# Каталог для хранения дерева
directory /var/lib/ldap/bases
# Уровень отладки
loglevel 0# Индексы для ускорения поиска в дереве
index objectClass eq# Включение необходимых схем. В каждой схеме описан набор классов
и их атрибутов.
# В дереве LDAP могут присутствовать только такие записи, которые
являются экземлярами
# классов, описанных в схемах, и удовлетворяют ограничениям этих классов
include /etc/openldap/schema/core.schema
include /etc/openldap/schema/cosine.schema
include /etc/openldap/schema/inetorgperson.schema
include /etc/openldap/schema/misc.schema
include /etc/openldap/schema/nis.schema
include /etc/openldap/schema/openldap.schema
# Включение схемы для хранения
настроек DHCP в LDAP
include
/etc/openldap/schema/dhcp.schema
# pid-файл и файл с аргументами запуска
pidfile
/var/run/slapd.pid
argsfile /var/run/slapd.args
...
# Индексы для ускорения поиска в дереве
index objectClass eq
#Индексы для DHCP
index dhcpHWAddress eq
index dhcpClassData
eq
dn: dc=myserver, dc=myprovider, dc=ru
objectClass: top
objectClass: dhcpServer
cn: myserver.myprovider.ru
dhcpServiceDN: cn=Network, dc=myserver, dc=myprovider, dc=ru
dn: cn=Network, dc=myserver, dc=myprovider, dc=ru
cn: Network
objectClass: top
objectClass: dhcpService
objectClass: dhcpOptions
dhcpPrimaryDN: cn=myserver.myprovider.ru, dc=myserver, dc=myprovider,
dc=ru
dhcpOption: domain-name "myserver.myprovider.ru"
dhcpOption: domain-name-servers 192.168.1.1
dhcpOption: time-offset -5
dhcpOption: ntp-servers 192.168.1.1
dhcpStatements: default-lease-time 21600
dhcpStatements: max-lease-time 43200
dhcpStatements: ddns-update-style ad-hoc
dn: cn=192.168.1.0, cn=Network, dc=myserver, dc=myprovider, dc=ru
cn: 192.168.1.0
objectClass: top
objectClass: dhcpSubnet
objectClass: dhcpOptions
dhcpNetMask: 24
dhcpOption: routers 192.168.1.1
dhcpOption: subnet-mask 255.255.255.0
dn: cn=host1, cn=192.168.1.0, cn=Network, dc=myserver, dc=myprovider,
dc=ru
cn: host1
objectClass: top
objectClass: dhcpHost
dhcpHWAddress: ethernet 00:c0:26:31:6a:13
dhcpStatements: fixed-address 192.168.1.11
dn: cn=host2, cn=192.168.1.0, cn=Network, dc=myserver, dc=myprovider,
dc=ru
cn: host2
objectClass: top
objectClass: dhcpHost
dhcpHWAddress: ethernet 00:c0:26:31:6a:14
dhcpStatements: fixed-address 192.168.1.12ldapadd -h 127.0.0.1 -x -D
"cn=manager,dc=myserver,dc=myprovider,dc=ru" -w "secret" -f dhcpd.ldifldapsearch -h 127.0.0.1 -LLL -b
"dc=myserver,dc=myprovider,dc=ru" -D
"cn=manager,dc=myserver,dc=myprovider,dc=ru" -w "secret"ldap-server "localhost";
ldap-port 389;
ldap-username "cn=manager,dc=myserver,dc=myprovider,dc=ru";
ldap-password "secret";
ldap-base-dn "dc=myserver,dc=myprovider,dc=ru";
ldap-method static;dn: cn=Network, dc=myserver, dc=myprovider, dc=ru
changetype: modify
replace: dhcpStatements
dhcpStatements: default-lease-time 21600
dhcpStatements: max-lease-time 43200
dhcpStatements: ddns-update-style interim
dhcpStatements: ddns-updates on
dhcpStatements: ddns-domainname "myserver.myprovider.ru"
dhcpStatements: ddns-rev-domainname "in-addr.arpa"
dhcpStatements: update-static-leases on
dhcpStatements: key DHCP_UPDATE { algorithm HMAC-MD5.SIG-ALG.REG.INT;
secret "WOfB3kj8IhJK4OZ5s3zHeQ=="
dhcpStatements: } zone myserver.myprovider.ru. { primary 192.168.1.1;
key DHCP_UPDATE
dhcpStatements: } zone 1.168.192.in-addr.arpa. { primary 192.168.1.1;
key DHCP_UPDATE
dhcpStatements: } #ldapmodify -h 127.0.0.1 -x -D
"cn=manager,dc=myserver,dc=myprovider,dc=ru" -w "secret" -f
dhcpd-ddns-add.ldif
$ ldapsearch -h 127.0.0.1 -LLL -b
"dc=myserver,dc=myprovider,dc=ru" -D
"cn=manager,dc=myserver,dc=myprovider,dc=ru" -w "secret"
"objectClass=dhcpService"
dn: cn=Network, dc=myserver, dc=myprovider, dc=ru
cn: Network
objectClass: top
objectClass: dhcpService
objectClass: dhcpOptions
dhcpPrimaryDN: cn=myserver.myprovider.ru, dc=myserver, dc=myprovider,
dc=ru
dhcpOption: domain-name "myserver.myprovider.ru"
dhcpOption: domain-name-servers 192.168.1.1
dhcpOption: time-offset -5
dhcpOption: ntp-servers 192.168.1.1
dhcpStatements: default-lease-time 21600
dhcpStatements: max-lease-time 43200
dhcpStatements: ddns-update-style interim
dhcpStatements: ddns-updates on
dhcpStatements: ddns-domainname "myserver.myprovider.ru"
dhcpStatements: ddns-rev-domainname "in-addr.arpa"
dhcpStatements: update-static-leases on
dhcpStatements: key DHCP_UPDATE { algorithm HMAC-MD5.SIG-ALG.REG.INT;
secret "
WOfB3kj8IhJK4OZ5s3zHeQ=="
dhcpStatements: } zone myserver.myprovider.ru. { primary 192.168.1.1;
key DHCP
_UPDATE
dhcpStatements: } zone 1.168.192.in-addr.arpa. { primary 192.168.1.1;
key DHCP
_UPDATE
dhcpStatements: } #
# ls -l /var/lib/bind
total 2
drwx--x--- 2 root
named 48 Feb
12 2003 dev
drwx--x--- 2 root
named 328 Jul 11 14:11
etc
drwx--x--- 2 root
named 48 Feb
12 2003 var
drwx--x--- 2 root
named 344 Jul 11 14:23
zone
# ls -l /var/lib/bind/etc/
total 36
-rw-r----- 1 root
named 100 Apr 29 14:31
dhcp.key
-rw-r----- 1 root
named 182 Jul 11 14:00
local.conf
-rw-r----- 1 root
named 298 Jul 11 14:07
myserver.myprovider.conf
-rw-r----- 1 root
named 293 Apr 29 14:33
named.conf
-rw-r----- 1 root
named 447 Feb 10
2003 options.conf
-rw-r----- 1 root
named 564 Feb
9 2003 rfc1912.conf
-rw-r----- 1 root
named 1515 Feb 9
2003 rfc1918.conf
-rw-r----- 1 root
named 108 Feb
9 2003 rndc.conf
-rw-r----- 1 root
named 97 Jul 11
14:04 rndc.key
# cat /var/lib/bind/etc/named.conf
// This is the primary configuration file for the BIND DNS server named.
//
// If you are just adding zones, please do that in
/var/lib/bind/etc/local.conf
include "/etc/options.conf";
include "/etc/rndc.conf";
include "/etc/dhcp.key";
include "/etc/rfc1912.conf";
include "/etc/local.conf";
# cat /var/lib/bind/etc/options.conf
options {
version "unknown";
directory "/zone";
pid-file "";
dump-file
"/var/run/named_dump.db";
statistics-file
"/var/run/named.stats";
/*
* Oftenly used
directives are listed below.
*/
/*
* For localhost
configuration, uncomment the listen-on directive below.
