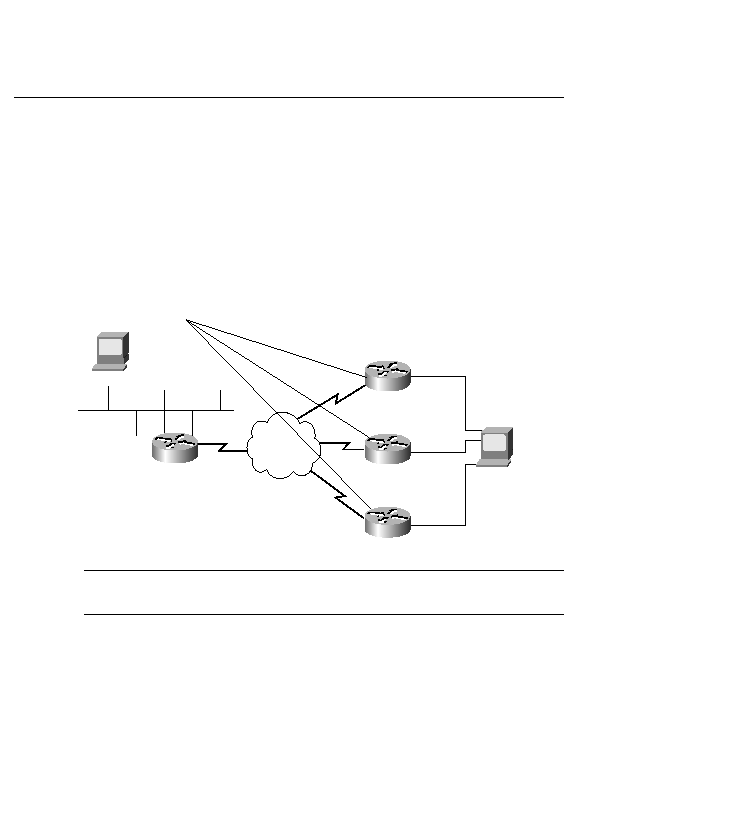
access lists can cause utilization of bandwidth. In Figure 15-11, the idea is to prevent the
desktop PC connected to R1, R2, and R3 from accessing the server on R4. It would be better to
place the access lists on R1, R2, and R3 rather than R4 because if you place the lists closer to
the source, unnecessary traffic is limited from crossing the WAN links and absorbing
bandwidth. This should be evaluated on a case-by-case basis and the proper design put
into place.
or outbound keywords are not used.
configuring simple or elaborate firewalls. As mentioned earlier, ordinary Cisco IOS is limited
in its capability when trying to protect a network. If a company is prone to denial-of-service
attacks and wants to stop being vulnerable, it needs a solution. Enter CBAC. CBAC examines
not only network layer and transport layer information, but also the application layer protocol
information (such as FTP information) to learn about the state of TCP and UDP connections.
CBAC maintains connection state information for individual connections similar to that of PIX
firewalls. This state information is used to make intelligent decisions about whether packets