Serial Tunnel (STUN) 483
FEPs are encapsulated into IP packets across the STUN tunnel. STUN tunneling is always
performed on serial ports, as shown in the figure.
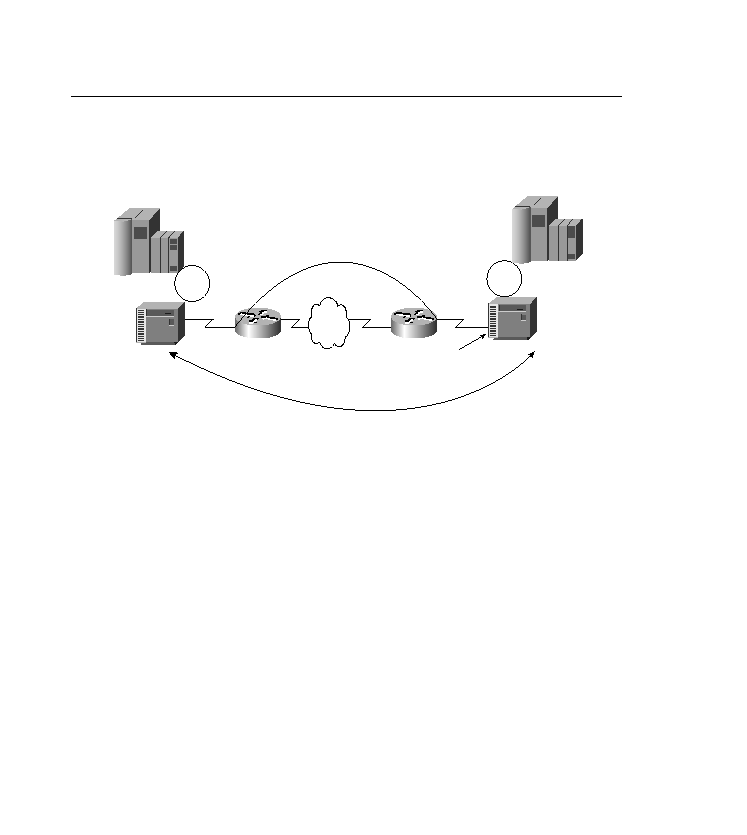
Figure 13-7
STUN FEP to FEP
In Figure 13-7, the tunnel is created using a TCP connection between the routers. The command
stun route all TCP 1.1.1.1 is applied to the serial interface and creates the tunnel. The
advantage of using TCP is that it lets the router provide the TCP acknowledgments locally
versus across the WAN. Acknowledging locally can increase throughput.
STUN Transport Protocols
STUN has three transport protocols available as choices for the CCDP:
·
TCP for local acknowledgment. It has the most overhead, but it also supports the most
features, including local acknowledgment. Choose this method if there are multiple
routers between endpoints of the STUN tunnels or if the redundancy and availability
requirements are critical. Figure 13-8 illustrates the TCP method for STUN.
IBM S/370
Token
Ring
IBM 3x74
IBM 3x74
Token
Ring
IBM S/370
IP
cloud
S0
SDLC
S0
SDLC
Router provides
acknowledgments
to FEP
Stun tunnel is from
serial port to
serial port
SDLC
87200333.book Page 483 Wednesday, August 22, 2001 1:41 PM