*/
// listen-on { 127.0.0.1; };
/*
* If forward directive
set to "only", the server will only query
* the forwarders.
*/
// forward only;
// forwarders { };
};
# cat /var/lib/bind/etc/dhcp.key
key DHCP_UPDATE {
algorithm HMAC-MD5.SIG-ALG.REG.INT;
secret "WOfB3kj8IhJK4OZ5s3zHeQ==";
};
# cat /var/lib/bind/etc/local.conf
// Consider adding the 1918 zones here, if they are not used in your
organization.
// include "/etc/rfc1918.conf";
// Add other zones here
include "/etc/myserver.myprovider.conf";
# cat /var/lib/bind/etc/myserver.myprovider.conf
zone "myserver.myprovider.ru" {
type master;
file "myserver.myprovider.ru";
forwarders {};
allow-update { key DHCP_UPDATE; };
};
zone "1.168.192.in-addr.arpa" {
type master;
file "1.168.192.in-addr.arpa";
forwarders {};
allow-update { key DHCP_UPDATE; };
};
# ls -l /var/lib/bind/zone/
total 32
-rw-r----- 1 root
named 433 Jul 11 14:49
1.168.192.in-addr.arpa
-rw-r----- 1 root
named 212 Feb
9 2003 127.in-addr.arpa
-rw-r----- 1 root
named 309 Feb
9 2003 empty
-rw-r----- 1 root
named 208 Feb 12
2003 localdomain
-rw-r----- 1 root
named 178 Jan 13
2003 localhost
-rw-r----- 1 root
named 561 Jul 11 14:49
myserver.myprovider.ru
# cat /var/lib/bind/zone/1.168.192.in-addr.arpa
$TTL
1D
@
IN SOA
myserver.myprovider.ru. root.myserver.myprovider.ru. (
2003050603 ; serial
12H
; refresh
1H
; retry
1W
; expire
1H
; ncache
)
IN NS
myserver.myprovider.ru.
1
IN PTR
myserver.myprovider.ru.
# cat /var/lib/bind/zone/myserver.myprovider.ru
$TTL
1D
@
IN SOA
ns.myserver.myprovider.ru. root.myserver.myprovider.ru. (
2003102202 ; serial
12H
; refresh
1H
; retry
1W
; expire
1H
; ncache
)
IN
NS ns.myserver.myprovider.ru.
IN
MX 10 mail.myserver.myprovider.ru.
@
IN
A 192.168.1.1
ns
IN
A 192.168.1.1
mail
IN
A 192.168.1.1dnssec-keygen -a HMAC-MD5 -b 128 -n USER DHCP_UPDATEJul 11 14:23:53 myserver named[3515]: client 192.168.1.1#32770:
updating zone 'myserver.myprovider.ru/IN': adding an RR
Jul 11 14:23:53 myserver named[3515]: client 192.168.1.1#32770:
updating zone 'myserver.myprovider.ru/IN': adding an RR
Jul 11 14:23:53 myserver named[3515]: journal file
myserver.myprovider.ru.jnl does not exist, creating it
Jul 11 14:23:53 myserver dhcpd: Added new forward map from
host1.myserver.myprovider.ru to 192.168.1.11
Jul 11 14:23:53 myserver named[3515]: client 192.168.1.1#32770:
updating zone '1.168.192.in-addr.arpa/IN': deleting an rrset
Jul 11 14:23:53 myserver named[3515]: client 192.168.1.1#32770:
updating zone '1.168.192.in-addr.arpa/IN': adding an RR
Jul 11 14:23:53 myserver named[3515]: journal file
1.168.192.in-addr.arpa.jnl does not exist, creating it
Jul 11 14:23:53 myserver dhcpd: added reverse map from
11.1.168.192.in-addr.arpa to host1.myserver.myprovider.ru
Jul 11 14:23:53 myserver dhcpd: DHCPREQUEST for 192.168.1.11 from
00:c0:26:31:6a:13 via eth0
Jul 11 14:23:53 myserver dhcpd: DHCPACK on 192.168.1.11 to
00:c0:26:31:6a:13 via eth0attributetype ( 1.1.2.1.1.1 NAME 'allowNat'
DESC 'allow use NAT'
EQUALITY booleanMatch
SYNTAX
1.3.6.1.4.1.1466.115.121.1.7 SINGLE-VALUE )
attributetype ( 1.1.2.1.1.2 NAME 'allowProxy'
DESC 'allow use proxy'
EQUALITY booleanMatch
SYNTAX
1.3.6.1.4.1.1466.115.121.1.7 SINGLE-VALUE )
attributetype ( 1.1.2.1.1.3 NAME 'forceProxy'
DESC 'force use proxy'
EQUALITY booleanMatch
SYNTAX
1.3.6.1.4.1.1466.115.121.1.7 SINGLE-VALUE )
objectclass ( 1.1.2.2.1.1 NAME 'internetAccess' SUP top STRUCTURAL
DESC 'internet access rules'
MUST ( allowNat $ allowProxy
$ forceProxy ))...
# Включение схемы для хранения
настроек DHCP в LDAP
include
/etc/openldap/schema/dhcp.schema
# Включение схемы для хранения
настроек Squid и IPTables
include
/etc/openldap/schema/internet-access.schema
# pid-файл и файл с аргументами запуска
pidfile
/var/run/slapd.pid
argsfile /var/run/slapd.args
...
dn: cn=host1, cn=192.168.1.0, cn=Network, dc=myserver, dc=myprovider,
dc=ru
changetype: modify
add: objectClass
objectClass: internetAccess
-
replace: allowNat
allowNat: TRUE
-
replace: allowProxy
allowProxy: TRUE
-
replace: forceProxy
forceProxy: TRUE
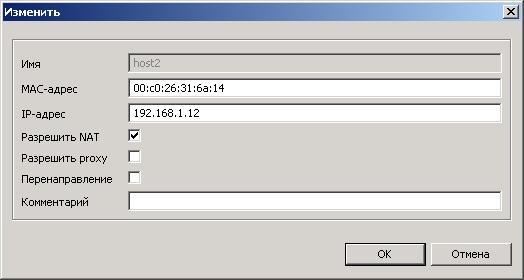
dn: cn=host2, cn=192.168.1.0, cn=Network, dc=myserver, dc=myprovider,
dc=ru
changetype: modify
add: objectClass
objectClass: internetAccess
-
replace: allowNat
allowNat: TRUE
-
replace: allowProxy
allowProxy: FALSE
-
replace: forceProxy
forceProxy: FALSE
ldapmodify -h 127.0.0.1 -x -D
"cn=manager,dc=myserver,dc=myprovider,dc=ru" -w "secret" -f
internet-access.ldif#!/bin/bash
ldapsearch -h 127.0.0.1 -LLL -b "dc=myserver,dc=myprovider,dc=ru" -D
"cn=manager,dc=myserver,dc=myprovider,dc=ru" -w "secret"
"(&(objectClass=internetAccess) ("$1"=TRUE))" | grep fixed-address
| awk '{print $3}'
# /opt/scripts/make_ldap_filter.sh allowProxy
192.168.1.11
#!/bin/sh
################################################################################
EXTERNAL_DEVICE="ppp0"
INTERNAL_DEVICE="eth0"
INTERNAL_ADDRESS="192.168.1.1"
IPTABLES="/sbin/iptables"
################################################################################
# Обнуляем таблицы
$IPTABLES -F
$IPTABLES -X
$IPTABLES -t nat -F
$IPTABLES -t nat -X
# Устанавливаем правила по умолчанию для тех пакетов,
# про которые мы случайно забудем при написании правил ;)
$IPTABLES -P INPUT DROP
$IPTABLES -P OUTPUT ACCEPT
$IPTABLES -P FORWARD DROP
# Создаем конечные цепочки для регистрации пакетов
# подробнее об этом в разделе 2.2.3
$IPTABLES -N allowed
$IPTABLES -A allowed -j ULOG --ulog-nlgroup 1 --ulog-qthreshold 50
--ulog-prefix allow
$IPTABLES -A allowed -j ACCEPT
$IPTABLES -N rejected
$IPTABLES -A rejected -j ULOG --ulog-nlgroup 1 --ulog-qthreshold 50
--ulog-prefix drop
$IPTABLES -A rejected -j DROP
# Выпускаем все пакеты наружу без ограничений
$IPTABLES -A OUTPUT -j allowed
# Впускаем все пакеты, которые пришли не с внешнего интерфейса
$IPTABLES -A INPUT ! -i $EXTERNAL_DEVICE -j allowed
# Не впускаем TCP-пакеты, пришедшие с внешнего интерфейса,
# для которых статус установлен в NEW, но которые на самом деле
таковыми не являются
$IPTABLES -A INPUT -i $EXTERNAL_DEVICE -p TCP ! --syn -m state --state
NEW -j rejected
