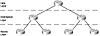
FIGURE 1.8 Logical view of the hierarchical model
| Previous | Table of Contents | Next |
Table 1.1 provides a summary of the functions defined by the hierarchical model.
| TABLE 1.1 The Three Tiers of the Hierarchical Model | |
| Tier | Function |
|---|---|
| Core | Typically inclusive of WAN links between geographically diverse locations, the core layer is responsible for the high-speed transfer of data. |
| Distribution | Usually implemented as a building or campus backbone or a limited private MAN (metropolitan-area network), the distribution layer is responsible for providing services to workgroups and departments. Policy is typically implemented at this layer, including route filters and summarization and access lists. However, the Cisco CID textbook answer for access lists is to place them in the access layer. |
| Access | The access layer provides a control point for broadcasts and additional administrative filters. The access layer is responsible for connecting users to the network and is regarded as the proper location for access lists and other services. However, network designers will need to compare their needs with the constraints of the model—it may make more sense to place an access list closer to the core, for example. The rules regarding each model are intended to provide the best performance and flexibility in a theoretical context. |
It is very important that designers understand the significance of the model’s three tiers. Therefore, let’s elaborate on the cursory definitions provided in Table 1.1. For reference, Figure 1.8 provides a logical view of the three-tier hierarchy.

FIGURE 1.8 Logical view of the hierarchical model
In generic terms, a core refers to the center of an object. In network design, this concept is expanded to mean the center of the network. Typically focused on the WAN implementation, the network core layer is responsible for the rapid transfer of data and the interconnection of various distribution and access layers. Therefore, the core routers typically do not have access lists or other services that would reduce the efficiency of the network. The core layer should be designed to have redundant paths and other fault-tolerance criteria. Without the core, all other areas would be isolated. Convergence and load balancing should also be incorporated into the core design. Note that servers, workstations, and other devices are typically not placed in the core.
Figure 1.9 illustrates the use of the core to interconnect three sites in the enterprise. This core is composed of a WAN medium—possibly Frame Relay, ATM, or point-to-point links.
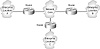
FIGURE 1.9 The core layer
In a pure three-tier model, the distribution layer serves as the campus backbone. For the exam, you should think of the core as being a WAN service that interconnects all of the sites to each other.
The distribution layer thus becomes a point in the network where policy and segregation may be implemented. Typically, the distribution layer assumes the form of a campus backbone or MAN. Access lists and other security functions are ideally placed in the distribution layer, and network advertisements and other workgroup functions are ideally contained in this layer as well.
 | Throughout this chapter the distribution and access layers are noted to be acceptable locations for access lists. This placement depends on the function of the list in question and the reduction in processing or administration that the placement will cause. Generally access lists are not included in the core layer, as historically this placement has impacted router performance substantially. The goal is to limit the number of lists required in the network and to keep them close to the edge, which encourages access-layer placement. However, given the choice of implementing 50 access-layer lists or two distribution-layer lists-all things being equal-most administrators would opt for fewer update points. Performance issues for ACLs are nowhere as significant as they once were, so this concern, especially with advanced routing such as NetFlow or multilayer switching, is substantially reduced. |
 | For the purposes of the CID exam, the proper placement of access lists is the access layer. For production networks, it is acceptable, and sometimes desirable, to place them in the distribution layer. For the CCNA/CCDA small-to-medium business examination, the proper placement of the access lists is always the distribution layer, which is different than the CID recommendation. |
For example, it would be appropriate for a SAP (Service Advertising Protocol) filter to block Novell announcements of printer services at the distribution layer because it is unlikely that users outside of the distribution layer would need access to them. The textbook answer, however, is to place access lists at the access layer of the model.
Route summarization and the logical organization of resources are also well aligned with the distribution layer. A strong design would encompass some logical method of summarizing the routes in the distribution layer. Figure 1.10 displays the IP (Internet Protocol) addressing and DNS (Domain Name Service) names for two distribution layers attached to the core. Note how 10.11.0.0/16 and 10.12.0.0/16 are divided at each router. Thus, routing tables in the core need only focus on one route, as opposed to the numerous routes that might be incorporated into the distribution area. In the same manner, the DNS subdomains are aligned with each distribution layer, which, along with IP addressing standards, will greatly augment the efficiency of the troubleshooting process. Troubleshooting is simplified when administrators can quickly identify the location and scope of a network outage—a benefit of addressing standards. In addition, route summarization, a concept presented in Chapter 4, can help avoid recalculations of the routing table that might lead to problems on lower-end routers.
| Previous | Table of Contents | Next |