
| Previous | Table of Contents | Next |
At this point, most readers preparing for the CID examination are undoubtedly well versed in the OSI (Open Systems Interconnection) model for network protocols.
 | If you need additional information regarding the OSI model and its relation-ship to the networking protocols, please consult one of the many texts on the subject, including the Sybex Network Press publications. |
This model (the OSI model) explains the functions and relationships of the individual protocols. Similarly, a number of other network design models have been established. Most of these models now focus on a single three-tier methodology. This approach preserves many of the criteria necessary for effective network design and will be presented later in this chapter.
Recall that the OSI model provides benefits in troubleshooting because each layer of the model serves a specific function. For example, the network layer, Layer 3, is charged with logical routing functions. The transport layer, Layer 4, is atop Layer 3 and provides additional services. In the TCP/IP world, Layer 3 is served by IP, and Layer 4 is served by TCP (Transmission Control Protocol) or UDP (User Datagram Protocol).
 | As a humorous aside, some network designers have added two additional layers to the OSI model—Layer 8, which refers to the political layer, and Layer 9, which represents the financial one. These layers are particularly appropriate in the context of this chapter. |
In the same manner, the network design models provide an overview of the function and abilities of each theoretical network design. The most common large network design, the three-tier approach, further defines functions for each tier. To move from one tier to another, packets should traverse the intermediate tier. Note that in this model the definitions are nowhere near as precise as they are in the OSI model, but the model should be adhered to as closely as possible.
This section will first present some of the alternatives to the OSI model and end with a detailed examination of the three-tier model. The caveats and guidelines for the three-tier approach will be examined in more detail than the other approaches, but readers and designers should consider the positive and negative impacts of each design.
The flat network may assume many forms, and it is likely that most readers are very comfortable with this design. In fact, most networks develop from this model.
A flat network contains no routers or Layer 3 awareness (Layer 3 of the OSI model). The network is one large broadcast domain. This does not preclude the incorporation of switches or bridges to isolate the collision domain boundaries and, depending upon the protocols in use, it could support up to a few hundred stations. Unfortunately though, this design rarely scales to support the demands of most networks in terms of users, flexibility, and security.
Performance may be only one concern. Typically, the need for access lists (ACLs) and other benefits at Layer 3 in the OSI model will require the incorporation of routers. The flat network model fails to address many of the important factors in network design—the most significant of which is scalability. Consider the impact of a single network interface card (NIC) sending a broadcast onto the network. At Layer 2, this broadcast would reach all stations. Should the NIC experience a fault where it continued to send broadcasts as fast as possible, the entire network would fail.
The traditional star topology typically meets the needs of a small company as it first expands to new locations. A single router, located at the company’s headquarters, interconnects all the sites. Figure 1.1 illustrates this design.
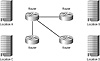
FIGURE 1.1 The star topology
The following list encompasses both the positive and negative aspects of such a topology, but the negative aspects should be somewhat obvious:
Star topologies are experiencing a resurgence with the deployment of private remote networks, including Digital Subscriber Line (DSL) and Frame Relay solutions. While the entire network will likely mesh into another model, the remote portion of the network will use the star topology. Note that the star topology is also called the hub-and-spoke model.
The ring topology builds upon the star topology with a few significant modifications. This design is typically used when a small company expands nationally and two sites are located close together. The design improves upon the star topology, as shown in Figure 1.2.
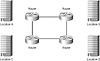
FIGURE 1.2 The ring topology
As you can see, the ring design eliminates one of the main negative aspects of the star topology. In the ring model, a single circuit failure will not disconnect any location from the enterprise network. However, the ring topology fails to address these other considerations:
Consider the last bullet item in the list and how the network designer would add a fifth location to the diagram. This is perhaps one of the most significant negative aspects of the design—a circuit will need to be removed and two new circuits added for each new location. Figure 1.3 illustrates this modification. Note that the thin line in Figure 1.3 denotes the ring configuration before Location E was added.
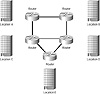
FIGURE 1.3 Adding a site in the ring topology
While the ring topology addresses the redundancy portion of the network design criteria, it fails to do so in an efficient manner. Therefore, its use is not recommended.
Mesh networks typically appear in one of two forms—full or partial. As their names imply, a full mesh interconnects all resources, whereas a partial mesh interconnects only some resources. In subsequent chapters, we will address some of the issues that impact partial-mesh implementations, including split-horizon and multiple-router hops.
Examine Figures 1.4 and 1.5, which illustrate a full- and partial-mesh network topology, respectively.
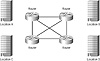
FIGURE 1.4 The full-mesh topology
Clearly, the full-mesh topology offers the network designer many benefits. These include redundancy and some scalability. However, the full-mesh network will also require a great deal of financial support. The costs in a full mesh increase as the number of PVCs (permanent virtual circuits) increases, which can eventually cause scalability problems.
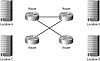
FIGURE 1.5 The partial-mesh topology
Assume that a designer is architecting a seven-site solution. Under the hub-and-spoke model, a total of six PVCs are needed (N-1). Under a full-mesh design, the number of PVCs equals 21 [N(N-1)/2]. For a small network without a well-defined central data repository, the costs may be worth the effort. In larger networks, the full-mesh design is a good tool to consider, but the associated costs and scalability issues frequently demand the use of other strategies.
| Previous | Table of Contents | Next |