# Впускаем TCP-пакеты, пришедшие с внешнего интерфейса на порт 22
# и пытающиеся установить новое соединение (для ssh)
$IPTABLES -A INPUT -i $EXTERNAL_DEVICE -p TCP --syn --dport 22 -j
allowed
# Впускаем все TCP-пакеты, пришедшие с внешнего интерфейса, для которых
соединение уже установлено
$IPTABLES -A INPUT -i $EXTERNAL_DEVICE -p TCP -m state --state
ESTABLISHED,RELATED -j allowed
# Впускаем все UDP-пакеты, пришедшие с внешнего интерфейса, необходимые
для DNS
$IPTABLES -A INPUT -i $EXTERNAL_DEVICE -p UDP --dport 53 -j allowed
$IPTABLES -A INPUT -i $EXTERNAL_DEVICE -p UDP --sport 53 -j allowed
# Впускаем все UDP-пакеты, пришедшие с внешнего интерфейса, необходимые
для NTP
$IPTABLES -A INPUT -i $EXTERNAL_DEVICE -p UDP --dport 123 -j allowed
$IPTABLES -A INPUT -i $EXTERNAL_DEVICE -p UDP --sport 123 -j allowed
# Впускаем все ICMP-пакеты, пришедшие с внешнего интерфейса
$IPTABLES -A INPUT -i $EXTERNAL_DEVICE -p ICMP -j allowed
# Не впускаем все прочие пакеты, пришедшие с внешнего интерфейса
$IPTABLES -A INPUT -i $EXTERNAL_DEVICE -j rejected
# Добавляем правила для всех хостов, которым разрешено использовать NAT
for i in `/opt/scripts/make_ldap_filter.sh allowNat`
do
# Заменяем адреса пакетов
$IPTABLES -t nat -A POSTROUTING -o $EXTERNAL_DEVICE
-s $i -j MASQUERADE
# Выпускаем все пакеты наружу без ограничений
$IPTABLES -A FORWARD -i $INTERNAL_DEVICE -o
$EXTERNAL_DEVICE -s $i -j allowed
# Не впускаем TCP-пакеты, пришедшие с внешнего
интерфейса, пытающиеся установить новое соединение
$IPTABLES -A FORWARD -o $INTERNAL_DEVICE -i
$EXTERNAL_DEVICE -p TCP --syn -d $i -j rejected
# Не впускаем ICMP-пакеты с типом 8 (request),
пришедшие с внешнего интерфейса
$IPTABLES -A FORWARD -o $INTERNAL_DEVICE -i
$EXTERNAL_DEVICE -p ICMP --icmp-type 8 -d $i -j rejected
# Впускаем все прочие пакеты
$IPTABLES -A FORWARD -o $INTERNAL_DEVICE -i
$EXTERNAL_DEVICE -d $i -j allowed
done
# Добавляем правила для всех хостов, которым разрешено использовать
прокси-сервер в прозрачном режиме
for i in `/opt/scripts/make_ldap_filter.sh forceProxy`
do
# Заворачиваем HTTP-запросы на прокси-сервер
$IPTABLES -t nat -A PREROUTING -s $i -p TCP --dport
80 -j REDIRECT --to-port 3128
done
#!/bin/sh
/opt/scripts/make_ldap_filter.sh allowProxy >
/etc/squid/allowed_hosts
hierarchy_stoplist cgi-bin ?
acl QUERY urlpath_regex cgi-bin \?
no_cache deny QUERY
auth_param basic children 5
auth_param basic realm Squid proxy-caching web server
auth_param basic credentialsttl 2 hours
refresh_pattern
^ftp:
1440 20% 10080
refresh_pattern ^gopher:
1440 0% 1440
refresh_pattern
.
0 20% 4320
acl all src 0.0.0.0/0.0.0.0
acl manager proto cache_object
acl localhost src 127.0.0.1/255.255.255.255
acl to_localhost dst 127.0.0.0/8
acl SSL_ports port 443 563
acl Jabber_ports port 5222
acl Safe_ports port
80 # http
acl Safe_ports port
21 # ftp
acl Safe_ports port 443 563 # https, snews
acl Safe_ports port
70 # gopher
acl Safe_ports port 210
# wais
acl Safe_ports port 1025-65535 # unregistered ports
acl Safe_ports port 280
# http-mgmt
acl Safe_ports port 488
# gss-http
acl Safe_ports port 591
# filemaker
acl Safe_ports port 777
# multiling http
acl CONNECT method CONNECT
http_access allow manager localhost
http_access deny manager
http_access deny !Safe_ports
http_access deny CONNECT !SSL_ports !Jabber_ports
acl allowed_hosts src "/etc/squid/allowed_hosts"
http_access allow allowed_hosts
http_access allow localhost
http_access deny all
http_reply_access allow all
icp_access allow all
httpd_accel_host virtual
httpd_accel_with_proxy on
httpd_accel_uses_host_header on
error_directory /usr/share/squid/errors/Russian-koi8-r
coredump_dir /var/spool/squid
visible_hostname myserver.myprovider.ru...
# Индексы для ускорения поиска в дереве
index objectClass eq
#Индексы для DHCP
index dhcpHWAddress eq
index dhcpClassData
eq
# Индексы для авторизации
index cn, uid, uidNumber, gidNumber eqdn: cn=Users, dc=myserver, dc=myprovider, dc=ru
objectClass: top
dn: cn=ldapuser1, cn=Users, dc=myserver, dc=myprovider, dc=ru
objectClass: posixAccount
cn: LDAP User 1
uid: ldapuser1
uidNumber: 1001
gidNumber: 10
homeDirectory: /home/ldapuser1
loginShell: /bin/bash
dn: cn=ldapuser2, cn=Users, dc=myserver, dc=myprovider, dc=ru
objectClass: posixAccount
cn: LDAP User 2
uid: ldapuser2
uidNumber: 1002
gidNumber: 10
homeDirectory: /home/ldapuser2
loginShell: /bin/bash
ldapadd -h 127.0.0.1 -x -D
"cn=manager,dc=myserver,dc=myprovider,dc=ru" -w "secret" -f users.ldif
После этого нужно установить pam_ldap и nss_ldap (apt-get
install pam_ldap
nss_ldap в ALT Linux) и отредактировать следующие файлы по образцу:passwd: files ldap nisplus nis
shadow: tcb files ldap nisplus nis
group: files ldap nisplus nis
hosts: files nisplus nis dns
ethers: files
netmasks: files
networks: files
protocols: files
rpc: files
services: files
bootparams: nisplus [NOTFOUND=return] files
netgroup: nisplus
publickey: nisplus
automount: files nisplus
aliases: files nisplushost 127.0.0.1
base dc=myserver,dc=myprovider,dc=ru
rootbinddn cn=manager,dc=myserver,dc=myprovider,dc=rusecretauth
sufficient /lib/security/pam_ldap.so
auth
required
/lib/security/pam_tcb.so shadow fork prefix=a$ count=8 nullok
use_first_pass
account
sufficient /lib/security/pam_ldap.so
account
required
/lib/security/pam_tcb.so shadow fork
password
sufficient /lib/security/pam_ldap.so
password
required
/lib/security/pam_passwdqc.so min=disabled,24,12,8,7 max=40
passphrase=3 match=4 similar=deny random=42 enforce=users retry=3
password
required
/lib/security/pam_tcb.so use_authtok shadow fork prefix=a$ count=8
write_to=tcb
session
required
/lib/security/pam_tcb.so
session
required
/lib/security/pam_limits.so
session
required
/lib/security/pam_mkhomedir.so skel=/etc/skel/ umask=0077auth
sufficient /lib/security/pam_ldap.so
use_first_pass
auth
required
/lib/security/pam_tcb.so shadow fork prefix=a$ count=8 nullok
use_first_pass
password
sufficient /lib/security/pam_ldap.so
password
required
/lib/security/pam_tcb.so use_authtok shadow fork prefix=a$ count=8
write_to=tcb# id ldapuser1
uid=1001(ldapuser1) gid=10(wheel) groups=10(wheel)
# passwd ldapuser1
passwd: updating all authentication tokens for user ldapuser1.
