Security Overview 559
-- Ping of death--A DoS type of attack that involves sending many small packets
that are reassembled by the server into large IP packets, consuming the server's
resources.
-- Mail flooding--A DoS type of attack that floods a server with e-mail and
consumes the server's resources. Other indications of this type of attack are
bandwidth consumed on the WAN links and an increase in router CPU process
utilization.
·
Configuration weaknesses--These weaknesses involve misplaced passwords, easily
guessed passwords, misconfigured equipment, and unsecured user accounts. Probably the
most common configuration weakness is with access lists--either misconfigured or
improperly placed on the router interfaces.
·
Policy weaknesses--These involve political constraints, lack of written policies, shortage
of administrative people, and so on. Most often, unauthorized changes to the network
topology or the installation of unapproved applications can create security holes.
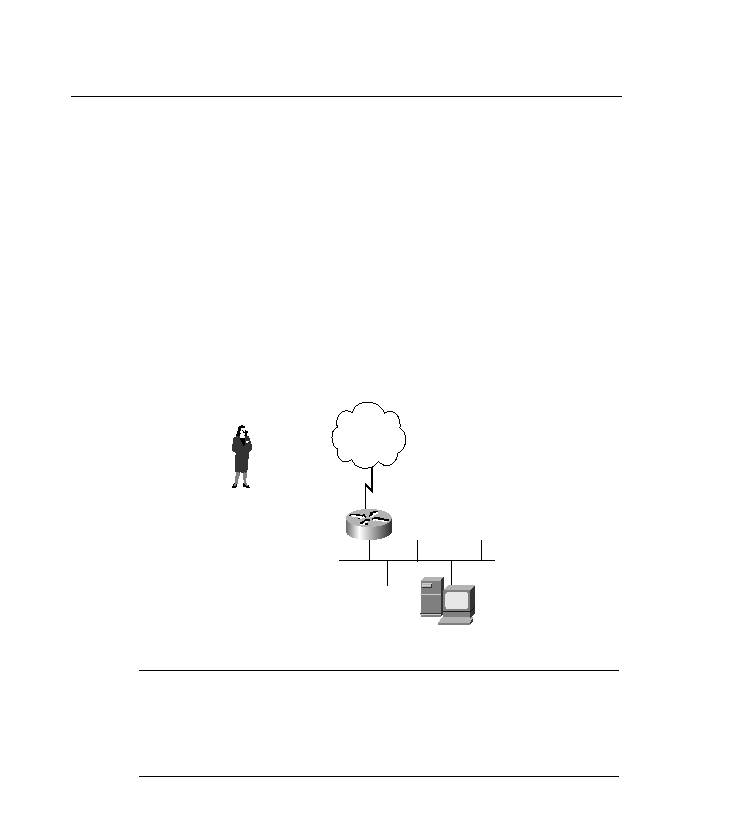
Figure 15-4
A Denial-of-Service Attack
TIP
Without the firewall feature set, Cisco routers support filtering by TCP or UDP ports and
inbound or outbound access lists. Within the Firewall feature set is content-based access
control (CBAC). CBAC has many other features, such as Java applet filtering, DoS detection
and prevention, TCP/UDP transaction logs, and real-time alerts. CBAC is available only with
the Firewall feature set. Engineers often assume that CBAC comes with the IP PLUS Feature
set, but it does not.
Internet
Server
Hacker sends many
packets to server
P P
P
PPP
P
P
P
PP
P
P
PP
P
P
P
P
P
Signs of a DOS attack:
Traffic utilization goes up
on serial link
Router processor
utilization rises
ТPУ
means packets
87200333.book Page 559 Wednesday, August 22, 2001 1:41 PM
