314
Chapter 6
Troubleshooting TCP/IP Connectivity
Problem Isolation in TCP/IP Networks
C
hapter 1 described three methods of attack for isolating network
problems. Here's a quick review:
Outside-In This approach entails starting troubleshooting at the remote
system and working back to the local host, one hop at a time.
Divide-by-Half This approach works by starting the troubleshooting in
the middle. From there, divide the isolated area in half again, and con-
tinue the troubleshooting until the problem is isolated.
Inside-Out This approach entails starting with the local host, and then
working your way to the remote host, one hop at a time.
All of these methods are effective because they are all systematic
approaches. When troubleshooting, it is very important to be systematic. By
following systematic procedures while troubleshooting, you can better man-
age the situation. If the correct process is followed, you will have documen-
tation that records all attempts made to fix the problem. This can stop you
from chasing your tail.
The outside-in method will be used in this section. Certain steps should be
followed when trying to isolate the problem. The easiest step is to use built-
in tools such as ping and traceroute. These commands are designed spe-
cifically to test reachability and path connectivity. Many problems can be
isolated by analyzing the output of these two commands.
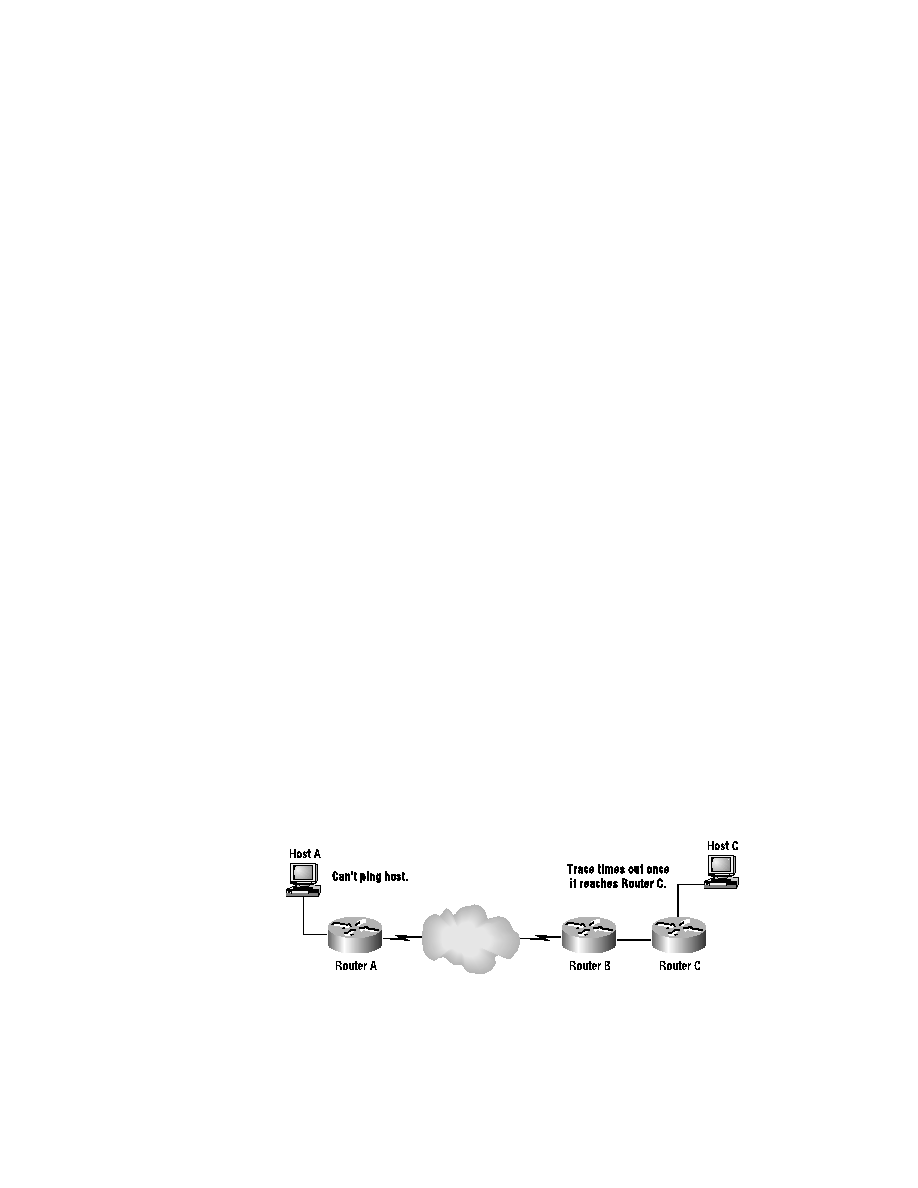
As shown in Figure 6.6, a good first step for isolating a problem between
Host A and Host C would be to ping Host C. This test indicates whether
Host C is reachable. If the ping fails, the next step would be to traceroute
to Host C. The results of the traceroute indicate where the problem is most
likely occurring.
F I G U R E 6 . 6
TCP/IP network failure isolation
Copyright ©2000 SYBEX , Inc., Alameda, CA
www.sybex.com