New password:
Re-enter new password:
LDAP password information changed for ldapuser1
passwd: all authentication tokens updated successfully.
$ su - ldapuser1
Password:
Creating directory '/home/ldapuser1'.
Creating directory '/home/ldapuser1/tmp'.
Creating directory '/home/ldapuser1/Documents'.
Creating directory '/home/ldapuser1/.mutt'.
Creating directory '/home/ldapuser1/.mutt/color.default'.
Creating directory '/home/ldapuser1/.xsession.d'.
$ ssh ldapuser1@localhost
ldapuser1@localhost's password:
Last login: Tue Apr 20 10:38:21 2004 from localhost.localdomain
$
2.1.6. Хранение в OpenLDAP
произвольной
справочной информации
attributetype ( 1.1.2.1.2.1 NAME 'comment'
DESC 'Host comment'
EQUALITY caseIgnoreMatch
SYNTAX
1.3.6.1.4.1.1466.115.121.1.15{256} )
objectclass ( 1.1.2.2.1.2 NAME 'hostsInfo' SUP top STRUCTURAL
DESC 'Hosts additional info'
MAY ( comment ))# В дереве LDAP могут присутствовать только такие записи, которые
являются экземлярами
# классов, описанных в схемах, и удовлетворяют ограничениям этих классов
include /etc/openldap/schema/core.schema
include /etc/openldap/schema/cosine.schema
include /etc/openldap/schema/inetorgperson.schema
include /etc/openldap/schema/misc.schema
include /etc/openldap/schema/nis.schema
include /etc/openldap/schema/openldap.schema
# Включение схемы для хранения настроек DHCP в LDAP
include /etc/openldap/schema/dhcp.schema
# Включение схемы для хранения настроек Squid и IPTables
include /etc/openldap/schema/internet-access.schema
# Включение схемы для хранения
справочной информации о хостах
include
/etc/openldap/schema/info.schema
# pid-файл и файл с аргументами запуска
pidfile
/var/run/slapd.pid
argsfile /var/run/slapd.args
...
dn: cn=host1, cn=192.168.1.0, cn=Network, dc=myserver, dc=myprovider,
dc=ru
changetype: modify
add: objectClass
objectClass: hostsInfo
dn: cn=host2, cn=192.168.1.0, cn=Network, dc=myserver, dc=myprovider,
dc=ru
changetype: modify
add: objectClass
objectClass: hostsInfoldapmodify -h 127.0.0.1 -x -D
"cn=manager,dc=myserver,dc=myprovider,dc=ru" -w "secret" -f info.ldif$ ldapsearch -h 127.0.0.1 -LLL -b
"dc=myserver,dc=myprovider,dc=ru" -D
"cn=manager,dc=myserver,dc=myprovider,dc=ru" -w "secret"
dn: dc=myserver, dc=myprovider, dc=ru
objectClass: top
objectClass: dhcpServer
cn: myserver.myprovider.ru
dhcpServiceDN: cn=Network, dc=myserver, dc=myprovider, dc=ru
dn: cn=Network, dc=myserver, dc=myprovider, dc=ru
cn: Network
objectClass: top
objectClass: dhcpService
objectClass: dhcpOptions
dhcpPrimaryDN: cn=myserver.myprovider.ru, dc=myserver, dc=myprovider,
dc=ru
dhcpOption: domain-name "myserver.myprovider.ru"
dhcpOption: domain-name-servers 192.168.1.1
dhcpOption: time-offset -5
dhcpOption: ntp-servers 192.168.1.1
dhcpStatements: default-lease-time 21600
dhcpStatements: max-lease-time 43200
dhcpStatements: ddns-update-style interim
dhcpStatements: ddns-updates on
dhcpStatements: ddns-domainname "myserver.myprovider.ru"
dhcpStatements: ddns-rev-domainname "in-addr.arpa"
dhcpStatements: update-static-leases on
dhcpStatements: key DHCP_UPDATE { algorithm HMAC-MD5.SIG-ALG.REG.INT;
secret "
WOfB3kj8IhJK4OZ5s3zHeQ=="
dhcpStatements: } zone myserver.myprovider.ru. { primary 192.168.1.1;
key DHCP
_UPDATE
dhcpStatements: } zone 1.168.192.in-addr.arpa. { primary 192.168.1.1;
key DHCP
_UPDATE
dhcpStatements: } #
dn: cn=192.168.1.0, cn=Network, dc=myserver, dc=myprovider, dc=ru
cn: 192.168.1.0
objectClass: top
objectClass: dhcpSubnet
objectClass: dhcpOptions
dhcpNetMask: 24
dhcpOption: routers 192.168.1.1
dhcpOption: subnet-mask 255.255.255.0
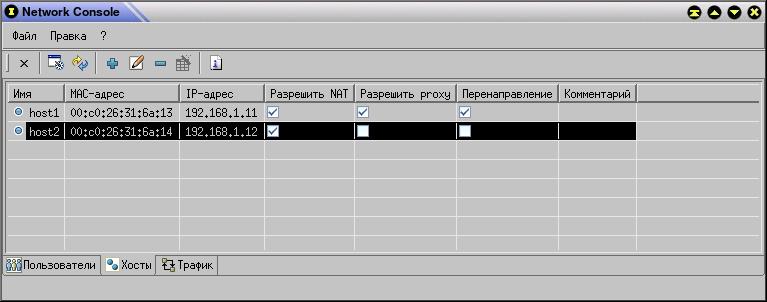
dn: cn=host1, cn=192.168.1.0, cn=Network, dc=myserver, dc=myprovider,
dc=ru
cn: host1
objectClass: top
objectClass: dhcpHost
objectClass: internetAccess
objectClass: hostsInfo
dhcpHWAddress: ethernet 00:c0:26:31:6a:13
dhcpStatements: fixed-address 192.168.1.11
allowNat: TRUE
allowProxy: TRUE
forceProxy: TRUE
dn: cn=host2, cn=192.168.1.0, cn=Network, dc=myserver, dc=myprovider,
dc=ru
cn: host2
objectClass: top
objectClass: dhcpHost
objectClass: internetAccess
objectClass: hostsInfo
dhcpHWAddress: ethernet 00:c0:26:31:6a:14
dhcpStatements: fixed-address 192.168.1.12
allowNat: TRUE
allowProxy: FALSE
forceProxy: FALSE
dn: cn=Users, dc=myserver, dc=myprovider, dc=ru
objectClass: top
dn: cn=ldapuser1, cn=Users, dc=myserver, dc=myprovider, dc=ru
objectClass: posixAccount
cn: LDAP User 1
uid: ldapuser1
uidNumber: 1001
gidNumber: 10
homeDirectory: /home/ldapuser1
loginShell: /bin/bash
userPassword:: MQ==
dn: cn=ldapuser2, cn=Users, dc=myserver, dc=myprovider, dc=ru
objectClass: posixAccount
cn: LDAP User 2
uid: ldapuser2
uidNumber: 1002
gidNumber: 10
homeDirectory: /home/ldapuser2
loginShell: /bin/bash
#!/bin/bash
echo "Apply DHCP settings ..."
service dhcpd restart
echo "Apply Firewall settings ..."
/opt/scripts/make_iptables.sh
service iptables save
echo "Apply Proxy settings ..."
/opt/scripts/make_squid.sh
service squid restartSET SQL DIALECT 3;
CREATE DATABASE 'localhost:billing' USER 'sysdba' PASSWORD 'masterkey';
/* Таблица для хранения данных о трафике, прошедшем через прокси-сервер */
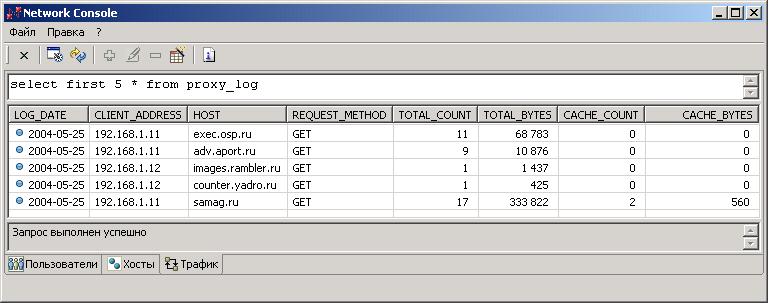
CREATE TABLE PROXY_LOG (LOG_DATE DATE, /* дата */
CLIENT_ADDRESS VARCHAR(256), /* адрес рабочей станции */
HOST VARCHAR(255), /* адрес сервера, на который отправлен HTTP-запрос */
REQUEST_METHOD VARCHAR(10), /* тип HTTP-запроса */
TOTAL_COUNT BIGINT, /* общее количество запросов */
TOTAL_BYTES BIGINT, /* общее количество запрошенных байт */
CACHE_COUNT BIGINT, /* количество запросов, для ответа на которые был использован кэш прокси-сервера */
CACHE_BYTES BIGINT); /* количество байт, взятых из кэша */
/* Таблица для хранения данных о трафике, прошедшем через NAT */
CREATE TABLE TRANSFER_LOG (LOG_DATE DATE, /* дата */
PROTOCOL SMALLINT, /* номер протокола (из /etc/protocols) */
SOURCE VARCHAR(15), /* отправитель пакета */
SOURCE_PORT INTEGER, /* порт отправителя */
DESTINATION VARCHAR(15), /* получатель пакета */
DESTINATION_PORT INTEGER, /* порт получателя */
INCOMING VARCHAR(4), /* входящий интерфейс */
OUTGOING VARCHAR(4), /* исходящий интерфейс */
PREFIX VARCHAR(25), /* префикс из ULOG */
PACKETS BIGINT, /* количество пакетов */
BYTES BIGINT); /* количество байт */
COMMIT WORK;
CREATE INDEX PROXY_LOG_DATE ON PROXY_LOG(LOG_DATE);
CREATE INDEX TRANSFER_LOG_DATE ON TRANSFER_LOG(LOG_DATE);
CREATE INDEX TRANSFER_LOG_DESTINATION ON TRANSFER_LOG(DESTINATION);
CREATE INDEX TRANSFER_LOG_DESTINATION_PORT ON TRANSFER_LOG(DESTINATION_PORT);
CREATE INDEX TRANSFER_LOG_INCOMING ON TRANSFER_LOG(INCOMING);
CREATE INDEX TRANSFER_LOG_OUTGOING ON TRANSFER_LOG(OUTGOING);
CREATE INDEX TRANSFER_LOG_PREFIX ON TRANSFER_LOG(PREFIX);
CREATE INDEX TRANSFER_LOG_SOURCE ON TRANSFER_LOG(SOURCE);
CREATE INDEX TRANSFER_LOG_SOURCE_PORT ON TRANSFER_LOG(SOURCE_PORT);
COMMIT WORK;
GRANT SELECT ON PROXY_LOG TO USER OPERATOR;
GRANT SELECT ON TRANSFER_LOG TO USER OPERATOR;
COMMIT WORK;
billing = /var/db/firebird/billing.fdb/opt/firebird/bin/isql -i metadata.sql#!/usr/bin/perl
#
# Based on loganalyzer (Sergey N. Yatskevich <syatskevich@altlinux.ru>)
#
# Обработка лога Squid'а и запись результатов в таблицу proxy_log
#
# При обработке лога извлекается следующая информация :
# 1) время (с детализацией по дням) обращения
# 2) машина, с которой произошло обращение
# 3) хост, к которому произошло обращение (только доменное имя)
# 4) метод обращения (GET или POST)
# 5) Взят-ли объект из кэша или произошла его загрузка из сети
# 6) объем загруженной информации
#
# Интересует "объем информации"/"количество обращений" в разрезе
# 1, 2, 3, 4
#
use URI;
use DBI;
$dsn = "dbi:InterBase:dbname=billing;host=firebird;ib_dialect=3";
$user = "sysdba";
$passwd = "system";
sub parseLogLine
{
($time, $duration, $client_address, $result_codes, $bytes, $request_method, $url, $rfc931, $hierarhy_code, $type) = split (/\s+/);
# Пропускаем сообщения об ошибках выдаваемых Squid пользователям
# и запросы к самому Squid'у
if ($result_codes =~ /^NONE/ || $url =~ /^cache_object:/)
{
return ("SKIP_LINE", "", "", "", "", 0, 0);
}
# Squid не проставляет при типе соединения CONNECT (по крайней
# мере для ICQ) используемый протокол, что вызывает ошибку
# в пакете URI. Поэтому добавляем протокол сами.
if ($request_method eq "CONNECT" && $url !~ /^https:/i)
{
$url = "https://$url";
}
$uri = URI->new ($url);
$uri = $uri->canonical;
$host = $uri->host;
($day, $month, $year) = (localtime ($time)) [3, 4, 5];
$month++;
$year += 1900;
$hit = ($result_codes =~ /_HIT/) ? 1 : 0;
return ("INSERT", "$year/$month/$day", $client_address, lc $host, $request_method, $hit, $bytes);
}
while (<STDIN>)
{
($state, $date, $client_address, $host, $request_method, $hit, $bytes) = parseLogLine ($_);
if ($state eq "INSERT")
{
$total_count{"$date $client_address $host $request_method"} ++;
$total_bytes{"$date $client_address $host $request_method"} += $bytes;
if ($hit == 1)
{
$hit_count{"$date $client_address $host $request_method"} ++;
$hit_bytes{"$date $client_address $host $request_method"} += $bytes;
}
}
}
$dbh = DBI->connect ($dsn, $user, $passwd, {AutoCommit => 0});
$sth = $dbh->prepare ("INSERT INTO proxy_log VALUES (?, ?, ?, ?, ?, ?, ?, ?)");
foreach $key (keys %total_count)
{
if ($total_bytes{$key} > 0)
{
($date, $client_address, $host, $request_method) = split (/ /, $key);
($hcount, $hbytes) = (exists $hit_count{$key}) ? ($hit_count{$key}, $hit_bytes{$key}) : (0, 0);
$sth->execute ($date, $client_address, $host, $request_method, $total_count{$key}, $total_bytes{$key}, $hcount, $hbytes);
if ($sth->state)
{
$dbh->rollback;
$dbh->disconnect;
die "Ошибка вставки записи, откат в начальное состояние\n";
}
}
}
$dbh->commit;
$dbh->disconnect;
Для регулярной очистки файла access.log и загрузки его содежимого в
базу данных можно использовать мехнизм logrotate. В этом случае файл /etc/logrotate.d/squid
необходимо отредактировать следующим образом:/var/log/squid/access.log {
daily
rotate 7
copytruncate
compress
notifempty
missingok
prerotate
cd /opt/scripts
./translate_squid.pl <
/var/log/squid/access.log
endscript
}
/var/log/squid/cache.log {
daily
rotate 7
copytruncate
compress
notifempty
missingok
}
/var/log/squid/store.log {
daily
rotate 7
copytruncate
compress
notifempty
missingok
# This script asks squid to rotate its logs on its own.
# Restarting squid is a long process and it is not worth
# doing it just to rotate logs
postrotate
/usr/sbin/squid -k rotate
endscript
}multicast groups=1
accounting file=/var/log/ulog-acctd/account.log
dump file=/var/log/ulog-acctd/dump
debug file=/var/log/ulog-acctd/debug.log
pid file=/var/run/ulog-acctd.pid
debug = syscall, misc, statistics, error, error-packet
accounting format="%t\t%p\t%s\t%S\t%d\t%D\t%P\t%b\t%i\t%o\t%f\n"
empty interface="none"
empty prefix="none"
flush=30
fdelay=0#!/usr/bin/perl
#
# Based on loganalyzer (Sergey N. Yatskevich <syatskevich@altlinux.ru>)
#
# Обработка лога ulog-acctd и запись результатов в таблицу transfer_log
#
# При обработке лога извлекается следующая информация :
# 1) время (с детализацией по дням) обращения
# 2) протокол (1 - ICMP, 6 - TCP, 17 - UDP)
# 3) отправитель пакета
# 4) порт отправителя
# 5) адресат пакета
# 6) порт адресата
# 7) входящий интерфейс
# 8) исходящий интерфейс
# 9) префикс ulog-acctd
# 10) количество и размер пакетов
# Интересует "размер пакетов"/"количество пакетов" в разрезе
# 1, 2, 3, 4, 5, 6, 7, 8, 9
#
use DBI;
$dsn = "dbi:InterBase:dbname=billing;host=firebird;ib_dialect=3";
$user = "sysdba";
$passwd = "system";
sub parseLogLine
{
($time, $protocol, $source, $source_port, $destination, $destination_port, $packets, $bytes, $incoming, $outgoing, $prefix) = split (/\s+/);
($day, $month, $year) = (localtime ($time)) [3, 4, 5];
$month++;
$year += 1900;
return ("INSERT", "$year/$month/$day", $protocol, $source, $source_port, $destination, $destination_port, $packets, $bytes, $incoming, $outgoing, $prefix);
}
while (<STDIN>)
{
($state, $date, $protocol, $source, $source_port, $destination, $destination_port, $packets, $bytes, $incoming, $outgoing, $prefix) = parseLogLine ($_);
if ($state eq "INSERT")
{
$total_packets{"$date $protocol $source $source_port $destination $destination_port $incoming $outgoing $prefix"} ++;
$total_bytes{"$date $protocol $source $source_port $destination $destination_port $incoming $outgoing $prefix"} += $bytes;
}
}
$dbh = DBI->connect ($dsn, $user, $passwd, {AutoCommit => 0});
$sth = $dbh->prepare ("INSERT INTO transfer_log VALUES (?, ?, ?, ?, ?, ?, ?, ?, ?, ?, ?)");
foreach $key (keys %total_packets)
{
if ($total_bytes{$key} > 0)
{
($date, $protocol, $source, $source_port, $destination, $destination_port, $incoming, $outgoing, $prefix) = split (/ /, $key);
$sth->execute ($date, $protocol, $source, $source_port, $destination, $destination_port, $incoming, $outgoing, $prefix, $total_packets{$key}, $total_bytes{$key});
if ($sth->state)
{
$dbh->rollback;
$dbh->disconnect;
die "Ошибка вставки записи, откат в начальное состояние\n";
}
}
}
$dbh->commit;
$dbh->disconnect;
Для регулярной очистки файла account.log и загрузки его содежимого в
базу данных можно использовать мехнизм logrotate. В этом случае файл /etc/logrotate.d/ulog-acctd
необходимо отредактировать следующим образом:/var/log/ulog-acctd/account.log /var/log/ulog-acctd/debug.log {
weekly
rotate 5
copytruncate
compress
notifempty
missingok
sharedscripts
prerotate
if [ -e /var/run/ulog-acctd.pid ]; then kill -STOP `cat /var/run/ulog-acctd.pid`; fi
endscript
postrotate
if [ -e /var/run/ulog-acctd.pid ]; then kill -CONT `cat /var/run/ulog-acctd.pid`; fi
endscript
}
| Скрипт |
Назначение |
networkconsole-linux-gtk2.sh |
Скрипт для запуска Network
Console в Linux с использованием GTK2 |
networkconsole-linux-motif.sh |
Скрипт для запуска Network Console в Linux с использованием OpenMotif |
networkconsole-win32.bat |
Скрипт для запуска Network Console в Windows |
 |
 |
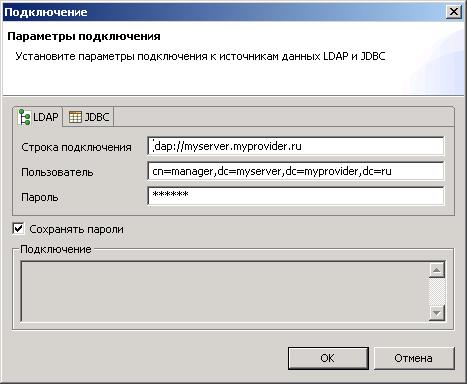
connection.ldap.context.hosts=cn\=192.168.1.0,cn\=Network,dc\=myserver,dc\=myprovider,dc\=ru
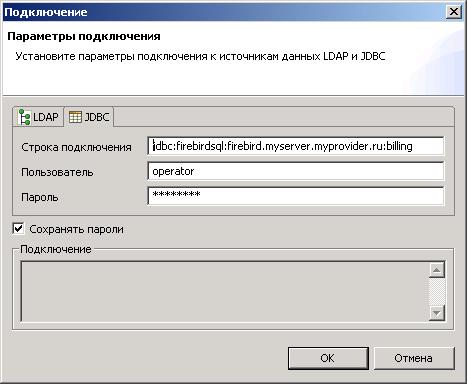
connection.ldap.context.users=cn\=Users,dc\=myserver,dc\=myprovider,dc\=ru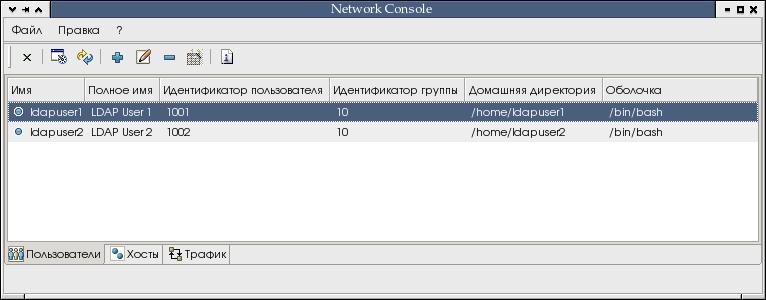
SET ECHO ON;
SET SQL DIALECT 3;
SET NAMES WIN1251;
CONNECT 'localhost:billing' USER 'sysdba' PASSWORD 'masterkey';
SET TERM ^ ;
CREATE PROCEDURE FULL_TRAFFIC (PERIOD_BEGIN DATE,
PERIOD_END DATE)
RETURNS (INCOMING_ALLOWED BIGINT,
INCOMING_REJECTED BIGINT,
OUTGOING BIGINT)
AS
begin
select sum(bytes) from transfer_log
where outgoing<>'ppp0' and incoming='ppp0' and prefix='allow'
and log_date>=:period_begin and log_date<=:period_end
into :incoming_allowed;
select sum(bytes) from transfer_log
where outgoing<>'ppp0' and incoming='ppp0' and prefix='drop'
and log_date>=:period_begin and log_date<=:period_end
into :incoming_rejected;
select sum(bytes) from transfer_log
where outgoing='ppp0' and incoming<>'ppp0'
and log_date>=:period_begin and log_date<=:period_end
into :outgoing;
suspend;
end ^
CREATE PROCEDURE NAT_TRAFFIC_BY_HOSTS (PERIOD_BEGIN DATE,
PERIOD_END DATE)
RETURNS (HOST VARCHAR(15) CHARACTER SET NONE,
INCOMING_ALLOWED BIGINT,
INCOMING_REJECTED BIGINT,
OUTGOING BIGINT)
AS
begin
for select destination, sum(bytes) from transfer_log
where outgoing='eth0' and incoming='ppp0' and prefix='allow'
and log_date>=:period_begin and log_date<=:period_end
group by destination
into :host, :incoming_allowed
do
begin
select sum(bytes) from transfer_log
where outgoing='eth0' and incoming='ppp0' and prefix='drop'
and log_date>=:period_begin and log_date<=:period_end and destination=:host
into :incoming_rejected;
select sum(bytes) from transfer_log
where outgoing='ppp0' and incoming='eth0'
and log_date>=:period_begin and log_date<=:period_end and source=:host
into :outgoing;
suspend;
end
end ^
CREATE PROCEDURE PROXY_TRAFFIC_BY_HOSTS (PERIOD_BEGIN DATE,
PERIOD_END DATE)
RETURNS (HOST VARCHAR(15) CHARACTER SET NONE,
TOTAL BIGINT,
CACHED BIGINT)
AS
begin
for select client_address, sum(total_bytes), sum(cache_bytes) from proxy_log
where log_date>=:period_begin and log_date<=:period_end
group by client_address
into :host, :total, :cached
do
begin
suspend;
end
end ^
CREATE PROCEDURE REJECTED_INNER_TRAFFIC (PERIOD_BEGIN DATE,
PERIOD_END DATE)
RETURNS (PROTOCOL SMALLINT,
SOURCE VARCHAR(15) CHARACTER SET NONE,
SOURCE_PORT INTEGER,
DESTINATION VARCHAR(15) CHARACTER SET NONE,
DESTINATION_PORT INTEGER,
BYTES BIGINT)
AS
begin
for select protocol, source, source_port, destination, destination_port,
sum(bytes) from transfer_log
where outgoing='eth0' and incoming='ppp0' and prefix='drop'
group by protocol, source, source_port, destination, destination_port
order by 6 desc
into :protocol, :source, :source_port, :destination, :destination_port, :bytes
do
begin
suspend;
end
end ^
CREATE PROCEDURE REJECTED_OUTER_TRAFFIC (PERIOD_BEGIN DATE,
PERIOD_END DATE)
RETURNS (PROTOCOL SMALLINT,
SOURCE VARCHAR(15) CHARACTER SET NONE,
SOURCE_PORT INTEGER,
DESTINATION VARCHAR(15) CHARACTER SET NONE,
DESTINATION_PORT INTEGER,
BYTES BIGINT)
AS
begin
for select first 25 protocol, source, source_port, destination, destination_port,
sum(bytes) from transfer_log
where outgoing<>'ppp0' and incoming='ppp0' and prefix='drop'
group by protocol, source, source_port, destination, destination_port
order by 6 desc
into :protocol, :source, :source_port, :destination, :destination_port, :bytes
do
begin
suspend;
end
end ^
SET TERM ; ^
COMMIT WORK ;
GRANT SELECT ON PROXY_LOG TO USER OPERATOR;
GRANT SELECT ON TRANSFER_LOG TO USER OPERATOR;
GRANT EXECUTE ON PROCEDURE FULL_TRAFFIC TO USER OPERATOR;
GRANT EXECUTE ON PROCEDURE NAT_TRAFFIC_BY_HOSTS TO USER OPERATOR;
GRANT EXECUTE ON PROCEDURE PROXY_TRAFFIC_BY_HOSTS TO USER OPERATOR;
GRANT EXECUTE ON PROCEDURE REJECTED_INNER_TRAFFIC TO USER OPERATOR;
GRANT EXECUTE ON PROCEDURE REJECTED_OUTER_TRAFFIC TO USER OPERATOR;
COMMIT WORK ;
CREATE TABLE TRANSLATION (LANGUAGE VARCHAR(10),
OBJECT_TYPE VARCHAR(25),
SYSTEM_NAME VARCHAR(256),
TRANSLATED_NAME VARCHAR(256) CHARACTER SET WIN1251);
INSERT INTO TRANSLATION (LANGUAGE, OBJECT_TYPE, SYSTEM_NAME, TRANSLATED_NAME) VALUES ('RU', 'PROCEDURE', 'FULL_TRAFFIC', 'Общее потребление трафика');
INSERT INTO TRANSLATION (LANGUAGE, OBJECT_TYPE, SYSTEM_NAME, TRANSLATED_NAME) VALUES ('RU', 'COLUMN', 'INCOMING_ALLOWED', 'Входящий разрешенный');
INSERT INTO TRANSLATION (LANGUAGE, OBJECT_TYPE, SYSTEM_NAME, TRANSLATED_NAME) VALUES ('RU', 'COLUMN', 'INCOMING_REJECTED', 'Входящий запрещенный');
INSERT INTO TRANSLATION (LANGUAGE, OBJECT_TYPE, SYSTEM_NAME, TRANSLATED_NAME) VALUES ('RU', 'COLUMN', 'OUTGOING', 'Исходящий');
INSERT INTO TRANSLATION (LANGUAGE, OBJECT_TYPE, SYSTEM_NAME, TRANSLATED_NAME) VALUES ('EN', 'PROCEDURE', 'FULL_TRAFFIC', 'General traffic consumption');
INSERT INTO TRANSLATION (LANGUAGE, OBJECT_TYPE, SYSTEM_NAME, TRANSLATED_NAME) VALUES ('RU', 'COLUMN', 'SYSTEM_NAME', 'Системное имя');
INSERT INTO TRANSLATION (LANGUAGE, OBJECT_TYPE, SYSTEM_NAME, TRANSLATED_NAME) VALUES ('EN', 'COLUMN', 'INCOMING_REJECTED', 'Incoming rejected');
INSERT INTO TRANSLATION (LANGUAGE, OBJECT_TYPE, SYSTEM_NAME, TRANSLATED_NAME) VALUES ('EN', 'COLUMN', 'OUTGOING', 'Outgoing');
INSERT INTO TRANSLATION (LANGUAGE, OBJECT_TYPE, SYSTEM_NAME, TRANSLATED_NAME) VALUES ('RU', 'COLUMN', 'TRANSLATED_NAME', 'Описание');
INSERT INTO TRANSLATION (LANGUAGE, OBJECT_TYPE, SYSTEM_NAME, TRANSLATED_NAME) VALUES ('EN', 'COLUMN', 'SYSTEM_NAME', 'System name');
INSERT INTO TRANSLATION (LANGUAGE, OBJECT_TYPE, SYSTEM_NAME, TRANSLATED_NAME) VALUES ('EN', 'COLUMN', 'TRANSLATED_NAME', 'Description');
INSERT INTO TRANSLATION (LANGUAGE, OBJECT_TYPE, SYSTEM_NAME, TRANSLATED_NAME) VALUES ('EN', 'COLUMN', 'INCOMING_ALLOWED', 'Incomong allowed');
INSERT INTO TRANSLATION (LANGUAGE, OBJECT_TYPE, SYSTEM_NAME, TRANSLATED_NAME) VALUES ('EN', 'COLUMN', 'HOST', 'Host');
INSERT INTO TRANSLATION (LANGUAGE, OBJECT_TYPE, SYSTEM_NAME, TRANSLATED_NAME) VALUES ('RU', 'PROCEDURE', 'NAT_TRAFFIC_BY_HOSTS', 'Потребление NAT-трафика по хостам');
INSERT INTO TRANSLATION (LANGUAGE, OBJECT_TYPE, SYSTEM_NAME, TRANSLATED_NAME) VALUES ('EN', 'PROCEDURE', 'NAT_TRAFFIC_BY_HOSTS', 'NAT traffic consumption by hosts');
INSERT INTO TRANSLATION (LANGUAGE, OBJECT_TYPE, SYSTEM_NAME, TRANSLATED_NAME) VALUES ('RU', 'COLUMN', 'HOST', 'Хост');
INSERT INTO TRANSLATION (LANGUAGE, OBJECT_TYPE, SYSTEM_NAME, TRANSLATED_NAME) VALUES ('EN', 'PROCEDURE', 'PROXY_TRAFFIC_BY_HOSTS', 'Proxy traffic consumption by hosts');
INSERT INTO TRANSLATION (LANGUAGE, OBJECT_TYPE, SYSTEM_NAME, TRANSLATED_NAME) VALUES ('RU', 'PROCEDURE', 'PROXY_TRAFFIC_BY_HOSTS', 'Потребление proxy-трафика по хостам');
INSERT INTO TRANSLATION (LANGUAGE, OBJECT_TYPE, SYSTEM_NAME, TRANSLATED_NAME) VALUES ('EN', 'COLUMN', 'TOTAL', 'Total');
INSERT INTO TRANSLATION (LANGUAGE, OBJECT_TYPE, SYSTEM_NAME, TRANSLATED_NAME) VALUES ('EN', 'COLUMN', 'CACHED', 'Cached');
INSERT INTO TRANSLATION (LANGUAGE, OBJECT_TYPE, SYSTEM_NAME, TRANSLATED_NAME) VALUES ('RU', 'COLUMN', 'TOTAL', 'Общий');
INSERT INTO TRANSLATION (LANGUAGE, OBJECT_TYPE, SYSTEM_NAME, TRANSLATED_NAME) VALUES ('RU', 'COLUMN', 'CACHED', 'Из кэша');
INSERT INTO TRANSLATION (LANGUAGE, OBJECT_TYPE, SYSTEM_NAME, TRANSLATED_NAME) VALUES ('EN', 'PROCEDURE', 'REJECTED_OUTER_TRAFFIC', 'Rejected outer traffic');
INSERT INTO TRANSLATION (LANGUAGE, OBJECT_TYPE, SYSTEM_NAME, TRANSLATED_NAME) VALUES ('RU', 'PROCEDURE', 'REJECTED_OUTER_TRAFFIC', 'Запрещенный внешний трафик');
INSERT INTO TRANSLATION (LANGUAGE, OBJECT_TYPE, SYSTEM_NAME, TRANSLATED_NAME) VALUES ('EN', 'COLUMN', 'PROTOCOL', 'Protocol');
INSERT INTO TRANSLATION (LANGUAGE, OBJECT_TYPE, SYSTEM_NAME, TRANSLATED_NAME) VALUES ('EN', 'COLUMN', 'SOURCE', 'Source');
INSERT INTO TRANSLATION (LANGUAGE, OBJECT_TYPE, SYSTEM_NAME, TRANSLATED_NAME) VALUES ('EN', 'COLUMN', 'SOURCE_PORT', 'Source port');
INSERT INTO TRANSLATION (LANGUAGE, OBJECT_TYPE, SYSTEM_NAME, TRANSLATED_NAME) VALUES ('EN', 'COLUMN', 'DESTINATION', 'Destination');
INSERT INTO TRANSLATION (LANGUAGE, OBJECT_TYPE, SYSTEM_NAME, TRANSLATED_NAME) VALUES ('EN', 'COLUMN', 'DESTINATION_PORT', 'Destination port');
INSERT INTO TRANSLATION (LANGUAGE, OBJECT_TYPE, SYSTEM_NAME, TRANSLATED_NAME) VALUES ('EN', 'COLUMN', 'BYTES', 'Bytes');
INSERT INTO TRANSLATION (LANGUAGE, OBJECT_TYPE, SYSTEM_NAME, TRANSLATED_NAME) VALUES ('RU', 'COLUMN', 'PROTOCOL', 'Протокол');
INSERT INTO TRANSLATION (LANGUAGE, OBJECT_TYPE, SYSTEM_NAME, TRANSLATED_NAME) VALUES ('RU', 'COLUMN', 'SOURCE', 'Источник');
INSERT INTO TRANSLATION (LANGUAGE, OBJECT_TYPE, SYSTEM_NAME, TRANSLATED_NAME) VALUES ('RU', 'COLUMN', 'SOURCE_PORT', 'Порт источника');
INSERT INTO TRANSLATION (LANGUAGE, OBJECT_TYPE, SYSTEM_NAME, TRANSLATED_NAME) VALUES ('RU', 'COLUMN', 'DESTINATION', 'Назначение');
INSERT INTO TRANSLATION (LANGUAGE, OBJECT_TYPE, SYSTEM_NAME, TRANSLATED_NAME) VALUES ('RU', 'COLUMN', 'DESTINATION_PORT', 'Порт назначения');
INSERT INTO TRANSLATION (LANGUAGE, OBJECT_TYPE, SYSTEM_NAME, TRANSLATED_NAME) VALUES ('RU', 'COLUMN', 'BYTES', 'Количество байт');
INSERT INTO TRANSLATION (LANGUAGE, OBJECT_TYPE, SYSTEM_NAME, TRANSLATED_NAME) VALUES ('EN', 'PROCEDURE', 'REJECTED_INNER_TRAFFIC', 'Rejected inner traffic');
INSERT INTO TRANSLATION (LANGUAGE, OBJECT_TYPE, SYSTEM_NAME, TRANSLATED_NAME) VALUES ('RU', 'PROCEDURE', 'REJECTED_INNER_TRAFFIC', 'Запрещенный внутренний трафик');
COMMIT WORK;
GRANT SELECT ON TRANSLATION TO USER OPERATOR;
COMMIT WORK ;
/opt/firebird/bin/isql -i procedures.sql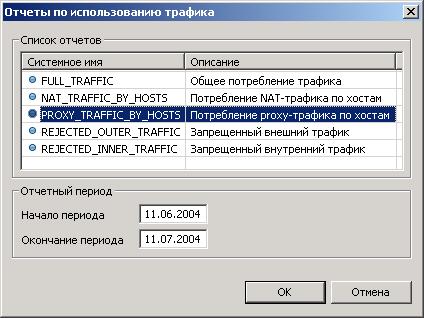
-- Потребление proxy-трафика по хостам
select * from proxy_traffic_by_hosts('11.04.2004','11.07.2004')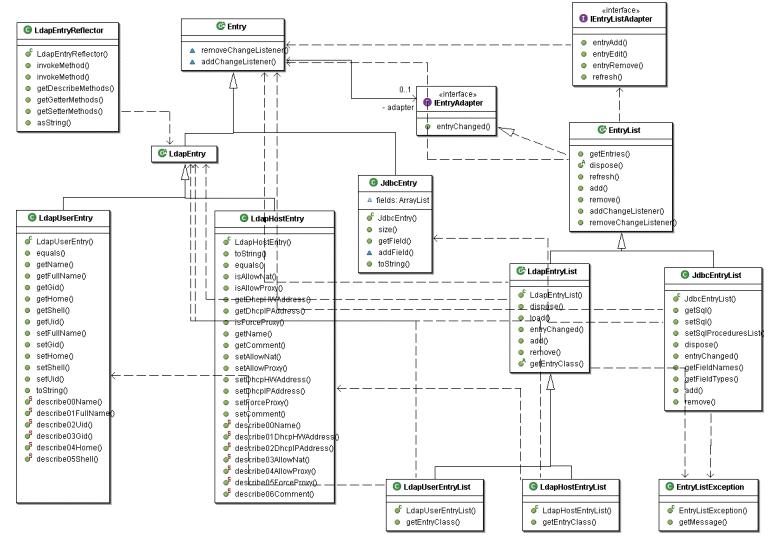
| Пакет |
Назначение |
| networkconsole.datamodel.persistance |
Сохранение/извлечение потомков
LdapEntry в/из LDAP посредством фабрик JNDI |
| networkconsole.datamodel.sax |
Представление потомков
LdapEntryList и JdbcEntryList в виде потока событий SAX для
использования в JAXP |
| networkconsole.datamodel.swt.dialogs |
Предоставление диалоговых окон для экспорта и редактирования потомков LdapEntryList и JdbcEntryList |
| networkconsole.datamodel.swt.providers |
Предоставление провайдеров JFace
отображения потомков LdapEntryList и JdbcEntryList в TableViewer |
rpm file:/home/public/distrib/nm-repository i586 nm
rpm-src file:/home/public/distrib/nm-repository
i586 nm